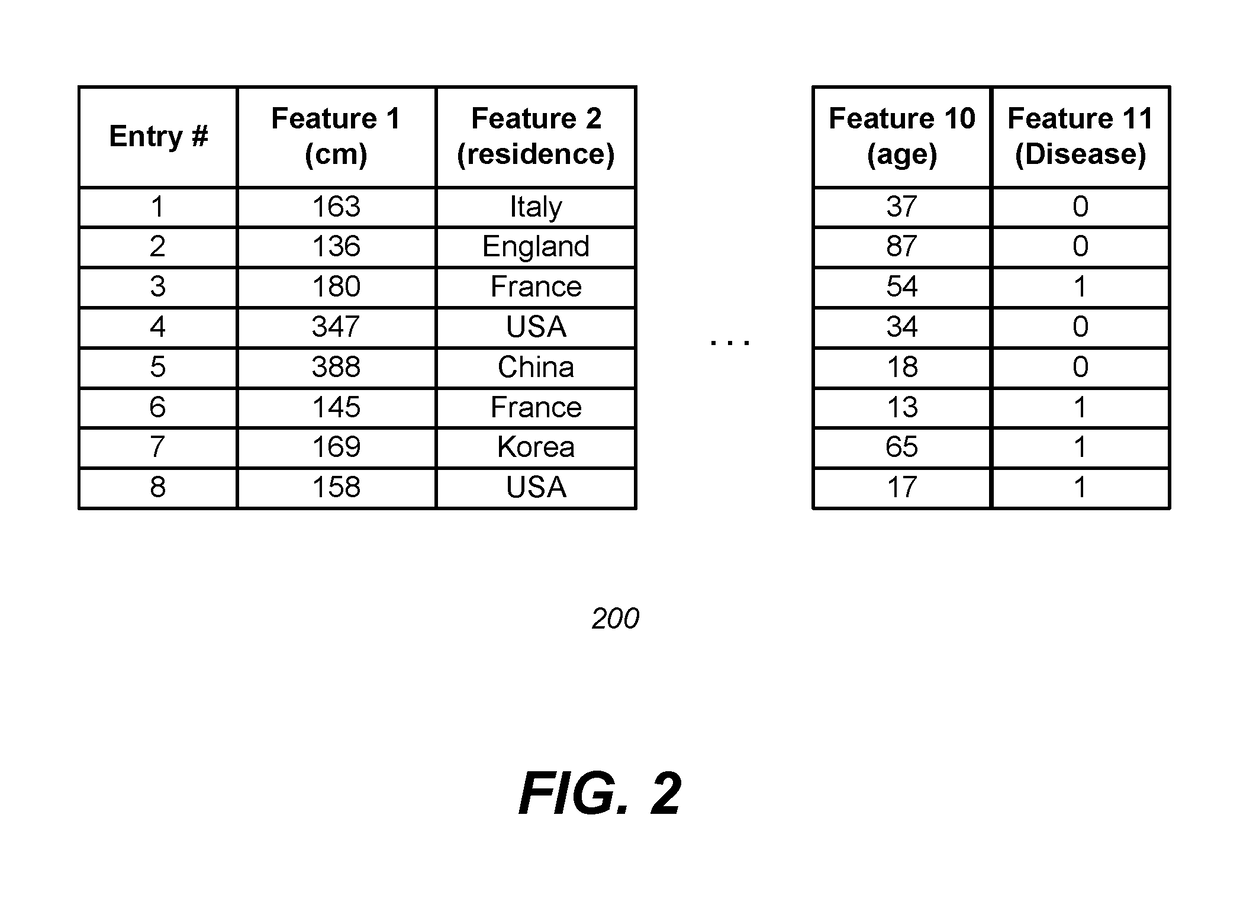
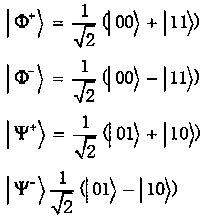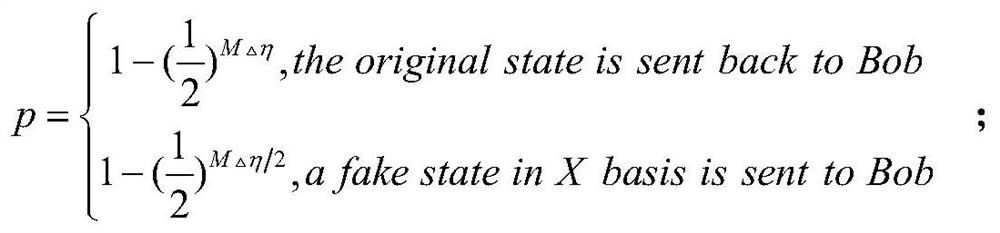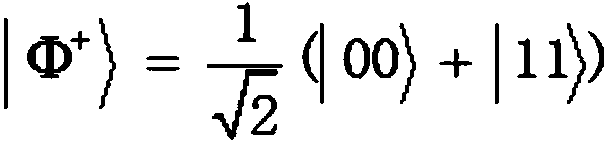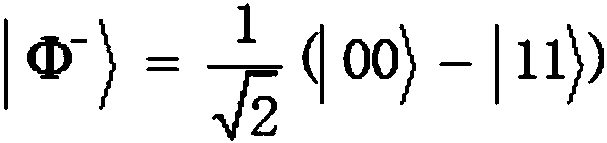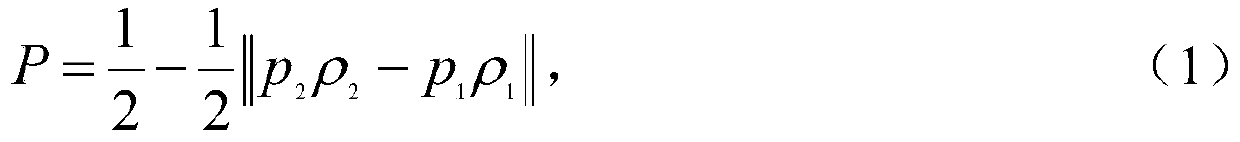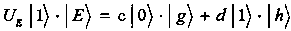Patents
Literature
30 results about "Database privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
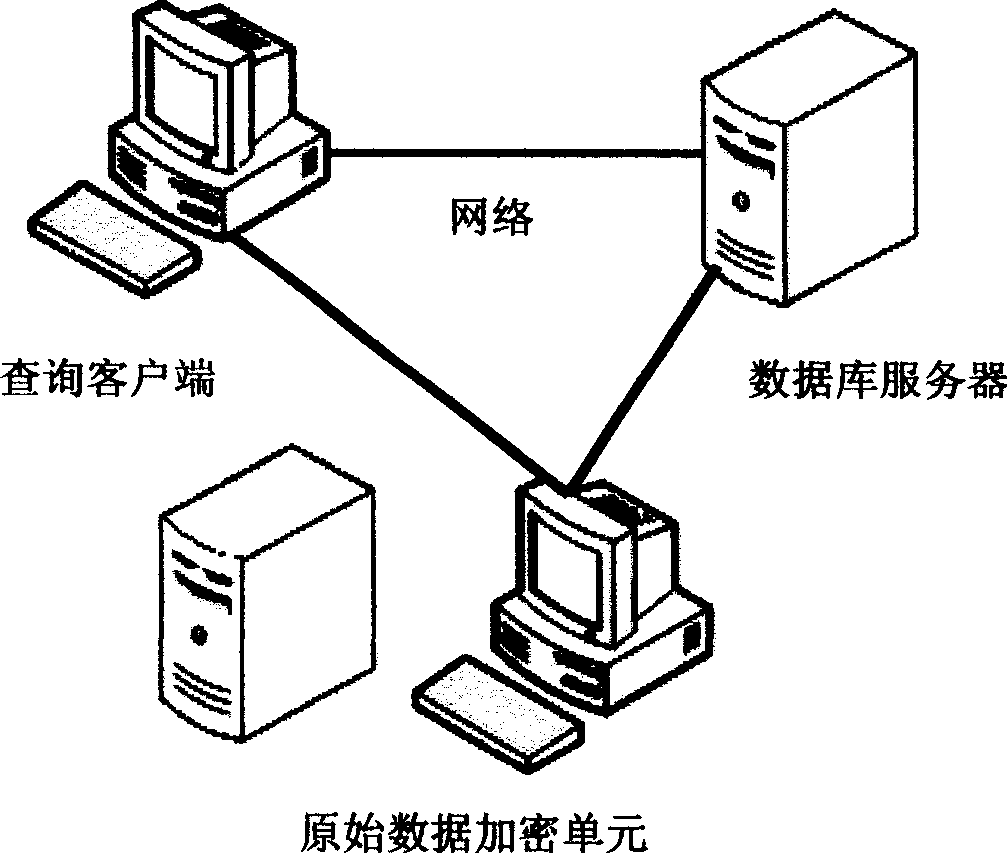
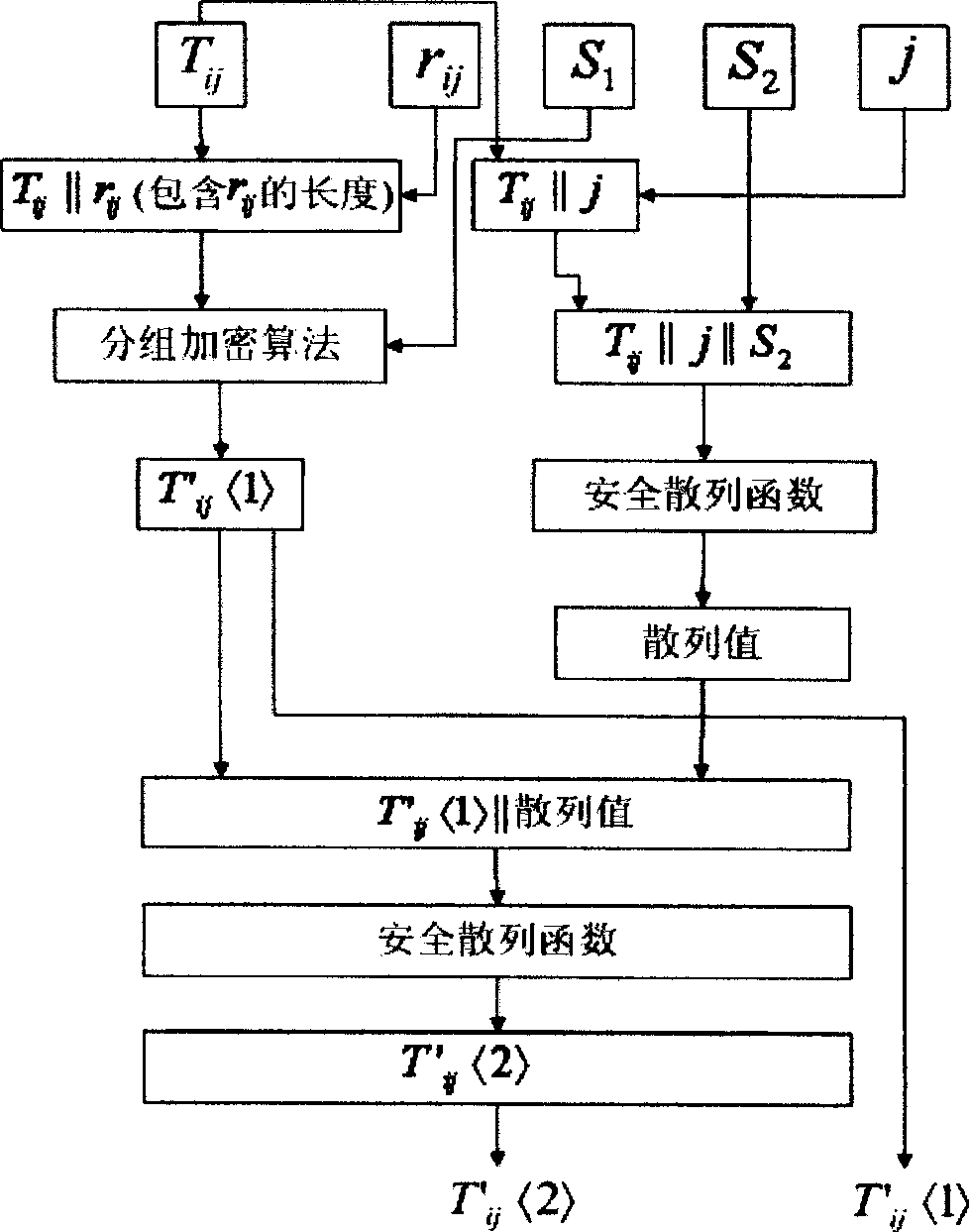
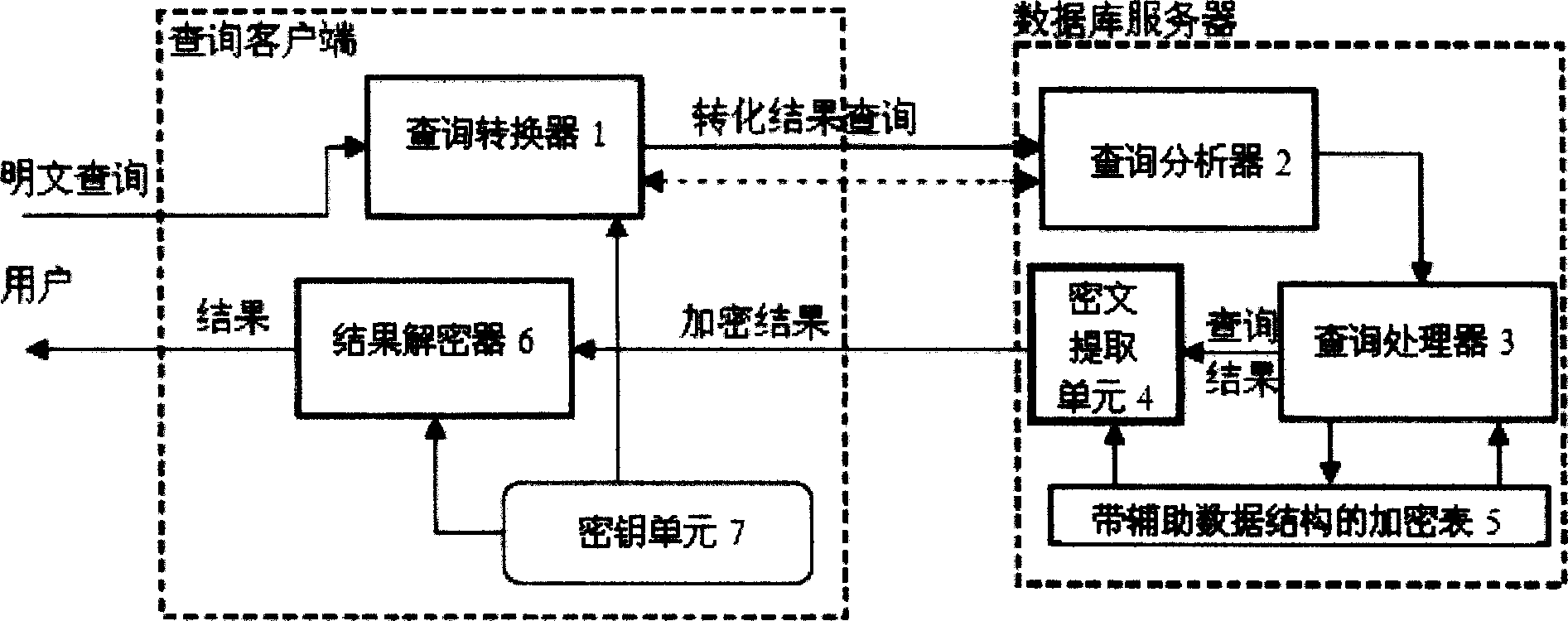
Ciphertext database privacy protection enquiring method
InactiveCN101436208AAchieve excellent efficiencySpecial data processing applicationsCiphertextDatabase server
The invention relates to realization of query of encrypted database tables by utilization of a structuralized additional data structure on the premise that an internal operating mechanism of a database management system is not changed, which comprises an encrypt data containing an index query structure generation method and a whole encrypt query process. A database server judges the retrievable information range of cryptographic keys of certain levels held by users first, and quickly performs information retrieval within the information range, so as to protect the privacy of information in the database.
