Patents
Literature
40 results about "Computer security model" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A computer security model is a scheme for specifying and enforcing security policies. A security model may be founded upon a formal model of access rights, a model of computation, a model of distributed computing, or no particular theoretical grounding at all. A computer security model is implemented through a computer security policy.
Computer security and management system
Owner:CISCO TECH INC
Computer security and management system
ActiveUS20020129264A1Memory loss protectionData taking preventionComputer security modelDirect execution
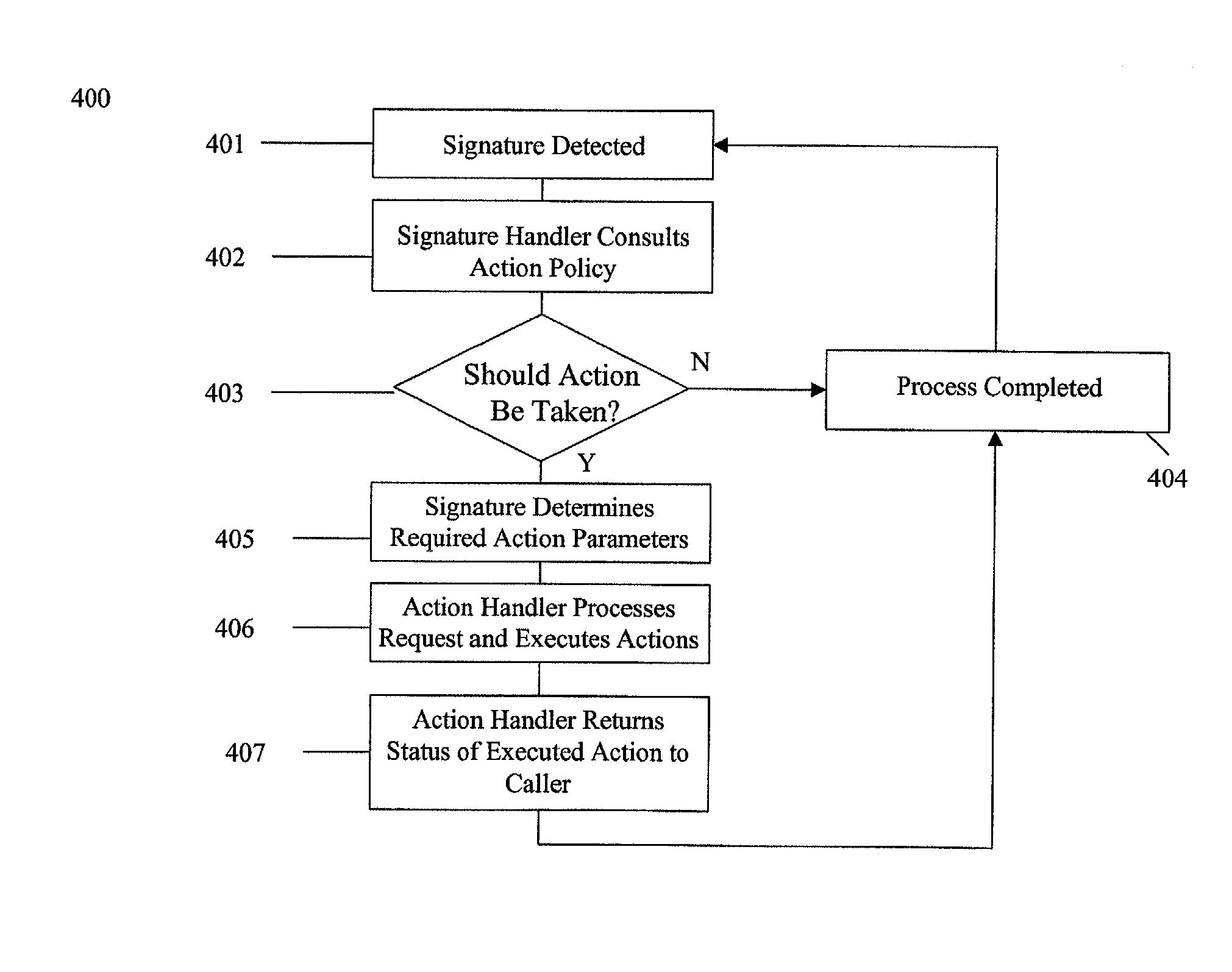
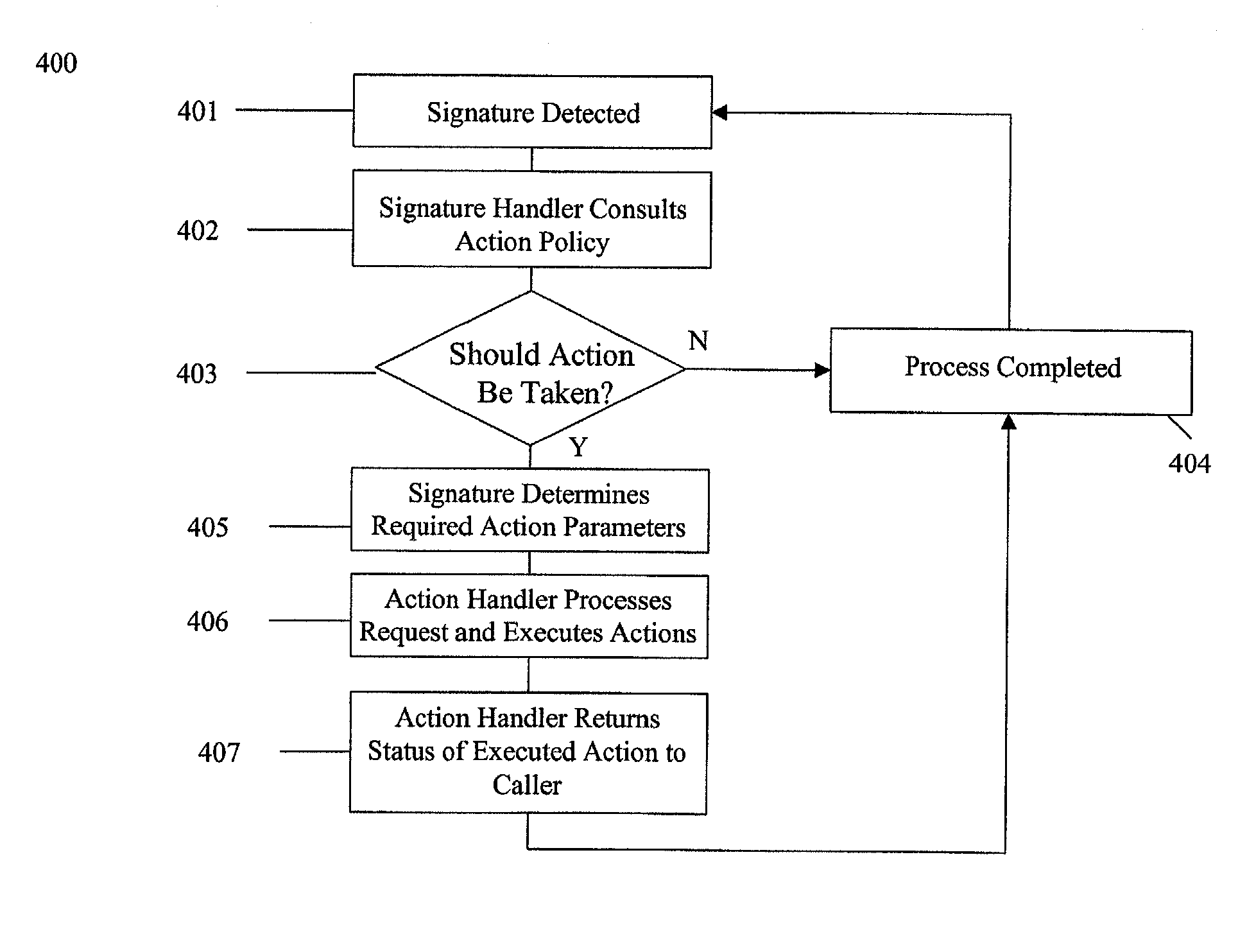
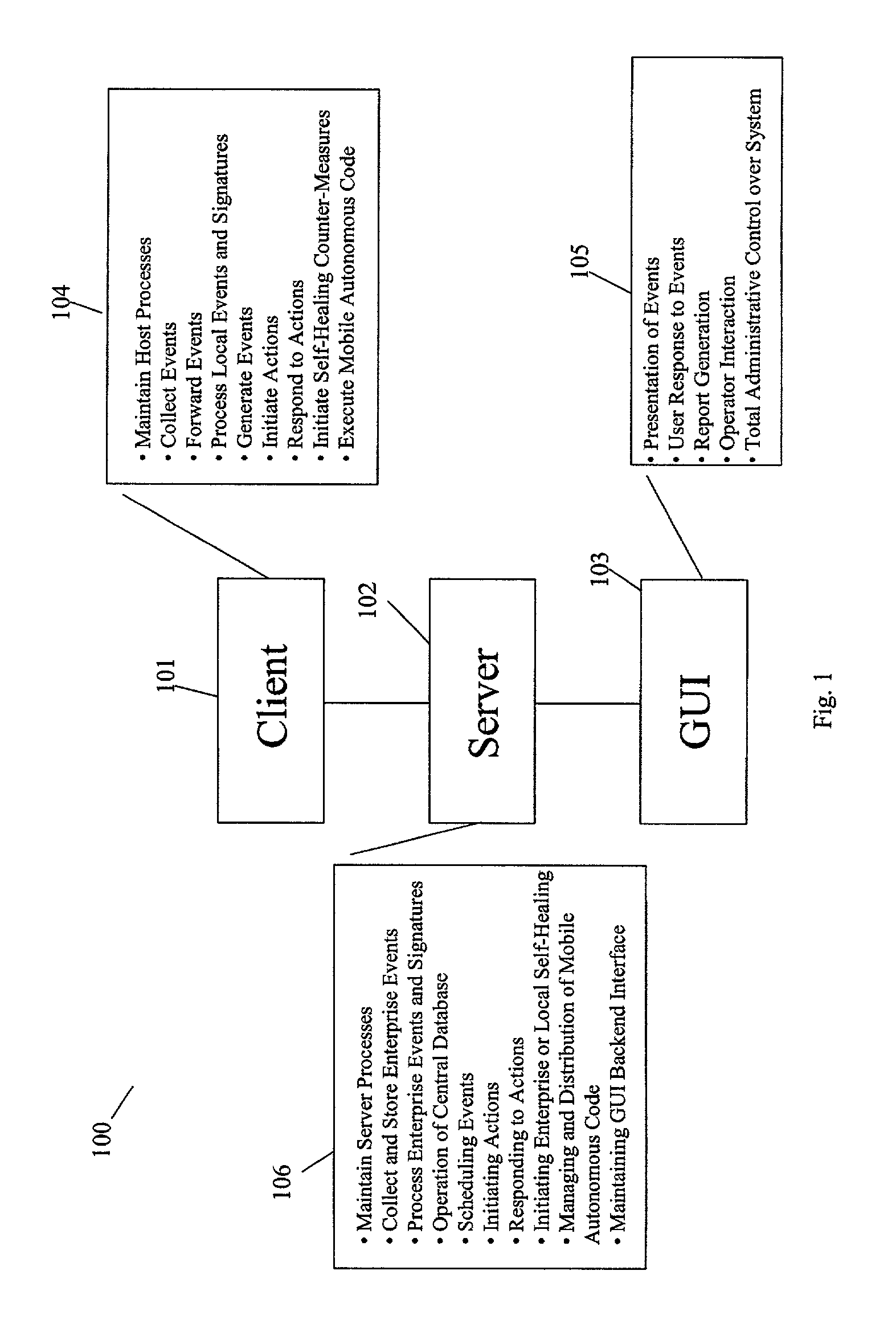
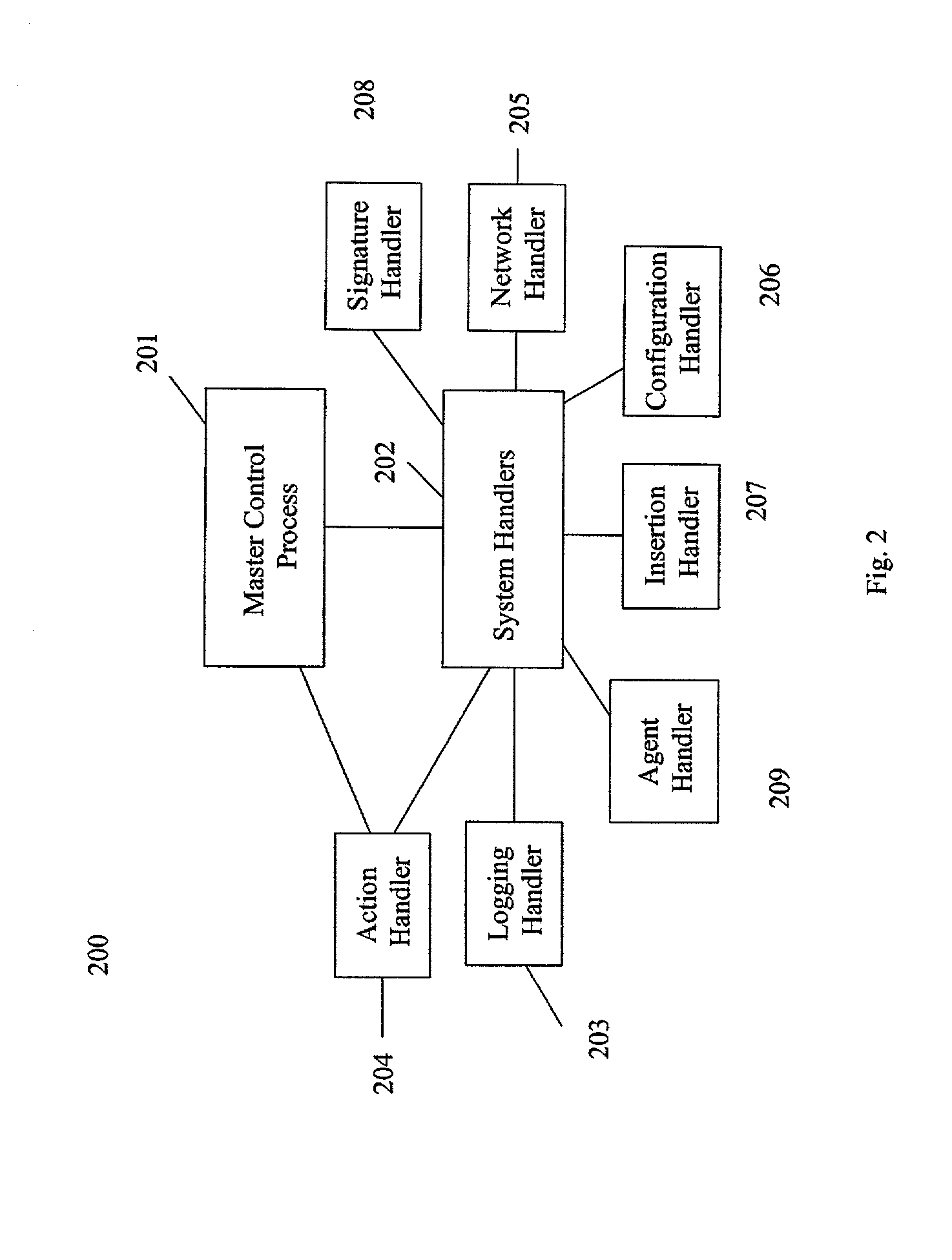
The present invention provides a generic distributed command, control, and communication framework that allows computer systems, devices, and operational personnel to interact with the network as a unified entity. The present invention provides these services by building upon a core communication architecture that permits local or remote execution of mobile program code, static execution of program code, flexible communication formats, self-healing network techniques, and expansion by the addition of new system modules, software handlers, or mobile autonomous agents.
Owner:CISCO TECH INC
Computer security system
InactiveUS7013485B2Digital data processing detailsUnauthorized memory use protectionComputerized systemSecurity domain
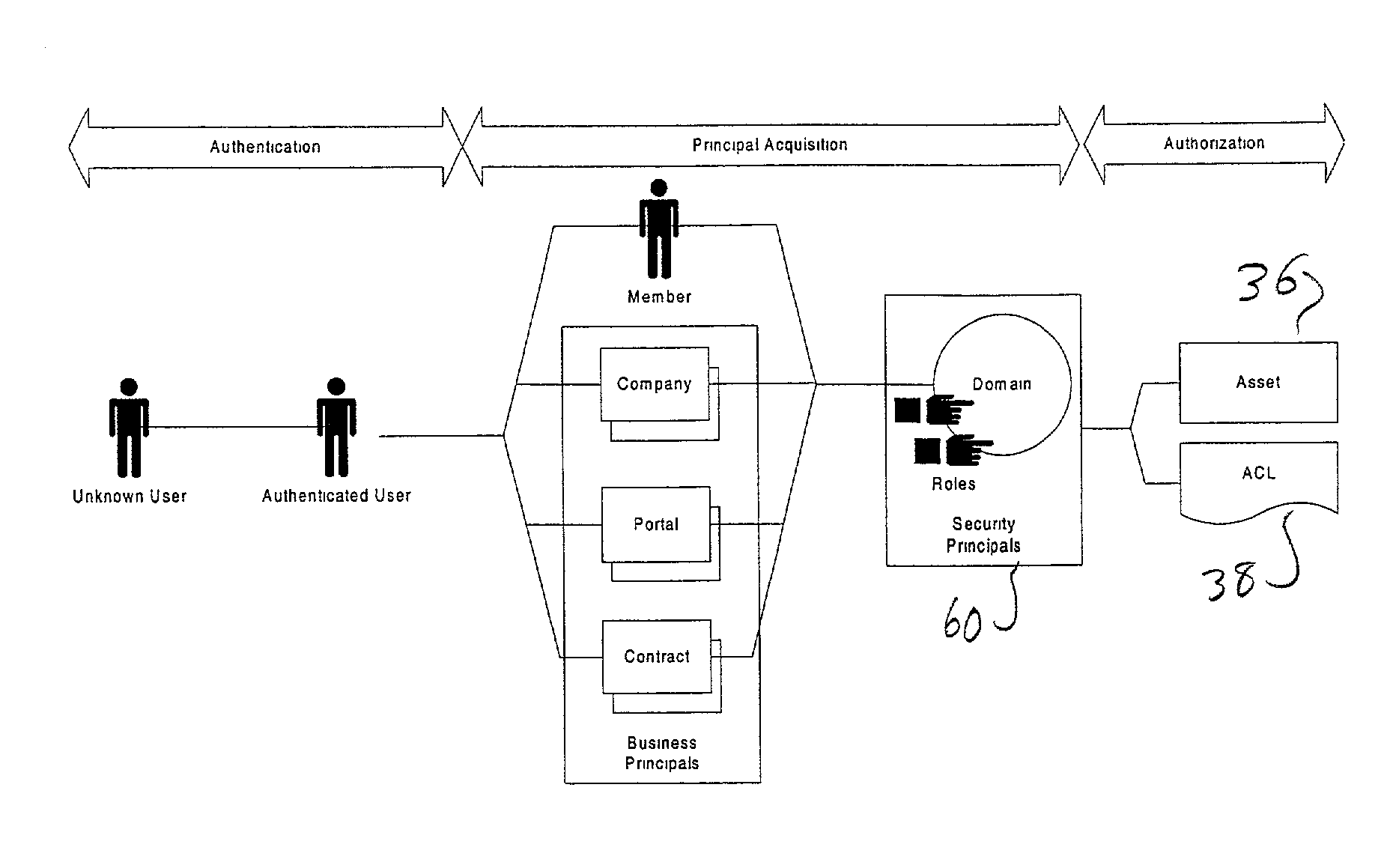
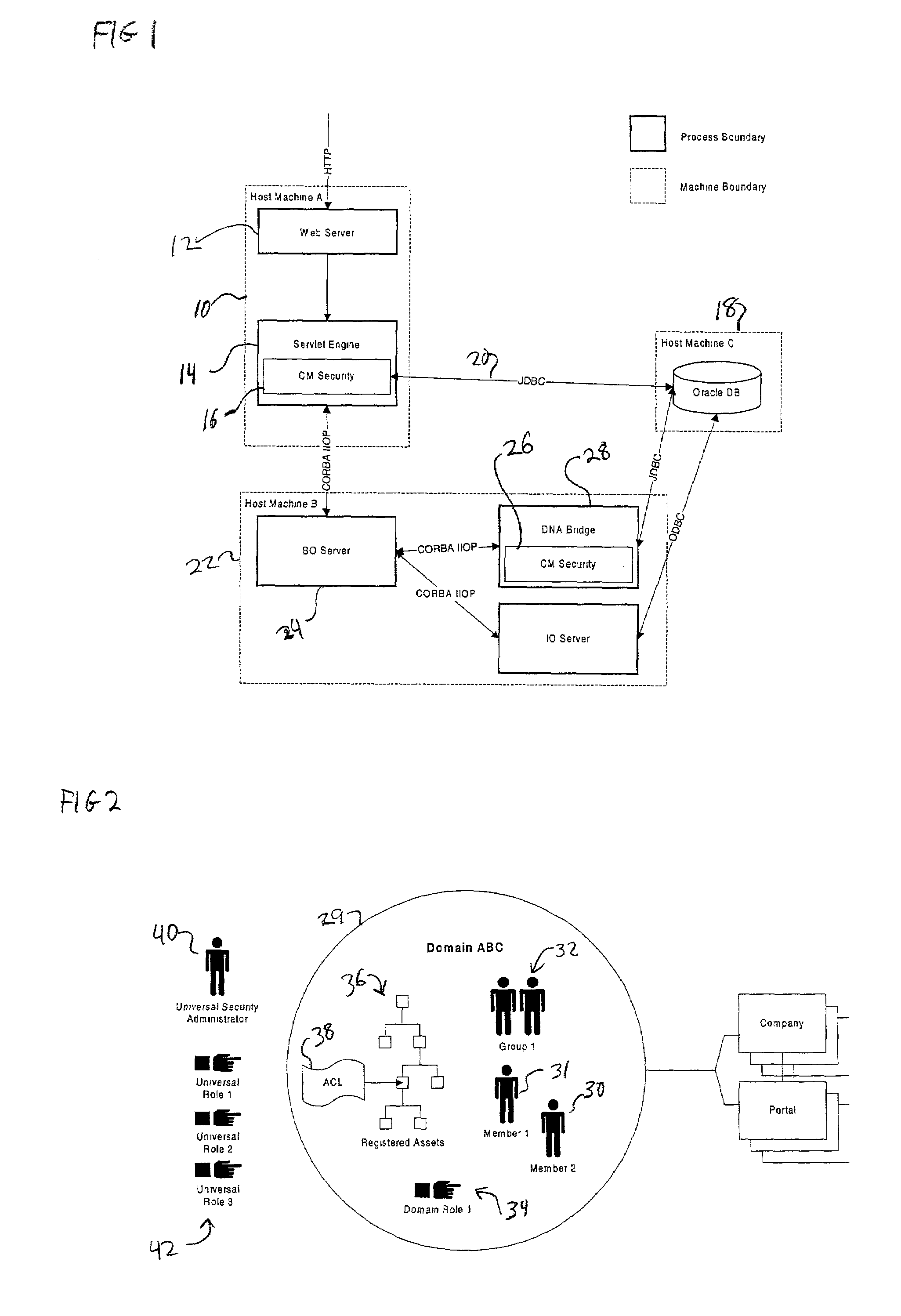
A security system for a computer system provides one or more security domains. Access to assets registered to the security system is controlled by rights and privileges. Rights are derived from roles, and each user is assigned one or more roles. Privileges are attached to assets, and an appropriate combination of rights and privileges is required before a user is granted the specified type of access to the asset.
Owner:JDA SOFTWARE GROUP
Computer security system
InactiveUS7131000B2Data processing applicationsDigital data processing detailsComputerized systemComputer security model
A computer system provides system-wide computer application security using role-based identifiers. The programmer identifies secured functions within a software application using a hierarchical identifier. The hierarchical identifiers are grouped together into privilege sets. The privilege sets and other hierarchical identifiers are grouped together into job functions, which are in turn grouped into larger subsets called user roles. These user roles are stored in a data store. User identifiers are created. Each user identifier is linked to one user role in the data store. A surrogate identifier is created to correspond to each user role and is stored in the data store. The surrogate identifiers are not disclosed to the users. A user is given permission to access secured functions within an application by retrieving a surrogate identifier from the data store, which shares the same user role as the user. Access rights are determined using the surrogate identifier to validate permissions on a security provider.
