Method and circuit for credible design of integrated circuit design process
An integrated circuit and circuit technology, applied in CAD circuit design, computer aided design, calculation, etc., can solve the problems that analog circuits are susceptible to process deviation, high monitor circuit scale and complexity, and affect measurement results, etc., to achieve Reduce the difficulty of testing, reduce the impact, and ensure the effect of accurate measurement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
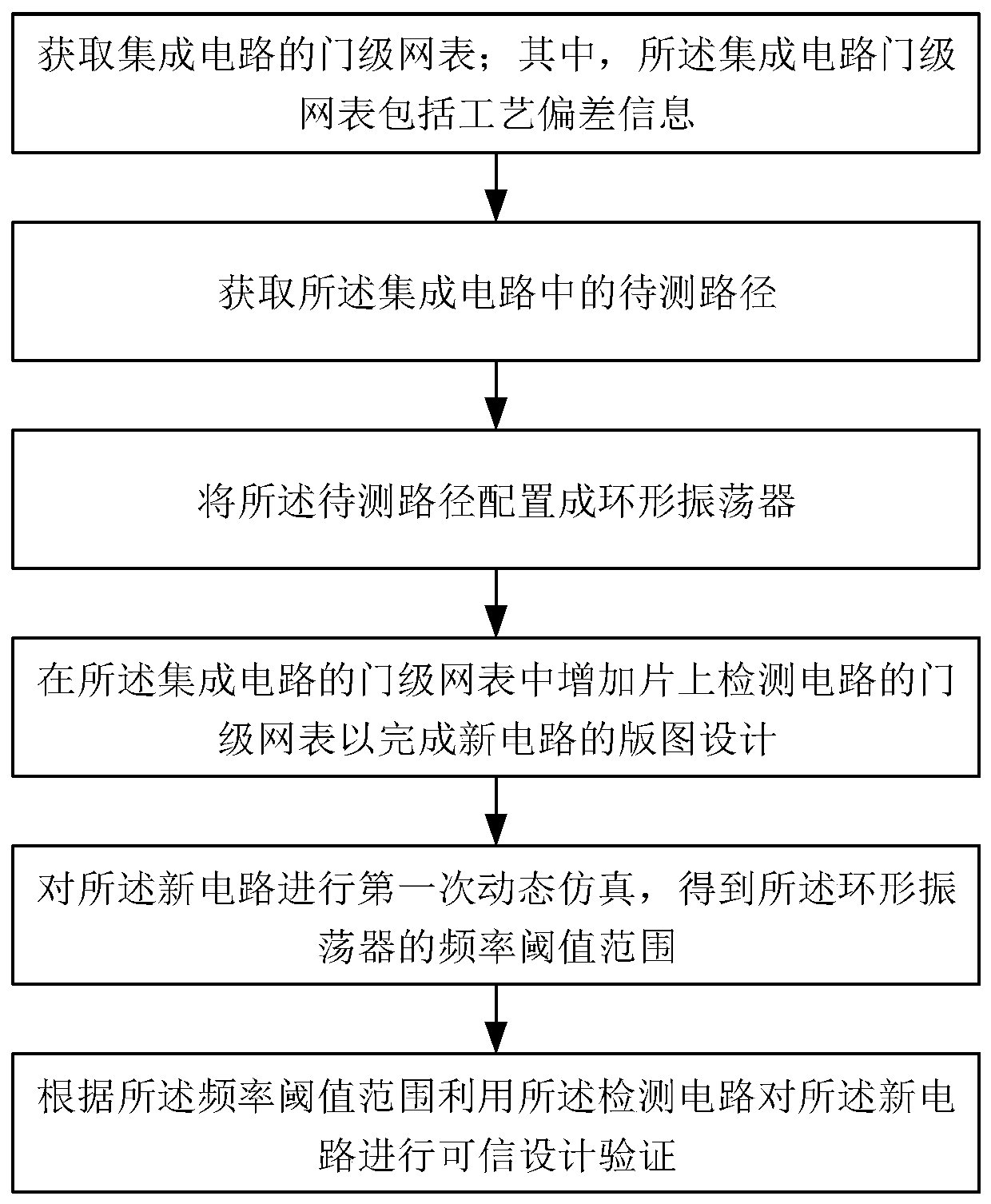
[0063] See figure 1 , figure 1 It is a flow chart of a method for trusted design of integrated circuit design process provided by an embodiment of the present invention, including:
[0064] Step 1: Obtain the gate-level netlist of the integrated circuit; wherein, the gate-level netlist of the integrated circuit includes process deviation information.
[0065] In this embodiment, said obtaining the gate-level netlist of the integrated circuit includes:
[0066] Read the lib file in the process library to obtain the first lib process library file;
[0067] Import process deviation to the first lib process library file to obtain the second lib process library file;
[0068] Compiling the second lib process library file to obtain a db process library file;
[0069] Constrain the db process library file and the integrated circuit to obtain gate-level netlists of multiple integrated circuits and timing constraint files corresponding to the gate-level netlists.
[0070] Specifical...
