Method and equipment for detecting course
A process and equipment technology, applied in the field of detecting hidden processes at the kernel level of the computer operating system, can solve problems such as non-universal and insufficient detection methods, and achieve the effect of ensuring accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
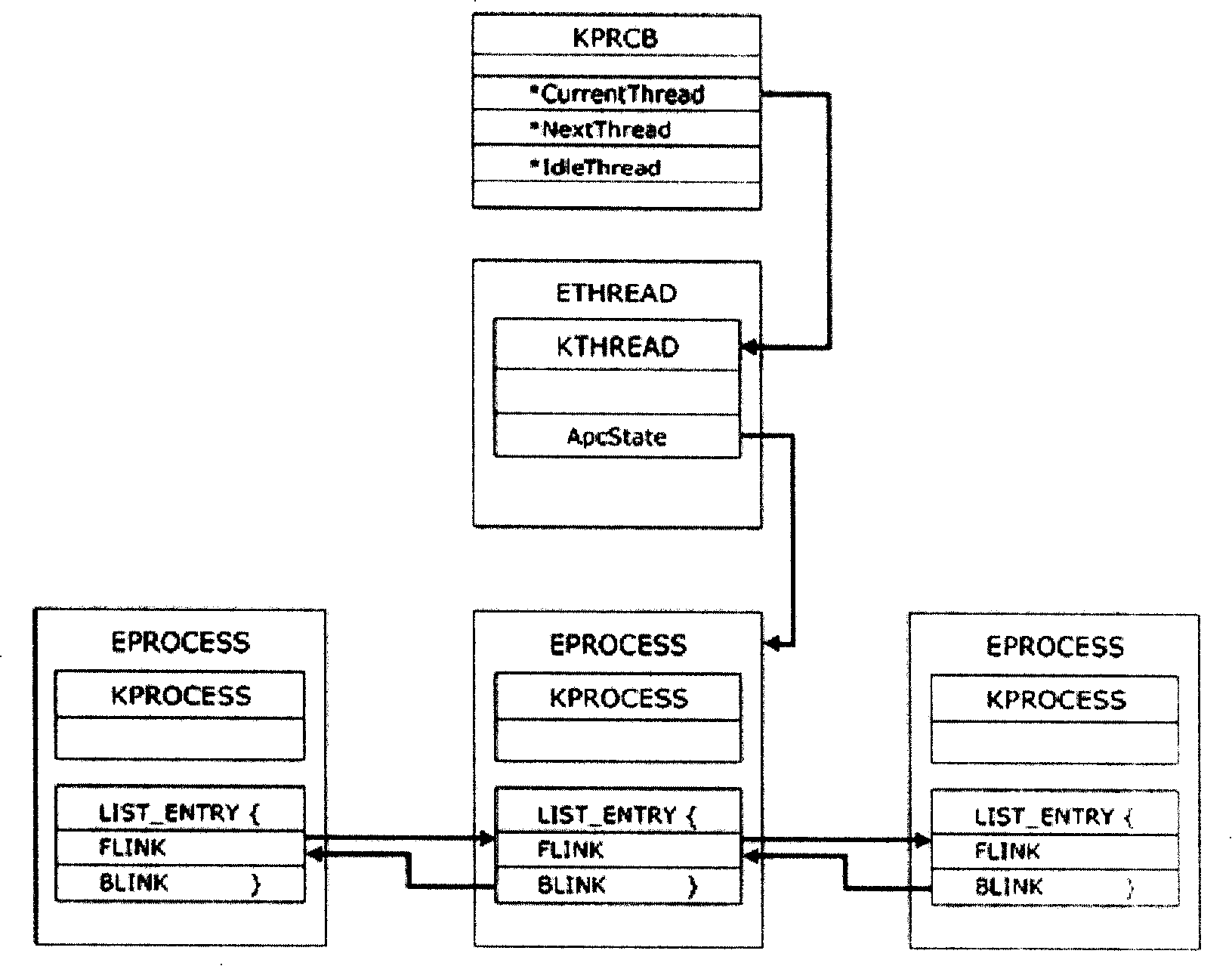
[0027] First, let's analyze the working principle of processes and threads. Modern operating systems generally run in a multi-task preemptive manner, and each process allocates a specific CPU time slice to achieve the purpose of execution, so that it looks like multiple tasks are running at the same time from a macro perspective. The time slice allocated by each process is determined by the CPU clock interrupt of the operating system. The system calls the interrupt to compare the time slice allocated by the current process. If the time slice is used up, it will use a specific scheduling algorithm based on the priority of each thread and other information. Select a new thread, then use its return value, an ETHREAD structure, as a parameter to complete the context switching function, thereby setting the parameters in ETHREAD, EPROCESS, and replacing the corresponding structure in the kernel processor control area (KPCRB) to After the thread switch is completed, the thread schedu...
