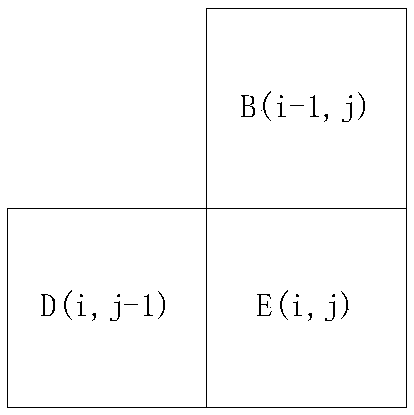Patents
Literature
182results about How to "Avoid scanning" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
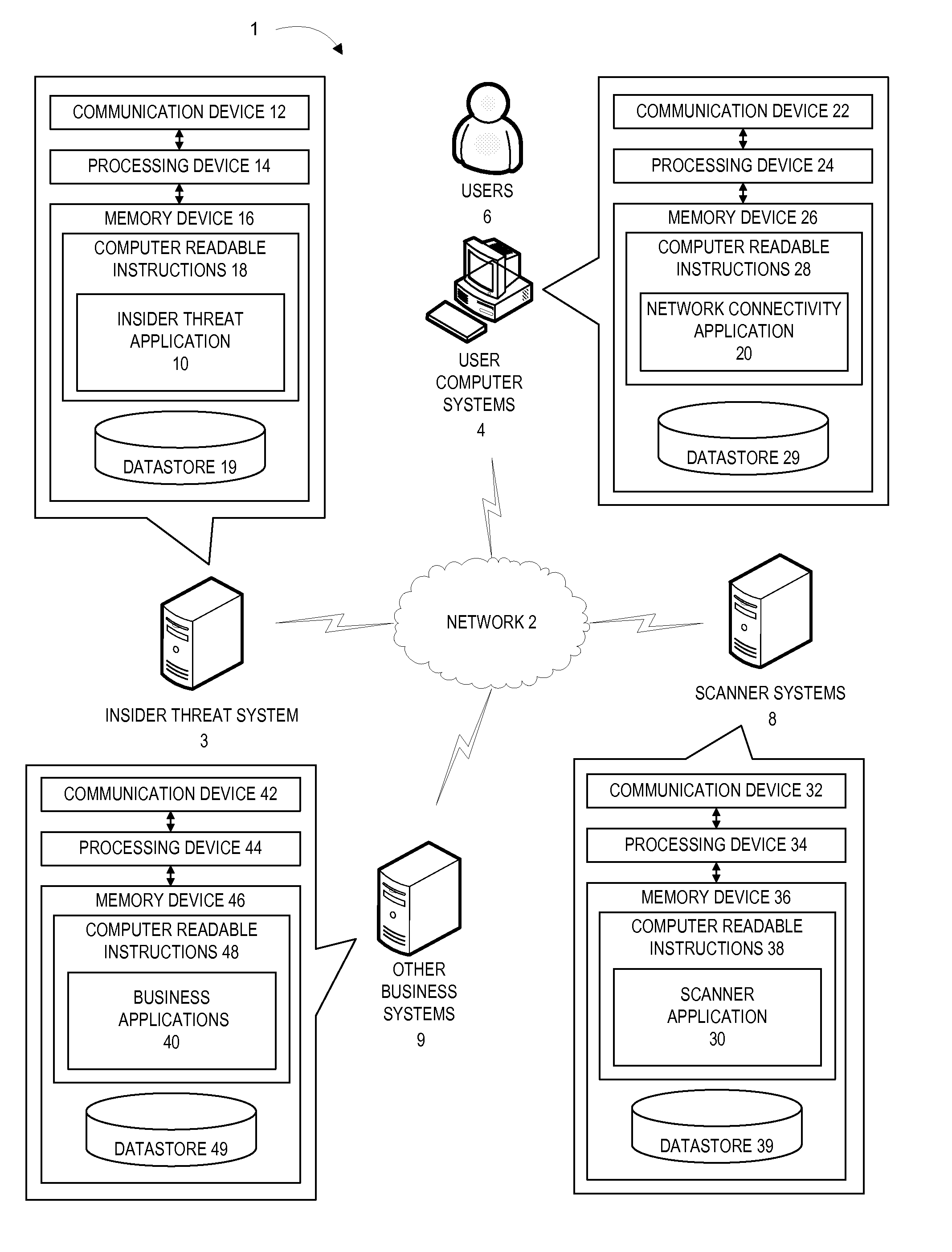
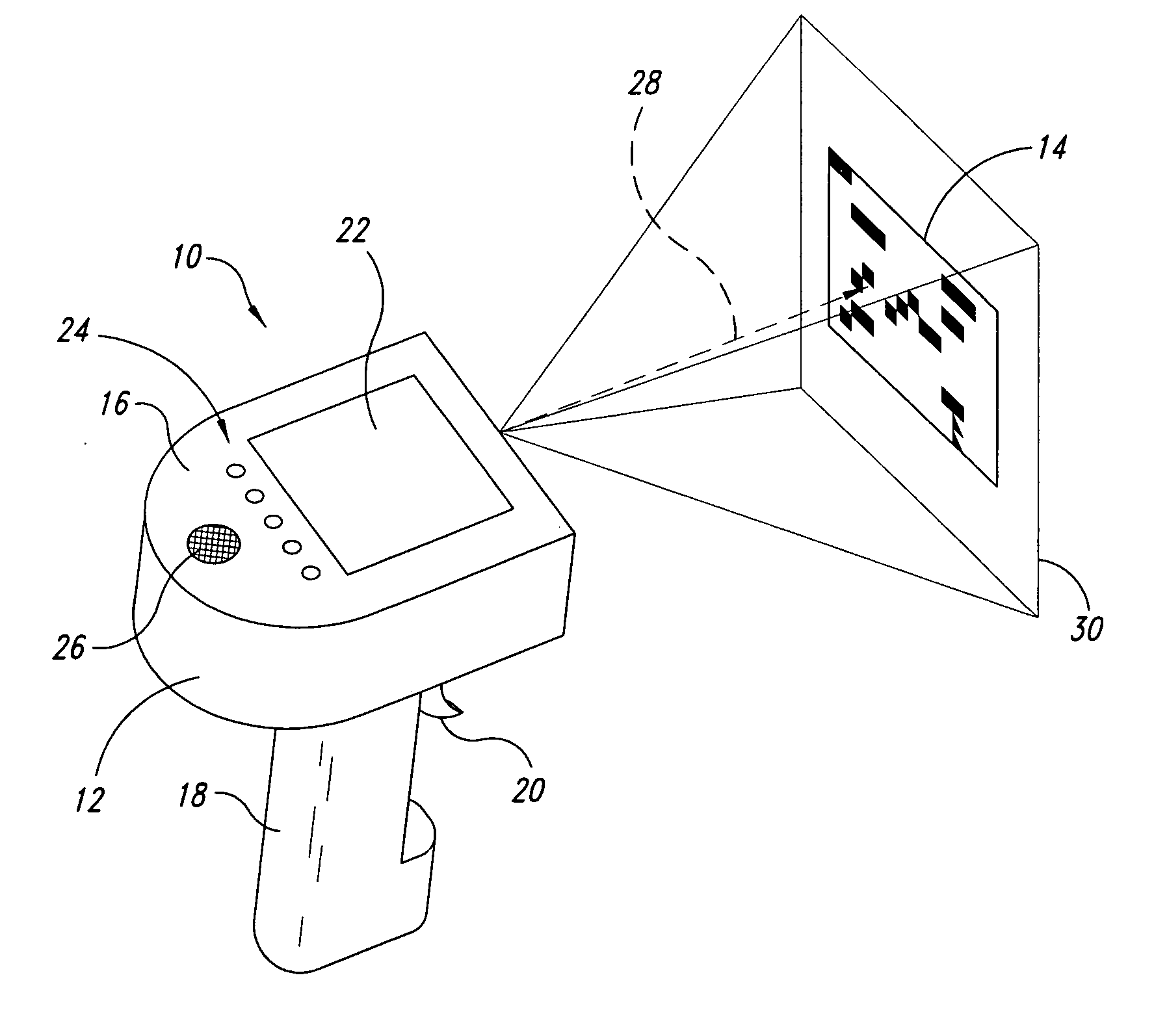
Insider threat ping and scan
ActiveUS20120198556A1Avoid scanningMemory loss protectionError detection/correctionInternet privacyDissemination
Embodiments of the present invention provide apparatuses and methods for identifying computer systems that pose a threat for potential dissemination of confidential information, and thereafter, scanning the computer systems for unauthorized activity related to potential dissemination of confidential information. Embodiments of the invention comprise compiling a list of user computer systems that are at risk of accessing, using, or disseminating confidential information; determining whether the computer systems on the list are available for scanning; and scanning the computer systems on the list to identify an incident related to potential or actual threats or breaches of confidential information.
Owner:BANK OF AMERICA CORP
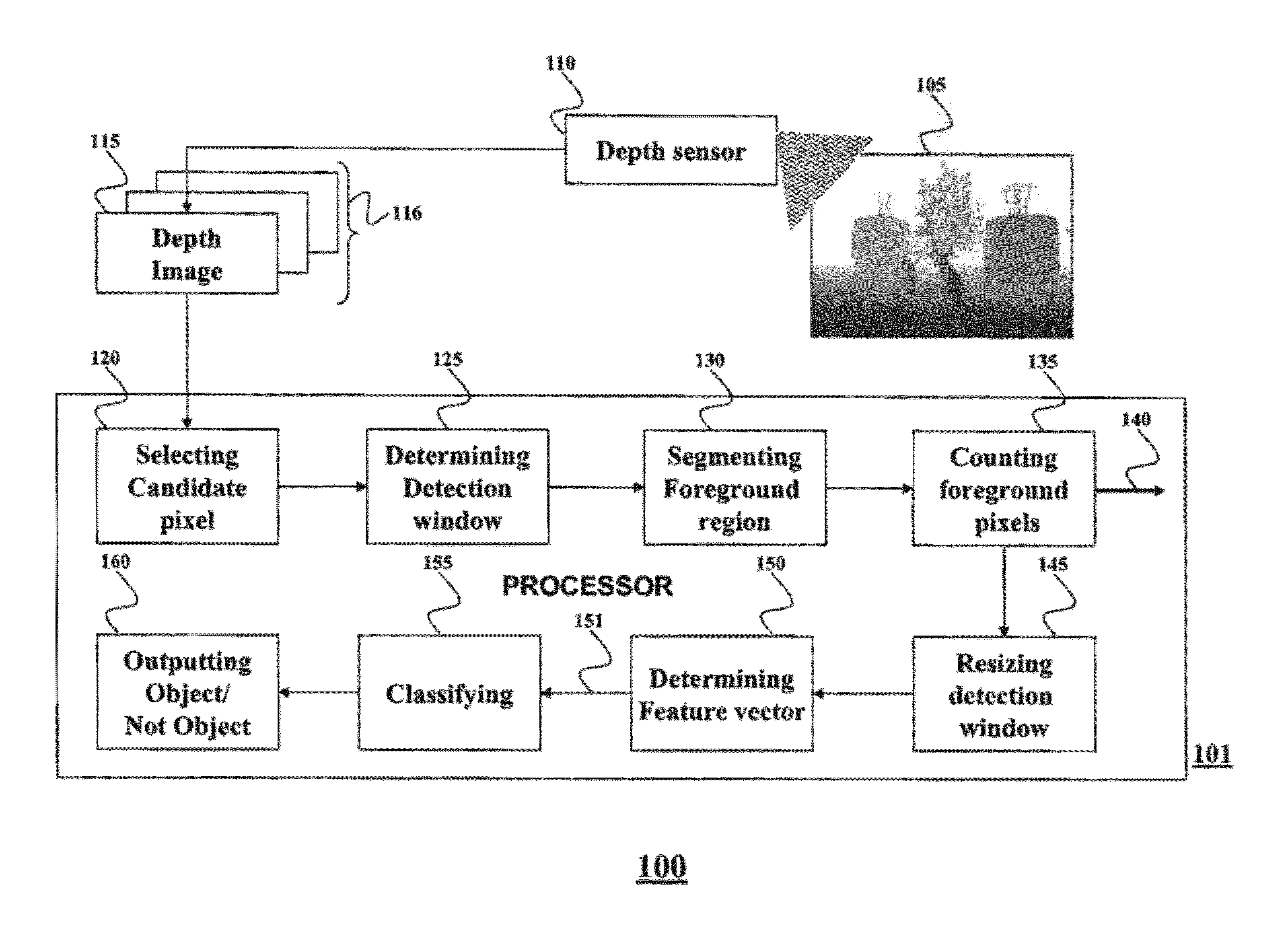
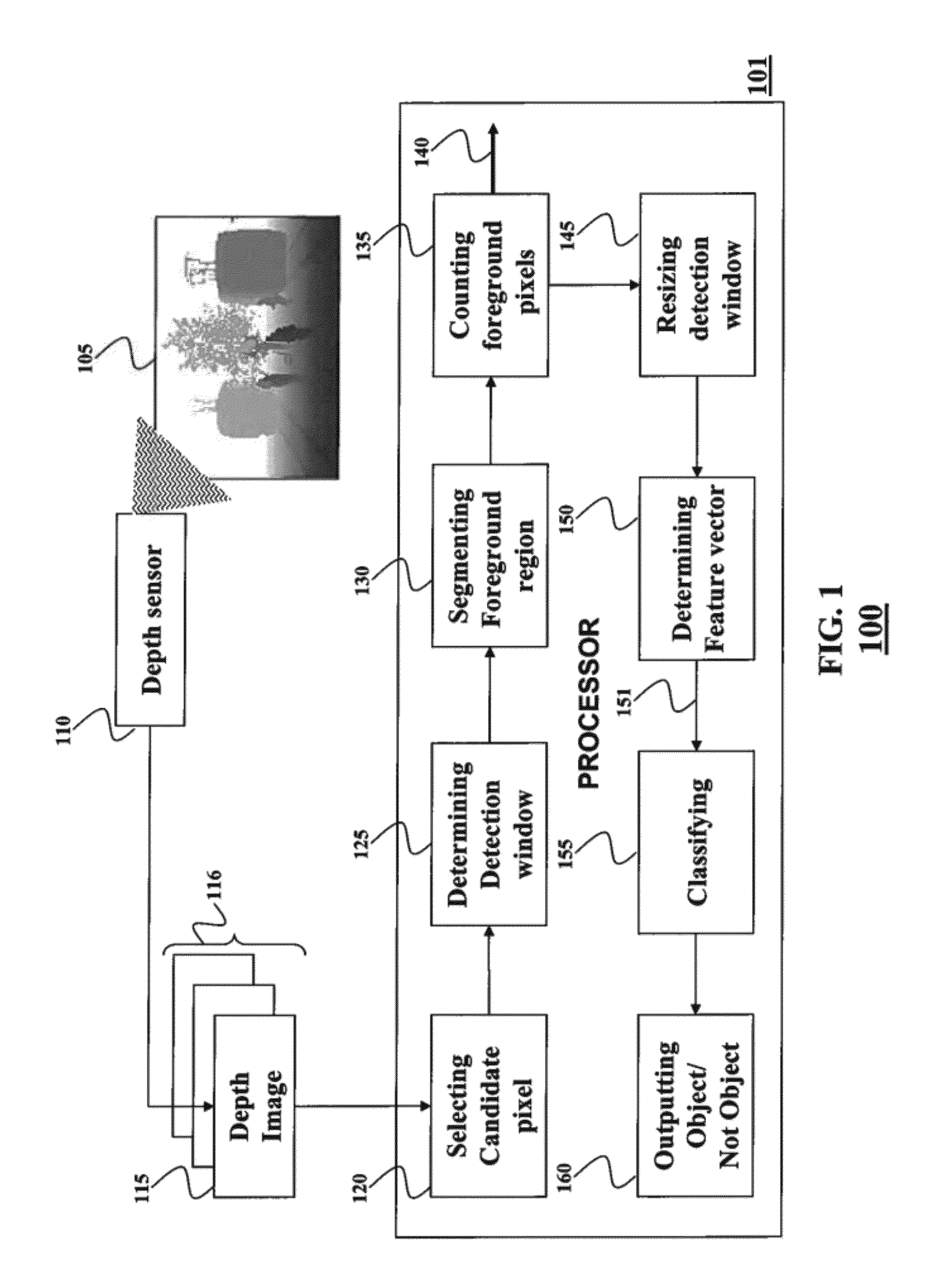
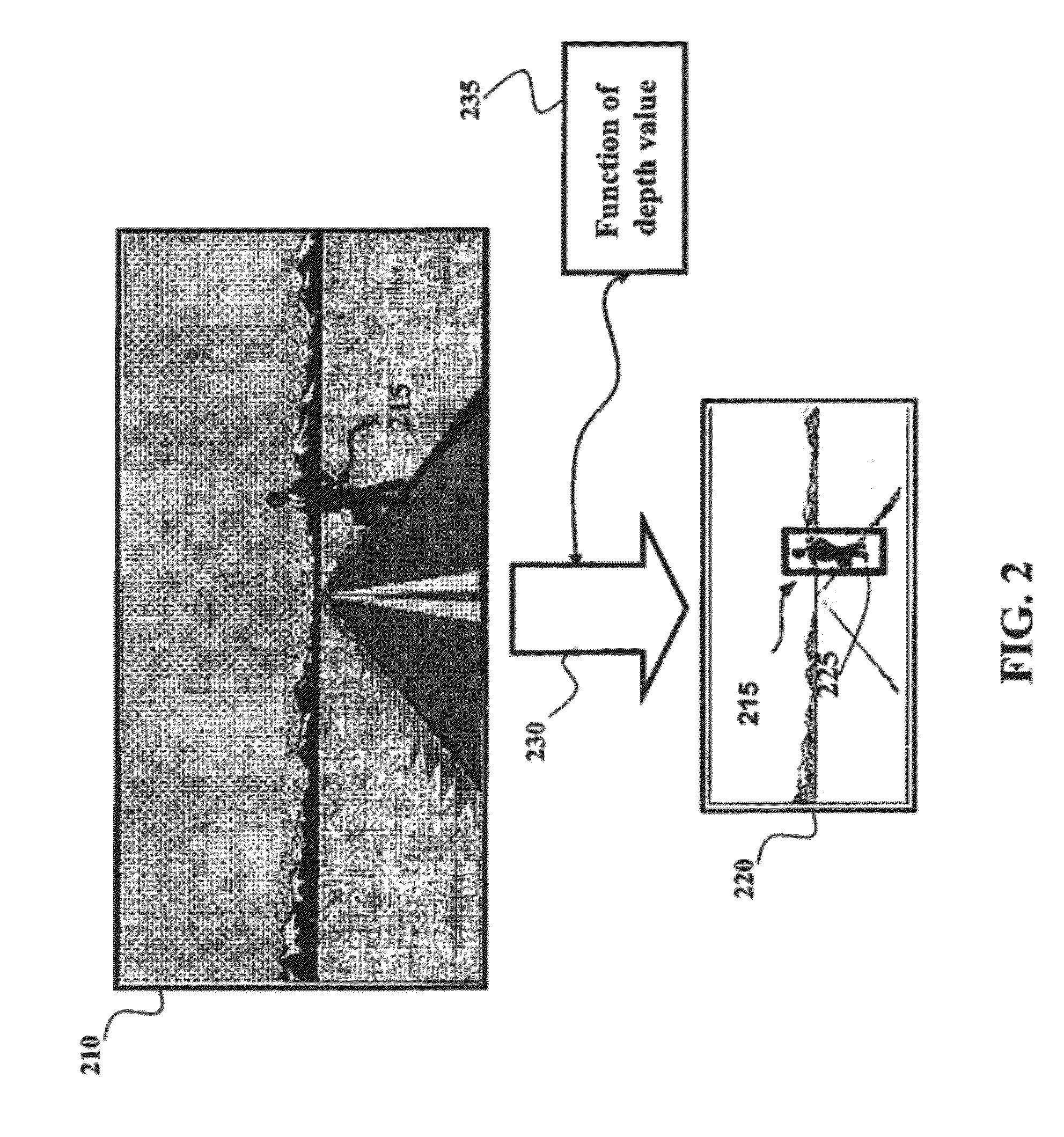
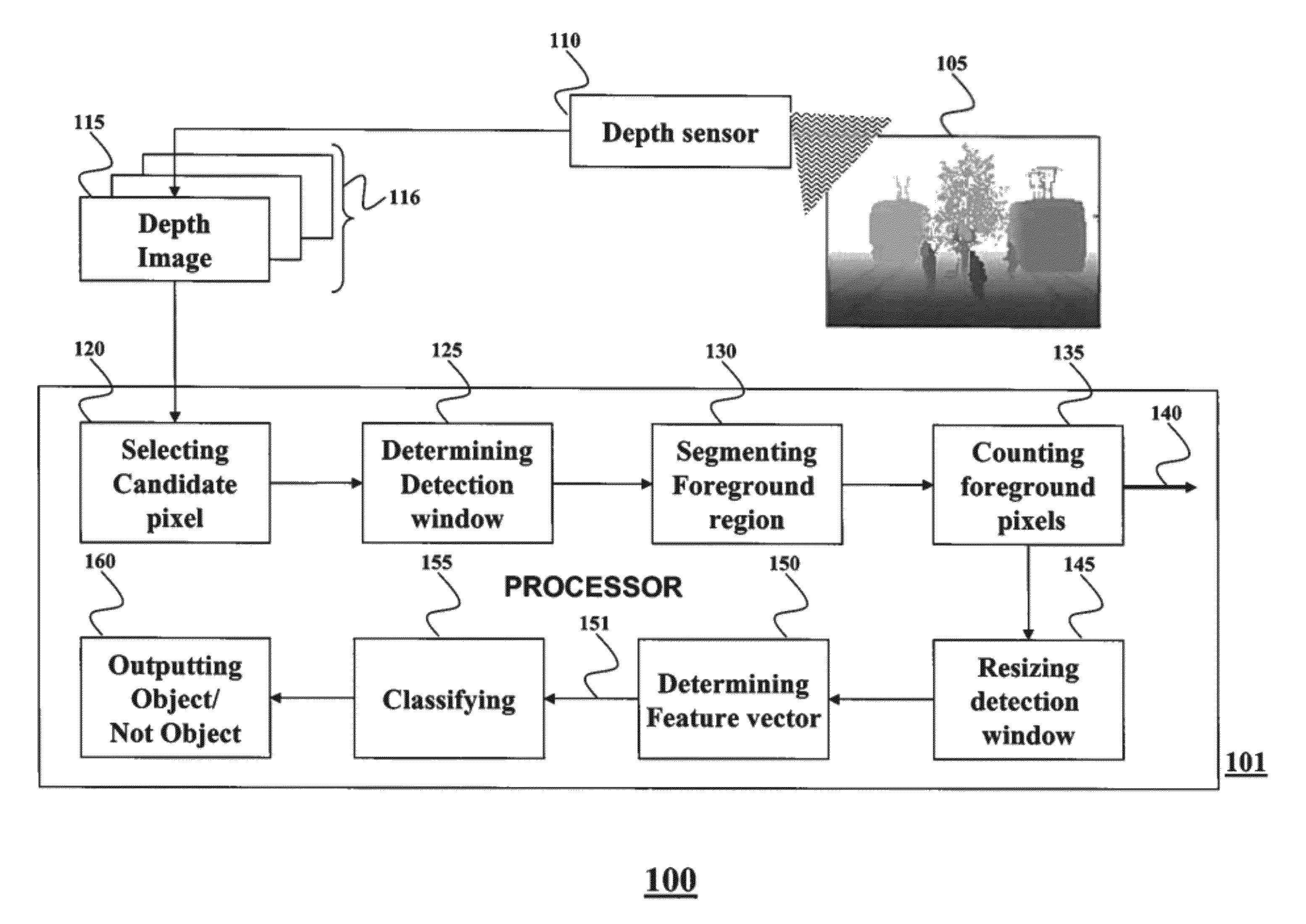
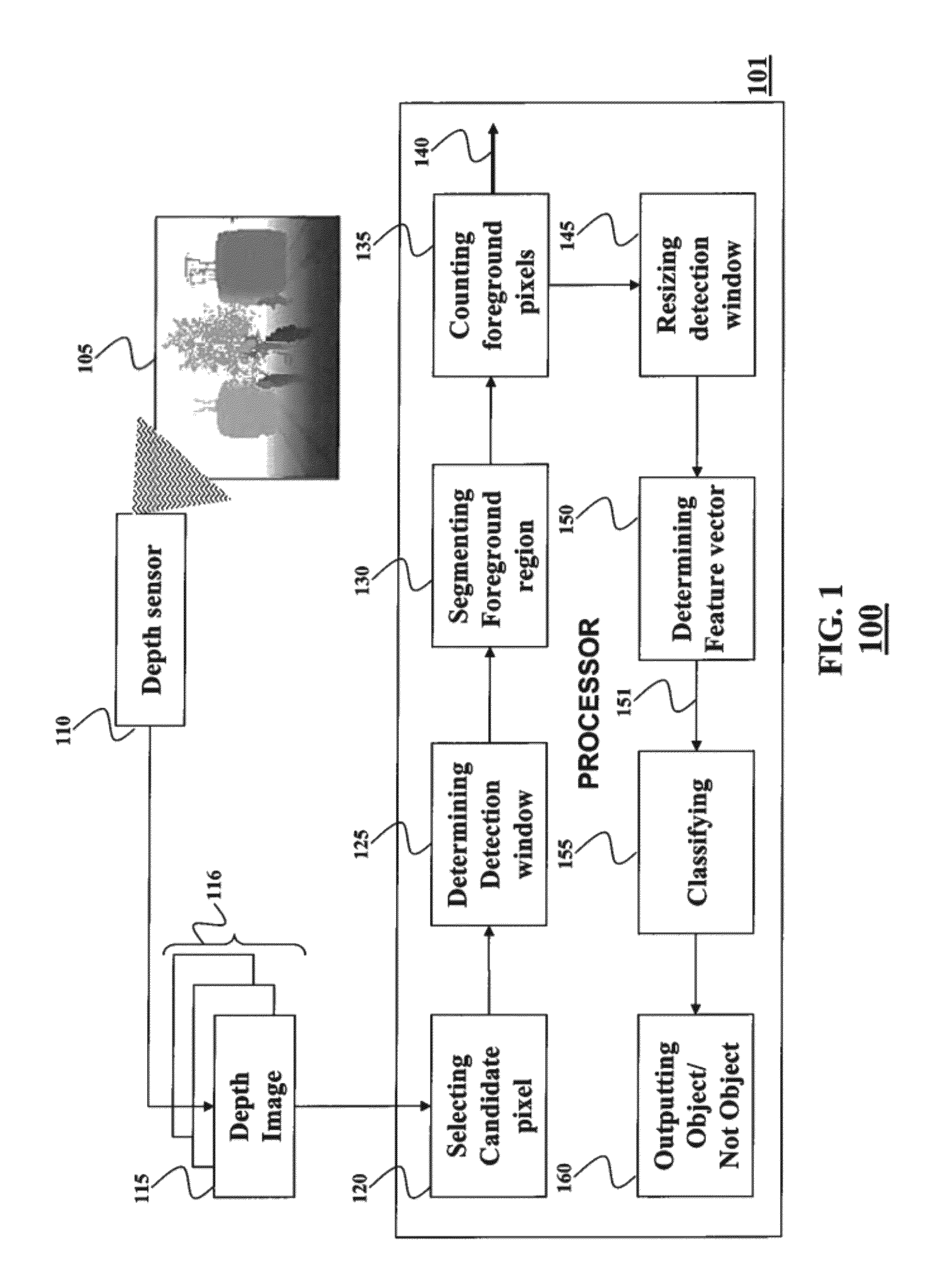
Object Detection in Depth Images
ActiveUS20120269384A1Efficient methodAvoid scanningColor television detailsClosed circuit television systemsFeature vectorWindow covering
