User verification method and device and electronic device
A user verification and electronic device technology, applied in the field of identity verification, can solve the problems of fuzzy fingerprints, biometric fingerprints are easily stolen and forged, and fingerprint identification is difficult to achieve the effect of improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
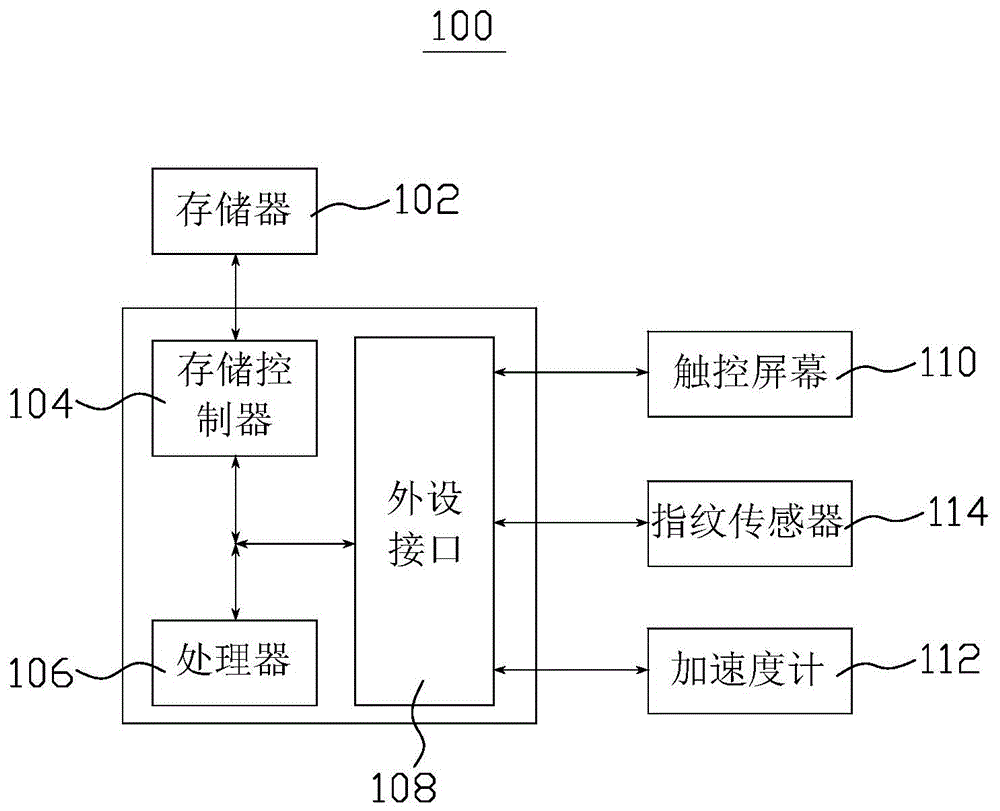
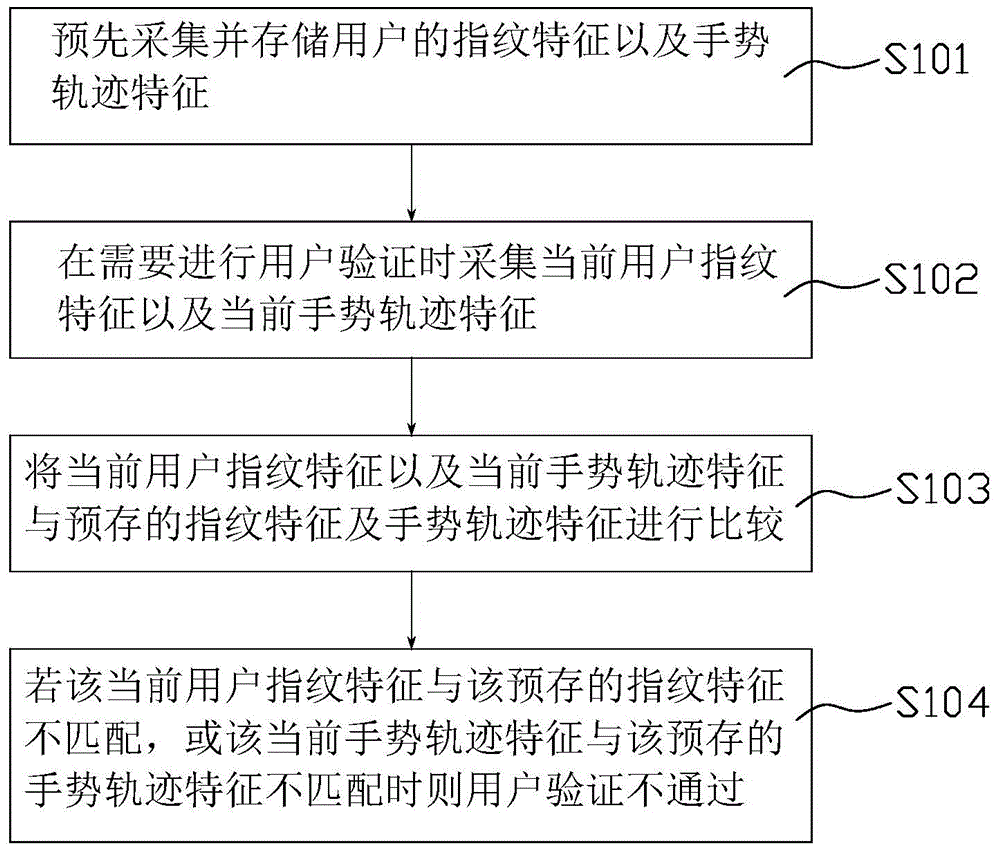
[0055] This embodiment provides a user authentication method, which can be used in the above-mentioned electronic device 100 . refer to figure 2 , the above method includes the following steps:
[0056] Setting step S101: Pre-collect and store the user's fingerprint features and gesture trajectory features.
