Security verification method during kernel operation of operation system
An operating system and safety verification technology, which is applied in the safe operation, prevention and removal of the operating system kernel, and the detection of computer operating system kernel viruses, which can solve problems such as counterfeiting security software and being unable to see files infected by viruses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
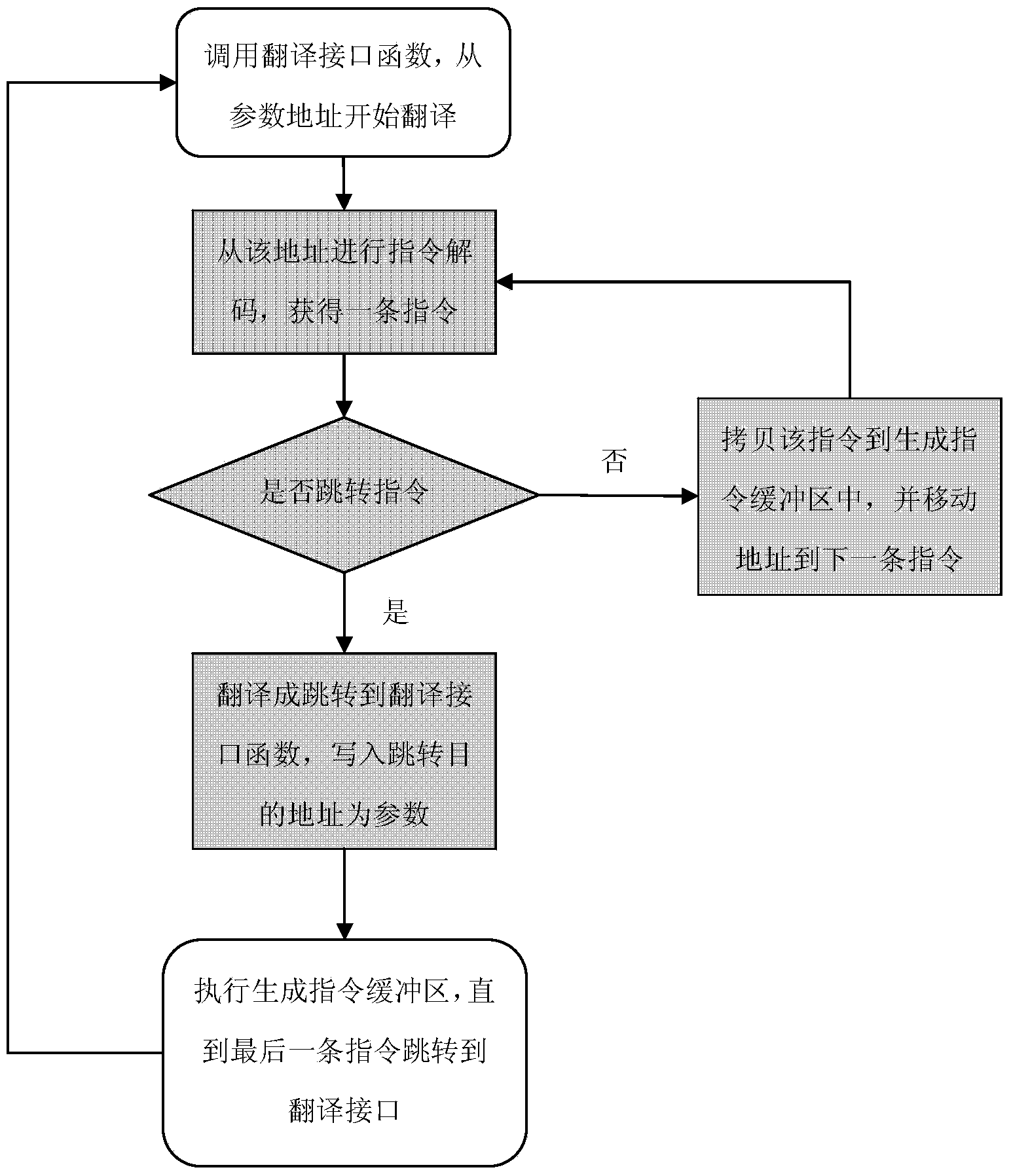
[0042] The present invention's original method for detecting the legitimacy of the kernel module at runtime only determines whether there are illegal instructions running in the kernel by detecting the identity between the instructions actually running in the kernel and the executable files of the confirmed legal kernel module, so as to ensure The high security of the kernel achieves the purpose of thorough detection and complete prevention of kernel virus intrusion.
[0043] A security verification method for operating system kernel runtime, comprising the following steps:
[0044] Step 1] Confirm the legitimacy of all kernel module files of the target OS:
[0045] Statically confirm the legality of all kernel module files of the target operating system, and save the integrity verification information of all legal kernel modules in the target operating system;
[0046] Step 2] Verify the legitimacy of the loaded modules in the kernel:
[0047]By enumerating the kernel modul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com