A method for detecting an object in a depth image includes determining a detection window covering a region in the depth image, wherein a location of the detection window is based on a location of a candidate pixel in the depth image, wherein a size of the detection window is based on a depth value of the candidate pixel and a size of the object. A foreground region in the detection window is segmented based on the depth value of the candidate pixel and the size of the object. A feature vector is determined based on depth values of the pixels in the foreground region and the feature vector is classified to detect the object.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Method for managing the spectrum of a multi-band wireless communication system
ActiveUS20130010719A1Avoid scanningNetwork traffic/resource managementWireless commuication servicesFrequency bandMultiple frequency
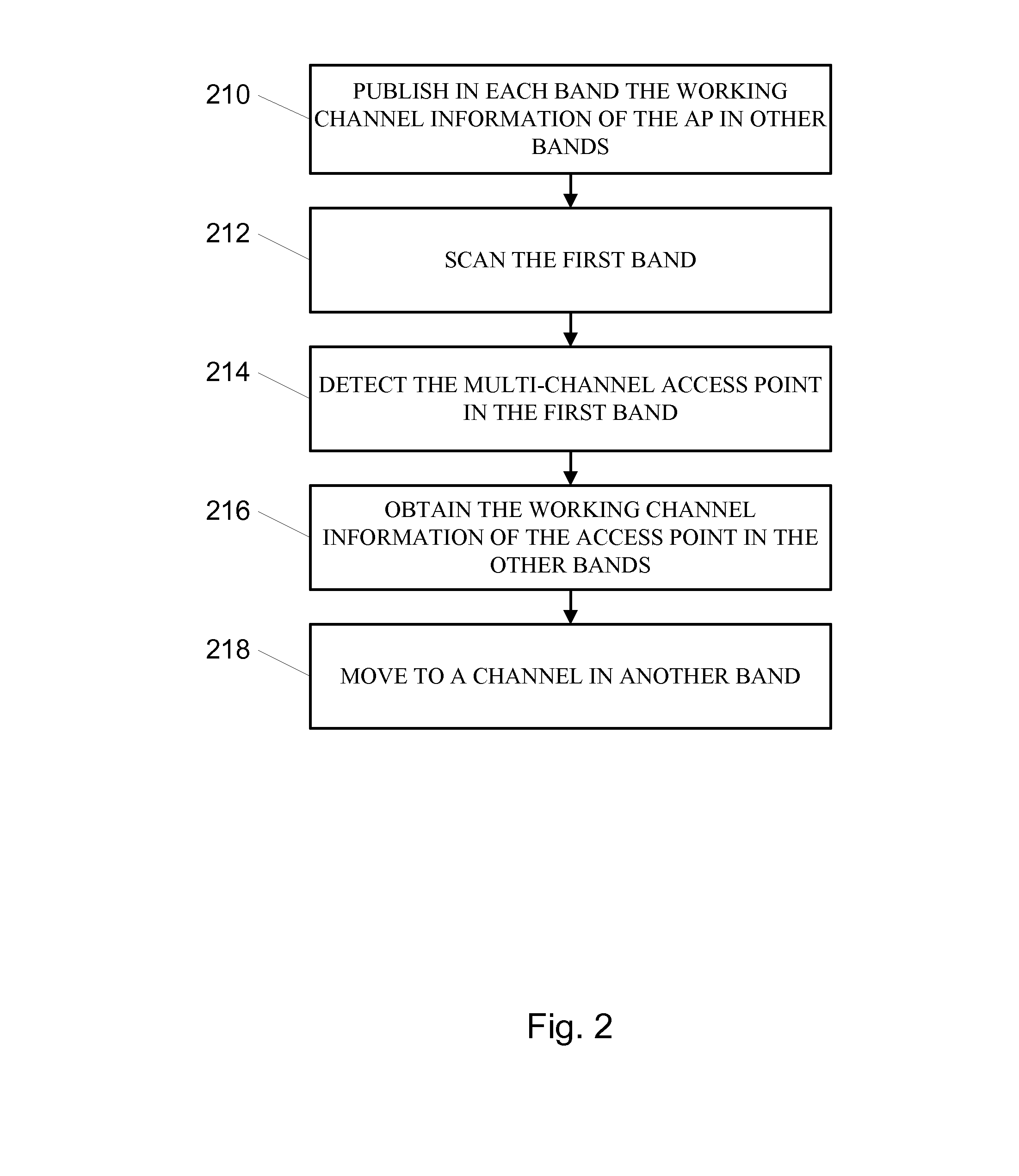
System and method for managing the spectrum of a multi-channel wireless communication system. Information related to other channels and bands is exchanged between a client associated to a first channel of the multi-channel wireless communication system and a multi-channel access point. The information includes, inter alia, capabilities of the access point and the client, working channel information of the access point, link quality metrics of the client in the other bands etc.
