Computer security control module and safeguard control method thereof
A computer security and control module technology, which is applied in computing, program control devices, instruments, etc., can solve problems such as untrustworthiness, lower system security, and lower ease of use, so as to improve ease of use, ensure safety, and prevent stolen effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
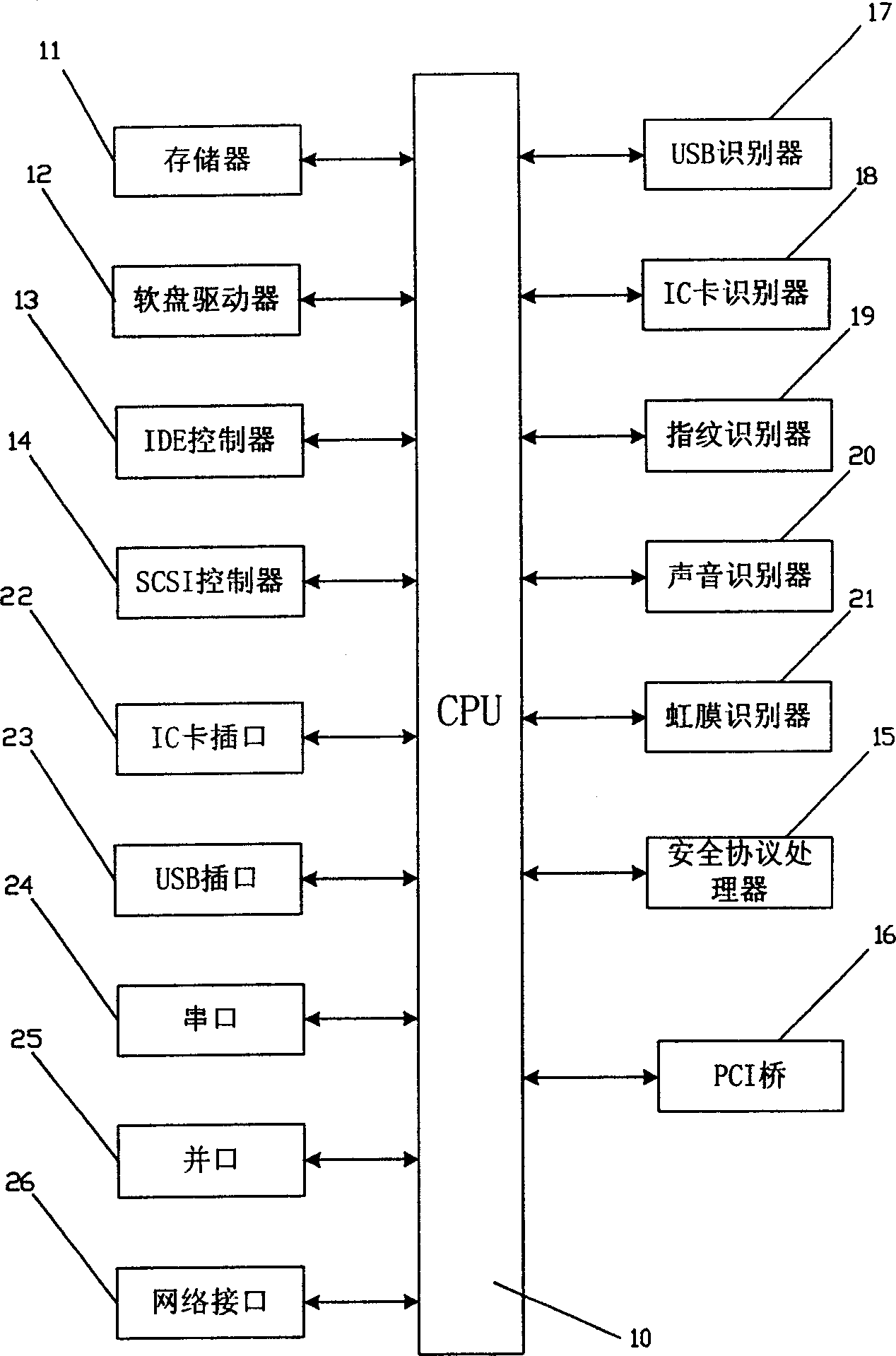
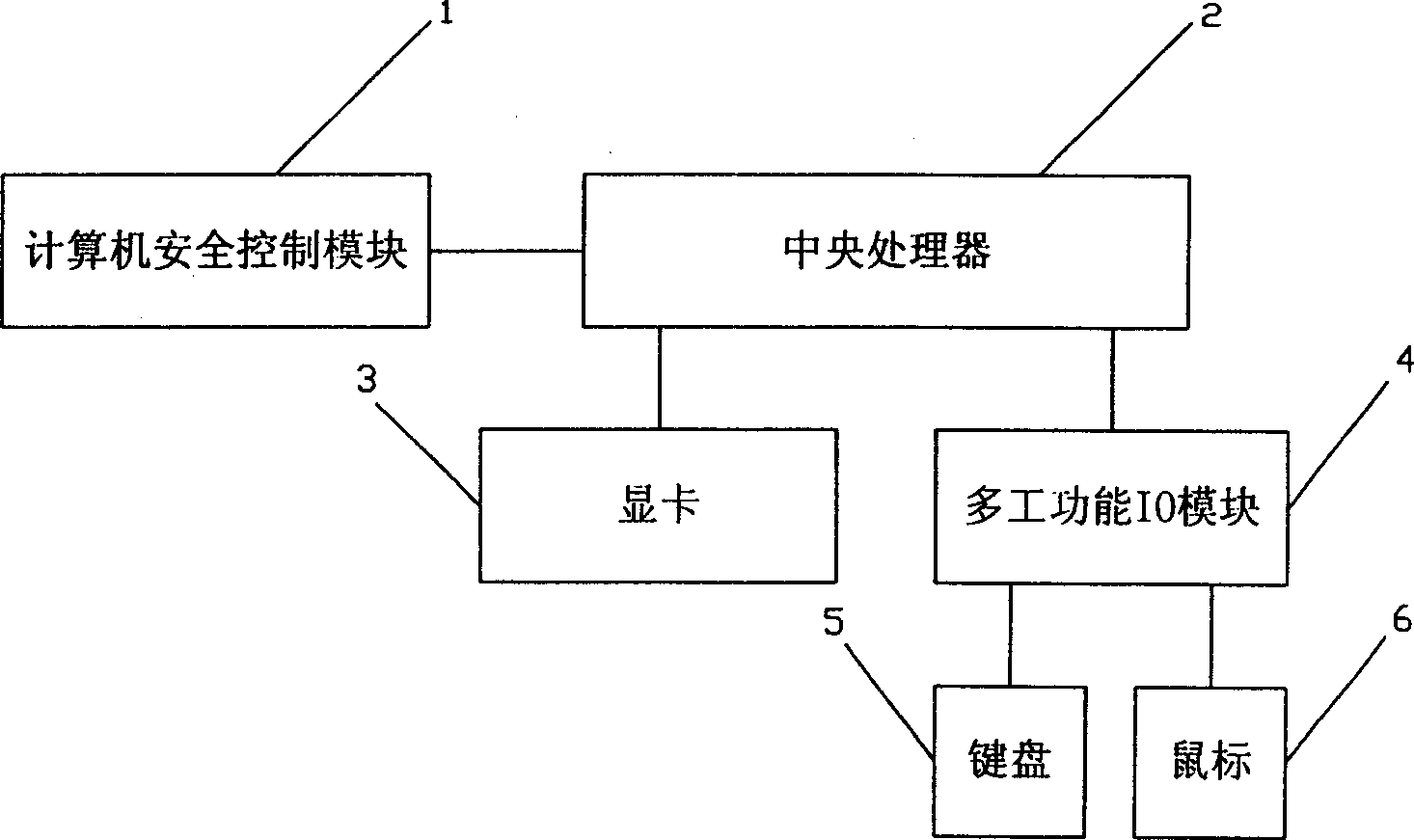
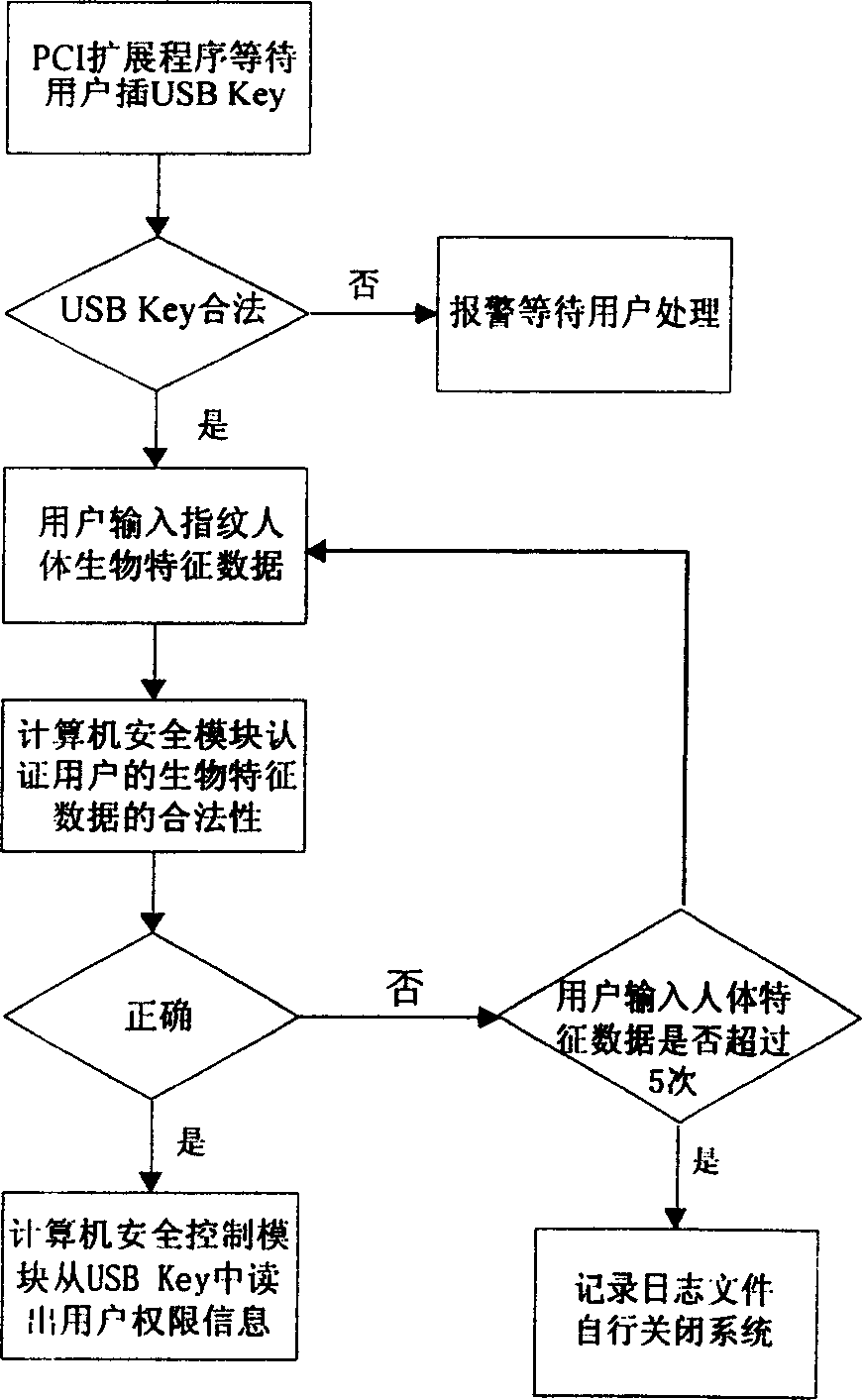
[0046] Such as figure 1 Shown is a schematic structural diagram of the computer security control module of the present invention. The computer security control module has a central processing unit (CPU) 10, and a memory 11, a floppy disk drive 12, an IDE controller 13 and a SCSI controller 14 are connected to the CPU 10. The computer security control module is a hardware module, and may also be a chip containing the computer security control module, or other forms of devices containing the computer security control module. The computer security control module implements security control on the computer through the PCI interface, or it may Outside computer; CPU10 it is the processor based on X86 core, can also be the processor of ARM, MIPS, POWER PC core, or other specialized processors; Memory 11 comprises random access memory and electrically erasable memory or / and only Read memory; IDE controller 13 and SCSI controller 14 are connected with hard disk, hard disk is no longer...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com