Owner:JOLLY SEVEN SERIES 70 OF ALLIED SECURITY TRUST I
Computer security method and apparatus
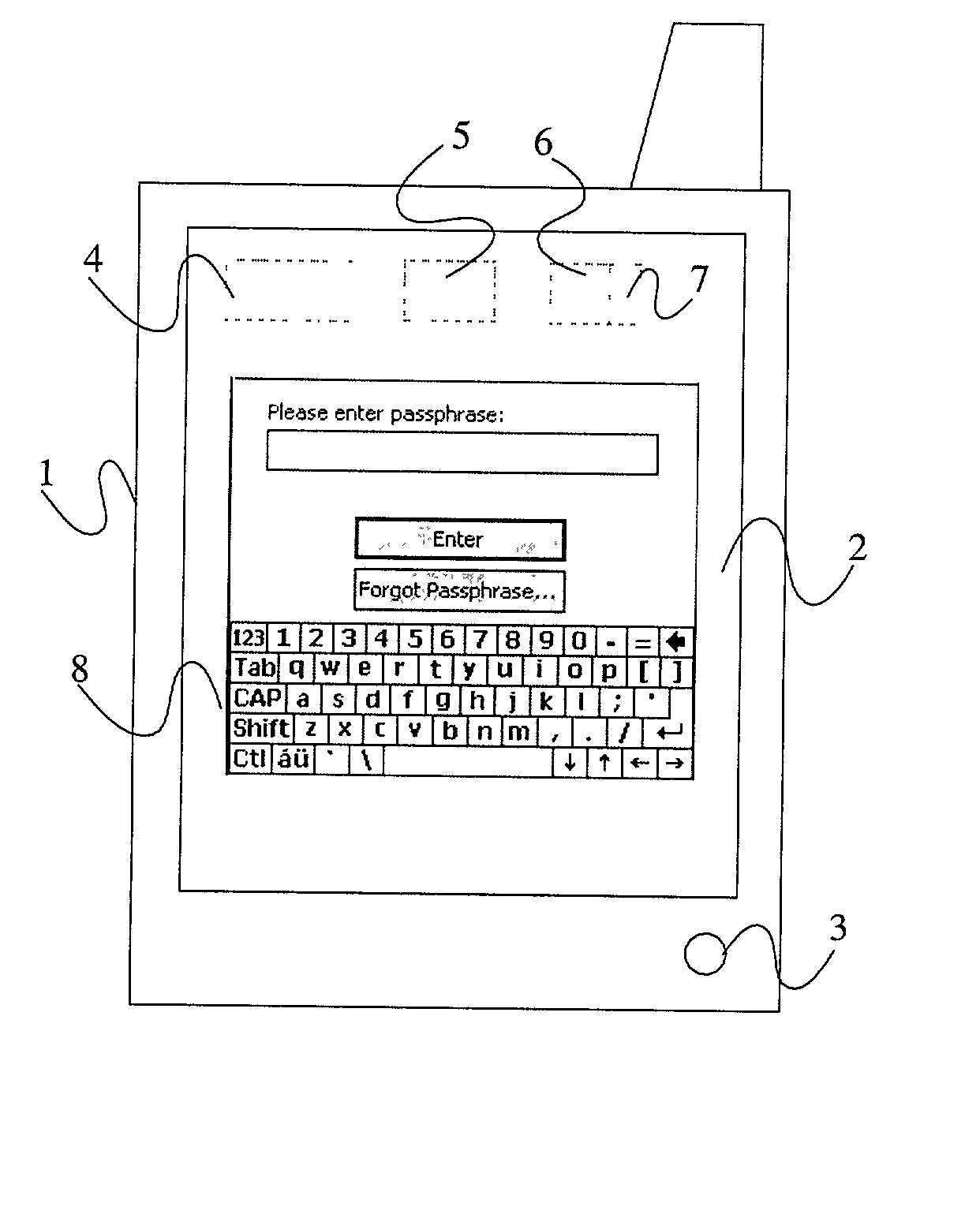
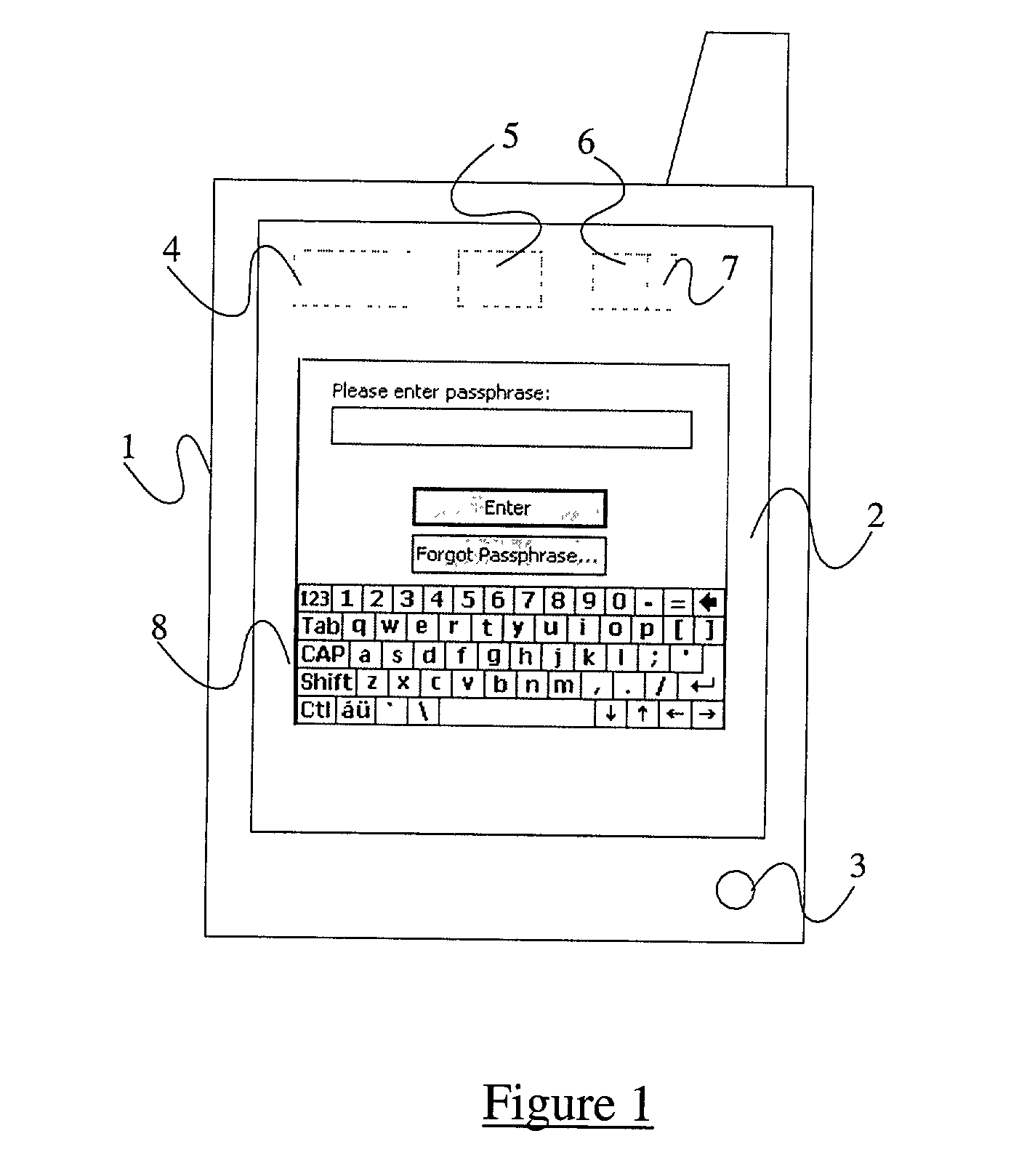
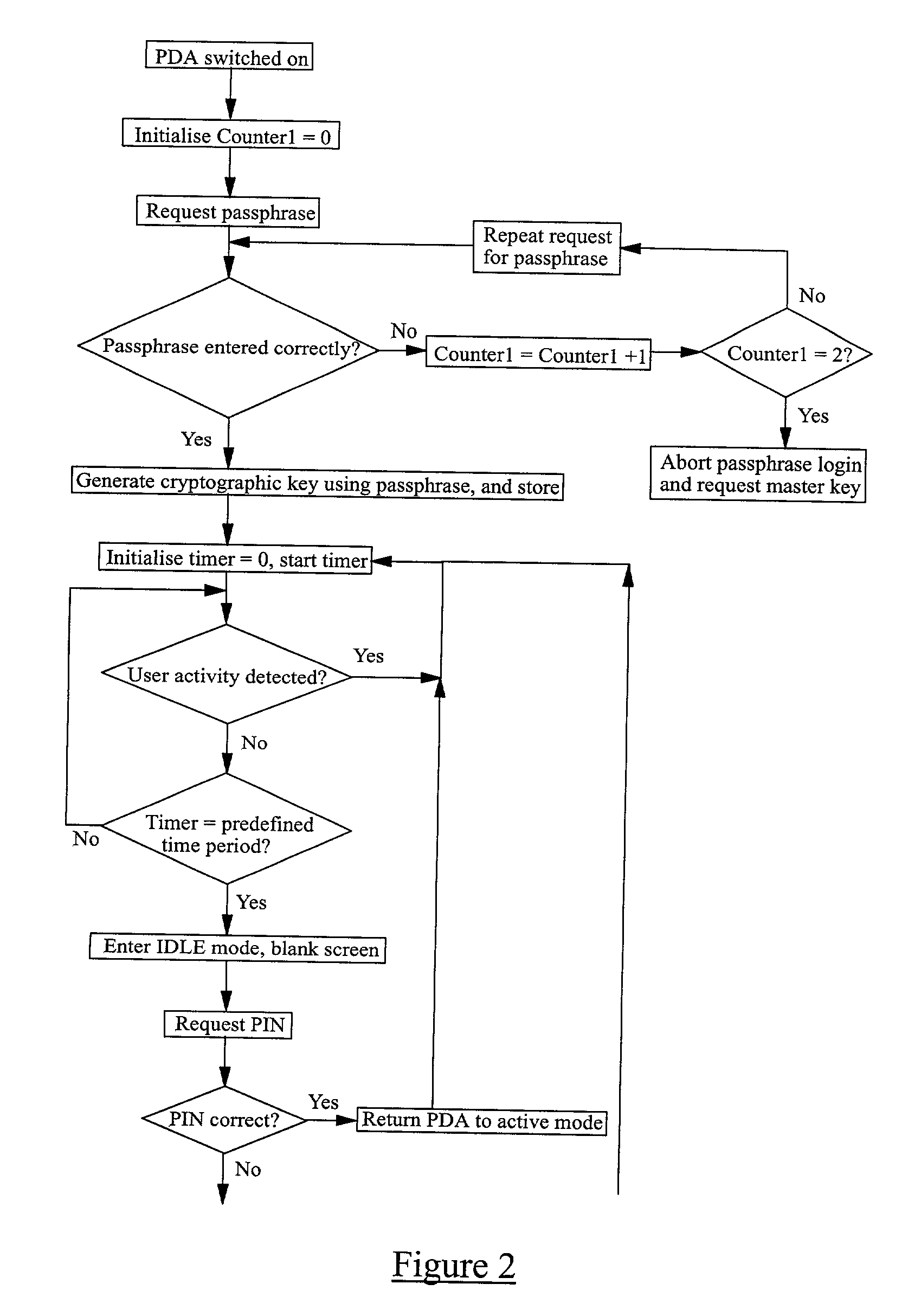
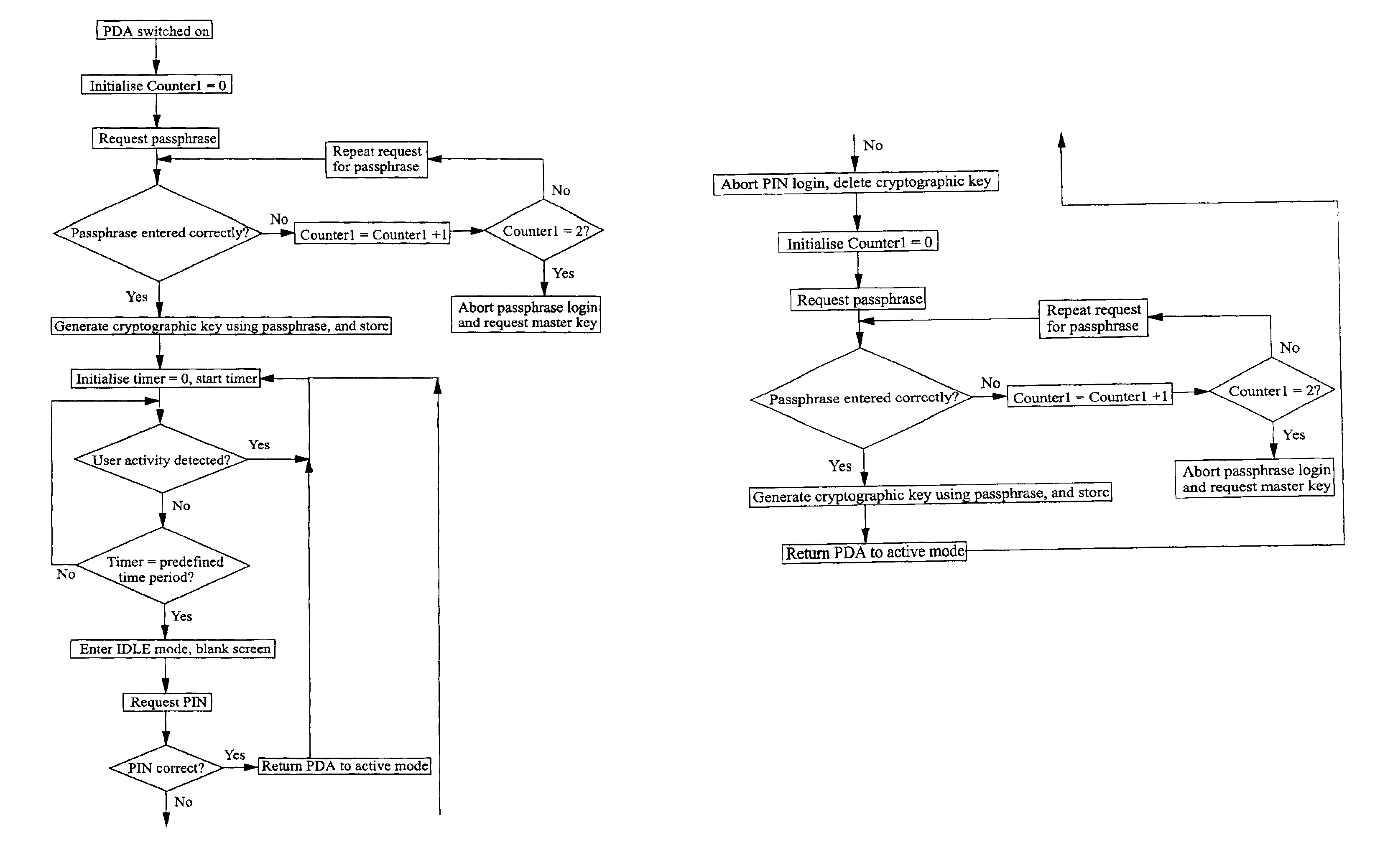
InactiveUS20030074566A1Internal/peripheral component protectionDigital data authenticationPassphrasePassword
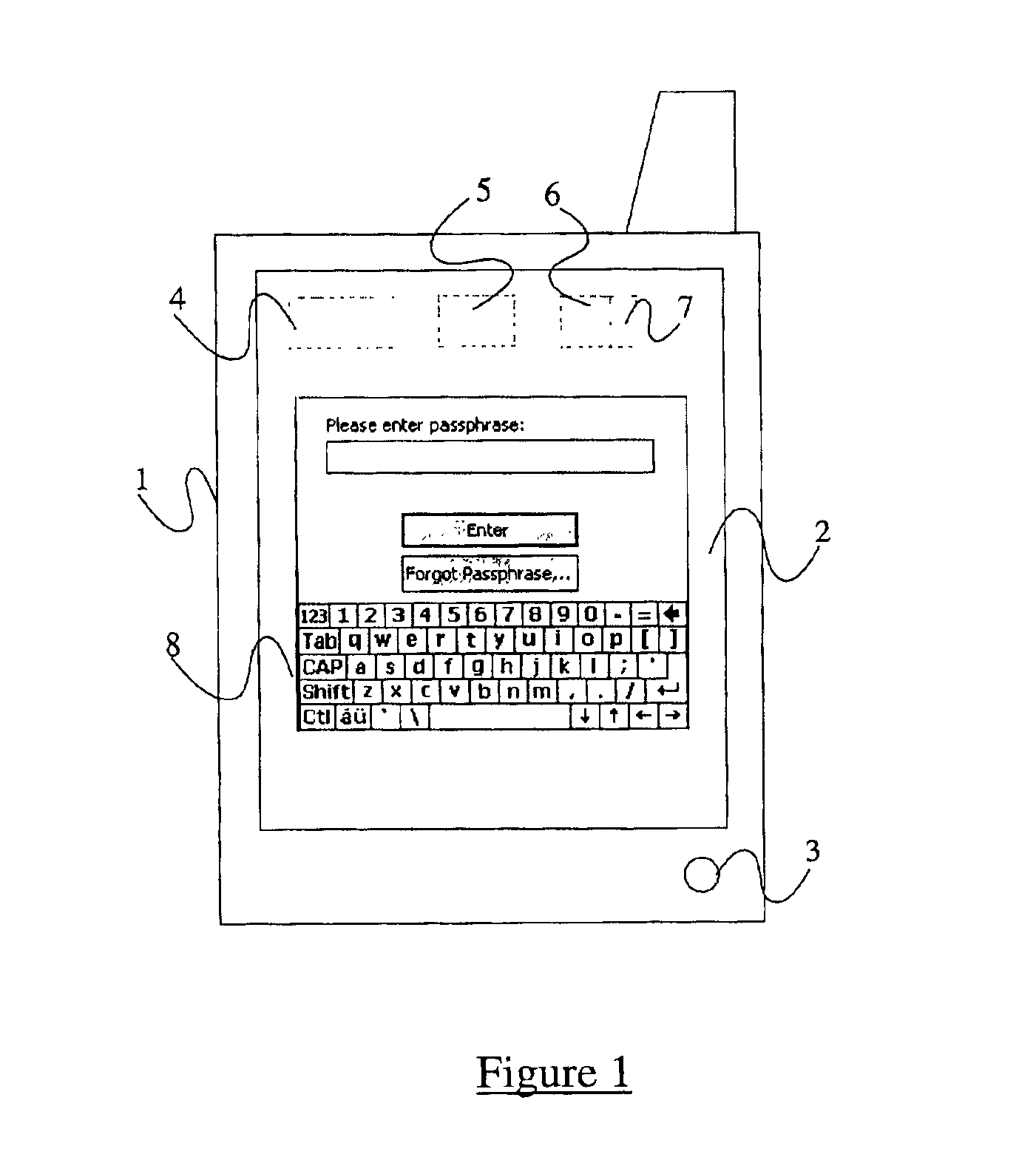
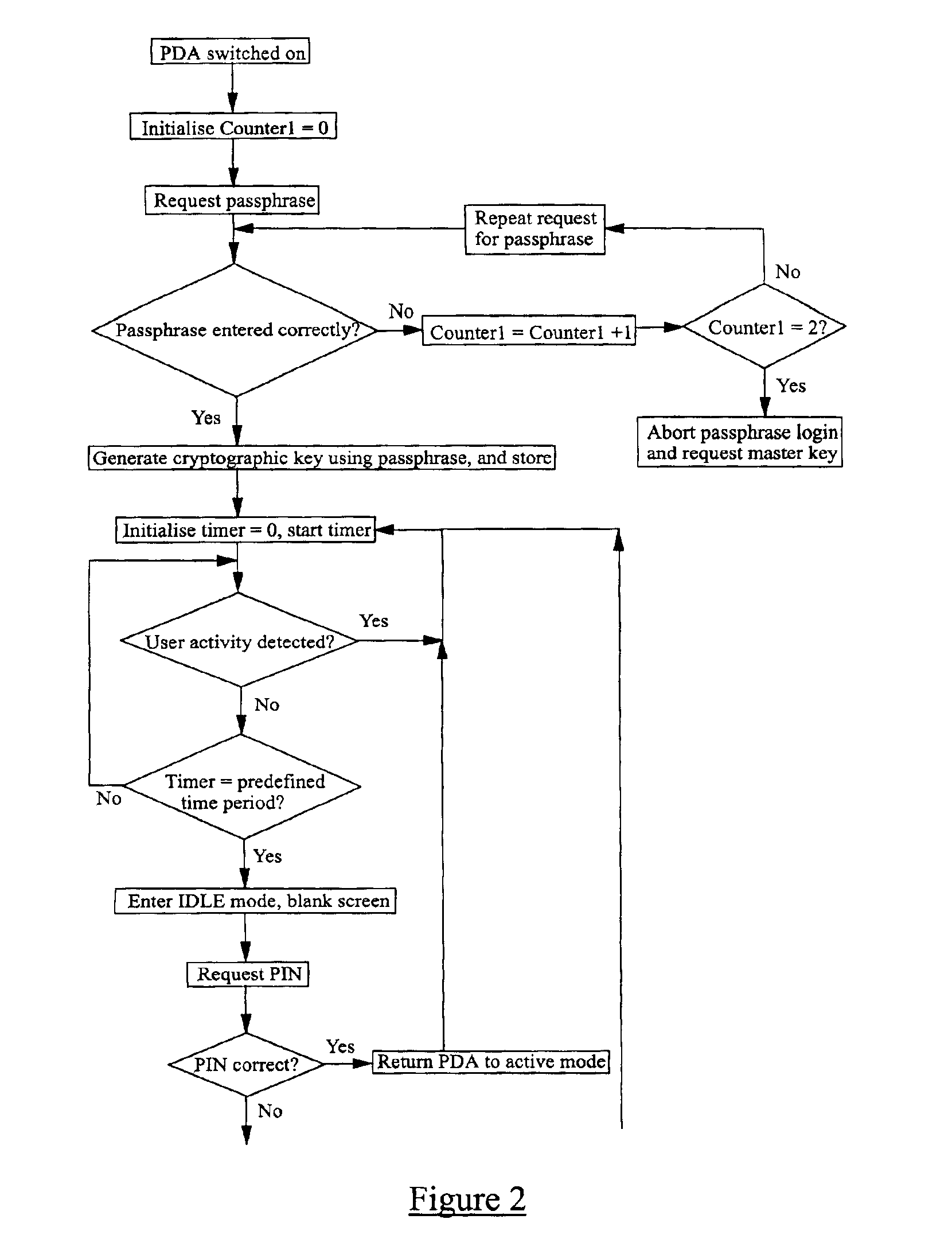
A method of securing data stored on an electronic device 1, the method comprising encrypting the data using a cryptographic key derivable from or accessed using a passphrase, requiring the entry into the device of the passphrase when a user wishes to access the data, subsequently inhibiting access to the data whilst the device 1 remains active, and requiring the entry into the device of a predefined password when a user wishes to access the data, the password being different from the passphrase.
Owner:F SECURE CORP
Computer security method and apparatus
InactiveUS6986050B2Sufficient entropyEasy and fast entryUnauthorized memory use protectionInternal/peripheral component protectionPassphrasePassword
A method of securing data stored on an electronic device 1, the method comprising encrypting the data using a cryptographic key derivable from or accessed using a passphrase, requiring the entry into the device of the passphrase when a user wishes to access the data, subsequently inhibiting access to the data whilst the device 1 remains active, and requiring the entry into the device of a predefined password when a user wishes to access the data, the password being different from the passphrase.
Owner:F SECURE CORP
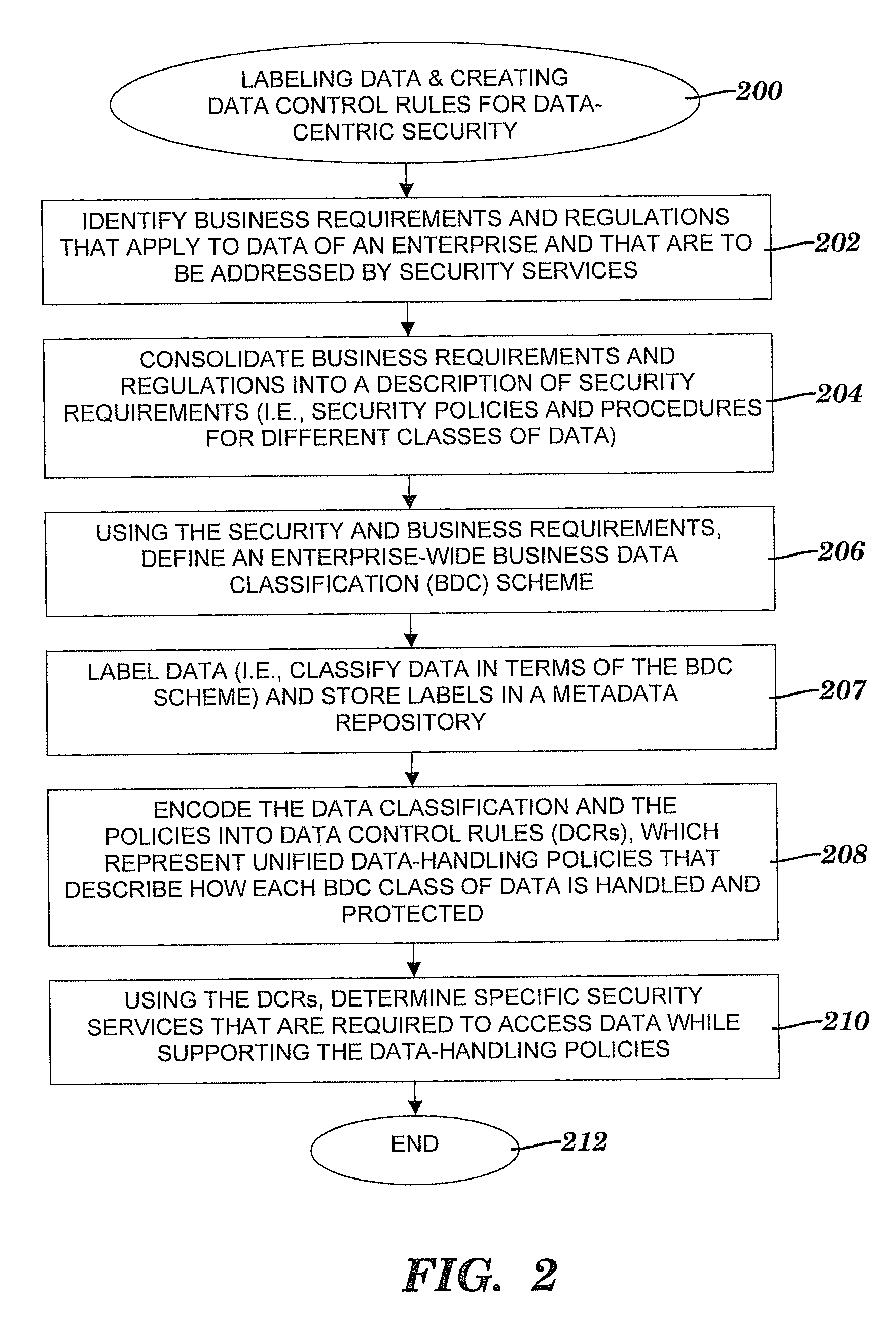
Method and system for controlling access to data via a data-centric security model
InactiveUS20090198697A1Facilitates effective collaborationLow costDigital data processing detailsComputer security arrangementsData controlMultiple attribute
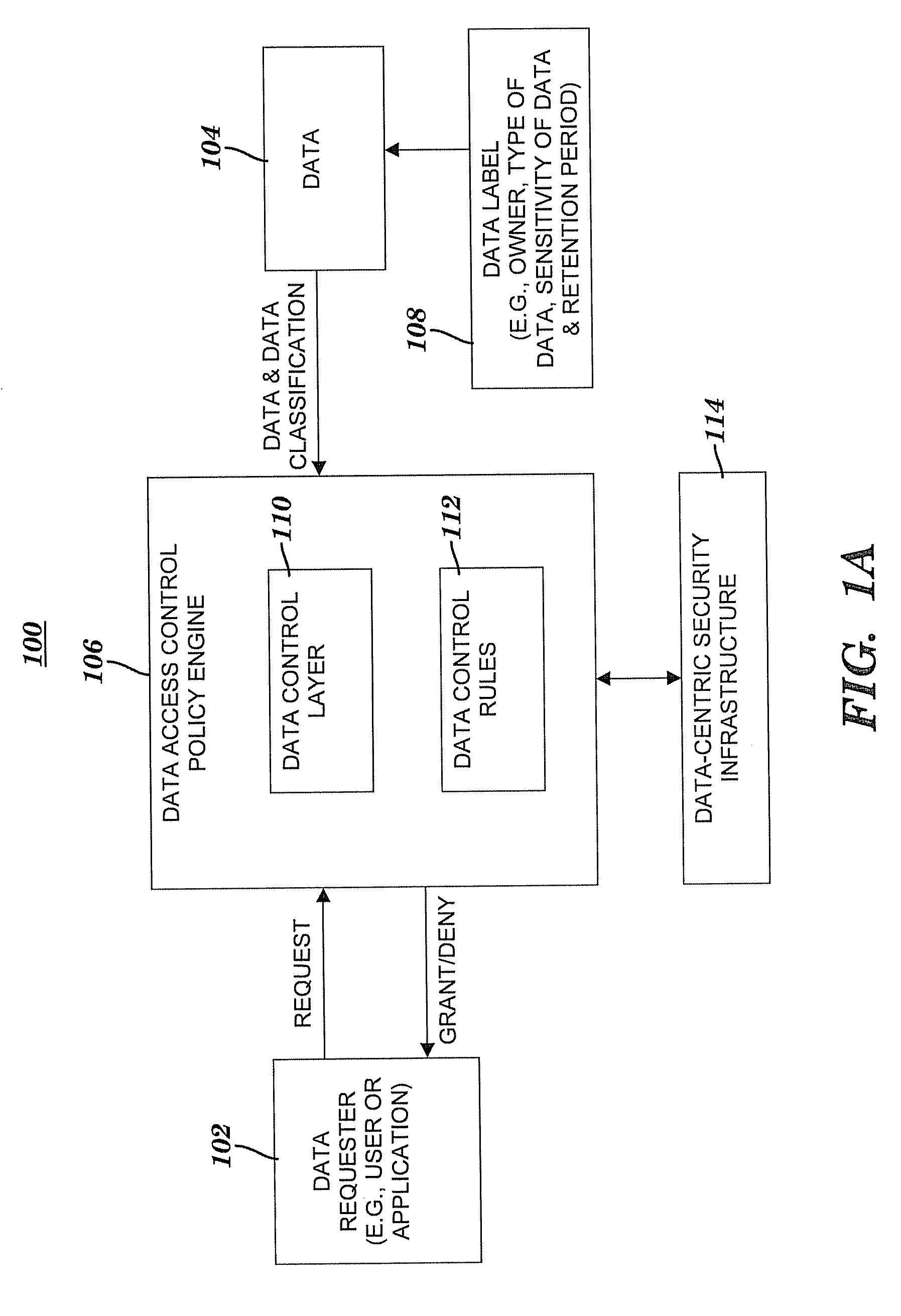
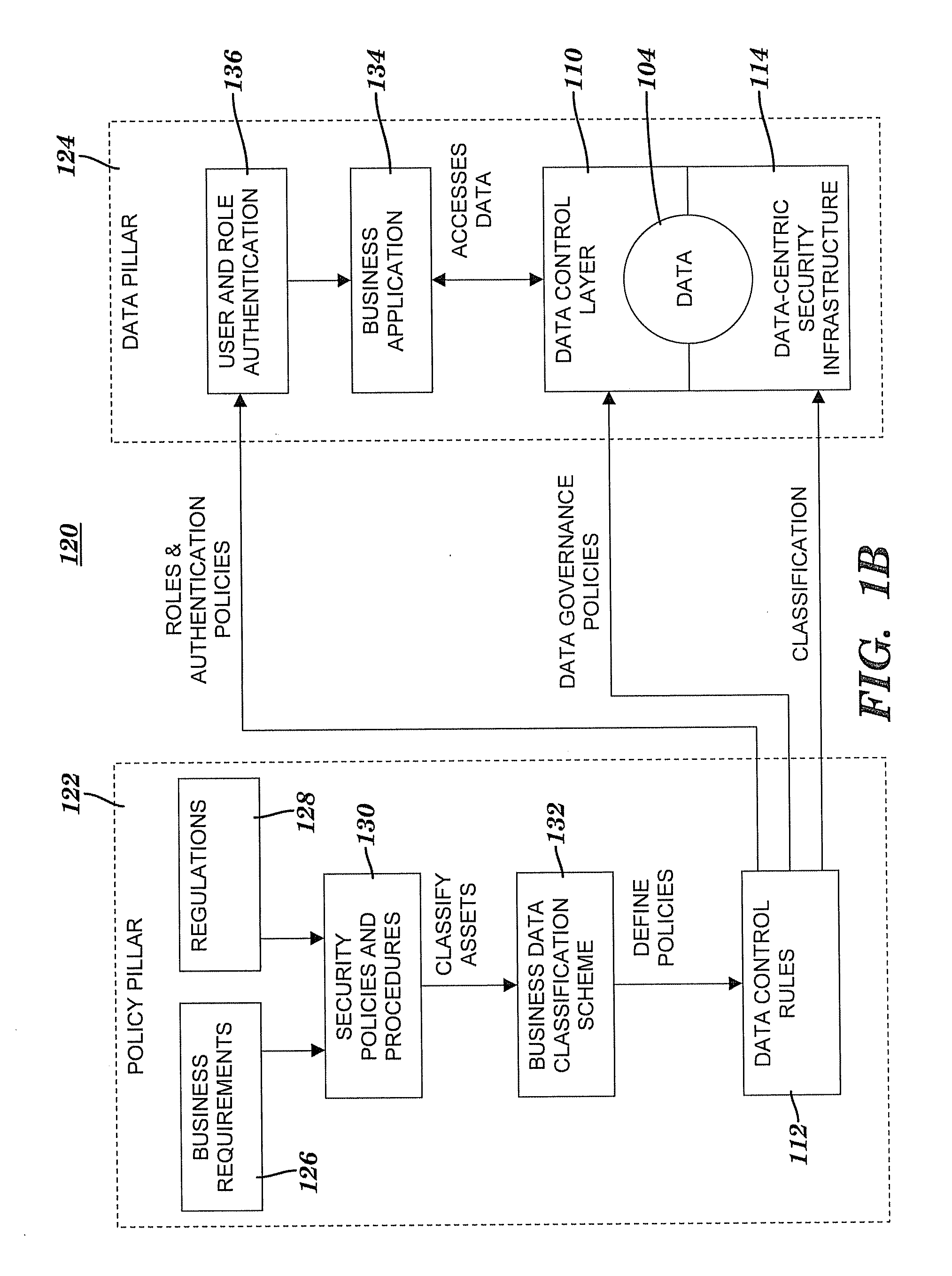
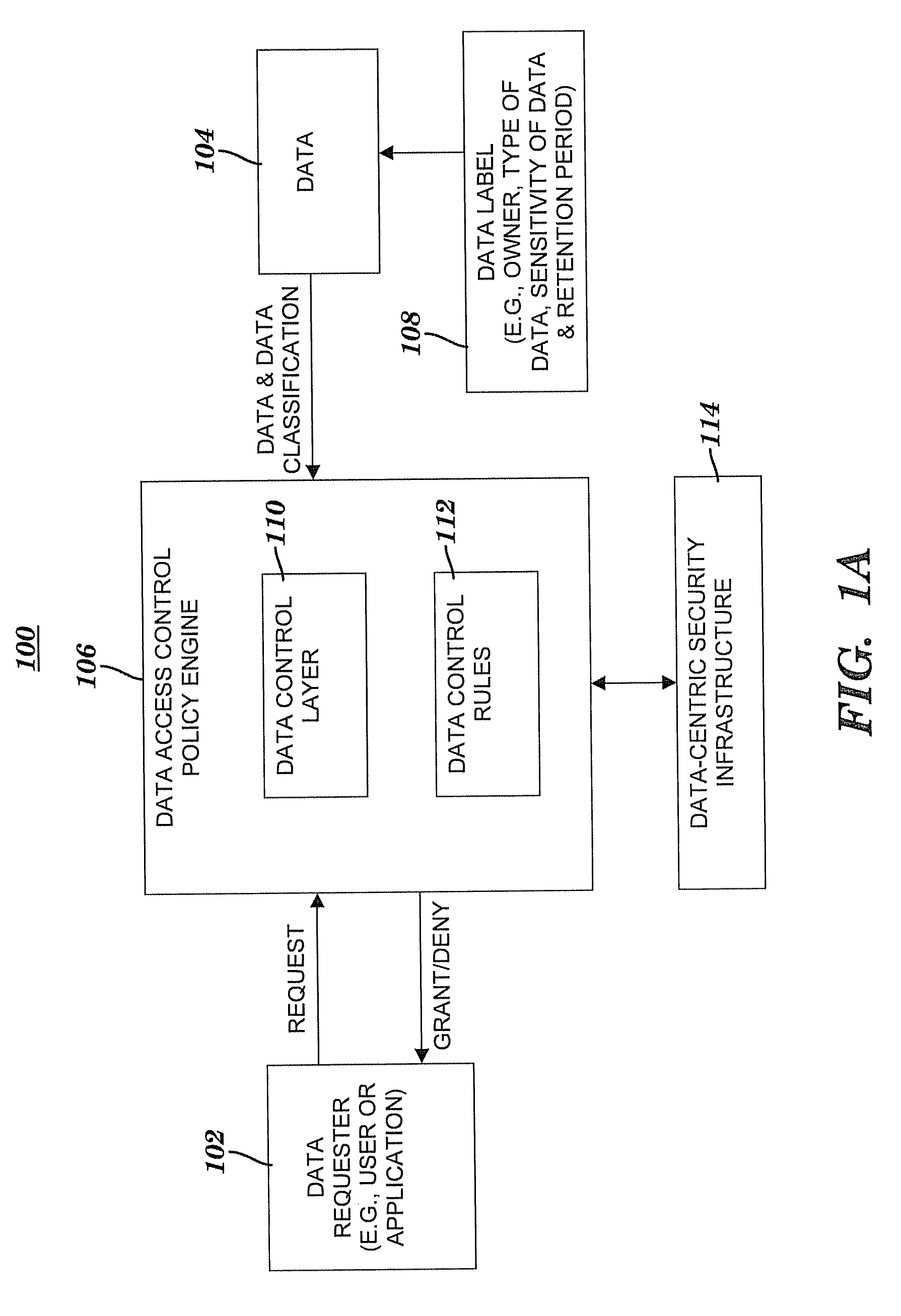
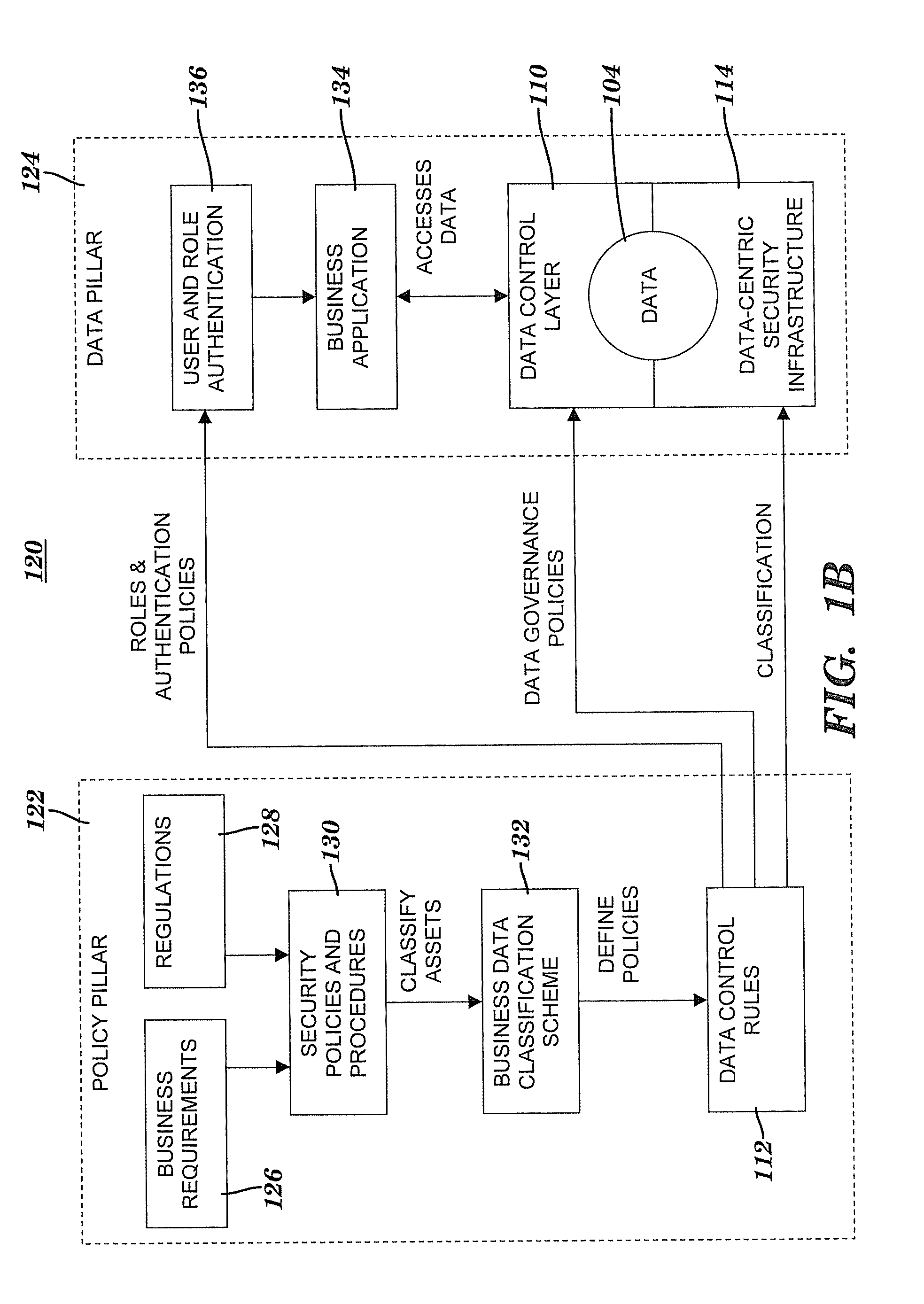
A method and system for controlling access to data via a data-centric security model. A business data classification scheme is defined as a hierarchy that includes data types aligned with business operations. A data element is labeled with a data label. The data label includes multiple attributes associated with a data-centric security model. A first attribute is a data type of the data element. A second attribute includes security requirements. Data control rules are automatically generated for an enforcement of the security requirements. The enforcement grants or denies to a user an access to the data element via a predefined action. The enforcement is based on a predefined association among the predefined action, a predefined role that includes the user, the data type and, optionally, a purpose for performing the predefined action.
Owner:IBM CORP
Computer security device
Owner:FOSTER GARY D +1
Method and system for controlling access to data via a data-centric security model
