Network hiding method for computer and network hiding system based on method
A computer and network technology, applied in the field of network stealth method and network stealth system based on this method, can solve the problems of increasing the difficulty of attacker penetration or virus infection, difficulty of attacker discovery and utilization, loss of effectiveness, etc., to increase network Effects of complexity, increased network complexity, and increased difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
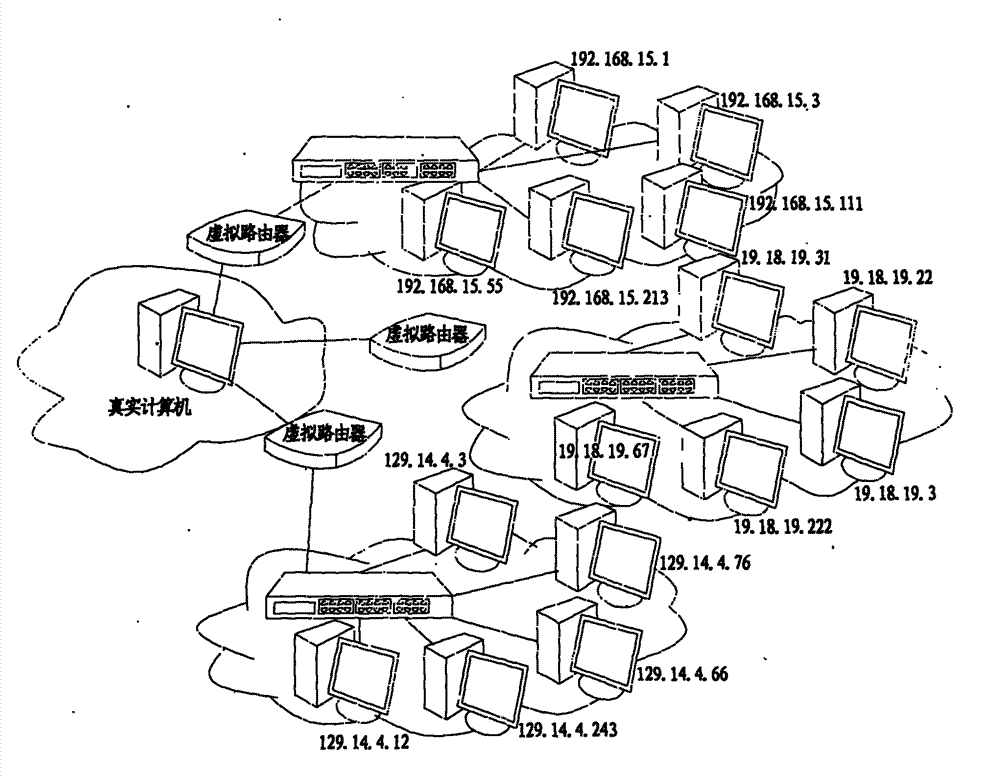
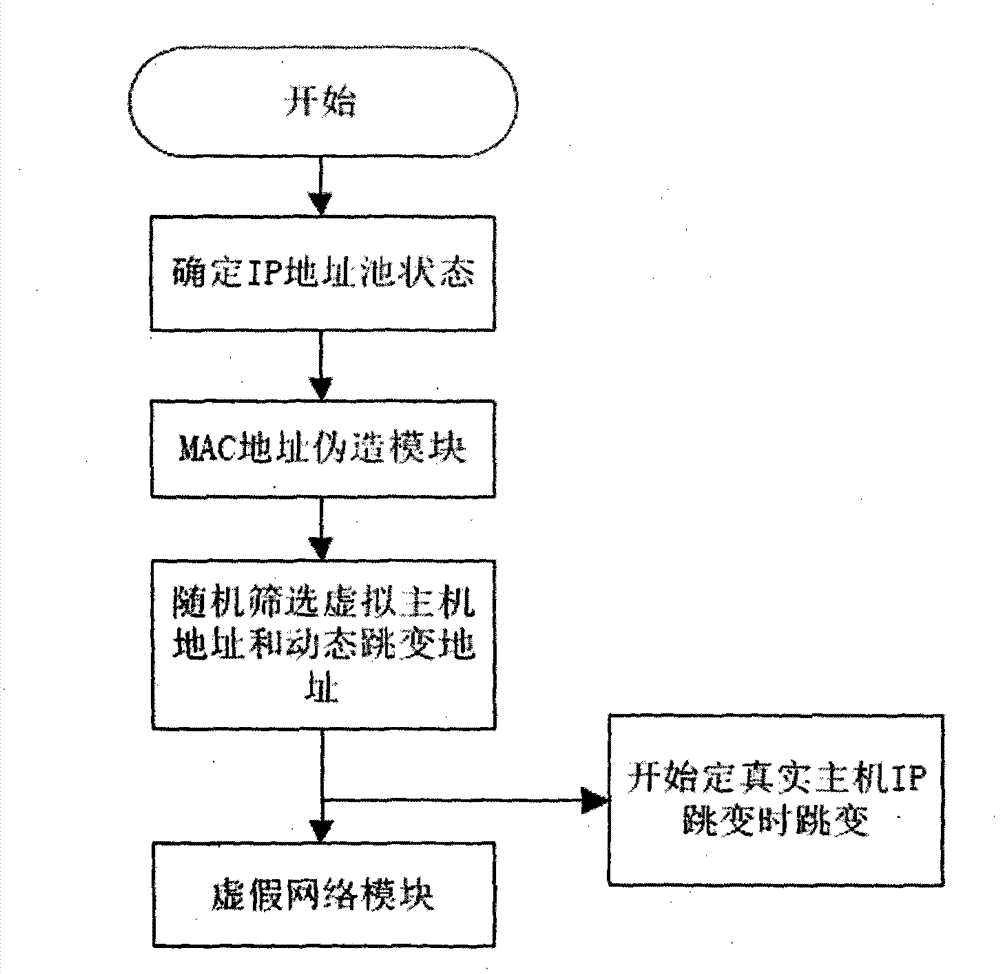
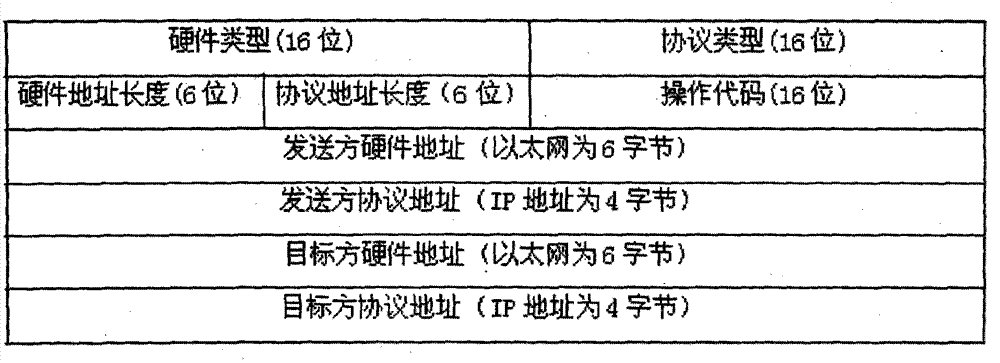
[0037]A computer network stealth method, the network stealth method includes adopting a passive processing strategy and an active processing strategy for detection data packets, the passive processing strategy includes judging the legality of data packets entering and leaving the computer, and detecting illegal The data traffic adopts the processing method of not accepting, not responding, not handing over to the normal protocol stack and writing bad records; the active processing strategy includes the following three methods: S1. When it is judged that the detection behavior is in progress, reply false information To confuse the explorer and increase the difficulty of attack; S2, forge false data traffic and network behavior of the real host, and disturb the sniffing behavior; S3, use the IP address of the real host as a jump element, and dynamically an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com