Multi-user quantum private query method
A query method, multi-user technology, applied in quantum computer, key distribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0073] 1. Application example of multi-user QPQ method
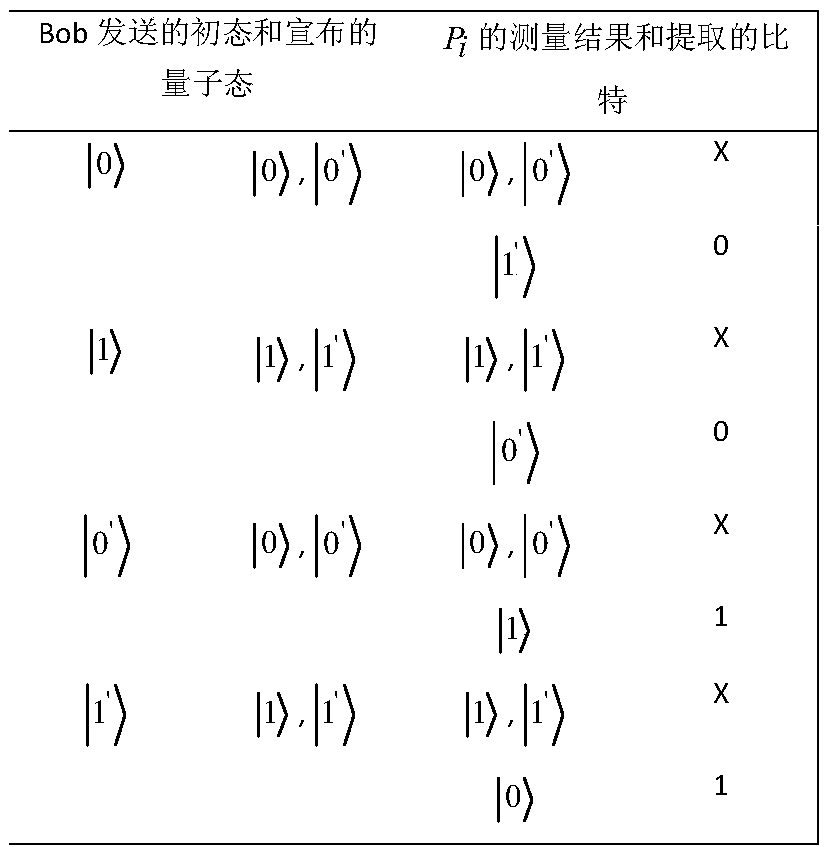
[0074] Here, an example is used to further illustrate the bit extraction process of the method of the present invention. If P i The measurement result of is |0> and Bob's announcement is 1, she will know that Bob's initial state must be |1'> and the key bit is 1.
[0075] 2. Discussion
[0076] As analyzed above, the smaller θ is, the P i The smaller the success probability of the independent measurement and the success probability of the joint measurement of , it means better database privacy. However, the larger θ is, Bob gets P i The smaller the probability of conclusiveness in a qubit, the better the privacy of the user. Therefore, in the method of the present invention, database privacy and user privacy should be compromised by choosing an appropriate value for θ. It should be noted that no matter what θ is, when P i When detecting Bob's loyalty in step S7, the false initial state attack initiated by Bob can ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com