InactiveUS7890530B2Facilitates effective collaborationLow costDigital data processing detailsComputer security arrangementsData controlStructure of Management Information
A method and system for controlling access to data via a data-centric security model. A business data classification scheme is defined as a hierarchy that includes data types aligned with business operations. A data element is labeled with a data label. The data label includes multiple attributes associated with a data-centric security model. A first attribute is a data type of the data element. A second attribute includes security requirements. Data control rules are automatically generated for an enforcement of the security requirements. The enforcement grants or denies to a user an access to the data element via a predefined action. The enforcement is based on a predefined association among the predefined action, a predefined role that includes the user, the data type and, optionally, a purpose for performing the predefined action.
Owner:IBM CORP
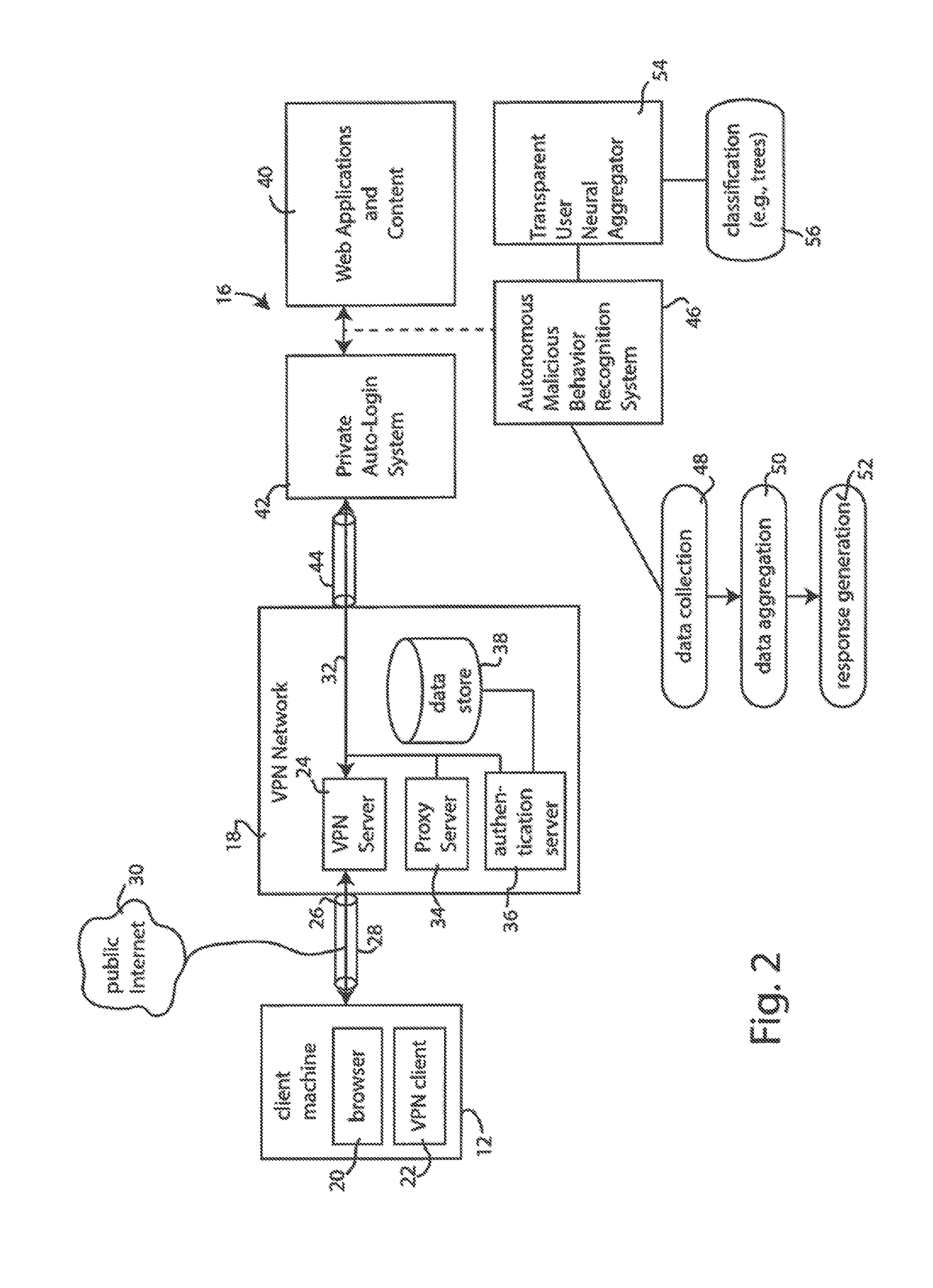
Computer security and usage-analysis system
Provided is a private and secure network that uses an authentication mechanism with a uniquely assigned private IP address and network credentials issued as part of a VPN certificate exchange. A first layer of authentication establishes a secure tunnel between user and VPN server, and a second layer of authentication connects that secure tunnel to the web site or resource, without passing the VPN certificate. Once authenticated, interaction between website or resource and user are automatically monitored for abnormal or malicious behavior and, if required, automatic verification and authentication response is generated.
Owner:ALTR SOLUTIONS INC
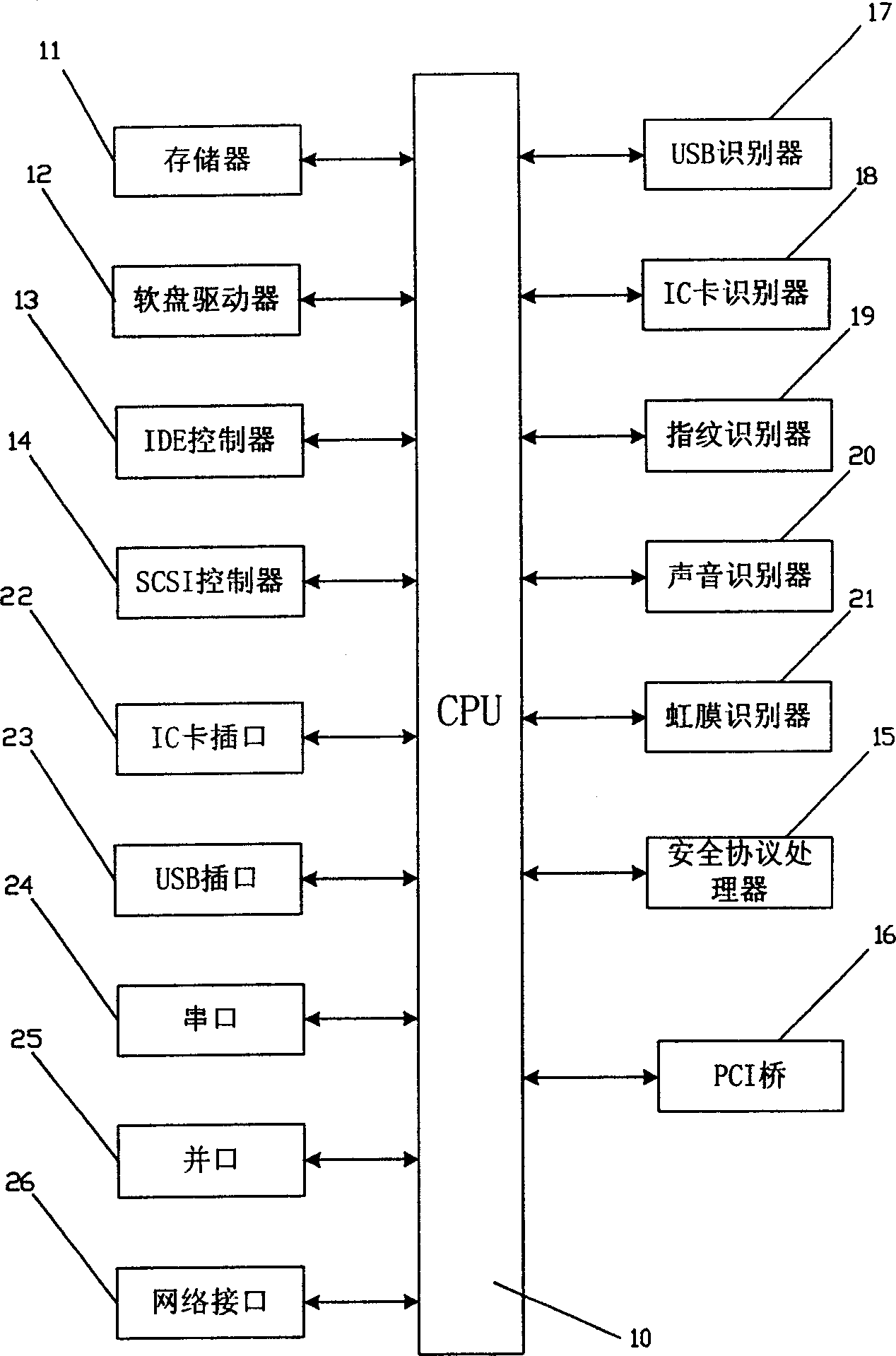
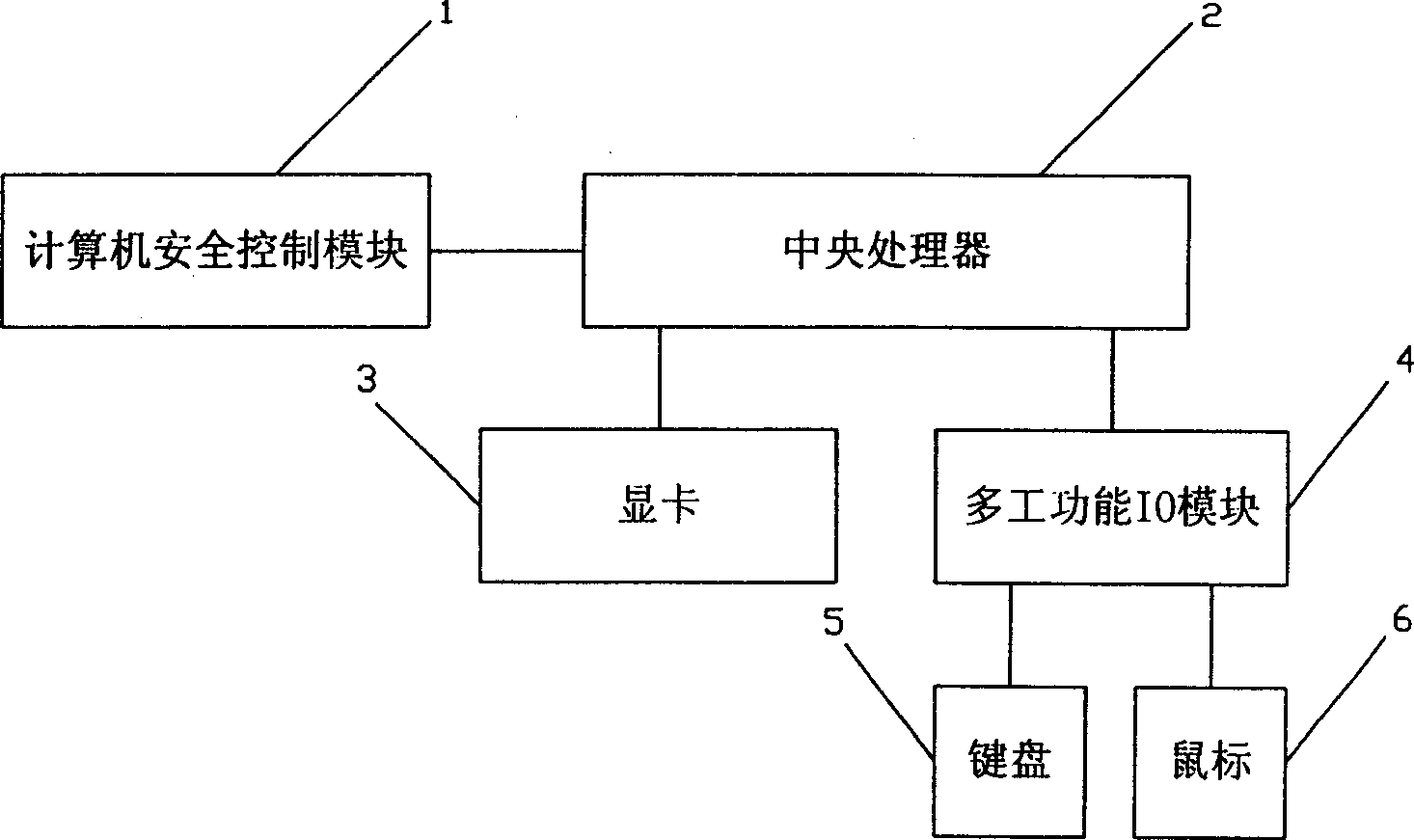
Computer security control module and safeguard control method thereof
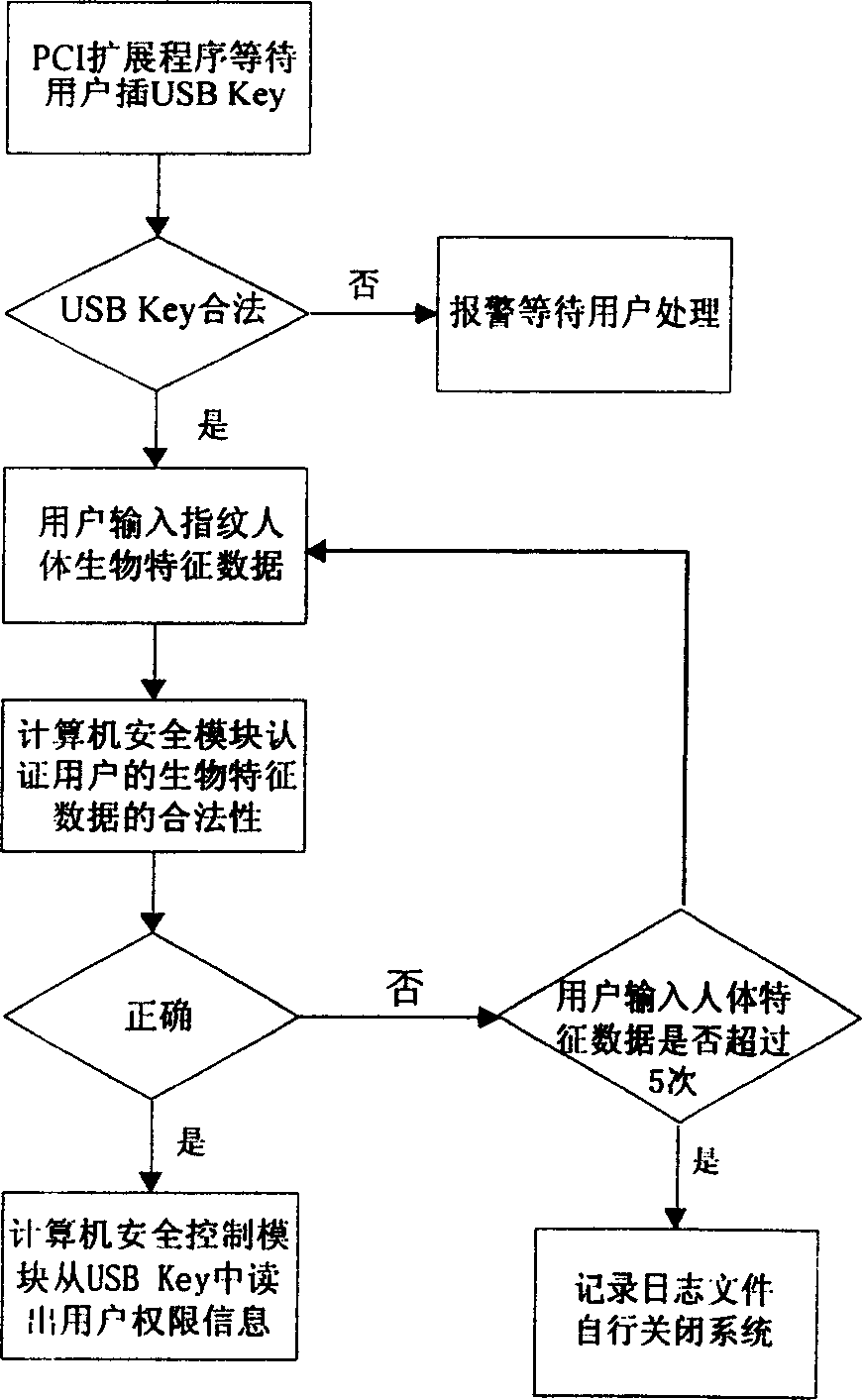
InactiveCN1621994AAddress system securityAddress network securityDigital data processing detailsProgram loading/initiatingSCSIOperational system
The computer safety control module includes CPU, memory connected to the CPU, connector, safety coprocessor, IDE controller, SCSI controller and identity authority identifier. The computer safety protecting control method includes: starting self-test with the safety module in the computer, alarming and waiting for the user to process in case of abnormality found in the self-test, and initiating BIOS program with the computer system unit to initialize the computer; calling computer safety control module PCI to expand ROM and to turn off the unsafe peripheral; performing user authority identification with the user's authority identifier; starting the hardware units based on the authority; entering the computer operation system, monitoring the system unit state and reporting regularly to the safety control module with the background monitoring program, and performing safety processing with the safety control module in case of illegal operation, etc.