Embodiment 2
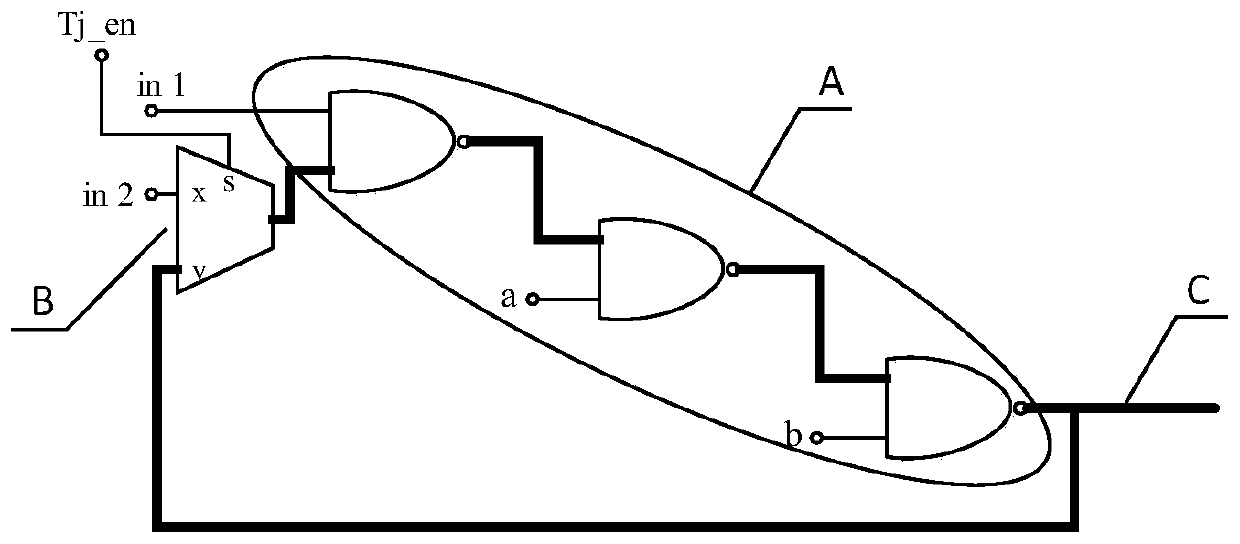
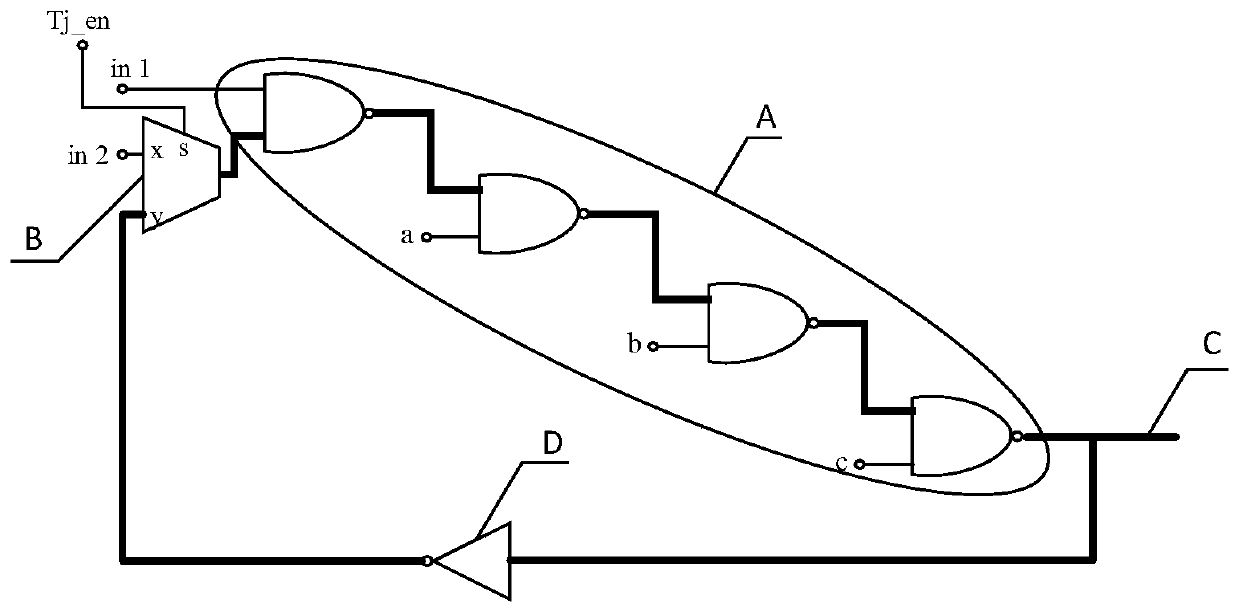
[0113] Another embodiment of the present invention also provides a circuit for trusted design of integrated circuit design process, please refer to Figure 4 , Figure 4 It is a block diagram of a circuit structure used in the credible design of the integrated circuit design process provided by the embodiment of the present invention, including:
[0114] A mode selection module 1, configured to configure the integrated circuit into several ring oscillators and output several oscillating signals;
[0115] A signal selection module 2, connected to the mode selection module 1, for selecting and outputting one of the plurality of oscillating signals;
[0116] The detection module 3 is connected to the signal selection module 2 and used for frequency detection of the oscillation signal.
[0117] In this embodiment, the mode selection module 1 includes a two-to-one data selector, which is set at the input end of the path to be tested in the integrated circuit, which enables the pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com