Owner:CELENO COMMUNICATIONS (ISRAEL) LTD
Shared device control method and server-client system
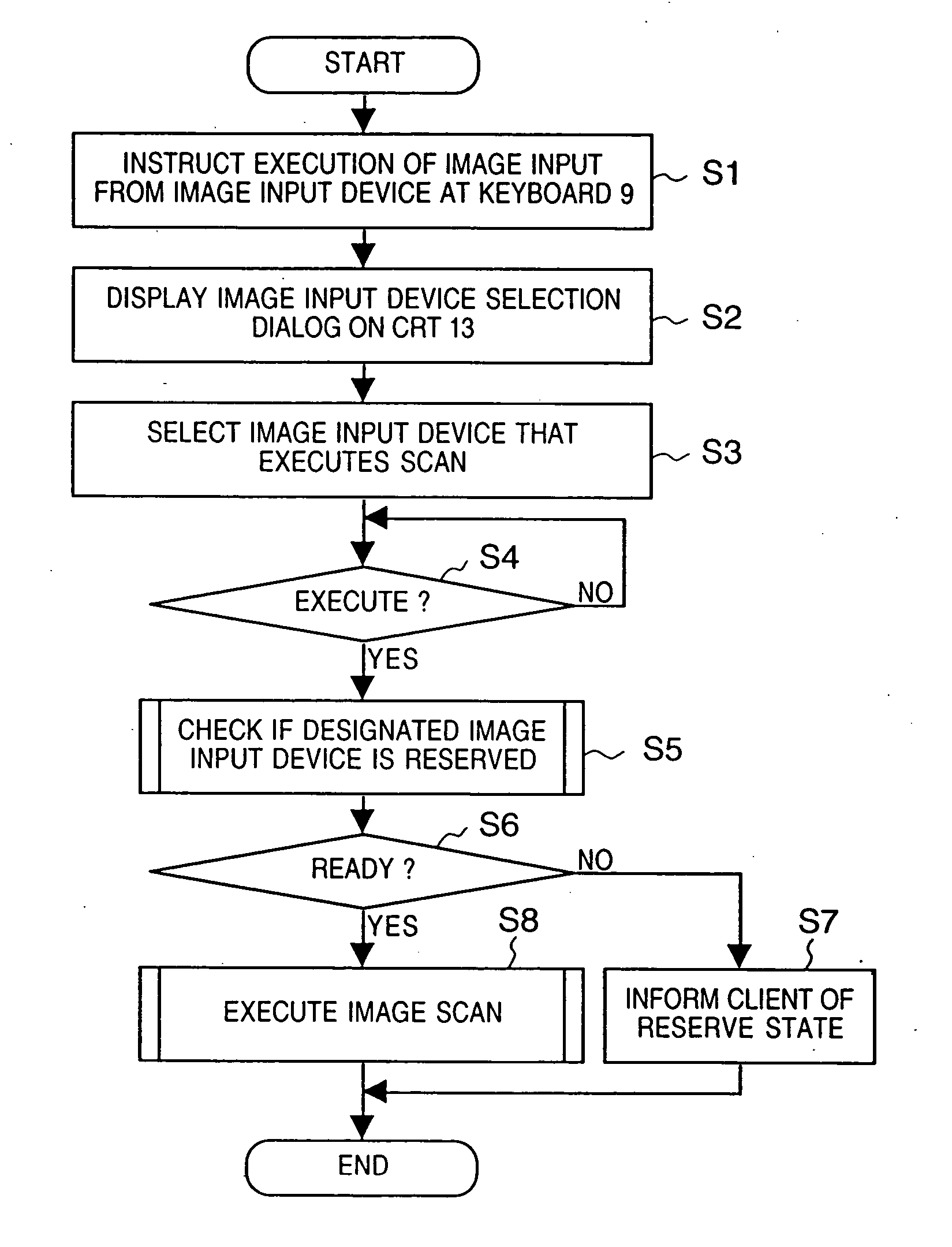
InactiveUS20050021795A1Unwanted situationAvoid scanningMultiple digital computer combinationsElectric digital data processingComputer hardwareNetwork connection
Provide a shared device control method and server-client system, which inform the client user of the state of a shared device upon accessing the connectable shared device on the network, thereby preventing unwanted situations (for example, the user cannot determine what has happened; the user cannot obtain a desired access result; access results in other fatal errors; and so forth). A shared device, to be shared by a plurality of data processing apparatuses connected via a network, is controlled by one of the plurality of data processing apparatuses, and the other data processing apparatuses inquires of the data processing apparatus controlling the shared device, a reserve or ready state of the shared device, or a mode which displays a window via the network, prior to use of the shared device informs the client user of the state of the shared device.
Owner:CANON KK
Object detection in depth images
ActiveUS8406470B2Scanning of the classifier can be avoidedEfficient methodColor television detailsClosed circuit television systemsFeature vectorObject detection
A method for detecting an object in a depth image includes determining a detection window covering a region in the depth image, wherein a location of the detection window is based on a location of a candidate pixel in the depth image, wherein a size of the detection window is based on a depth value of the candidate pixel and a size of the object. A foreground region in the detection window is segmented based on the depth value of the candidate pixel and the size of the object. A feature vector is determined based on depth values of the pixels in the foreground region and the feature vector is classified to detect the object.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Method and system for radio access technology monitoring in a wireless communications system
ActiveUS20090274121A1Not wasting air interface communication resourceQuality improvementAssess restrictionWireless commuication servicesRadio access technologyCommunications system
A method and apparatus are provided for radio access technology (RAT) monitoring, in a wireless system environment having wireless communications equipment and at least two different RATs that coexist for providing to the equipment access to one or more communications networks. The equipment has at least two subsystems, each adapted for establishing and maintaining an active communications connection with a certain one of the different RATs. The equipment selects at least a first RAT, among all the RATs available in a certain geographical area, for establishing the active communications connection, according to a monitored characteristic of the first RAT. The method includes scanning a characteristic of a second RAT available for communication in the geographical area while the equipment maintains an active communications connection with the first RAT, and performing the scanning step when the equipment does not transmit signals through the active communications connection maintained with the first RAT.
Owner:SEQUANS COMMUNICATIONS
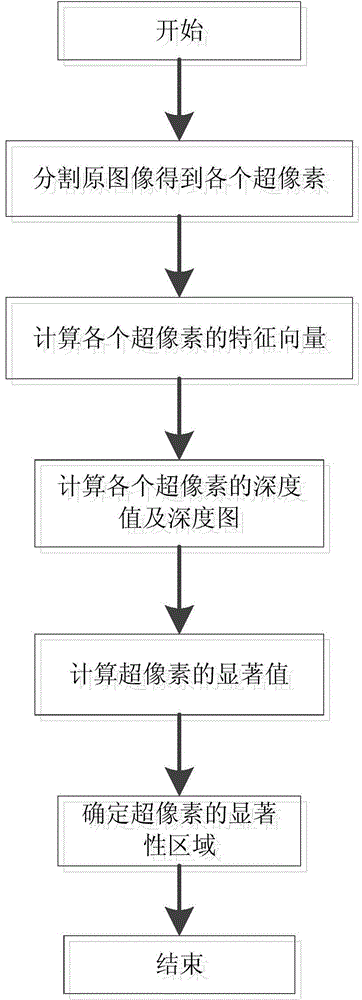
Extraction method of visual saliency area based on monocular depth map
InactiveCN104574366AReduce noise interferenceTest results are obviousImage enhancementImage analysisFeature vectorVisual saliency
The invention discloses an extraction method of a visual saliency area based on a monocular depth map. The extraction method of the visual saliency area comprises the following sequential steps: dividing an original image to obtain super pixels; building a characteristic vector of each super pixel to estimate an absolute depth characteristic of absolute depth in a scene in the image; building a probability model by using a Gaussian-Markov random field model, calculating a distance relation between the super pixel characteristic vector and an adjacent super pixel characteristic vector by virtue of the probability model to obtain a relative depth characteristic on the basis of the absolute depth characteristic and obtain depth values and depth maps of the super pixels simultaneously; calculating saliency values of the super pixels; calculating a gain coefficient according to the depth values and correcting the saliency values by using the gain coefficient. The extraction method can be used for quickly and automatically identifying the saliency objects in the image without any prior knowledge, is high in universality and can also be used for accurately detecting the saliency area.