Owner:北京太极英泰信息科技有限公司 +1
Automated Method for Self-Sustaining Computer Security
InactiveUS20060259819A1Improve user securityImprove efficiencyError detection/correctionPlatform integrity maintainanceAnti virusComputer security model
Owner:CONNOR MATTHEW A
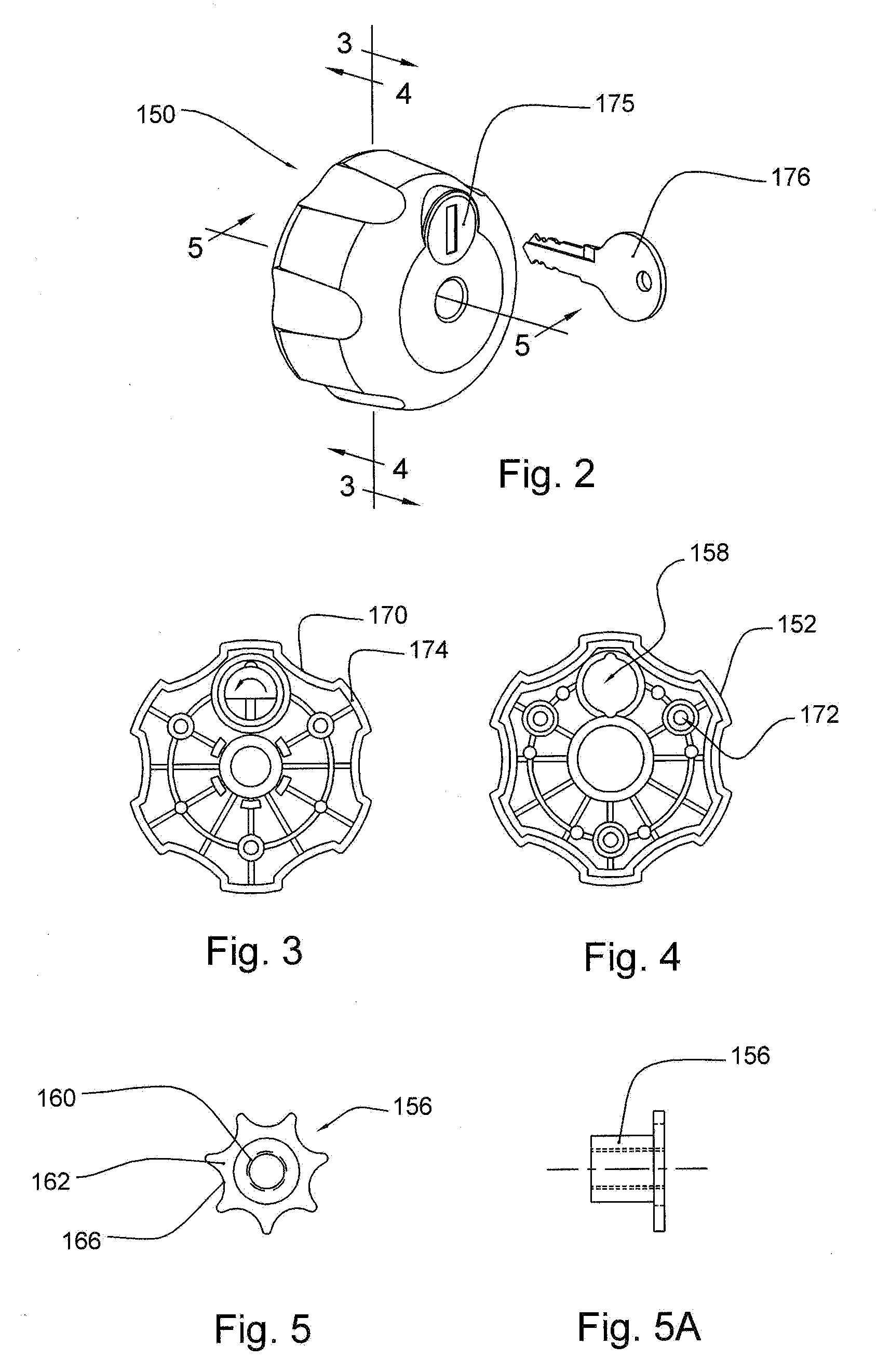
Computer security locks having separate key pairs
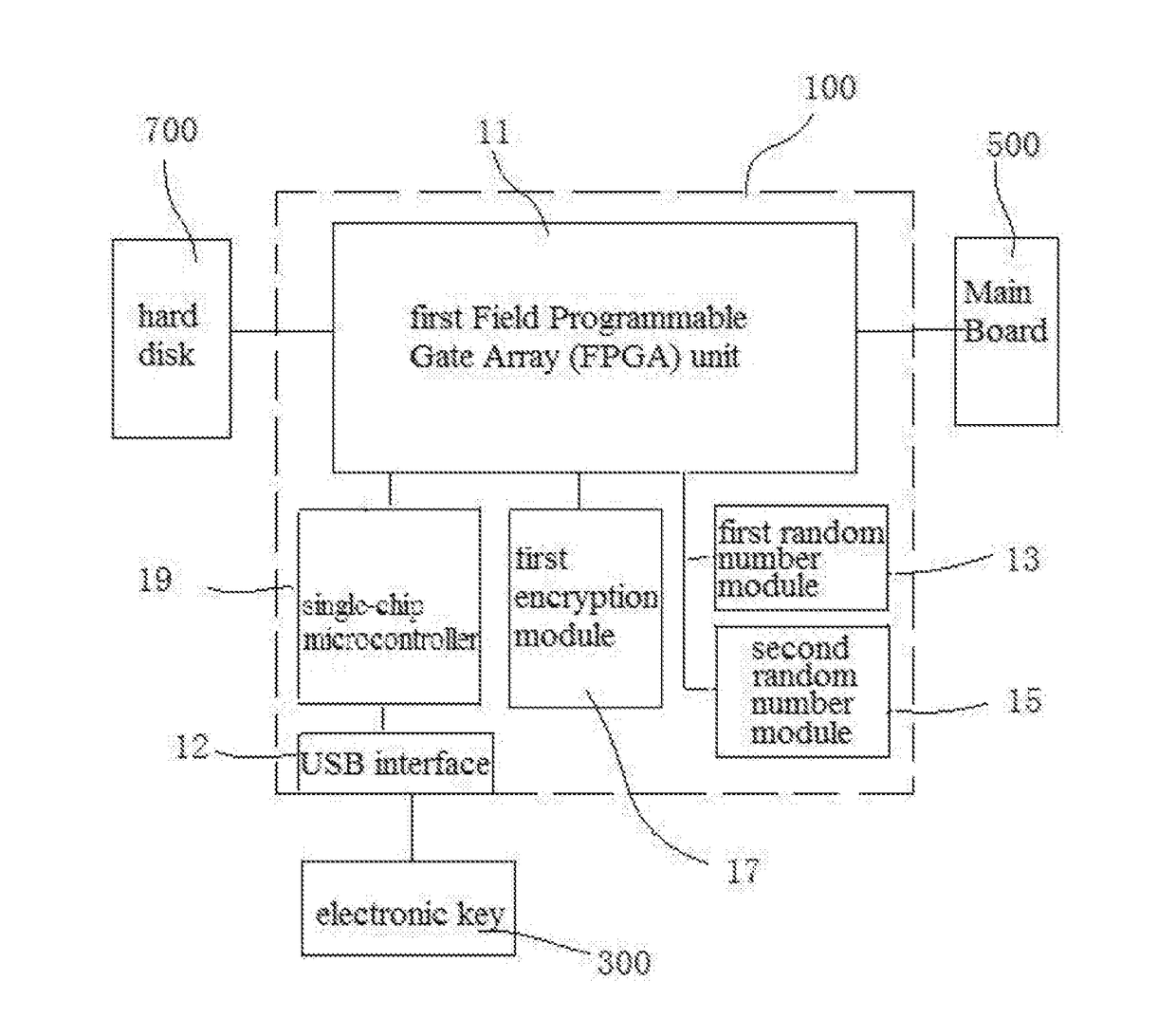
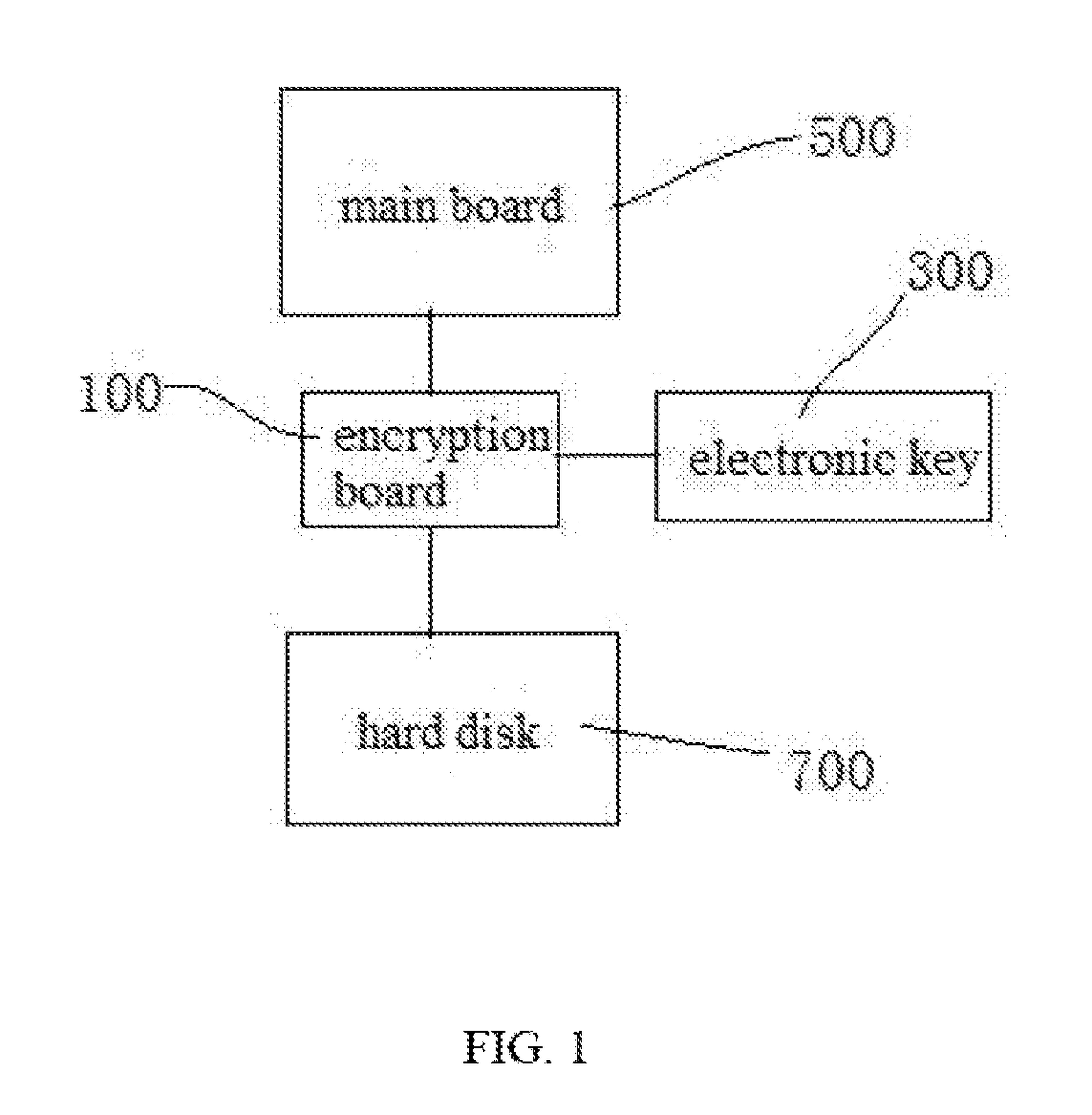
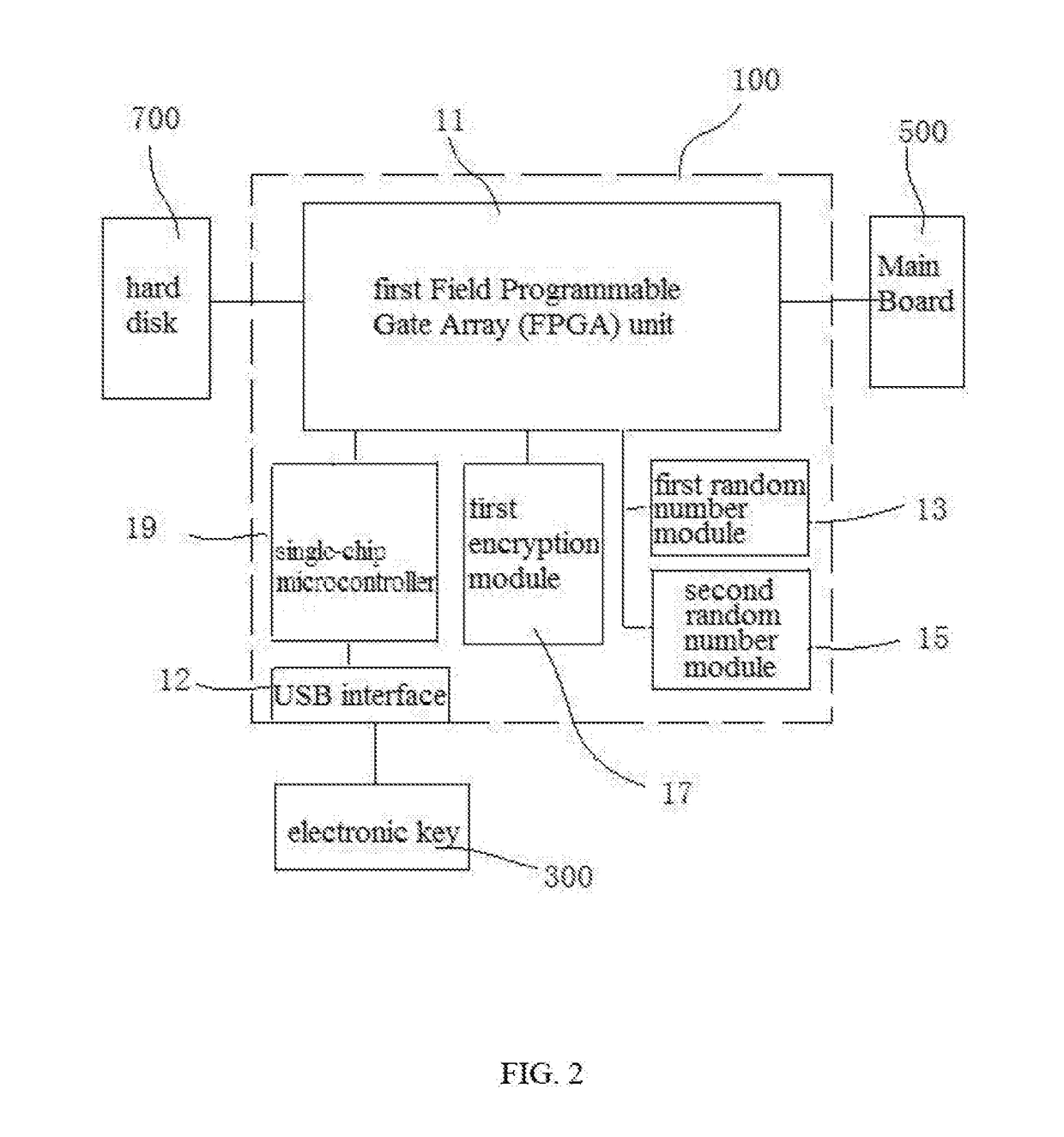
ActiveUS20170373851A1SpeedKeep data safeMultiple keys/algorithms usagePublic key for secure communicationComputer security modelDisk partitioning
A computer security lock having separate key pairs includes an encryption board inserted between a main board and a hard disk, and an encryption board being inserted into the encryption board to perform a real-time authentication process. The electronic key and the encryption board performs the real-time authentication process and hardware anti-copy self-testing process, and encrypt the data communicated between the encryption board and the electronic key. After passing the authentication process and the hardware anti-copy self-testing process, the electronic key combines an internally stored key list with the key list on the encryption board, and selects a user key to encrypt / decrypt the data on the disk according to the partition of the hard disk where the encrypted data is written to. The computer security lock can assure the safety of the data, and the hardware is prevented from being copied.
Owner:CHINA ZHENHUA GRP SCI & TECH +1
Computer security method and computer system
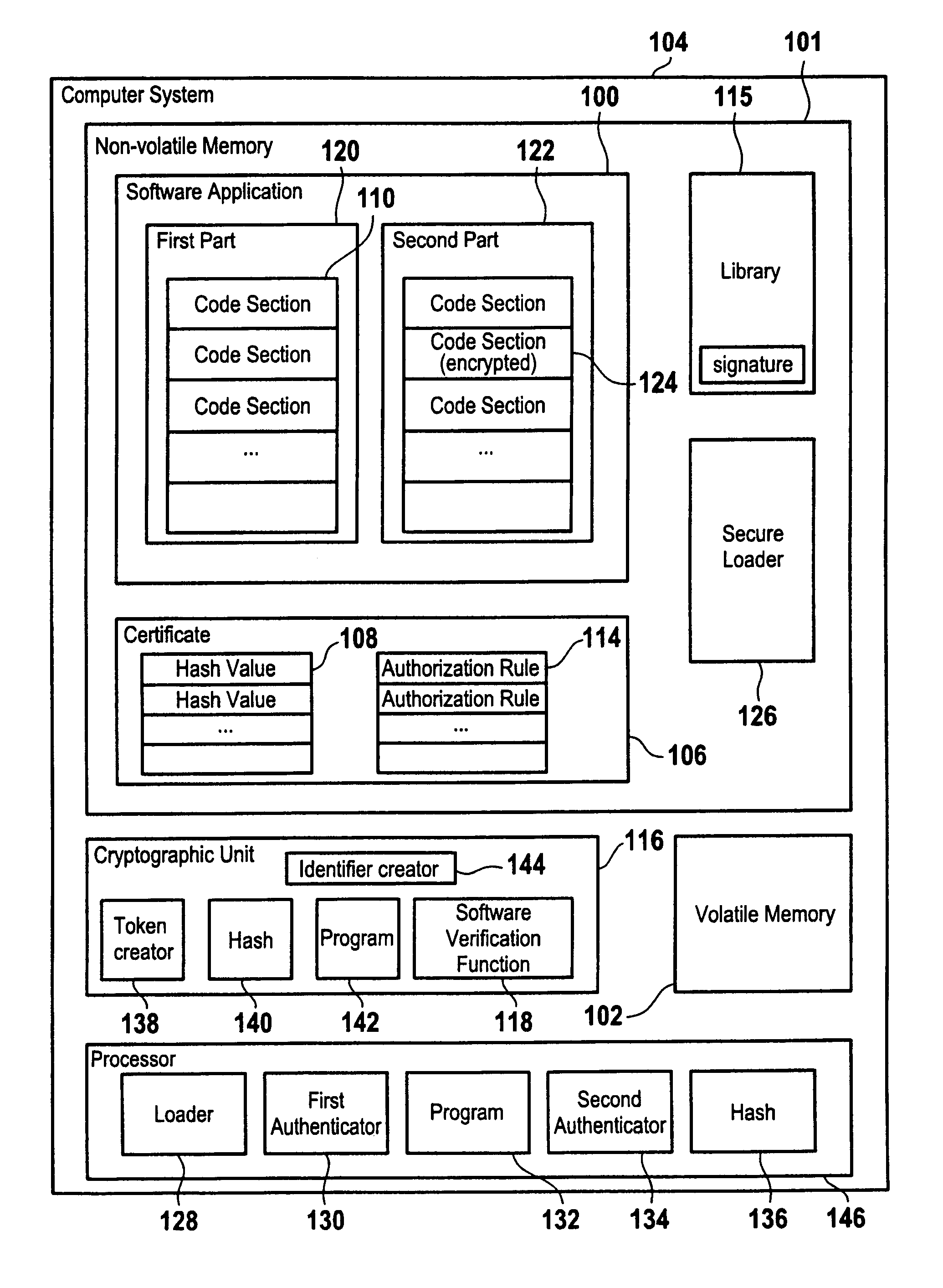
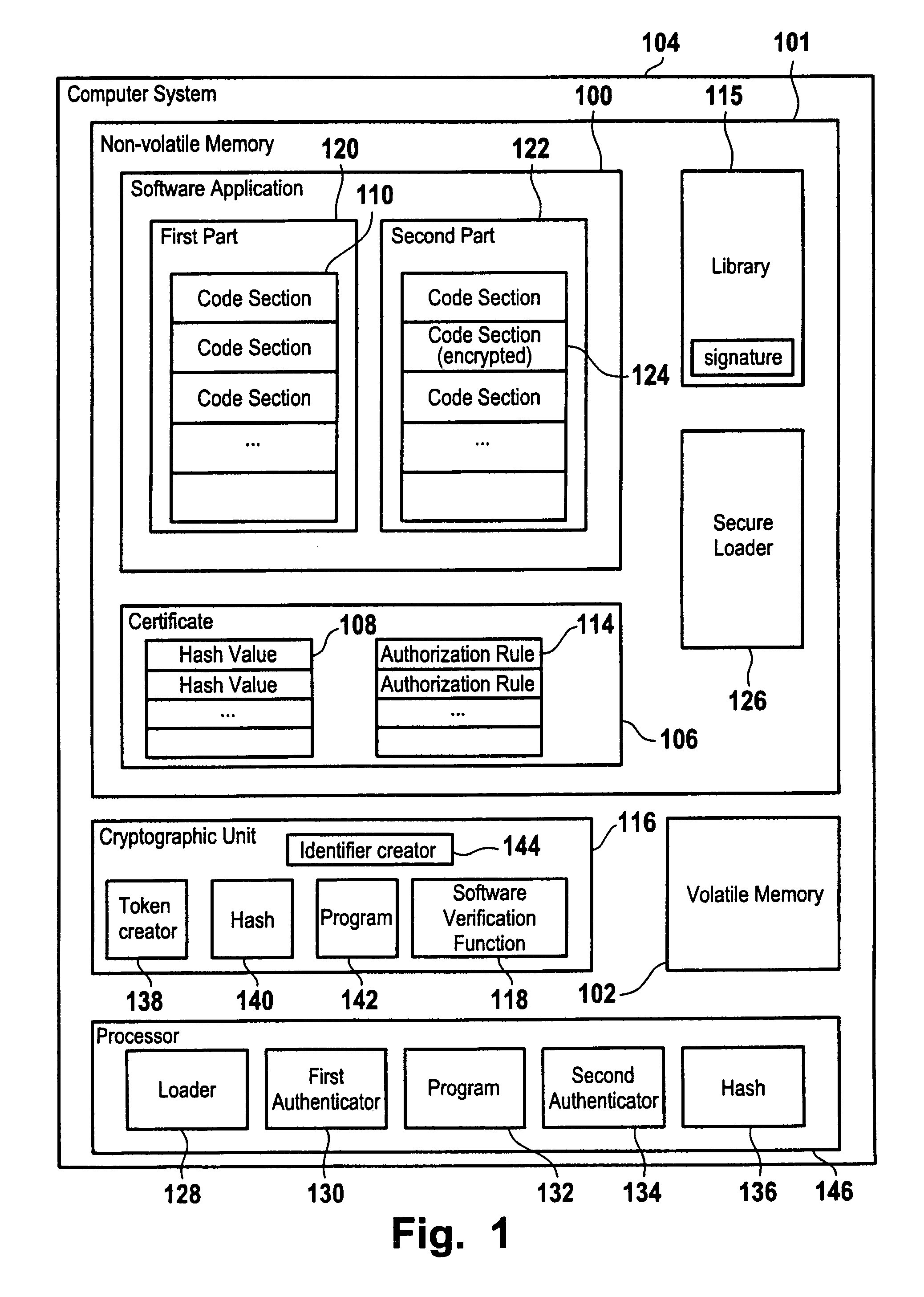
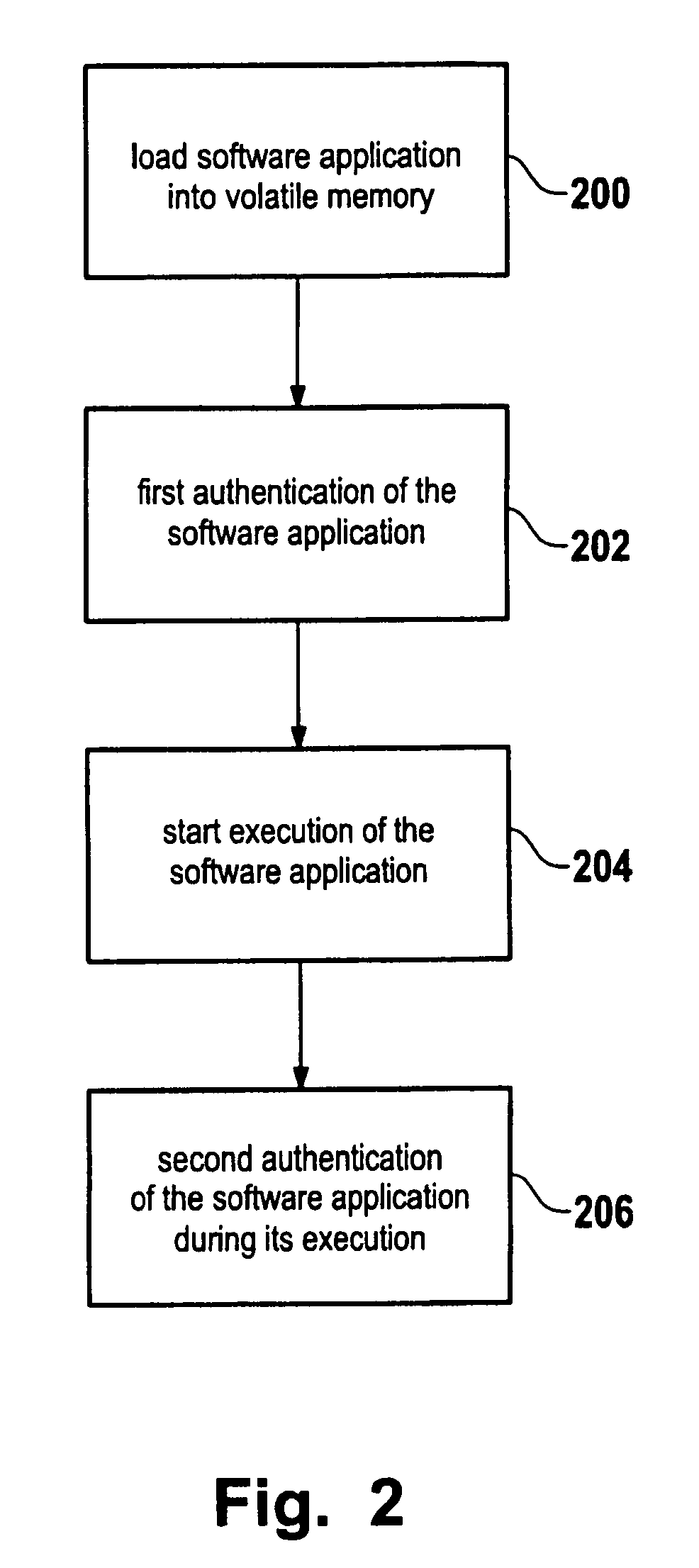
ActiveUS8051299B2Ensure integrityExecution of applicationUnauthorized memory use protectionHardware monitoringComputerized systemComputer security model
A method for secure loading, integrity checking of the runtime image and control over the runtime execution of applications which ensures that a software application loads only code it was authorized to load, and that the software application is monitored for unauthorized modifications of the runtime image. The method proposed can be used as a basis for further enforcing of authorization rules during the execution of an application, e.g. for Digital Rights Management.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
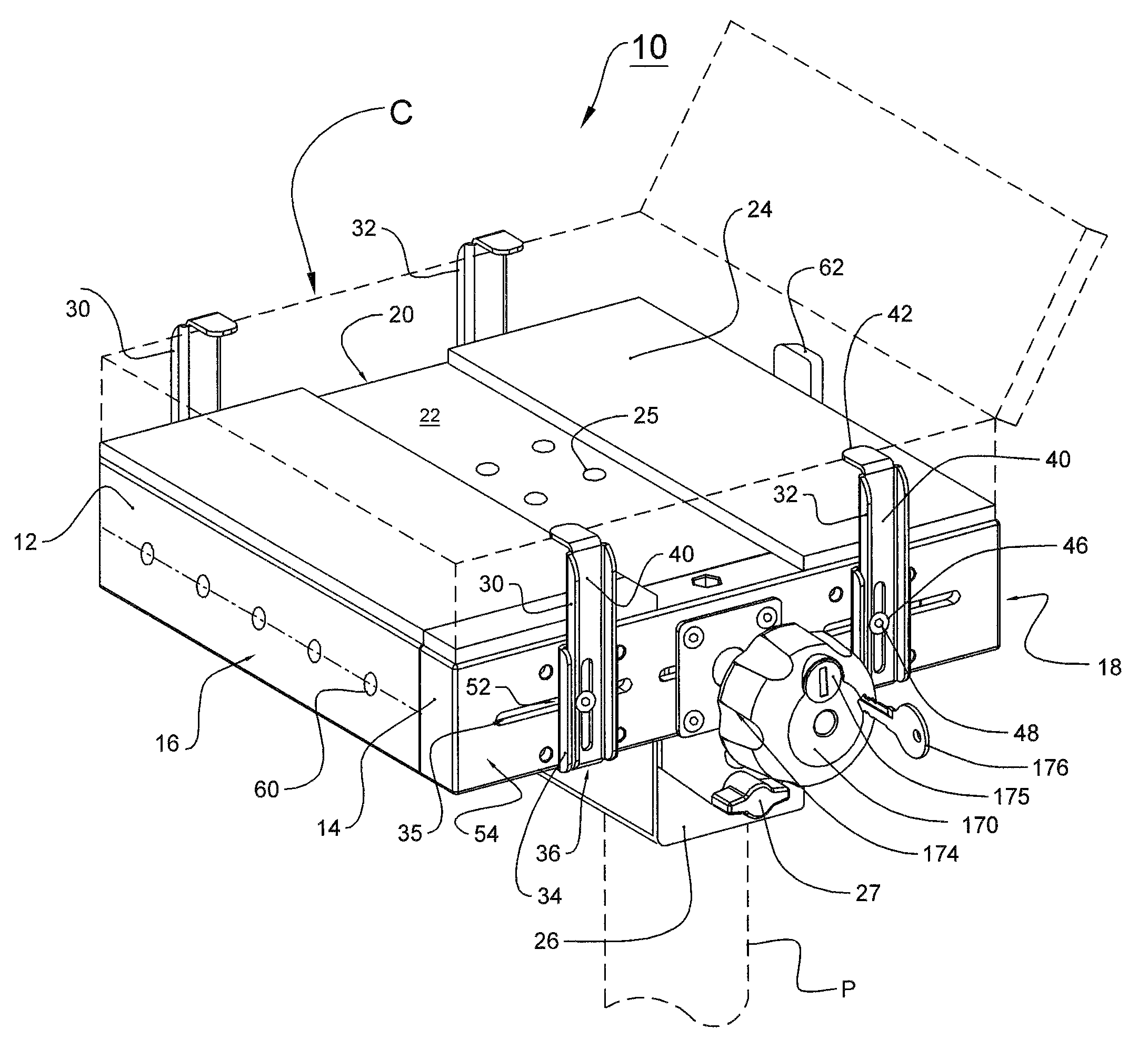
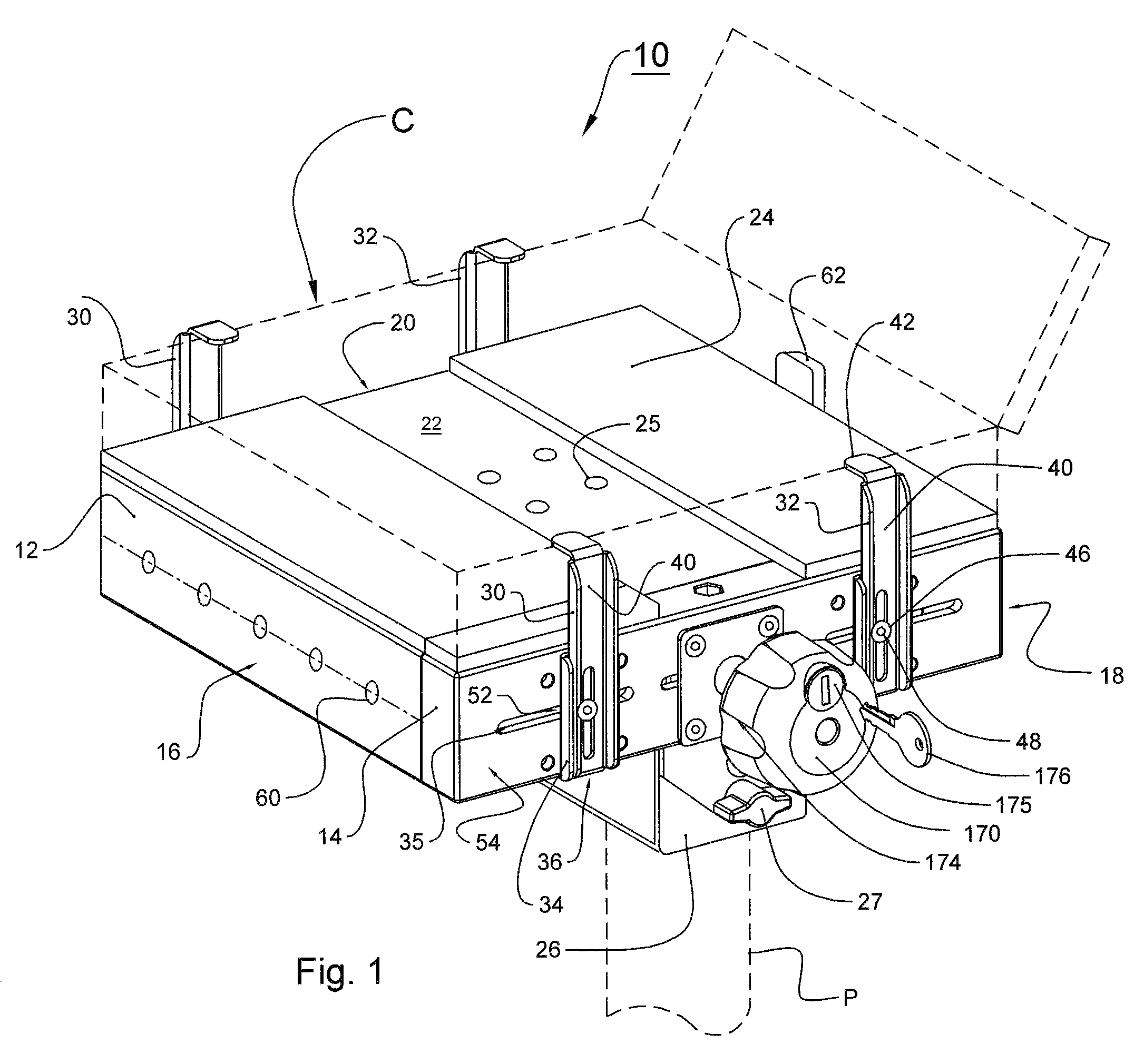
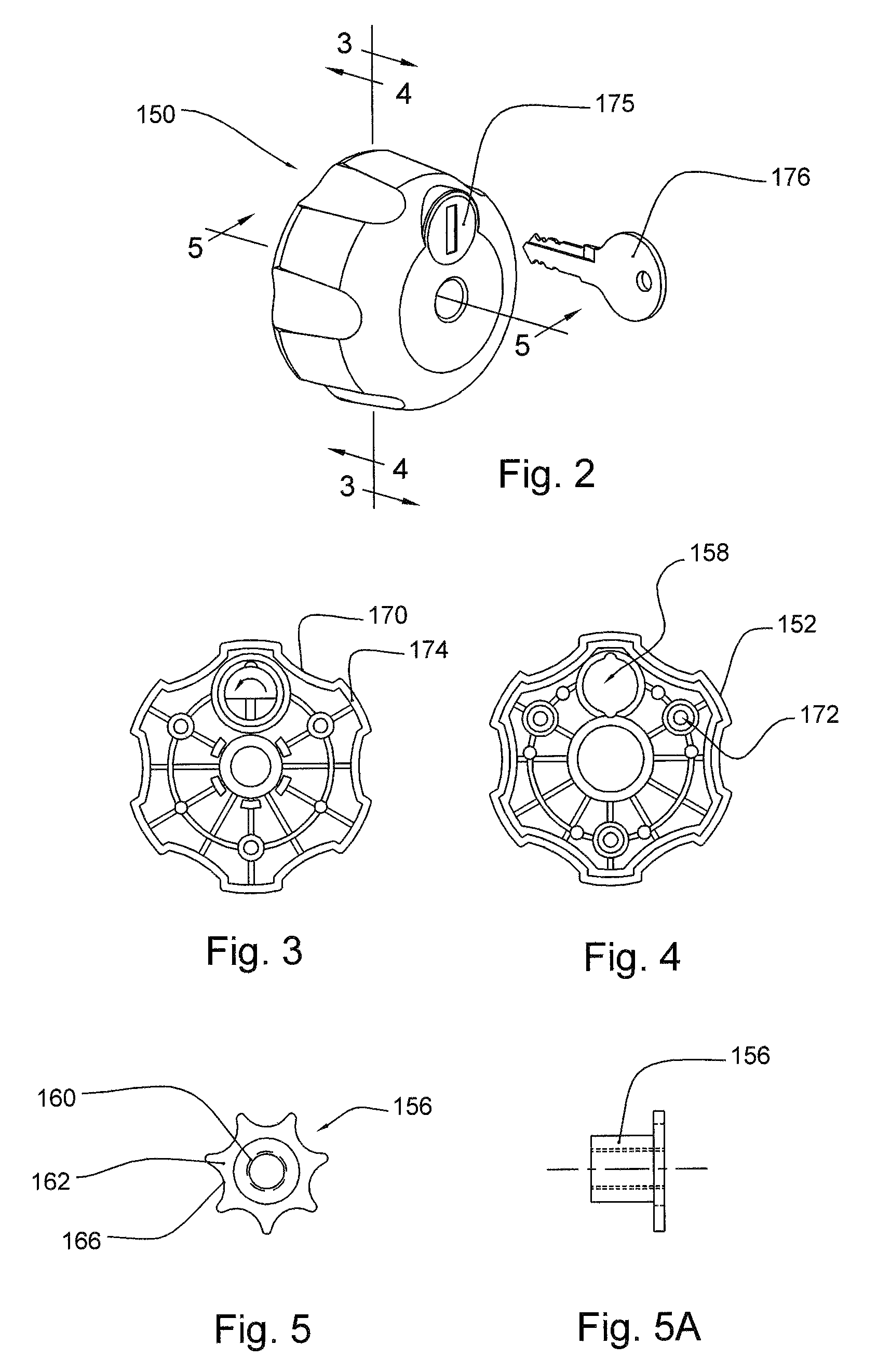
Computer security device
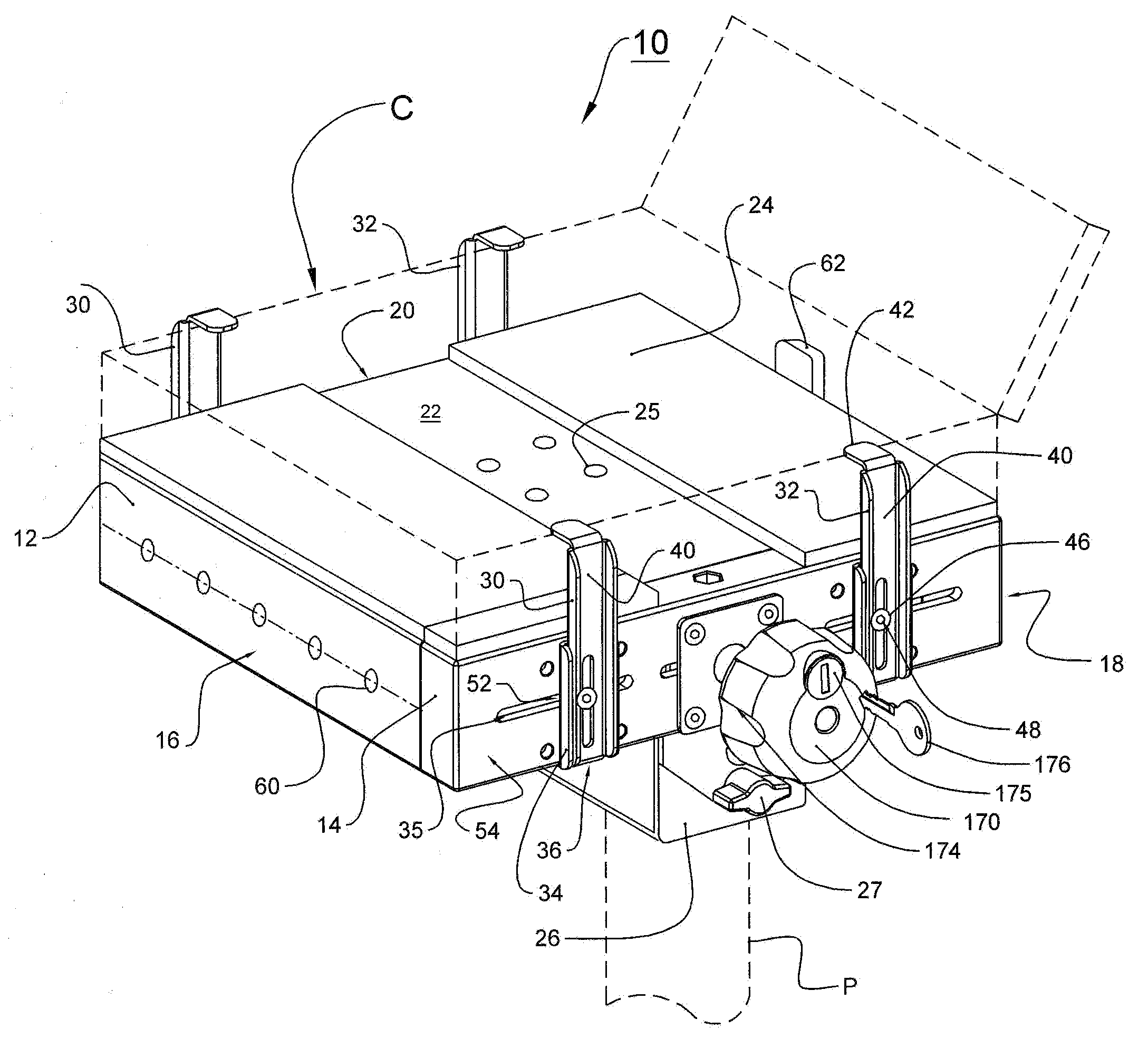
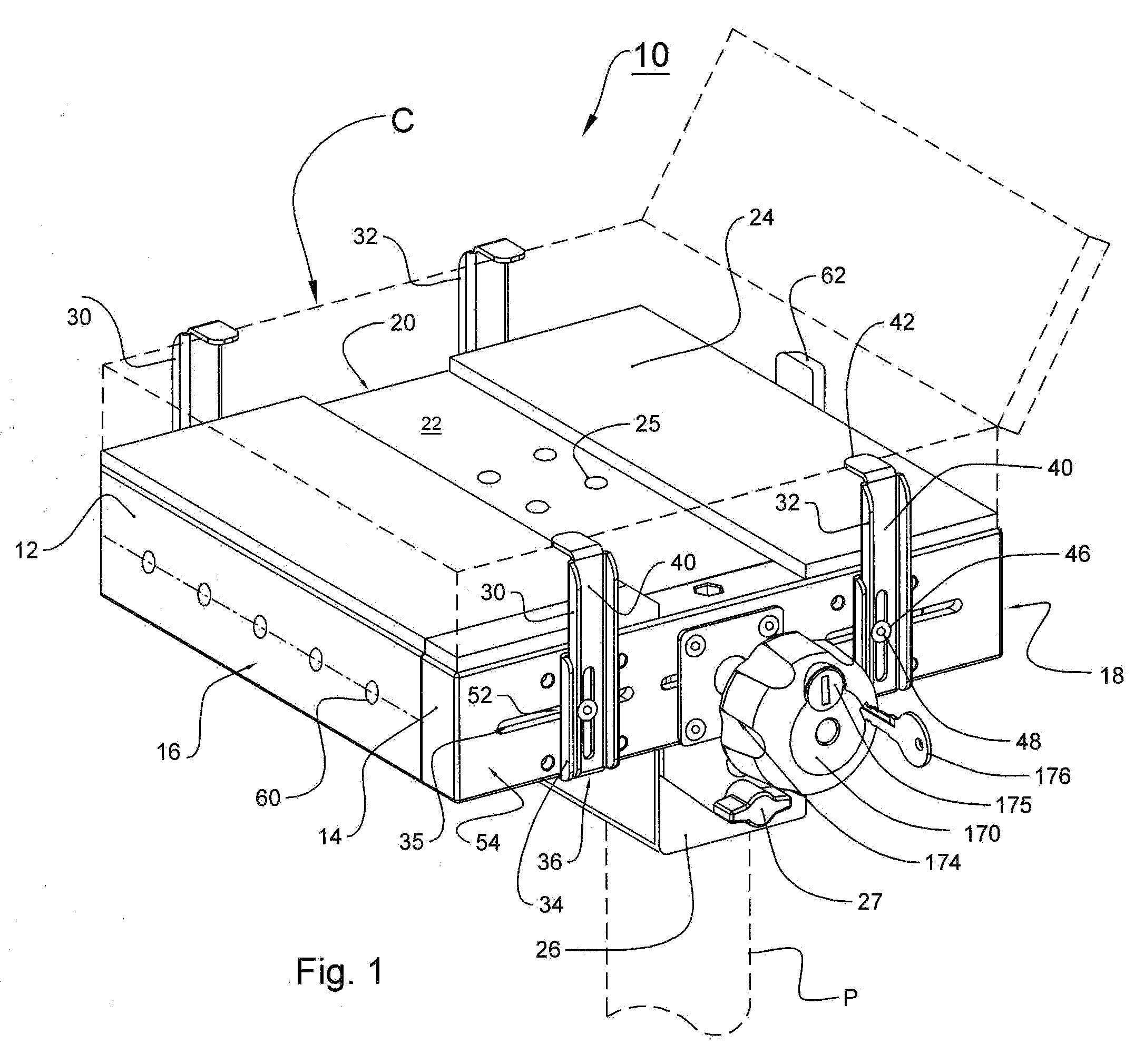
InactiveUS20100326144A1Prevent movementClothing locksLocks for portable objectsComputer security modelMechanical engineering
A security device to secure a computer may include a substantially vertical pedestal, a fixed platform mounted on the pedestal, a clamping table to cooperate with the fixed platform to secure the computer and a locking assembly to allow the clamping table to be moved to allow the computer to be attached and released from the fixed platform in an unlocked state and to prevent the clamping table from being moved to hold the computer in a locked state, The locking assembly may include a locking knob to operate the locking assembly between the locked state and the unlocked state, and the locking knob may rotate freely in the locked state and rotates to allow the clamping table to be moved in the unlocked state.
