Computer security starting method based on heterogeneous multi-core chip
A computer security and heterogeneous multi-core technology, which is applied in the field of computer security boot based on heterogeneous multi-core chips, can solve the problems of hidden dangers of sensitive information, inability to fully grasp, and no security of the platform at all, so as to achieve the effect of guaranteeing safe boot
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The technical solutions of the present invention will be described in further detail below with reference to the accompanying drawings and preferred embodiments. It should be understood that the specific embodiments described herein are only used to explain the present invention, and are not used to limit the technical solutions of the present invention.
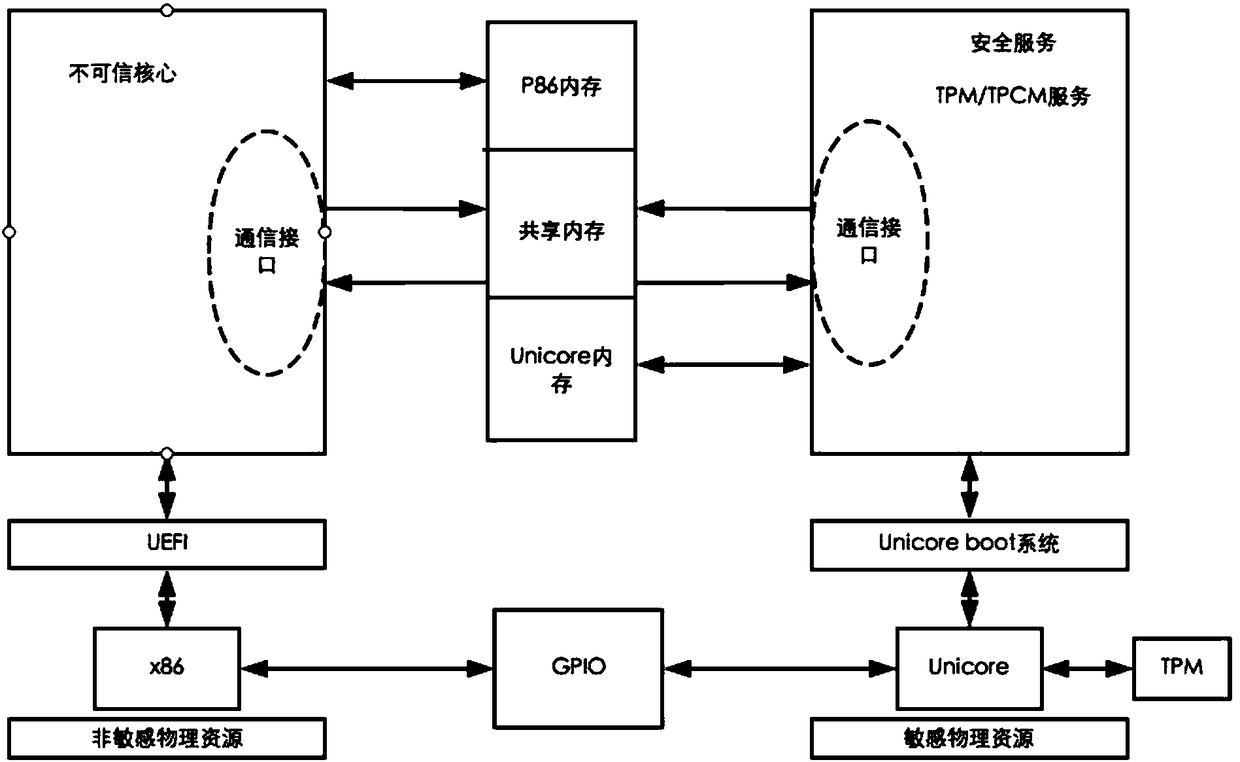
[0021] like figure 1 shown is an architecture diagram of an embodiment of a computer security boot method based on heterogeneous multi-core chips of the present invention, wherein:
[0022] The trusted core is the Unicore processor with independent intellectual property rights of the Microprocessor R&D Center of Peking University as an example.
[0023] The untrusted core is an x86 architecture processor.
[0024] In terms of hardware division, the TPM must be exclusively owned by the trusted core, and the division of other sensitive resources can be different according to the specific implementation. The GPIO is s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com