Kernel level rootkit detection method and system in Andriod system
A technology of Android system and detection method, which is applied in the direction of computer security devices, instruments, calculations, etc., to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0076] The present invention will be further described in detail in conjunction with the following specific embodiments and accompanying drawings. The process, conditions, experimental methods, etc. for implementing the present invention, except for the content specifically mentioned below, are common knowledge and common knowledge in this field, and the present invention has no special limitation content.
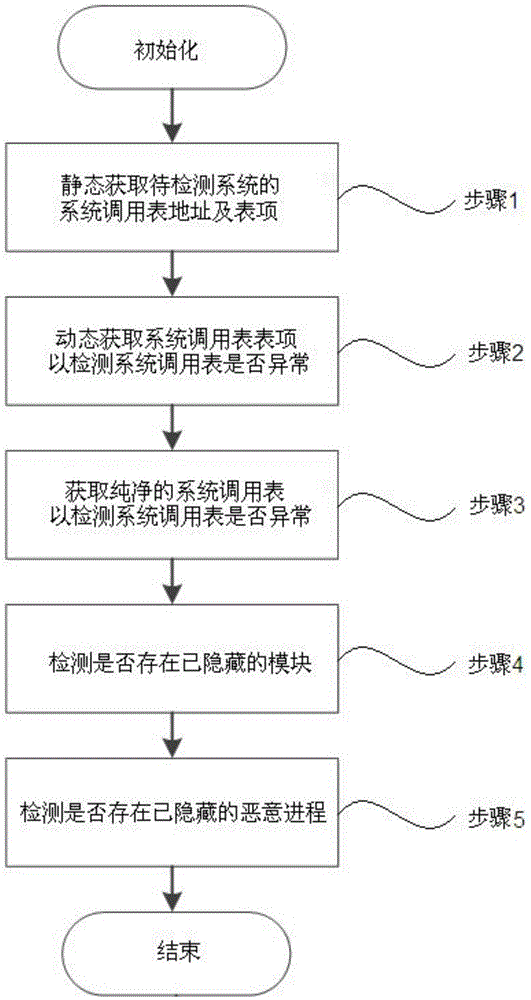
[0077] The technical solution of the present invention is based on the Android platform, is aimed at the characteristics of the ARM processor, avoids the singleness of the traditional detection method, thereby detects the rootkit that has invaded, and reports the rootkit with illegal behavior, such as figure 1 Specifically, the following steps are shown:
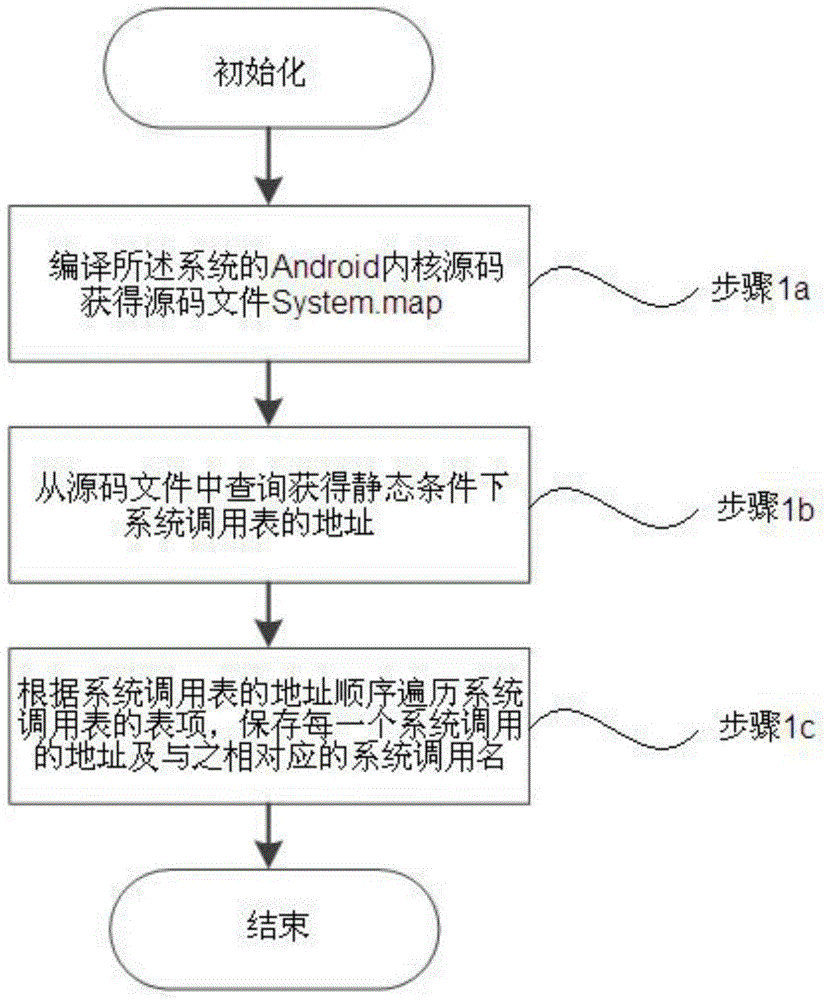
[0078] Step 1: statically obtain the address of the system call table of the system to be detected, and obtain the entries in the system call table;
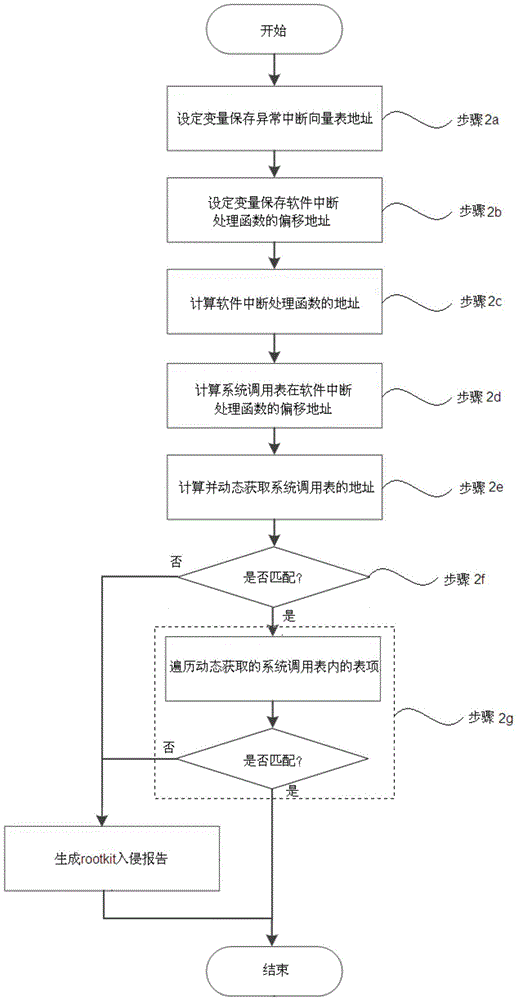
[0079] Step 2: Use the self-trap instruction SWI to enter the kerne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com