Owner:FOSTER GARY D +1
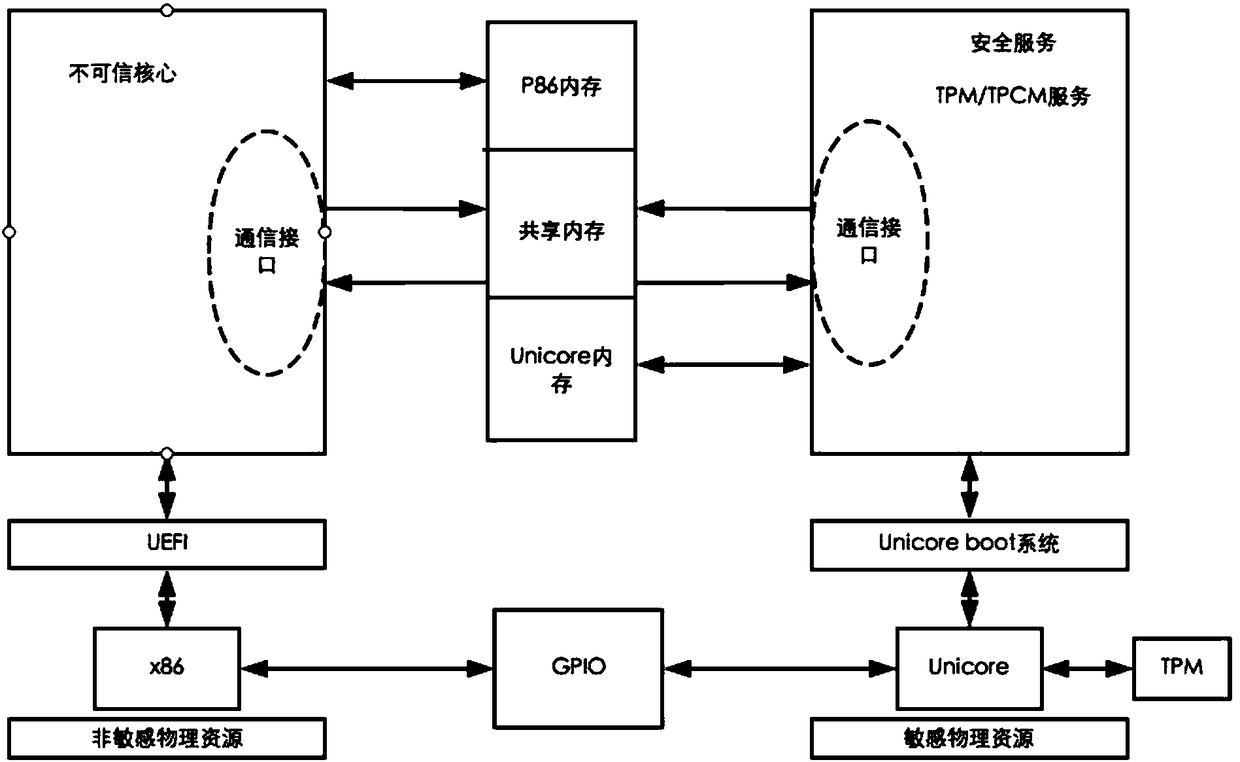
Computer security starting method based on heterogeneous multi-core chip
InactiveCN108460282ASecure BootPlatform integrity maintainanceIntellectual propertyComputer security model
The invention discloses a computer security starting method based on a heterogeneous multi-core chip. The method includes: using at least one trusted core on the basis of a heterogeneous multi-core platform to ensure security of an untrusted core. The trusted core is used as a monitoring core, and the untrusted core is used as a computing core; the trusted core and the untrusted core are heterogeneous, and a CPU core with independent intellectual property is a first choice of the trusted core. The trusted core and the untrusted core are isolated by hardware, and sensitive hardware resources are collected to the trusted core. The trusted core is communicated with the untrusted core through cooperation of shared memory and inter-core interruption. The trusted core is guided by adopting a self-developed system, and provides security services outwards, and the untrusted core is guided by adopting a UEFI (Unified Extensible Firmware Interface) system. A core of the method is to ensure the security of the untrusted core on the basis of the heterogeneous multi-core platform through the trusted core. Realization of the method is not limited by specific platforms and starting manners, and the method can be applied simply with the need for satisfying basic requirements.
Owner:PEKING UNIV
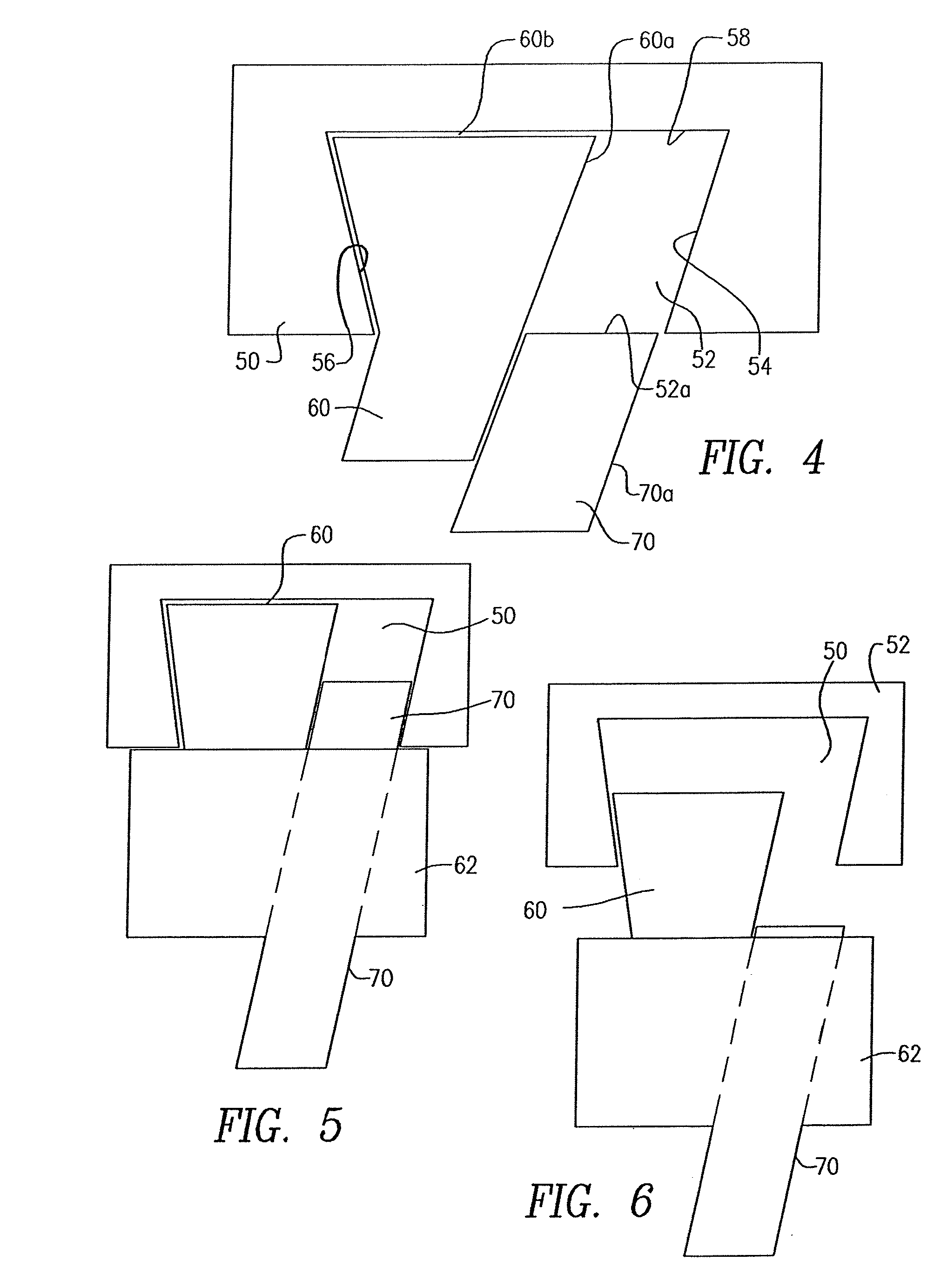
Computer security lock for trapezoidal security slot
ActiveUS9137911B2Digital data processing detailsLocks for portable objectsLocking mechanismComputer security model
A lock that is configured to be attached to electronic equipment requiring securing against theft and the lock comprising: a lock body; a locking element protruding from the lock body and having a forward distal section that is comparatively wider in cross-sectional size compared to a rear section thereof, the forward section being configured to be insertable into a cavity formed in the equipment, where the cavity is defined by an opening having a size and shape slightly larger than the cross-sectional size of the forward section of the locking element and an interior larger in cross-sectional size than the opening of the cavity; a slidable locking pin configured to slide alongside the locking element and into the cavity, after the locking element has been inserted into said cavity, to substantially fill a space of the cavity left unoccupied by the locking element; a sliding mechanism coupled to the locking pin and configured to slide the locking pin into and out of the cavity; and a locking mechanism to lock the locking mechanism within the lock body to prevent withdrawal of the locking element from the cavity.