[0057] For example, by collecting the fingerprint features of the user through the fingerprint sensor 114 or the touch screen 110 , the fingerprint features of one or more fingers may be collected. One or more gesture trajectory data of the user can be collected through the touch screen 110, and the trajectory characteristics of the gestures can be recorded.
[0058] Collection step S102: collecting the current user's fingerprint feature and the current gesture track feature when user verification is required.
[0059] The aforementioned occasions when user authentication is required refer to various occasions where user authentication is required, such as when unlock...
no. 2 example
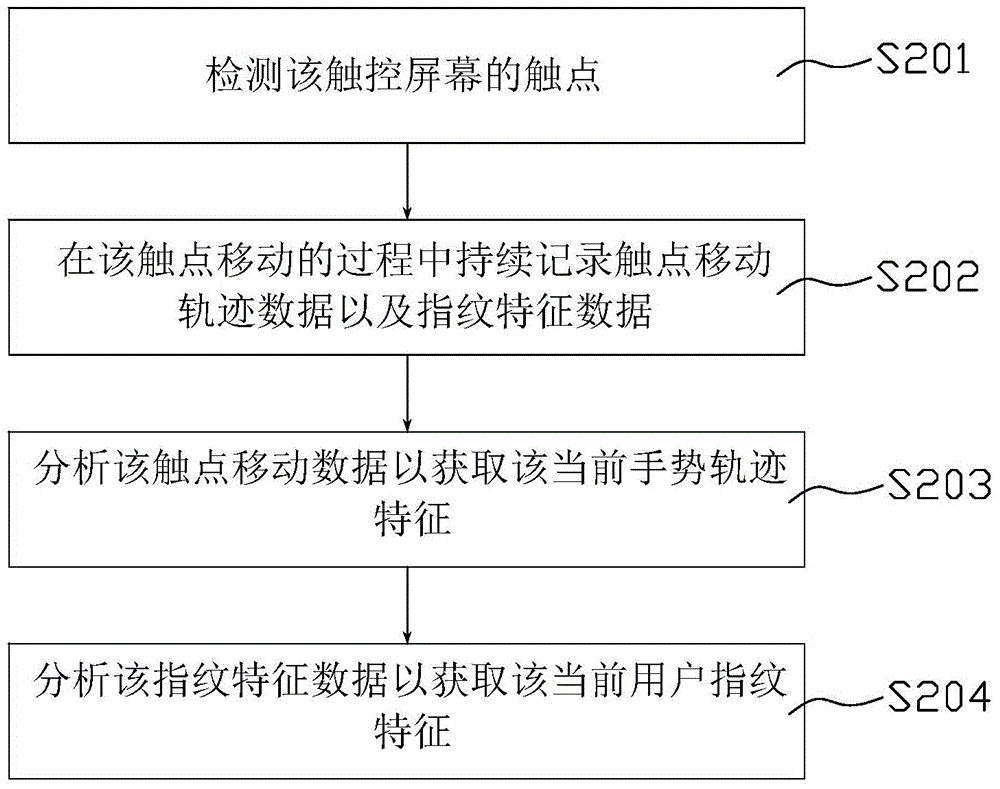
[0064] This embodiment provides a user authentication method, which can be used in the above-mentioned electronic device 100 . The method of this embodiment and figure 2 The method shown is similar, except that, see image 3 , the collection step S102 may specifically include the following steps:
[0065] Step S201 , detecting the touch points of the touch screen.
[0066] refer to Figure 4 , which is a schematic diagram of a finger 20 touching the touch screen 110 , and its contact point is 21 .
[0067] Step S202, continuously collect the position and fingerprint samples corresponding to the touch point during the movement of the touch point.
[0068] see also Figure 4 and Figure 5 , which is a schematic diagram of the contact 21 moving from the initial position to the final position. During this process, the position coordinates of the touch point and fingerprint samples are recorded at intervals (sampling interval). It can be understood that the sampling freque...
no. 3 example
[0083] This embodiment provides a user authentication method, which can be used in the above-mentioned electronic device 100 . The method of this embodiment and image 3 The method shown is similar, except that, see Figure 6 , the verification step S104 includes the following steps:
[0084] Step S301, judging whether the current user's fingerprint feature matches the pre-stored fingerprint feature; if they match, go to step S302; otherwise, the user verification fails.
[0085] Step S302, judging whether the current user's gesture feature matches the pre-stored gesture feature; if they match, go to step S303; otherwise, the user verification fails.
[0086] Step S303, judging whether the fingerprint feature of the current user matches the gesture feature of the current user; if they match, the user verification is passed; otherwise, the user verification is not passed.
[0087] For example, in step S101, fingerprint features of multiple fingers and multiple user gesture f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com