Method for hiding Chebyshev neural network chaotic digital watermark information
A Chebyshev, neural network technology, applied in the field of information security, can solve the problems of restricting the application of sequence passwords and the time can not be calculated theoretically, to increase the difficulty and improve the security effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
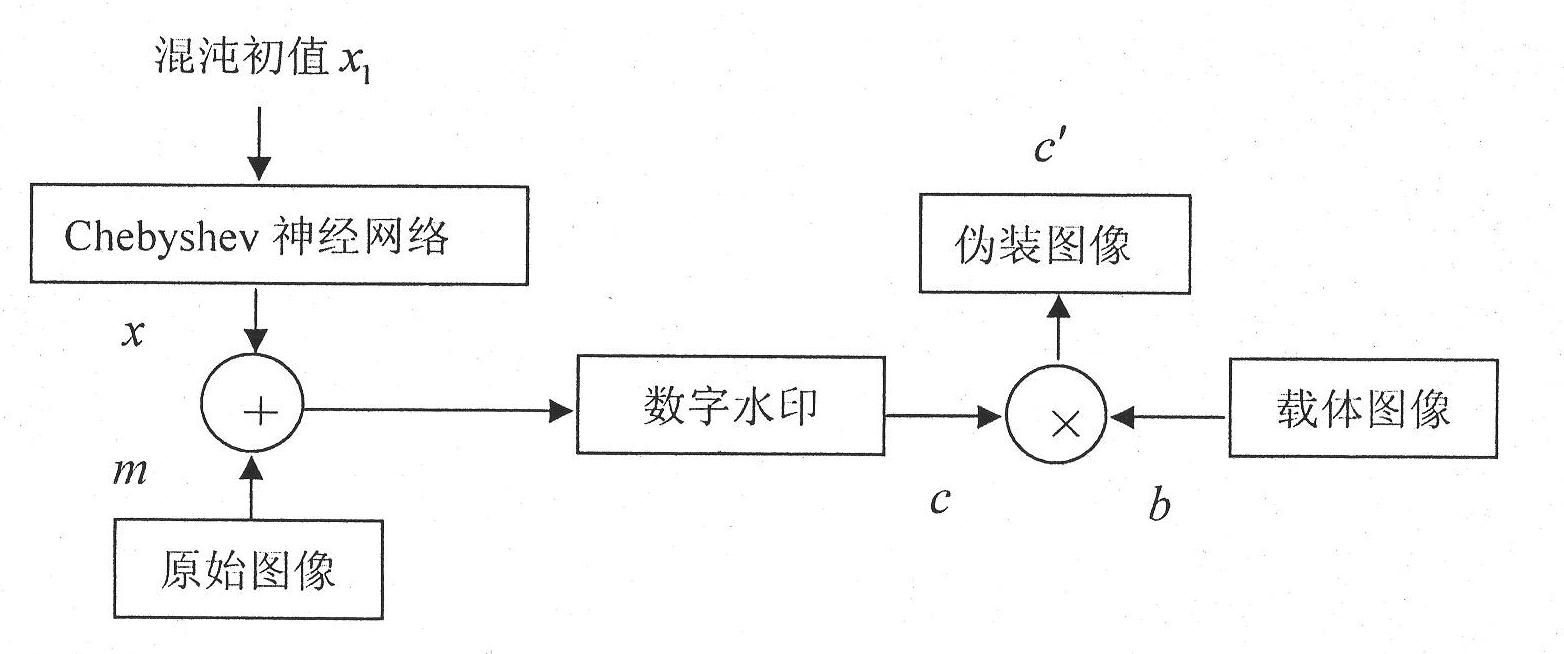
[0034] Chebyshev neural network chaotic digital watermark information hiding method of the present invention:
[0035] 1. The sender performs the following operations:
[0036] (1) Generate chaotic sequence
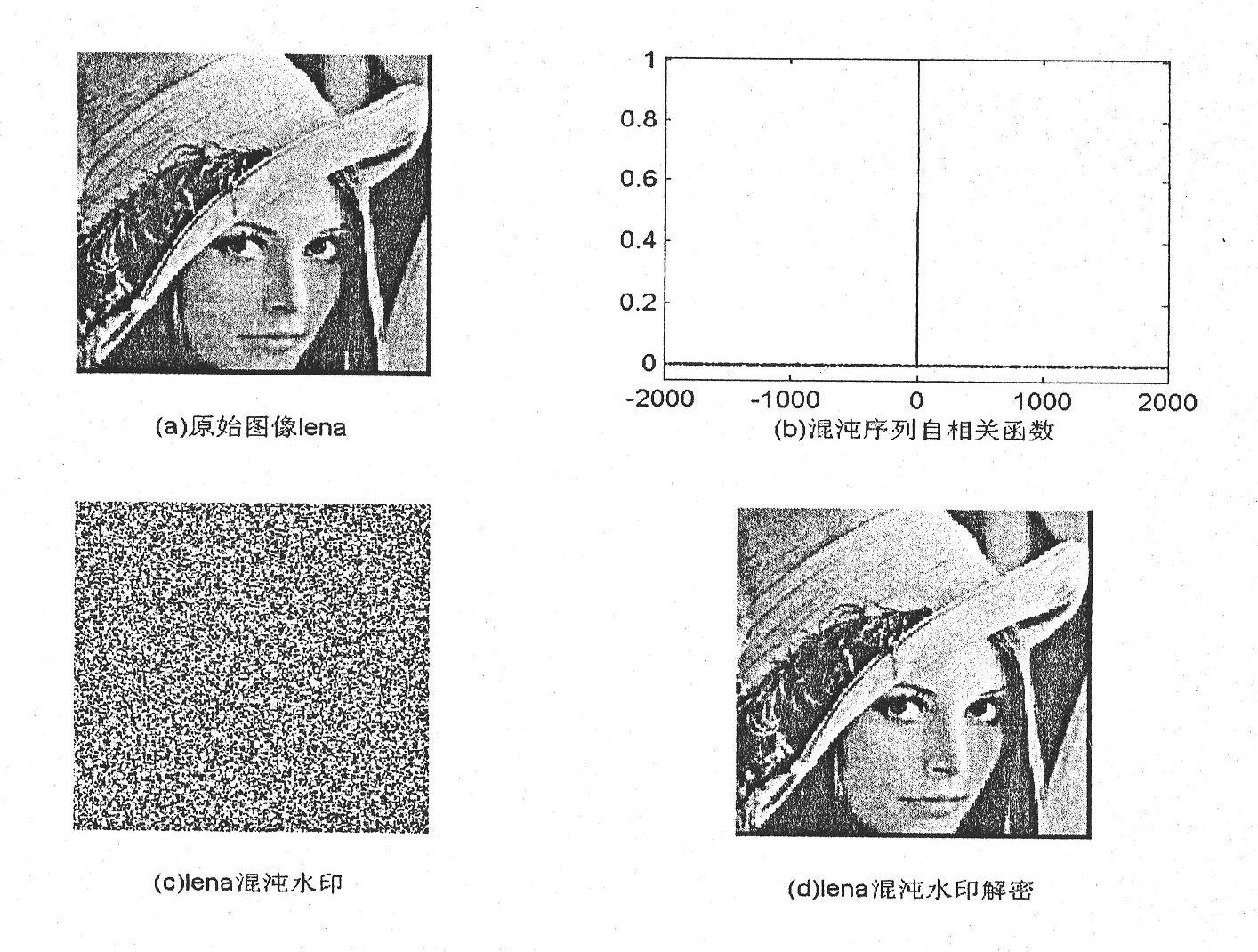
