Security protection method of communication data of special electricity public network
A public network communication and data security technology, which is applied in the direction of secure communication devices, electrical components, network connections, etc., can solve problems such as fragile security, low security, and high security, and achieve reliable behavior auditing, improving security, and ensuring The effect of identity reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
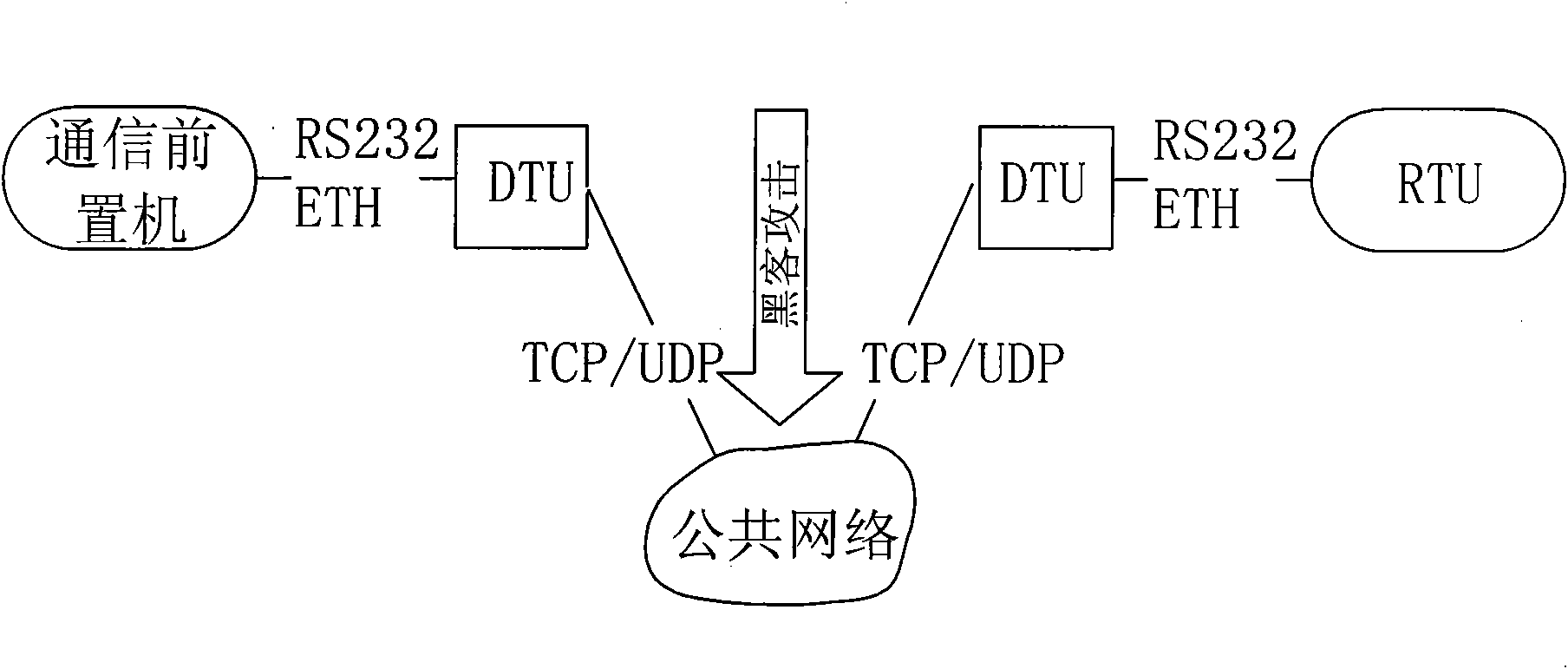
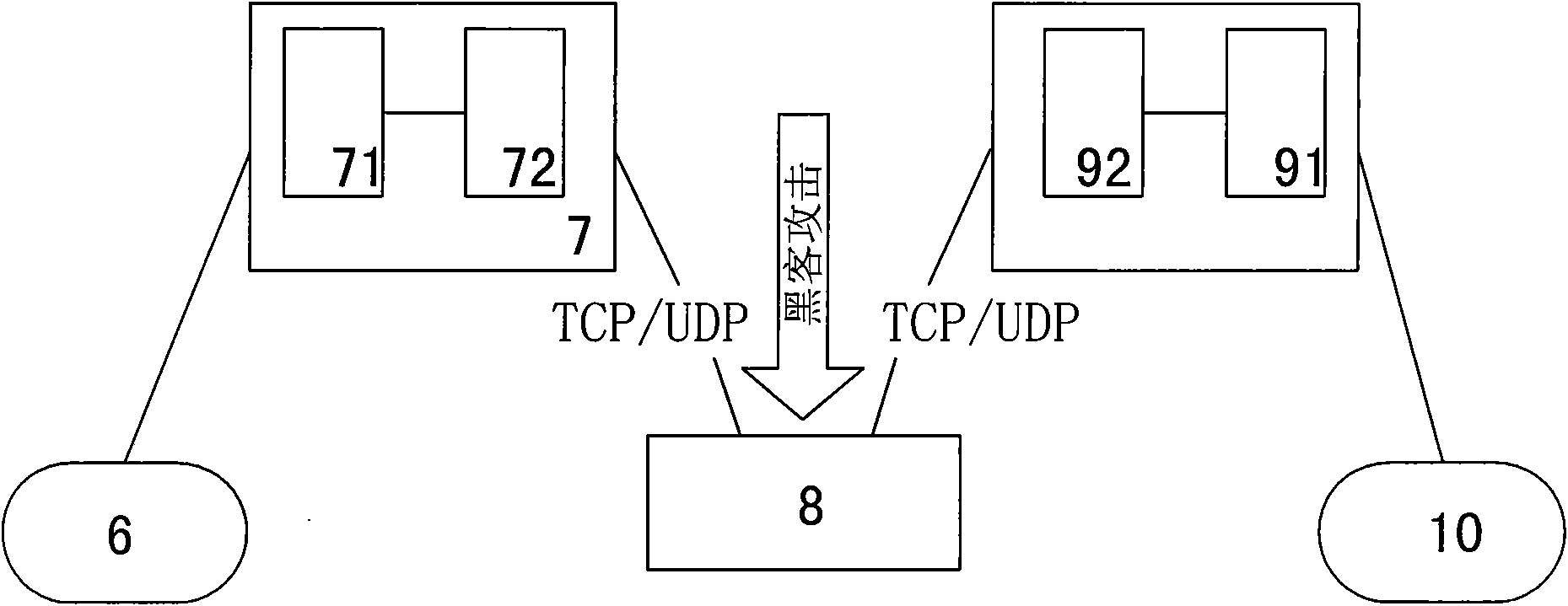
[0035] Such as figure 2 As shown, the environment after application of the present invention is: the calling telecontrol communication security gateway 7 and the called telecontrol communication security gateway 9 are connected to the public network 8 by dialing, and an encrypted communication is established for the communication front-end processor 6 and the remote RTU10 Public network communication channel, the data is connected to the telecontrol communication security gateway 7 through the serial port or the network from the communication front-end processor 6, then connected to the public network 8 through the telecontrol communication security gateway 7, and then connected to the telecontrol communication security gateway from the public network 8 9. Connect the remote RTU10 through a serial port or a network, the calling remote communication security gateway 7 is provided with an internal network host I71 and an external network host I72, and the called remote communica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com