Owner:SOUTH CHINA UNIV OF TECH
Method for managing the operation of a wireless apparatus configured to exchange information with a millimeter-wave communication device, and corresponding apparatus
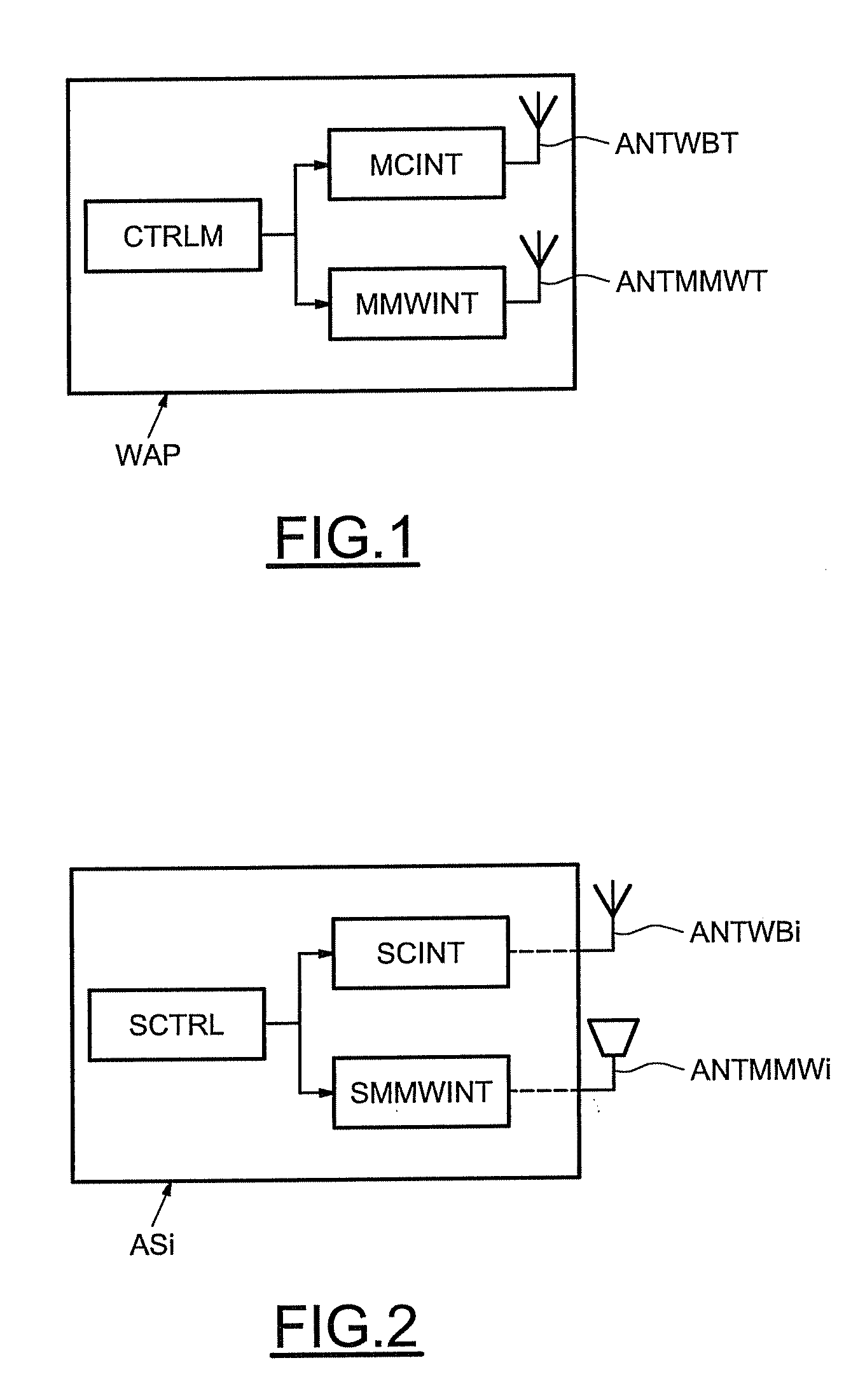
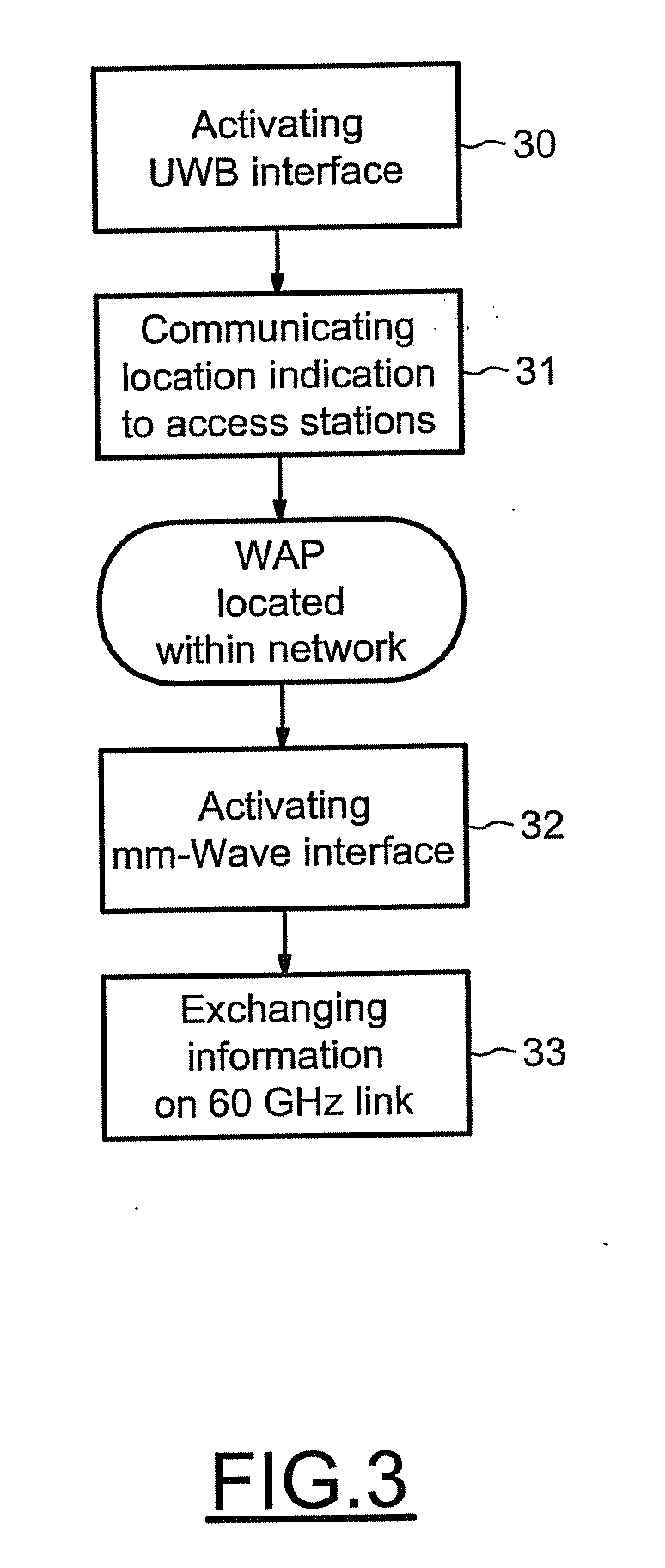
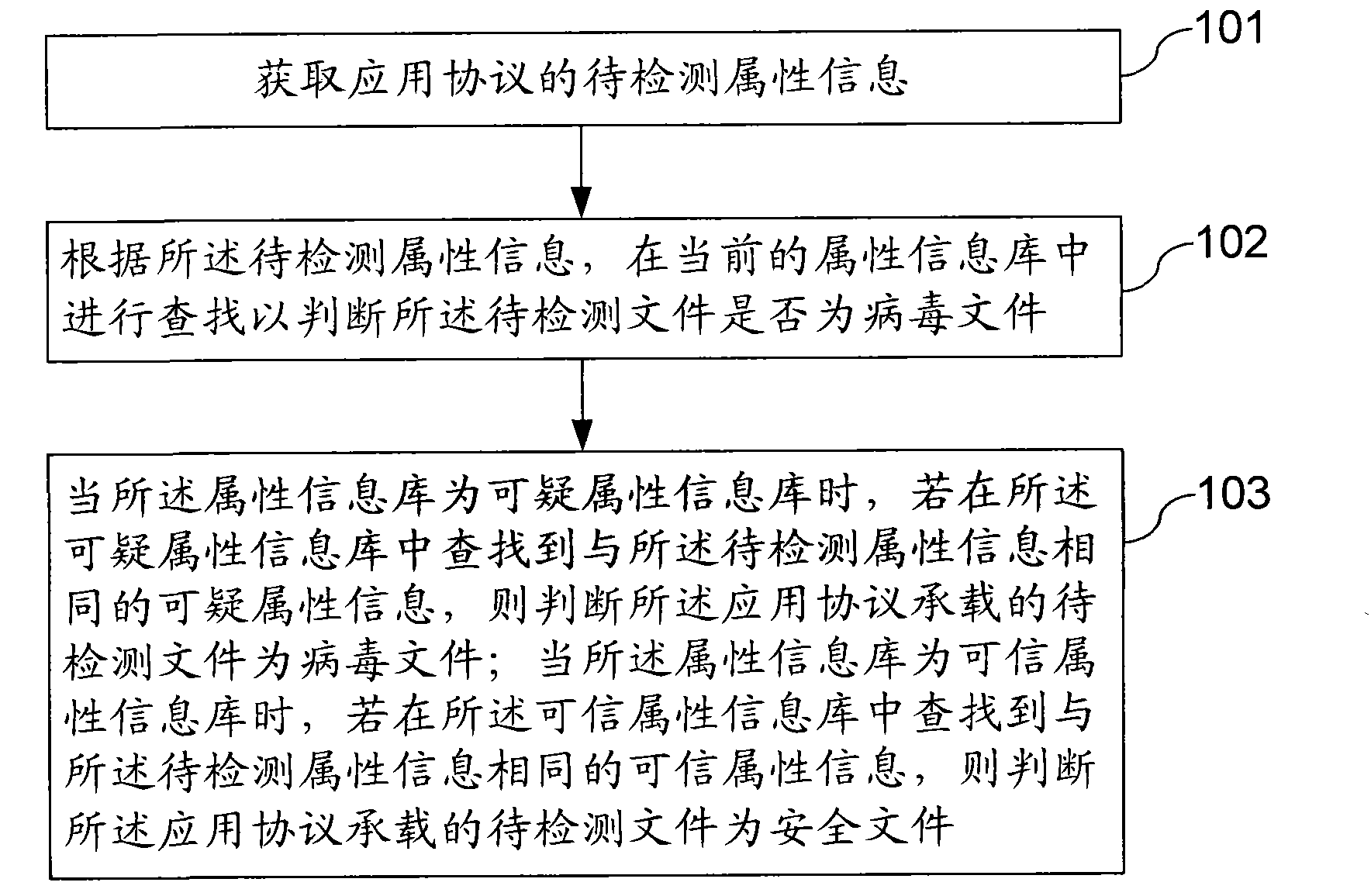
ActiveUS20090213901A1Improve abilitiesAvoid scanningElectromagnetic transmission non-optical aspectsConnection managementCommunication interfaceMillimetre wave
A wireless apparatus includes a millimeter-wave communication interface configured to exchange information within a millimeter-wave communication network, an UWB communication interface and control means or circuitry configured to activate the UWB interface for communicating location indication to the communication network according to an UWB communication standard. The location indication is intended for locating the wireless apparatus within the network.
Owner:STMICROELECTRONICS INT NV
Method and device for detecting viruses and gateway equipment
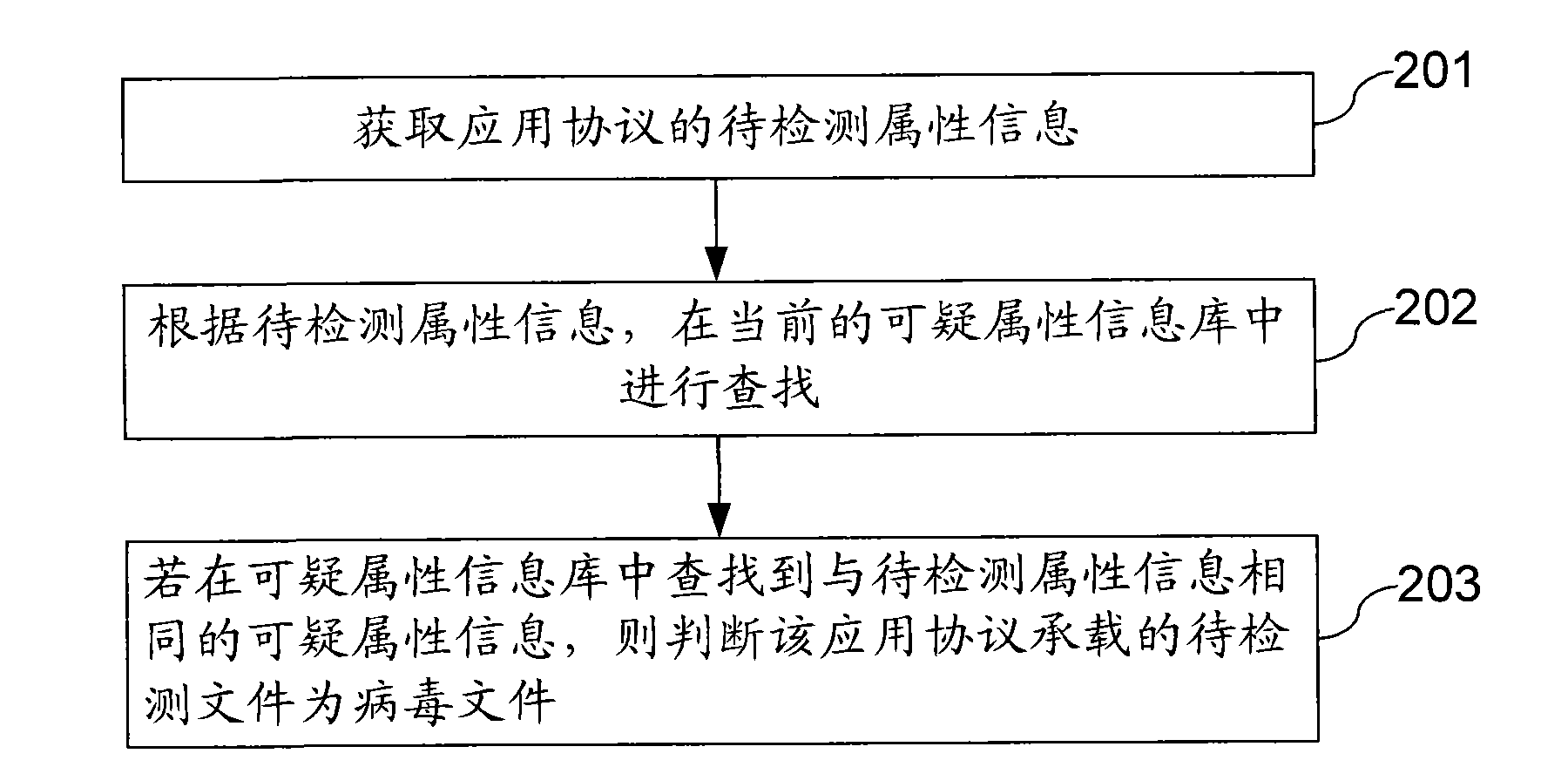
ActiveCN101795267AAvoid scanningImprove scan performancePlatform integrity maintainanceData switching networksAnti virusInformation repository
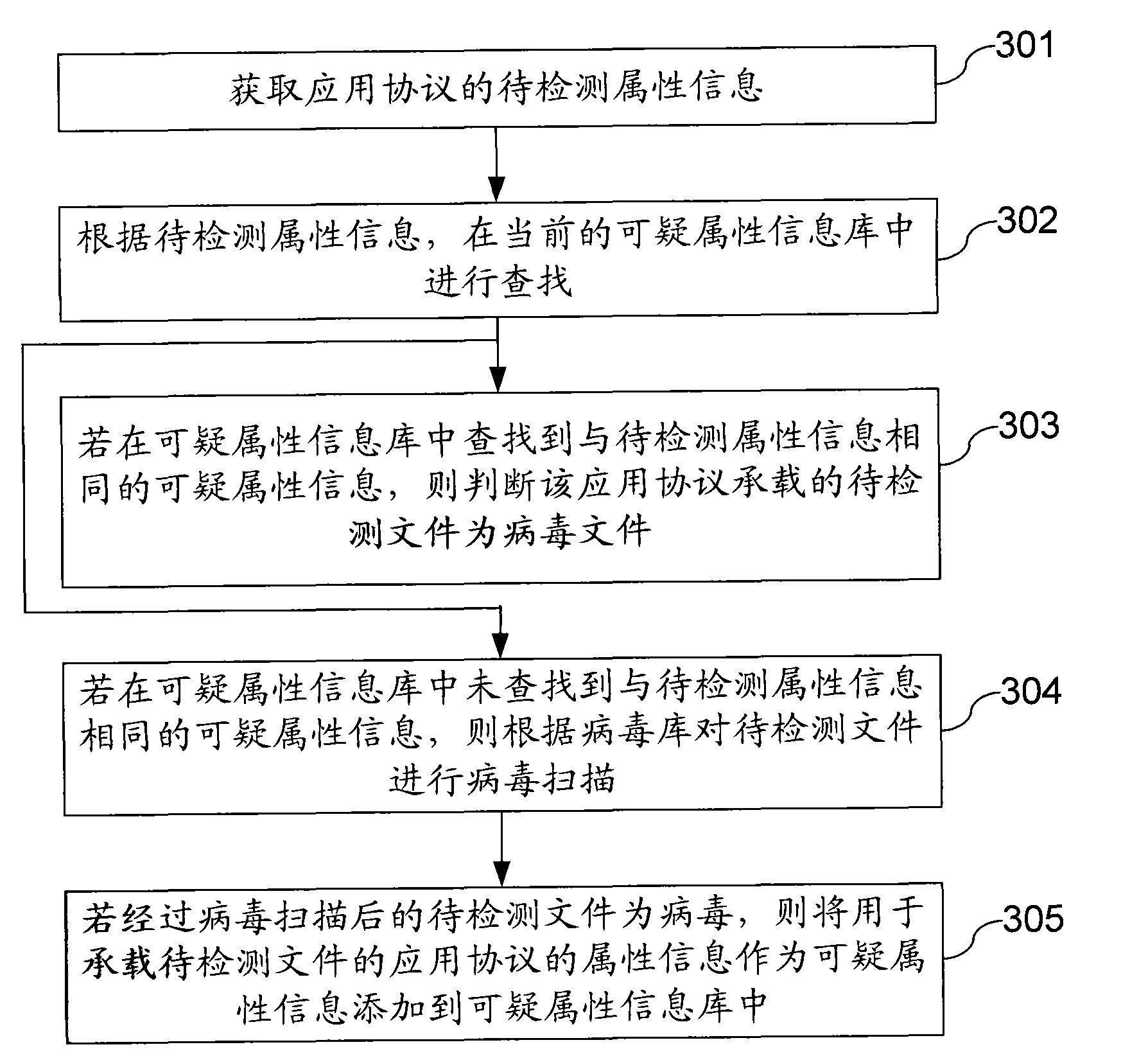
The embodiment provides a method and a device for detecting viruses and gateway equipment. The method comprises the steps of: obtaining attribute information to be detected for loading the application protocol of a document to be detected, and searching in a current attribute information library according to the attribute information to be detected, wherein the attribute information library comprises a suspicious attribute information library or a credible attribute information library; judging whether the document to be detected is a virus document when searching suspicious attribute information which is the same with the attribute information to be detected in the suspicious attribute information library; and judging whether the document to be detected is a safe document when searching credible attribute information which is the same with the attribute information to be detected in the credible attribute information library. The document to be detected is judged to be a virus document or not by searching in the current suspicious attribute information library according to the attribute information to be detected of the application protocol, which avoids scanning viruses to each document to be detected according to a virus library, improves the scanning performance of a gateway anti-virus method, and lowers the cost.
