Network-based detection method of rebound ports Trojan horse
A detection method and port technology, applied in the field of network information security, can solve the problems of not allowing the host to install anti-virus software and Trojan-killing tools, and the inability of anti-virus software and Trojan-killing tools to function.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
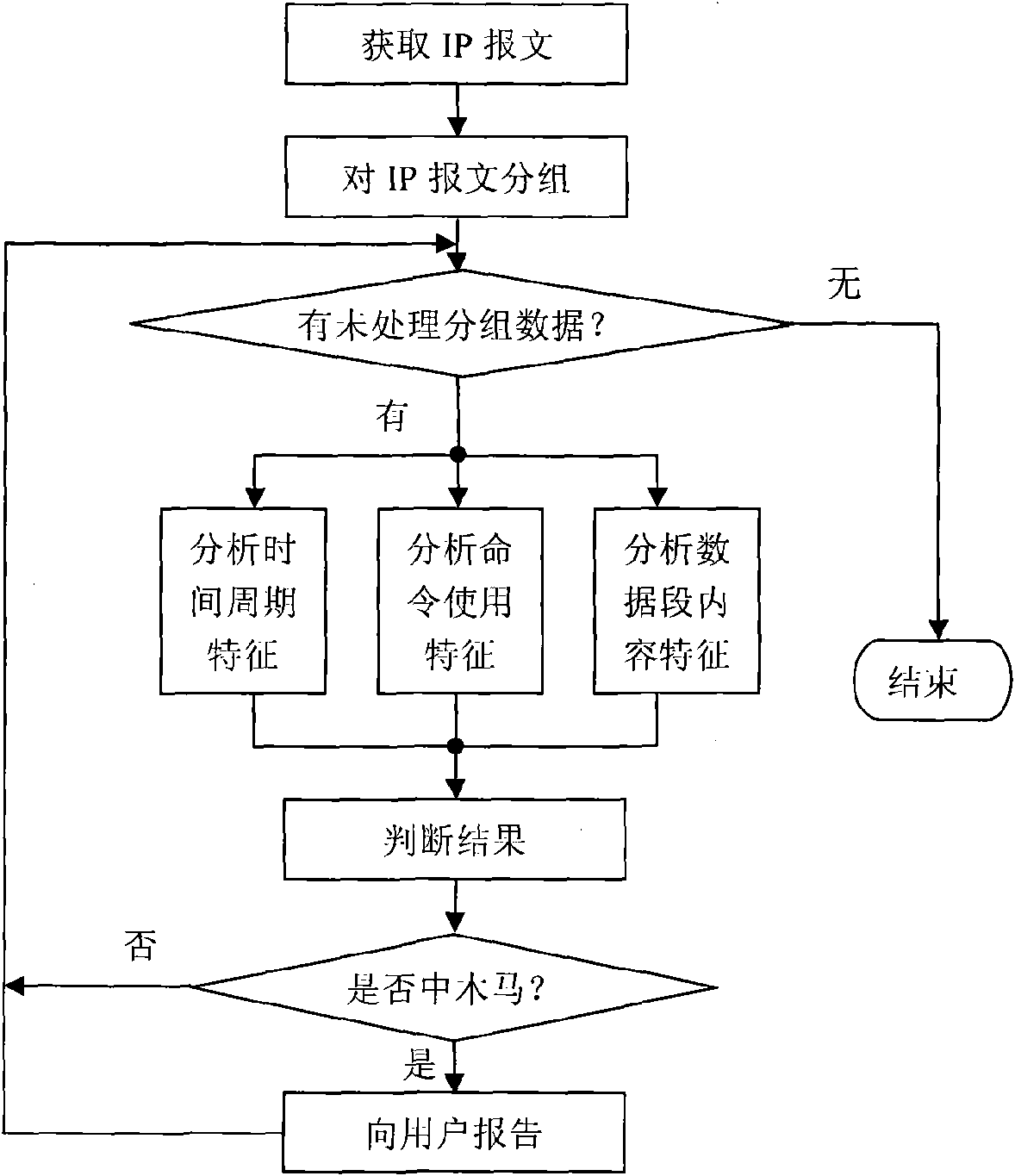
[0060] According to the above technical solutions, the present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
[0061] Taking a kind of more popular rebounding port type Trojan horse in China—the gray pigeon Trojan horse as an example, the detection process of the Trojan horse using the present invention is explained. In this example, the sampling time period T=30 minutes, the parameter T 0 = 0.1, m 1 = m 2 = m 3 = 0.9.