Owner:BEIJING JIAOTONG UNIV
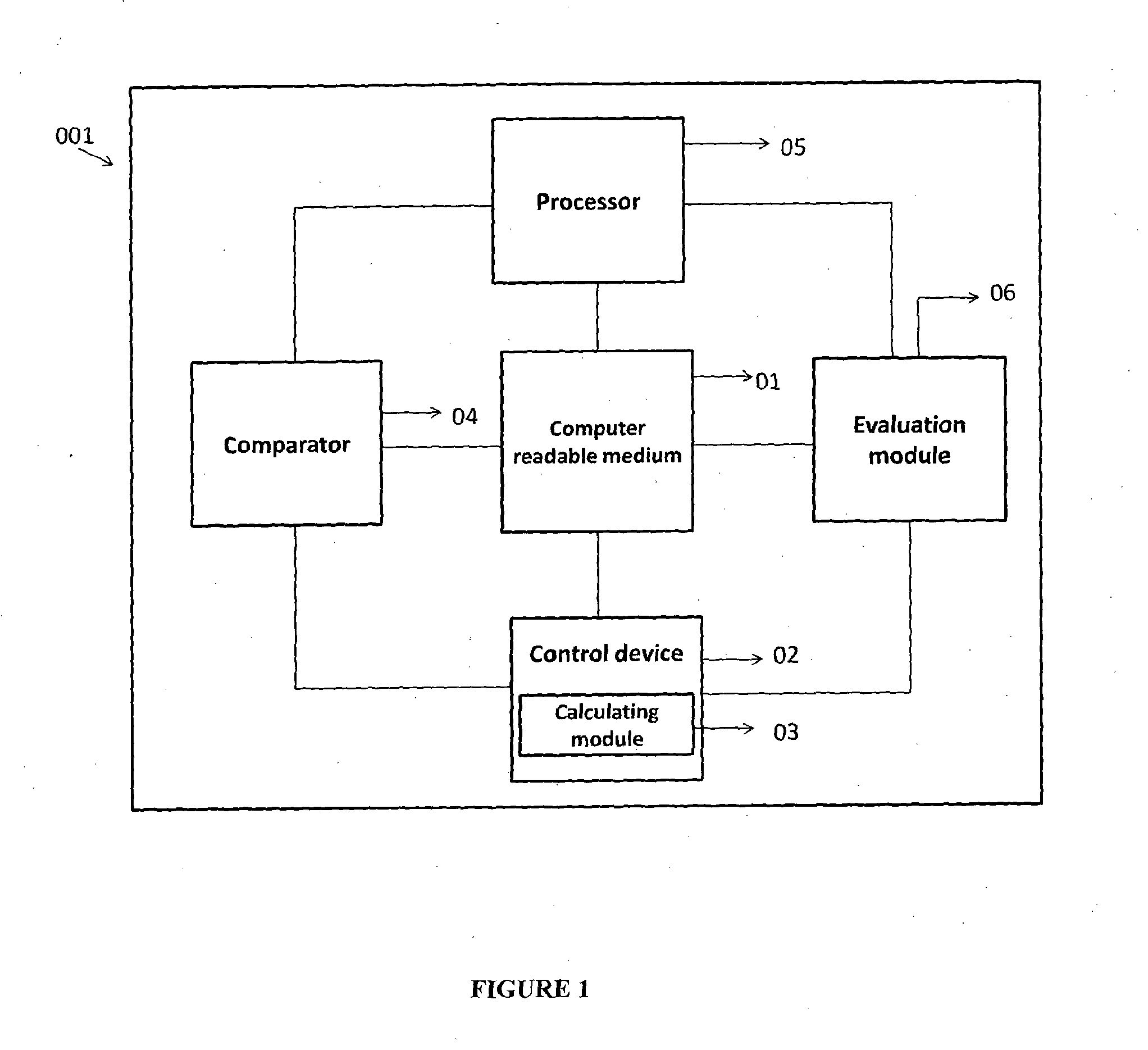
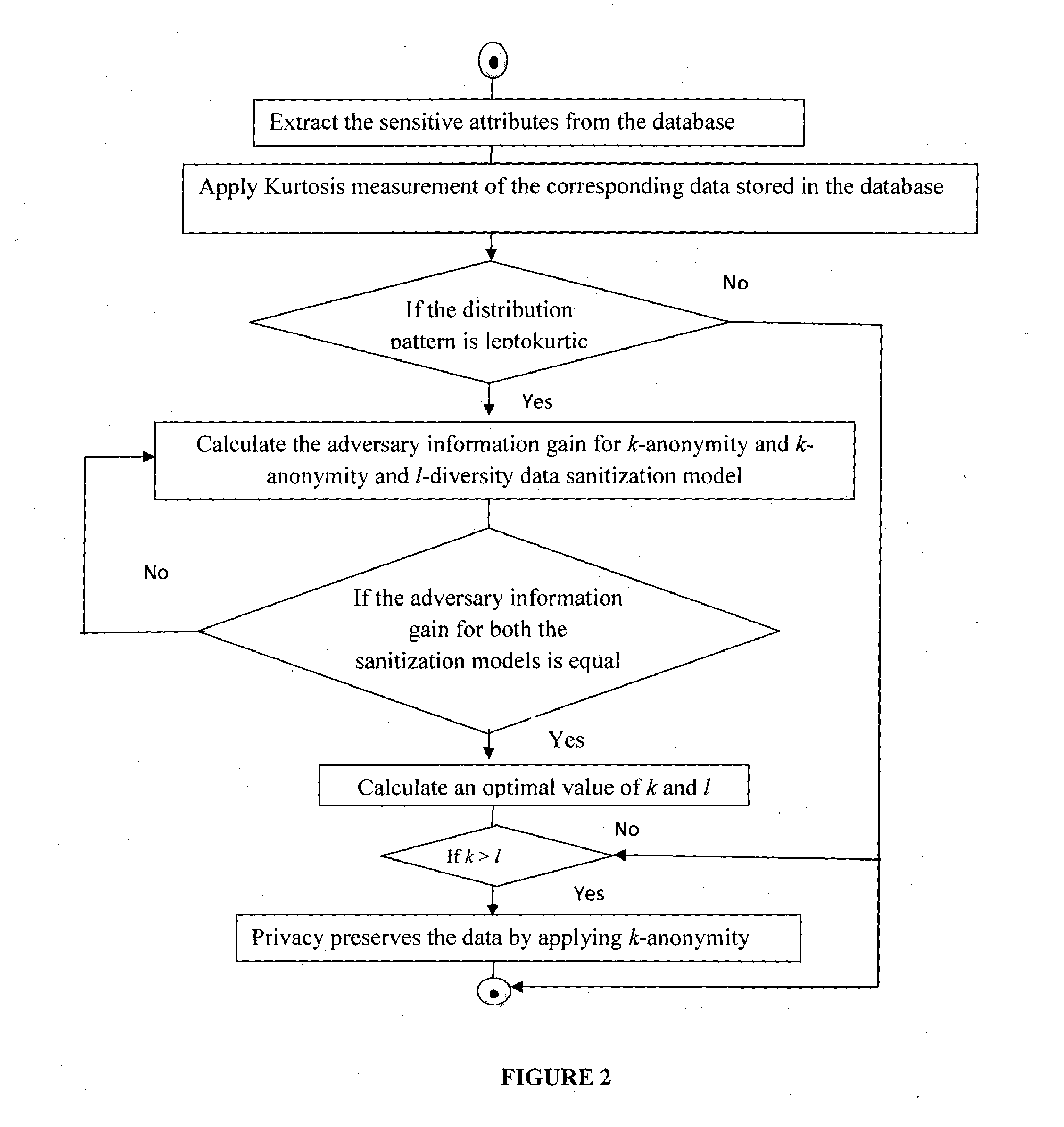
System and method for database privacy protection
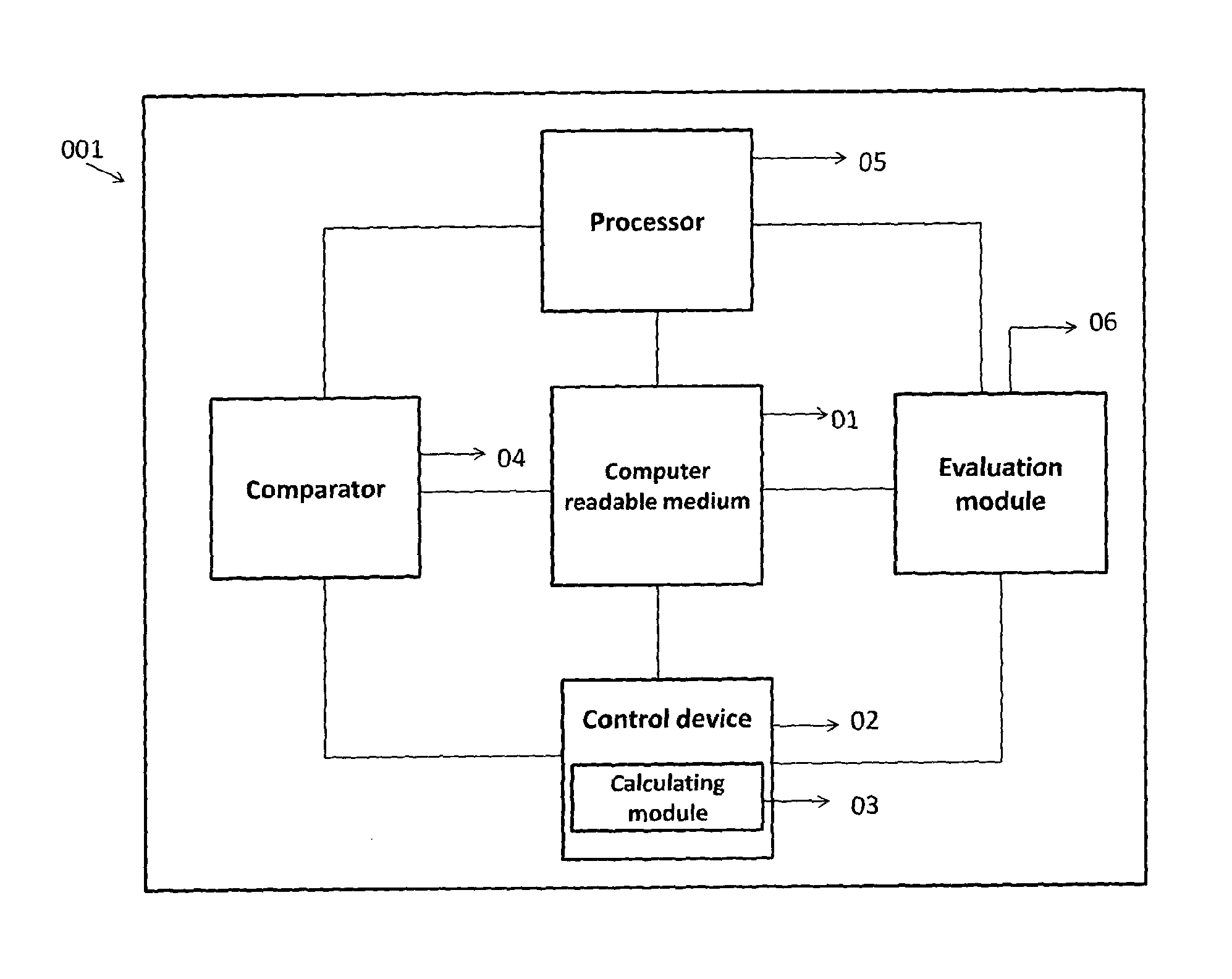
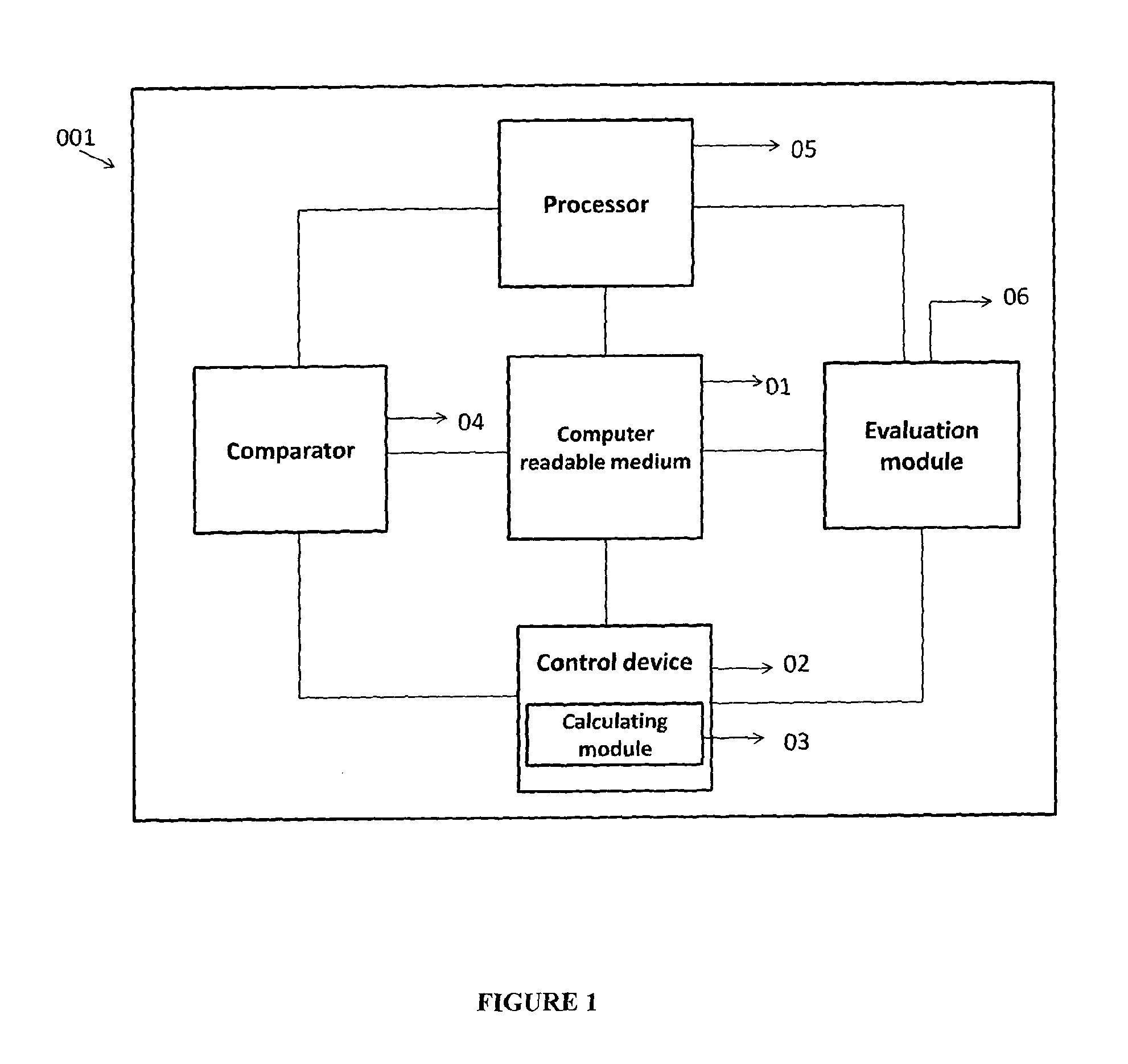
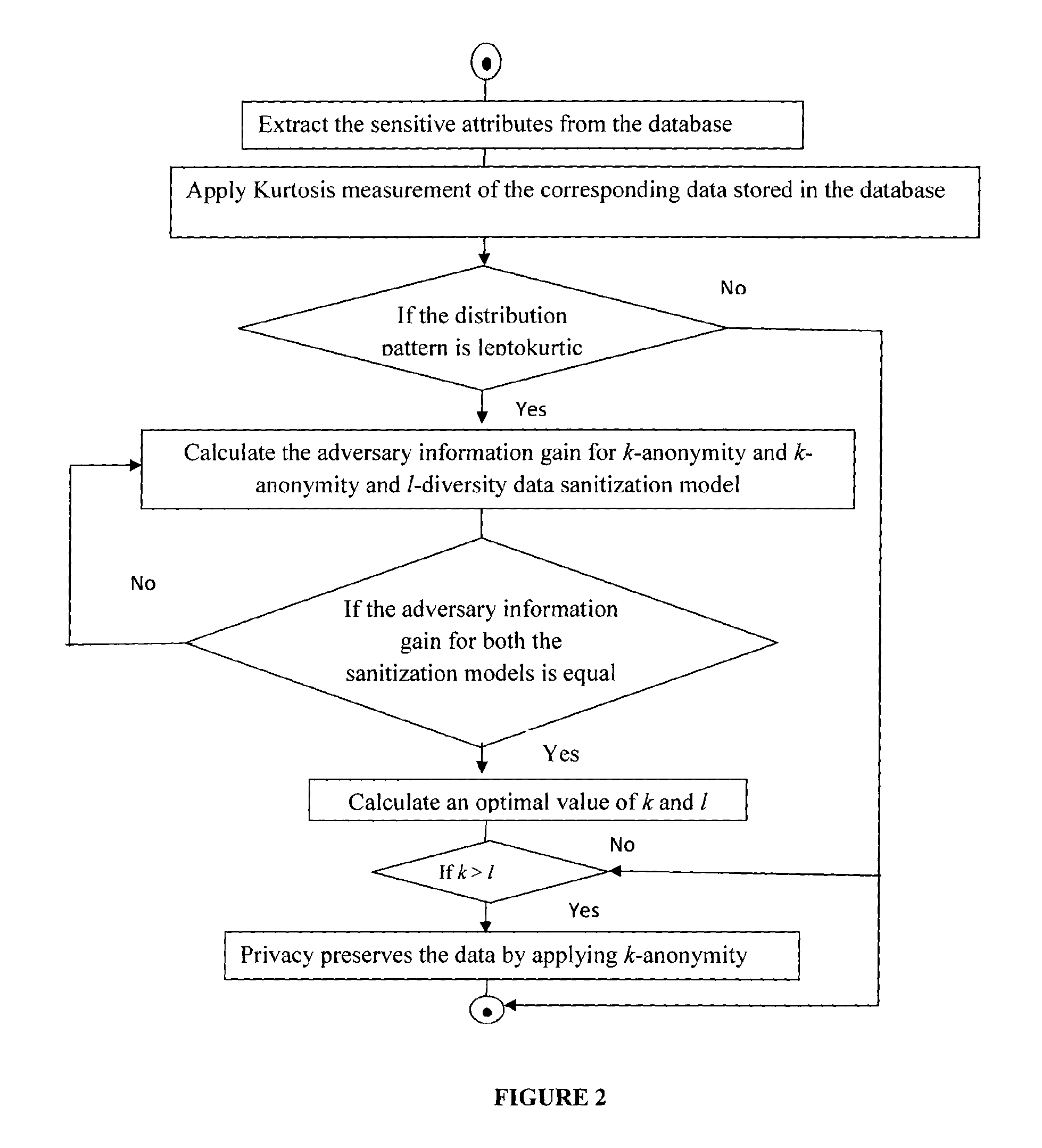
ActiveUS20140237620A1Reduce complexitySame quantityDigital data processing detailsAnalogue secracy/subscription systemsK-anonymityAdversary
The invention relates to a system and a method for privacy preservation of sensitive attributes stored in a database. The invention reduces the complexity and enhances privacy preservation of the database by determining the distribution of sensitive data based on Kurtosis measurement. The invention further determines and compares the optimal value of k-sensitive attributes in k-anonymity data sanitization model with the optimal value of l sensitive attributes in l diversity data sanitization model using adversary information gain. The invention reduces the complexity of the method for preserving privacy by applying k anonymity only, when the distribution of the sensitive data is leptokurtic and optimal value of k is greater than the optimal value of l.
Owner:TATA CONSULTANCY SERVICES LTD
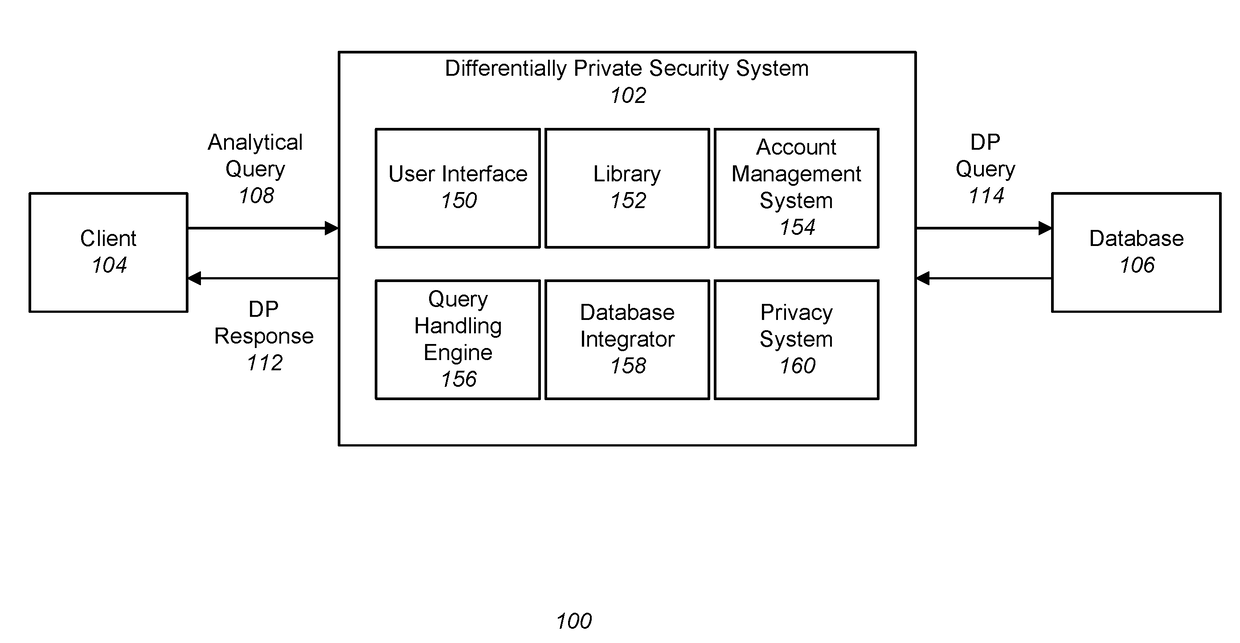
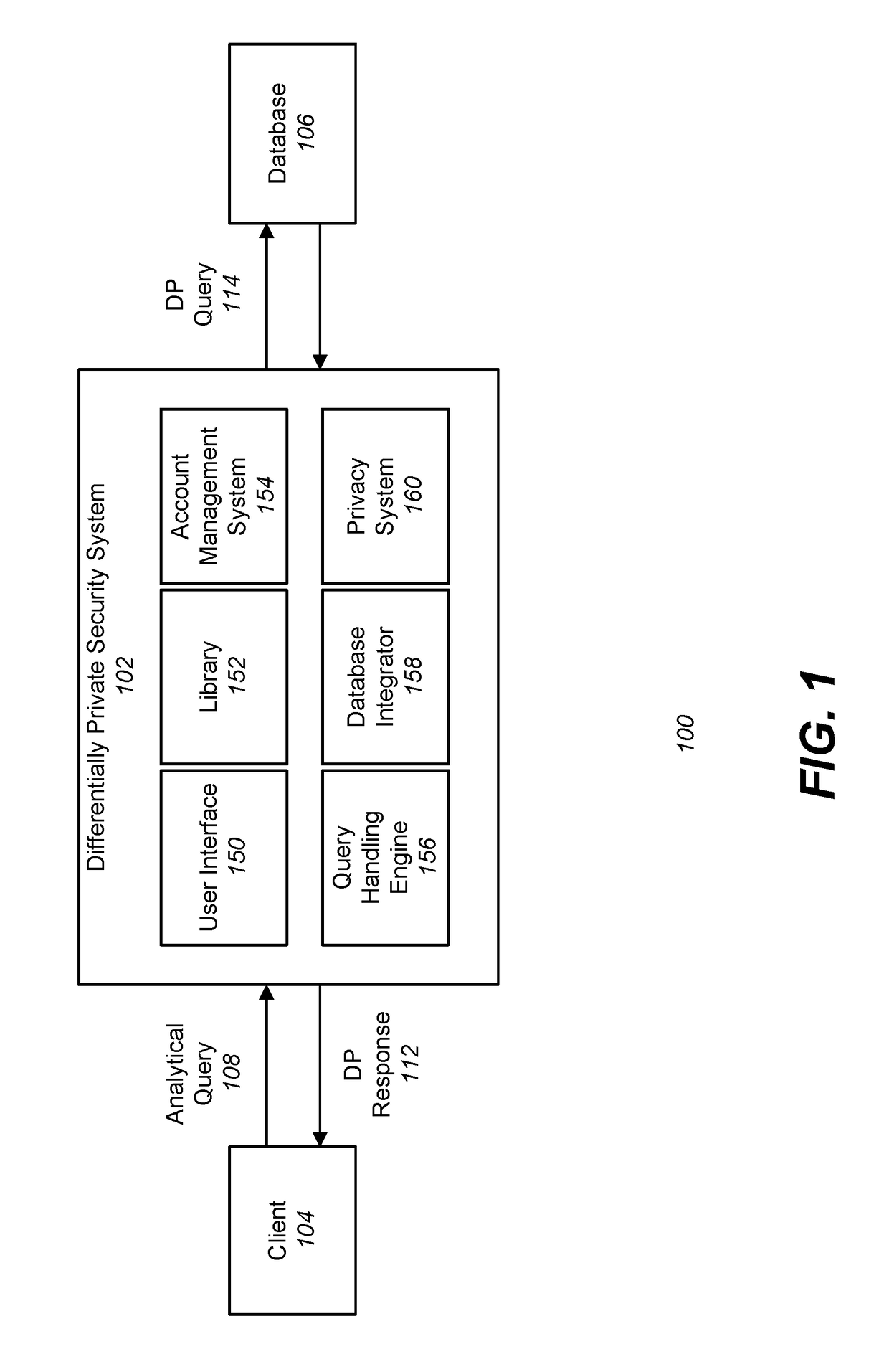
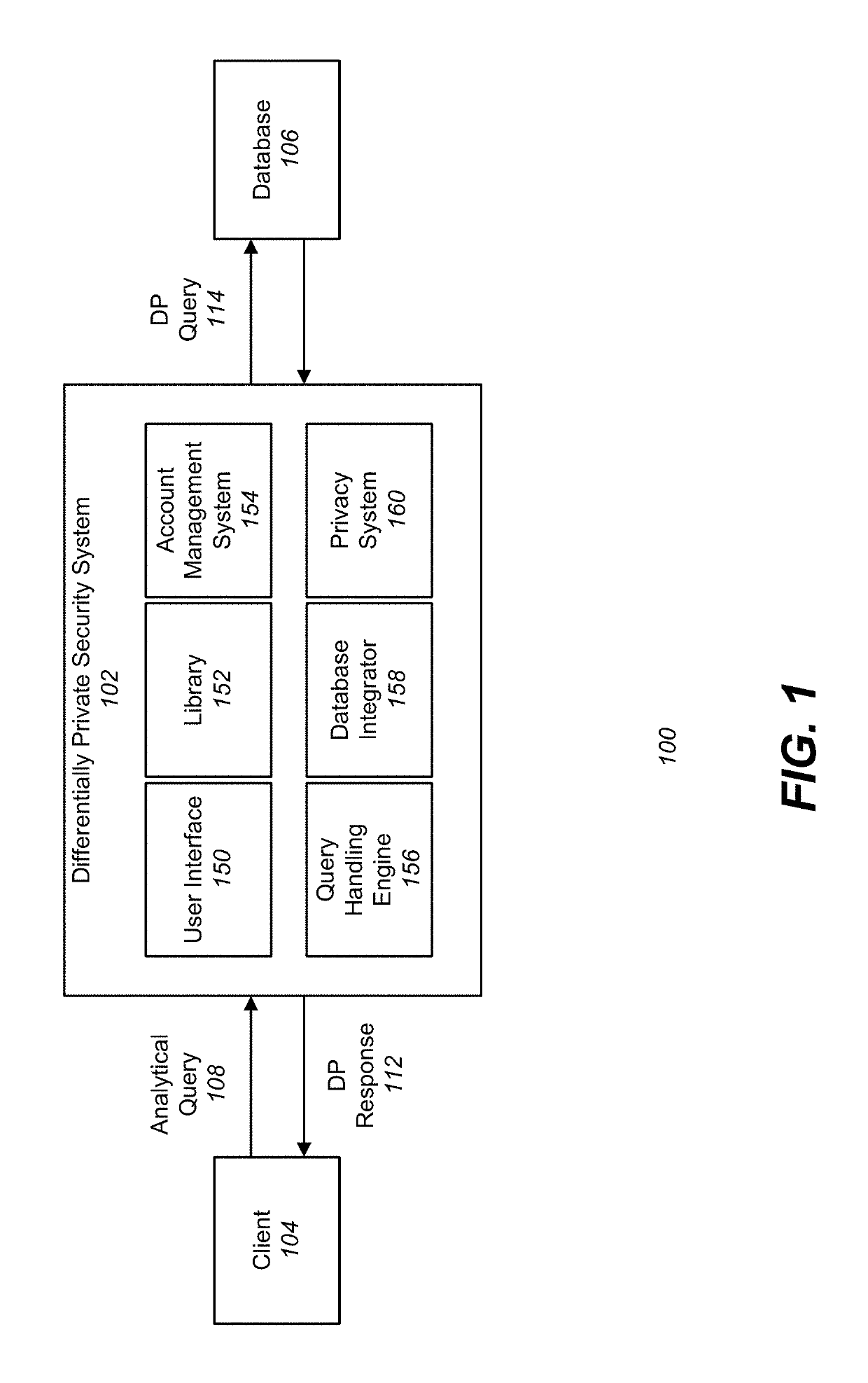
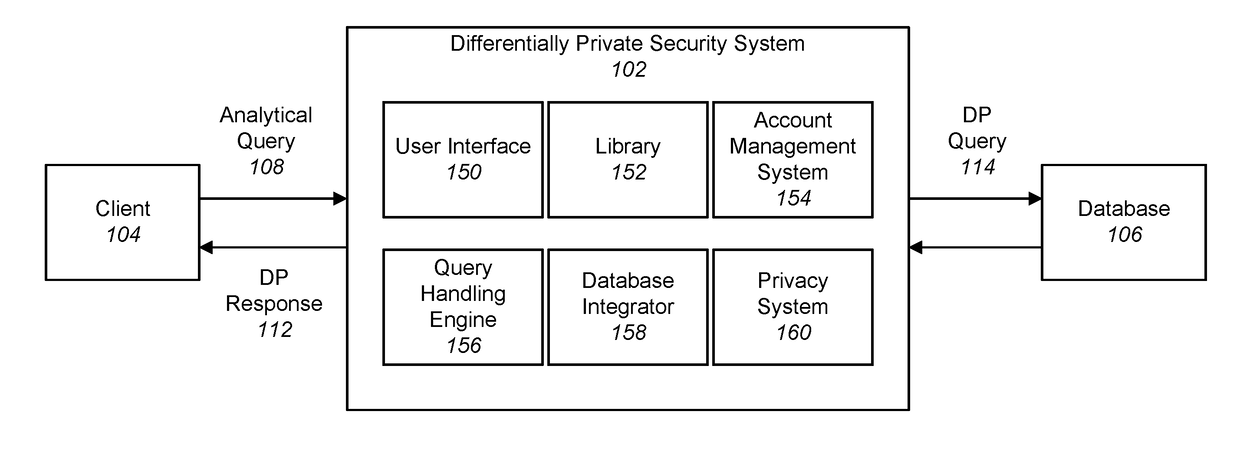
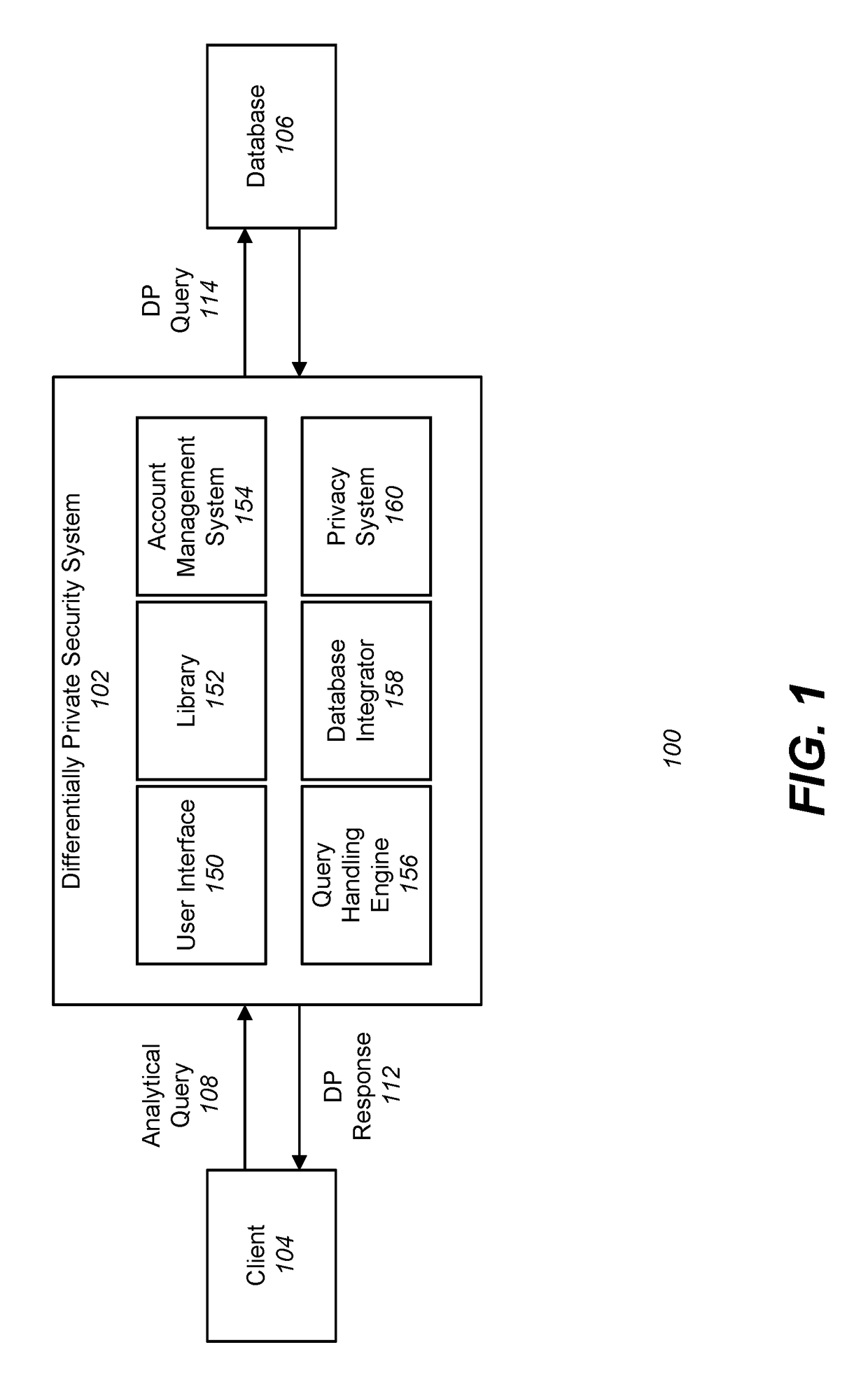
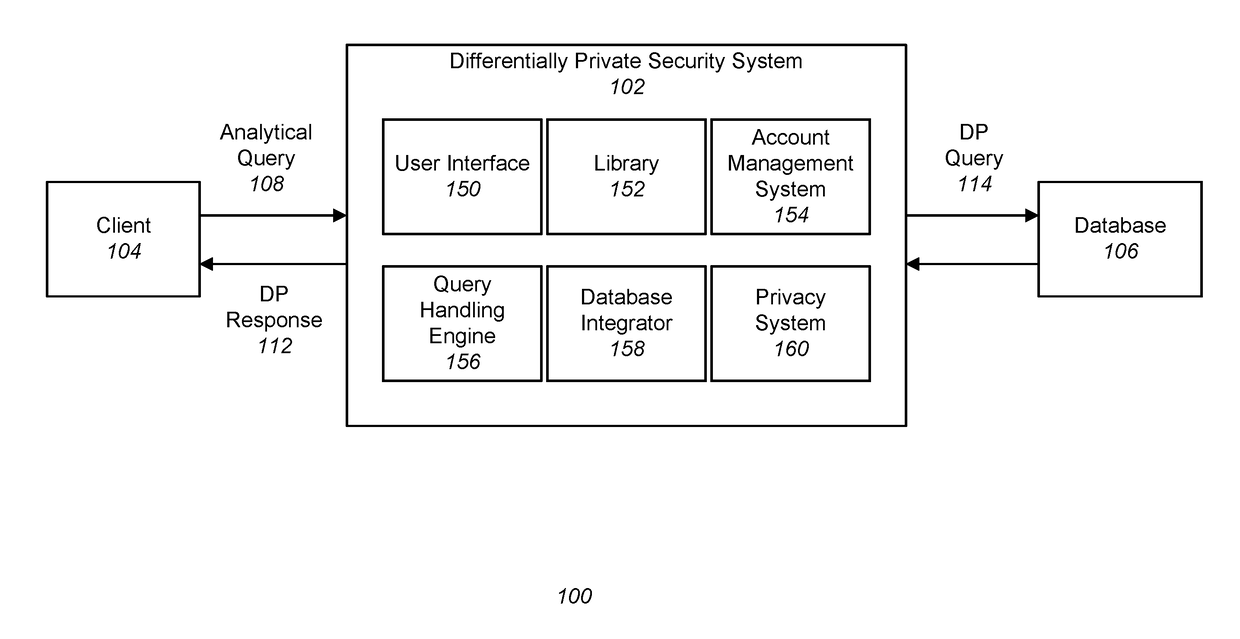
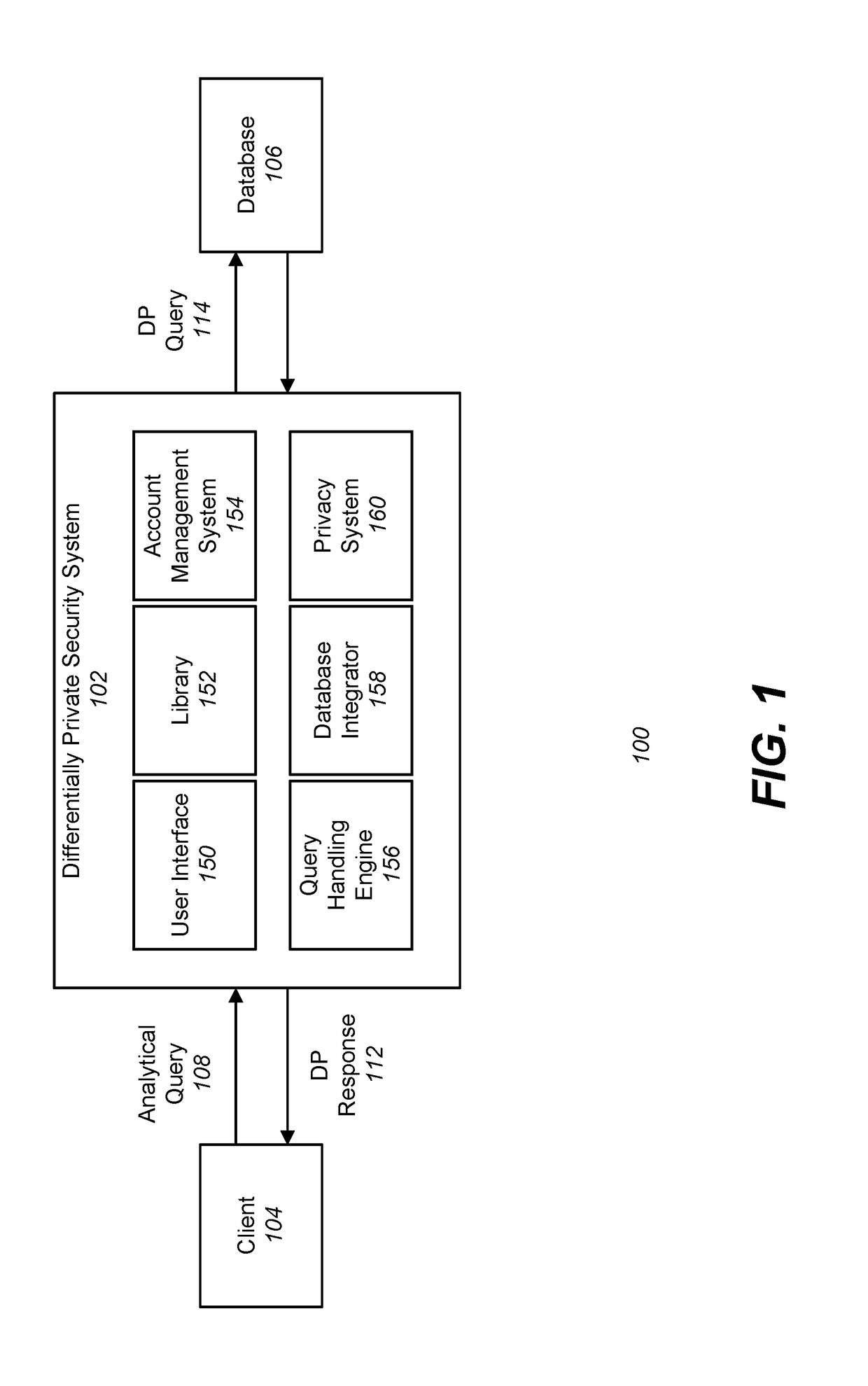
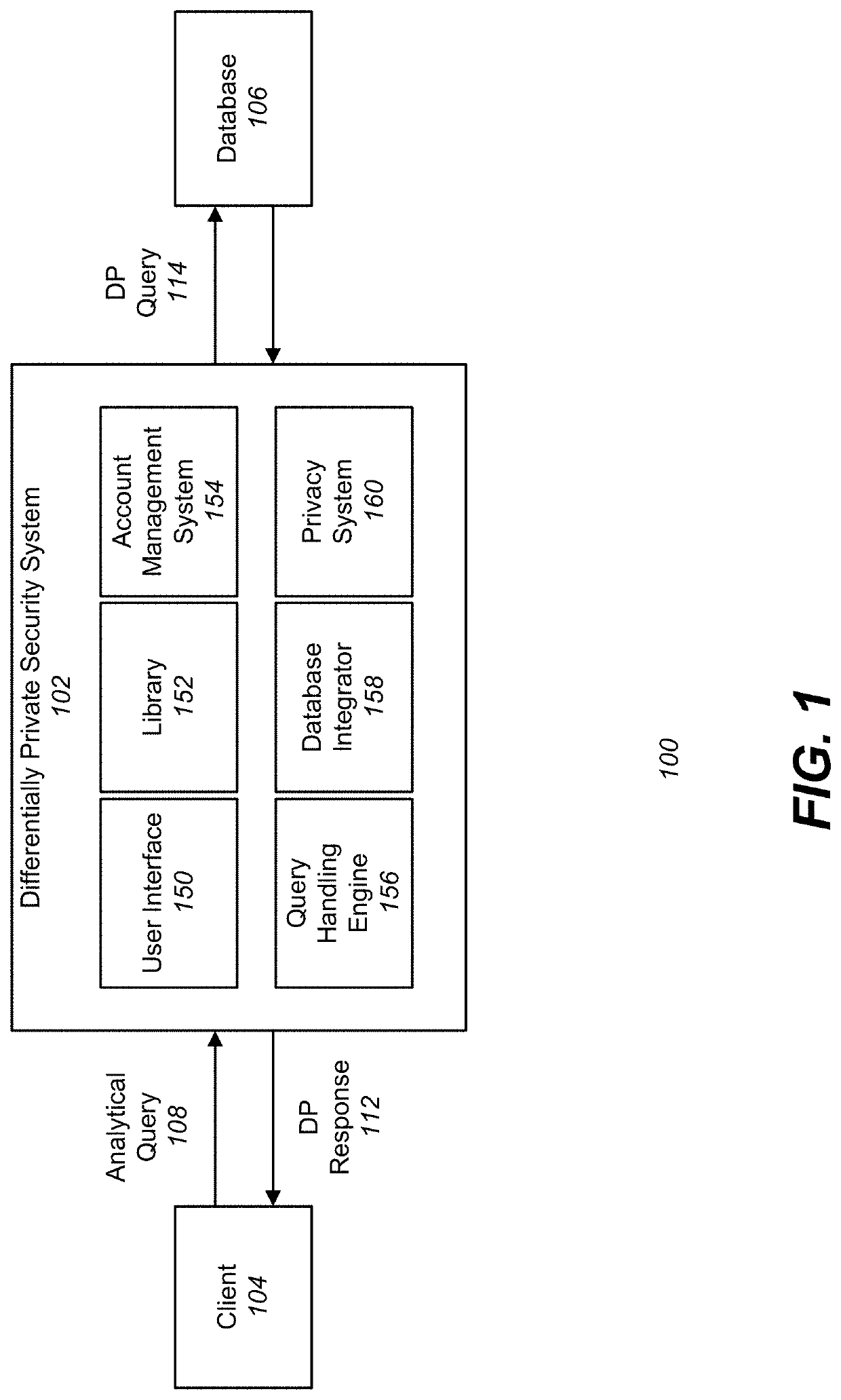
Differentially private processing and database storage
A hardware database privacy device is communicatively coupled to a private database system. The hardware database privacy device receives a request from a client device to perform a query of the private database system and identifies a level of differential privacy corresponding to the request. The identified level of differential privacy includes privacy parameters (∈,δ) indicating the degree of information released about the private database system. The hardware database privacy device identifies a set of operations to be performed on the set of data that corresponds to the requested query. After the set of data is accessed, the set of operations is modified based on the identified level of differential privacy such that a performance of the modified set of operations produces a result set that is (∈,δ)-differentially private.
Owner:SNOWFLAKE INC
Differentially private processing and database storage
A hardware database privacy device is communicatively coupled to a private database system. The hardware database privacy device receives a request from a client device to perform a query of the private database system and identifies a level of differential privacy corresponding to the request. The identified level of differential privacy includes privacy parameters (ε,δ) indicating the degree of information released about the private database system. The hardware database privacy device identifies a set of operations to be performed on the set of data that corresponds to the requested query. After the set of data is accessed, the set of operations is modified based on the identified level of differential privacy such that a performance of the modified set of operations produces a result set that is (ε,δ)-differentially private.
Owner:SNOWFLAKE INC
Differentially Private Processing and Database Storage
A hardware database privacy device is communicatively coupled to a private database system. The hardware database privacy device receives a request from a client device to perform a query of the private database system and identifies a level of differential privacy corresponding to the request. The identified level of differential privacy includes privacy parameters (ε,δ) indicating the degree of information released about the private database system. The hardware database privacy device identifies a set of operations to be performed on the set of data that corresponds to the requested query. After the set of data is accessed, the set of operations is modified based on the identified level of differential privacy such that a performance of the modified set of operations produces a result set that is (ε,δ)-differentially private.