Owner:CHENGDU HUAWEI TECH
Data processing method
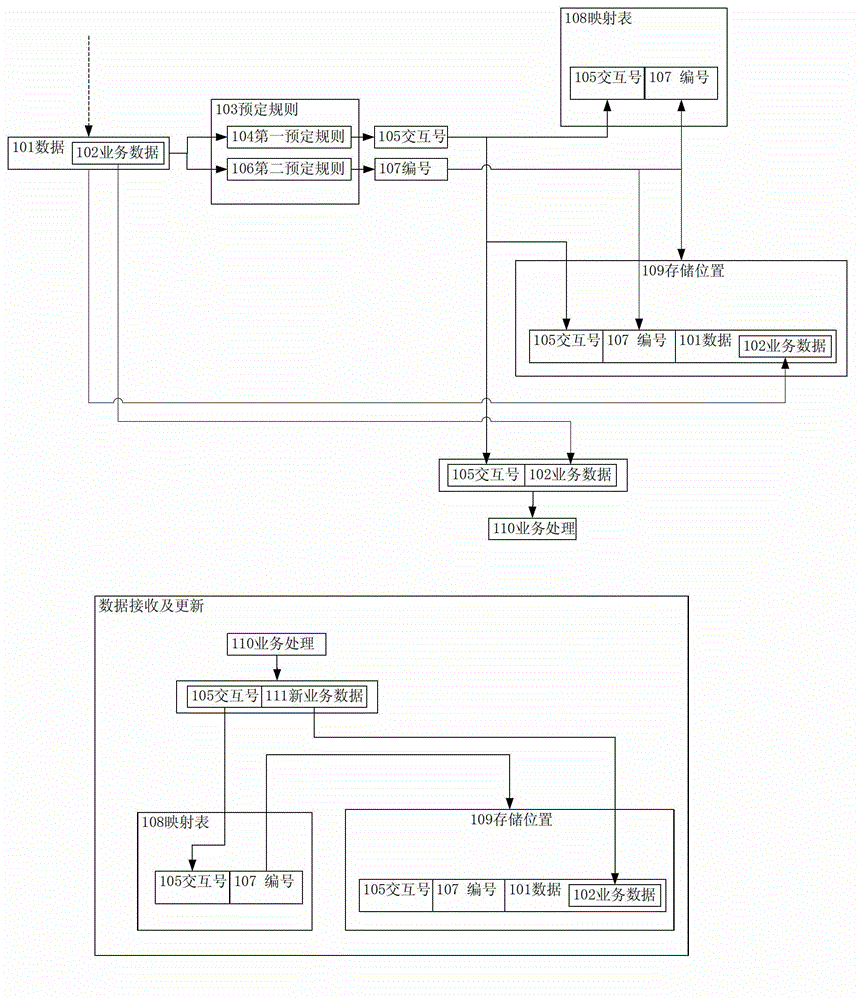
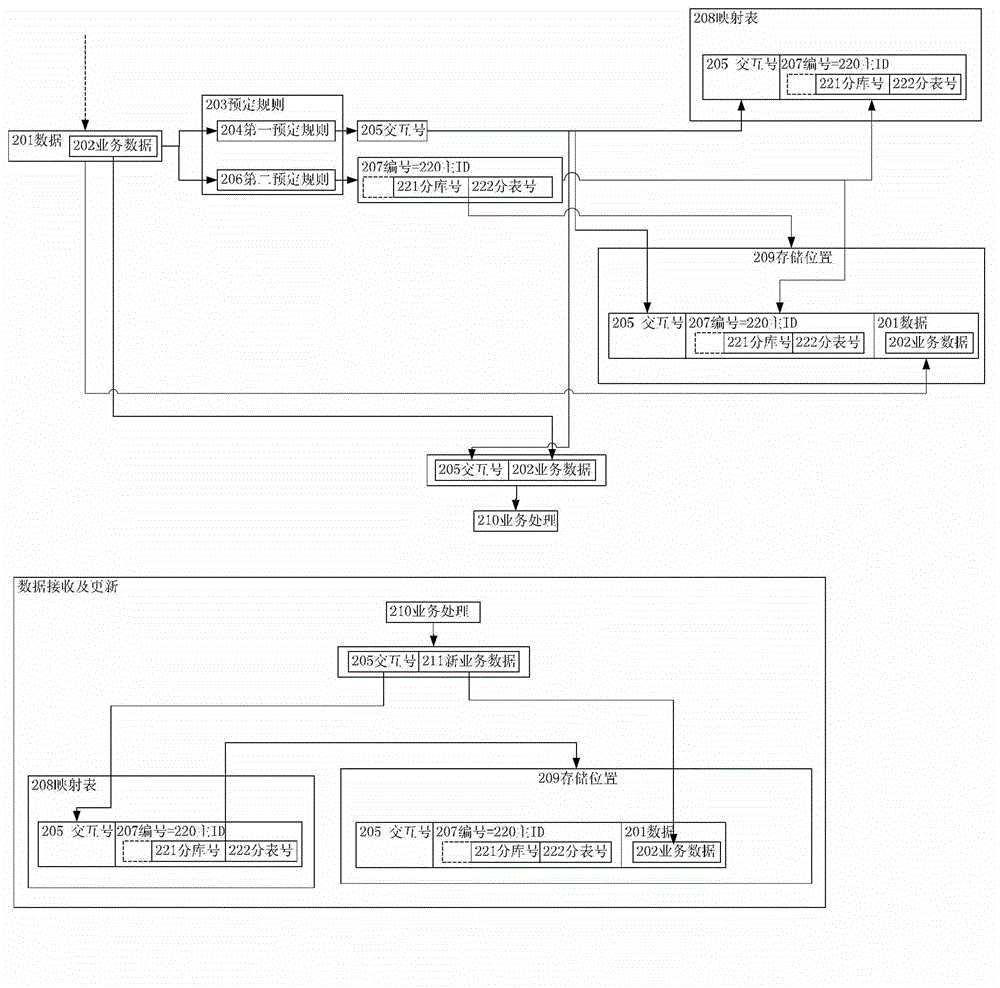
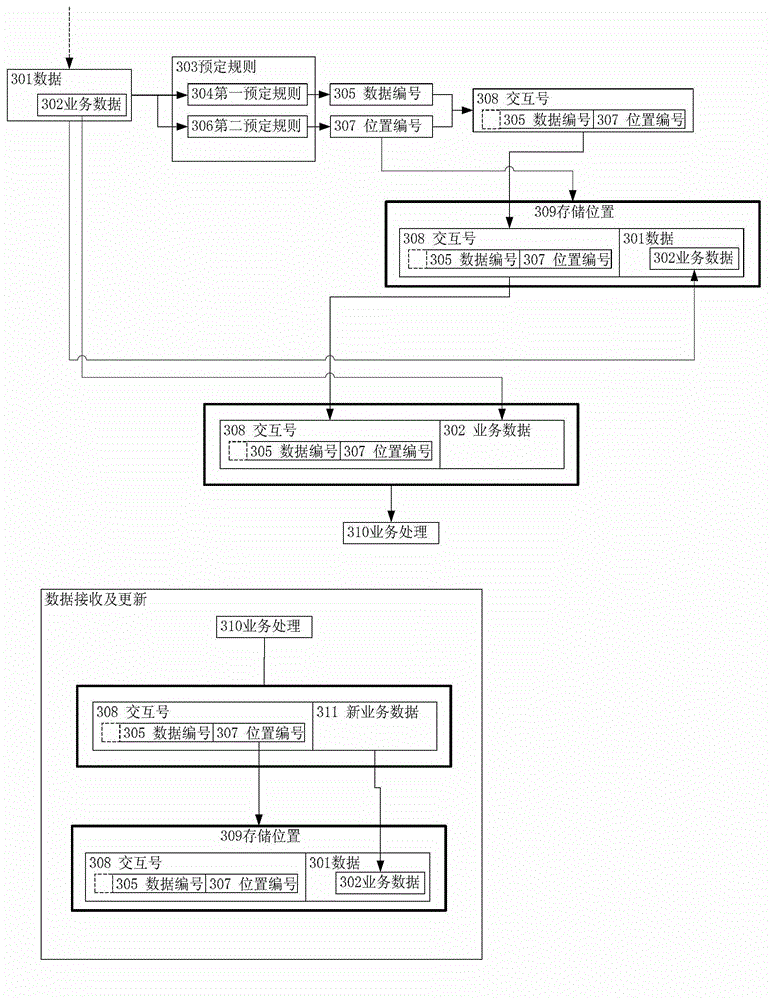
ActiveCN103942209AReduce overheadAvoid scanningDatabase distribution/replicationSpecial data processing applicationsDatabaseSerial code
The invention provides a data processing method. The method includes the steps that one of one or more items of data including service data is obtained, wherein the one or more items of data wait for service processing; according to a preset rule, an interaction number and a serial number corresponding to the interaction number are generated for one item of data; a mapping table is established for generating a mapping relation between the interaction number and the serial number; one item of data, the interaction number and the serial number are stored at storage positions in a sub-library and a sub-table in a main database, wherein the sub-library and the sub-table correspond to the one item of data and are indicated by the serial number; the service data of the one item of data and the interaction number are sent to perform service processing. According to the method, a storage seeking mode of a distributed system is improved, the library and table where the data are located can be accurately positioned, all libraries and all tables in the database are prevented from being scanned, the overhead for the database is reduced, and the capacity for processing the data through the system is improved.
