Transmitting/receiving method for secret communication
A receiving method and technology of sending method, which are applied in the field of sending/receiving of stealth communication, can solve the problems of low security, easy to be attacked, etc., and achieve the effect of good concealment, good security and good secrecy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
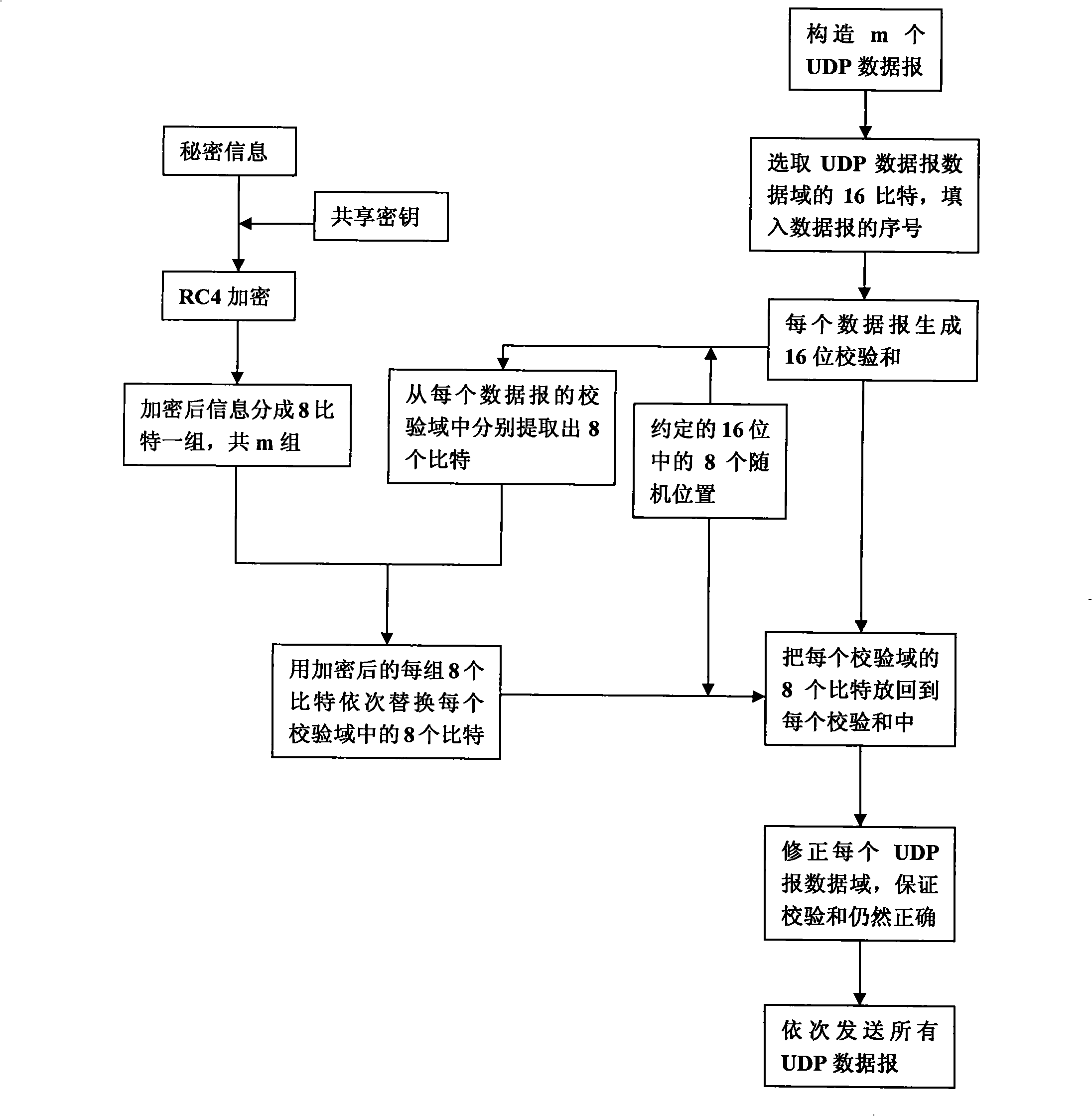
[0042] The content of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0043] 1. Use the data unit of the TCP protocol as the concealed carrier (see attached figure 1 And attached figure 2 ) method steps are:
[0044] (1) Encrypt the secret message. The key is shared by the sender and the receiver, the cryptographic algorithm uses RC4, and the encrypted information is divided into 8-bit groups, a total of m groups.
[0045] (2) Construct m TCP segments. The source port, destination port, serial number and other header fields and data fields of each TCP segment are filled with corresponding correct values, and a 16-bit checksum is generated. The checksum generation process is to calculate the checksum with the header, data and pseudo-header of the TCP segment. When calculating, first divide the part to be checked into a sequence of 16-bit words, and set the checksum to Zero, after adding all 16-bit words using...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com