Owner:SNOWFLAKE INC
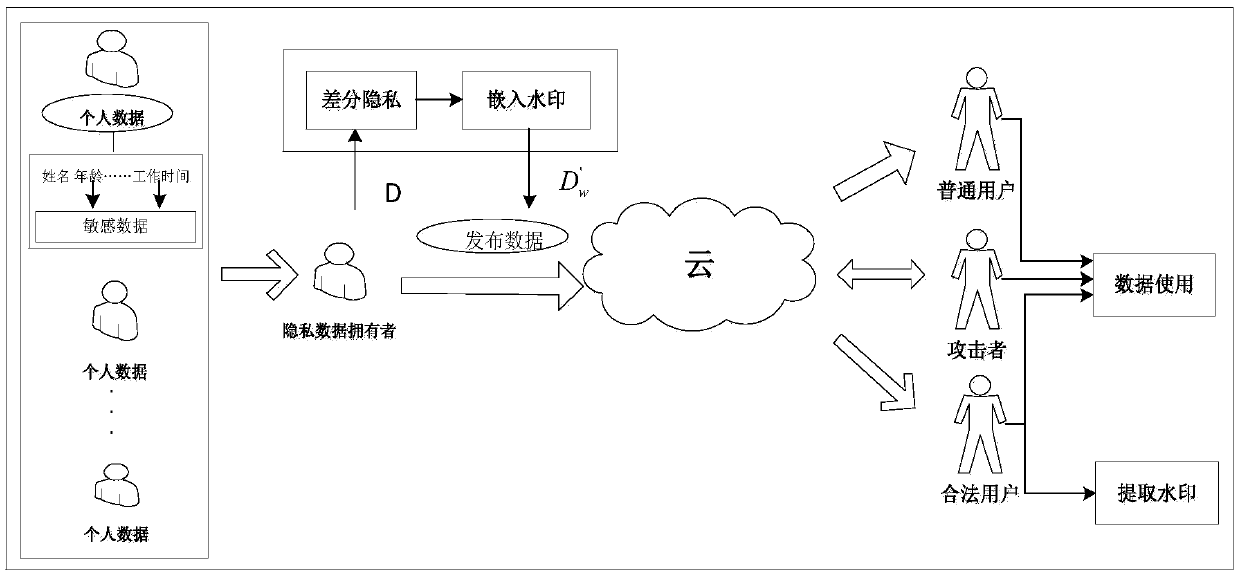
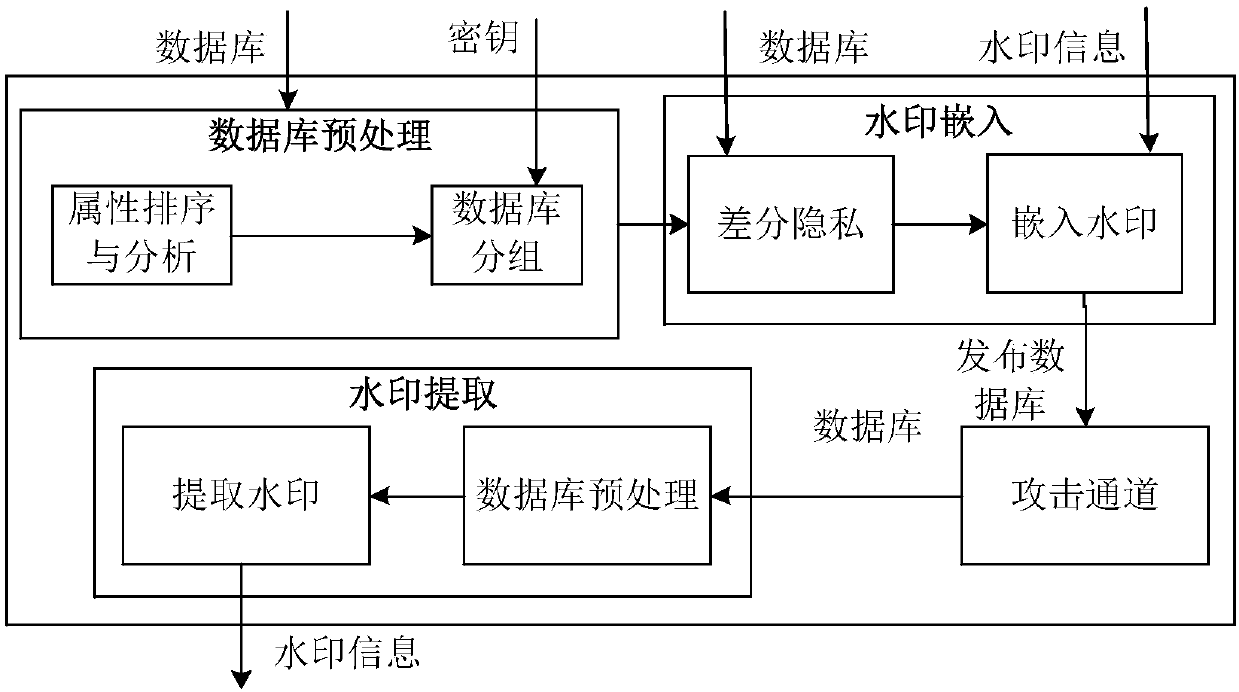
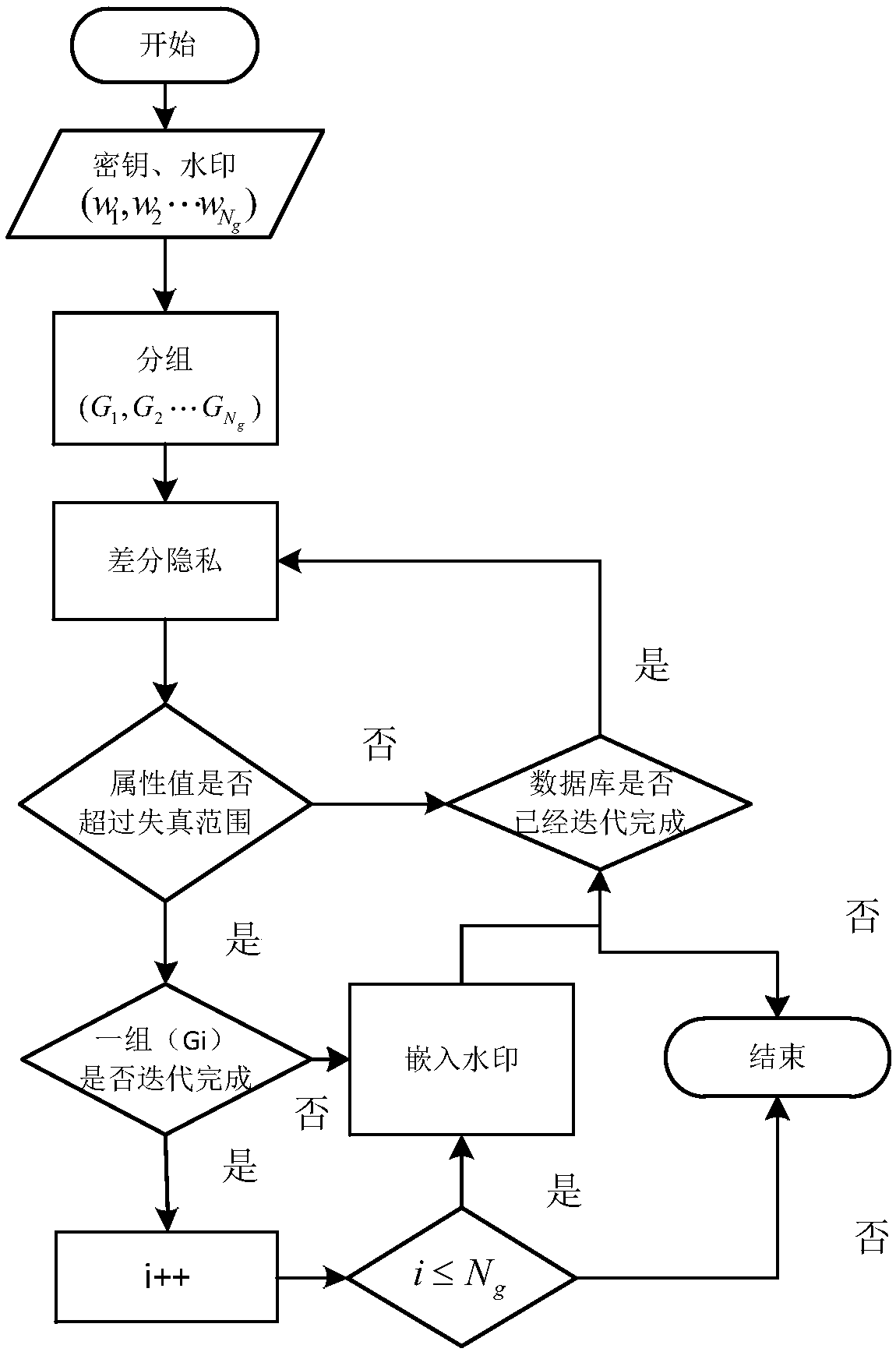
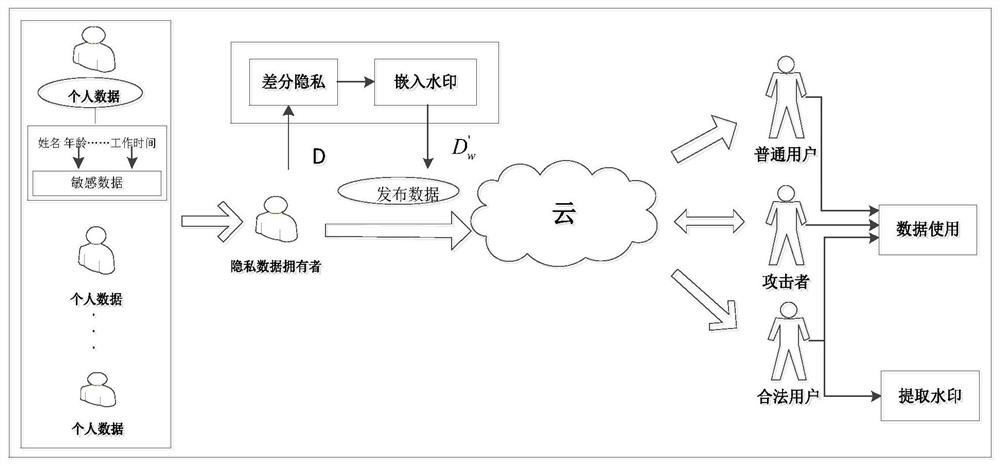
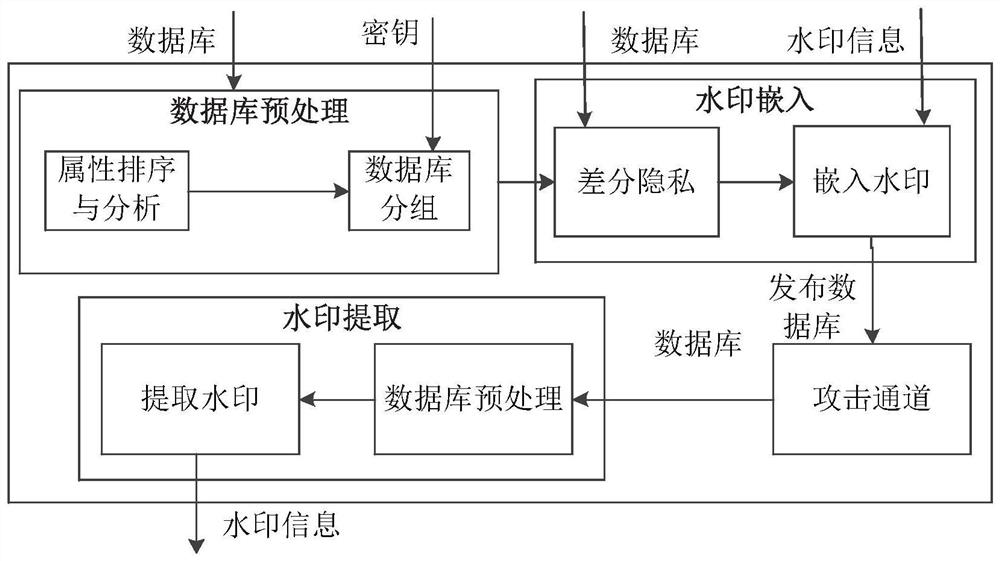
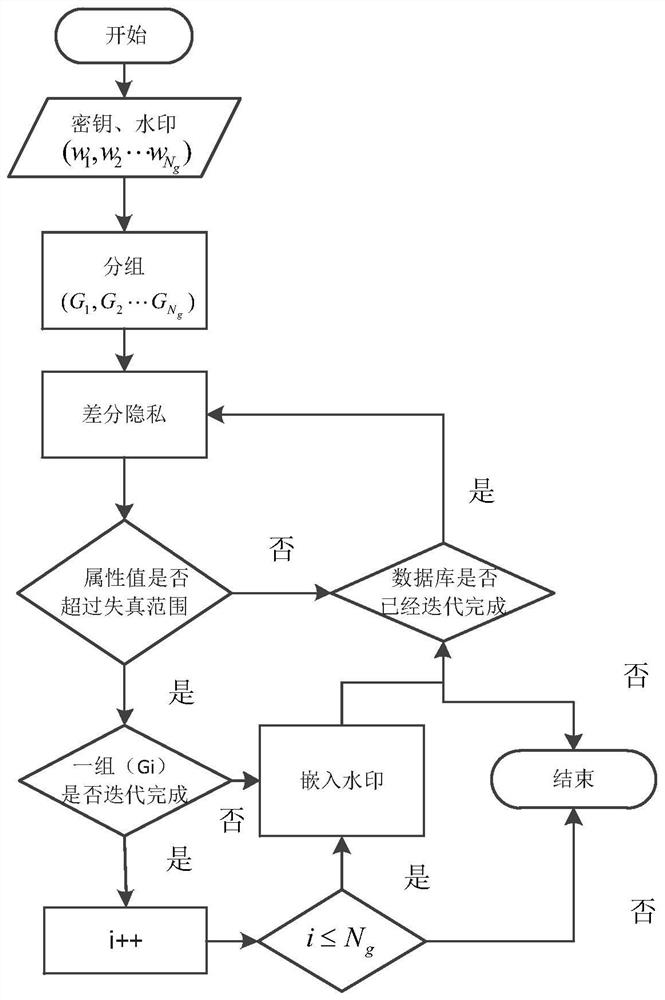
Database watermarking based on local differential privacy
ActiveCN109033766ACopyright protectionProtect private informationProgram/content distribution protectionData integrityWatermark method
The invention discloses a database watermark method based on local differential privacy. The method comprises: sorting the attributes according to the attribute name of the database, and grouping thetuples according to the primary key of the tuples in the database for embedding the watermark; performing differential privacy of sensitive attributes in database; the watermark being embedded according to the characteristics of the data in the database after differential privacy, and then the watermarked database being published to the cloud; users downloading published databases from the cloud,watermarks being extracted from published databases for copyright tracking and data integrity verification. The database watermarking method based on the local differential privacy not only maintainsthe nature of the differential privacy but also reduces the data distortion caused by the differential privacy, and has high robustness against various attacks such as the addition, modification, deletion and the like of the database. The invention is used for providing a comprehensive protection mechanism for the security of database privacy, tamper integrity, source reliability and the like.
Owner:HEFEI UNIV OF TECH
Differentially Private Processing and Database Storage
Owner:SNOWFLAKE INC
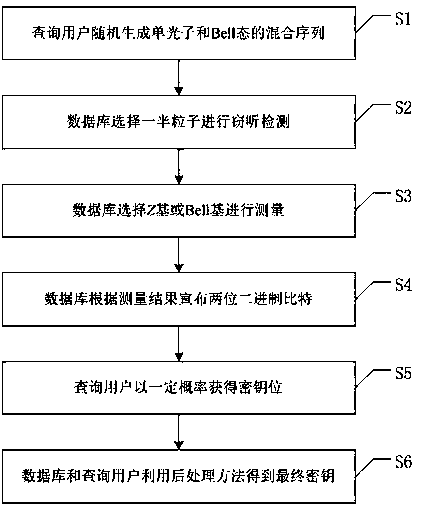
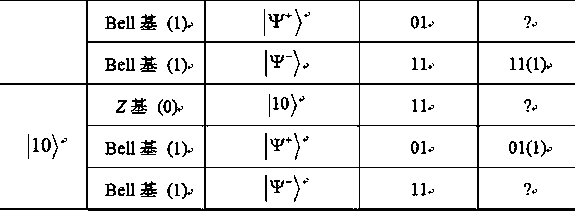
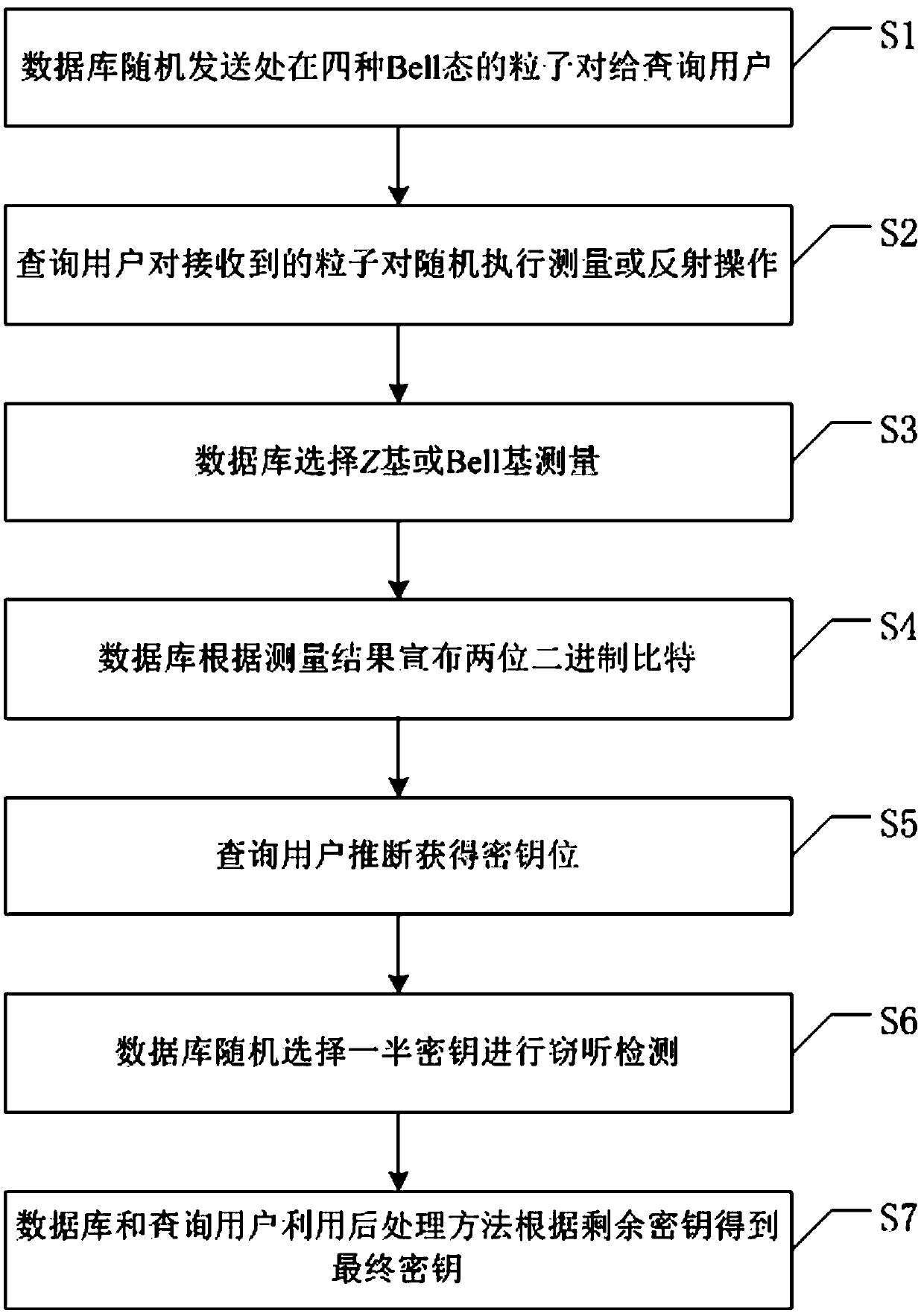
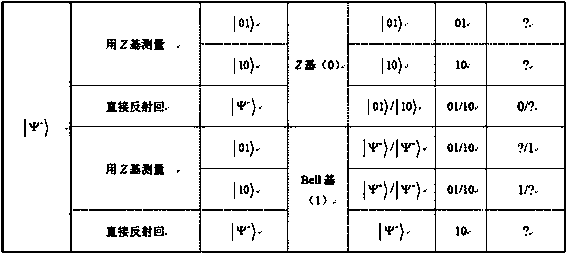
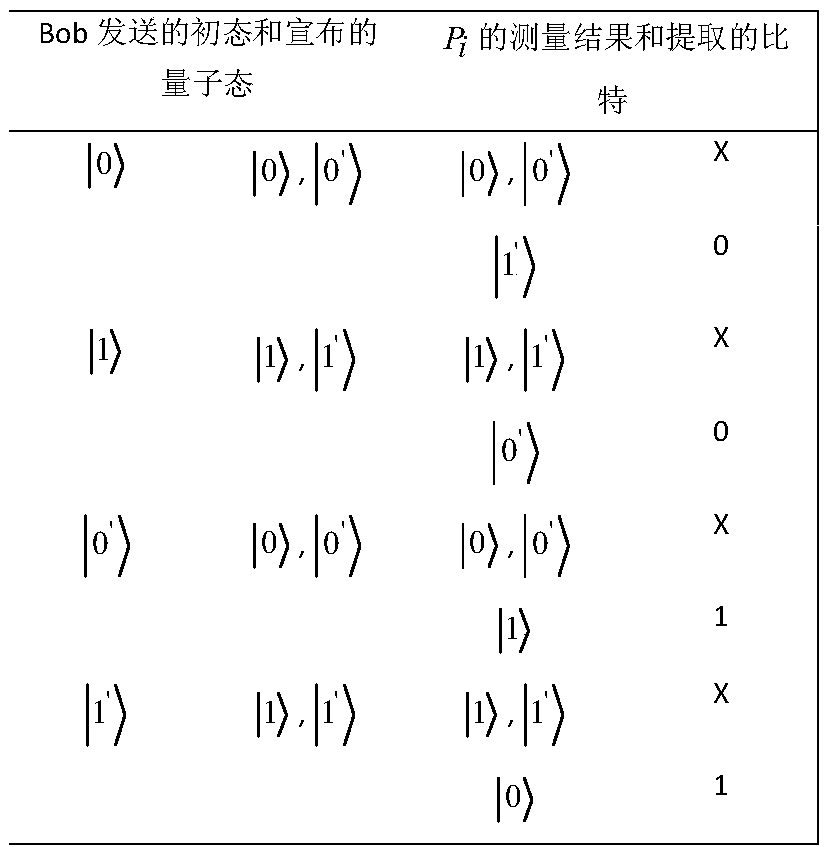
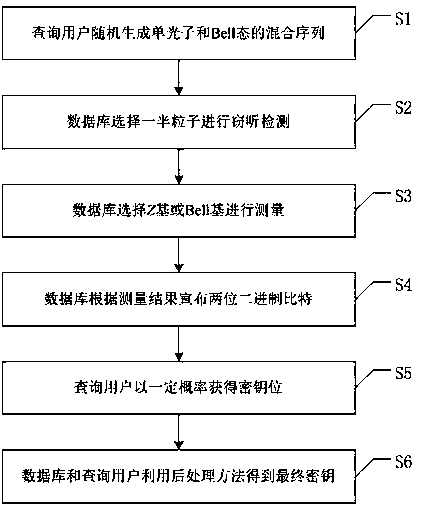
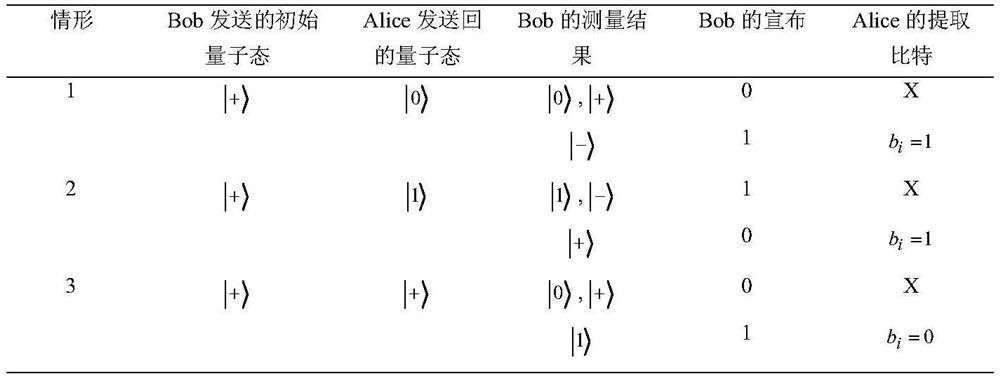
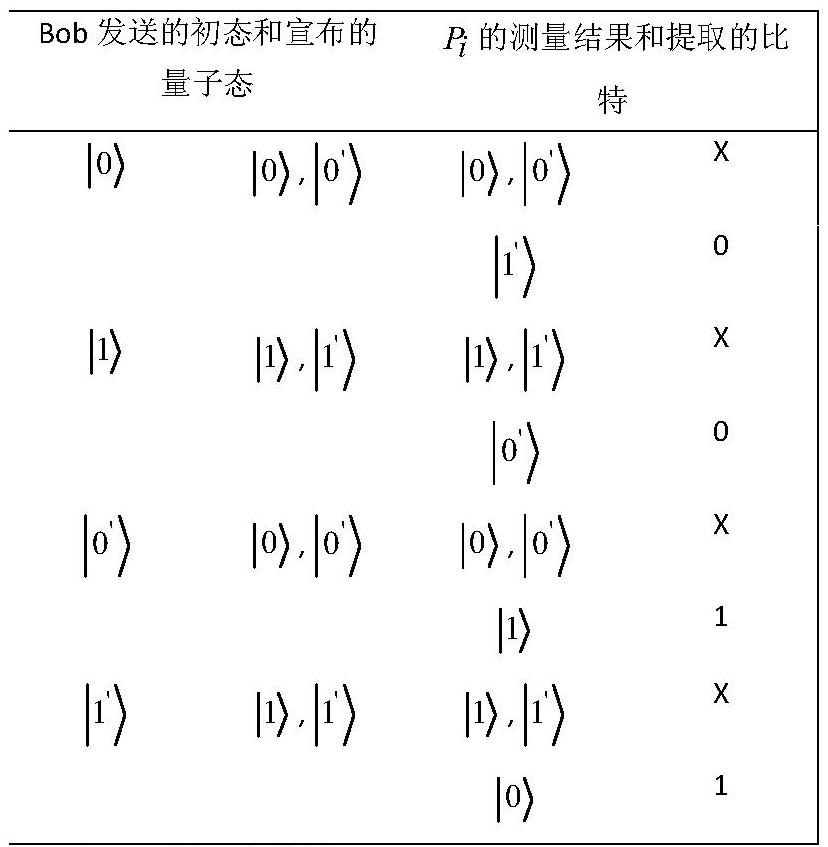
One-way transmission quantum database privacy query method
ActiveCN110929294AImplement privacy queryEasy to implementDigital data protectionBell stateEngineering
The invention discloses a one-way transmission quantum database privacy query method, comprising the steps that a query user randomly generates a mixed sequence of a single photon and a Bell state; the database selects half of particles for eavesdropping detection; the database selects a Z base or a Bell base for measurement; the database announces two binary bits according to a measurement result; the query user obtains a key bit at a certain probability; and the database and the query user obtain a final key by using a post-processing method. According to the one-way transmission quantum database privacy query method, the query user only needs to send the quantum information to the database owner once, so that the privacy query of the user on the database can be realized, and the realization method is simpler; and on the basis of ensuring completion of privacy query, the quantum bit use efficiency is improved, and no matter whether an internal eavesdropper or an external eavesdroppercannot obtain additional key information.