Embodiment 2
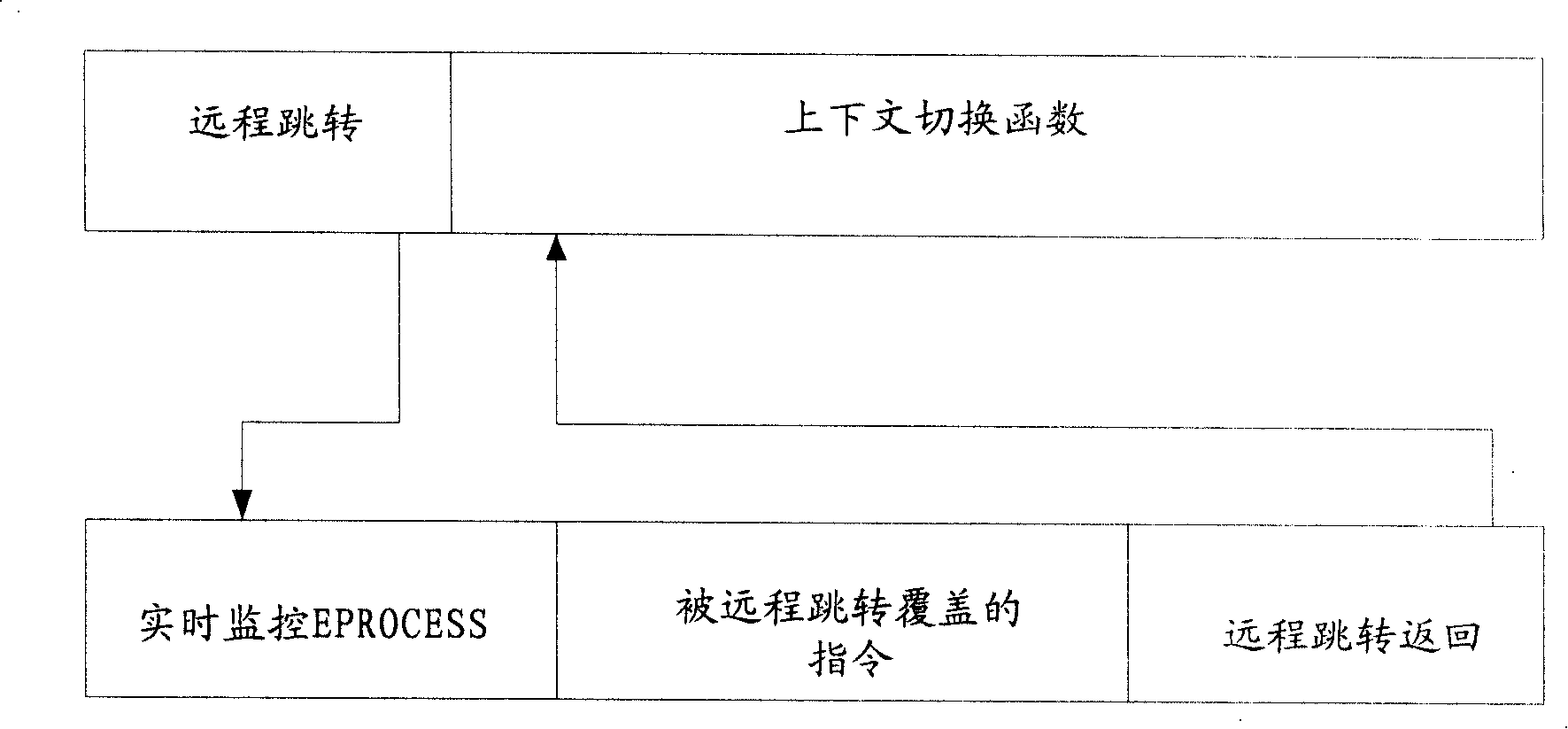
[0042] In order to prevent an attacker from performing a similar hooking behavior on the context switching function, on the basis of the first embodiment, the dynamic monitoring and updating of the remote jump and its alarm log are added to ensure the accuracy of detection.
[0043] The specific operation of the second embodiment is that after finding the address of the context switching function in the address space, first check the first few bytes, if it is found that it has been modified to a remote jump, record the alarm log, and restore it, and then Perform remote jump modification.