Owner:ADVANCED NEW TECH CO LTD
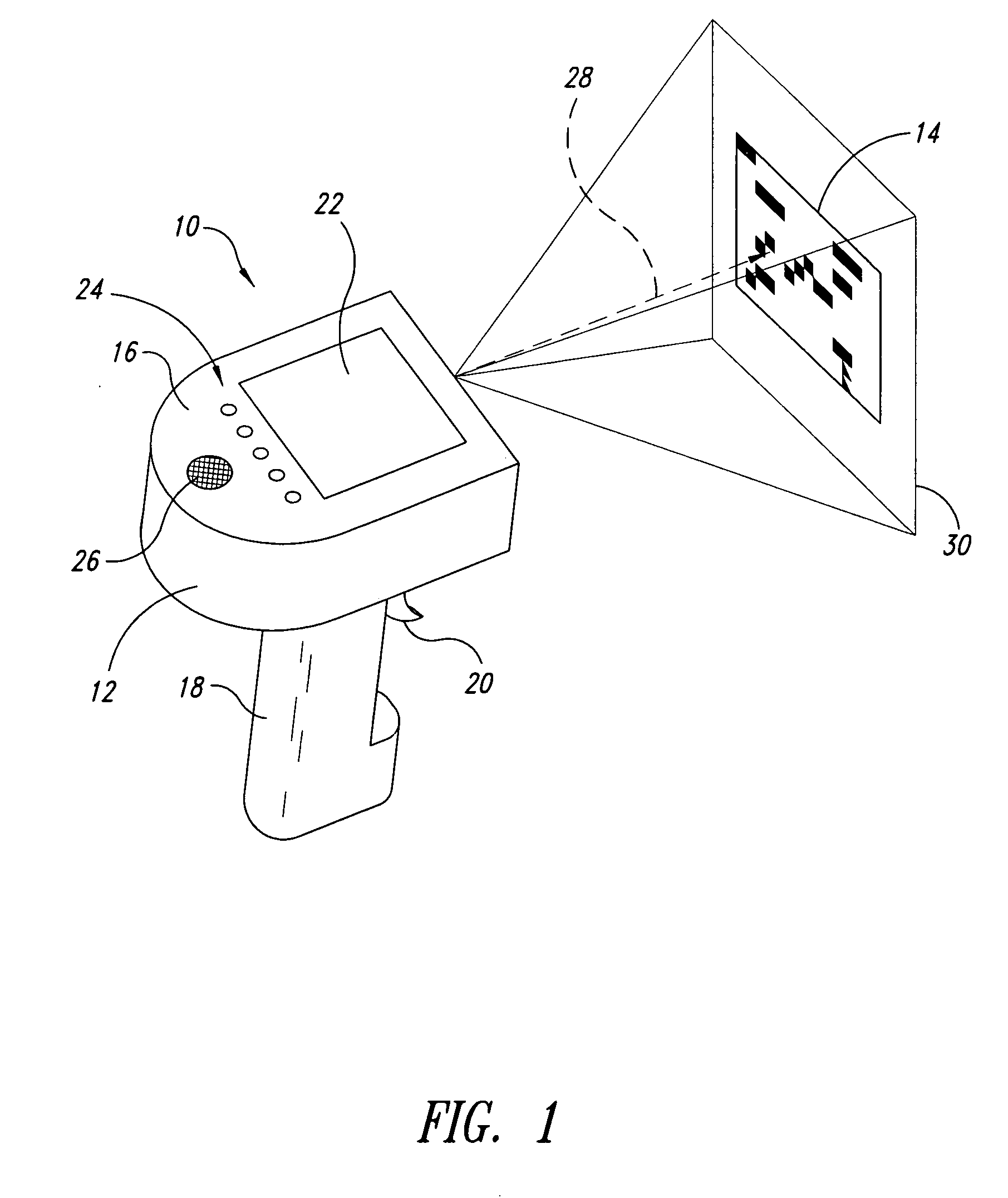
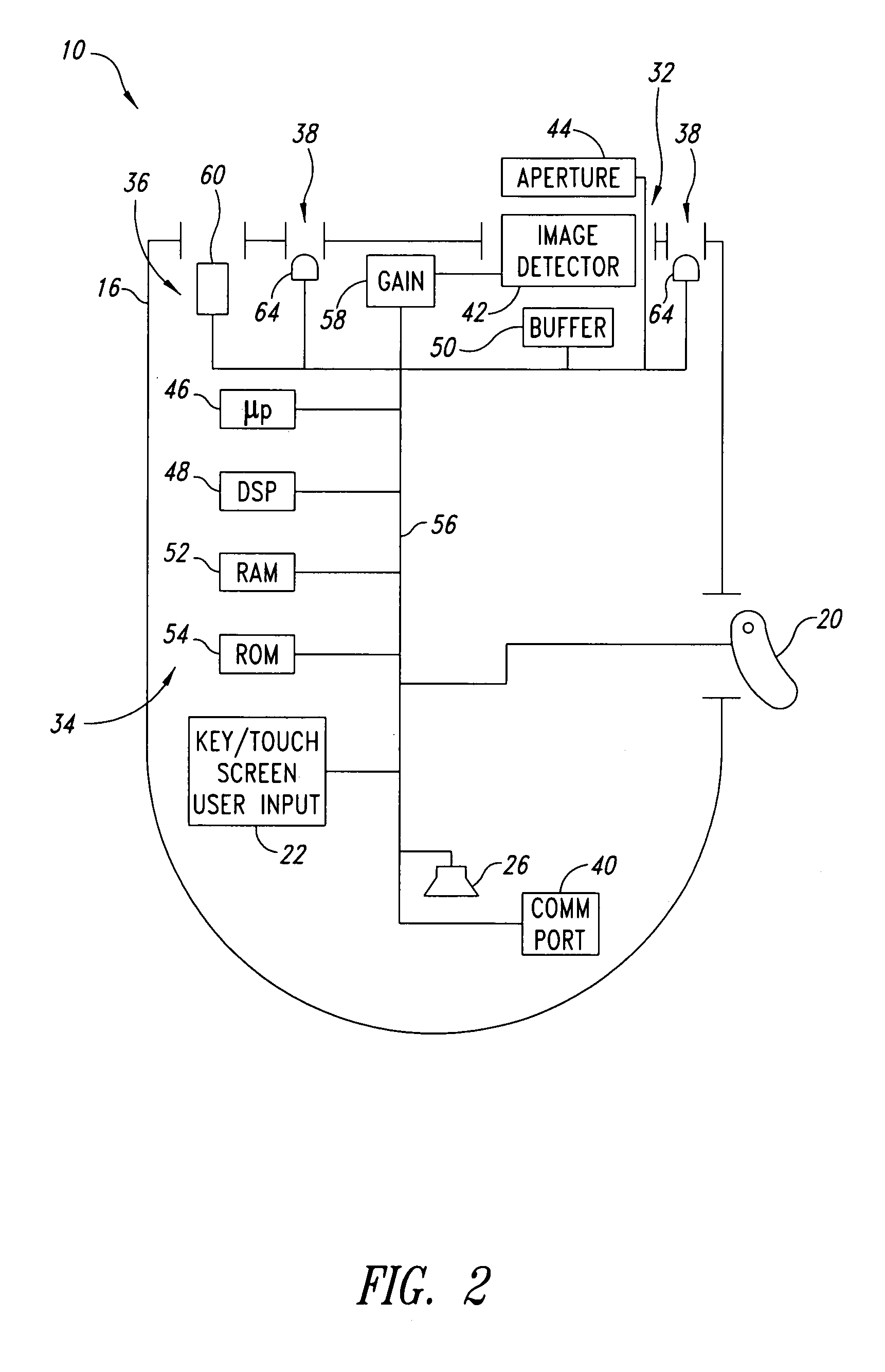
System, method and article for enhancing aiming in machine-readable symbol readers, such as barcode readers
InactiveUS20050274806A1Easy to aimQuicker and efficient to capture and decodeCharacter and pattern recognitionSensing by electromagnetic radiationBarcode readerSystems approaches
A reader for reading machine-readable symbols such as barcode, area or matrix code, or stack code symbols employs an aiming beam which may continue to provide an indication of an orientation of a field-of-view of the reader for a set interval following a successful decode of a machine-readable symbol. This provides a more intuitive and efficient user interface, allowing a user to quickly aim at a next symbol to be acquired, without inadvertently acquiring and / or decoding an unintended symbol. This may also reduce the number of user actions required to operate the reader, and may simplify the triggering mechanism interface.
Owner:INTERMEC IP
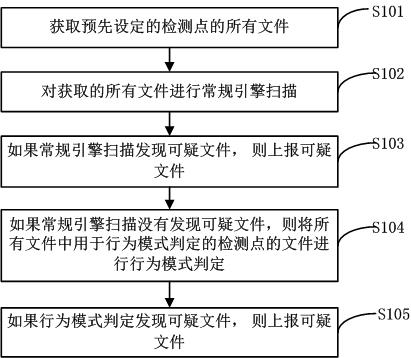
Method and system for quickly detecting malicious code
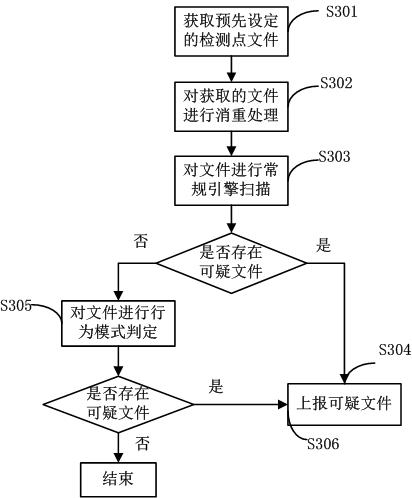
ActiveCN102024113AQuick checkRapid positioningPlatform integrity maintainanceDirectional analysisData acquisition
The invention discloses a method and a system for quickly detecting a malicious code. The method comprises the following steps of: acquiring all files at preset detection points; performing conventional engine scanning on all the acquired files; reporting a suspicious file if the suspicious file is discovered; performing behavior pattern judgment on files at detection points for the behavior pattern judgment in all the files if the suspicious file is not discovered; and reporting the suspicious file if the suspicious file is discovered. In the method, other normal files can be prevented from being scanned and the malicious code can be quickly positioned, so that the detection speed is improved. Meanwhile, in the method, attributes of a file without a feature code can be directly judged, so data acquisition and directional analysis are performed on a special environment, and the malicious code which cannot be detected by the conventional quick scanning is detected.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
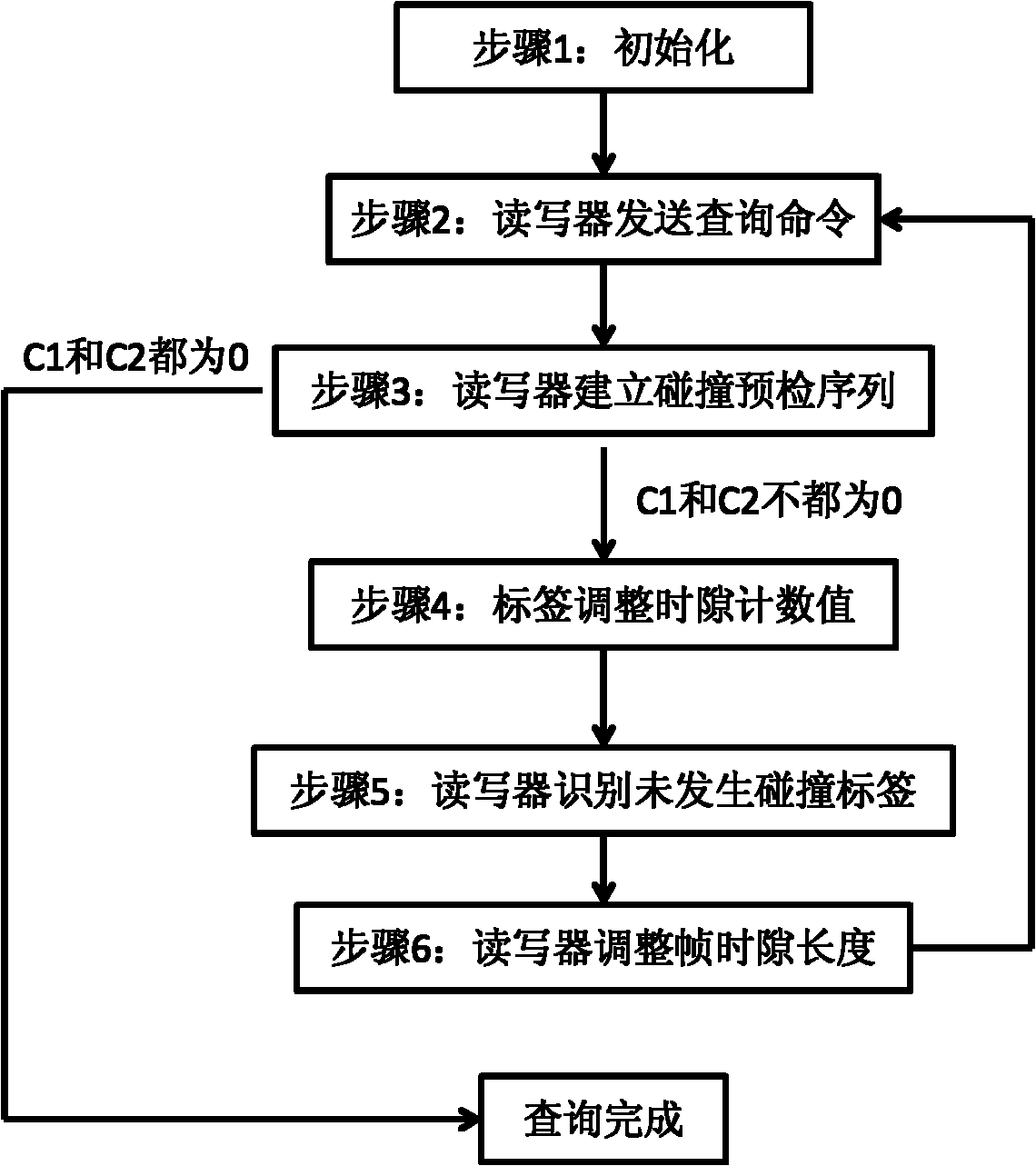
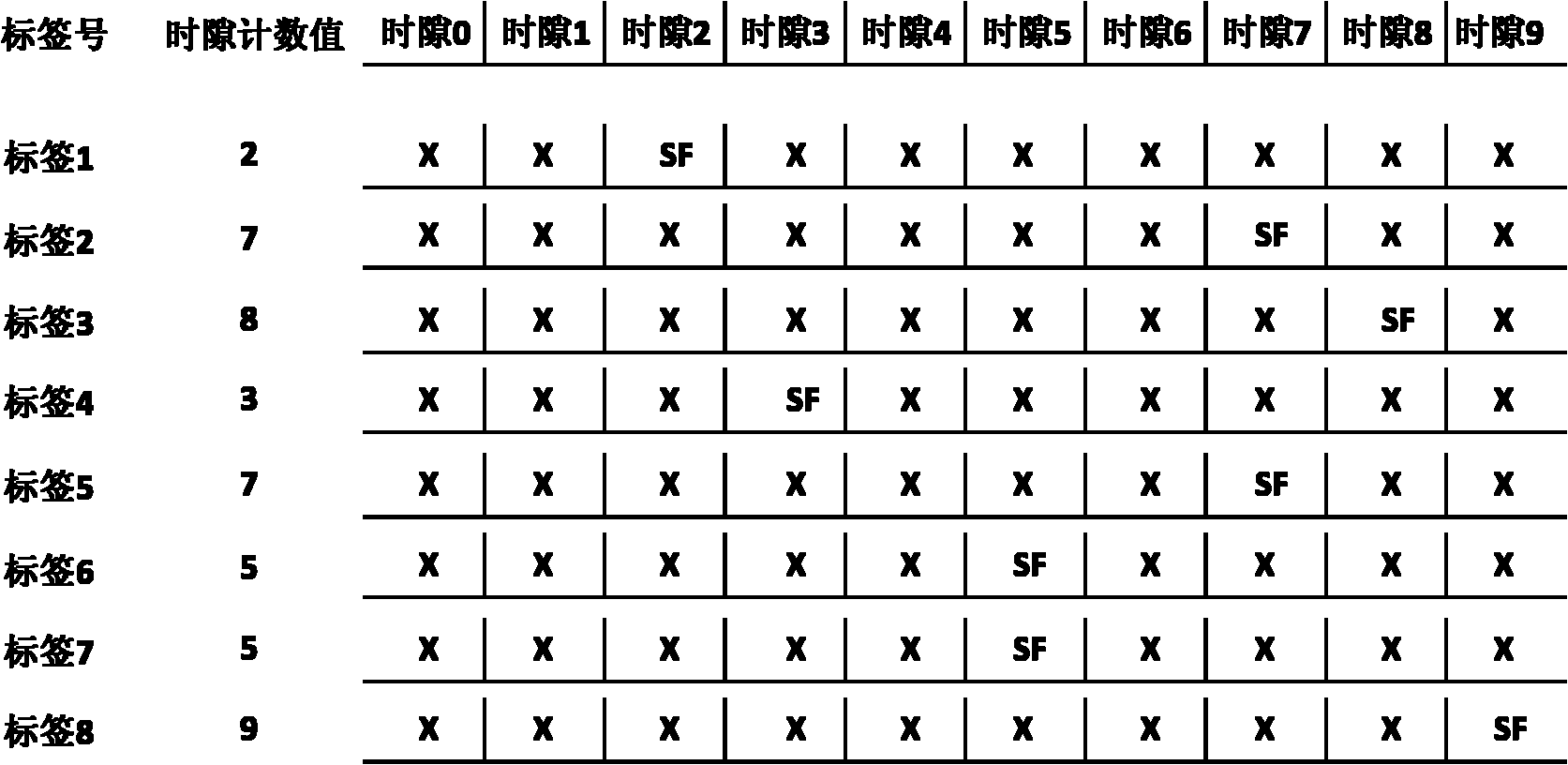
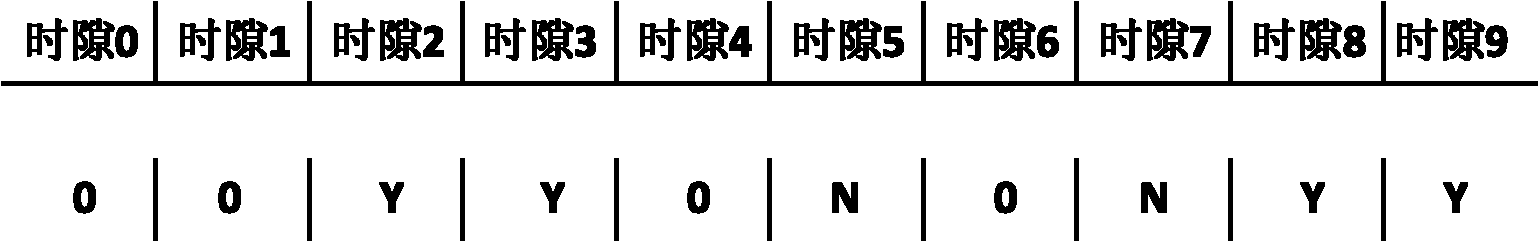
Time slot scanning anti-collision method based on collision precheck
ActiveCN102004895AImprove communication efficiencyImprove efficiencyCo-operative working arrangementsSensing record carriersCollision detectionFrame time
The invention provides an anti-collision method used in a radio-frequency identification system for realizing the communication between a single reader writer and multiple tags. The technical scheme comprises the following six steps: 1, initialization is carried out; 2, the reader writer sends an inquiry command; 3, the reader writer establishes a collision precheck sequence; 4, the tags adjust the time slot count value; 5, the reader writer identifies tags not subjected to collision; and 6, the reader writer adjusts the frame time slot length. By combining the empty time slot scanning technology and the short-frame collision detection technology, the invention omits the check of the reader writer on idle time slots and time slots occupied by the multiple tags, thereby improving the multi-tag identification efficiency of the system.
