Database watermarking method based on local differential privacy
A differential privacy, database technology, applied in the field of database security, can solve problems such as inability to protect privacy, degradation, and distorted data quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
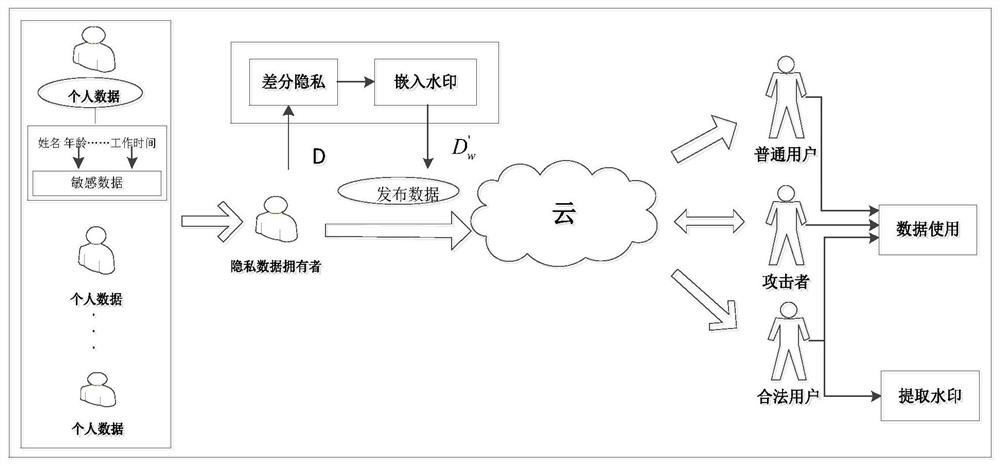
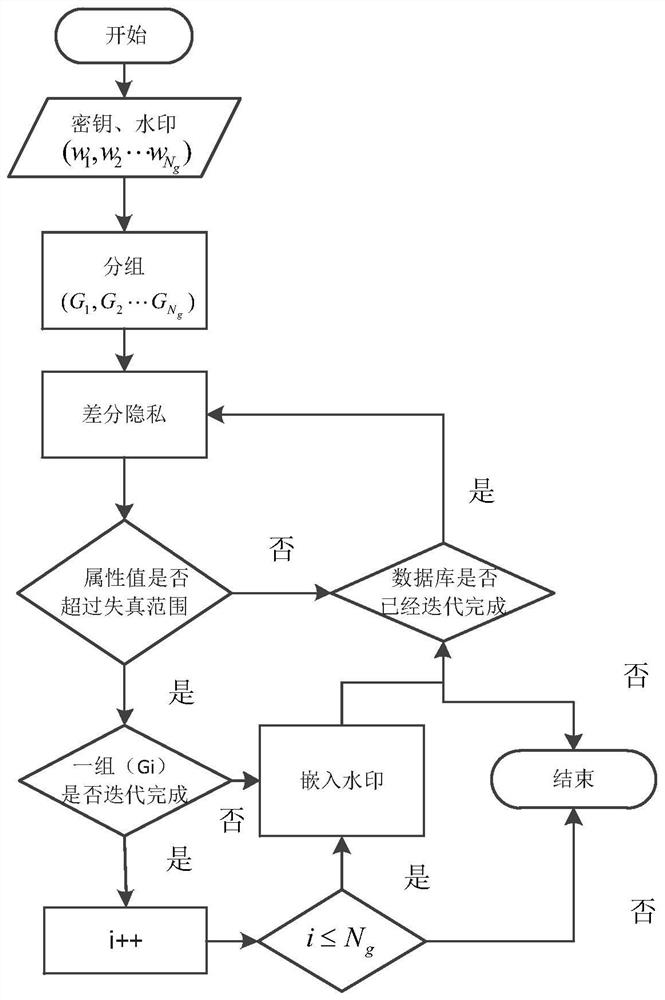
[0047] see figure 1 , the database watermark method based on local differential privacy in this example is: sort the attributes according to the attribute names of the database, group the tuples according to the primary key of the tuples in the database for watermark embedding; perform differential privacy on the sensitive attributes in the database, The watermark is embedded according to the distortion of the data after differential privacy, and then the database after the watermark is released to the cloud; all users can download the published database from the cloud and use the database but cannot obtain the sensitive data of an individual in the database through data analysis , the legitimate user who has the key can not only use the database, but also extract the watermark from the published database for copyright tracking and data integrity verification, and the attacker can attack the database and republish it to the cloud.
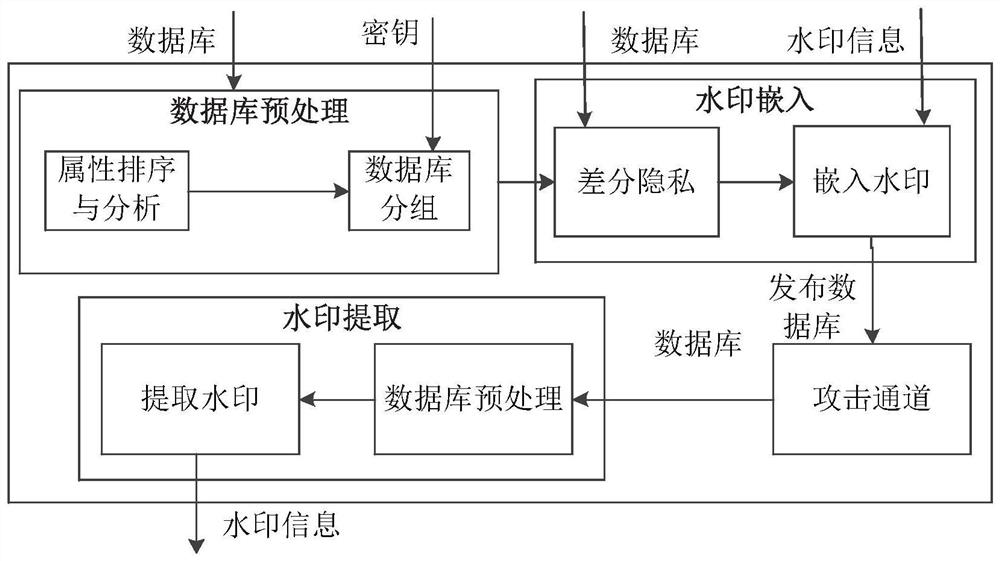
[0048] see figure 2 , in this embodiment, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com