Owner:广州智租信息科技有限责任公司
Differentially Private Processing and Database Storage
Owner:SNOWFLAKE INC
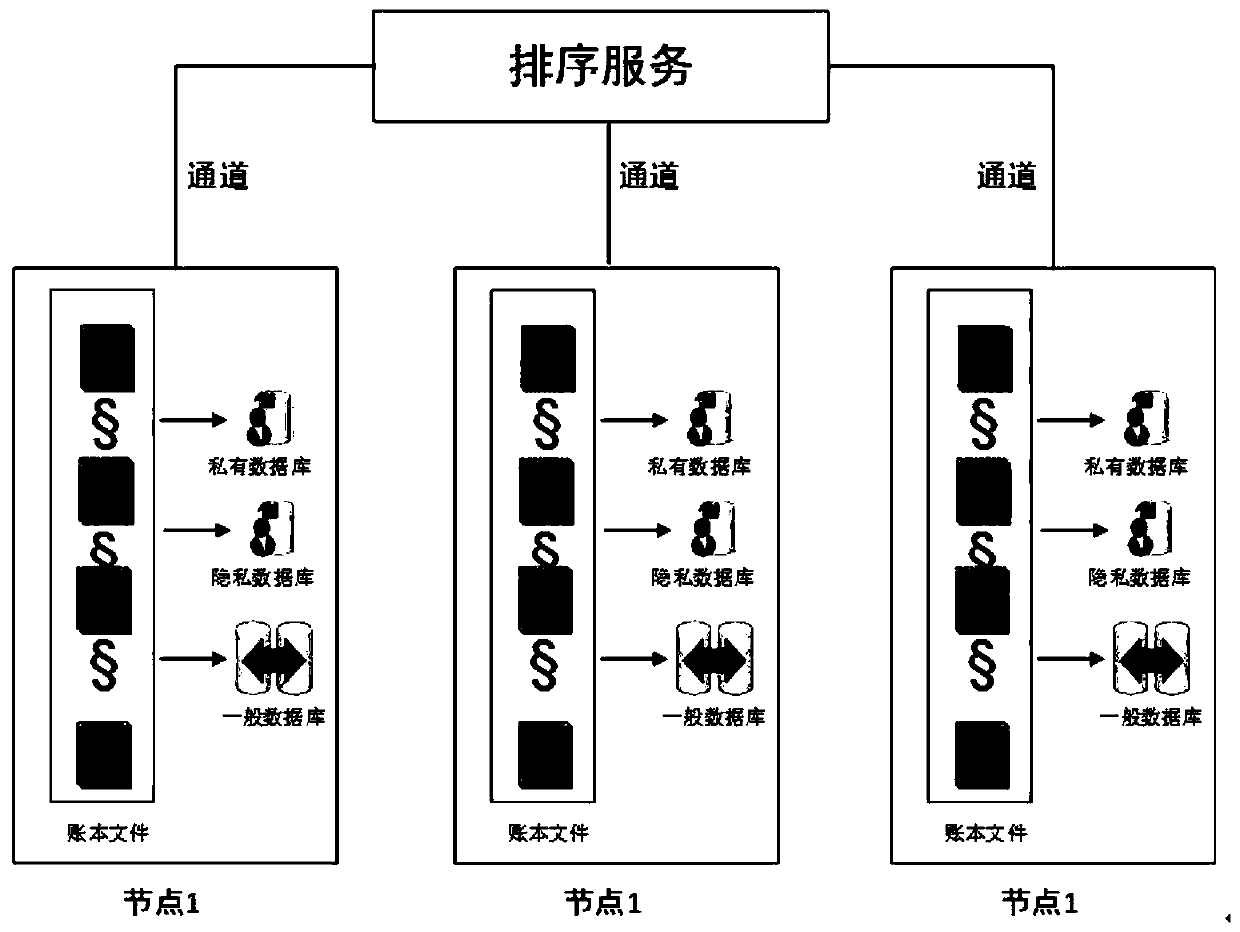
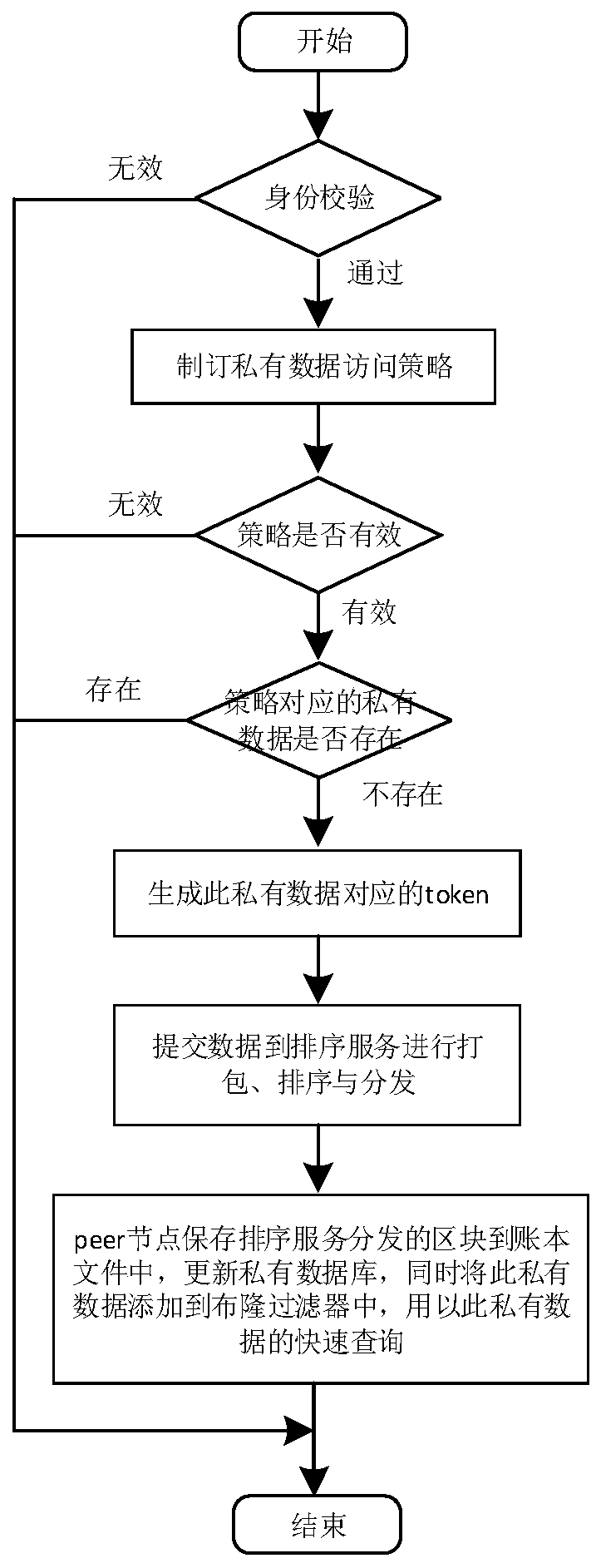
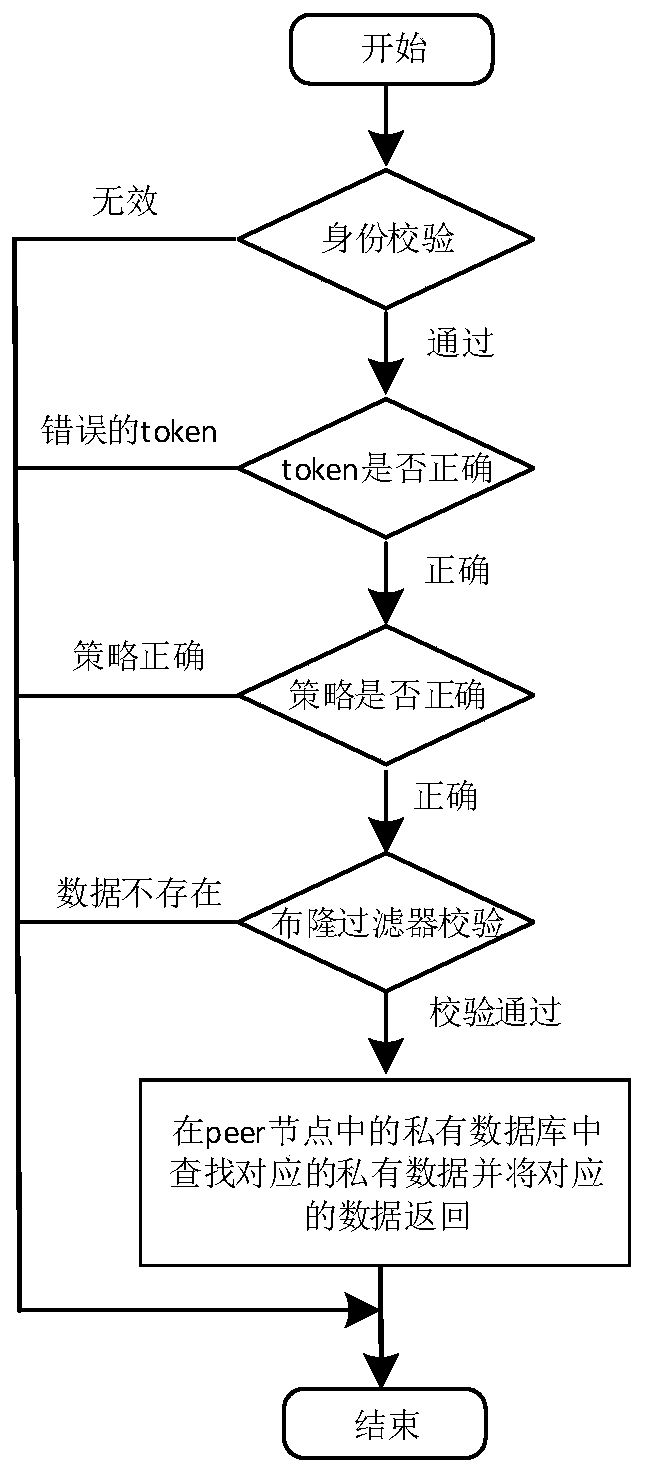
Private and private data protection mechanism in alliance chain
ActiveCN110851862ARealize security protectionAvoid disclosureDigital data protectionComputer networkInternet privacy
The invention provides a private and private data protection mechanism in an alliance chain. The private and private data protection mechanism comprises a node and a sorting service, the node is in communication connection with the sorting service through a channel; an account book file, a private database, a private database and a general database are stored in the node, and the private database,the private database and the general database are connected with the account book file through peer nodes; and private data, private data and general data are stored in the account book file. The method has the beneficial effects that the security protection of private and private data in the alliance chain can be effectively realized, and the private and private data is prevented from being disclosed to all members in the alliance chain.
Owner:CETC BIGDATA RES INST CO LTD
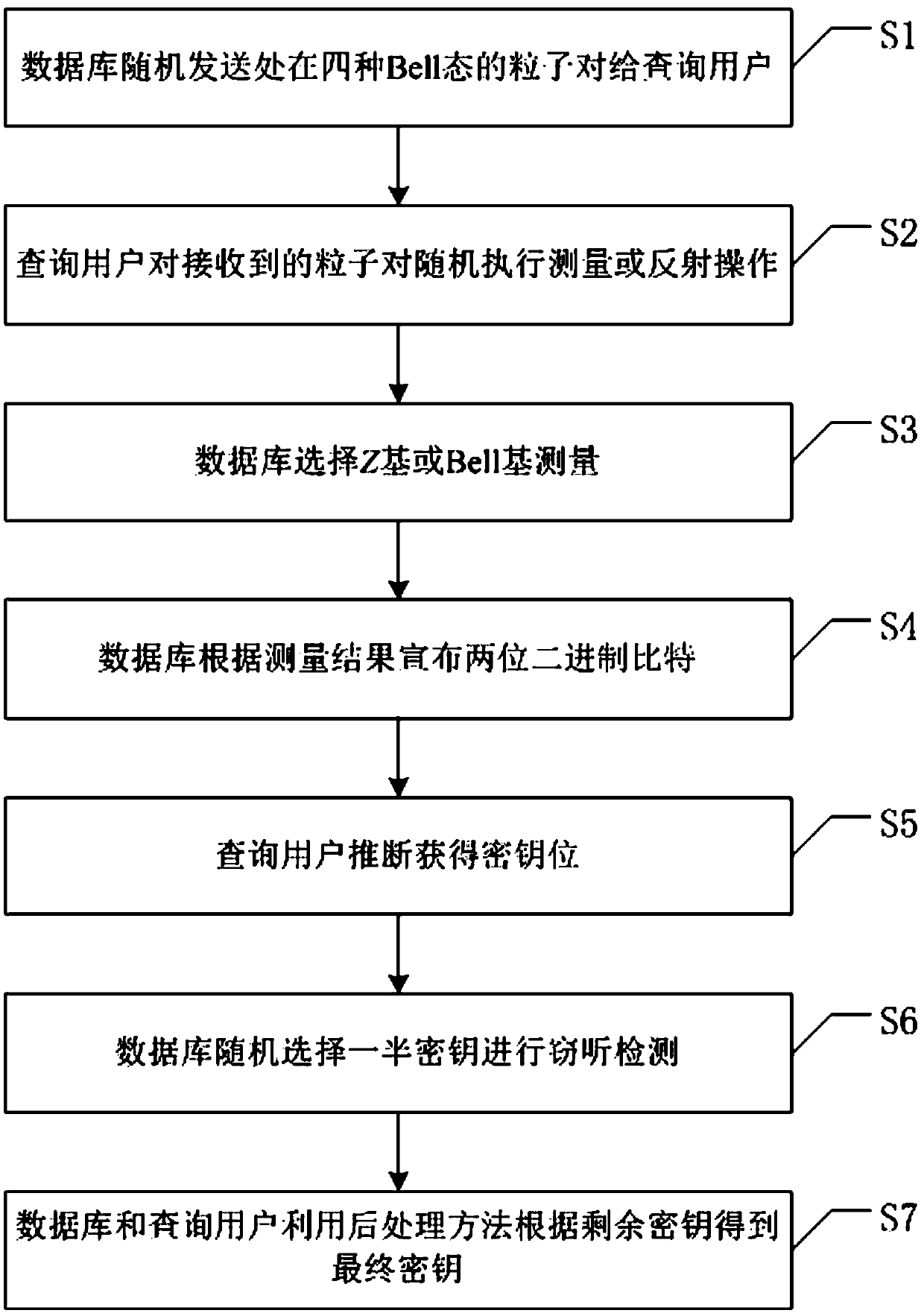
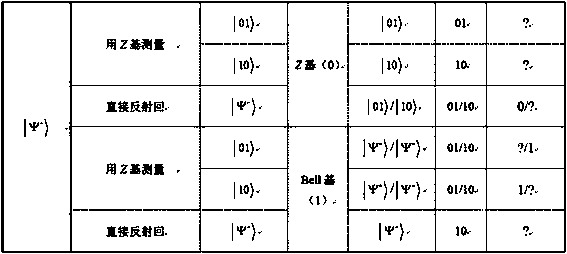
Bidirectional communication quantum database privacy query method based on Bell state
ActiveCN110932792AImplement privacy querySimplify the ability to configure quantum devicesKey distribution for secure communicationDigital data protectionBell stateData mining
The invention discloses a bidirectional communication quantum database privacy query method based on a Bell state. The method comprises the steps that a database randomly sends particle pairs in fourBell states to a query user, the query user randomly executes measurement or reflection operation on the received particle pair; wherein the database selects Z-based or Bell-based measurement, the database announces two binary bits according to a measurement result, the query user deduces to obtain a key bit, the database randomly selects a half key for eavesdropping detection, and the database and the query user obtain a final key according to the remaining keys by using a post-processing method. According to the invention, based on the Bell state, through bidirectional communication betweenthe database and the user, the quantum bit use efficiency is improved, the query key generation process is simplified, the privacy query of the user for the database is realized, and internal and external eavesdroppers cannot obtain the key.