Owner:NAT UNIV OF DEFENSE TECH
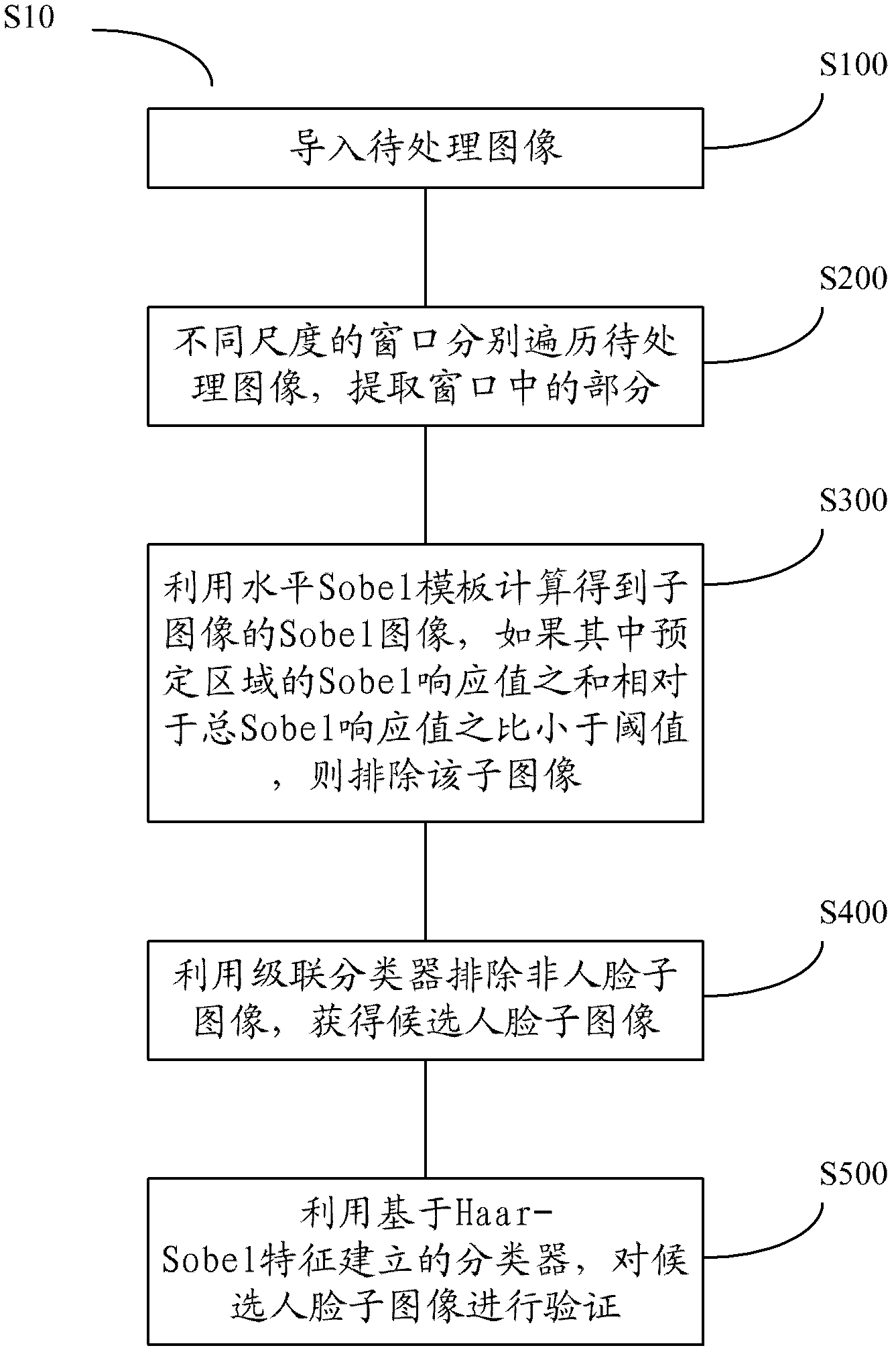
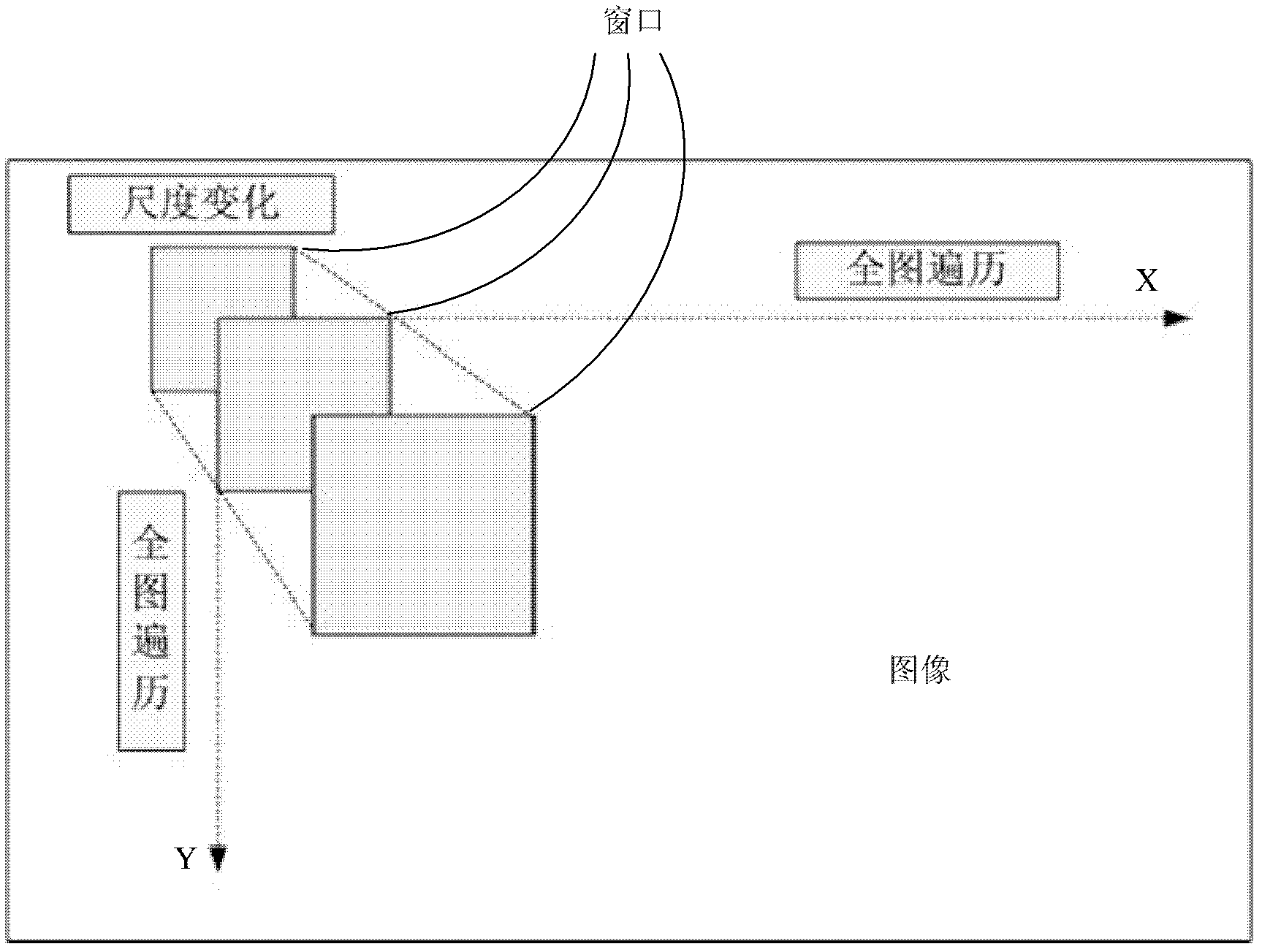
Human face detection method and human face detection equipment
ActiveCN103049733AGuaranteed detection effectGuaranteed detection speedCharacter and pattern recognitionFace detectionPattern recognition
The invention provides a human face detection method, comprising the steps of: importing: importing an image to be processed; sub-image extracting: traversing the image to be processed by using windows of different scales to extract parts of the image to be processed in the windows to serve as sub-images; preprocessing: specific to the sub-images, calculating a Sobel image of each sub-image by using a horizontal Sobel template, and excluding the sub-image if the ratio of the sum of Sobel response values of a predetermined region in the Sobel image to the total Sobel response value of the sub-image is smaller than a preset ratio threshold; detecting: specific to the sub-images passing the preprocessing, excluding non-human-face images by using an Adaboost cascade classifier to obtain candidate human-face sub-images; and verifying: specific to the candidate human-face sub-images, verifying the candidate human-face sub-images by using an Adaboost classifier established based on Haar-Sobel features so as to exclude the non-human-face sub-images, wherein the rest sub-images are taken as the human-face sub-images. The invention further provides human-face detection equipment correspondingly.
