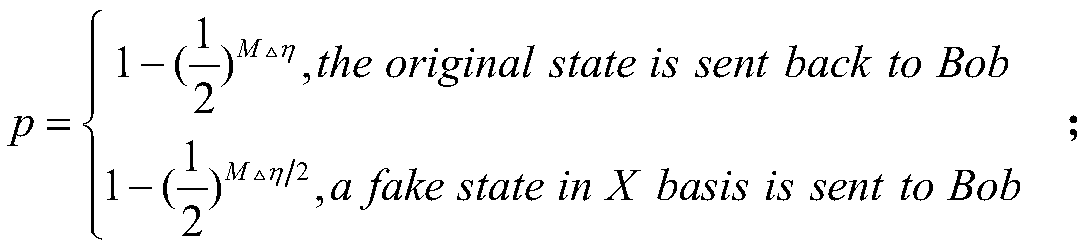Sequence rearrangement-based quantum database privacy query method with better user privacy performance
A query method and database technology, applied in the direction of digital data protection, electronic digital data processing, special data processing applications, etc., can solve the problems of secret information leakage, user loss, fatal blow, etc., to resist Trojan horse attacks and reduce space complexity The effect of reducing the difficulty and cost of implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
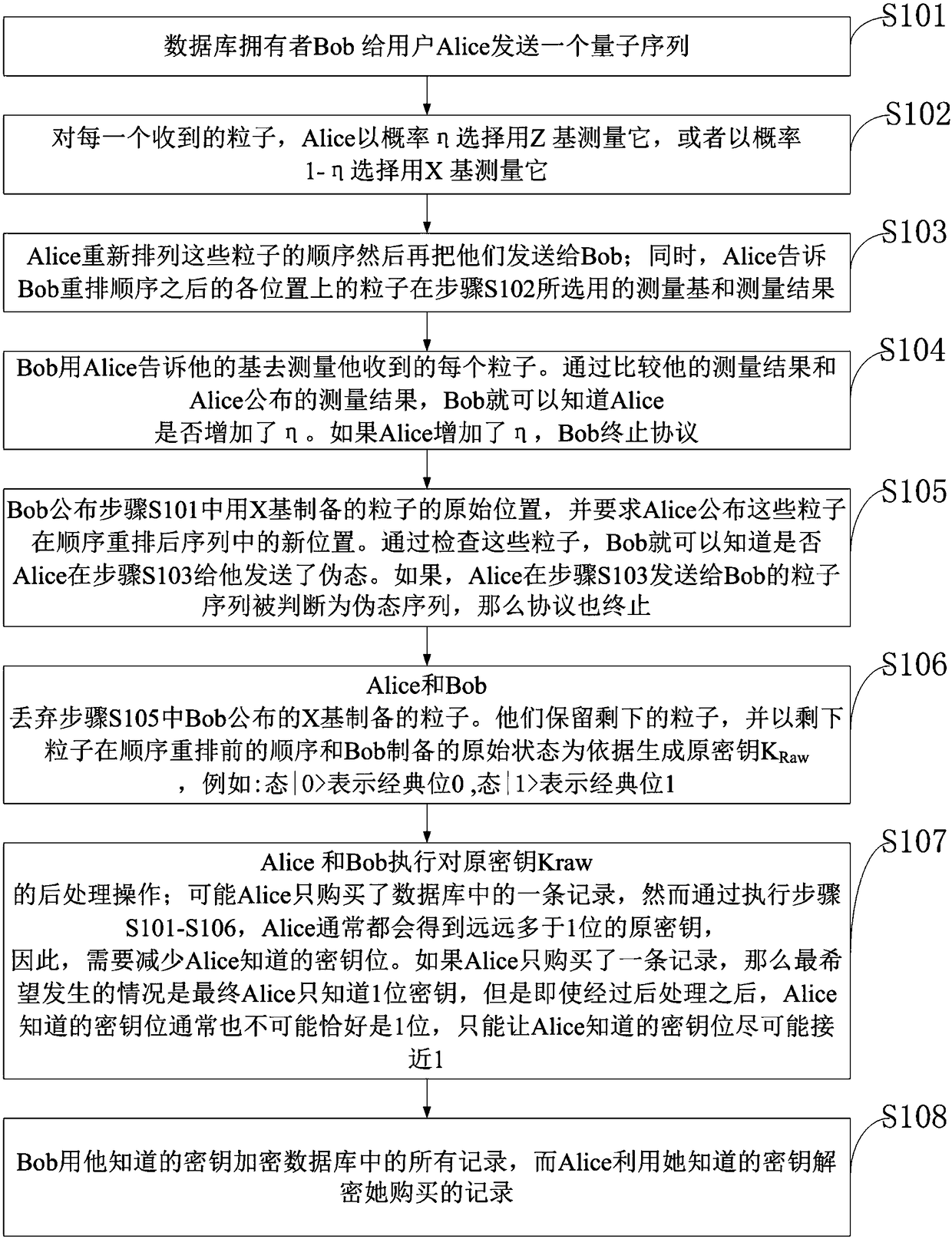
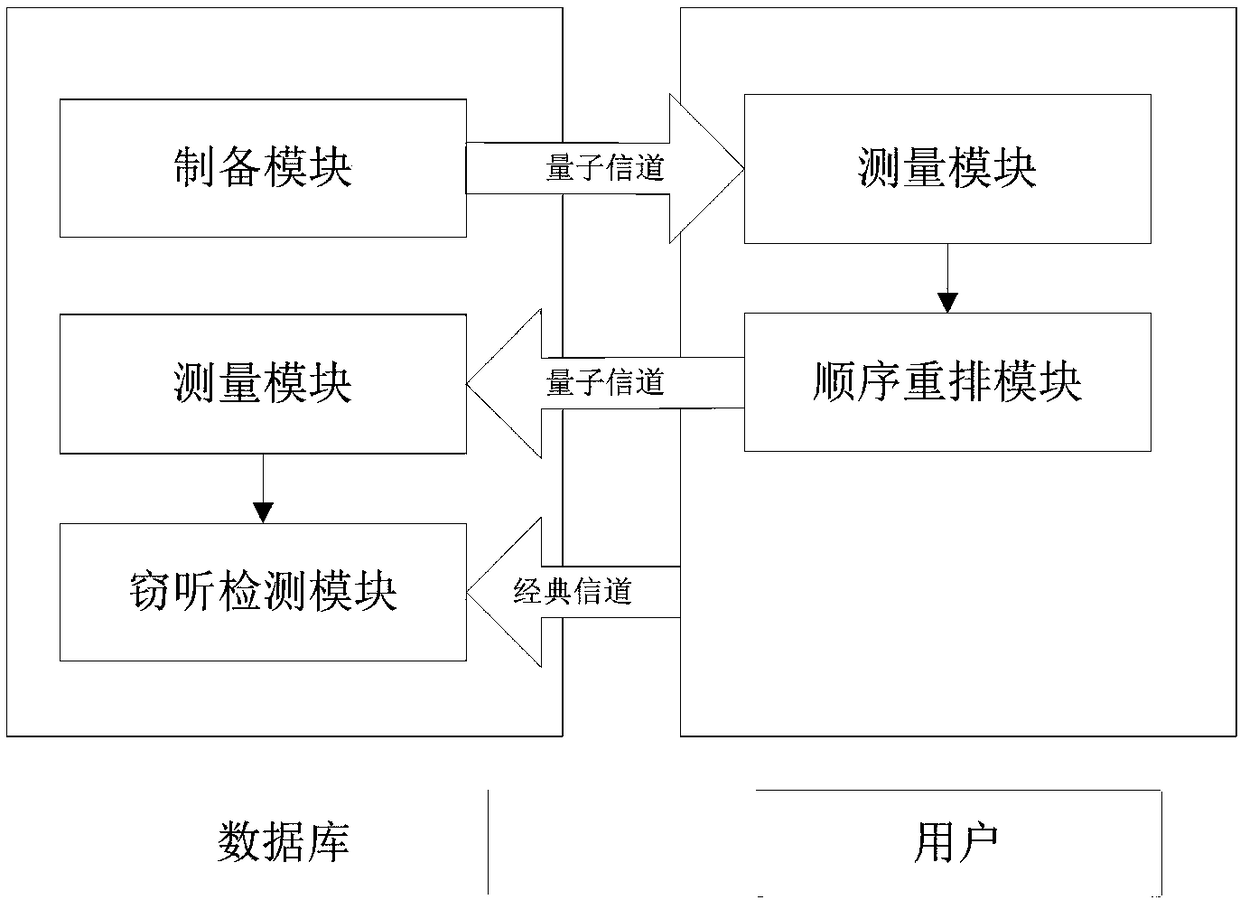
[0032] In order to make the object, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
[0033]In the existing technology, multiple database copies are required to provide perfect user privacy protection. Not only is the space complexity high, but also it is difficult to manage multiple database copies in a unified manner. Therefore, most of the existing technologies believe that user privacy is not required in some cases. Perfect protection is only safe under a certain premise. Therefore, the requirements for user privacy protection are relaxed. In the existing quantum database privacy query protocols, the protection of user privacy is only sensitive to deception, that is, it is impossible for the database own...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com