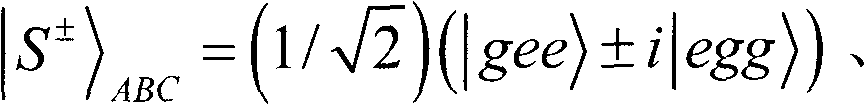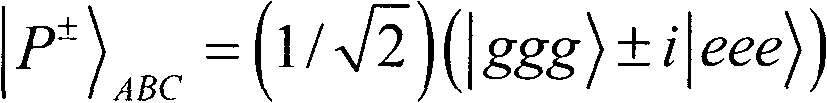Quantum steganography protocol based on quantum electrodynamics (QED)
A quantum steganography, protocol technology, applied in key distribution, can solve complex problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
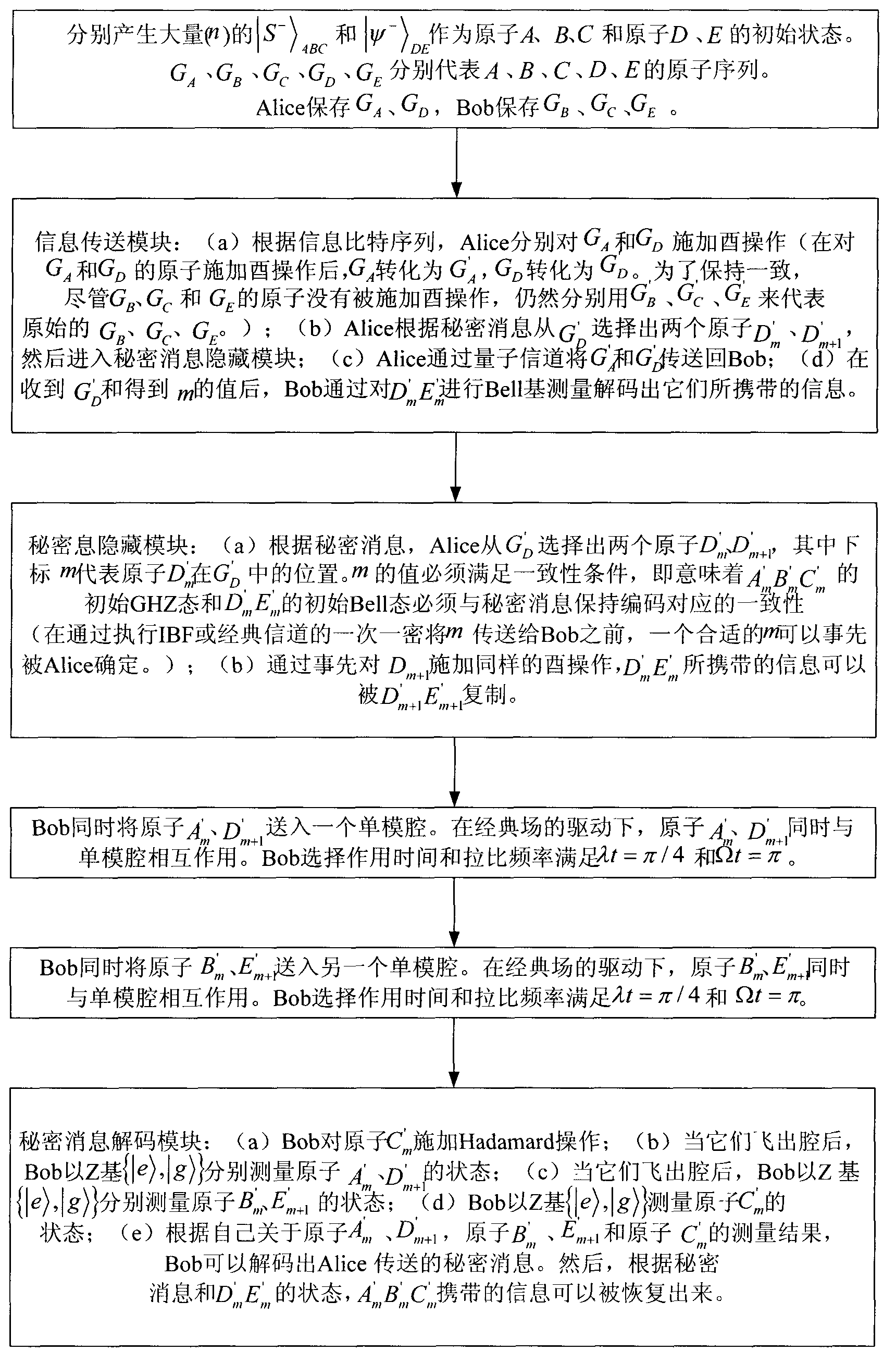
[0065] 1. Application example of quantum steganography protocol
[0066] Suppose the 2-bit secret message Alice wants to send to Bob is 00. Alice produces a message sequence...11 11 ...00 00 ...10 01 ...01 10 ...to Bob (the information is divided by 2 bits, because each U j represent 2 bits of information). Suppose the group numbers of 11, 00, 10, and 01 are 6, 10, 15, and 19, respectively. In S3, Alice can make m equal to 6, 10, 15, and 19 respectively to satisfy the consistency shown in Table 1. If m=6, A' 6 B' 6 C' 6 will be |S + >, D' 6 E' 6 will be |ψ + >. Correspondingly, the secret message 00 passes through A' in chamber QED 6 B' 6 C' 6 and D' 7 E' 7 Between entanglement exchange and Hadamard operations for teleportation. If m=10, 15, 19, using the same method, the secret message 00 can also be sent to Bob. Since it is used as an auxiliary Bell state to help hide secret information, D′ 7 E' 7 Cannot transmit information like other normal Bell stat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com