Covert communication method under cloud computing environment
A cloud computing environment, covert communication technology, applied in the field of information security, can solve problems such as difficult to detect covert communication methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] Below in conjunction with accompanying drawing, the present invention will be further described through embodiment, but does not limit the scope of the present invention in any way.
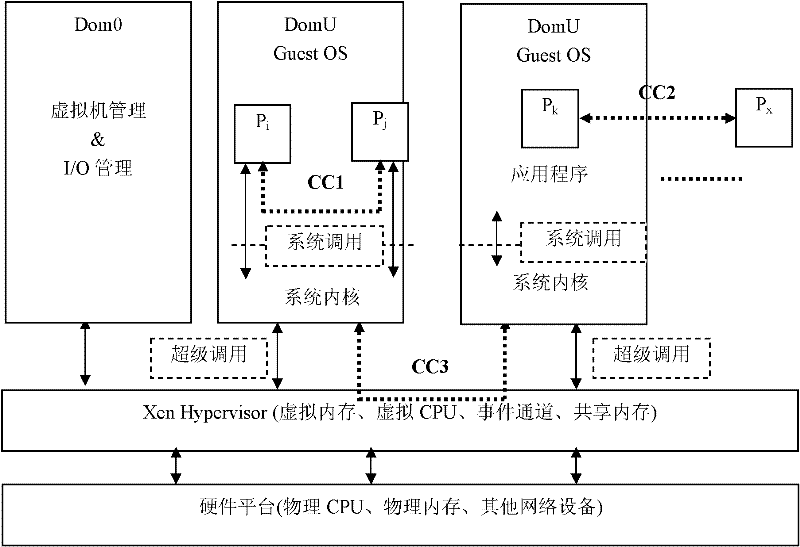
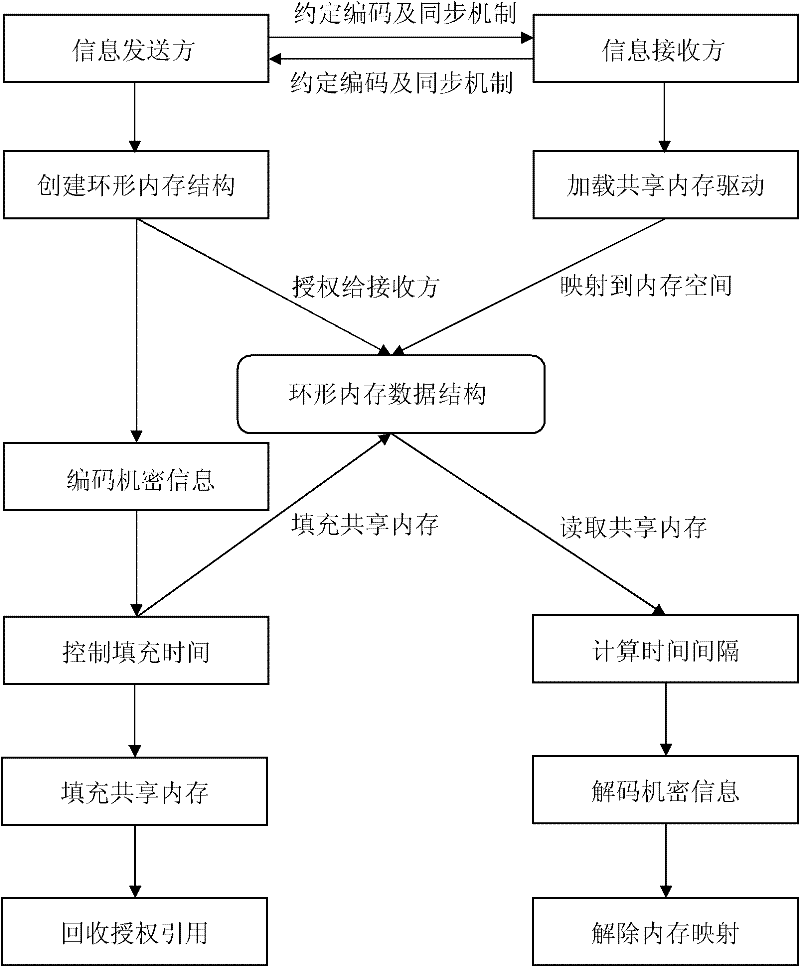
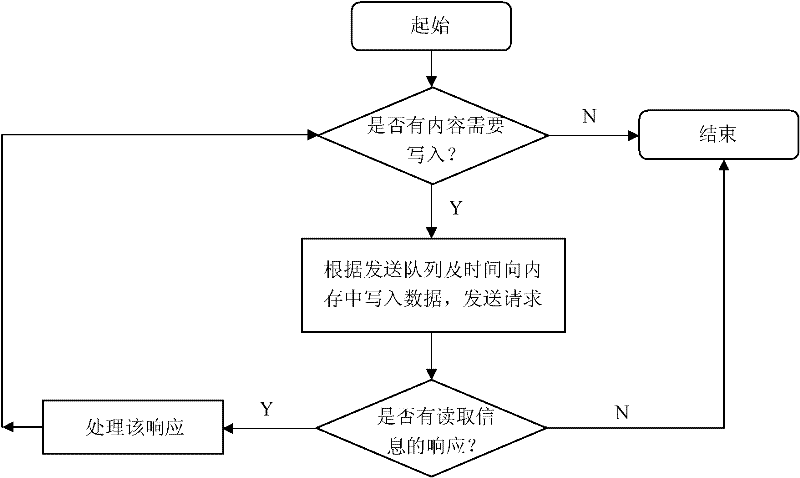
[0070] The present invention is a covert communication method for cloud computing virtualization platform, the overall process is as follows figure 2 As shown, taking the attack on the Xen virtual machine as an example, it specifically includes:
[0071] 1) The sender P i and receiver P j Agree on the encoding mechanism and synchronization mechanism for the transmission of confidential information. Agreed information includes confidential information transmission start / stop identifier S start and S end , and the binary encoding method of confidential information, and use T0 and T 1 represent the binary symbols 0 and 1 respectively and T 0 1 ,like Figure 4 shown. In this example, S start and S end They are represented by '11110000' respectively, that is, when '11110000' appears ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com