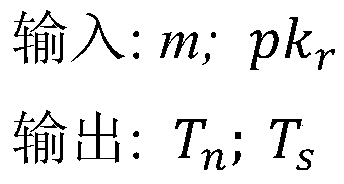Data covert transmission method based on block chain network
A transmission method and data concealment technology, applied in digital transmission systems, transmission systems, data processing applications, etc., can solve the problems of low concealment, inability to solve group leakage, poor scalability, etc., achieve high concealment, avoid statistical Regular, scalable effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
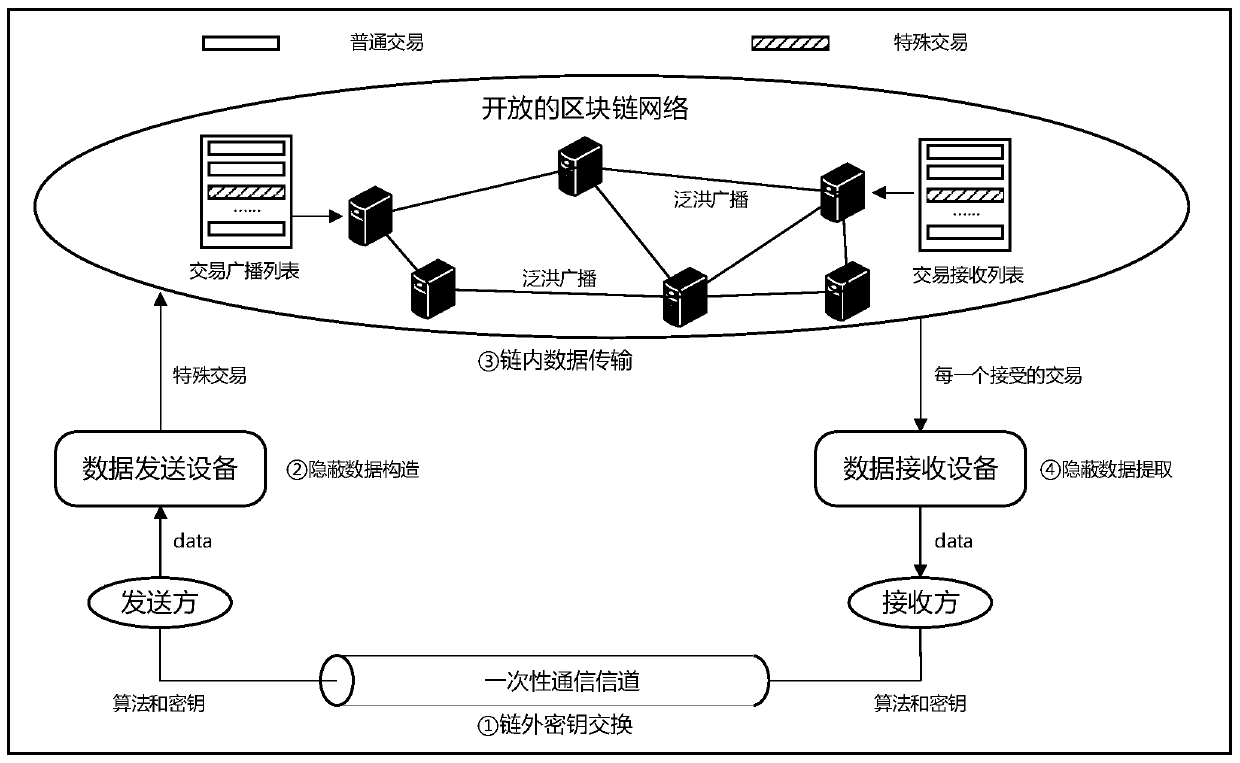
[0031] see figure 1 , the present invention provides a technical solution: a data covert transmission method based on a block chain network, including the following process:
[0032] 1. Out-of-chain key exchange phase: Before the data is transmitted in a concealed manner, the sender and receiver must exchange their respective public keys in advance. This process will be implemented in an off-chain communication channel, requiring a direct exchange of information between the receiver and the sender. To reduce the risk of off-chain communications being monitored by potential adversaries, the number of off-chain key exchanges must be kept to a minimum. In this scheme, the sender and the receiver only need one key exchange to safely complete multiple data transmissions. Off-chain key exchange can be implemented using existing technologies. For example, data transmission technology based on SSL encryption.