Owner:亚信科技(中国)有限公司
Ciphertext database privacy protection enquiring method
InactiveCN101436208BAchieve excellent efficiencySpecial data processing applicationsCiphertextDatabase server
The invention relates to realization of query of encrypted database tables by utilization of a structuralized additional data structure on the premise that an internal operating mechanism of a database management system is not changed, which comprises an encrypt data containing an index query structure generation method and a whole encrypt query process. A database server judges the retrievable information range of cryptographic keys of certain levels held by users first, and quickly performs information retrieval within the information range, so as to protect the privacy of information in the database.
Owner:BEIJING JIAOTONG UNIV
Differentially private processing and database storage
A hardware database privacy device is communicatively coupled to a private database system. The hardware database privacy device receives a request from a client device to perform a query of the private database system and identifies a level of differential privacy corresponding to the request. The identified level of differential privacy includes privacy parameters (ε,δ) indicating the degree of information released about the private database system. The hardware database privacy device identifies a set of operations to be performed on the set of data that corresponds to the requested query. After the set of data is accessed, the set of operations is modified based on the identified level of differential privacy such that a performance of the modified set of operations produces a result set that is (ε,δ)-differentially private.
Owner:SNOWFLAKE INC
Multi-user quantum privacy query method with authentication
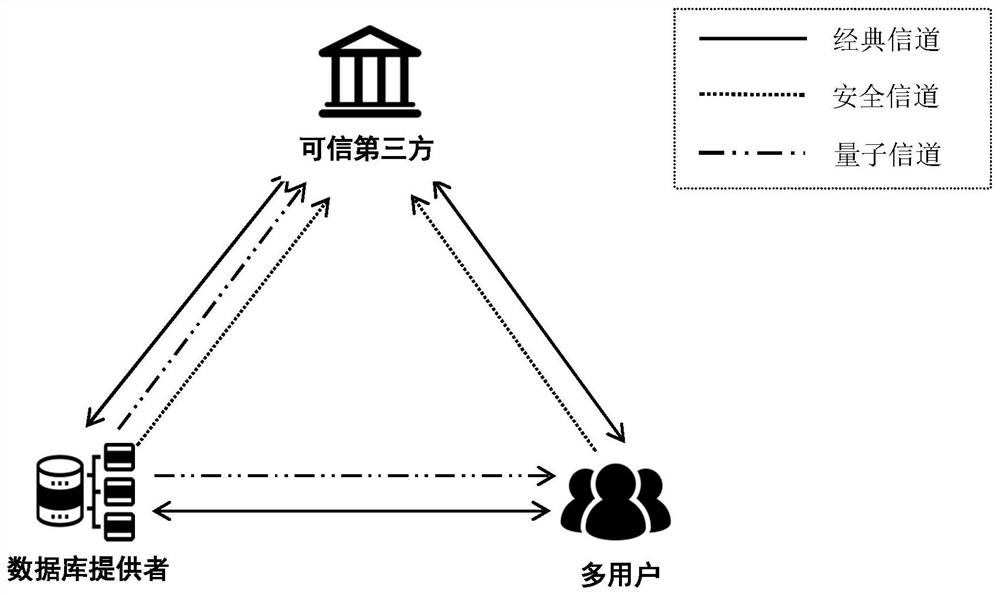
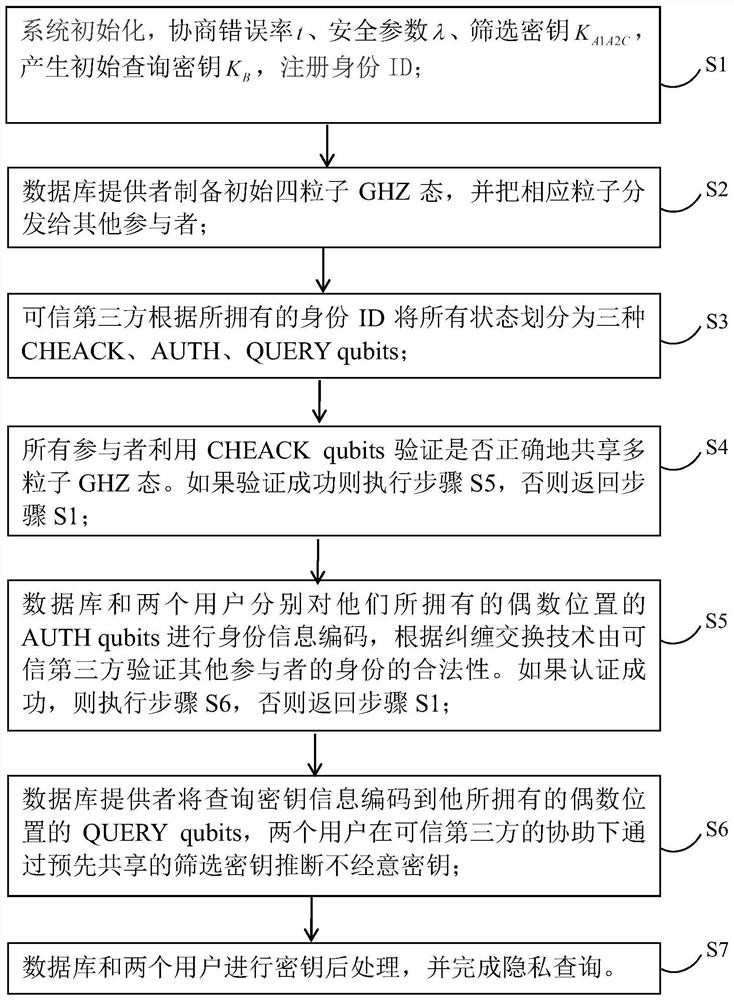
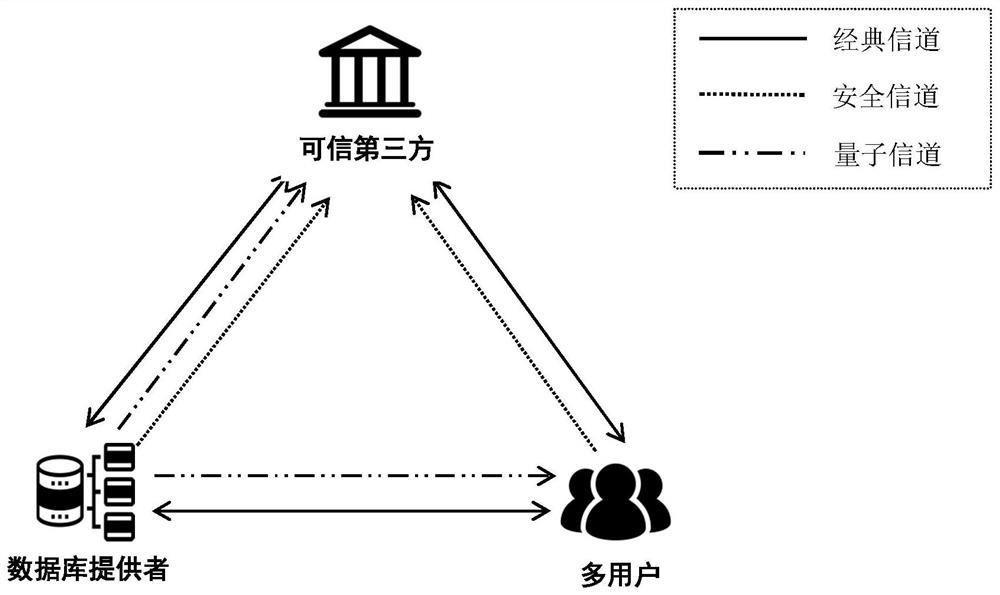
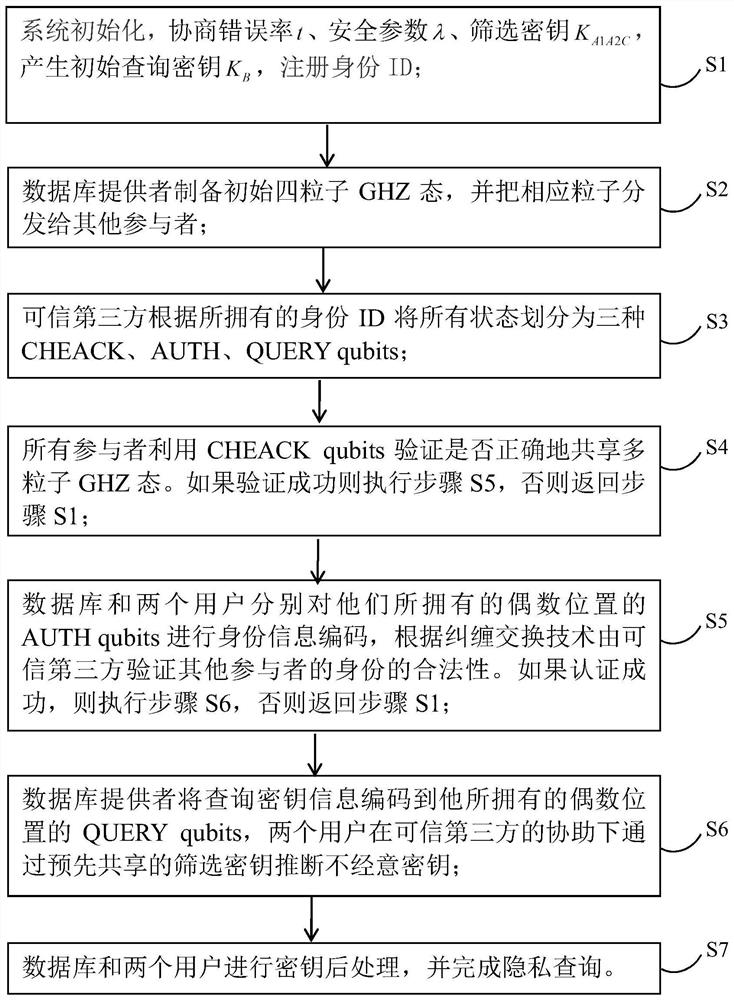
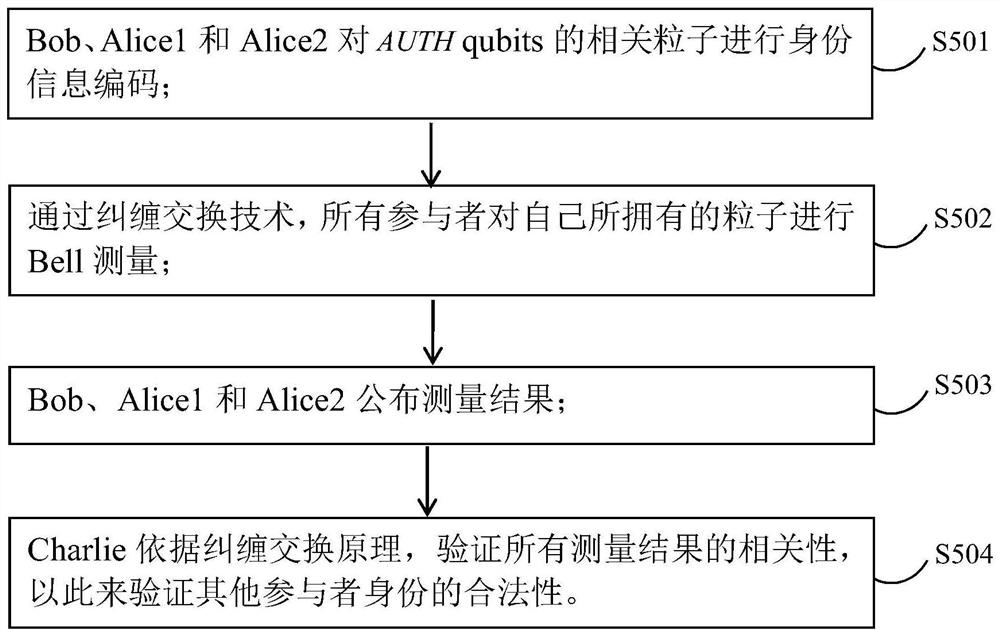
ActiveCN113114456AGuaranteed privacy and securityImprove securityKey distribution for secure communicationUser identity/authority verificationKey (cryptography)Attack
The invention relates to the field of quantum communication and quantum cryptography, in particular to a multi-user quantum privacy query method with authentication, which comprises the following steps that: participants negotiate important security parameters; the database provider prepares an initial multi-particle GHZ state and distributes corresponding particles to other participants; all participants perform security detection to verify whether the quantum state is shared securely; a database owner and a user utilize an entanglement swapping technology to convert bidirectional identity authentication between a database and each user into verification of legality of identities of other participants by a trusted third party; if the identity authentication of the participant succeeds, the database provider carries out casual key negotiation with the user; and the database provider and the user carry out key post-processing and complete privacy query. According to the method, an identity authentication mechanism is added, the security of multi-user quantum privacy query is enhanced, database privacy and user privacy of the same level are achieved, and external counterfeit attacks and man-in-the-middle attacks can be defended.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Method for processing big data based on MLDM algorithm meeting secondary aggregation
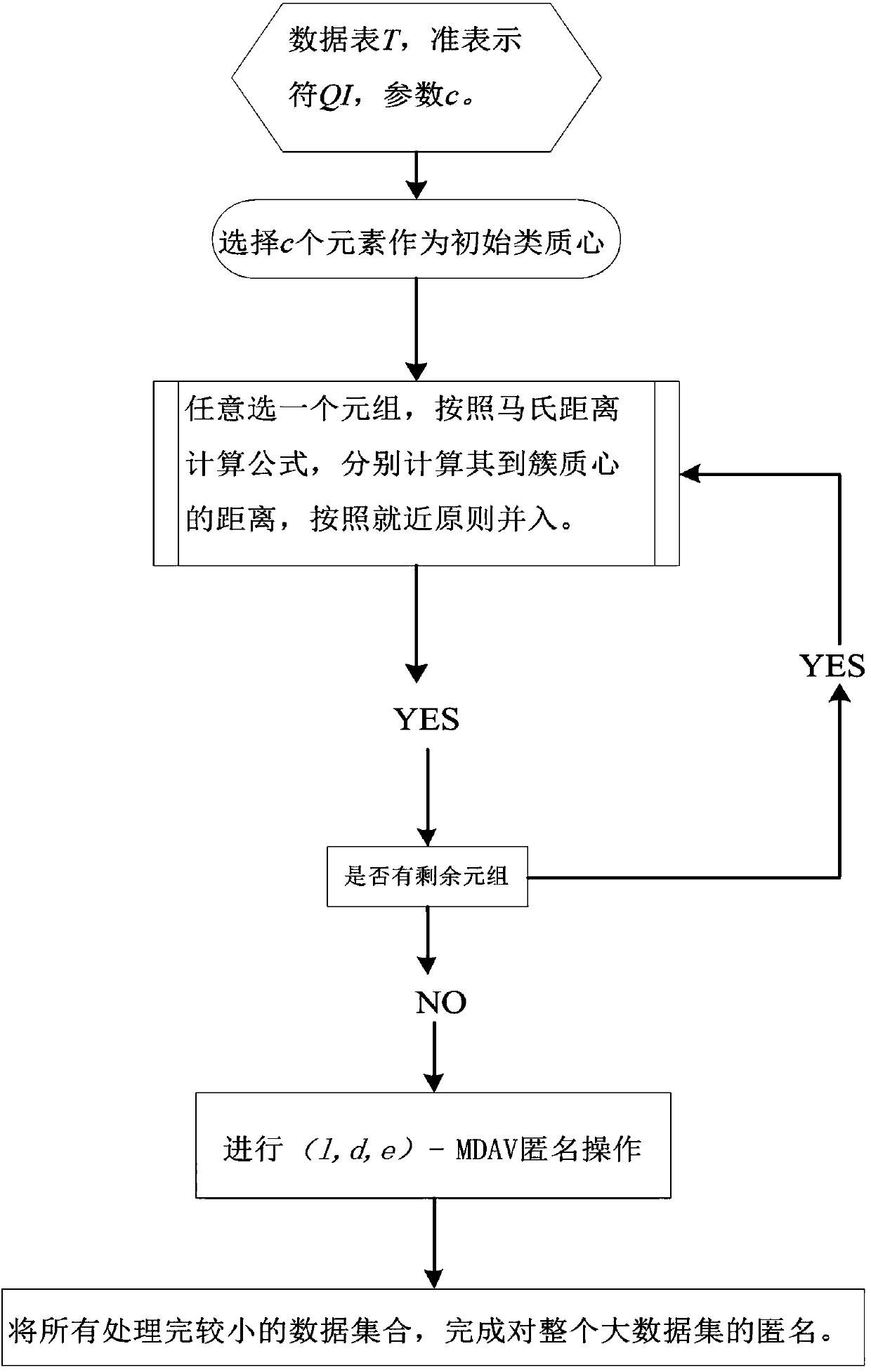
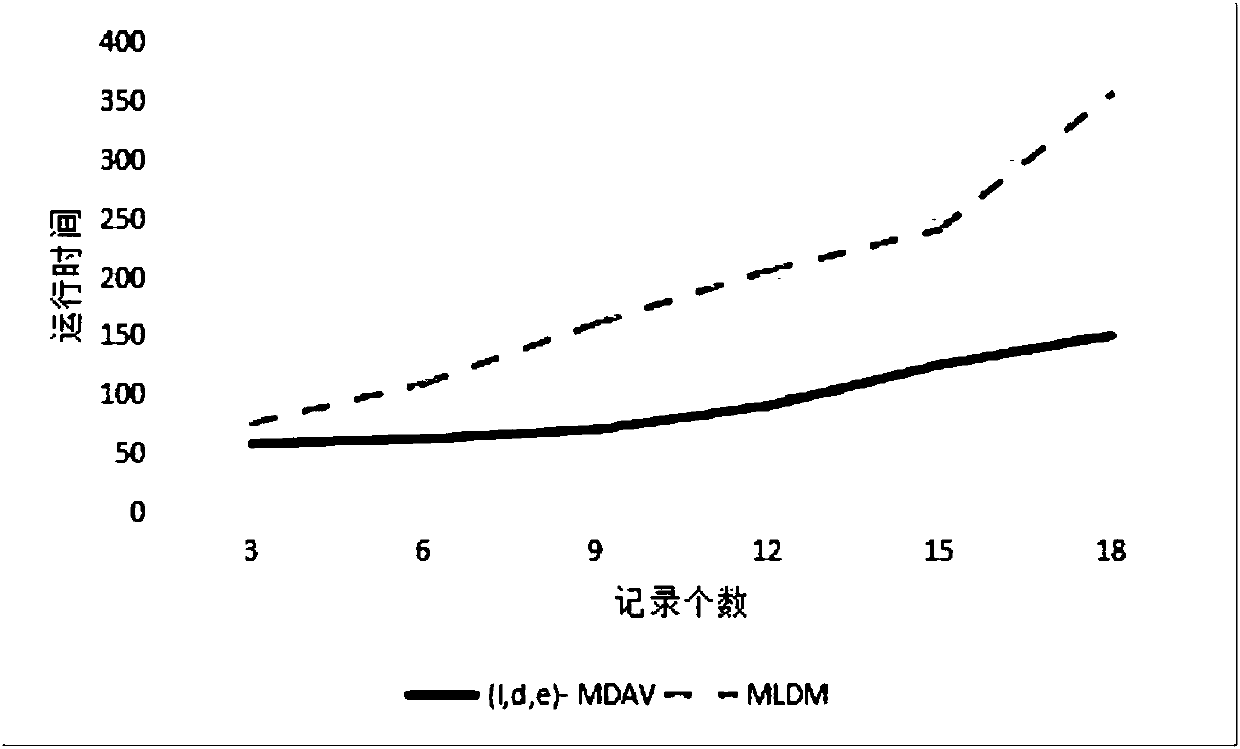
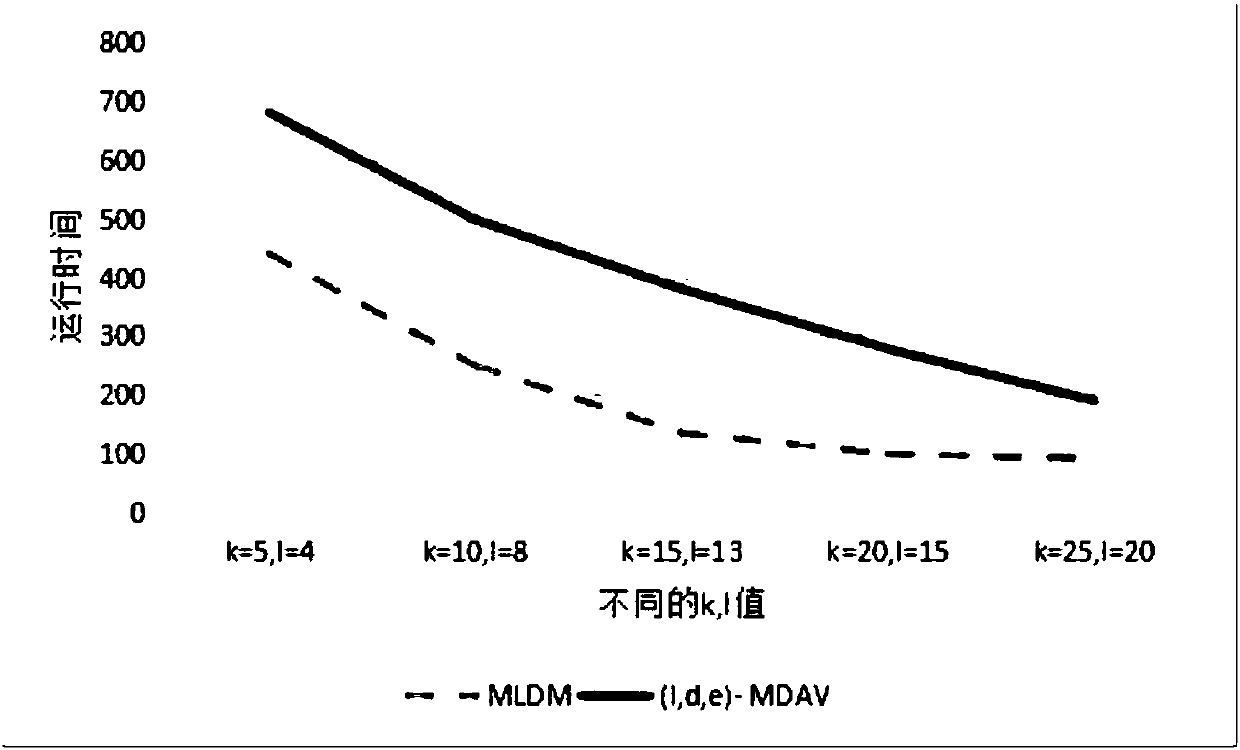
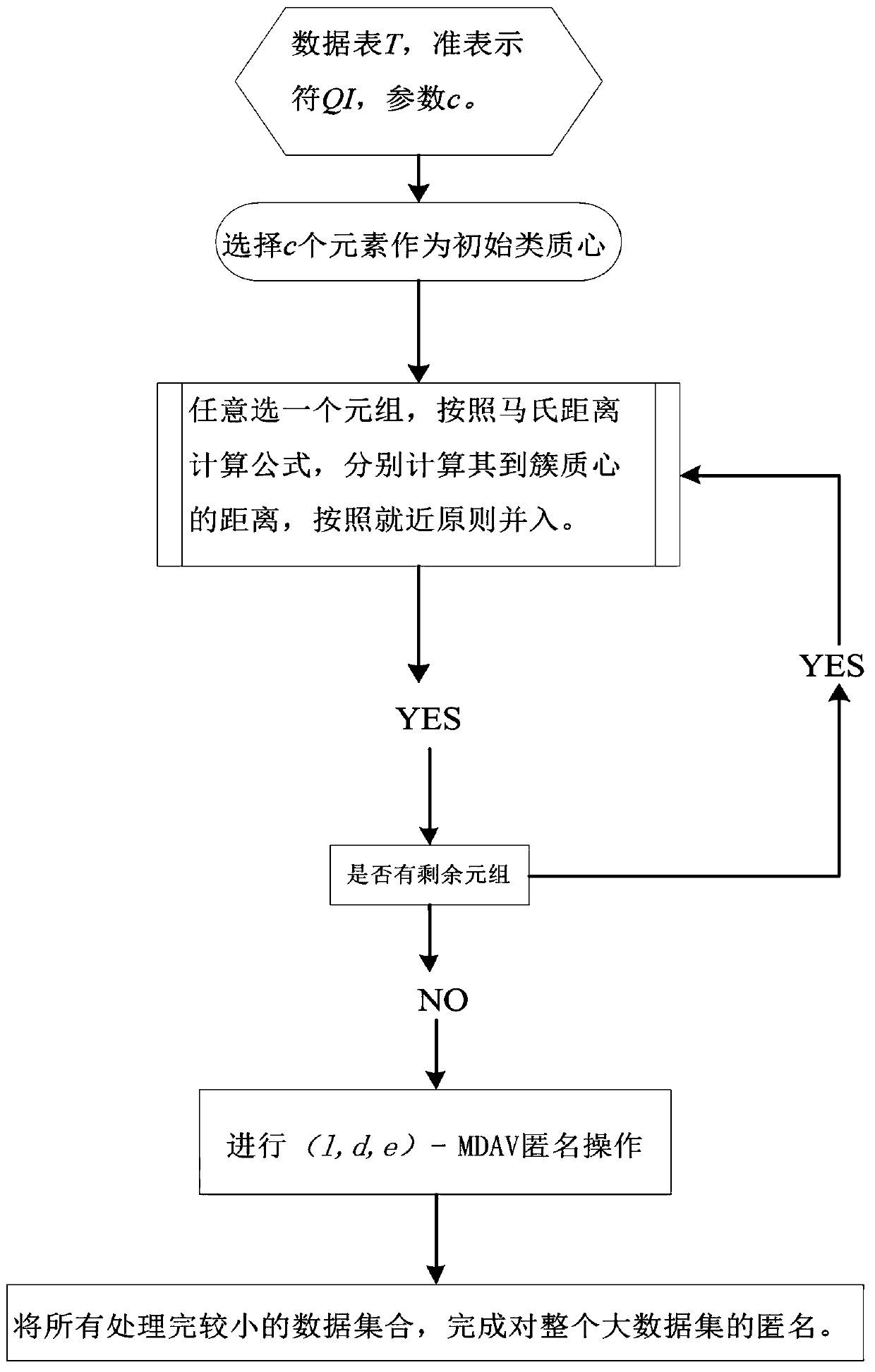
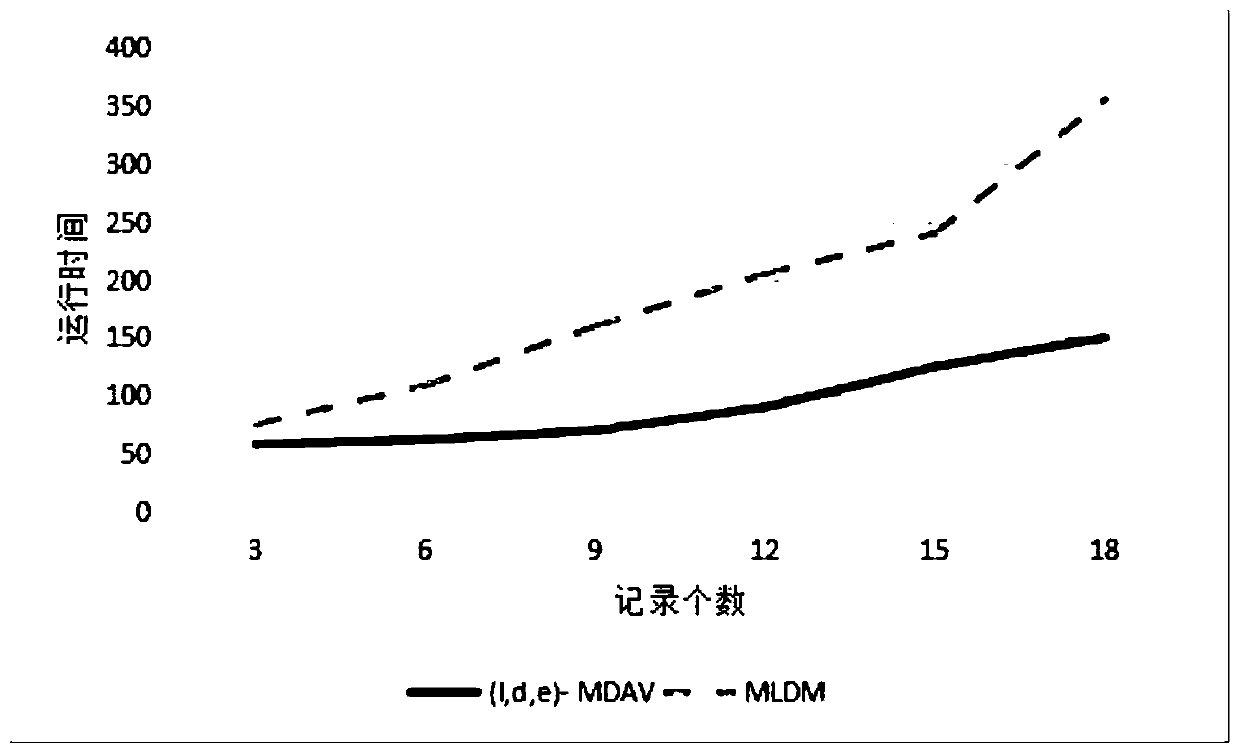
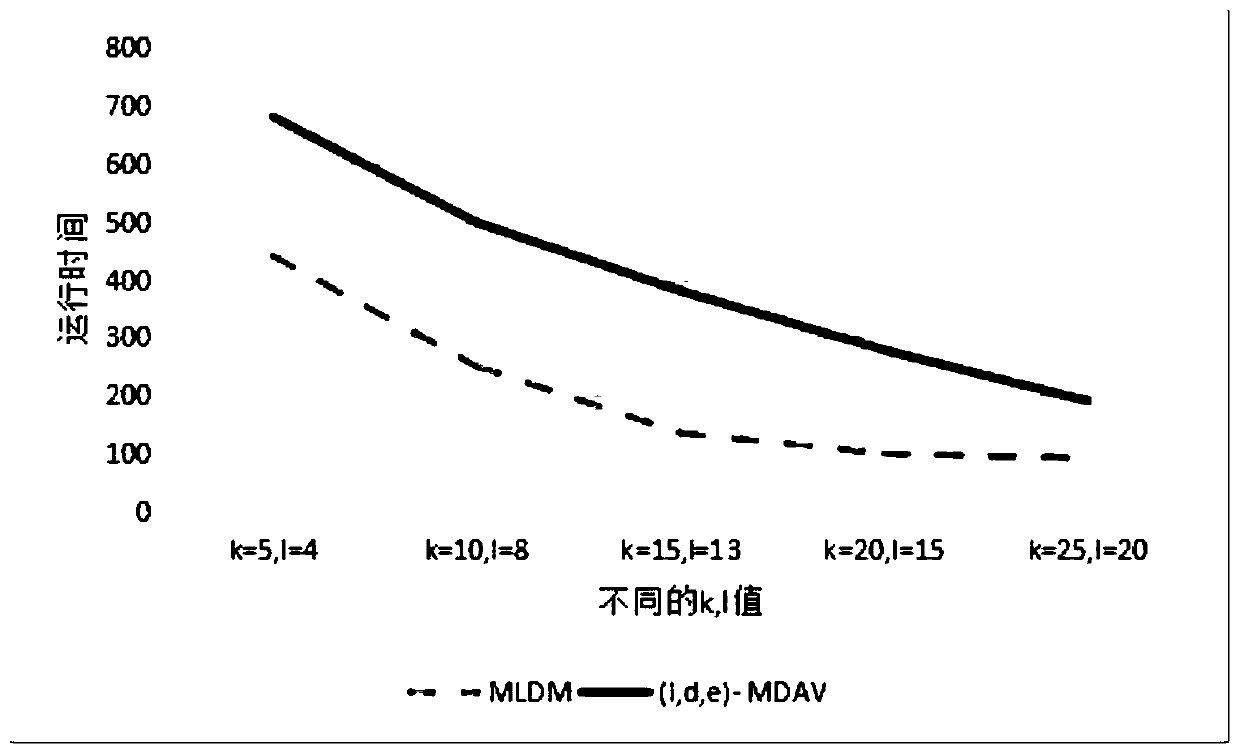
ActiveCN107305614AEasy to operateEasy to operate anonymouslyDigital data protectionData miningPrivacy protectionTime complexity
The invention belongs to the technical field of database privacy protection, and discloses a method for processing big data based on an MLDM algorithm meeting secondary aggregation. The method comprises the steps of introducing a k-means algorithm based on a (1,d,e)-MDAV algorithm; and when a big data set is processed, dividing the big data set into a plurality of small data sets firstly, then processing each small data set by using the (1,d,e)-MDAV algorithm, and finally combining the processed data, thereby enabling the whole data set to meet a (1,d,e)-diversity rule, and obtaining relatively low algorithm time complexity and relatively short algorithm time through improvement. According to the method, a k-means algorithm is introduced based on the (1,d,e)-MDAV algorithm; a new MLDM algorithm is proposed; and when the big data set is processed, the big data set is divided into the small data sets firstly, then each small data set is processed by using the (1,d,e)-MDAV algorithm, and finally the processed data are combined, so that the whole data set can meet the (1,d,e)-diversity rule, and the relatively low algorithm time complexity and the relatively short algorithm time can be obtained through the improvement.
