Network covert channel detecting method
A detection method and covert channel technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., to achieve the effect of improving reliability and reliable detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to clearly describe the implementation process of the present invention, specific embodiments are described step by step below.
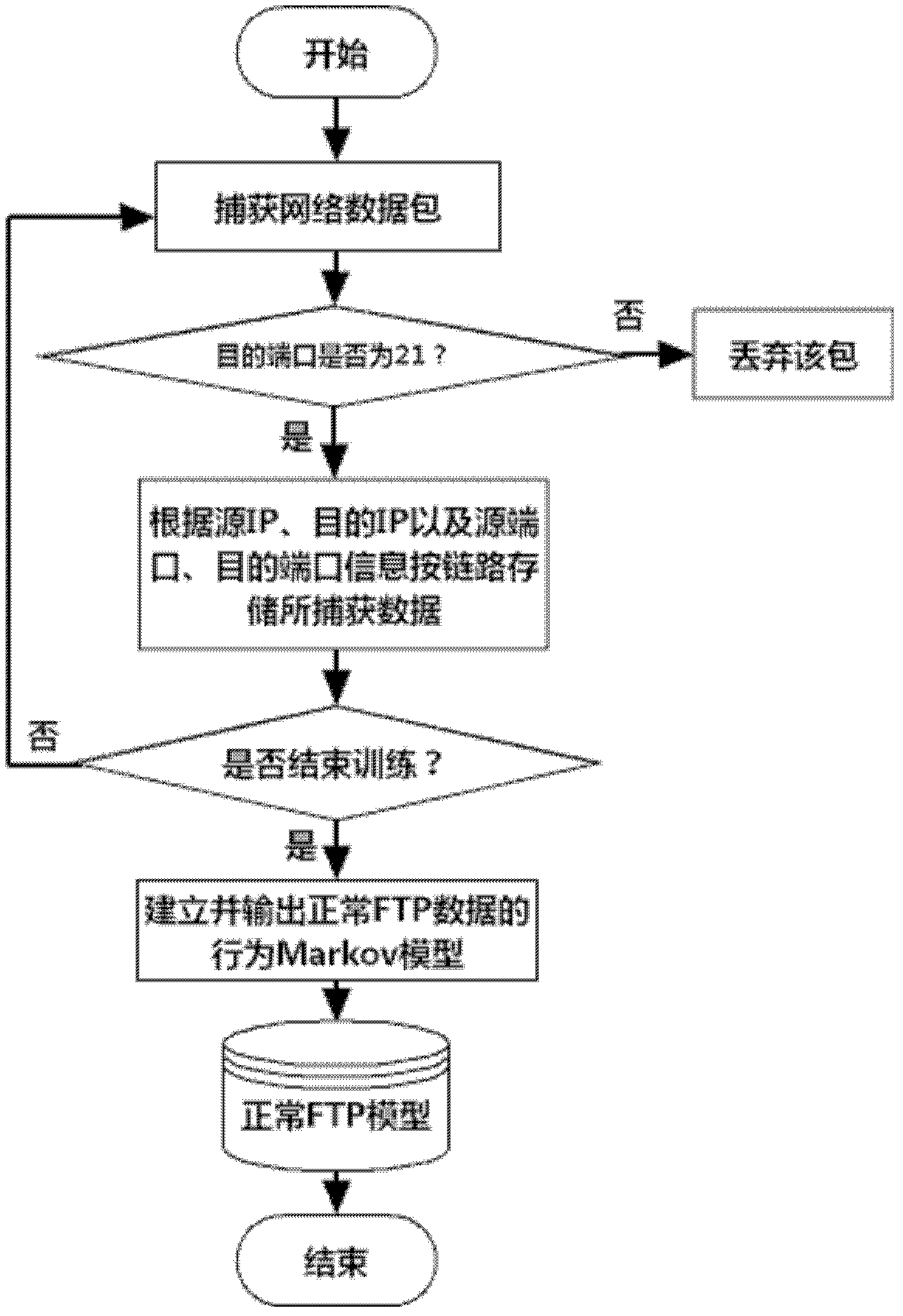
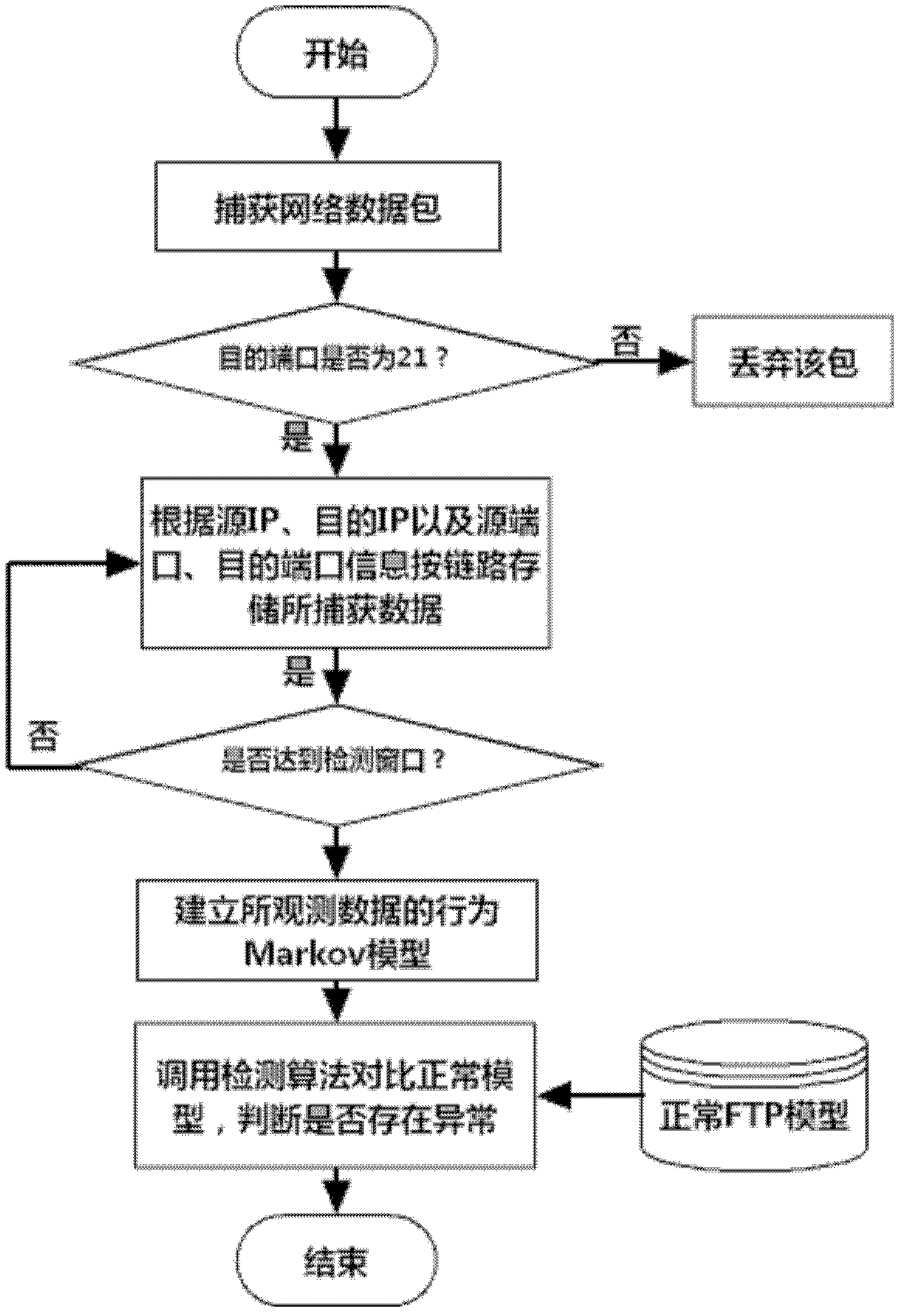
[0034] (1) Data acquisition
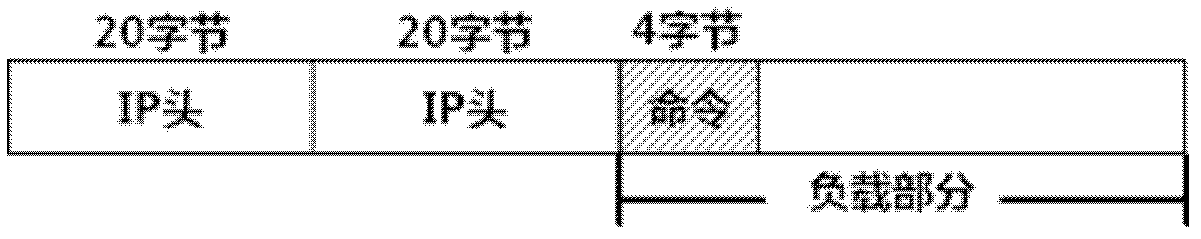
[0035] Using the packet capture program designed based on Winpcap, by setting the destination port, and storing the FTP data packets on a single link according to the data of the source IP, destination IP and source port, and then extracting its command information to form a command sequence for FTP communication Denote as C=[C 1 , C 2 ,...,C m ], where C m Extract FTP commands for a single link.
[0036] (2) Model establishment
[0037] The above obtained FTP communication command sequence C=[C 1 , C 2 ,...,C m ] is transformed into its corresponding behavior mode and recorded as o=[o 1 , o 2 ,...o n ], and use the Markov chain method to model the obtained n behaviors, and obtain the Markov model as M=(P, Q), where P is the transition probability matrix of the n behaviors, and Q is the FTP beha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com