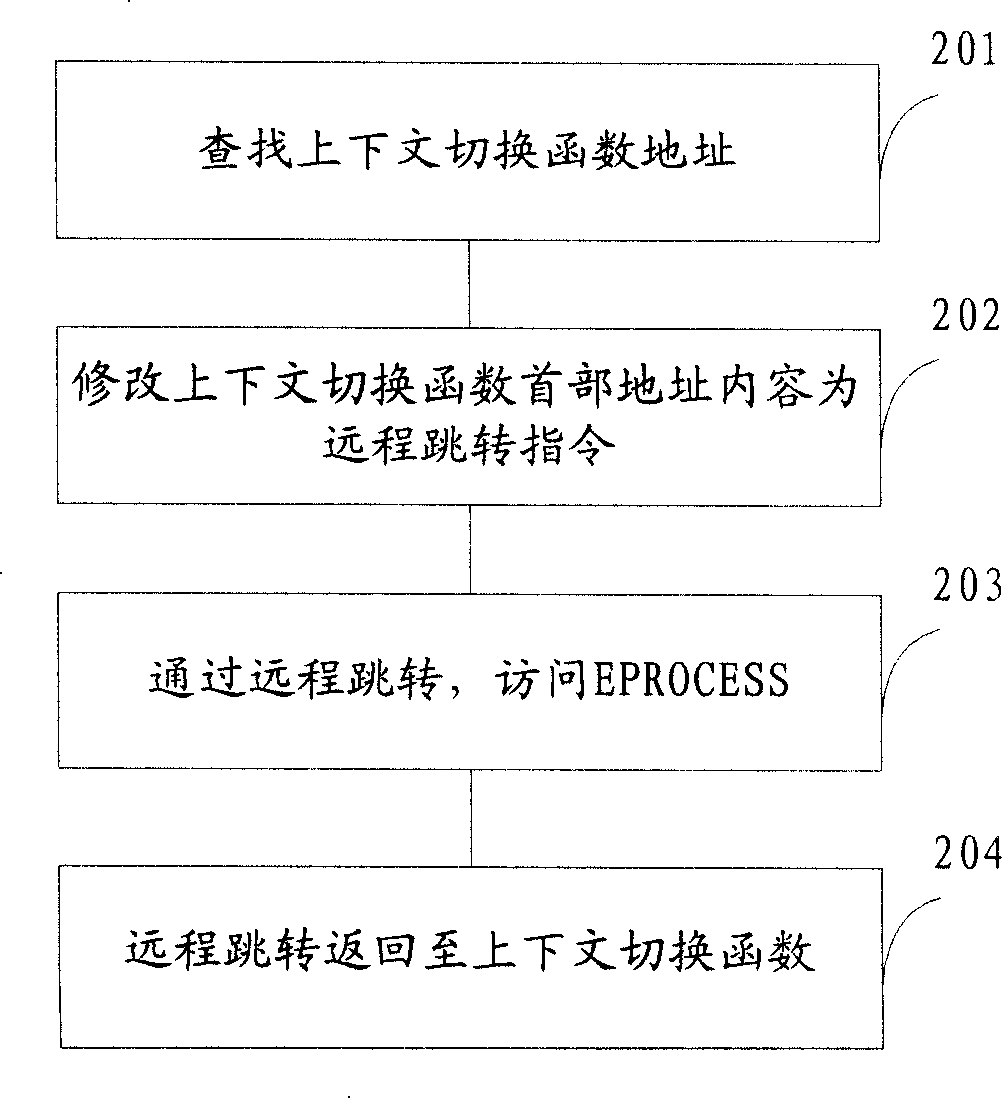
[0044] Such as Figure 4 Shown, embodiment two comprises:
[0045] Step 401: Find the address of the context switching function;
[0046] Step 402: Check whether the byte in front of the address of the context switching function has been tampered with, if so, execute step 403, otherwise, execute step 404;
[0047] Step 403: restore the tampered address to its original state;
[0048] Ste...
Embodiment 3
[0053] The above two embodiments can accomplish the purpose of detecting the current process, but further judgment is needed to determine which malicious processes are hidden by the DKOM.
[0054] Any process must interact with the operating system through the API, and most of the interactions are passed to the kernel through system calls, and those processes that do not use any API can not play any role in the system, so you can use the system call manager to Intercept the system call, and then get the EPROCESS of the current process.
[0055] On the basis of embodiment one or embodiment two, embodiment three compares the process information such as detected process ID and process image file name with the current process ID and process image file name obtained by calling API, if inconsistent, It means that there is a hidden process based on the kernel level, that is, there is a DKOM rootkit.
[0056] In order to ensure that the image files of the real-time detection unit and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com