Owner:XIDIAN UNIV
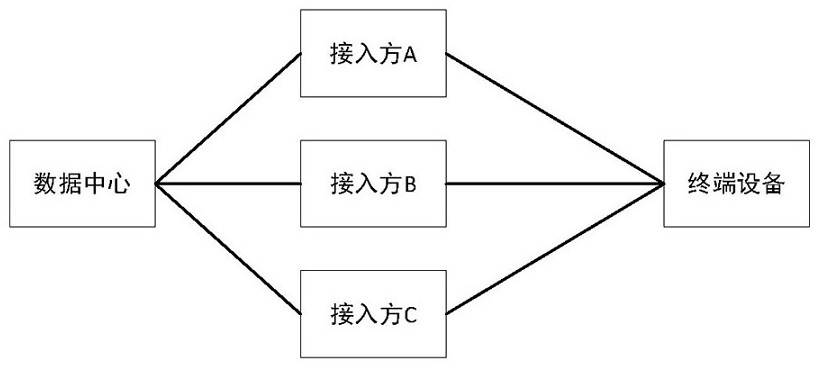
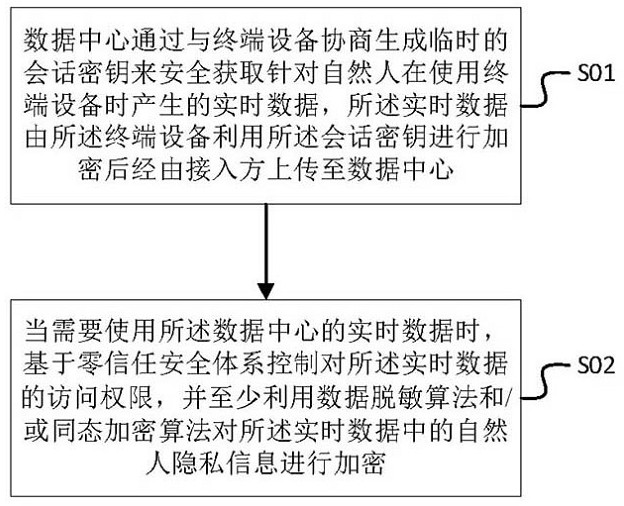
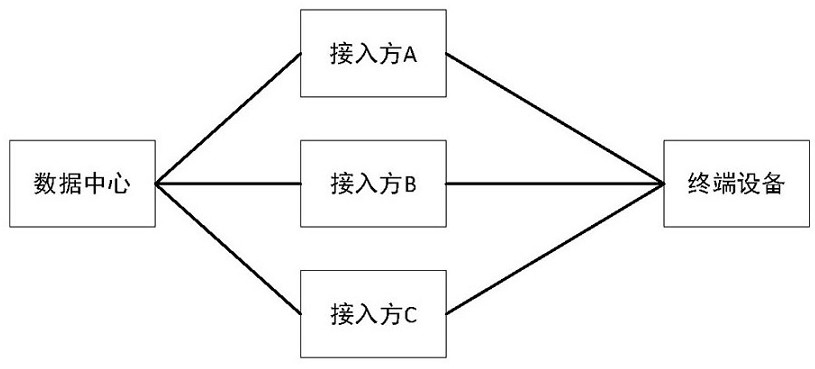
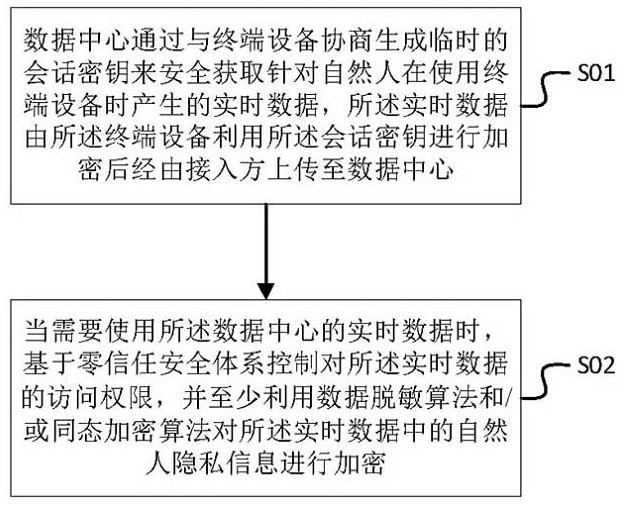
Natural person database privacy security protection method and device and terminal equipment
The invention is applicable to the technical field of data processing, and provides a natural person database privacy security protection method and device and terminal equipment, and the method is applied to a system comprising a data center, an access party and the terminal equipment. The natural person database privacy security protection method the following steps that a data center negotiates with terminal equipment to generate a temporary session key so as to safely obtain real-time data generated when a natural person uses the terminal equipment, and the real-time data is encrypted by the terminal equipment by using the session key and then is uploaded to the data center through an access party; and when the real-time data of the data center needs to be used, the access authority to the real-time data is controlled based on a zero-trust security system, and the natural person privacy information in the real-time data is encrypted at least by using a data desensitization algorithm and / or a homomorphic encryption algorithm. According to the method, the privacy information about the natural person in the data can be effectively prevented from being leaked in any link of using the data.
Owner:北京东方通软件有限公司 +2
Multi-user quantum private query method
According to a multi-user quantum private query method provided by the invention, the product state of the single photon state is used as an initial quantum resource, so that n users can query the data of the database at the same time. In the method of the invention, database privacy and user privacy should be compromised by selecting an appropriate value for theta. Due to the loyalty detection process of the database owner, a smaller theta can be preferentially selected to ensure better database privacy. Furthermore, the method of the present invention is loss tolerant, feasible in the case of large databases, robust to quantum storage attacks, and flexible.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
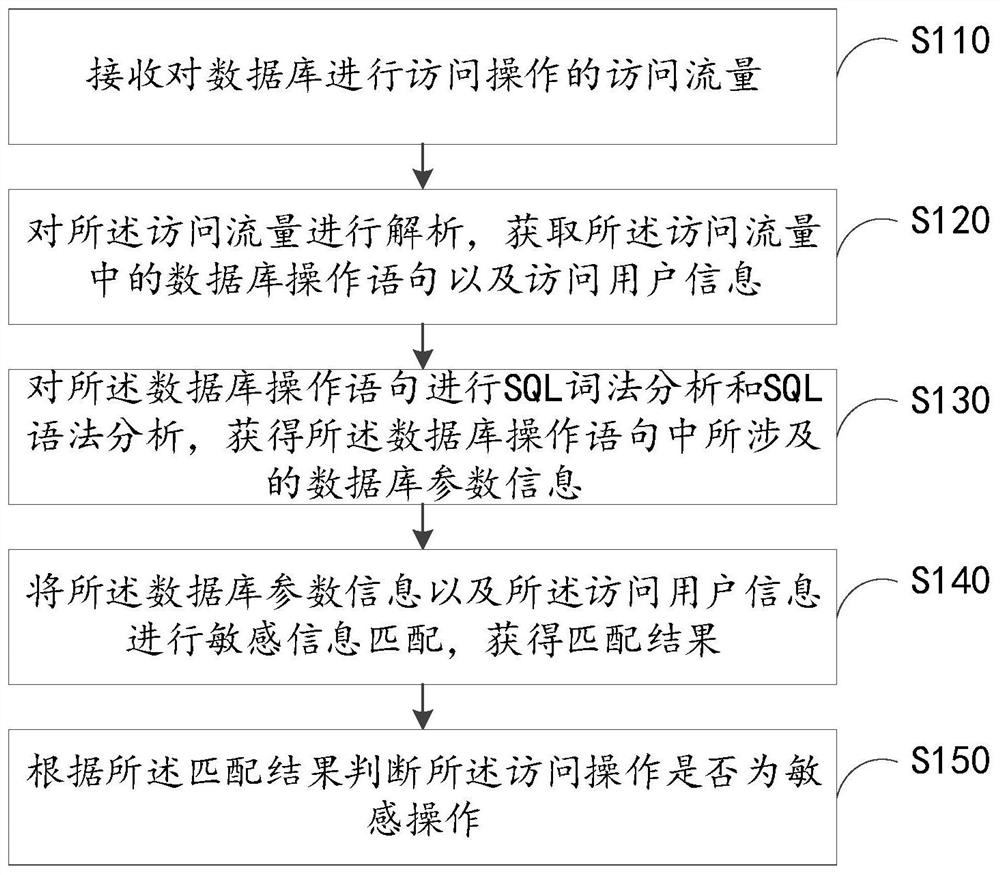
Database security management method and device, electronic equipment and readable storage medium
The invention provides a database security management method and device, electronic equipment and a readable storage medium, and relates to the technical field of data security. The method comprises the steps of receiving access traffic for performing access operation on a database; analyzing the access flow, and obtaining a database operation statement and access user information in the access flow; performing SQL lexical analysis and SQL grammatical analysis on the database operation statement to obtain database parameter information involved in the database operation statement; performing sensitive information matching on the database parameter information and the access user information to obtain a matching result; and judging whether the access operation is a sensitive operation or not according to a matching result. According to the scheme, the parameter information in the statement can be analyzed more quickly and accurately through SQL lexical analysis and SQL grammatical analysis, so that the matching of the sensitive information is more accurate, the operation of a user can be accurately recognized to prevent some violation operations, and the leakage of private data of adatabase is avoided.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
System and method for database privacy protection
ActiveUS9355258B2Reduce complexitySame quantityDigital data protectionTransmissionK-anonymityInformation gain
The invention relates to a system and a method for privacy preservation of sensitive attributes stored in a database. The invention reduces the complexity and enhances privacy preservation of the database by determining the distribution of sensitive data based on Kurtosis measurement. The invention further determines and compares the optimal value of k-sensitive attributes in k-anonymity data sanitization model with the optimal value of l sensitive attributes in l diversity data sanitization model using adversary information gain. The invention reduces the complexity of the method for preserving privacy by applying k anonymity only, when the distribution of the sensitive data is leptokurtic and optimal value of k is greater than the optimal value of l.
