Android malicious application detection method and system based on multi-feature fusion
A malicious application, multi-feature fusion technology, applied in the field of network security, can solve problems such as high-dimensional feature analysis of rare sample families of malicious code, achieve efficient fusion processing, prevent overfitting, and reduce interference.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The present invention will be described in detail below with reference to the accompanying drawings and examples.
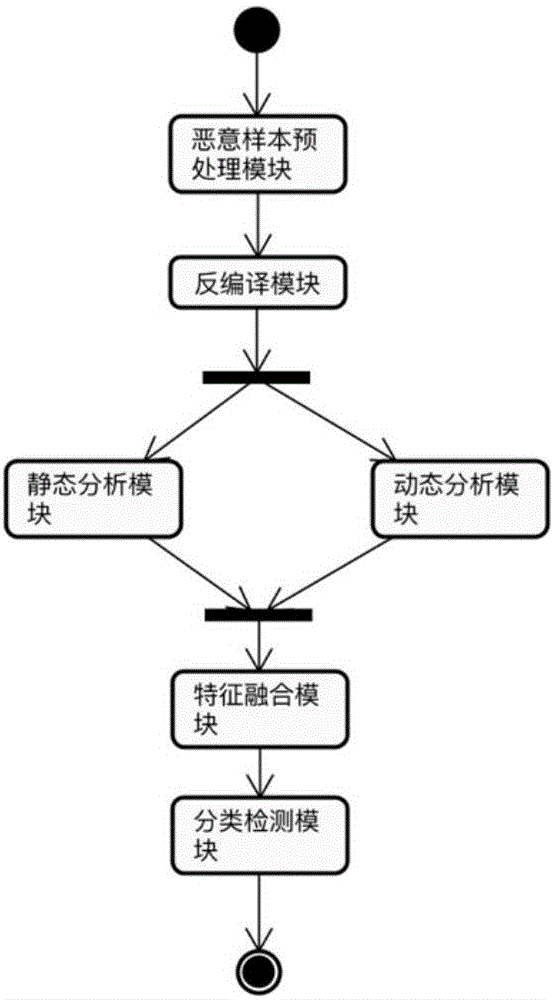
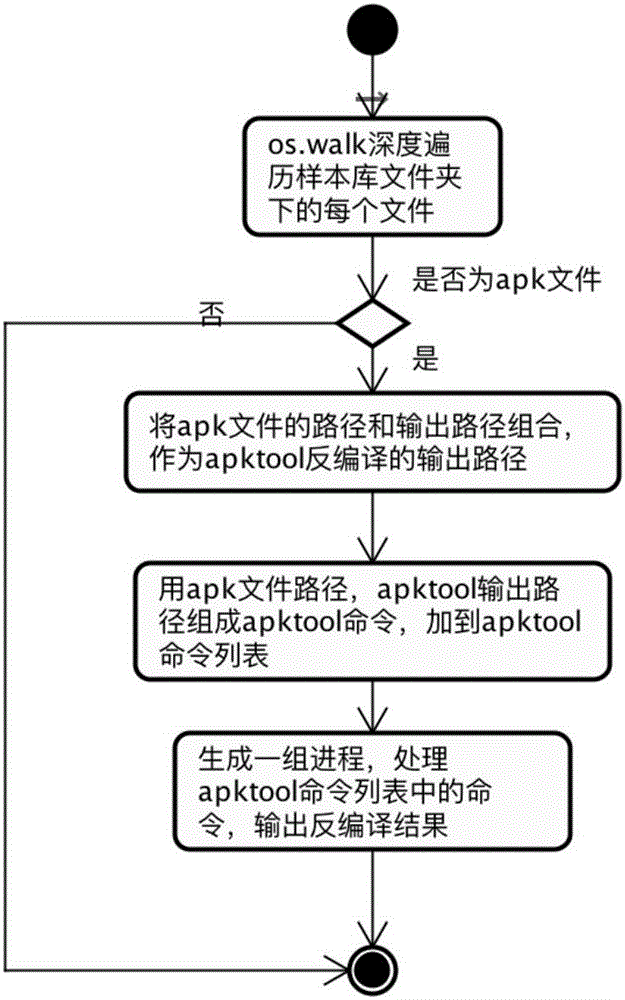
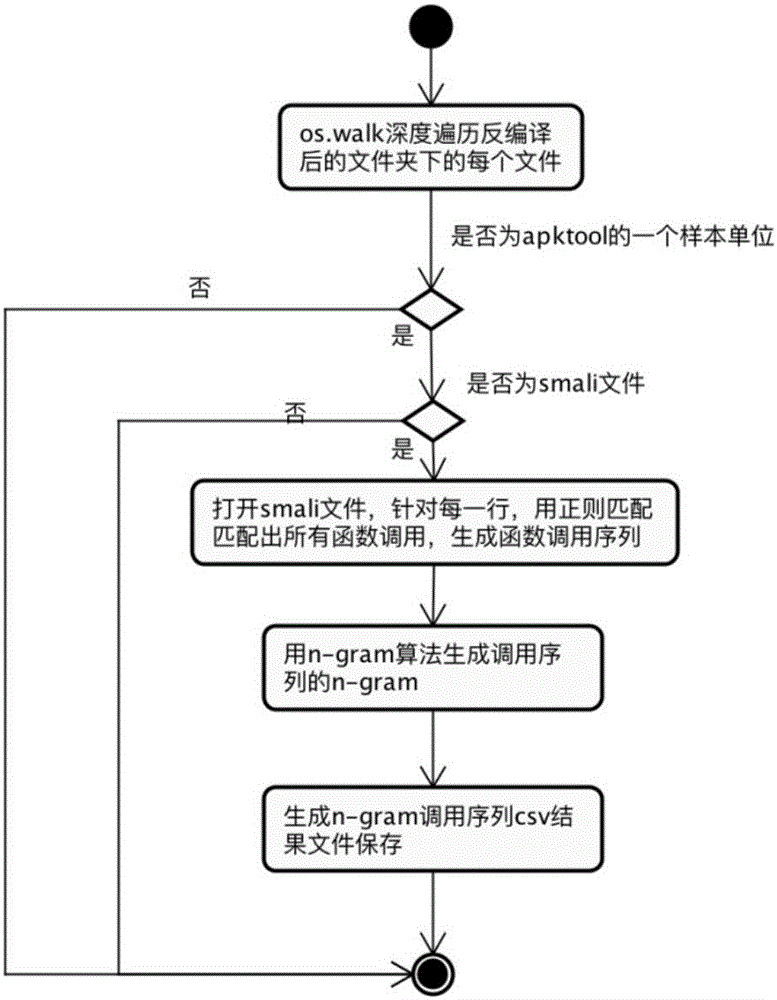
[0053] The present invention proposes a detection scheme for Android malicious applications based on multi-feature fusion, and its basic idea is: decompile Android malicious application samples to obtain decompiled apk files; extract static data from decompiled apk files Features; extract dynamic features by running the apk file in the Android emulator; for static features and dynamic features, use the text hash algorithm part of the local sensitive hash algorithm to perform feature mapping, and map to the low-dimensional feature space to obtain the fused Feature vectors; finally, based on the fused feature vectors, a classifier is trained using a machine learning classification algorithm; the classifier is used to classify and detect Android malicious applications.
[0054] In order to achieve the above solution, the present invention provides a multi-fea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com