Owner:AVGANIM MEIR
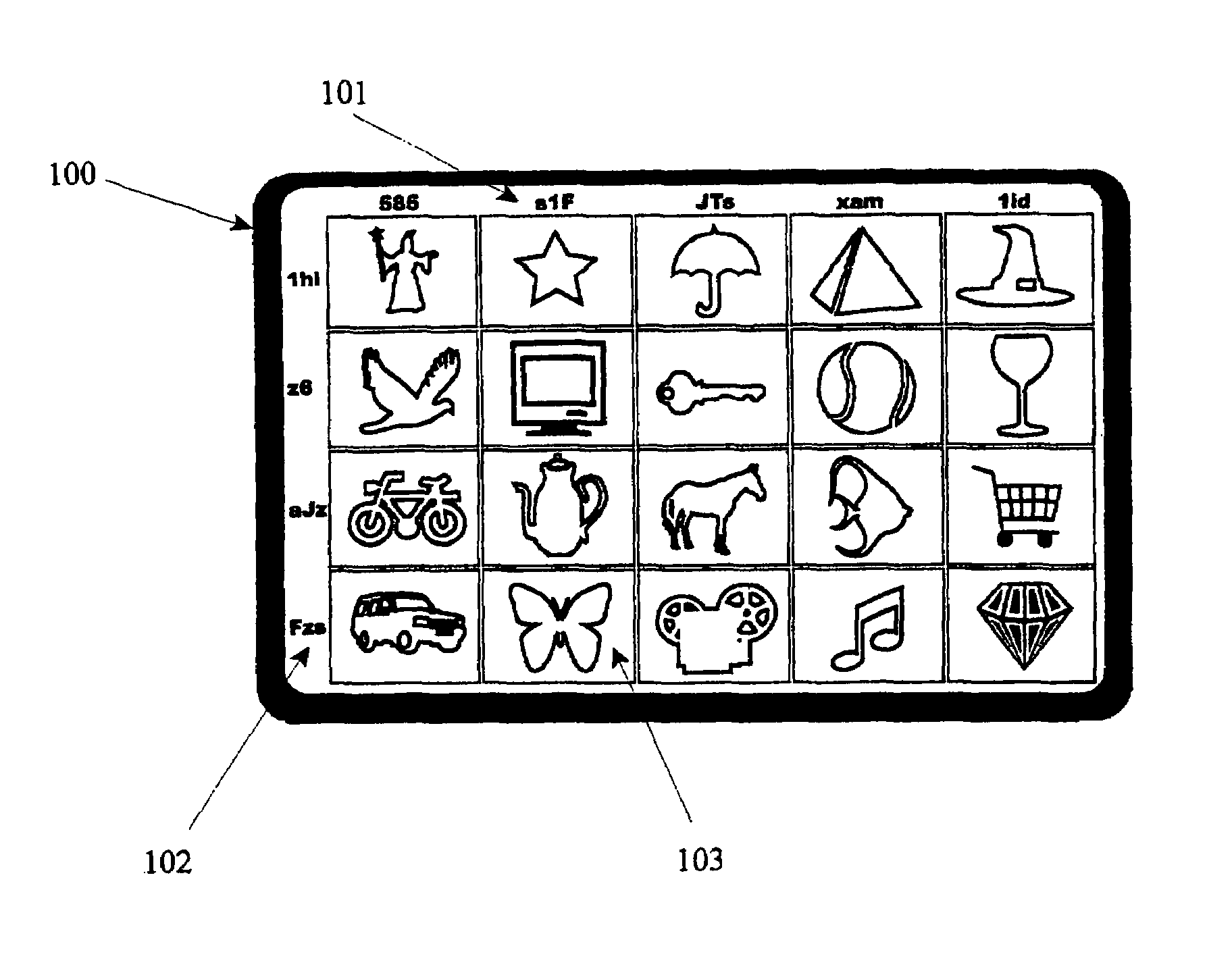
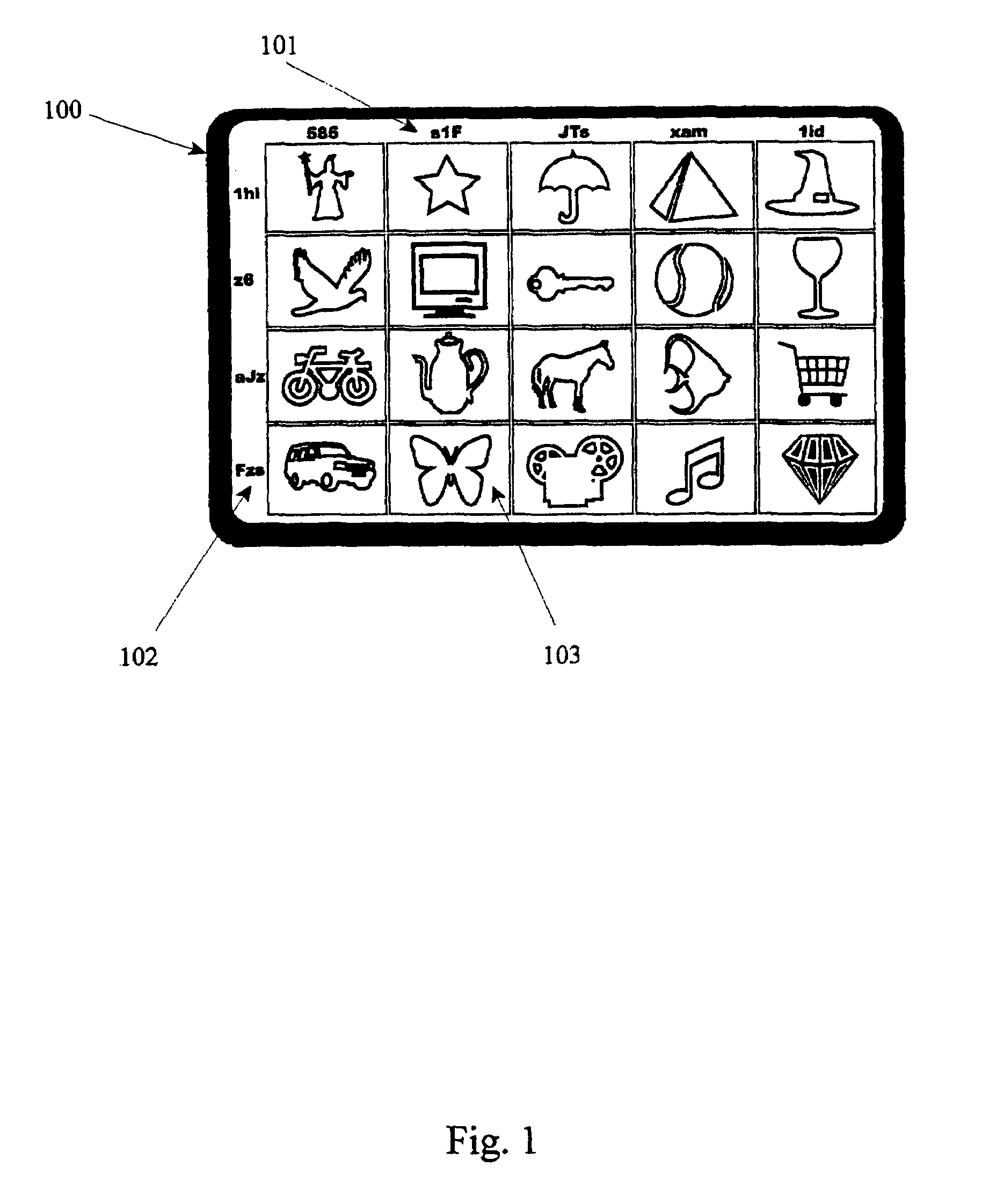
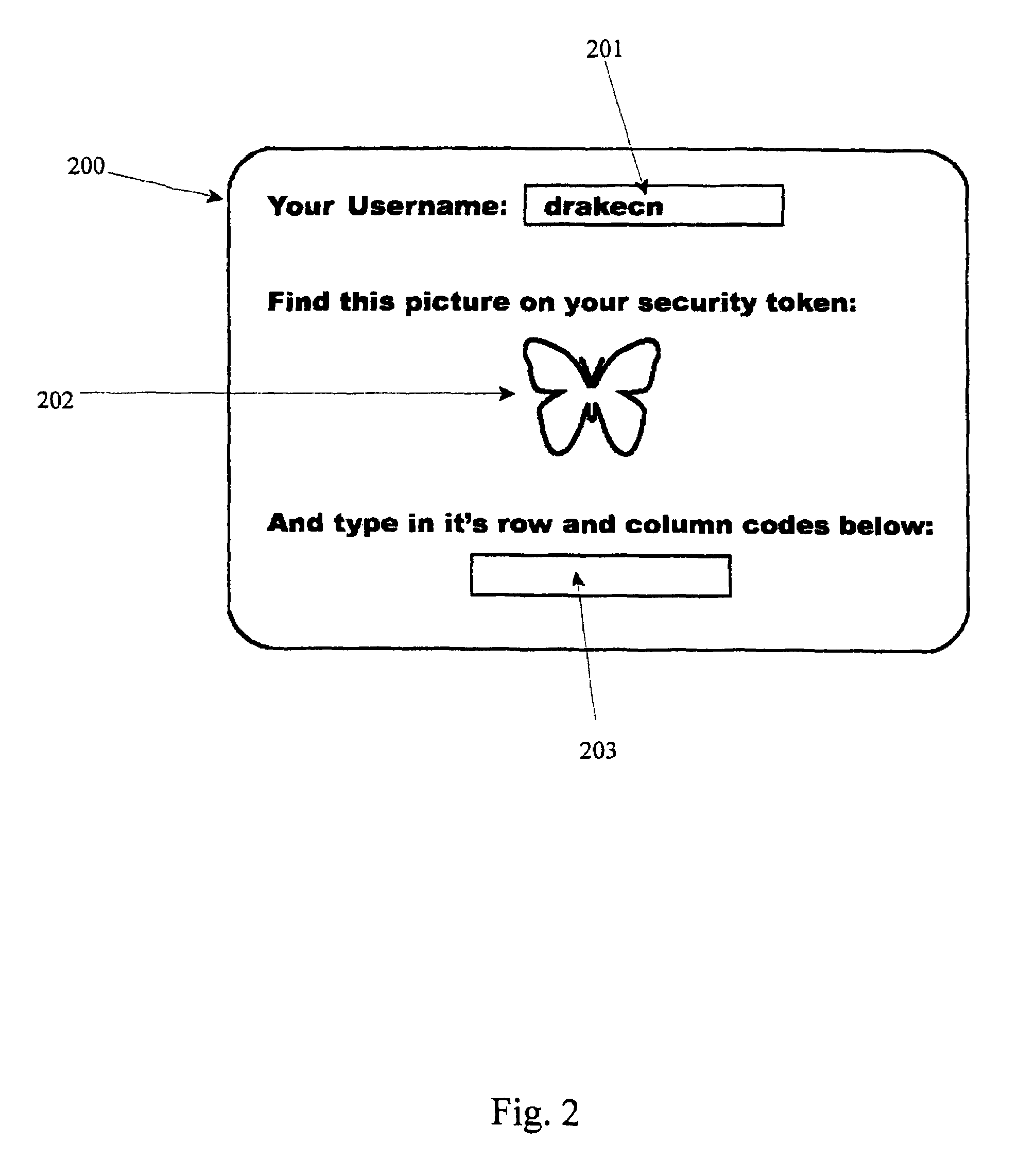
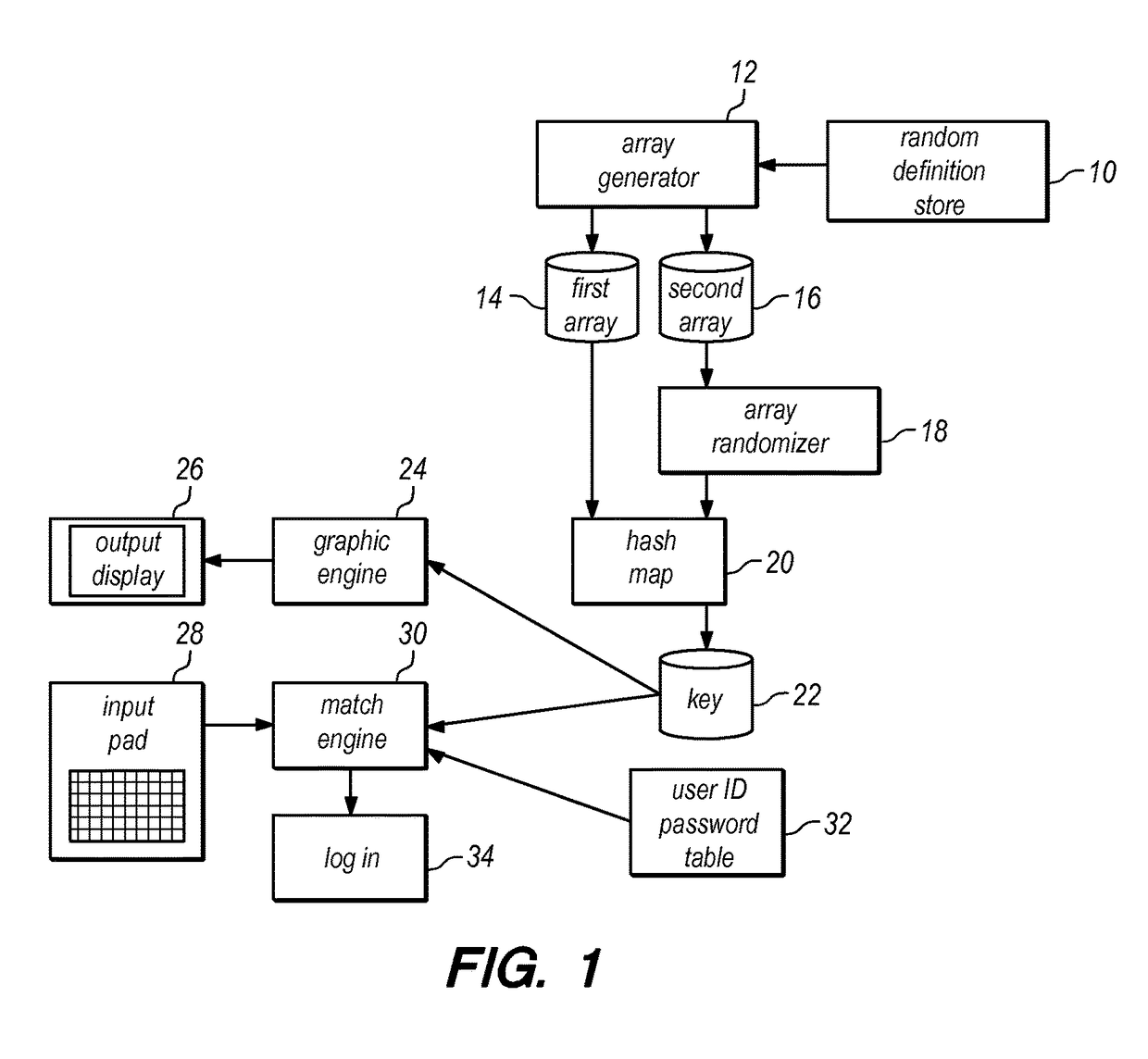
Computer security using visual authentication
ActiveUS8176332B2Improve securityUser identity/authority verificationDigital data authenticationComputerized systemPassword protection
A physical token to the user in the form of a unique card having a grid of images thereon. Each column and row of images has a unique text string of text. In addition, each user knows a special image, not necessarily present on the token card, on which one particular point or zone functions as an extra authentication feature. Users may be queried for a username, then shown a random one of the images on their card, and asked for the row text string plus column text string identifying the image. Users are also prompted to select their particular point or zone within their known special image, which is displayed, among a jumble of other images, by the computer system requesting authorization, such display serving to authenticate the computer system to the user. The system may be combined with password protection and methods to identify a user's machine.
Owner:CRYPTOPHOTO COM
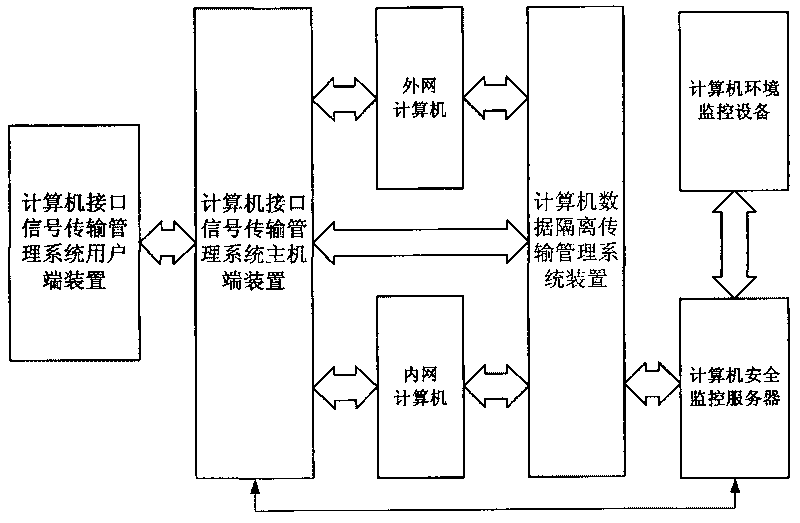
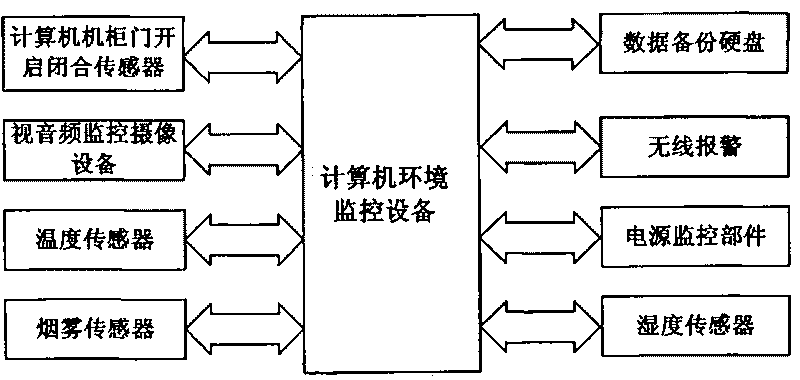
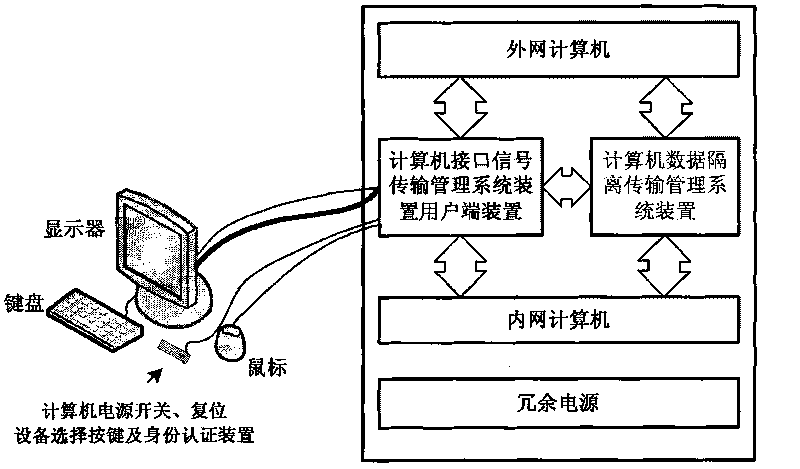
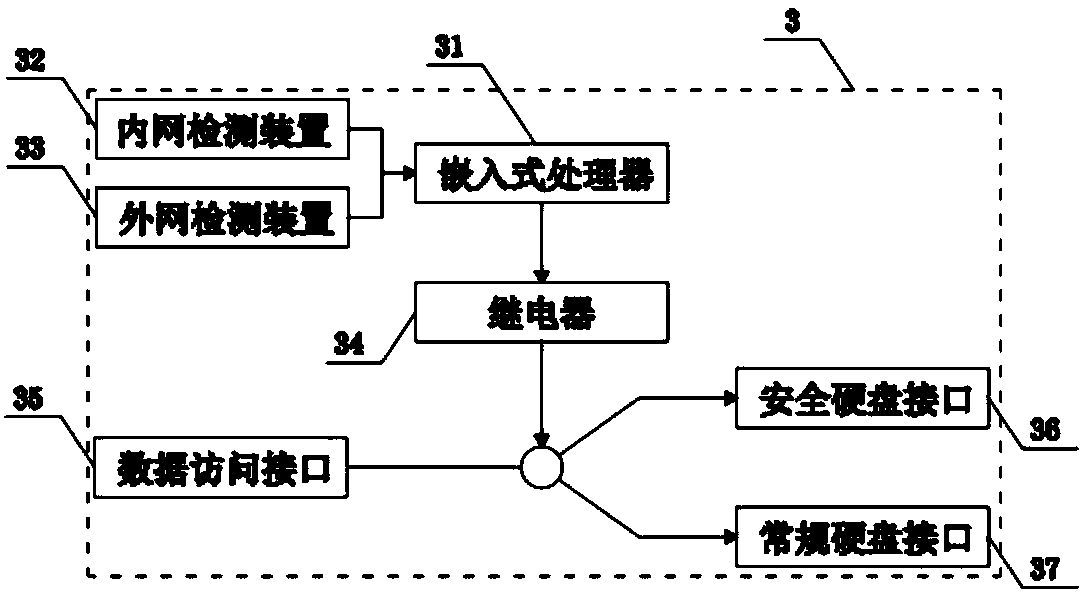
Computer security system and method thereof
InactiveCN101699456ASafe working environmentReliable working environmentInternal/peripheral component protectionDisplay deviceThe Internet
The invention provides a computer security system and a method thereof. The system comprises a host device of a computer interface signal transmission and management system, a client device of the computer interface signal transmission and management system, a computer data isolation transmission and management system device, a computer security monitoring server, a computer environment monitoring device, an outer network computer and an inner network computer. The method comprises the following steps: the computer interface signal transmission and management system isolates the host computer from a display device, a mouse keyboard inputting device, a computer interface signal, a reset interface signal and an on / off interface signal. The user surfs the internet to communicate with the outside world by the outer network computer and performs secure and confidential work by the inner network computer; the computer data isolation transmission and management system is connected with the outer network computer and the inner network computer, so that the data which needs to be transmitted is transmitted under the monitoring condition of computer security monitor and management software.
Owner:SHENZHEN UTEPO TECH CO LTD
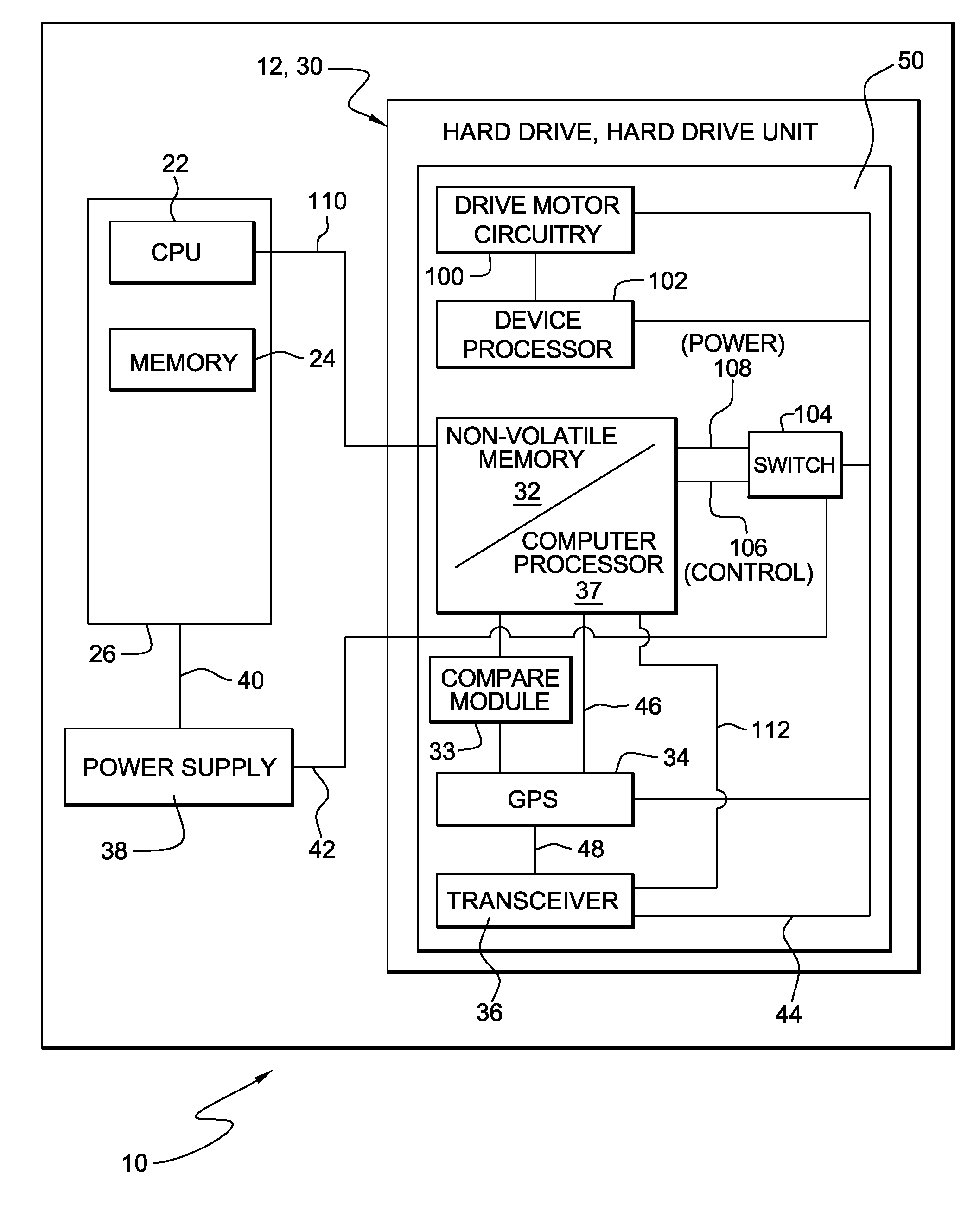
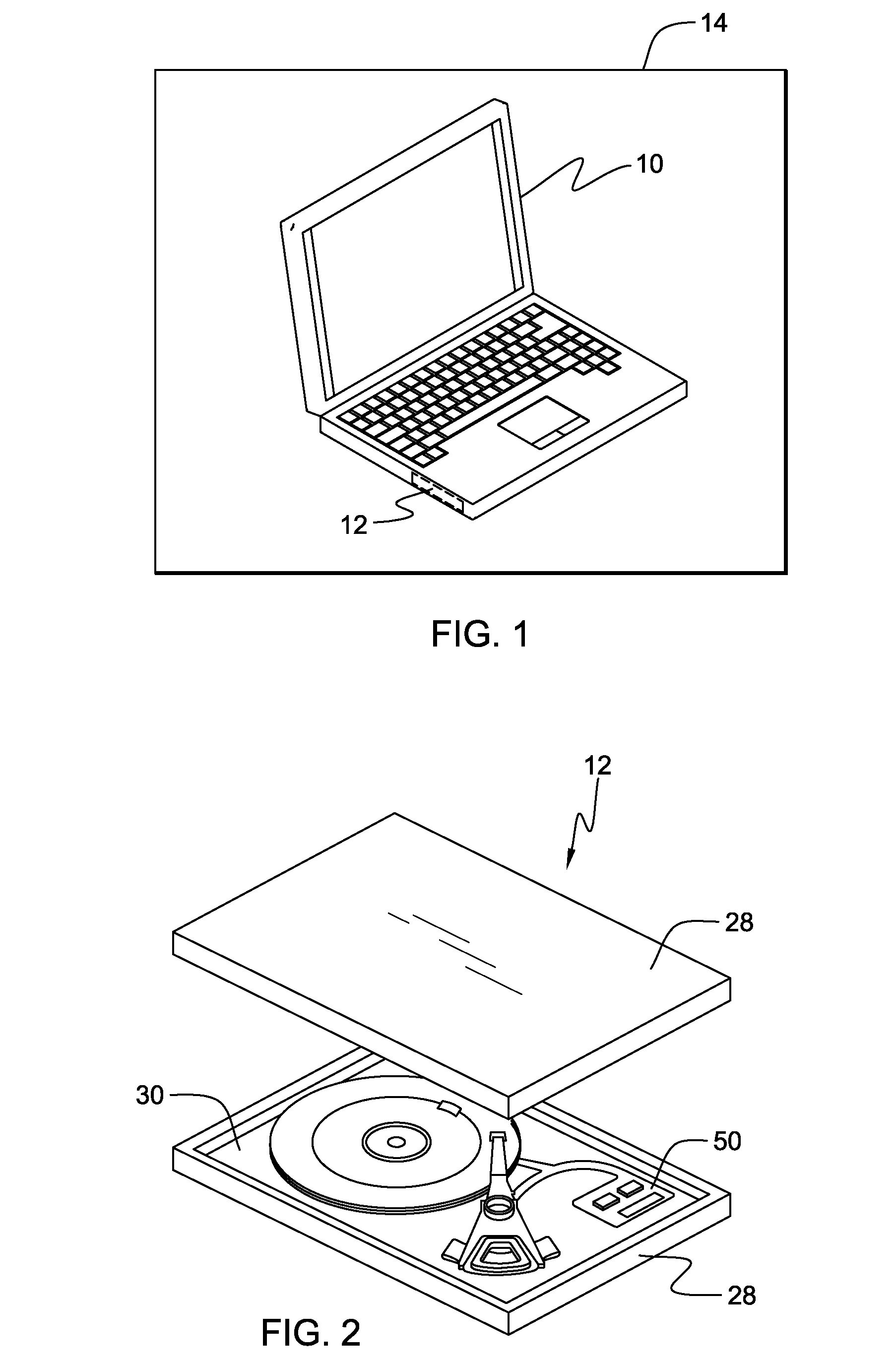
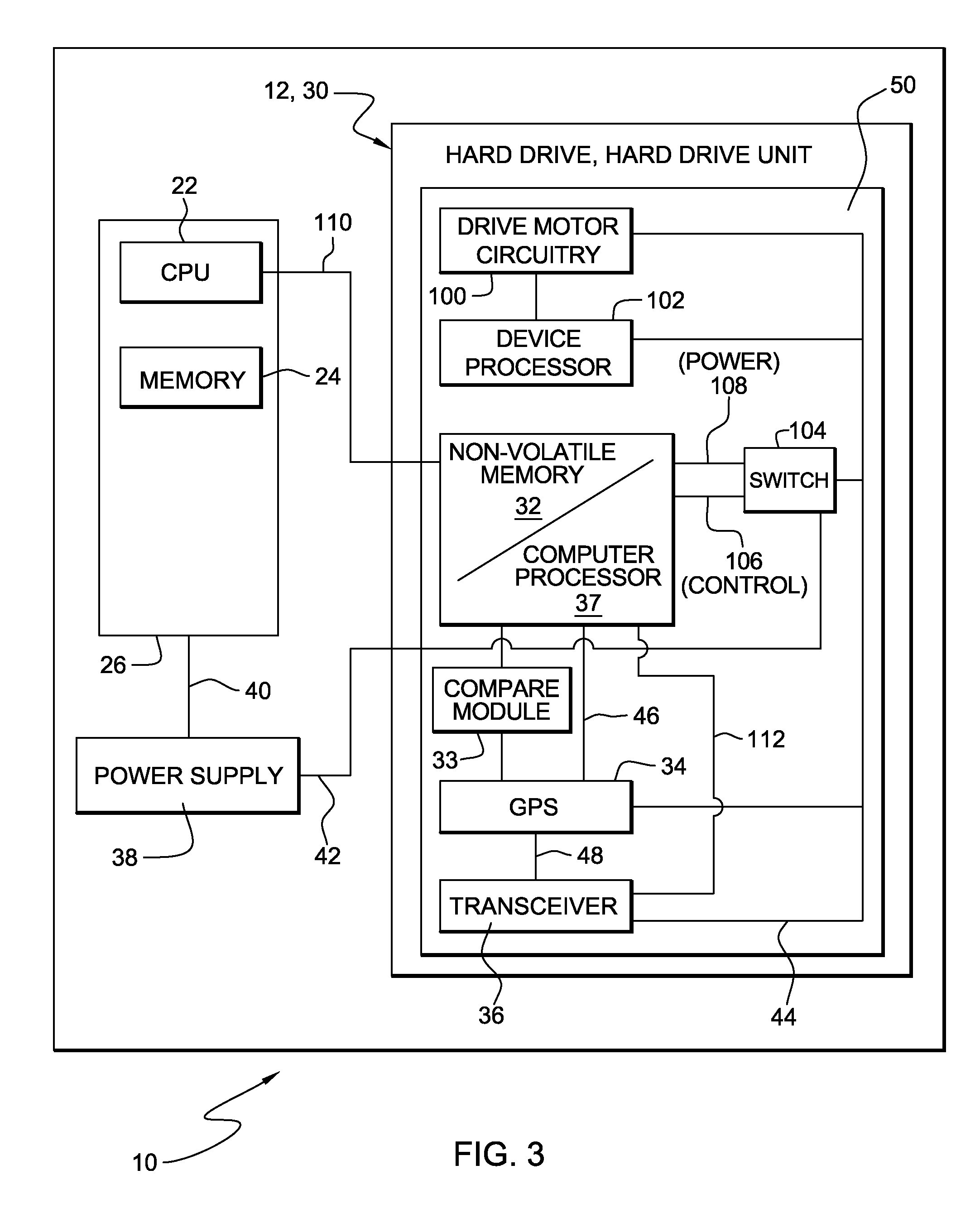
Computer security system having integrated GPS
InactiveUS20110072523A1Error detection/correctionVolume/mass flow measurementHard disc driveComputer module
A computing apparatus having a hard drive storage unit which includes a global positioning system, a non-volatile memory and a compare module. The non-volatile memory stores a permitted zone of operation of the hard drive storage unit while the compare module monitors the current location. If the compare module detects a current location of the hard drive storage unit as tracked by the global positioning system which is outside of the permitted zone of operation as stored in the non-volatile memory, the non-volatile memory contains at least one command implemented by a computer processor that may cause the hard drive storage unit to become disabled.
Owner:KYNDRYL INC
Computer security system and method based on user-intended final destination
A system and method is described for protecting applications against malicious URL links by identifying a final destination. The system and method also includes enabling a user process to directly connect to the final destination, bypassing the original URL altogether; thereby bypassing the hacker's ability to use that URL to programmatically send the application to a malicious site.