[0062] Through analysis, it is found that the server of the Gray Pigeon Trojan has the following network behavior characteristics:
[0063] (1) Time feature: the time period for the gray pigeon Trojan server to access the broiler is 10 seconds;
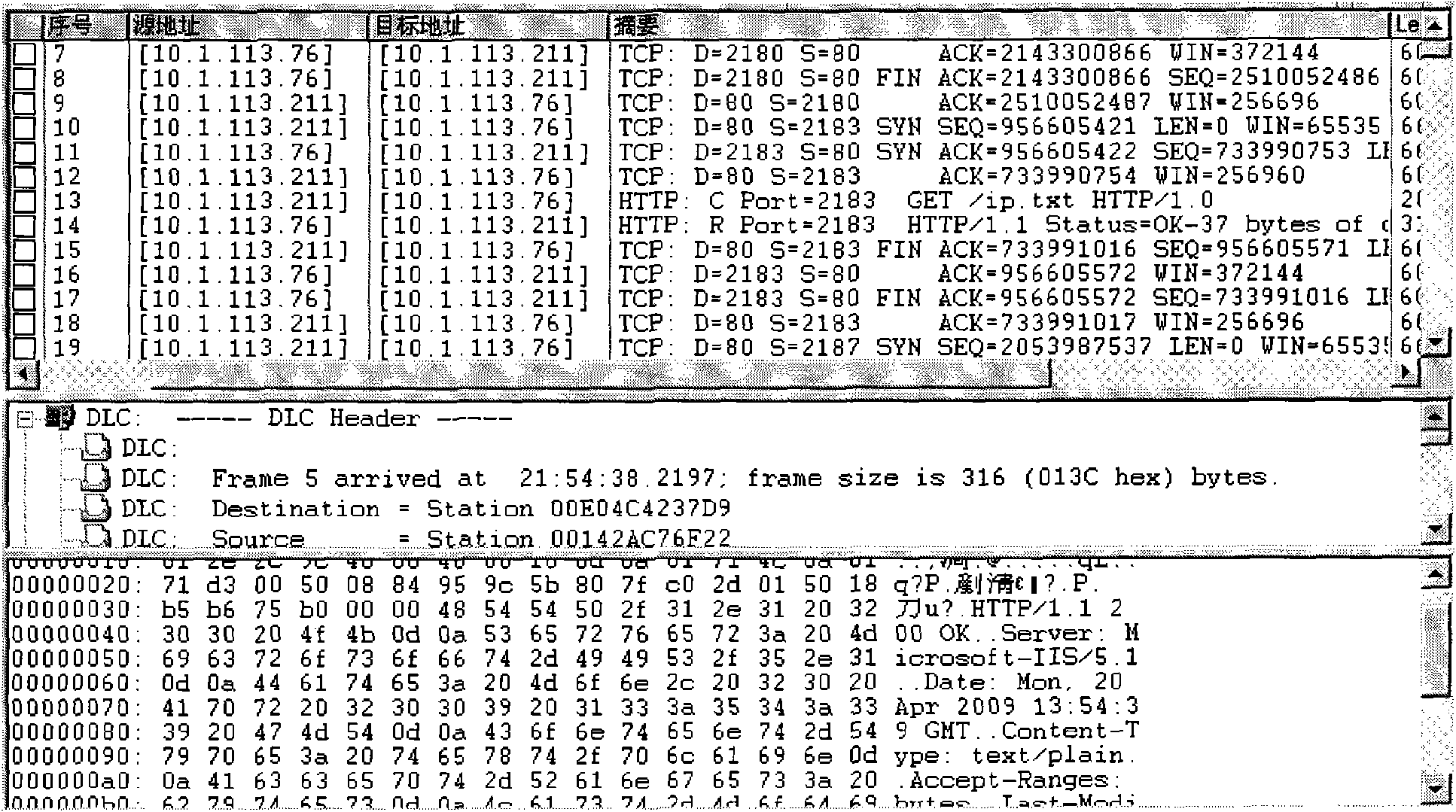
[0064] (2) Protocol features: the server of the gray pigeon Trojan uses the GET command of the http protocol to access the broiler, and the port is port 80;
[0065] (3) Data content characteristics: the content of the file returned by the broiler to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com