Ciphertext database privacy protection enquiring method
A privacy protection and query method technology, which is applied in electrical digital data processing, special data processing applications, instruments, etc. It can solve the problem that the ciphertext data table does not maintain the same attribute value sequence relationship of different attributes, limited security, and single query method, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
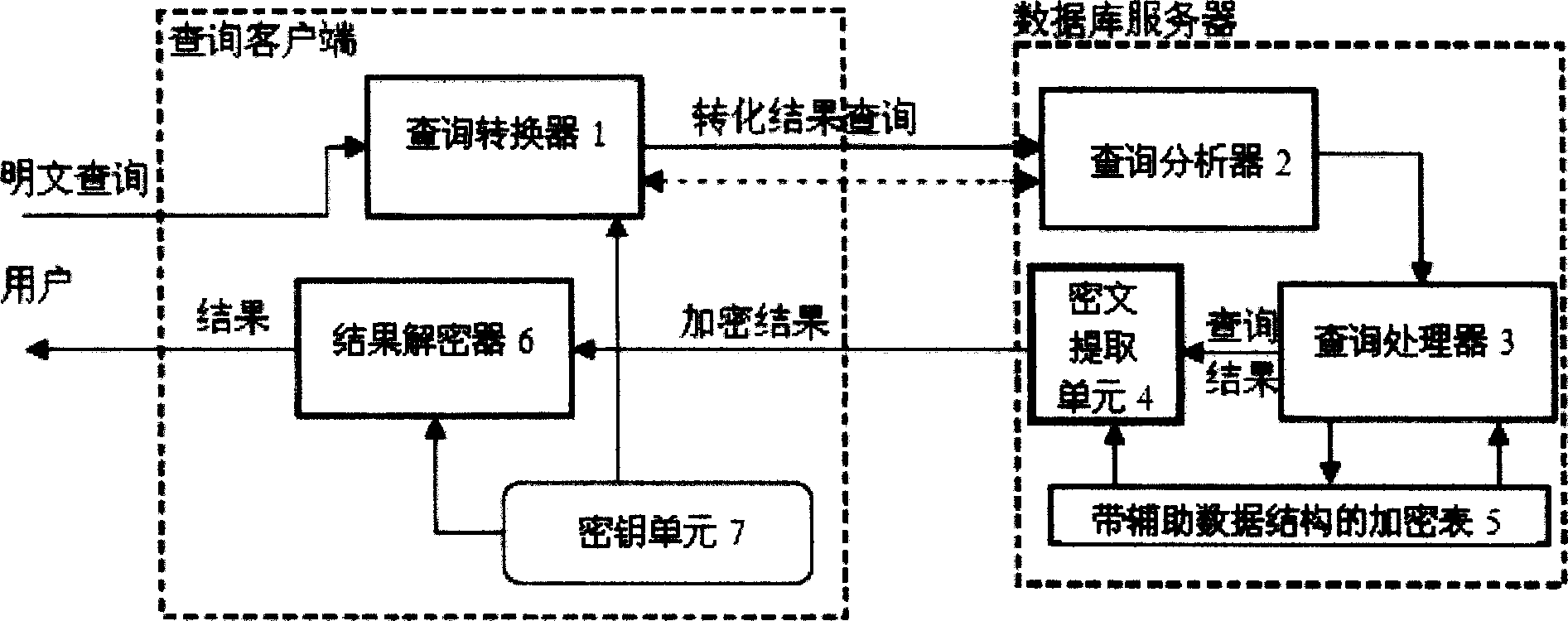
Image
Examples
Embodiment Construction
[0042] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
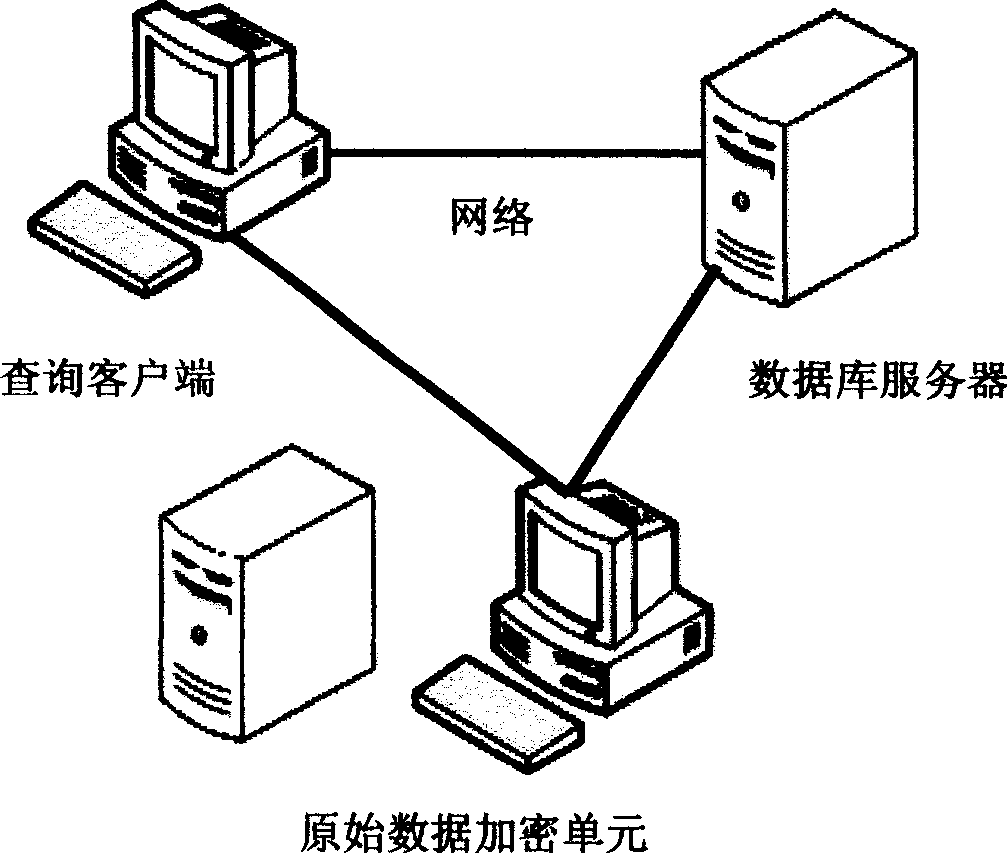
[0043] figure 1 is a schematic diagram of a ciphertext database query system according to an embodiment of the present invention. Wherein the original data encryption processing unit, the query client and the database server are connected to each other through the network. The network includes, but is not limited to, a local area network, a wide area network, and the Internet.