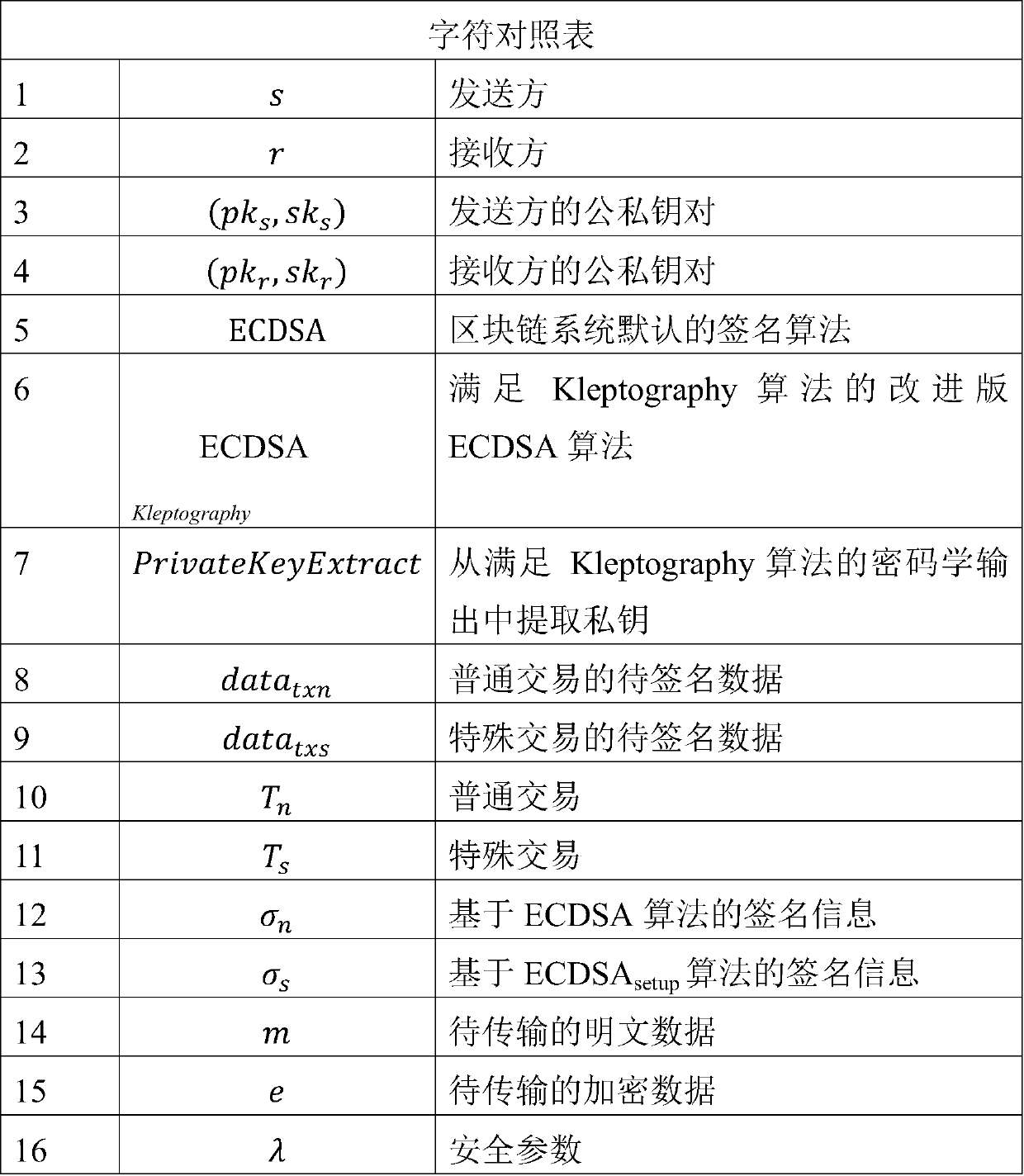
[0033] 2. Concealed data construction stage: In this stage, the sender...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com