Owner:WOOD MICHAEL C
Remote security servers for protecting customer computers against computer security threats
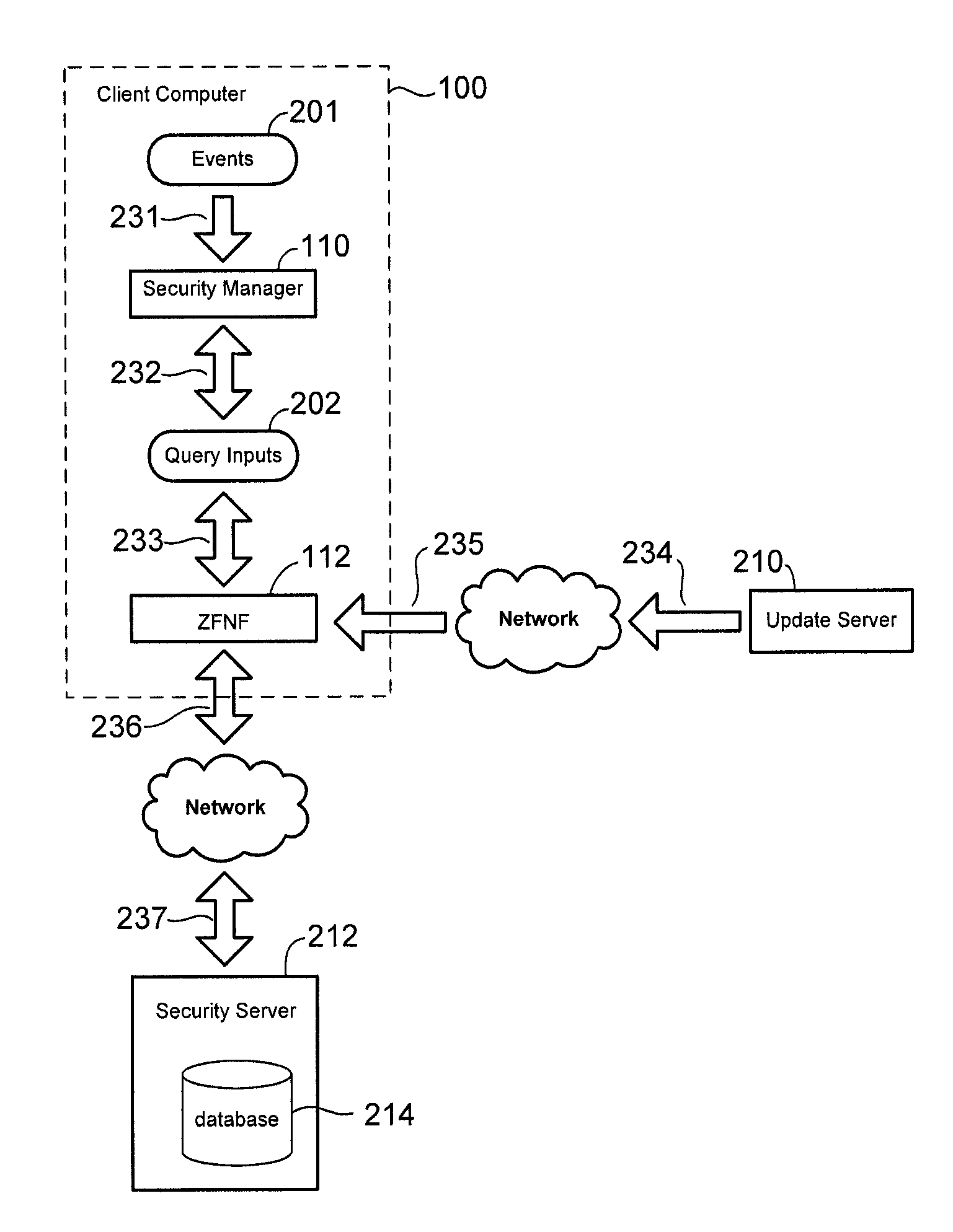
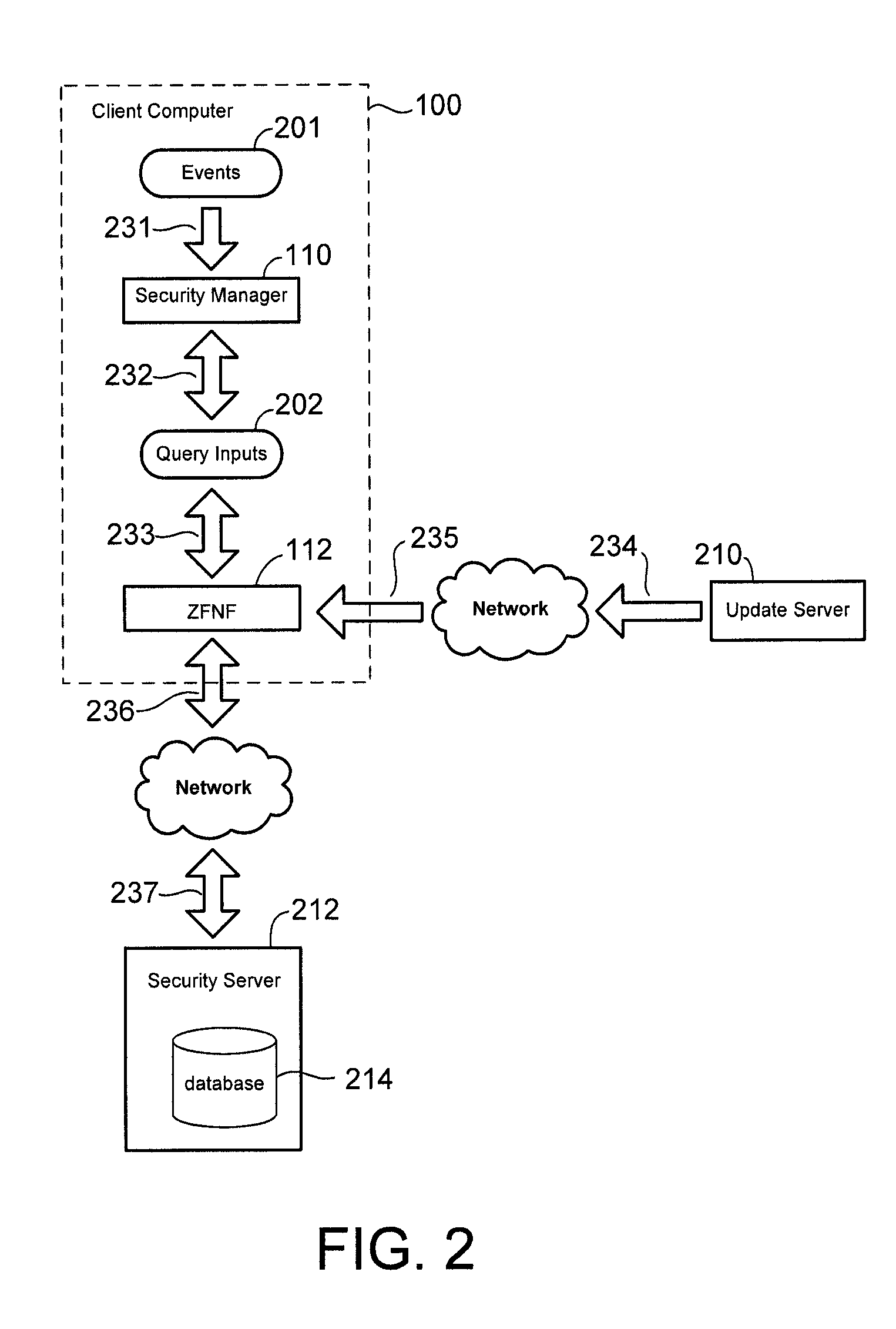
ActiveUS8132258B1Memory loss protectionUnauthorized memory use protectionComputer security modelClient-side
A client computer may be configured to perform computer security operations in conjunction with a remotely located security server. Upon detection of a computer security event, such as reception of a file, the client computer may generate a query input and determine if the query input has corresponding security information in the security server. When the query input has corresponding security information, the client computer may forward the query input to the security server. In response, the security server may retrieve the security information using the query input and provide the security information to the client computer. As a particular example, the security event may be reception of a file in the client computer and the security information may indicate whether or not the file is infected with a computer virus.
Owner:TREND MICRO INC
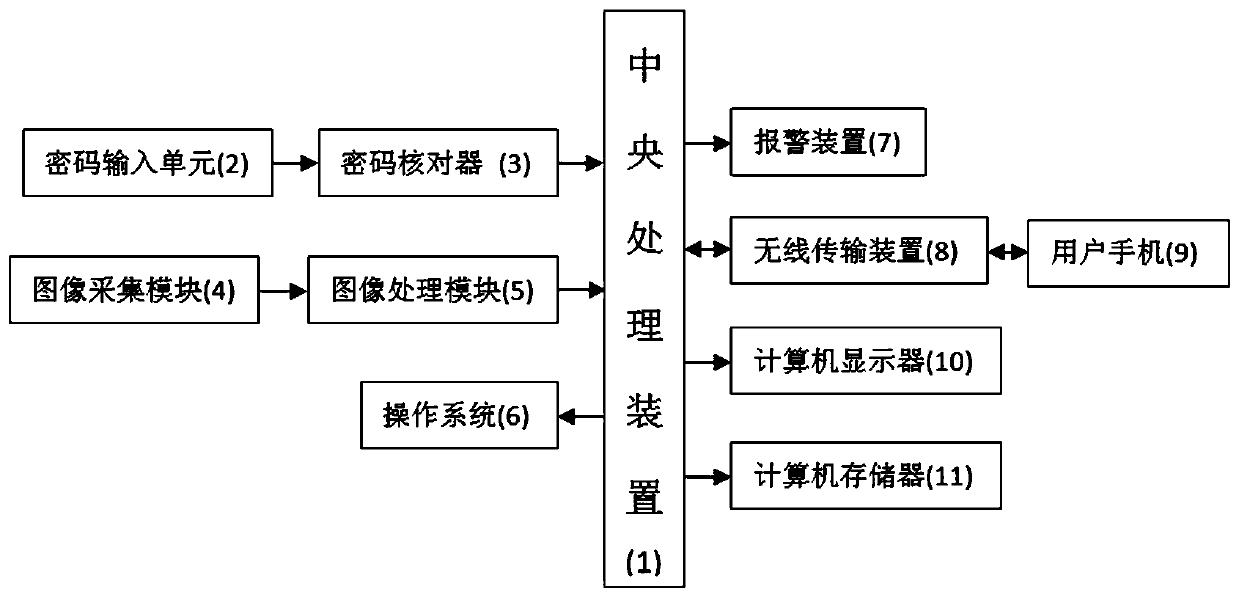
Computer security login guarantee system
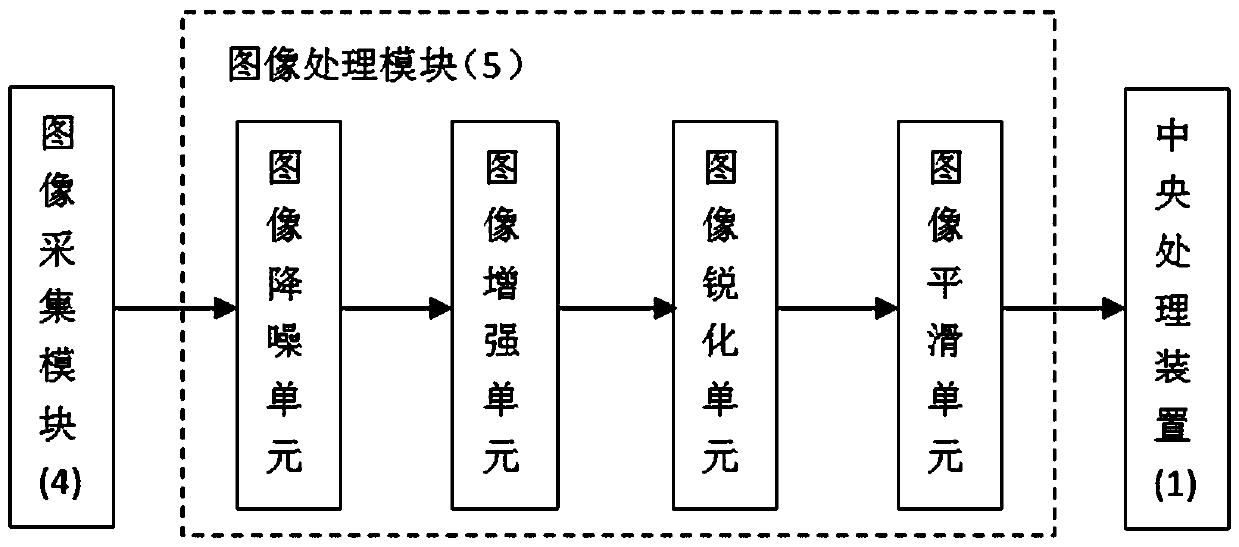
InactiveCN108846270AImprove information securityEfficient extractionImage enhancementDigital data authenticationComputer usersOperational system
The invention provides a computer security login guarantee system. The computer security login guarantee system adopts a central processing device, a password input unit, a password checker, an imagecollection module, an image processing module, an operating system, an alarm device, a wireless transmission device, a user mobile phone, a computer display and a computer memory, a computer owner canauthorize a computer user to use a computer through the mobile phone and can also obtain face image information of the personnel logging in the computer so as to know who is using the computer, and can also know who logs in / attempts to log in the computer at what time through the computer memory, so that the information security of the computer is greatly improved, wherein the image processing module performs image denoising, image enhancement, image sharpening and image smoothing on collected images in turn to collect the image information of the image collection module efficiently and quickly, and the recognition accuracy of the face of the personnel logging in the computer can be improved to effectively reduce the occurrence of misjudgments.
Owner:CHANGZHOU UNIV
Computer security method and apparatus
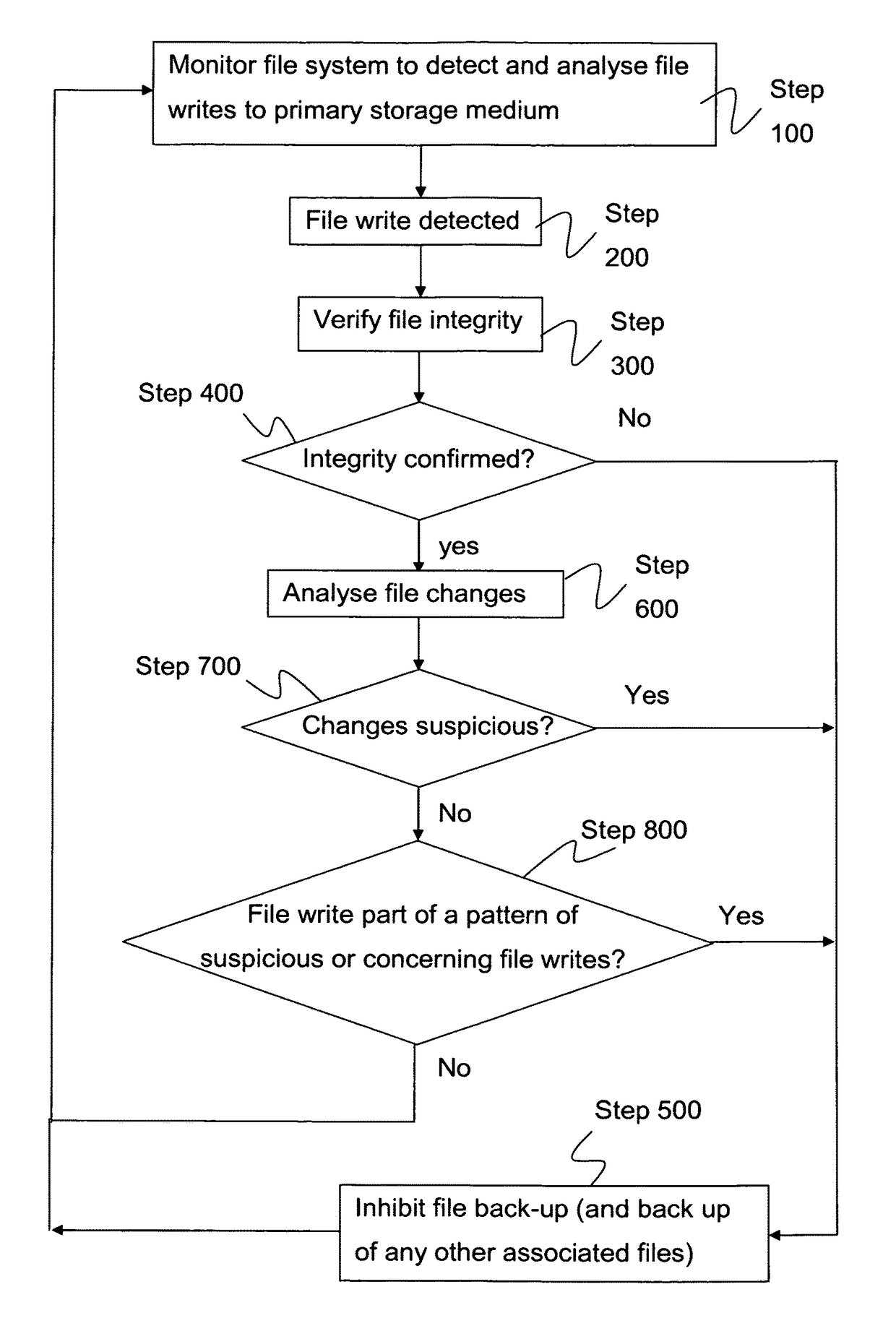
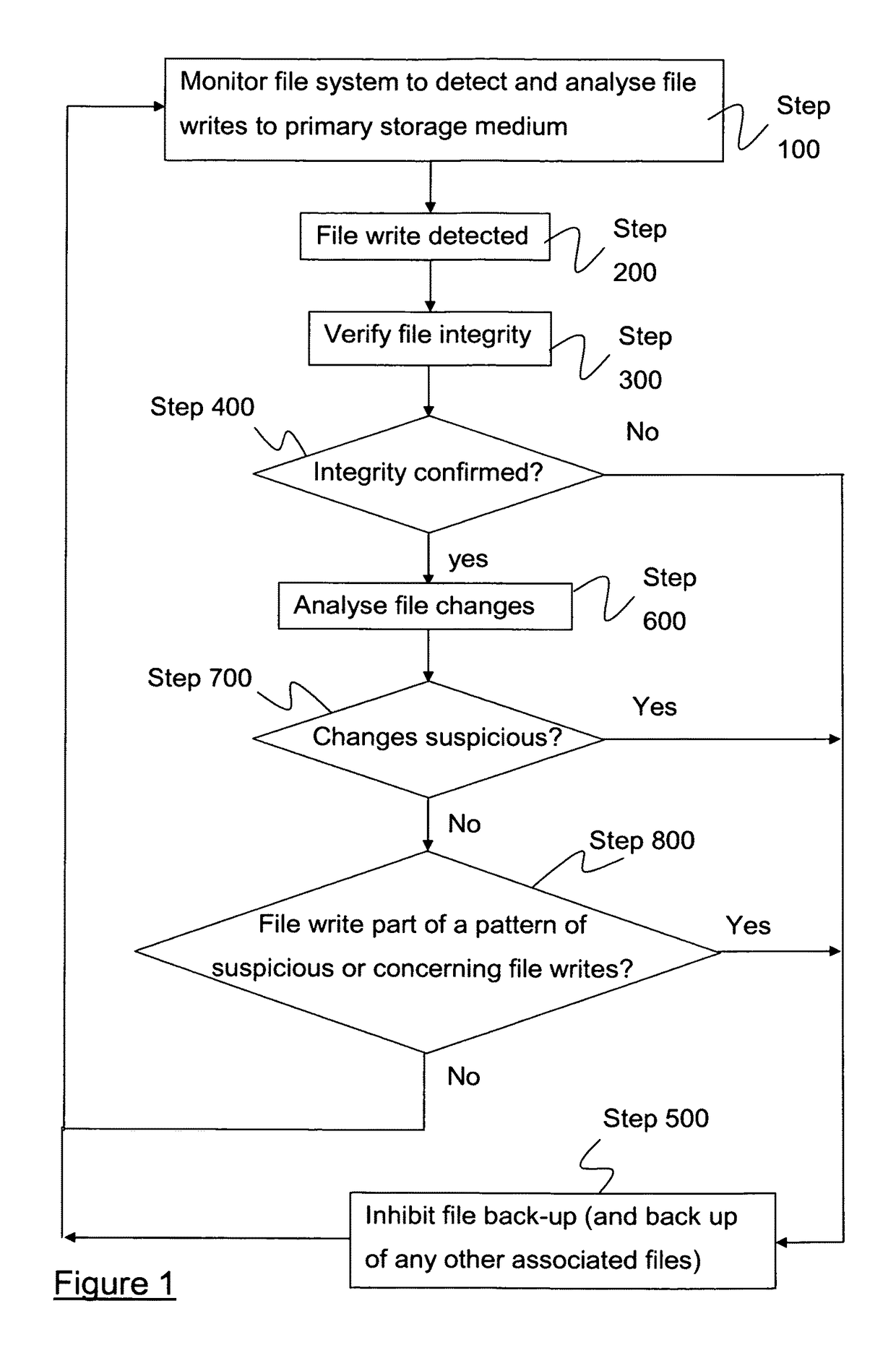
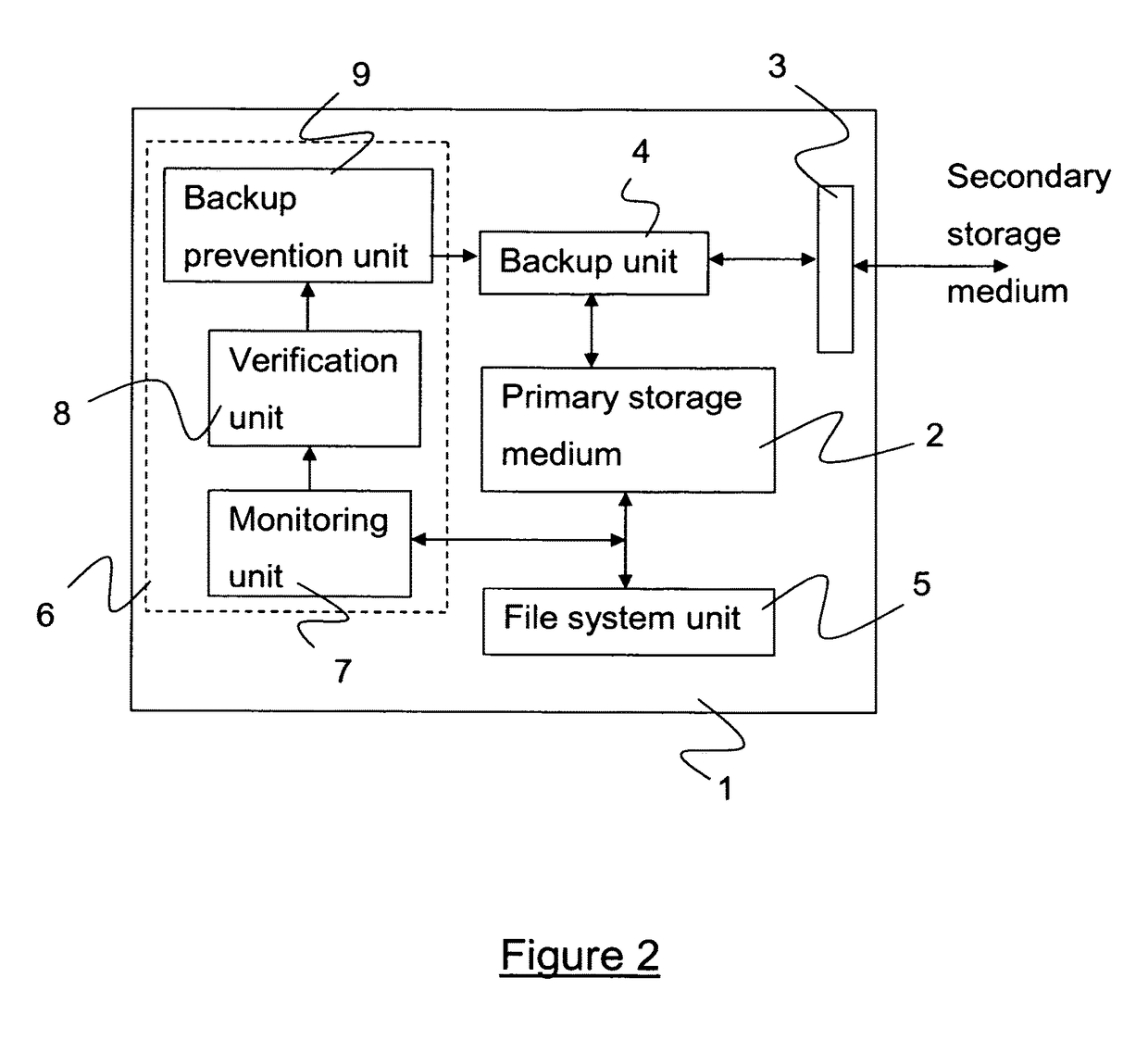
ActiveUS9779267B2Reduce riskReduce dataDigital data processing detailsDigital data protectionFile systemComputerized system
A method of controlling a process on a computer system for backing-up files stored in a primary storage medium, to a secondary storage medium. The method comprises monitoring a file system implemented on the computer system in order to detect write operations made by the file system to said primary storage medium. Upon detection of a write operation, the integrity of a file being written is verified and / or changes in the file identified with respect to a version of the file currently stored in the primary storage medium and which is being replaced. In the event that the integrity of a file being written by the file system is compromised, and / or any identified changes in the file are suspicious, then the file is identified to the back-up process such that automatic back-up of the file is inhibited.