Owner:TATA CONSULTANCY SERVICES LTD
Database watermarking method based on local differential privacy
ActiveCN109033766BCopyright protectionProtect private informationProgram/content distribution protectionData integrityAttack
The invention discloses a database watermarking method based on local differential privacy. The attributes are sorted according to the attribute names of the database, and the tuples are grouped according to the primary key of the tuples in the database for watermark embedding; the sensitive attributes in the database are differentially private. ; According to the characteristics of the data in the database after differential privacy, the watermark is embedded, and then the watermarked database is released to the cloud; the user downloads the published database from the cloud, and extracts the watermark from the published database for copyright tracking and data integrity verification. The database watermarking method based on local differential privacy of the present invention not only maintains the property of differential privacy but also reduces data distortion caused by differential privacy, and has high robustness against various attacks such as addition, modification, and deletion of databases. The invention is used to provide a comprehensive protection mechanism for database privacy security, tamper integrity, source reliability and the like.
Owner:HEFEI UNIV OF TECH
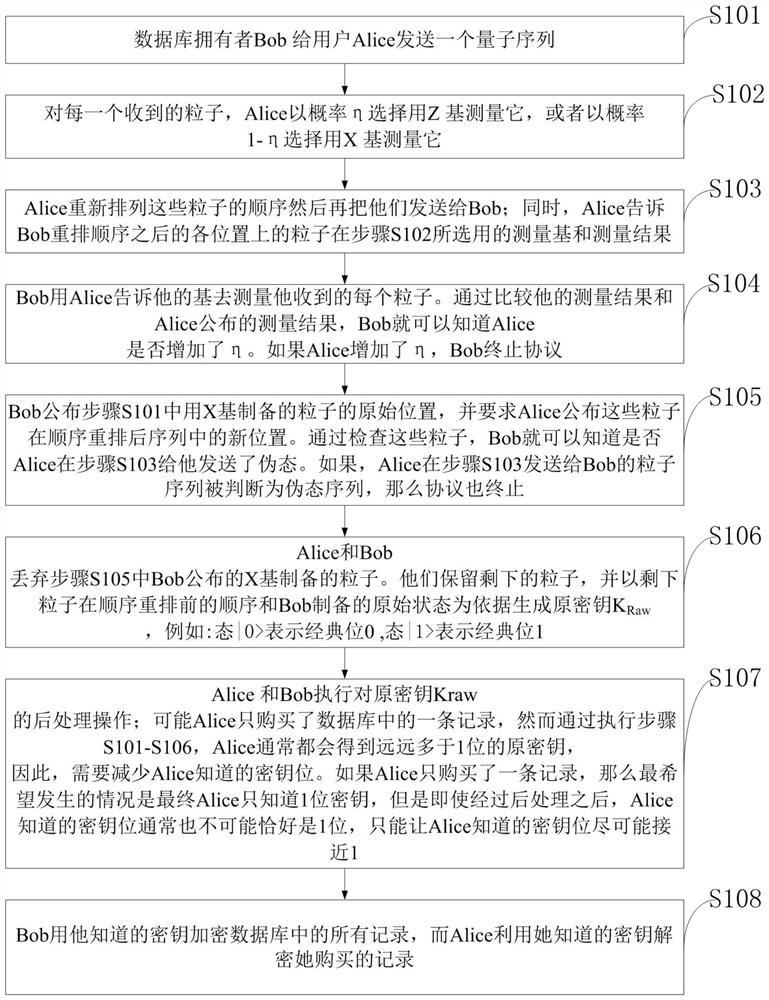
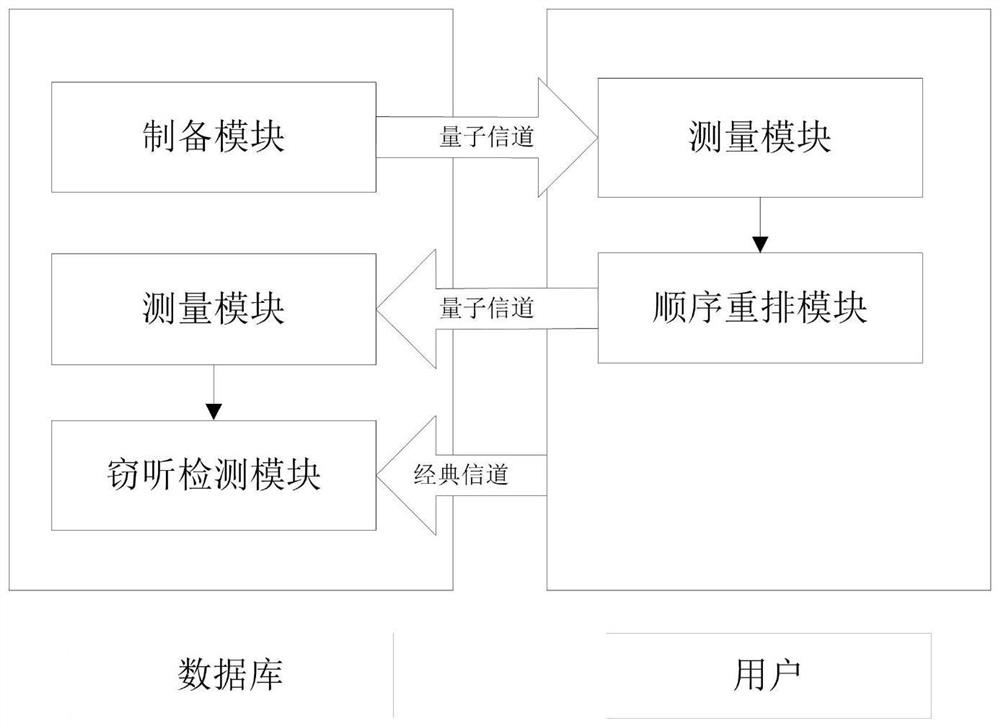
A Quantum Database Privacy Query Method Based on Order Rearrangement for Better User Privacy
ActiveCN108363927BImprove privacyImprove privacy protectionDigital data information retrievalDigital data protectionWavelength filterTrojan horse
The invention belongs to the technical field of database privacy query, and discloses a quantum database privacy query method based on sequence rearrangement for better user privacy. The database owner Bob sends a quantum sequence to user Alice; for each received particle, Alice Choose to measure the particles with the Z-base with probability η, or choose to measure the particles with the X-base with probability 1-η; Alice rearranges the order of these particles and then sends the rearranged particles to Bob; at the same time, Alice tells The measurement basis and measurement results selected by the particles at each position after Bob's rearrangement order; etc. The quantum database privacy query protocol proposed by the invention can obtain better user privacy performance than spoofing sensitivity, and can also resist Trojan attacks without a wavelength filter and a photon number distributor with an auxiliary monitoring detector.
Owner:哈尔滨同创普润科技有限公司
A multi-user quantum privacy query method with authentication
ActiveCN113114456BGuaranteed privacy and securityImprove securityKey distribution for secure communicationUser identity/authority verificationKey (cryptography)Attack
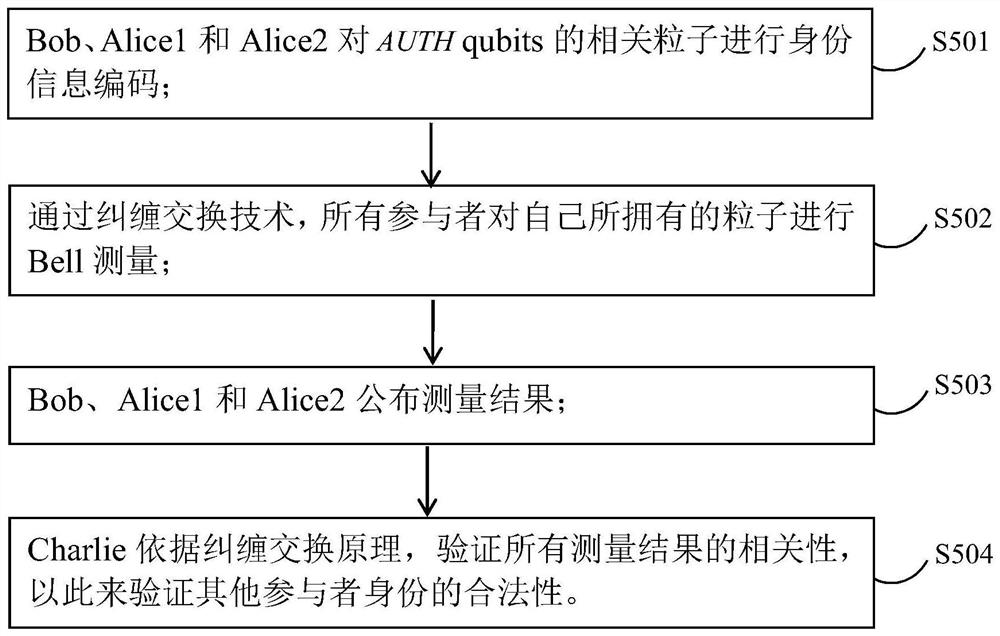
The invention relates to the fields of quantum communication and quantum cryptography, in particular to a multi-user quantum privacy query method with authentication, which includes: negotiating important security parameters between participants; a database provider prepares an initial multi-particle GHZ state, and converts corresponding particles into Distributed to other participants; all participants conduct security checks to verify whether the quantum state is safely shared; database owners and users use entanglement exchange technology to convert the two-way authentication between the database and each user into a trusted third party to verify other The legitimacy of the participant's identity; if the participant's identity authentication is successful, the database provider and the user conduct inadvertent key negotiation; the database provider and the user perform key post-processing, and complete the privacy query. The invention adds an identity authentication mechanism to enhance the security of multi-user quantum privacy query, not only has the same level of database privacy and user privacy, but also can defend against external counterfeiting attacks and man-in-the-middle attacks.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Quantum database privacy query method based on one-way transmission
ActiveCN110929294BImplement privacy queryEasy to implementDigital data protectionBell stateEngineering
The invention discloses a one-way transmission quantum database privacy query method. The method includes querying a user to randomly generate a mixed sequence of single photons and Bell states, and the database selects half of the particles for wiretapping detection, and the database selects Z Base or Bell base is measured, the database announces two binary bits according to the measurement results, and the query user obtains the key bit with a certain probability, and the database and the query user use the post-processing method to obtain the final key. The invention only needs to query the user to send quantum information to the database owner once to realize the user's privacy query to the database, and the implementation method is simpler; on the basis of ensuring the completion of the privacy query, the use efficiency of qubits is improved, and no matter whether it is internal Neither an external eavesdropper can obtain additional key information.
Owner:广州智租信息科技有限责任公司
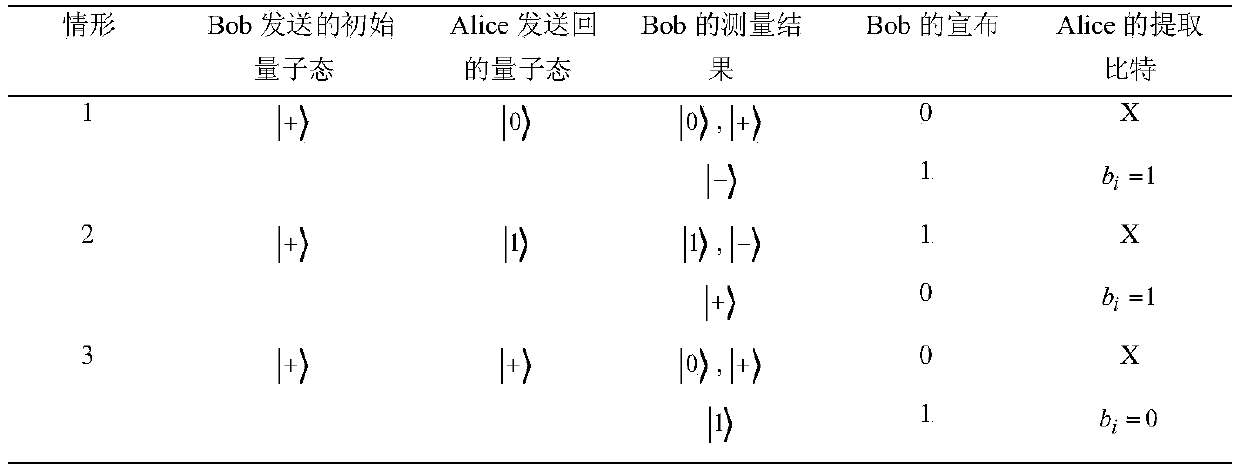
Semi-quantum private query method without stimulating measurement capability of classic user
ActiveCN111162904AManipulation is accurateKey distribution for secure communicationDigital data information retrievalAttackMedicine
The invention provides a semi-quantum private query method without stimulating the measurement capability of a classical user, and by utilizing the law of quantum mechanics, a user can secretly queryone piece of data from a database on the premise of ensuring the user privacy and the database privacy. The method provided by the invention has the following characteristics: (1) only one quantum state is adopted as an initial quantum state; (2) a classical user is not required to execute measurement operation; (3) the method is deception-sensitive, which means that if database privacy or user privacy is invaded, attack behaviors can be detected.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Natural person database privacy security protection method, device and terminal equipment
Owner:北京东方通软件有限公司 +2
A semi-quantum private query method that does not excite classical user measurement capabilities
ActiveCN111162904BManipulation is accurateKey distribution for secure communicationDigital data information retrievalAttackUser privacy
Owner:ZHEJIANG GONGSHANG UNIVERSITY
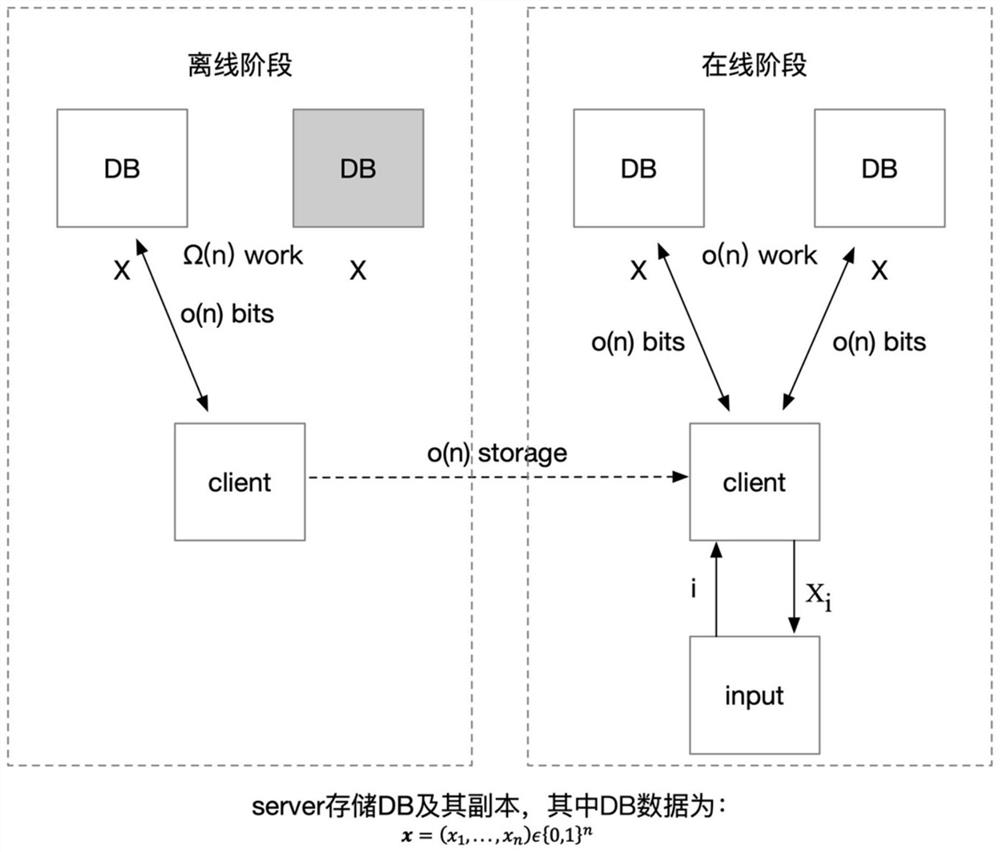
Method, system and device for improving privacy query online efficiency and storage medium
PendingCN114186103AImprove privacyImprove privacy query efficiencyOther databases indexingOther databases queryingBusiness enterprisePrivacy protection
The invention discloses a method, a system and equipment for improving privacy query online efficiency and a storage medium, specifically, privacy query is decomposed into an offline part and an online part, the offline part refers to that user query performs related data preparation and calculation work offline, and the online part refers to that data is requested from a database in real time. In the offline stage, the client obtains the'intermediate value 'of total data through an algorithm, in the online stage, the client obtains the position of the data needing to be inquired in the database through the'intermediate value', the client initiates a request to the database to obtain the data, and data items needing to be inquired are obtained by combining the previous intermediate value. The privacy of data query can be protected, and meanwhile, the efficiency of data query is improved. The database privacy query efficiency bottleneck is solved, and the financial service privacy protection requirement can be well supported. Particularly, when a bank performs joint modeling and portraying on customers and enterprises, privacy and performance can be ensured.
Owner:CHINA ZHESHANG BANK
A method of processing large data based on the mldm algorithm satisfying the quadratic aggregation
ActiveCN107305614BEasy to operateEasy to operate anonymouslyDigital data protectionData miningRound complexityPrivacy protection
The invention belongs to the technical field of database privacy protection, and discloses a method for processing big data based on an MLDM algorithm meeting secondary aggregation. The method comprises the steps of introducing a k-means algorithm based on a (1,d,e)-MDAV algorithm; and when a big data set is processed, dividing the big data set into a plurality of small data sets firstly, then processing each small data set by using the (1,d,e)-MDAV algorithm, and finally combining the processed data, thereby enabling the whole data set to meet a (1,d,e)-diversity rule, and obtaining relatively low algorithm time complexity and relatively short algorithm time through improvement. According to the method, a k-means algorithm is introduced based on the (1,d,e)-MDAV algorithm; a new MLDM algorithm is proposed; and when the big data set is processed, the big data set is divided into the small data sets firstly, then each small data set is processed by using the (1,d,e)-MDAV algorithm, and finally the processed data are combined, so that the whole data set can meet the (1,d,e)-diversity rule, and the relatively low algorithm time complexity and the relatively short algorithm time can be obtained through the improvement.
Owner:XIDIAN UNIV
Multi-user Quantum Private Query Method
ActiveCN111431712BQuantum computersKey distribution for secure communicationTheoretical computer scienceUser privacy
The invention proposes a multi-user quantum private query method, which uses the product state of a single photon state as an initial quantum resource, and can realize n users querying data in a database at the same time. In the method of the present invention, database privacy and user privacy should be compromised by choosing an appropriate value for θ. Due to the loyalty checking process to the database owner, a smaller θ can be preferentially chosen to ensure better database privacy. In addition, the method of the present invention is wear-tolerant, feasible in the case of large databases, robust against quantum storage attacks and flexible.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Bidirectional Communication Quantum Database Privacy Query Method Based on Bell State
ActiveCN110932792BImplement privacy querySimplify the ability to configure quantum devicesKey distribution for secure communicationDigital data protectionBell stateGeneration process
The invention discloses a two-way communication quantum database privacy query method based on the Bell state. The method includes that the database randomly sends particle pairs in four Bell states to the query user, and the query user randomly performs measurement or reflection on the received particle pairs. operation, database selection Z Base or Bell base measurement, the database announces two binary bits according to the measurement results, the query user infers the key bits, the database randomly selects half of the keys for wiretapping detection, and the database and query users use the post-processing method to obtain the final key based on the remaining keys . The invention improves the efficiency of qubit usage through the two-way communication between the database and the user based on the Bell state, simplifies the generation process of the query key, realizes the user's private query of the database, and prevents internal and external eavesdroppers from obtaining the key.
Owner:亚信科技(中国)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com