Java Web application memory Trojan horse detection method, terminal equipment and storage medium
A memory Trojan horse and detection method technology, applied in software engineering design, creation/generation of source code, instrument, etc., can solve problems such as large resource consumption, abnormal process crash, and impact on business applications, so as to achieve low resource consumption and avoid I/O The effect of the O operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
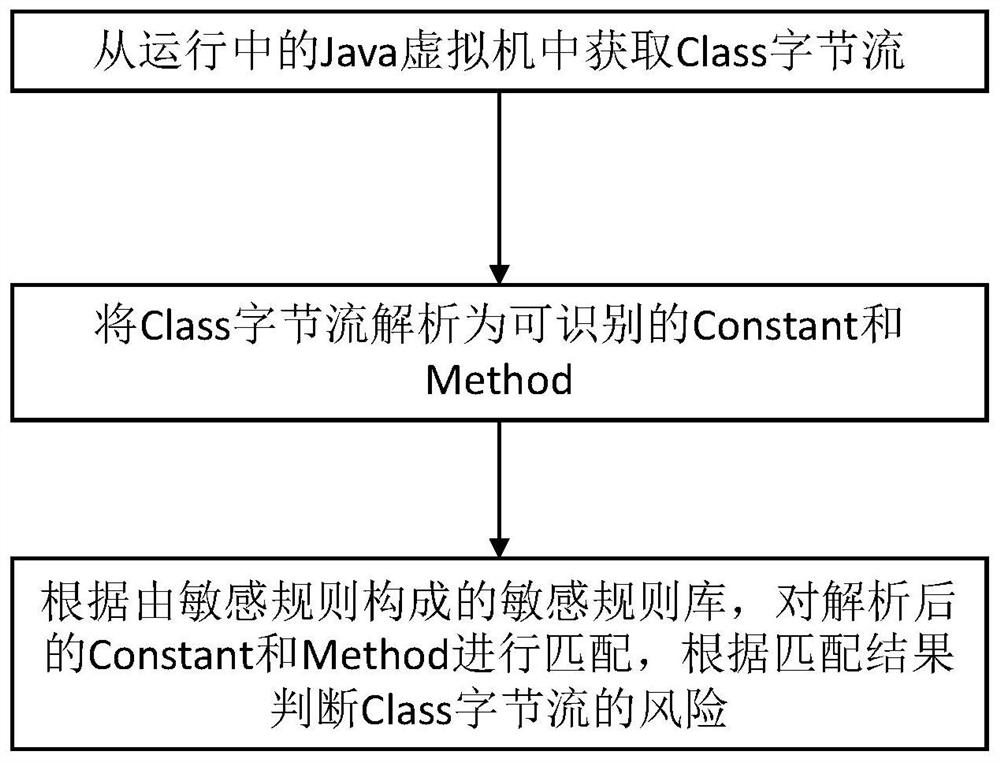
[0024] The embodiment of the present invention provides a Java Web application memory Trojan detection method, such as figure 1 As shown, the method includes the following steps:
[0025] S1: Obtain a Class byte stream from a running Java Virtual Machine (Java Virtual Machine, JVM).
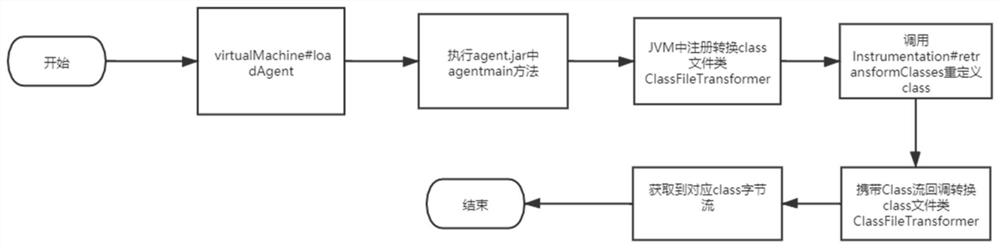
[0026] In this embodiment, the Class byte stream is obtained from the running Java virtual machine by Java agent technology, such as figure 2 As shown, the specific implementation method is as follows: write a jar file in advance according to the Java agent technical specification, use VirtualMachine.attach(pid) to inject the written jar file into the target process, register the conversion class file class ClassFileTransformer in the Java virtual machine, and call After InstrumentationUtils#retransformClasses redefines the Class, the Class byte stream running in the Java virtual machine can be captured.
[0027] S2: Parse the Class byte stream into recognizable Constant and Method.
[0028] ...
Embodiment 2
[0052] The present invention also provides a Java Web application memory Trojan detection terminal device, including a memory, a processor, and a computer program stored in the memory and operable on the processor, when the processor executes the computer program The steps in the above method embodiment of Embodiment 1 of the present invention are realized.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com