Owner:F SECURE CORP
Computer security protecting method, computer security protecting device and computer
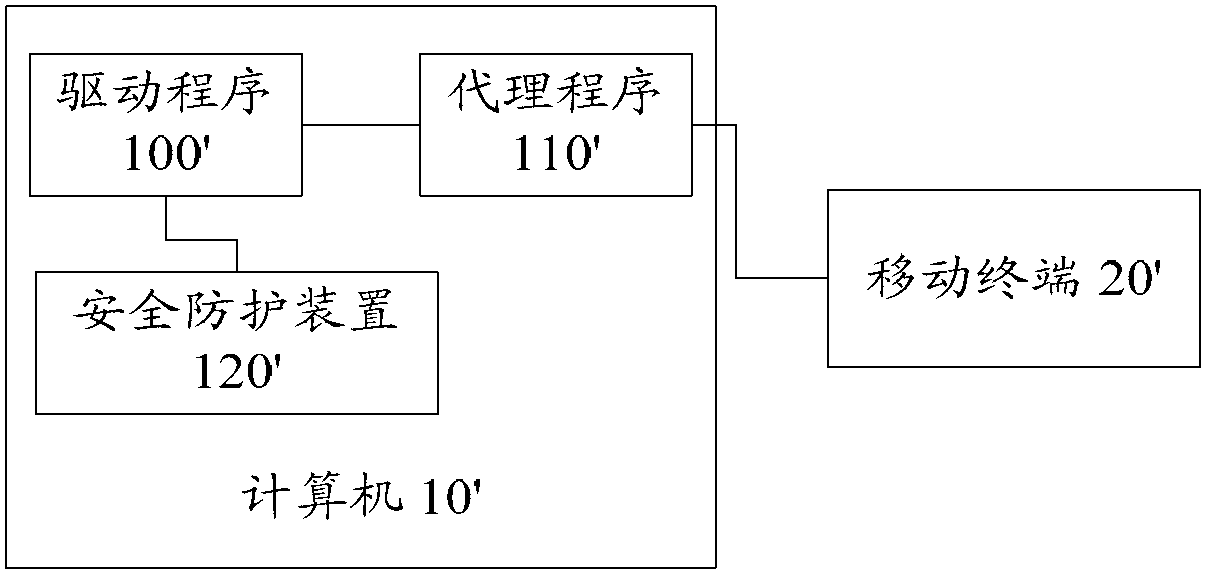
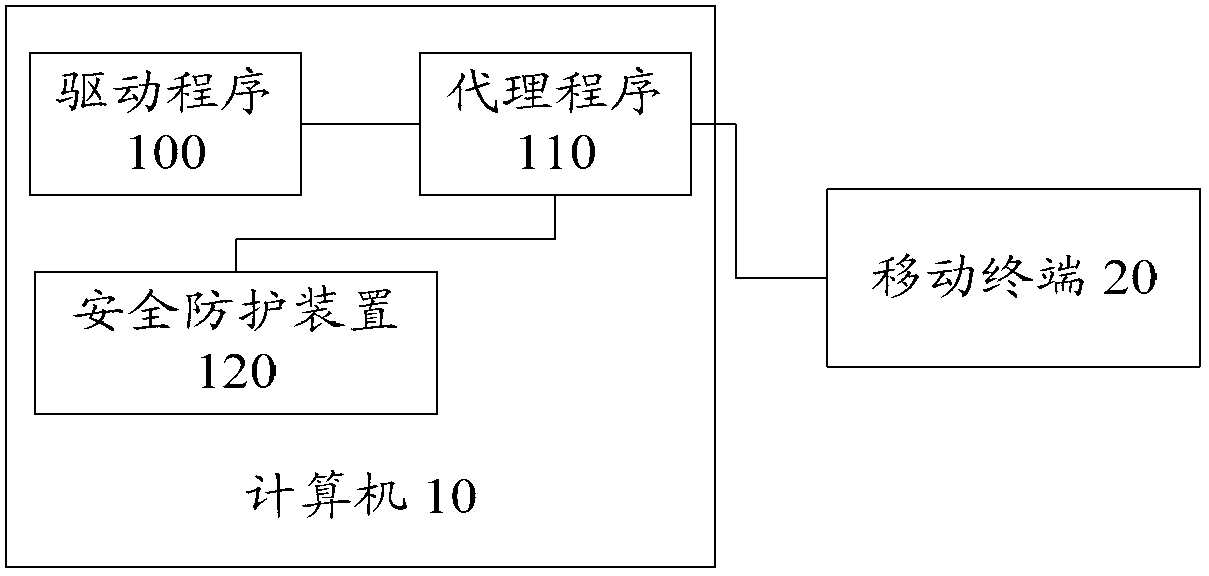
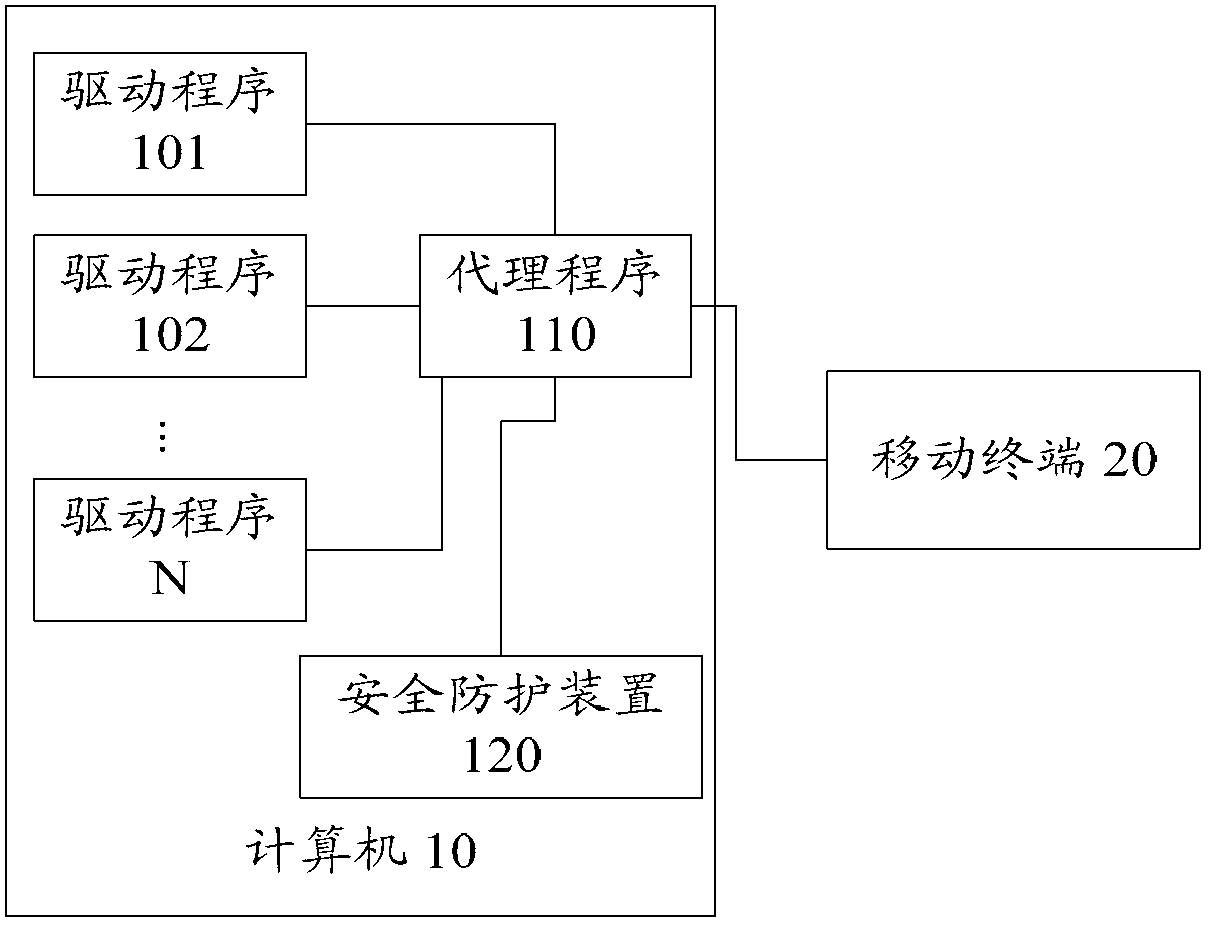
ActiveCN102915418AImprove the protective effectPlatform integrity maintainanceComputer security modelApplication software
The invention provides a computer security protecting method, a computer security protecting device and a computer. The computer security protecting method comprises the following steps: verifying an agent program of a mobile terminal application program and judging whether the agent program is legal, wherein the mobile terminal application program is connected with the mobile terminal through the agent program, and the mobile terminal application program and the agent program are both arranged in the computer; and when the agent program is judged to be illegal, rejecting the data interaction between the mobile terminal and the mobile terminal application program. With the adoption of the method, the problems in the prior art that a computer security protection method cannot provide security protection to the computer when the agent program of a mobile terminal driving program is illegally replaced or modified are solved, so that better security protection is provided for the computer.
Owner:KINGSOFT
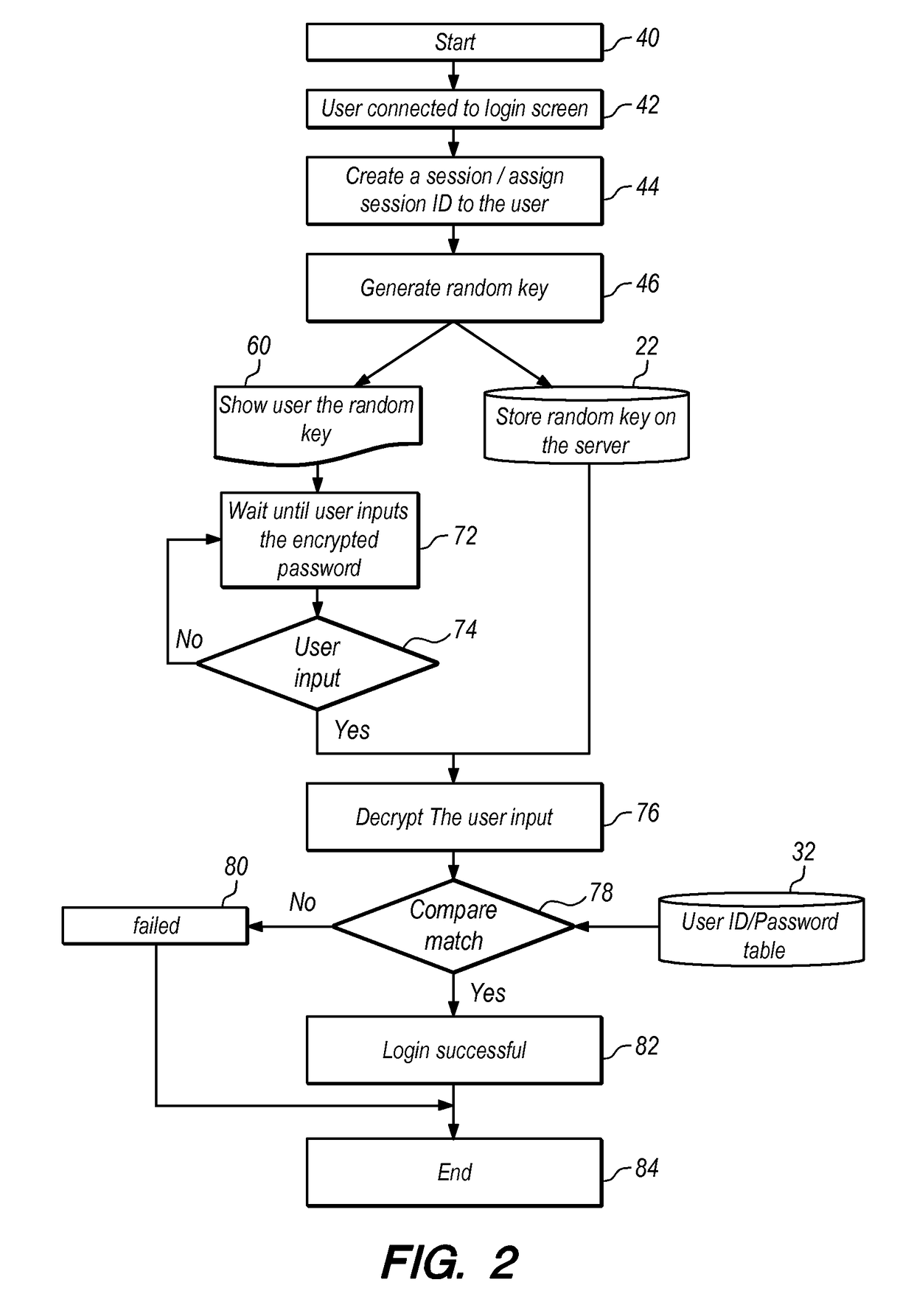
Computer security system and method to protect against keystroke logging
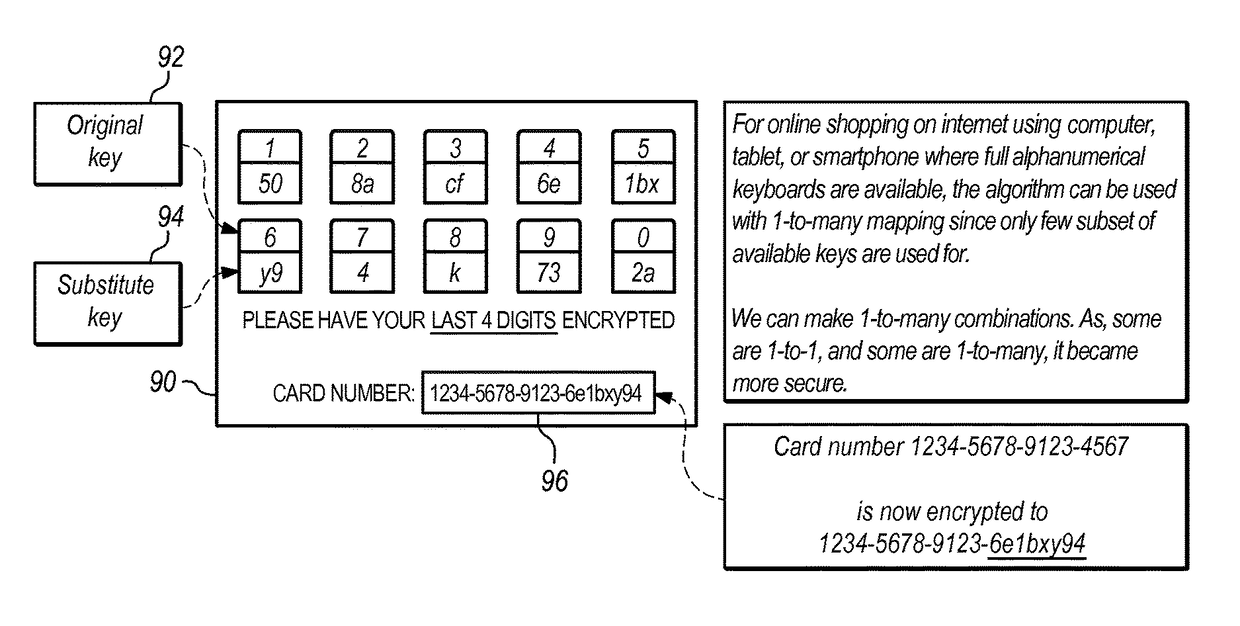
ActiveUS9768959B2The equipment is easy to operateImprove securityKey distribution for secure communicationUser identity/authority verificationPasswordComputer security model
Static security credentials are replaced by pseudonyms and session-specific passwords to increase security associated with user login attempts, and specifically to defeat keylogging attacks. For each login event, the system generates unique, session-specific credentials by randomly replacing characters within a given username and password. The random character generation ensures that system login attempts use different combinations of characters, thereby producing a new username and password for every user session. The client side of the system requires only the capability to display an image file, with specialized software / hardware limited to the server side, thereby facilitating the use of the system by a wide range of client devices.
Owner:LIVERAMP
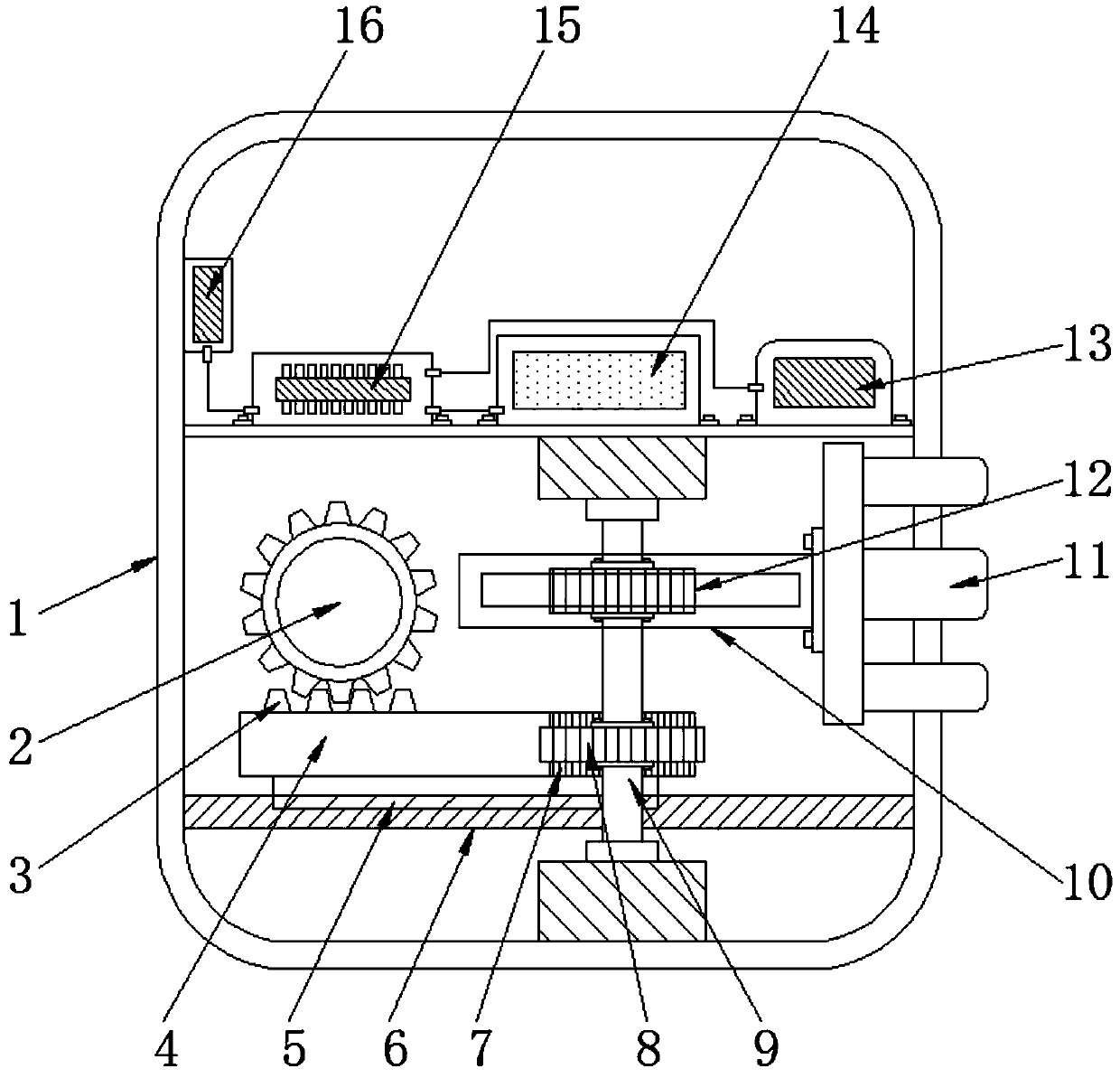
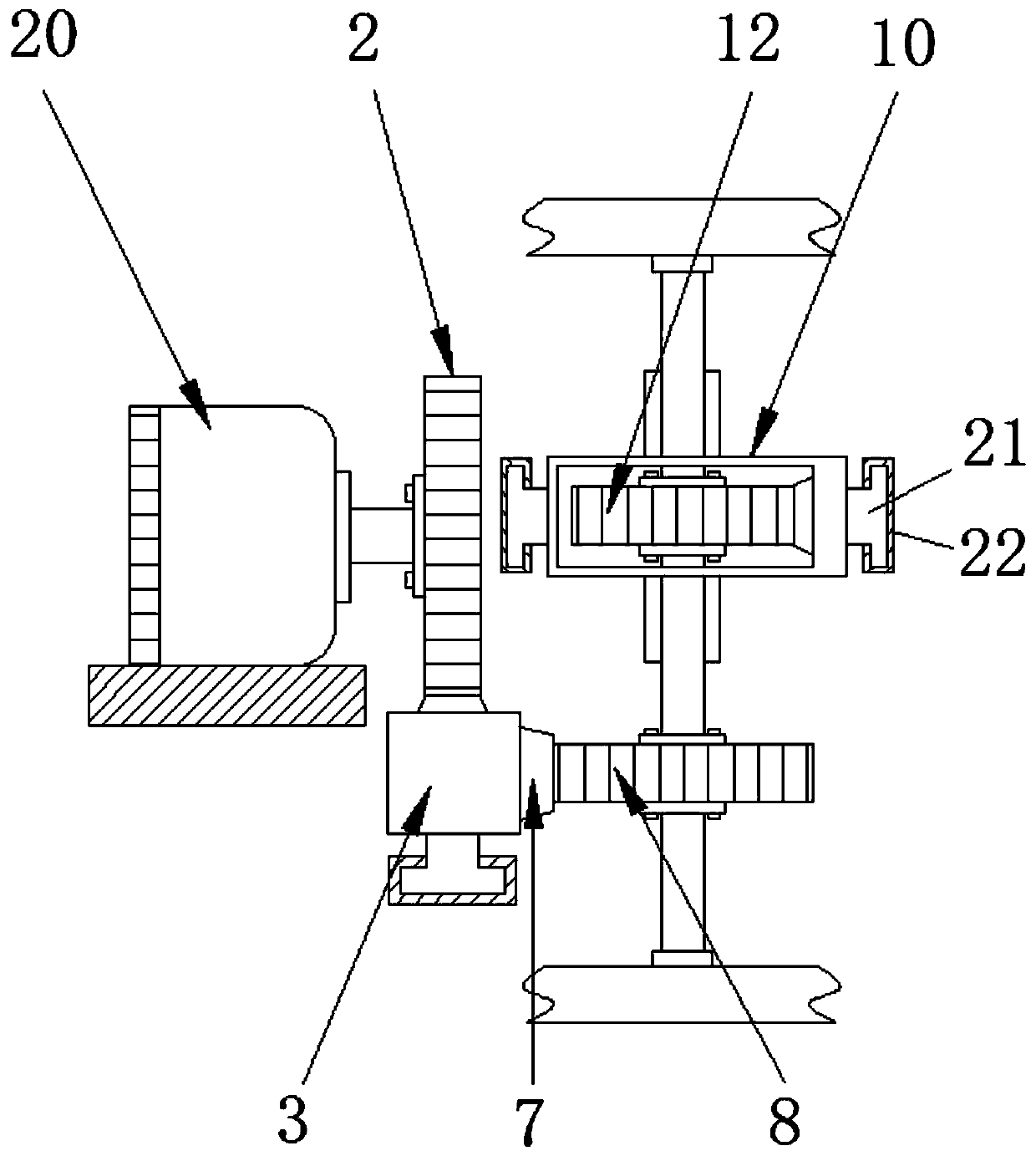
Computer security device and fingerprint unlocking method and password unlocking method thereof
ActiveCN109784106AProtection securitySimple structureInternal/peripheral component protectionDigital data authenticationPasswordElectric machinery
The invention discloses a computer security device and a fingerprint unlocking method and a password unlocking method thereof. The device includes a first gear and a battery. The first gear is fixed with a rotor of the anti-theft lock motor through a bolt. The anti-theft lock motor is fixed in the shell through a motor base. A rack is mounted below the first gear; the rack and the first tooth groove are integrally formed. Meanwhile, the rack and the second tooth groove are integrally formed. A first sliding block is welded to the lower side of the rack and matched with the first sliding groovein size, meanwhile, the first sliding groove is welded into the shell, the second gear is installed on a shaft rod through a bolt, the lower side of the shaft rod is installed on an installation basein the shell through a bearing, and meanwhile a third gear is fixedly installed on the upper side of the shaft rod through a bolt. According to the computer security decryption device, two modes of fingerprint unlocking and password unlocking are used for unlocking operation, so that the security of the server is protected, and meanwhile, the anti-theft effect of the server is improved.
Owner:SHAANXI SCI TECH UNIV
Computer security login system based on Internet of Things
InactiveCN110298169AEnsure safetyGuaranteed privacyPower supply for data processingDigital data authenticationData platformStandby power
The invention discloses a computer security login system based on Internet of Things, belongs to the technical field of computers, and solves the problem that normal login verification work cannot berealized when a computer is in emergency power failure in an existing system. The system comprises a computer terminal module used for verifying user login, a front control module, used for controlling the computer terminal module to operate; a data platform module used for processing login data; a standby power supply module used for storing energy and supplying power. The data platform module isconnected with the pre-control module through a local area network. The system has the advantages of being stable in operation and convenient and fast to operate, meanwhile, due to the arrangement ofthe standby power supply module, power can be supplied to a computer when the computer is powered off, the computer security login system further has the advantage of being safe in login, and the safety of user data and the privacy of a user are guaranteed.
Owner:浙江无极互联科技有限公司
Computer security system and method
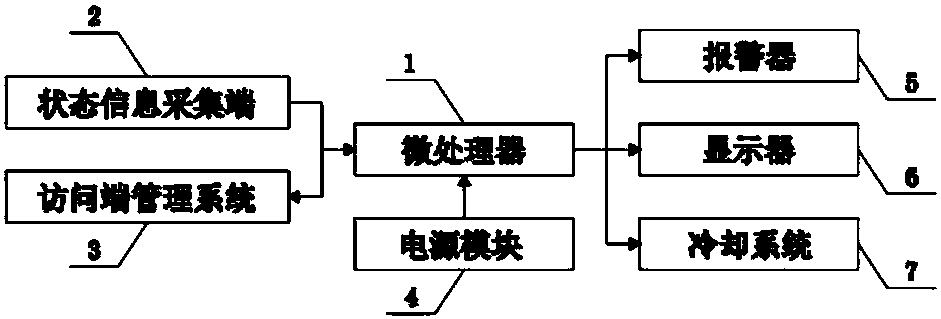
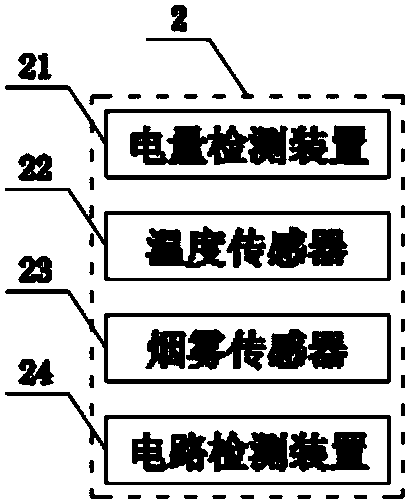
InactiveCN108509319AImprove securityReal-time monitoring of hardware statusDigital data processing detailsHardware monitoringEngineeringElectronic information
The invention belongs to the technical field of electronic information, and particularly discloses a computer security system and method. The system comprises a microprocessor; an input port of the microprocessor is connected with output ports of a state information collection end and a power module through data lines; the state information collection end comprises an electric quantity detection apparatus, a temperature sensor, a smoke sensor and a circuit detection apparatus; output ports of the electric quantity detection apparatus, the temperature sensor, the smoke sensor and the circuit detection apparatus are connected with the input port of the microprocessor through data lines; and a transmission port of the microprocessor is connected with a transmission port of an access end management system through a data line. According to the scheme, a network environment and a hardware state of a computer can be monitored in real time; problems can be timely discovered and reminded; and the security of network use is improved.
Owner:HENAN UNIV OF ANIMAL HUSBANDRY & ECONOMY
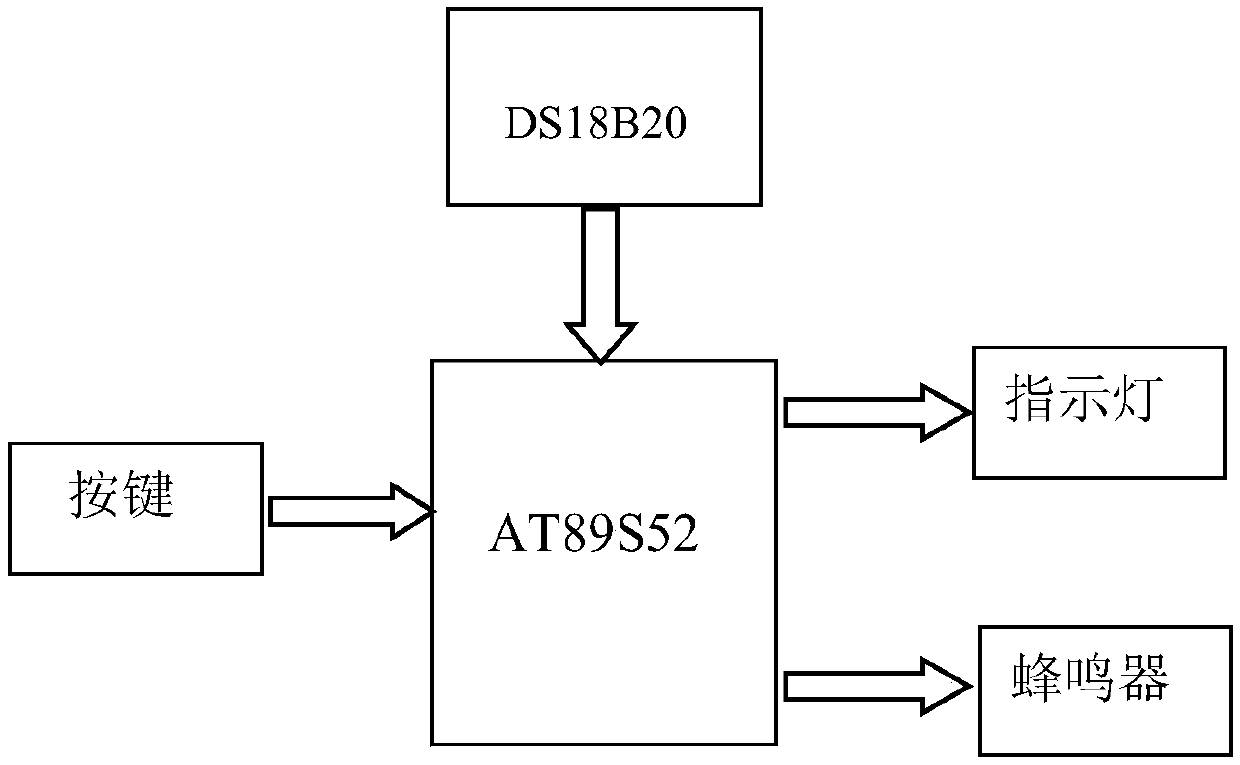
Computer security system
InactiveCN105528282AHardware monitoringInternal/peripheral component protectionComputer security modelSingle chip
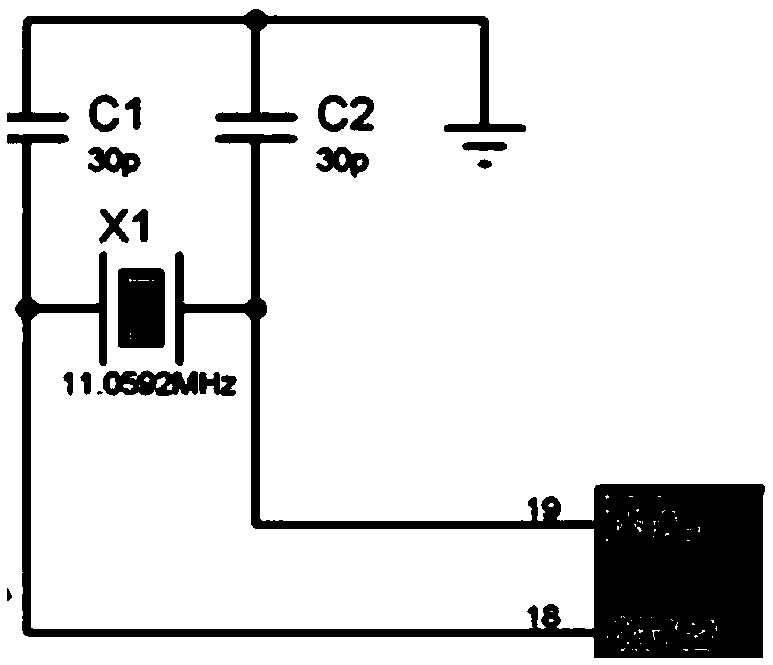
The invention discloses a computer security system, comprising an AT89S52 single-chip microcomputer, a temperature sensor DS18B20, a key, indicator lights and a buzzer. When in use, the computer security system disclosed by the invention is installed in a mainframe box of a computer, wherein the key and the indicator light are arranged on a shell of a computer mainframe; temperature information in the mainframe is collected by the temperature sensor DS18B20; a temperature signal monitored by the temperature sensor DS18B20 is read by a P2.4 port of the AT89S52 single-chip microcomputer in real time, and the temperature signal is compared with set limit alarm temperature; when the temperature signal exceeds the alarm temperature, a signal is sent to the buzzer by a P2.3 port of the AT89S52 single-chip microcomputer to control the buzzer to perform alarm output, and meanwhile, a red indicator light is controlled to be turned on through a P2.1 port.
Owner:GAOZHI TECH TIANJIN CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com