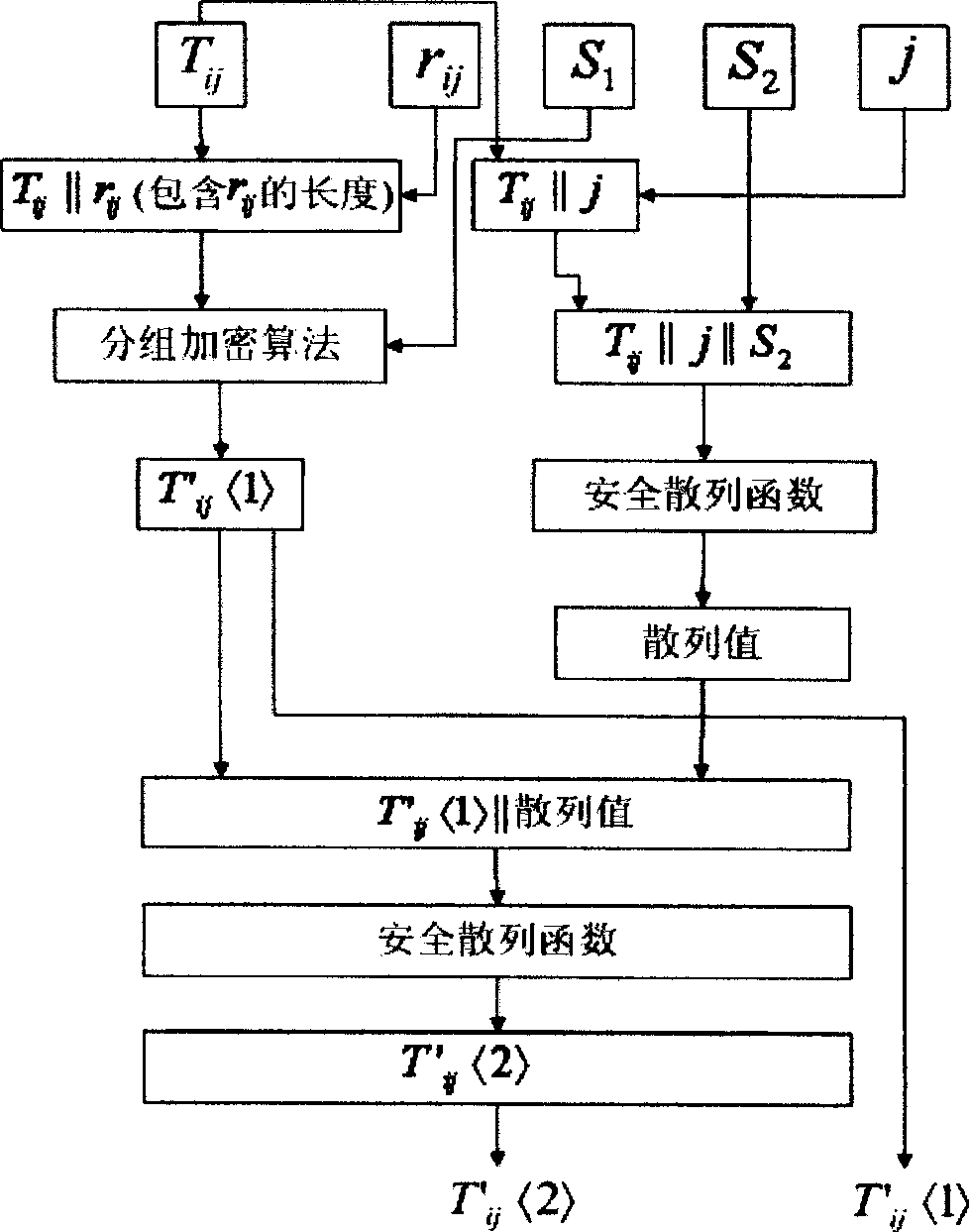
[0044] figure 2 It is a flow chart of data processing for an original data encryption processing unit to obtain a ciphertext value and an index value according to an embodiment of the present invention. As we all know, in the database query system, the most critical is the data structure of the stored data in the database, and the query protocol of how to use the stored data structure to query.
[0045] The data structure of the stored data set in the ciphertext d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com