Counterfeit TCP covert communication method based on SYN-ACK dual-server rebound pattern
A covert communication and dual-server technology, applied in the field of information hiding, can solve the problems of unreliable covert communication and low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
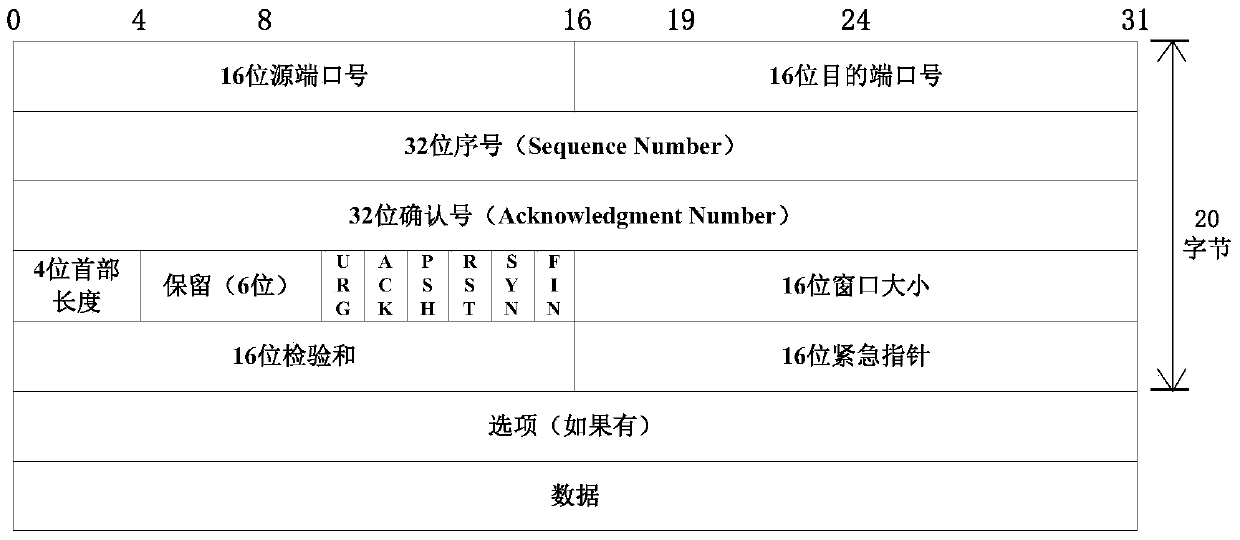
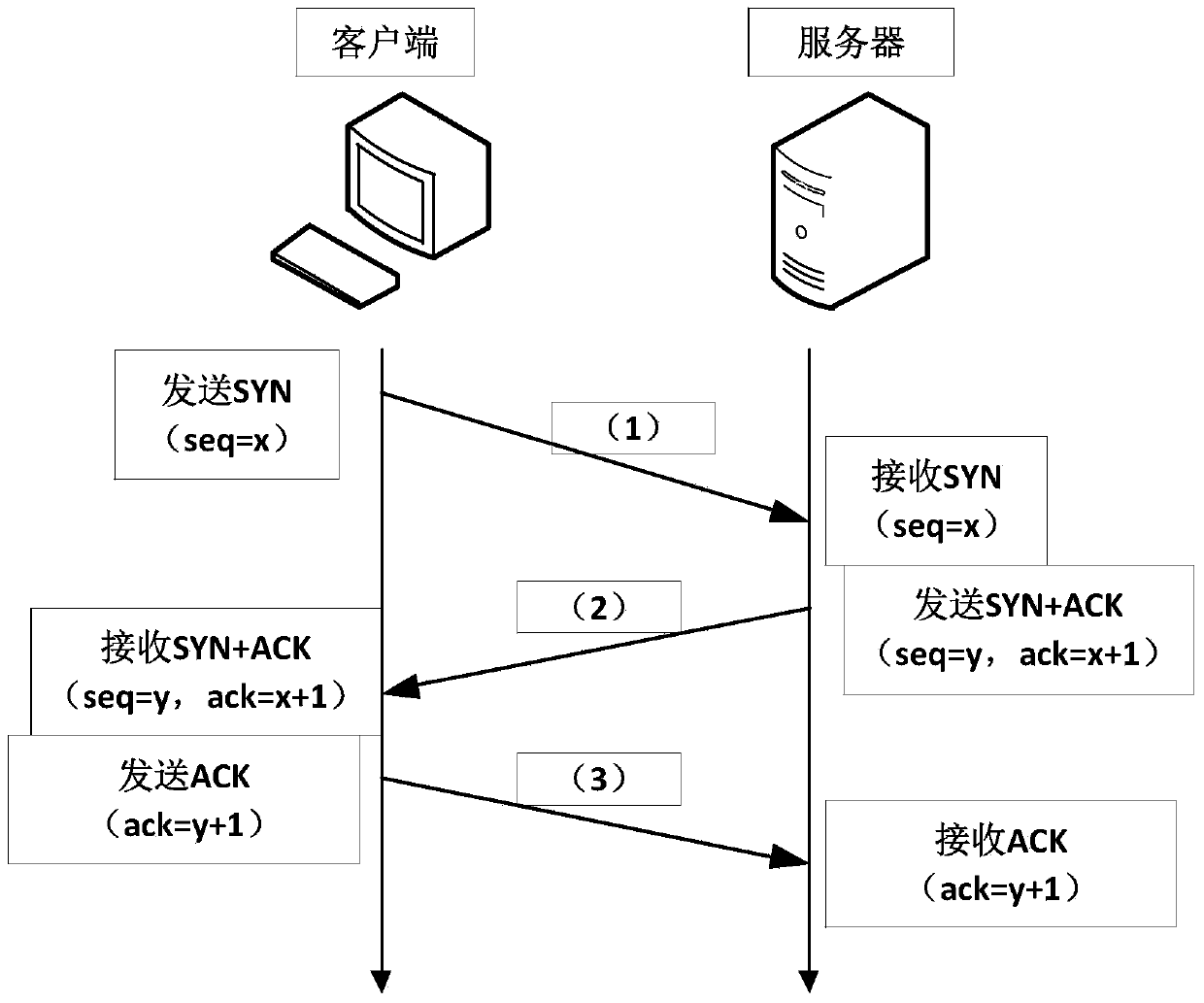
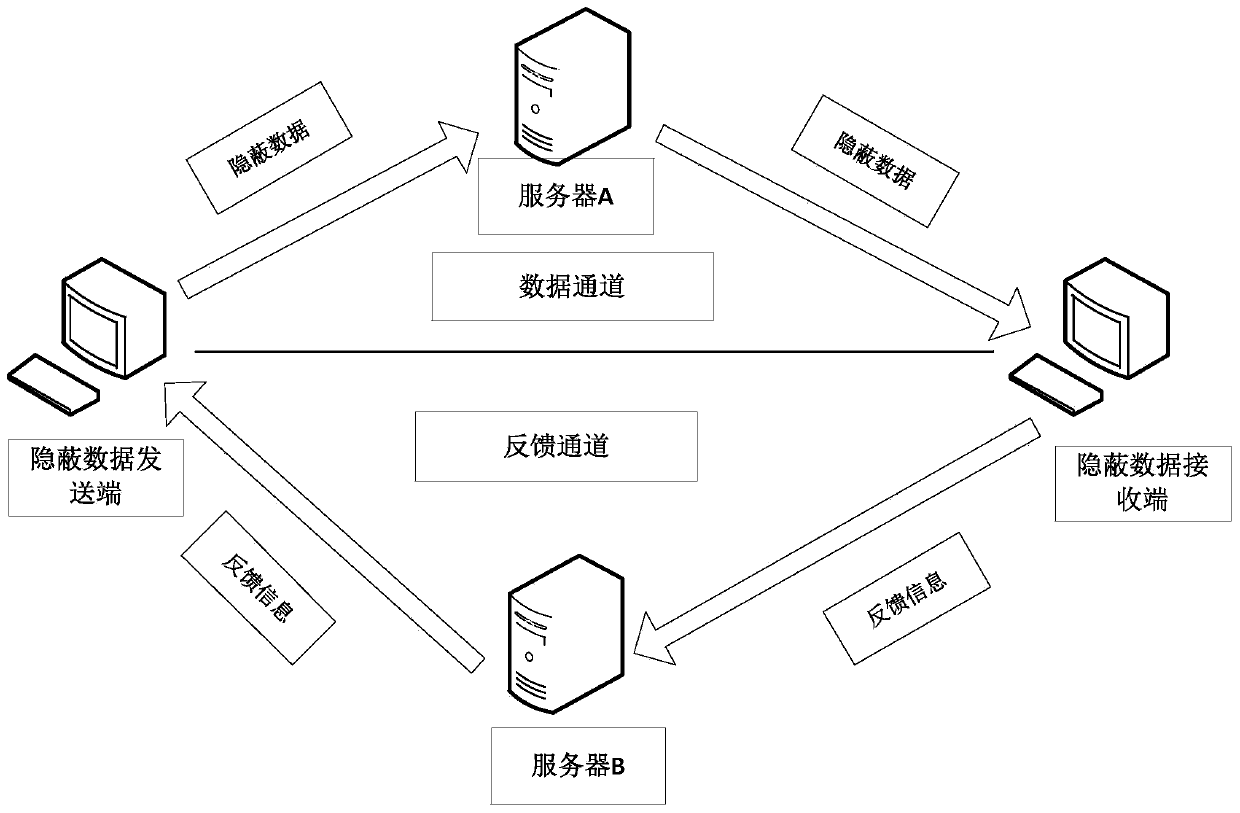
[0100] In order to fully disclose the content of the present invention, before introducing the specific implementation method of the invention, the working environment of the present invention is firstly introduced. The present invention adopts double-server rebound technology to build a communication channel, and utilizes the establishment stage of the TCP connection between the client and the server to transmit data, and its application scenarios are as follows: image 3 shown. The sending end of described secret information communicates with the receiving end through bounce server A or bounce server B; Embedding concealed information, and embedding the IP address and port of the receiving end of the secret information, the rebound server A bounces the secret information to the receiving end of the secret information for the second time through the confirmation number field of the TCP data packet according to the embedded IP address and port. Handshake; the receiving end of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com