[0037] For the Logistic chaotic sequence x k+1 =μx k (1-x k ); k=1, 2, ..., s, take the standard Logistic chaos μ=4.0, let the initial value of the chaos x 1 =0.12, the number of samples s=100, the available training samples are (x t , x t+1 ), t=1, 2, ..., 100;
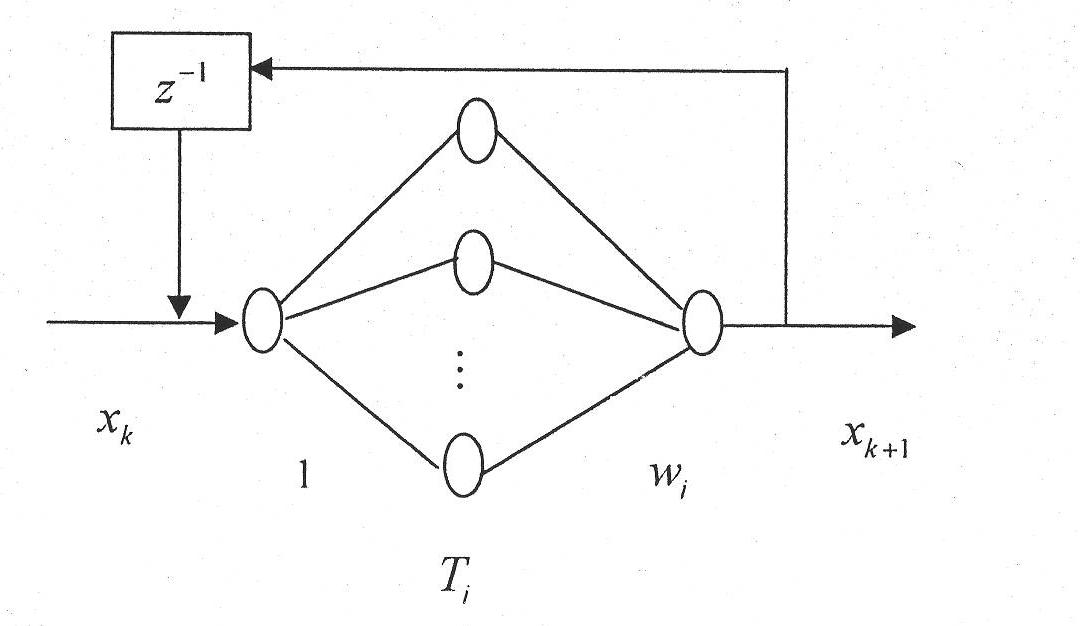
[0038] (2) Construct a neural network model
[0039] exist figure 1 In the shown neural network, the number of neurons in the hidden layer is assumed to be n=3, the learning rate η=0.1, and the initial weight is randomly selected. For training samples (x t , x t+1 ), t=1, 2,..., 100 After 300 times of learning, the training index J=3.2517×10 -6 , the final weight vector W=[-2, 4, -2], indicating that the neural network model is constructed successfully;
[0040] (3) Information encryption
[0041] T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com