System rogue program detecting method and device
A malicious program and malicious technology, which is applied in the field of system malicious program detection for rootkit-type stubborn Trojans, can solve the problems of low detection accuracy of Trojans, leakage of viruses and failure to identify hidden Trojans, etc., so as to improve detection accuracy and security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
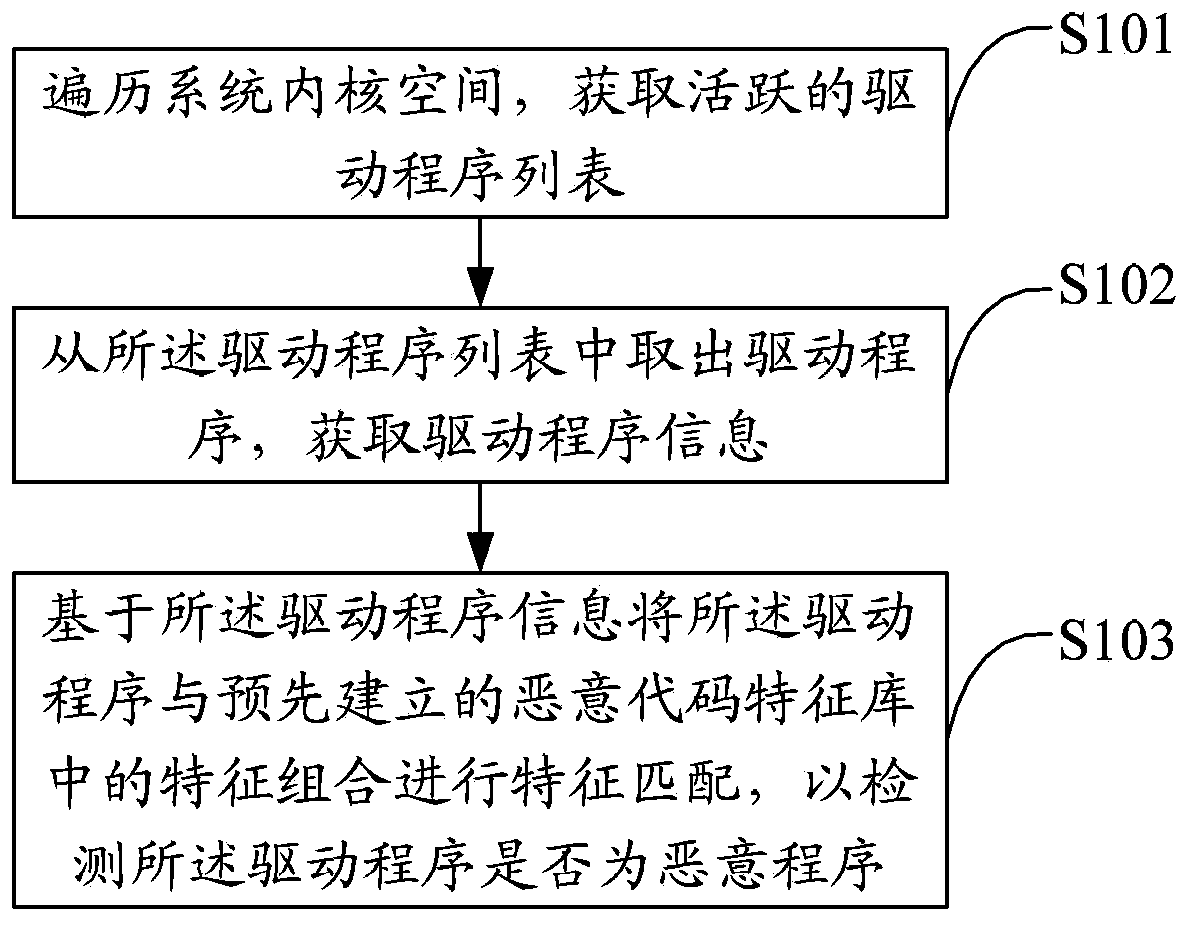
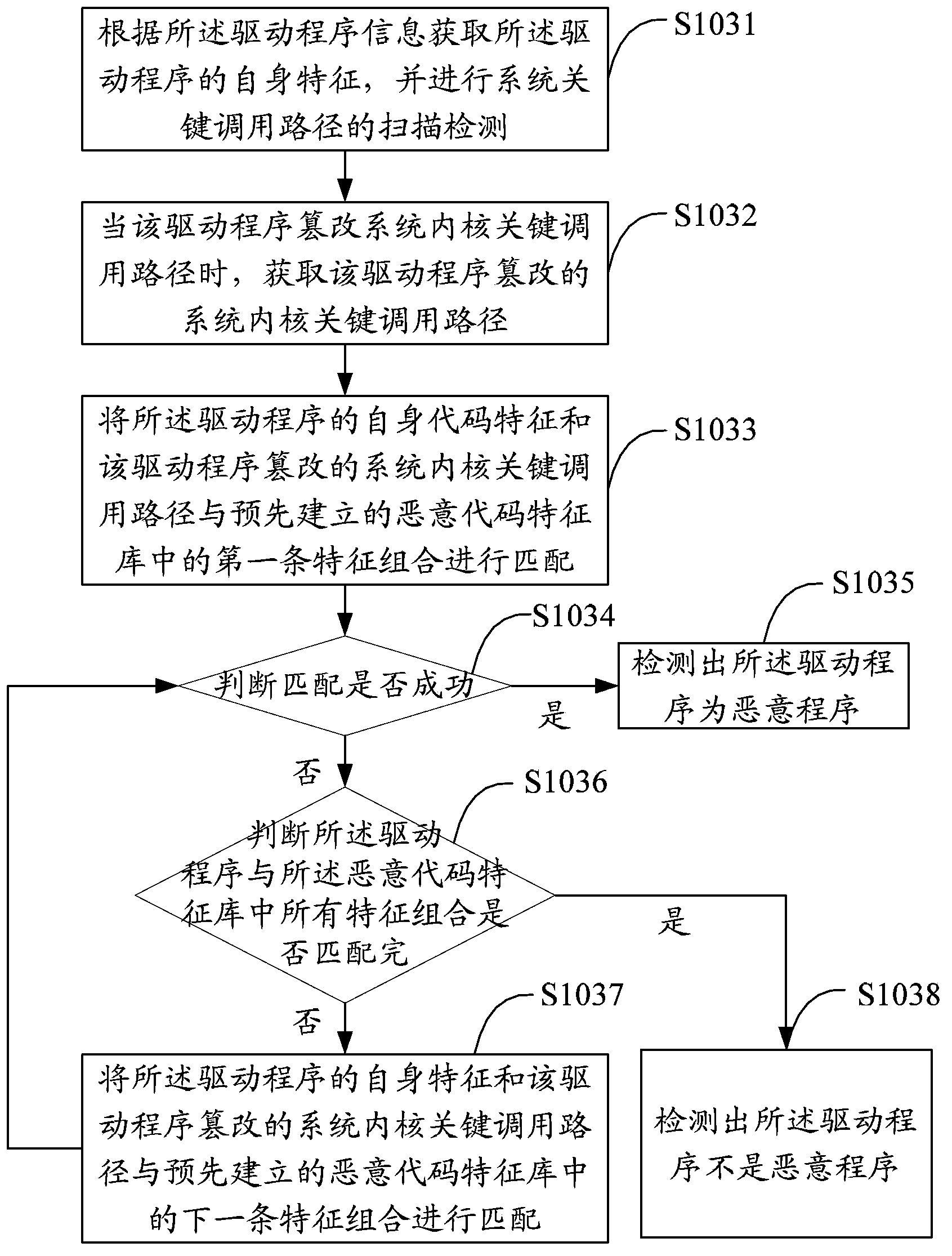
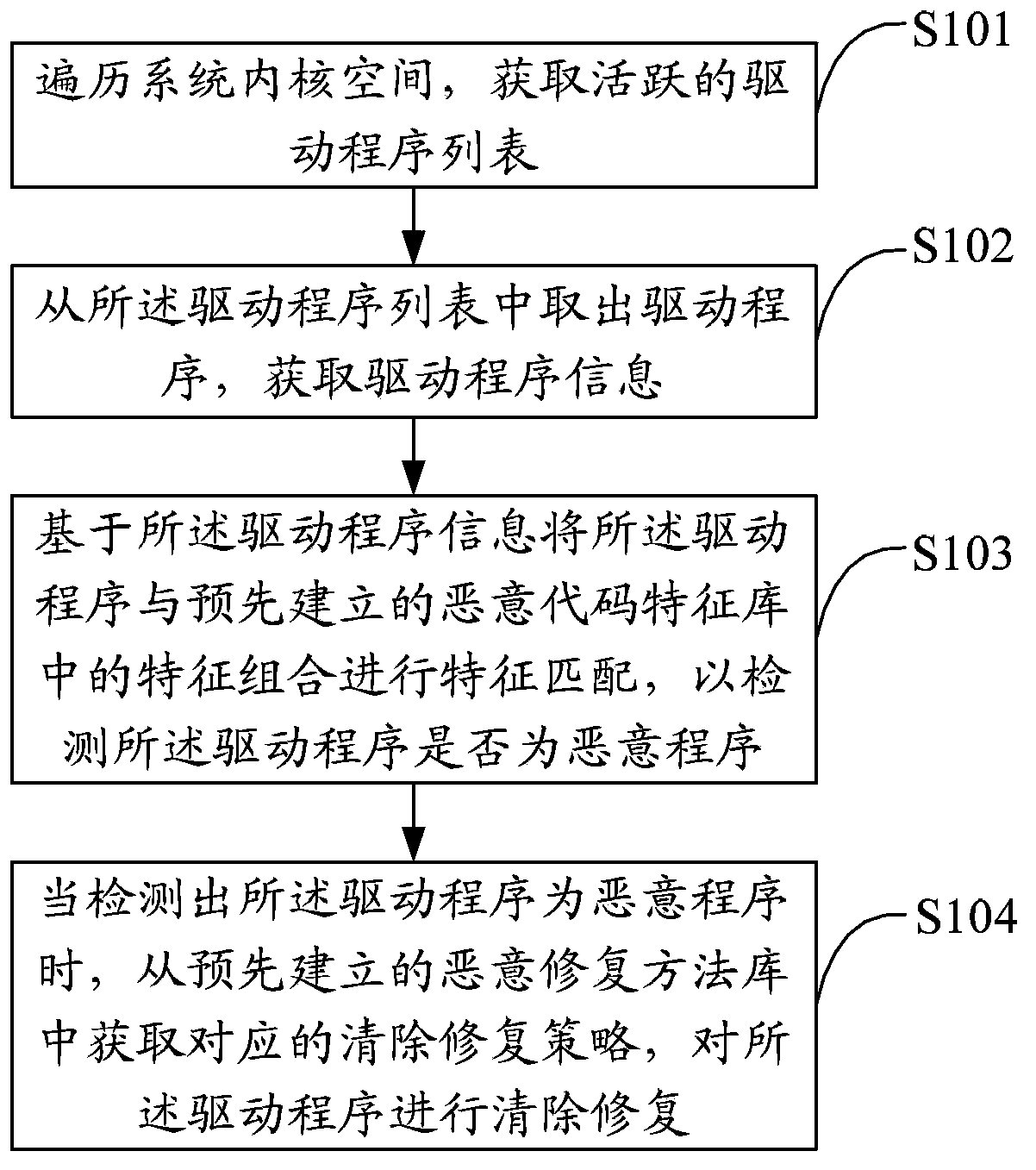
[0032] The solution of the embodiment of the present invention is mainly to: obtain the active driver program in the system kernel space, perform feature matching on the driver program information and the feature combination in the malicious code feature library, check the security status of the system kernel at the driver level, and detect the security status of the system. Whether the key call path has been tampered with and destroyed by stubborn malicious programs, and further select the corresponding removal and repair strategy for rootkit Trojans and other malicious programs to clear and repair, so as to improve the detection accuracy of system malicious programs and improve system security.
[0033] Such as figure 1 As shown, the first embodiment of the present invention proposes a system malicious program detection method, including:
[0034] Step S101, traversing the system kernel space to obtain a list of active drivers;
[0035] This embodiment uses the kernel featu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com