Owner:RICOH KK
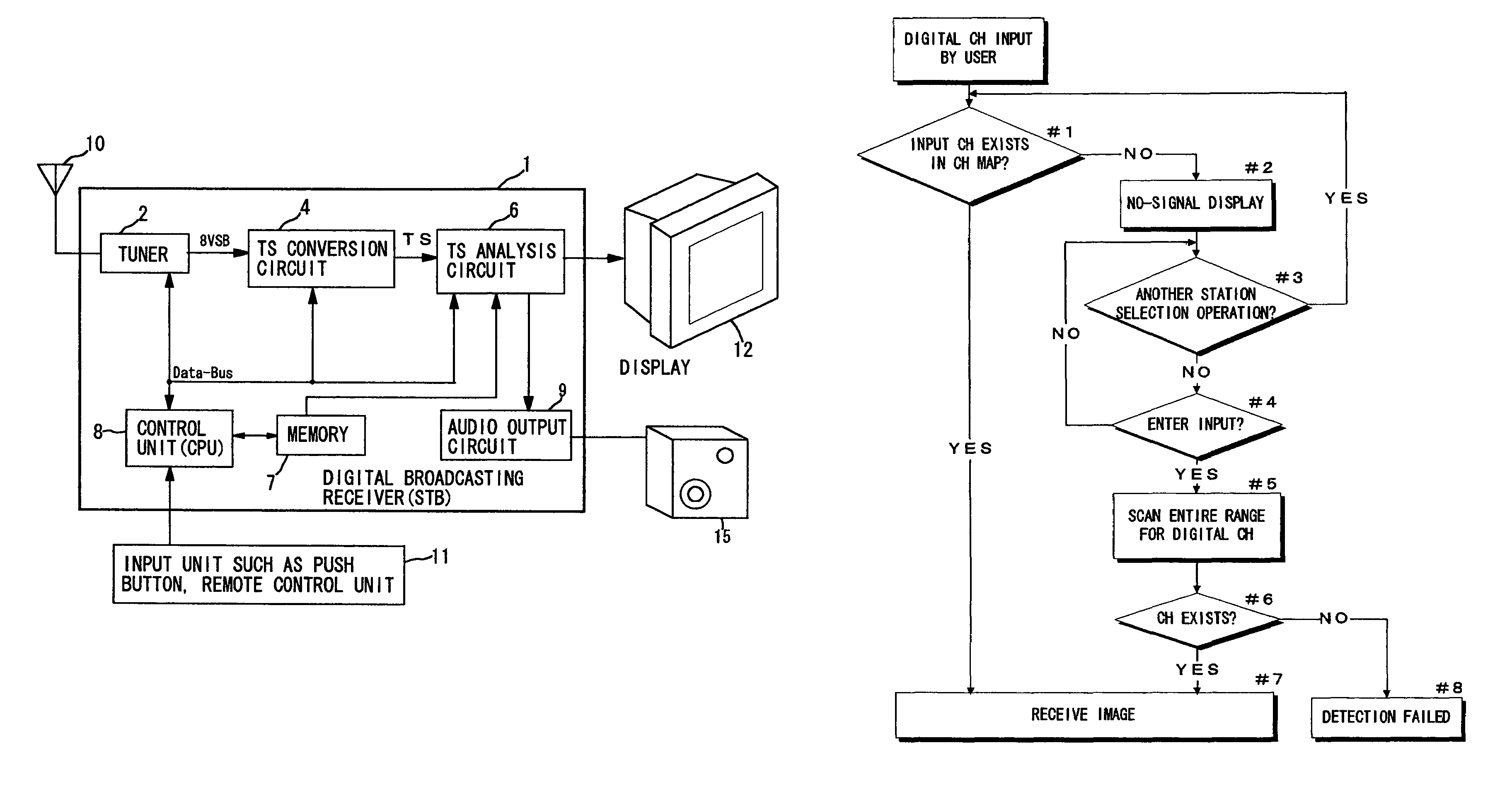
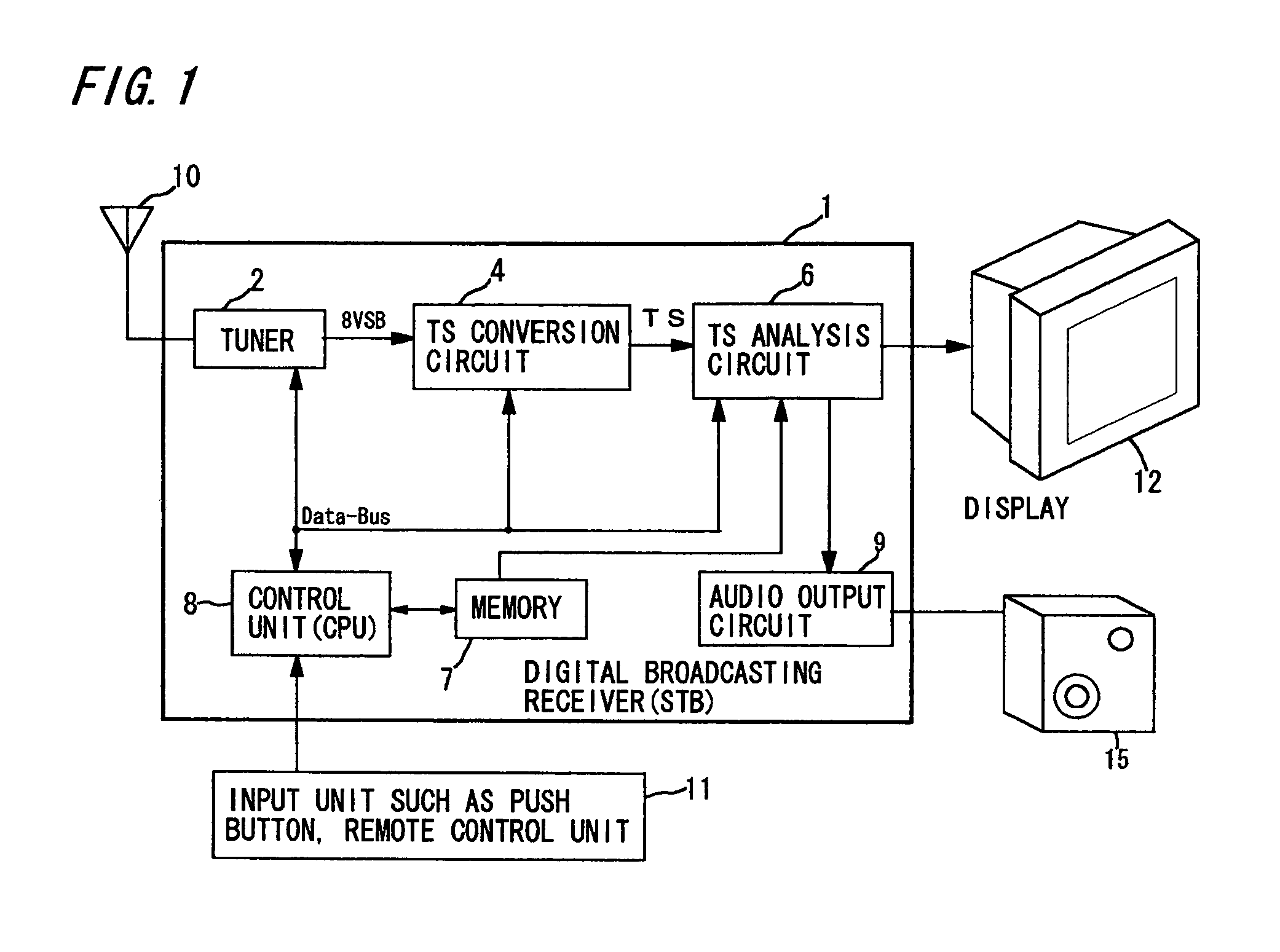
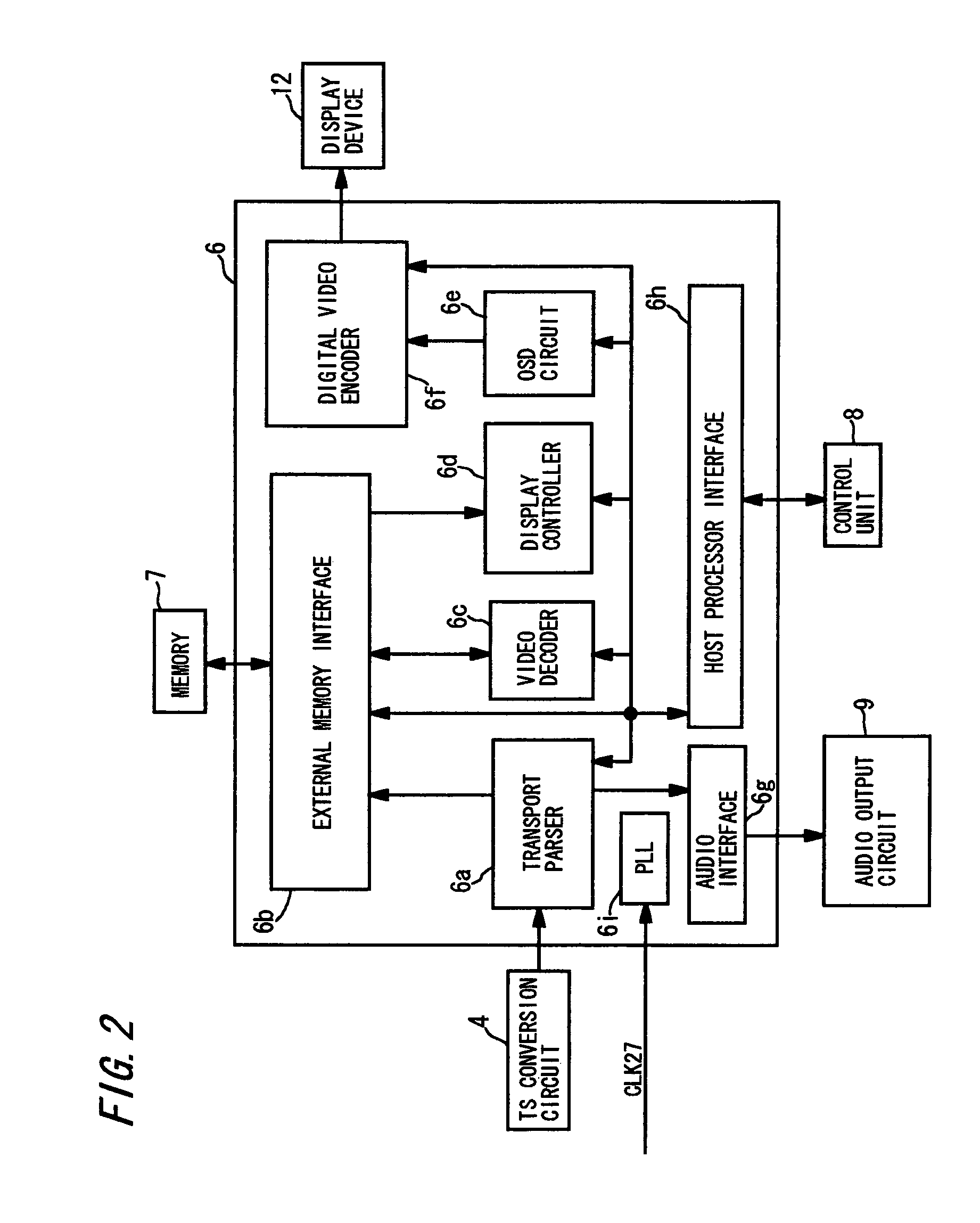
Digital broadcasting receiver
InactiveUS7092044B2Avoid scanningBroadcast with distributionTelevision system detailsUser inputDisplay device
A digital broadcasting receiver that uses a channel map containing broadcast information such as channel numbers and virtual channel numbers is described. When a user selects a certain digital channel number, a control unit consisting of a CPU makes a search as to whether or not the number exists in the channel map. If the number does not exist, “No Signal” notice is displayed on a display and if the user selects a scan instruction then, the entire range of frequency band of the broadcasting signal is scanned. If a signal that corresponds to the digital channel number exists, its broadcast is received. Therefore, a search is possible even when the user knows only a virtual channel number and the digital channel number entered by the user is not registered in the channel map.
Owner:FUNAI ELECTRIC CO LTD
Fast star map identification method of star sensor
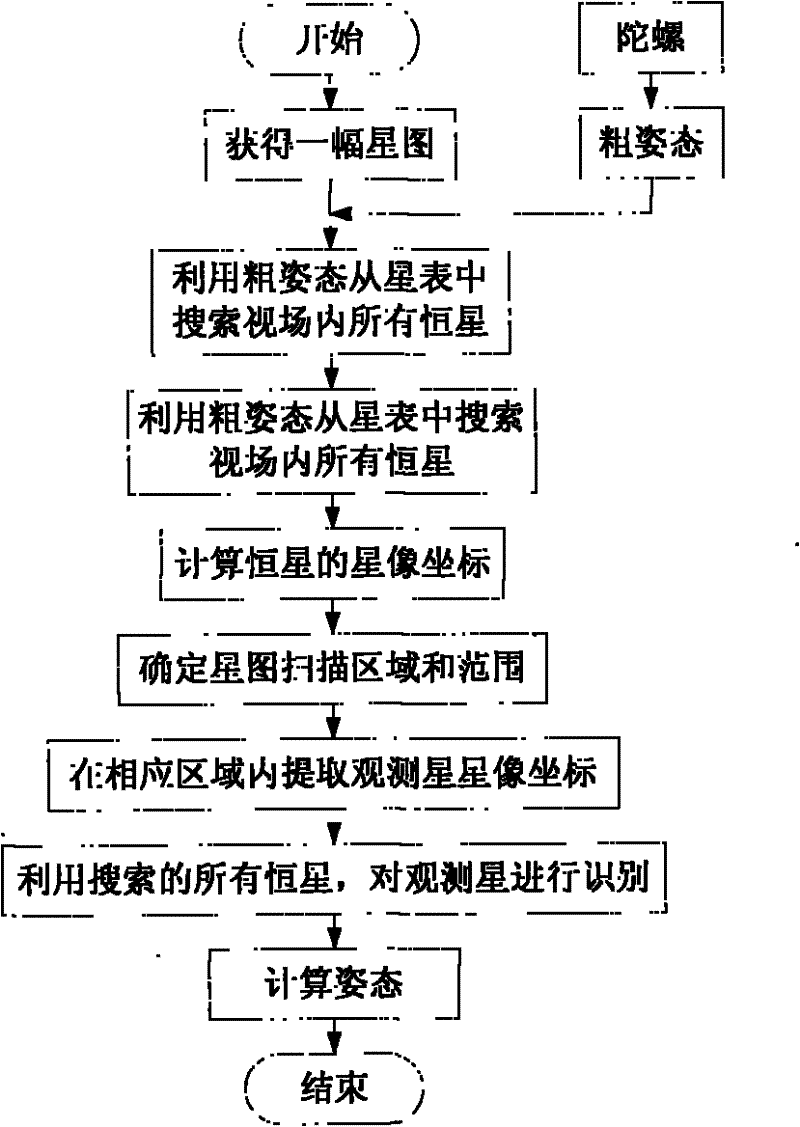
InactiveCN102128623AAvoid all-sphere searchShorten recognition timeNavigation by astronomical meansStar sensorIdentification rate
The invention provides a fast star map identification method of a star sensor, which avoids all-celestial sphere search, reduces the identification time and improves the identification rate. The method comprises the following steps: obtaining a complete star map, and obtaining the current rough gesture of the star sensor by use of a gyroscope combination system; searching all fixed stars in the viewing field from a star table by use of the rough gesture through the star sensor, and calculating possible positions of all fixed stars in the viewing field in an image plane; scanning a small area of the star map centered on the positions, and extracting the star image coordinates of a corresponding observation star; identifying the extracted observation star by use of all fixed stars in the viewing field; and sending the identification result to a gesture calculation module which calculates the current gesture of the star sensor. According to the invention, possible fixed stars in the viewing field of the star sensor are predicted by use of the sensor information, and only by scanning the possible position range in the star map, the star image coordinates of the observation star can be extracted from the star map, thereby avoiding the process of scanning the entire star map; and moreover, as all-celestial sphere search is avoided, the identification time is reduced, and the identification rate is improved.
Owner:HARBIN INST OF TECH
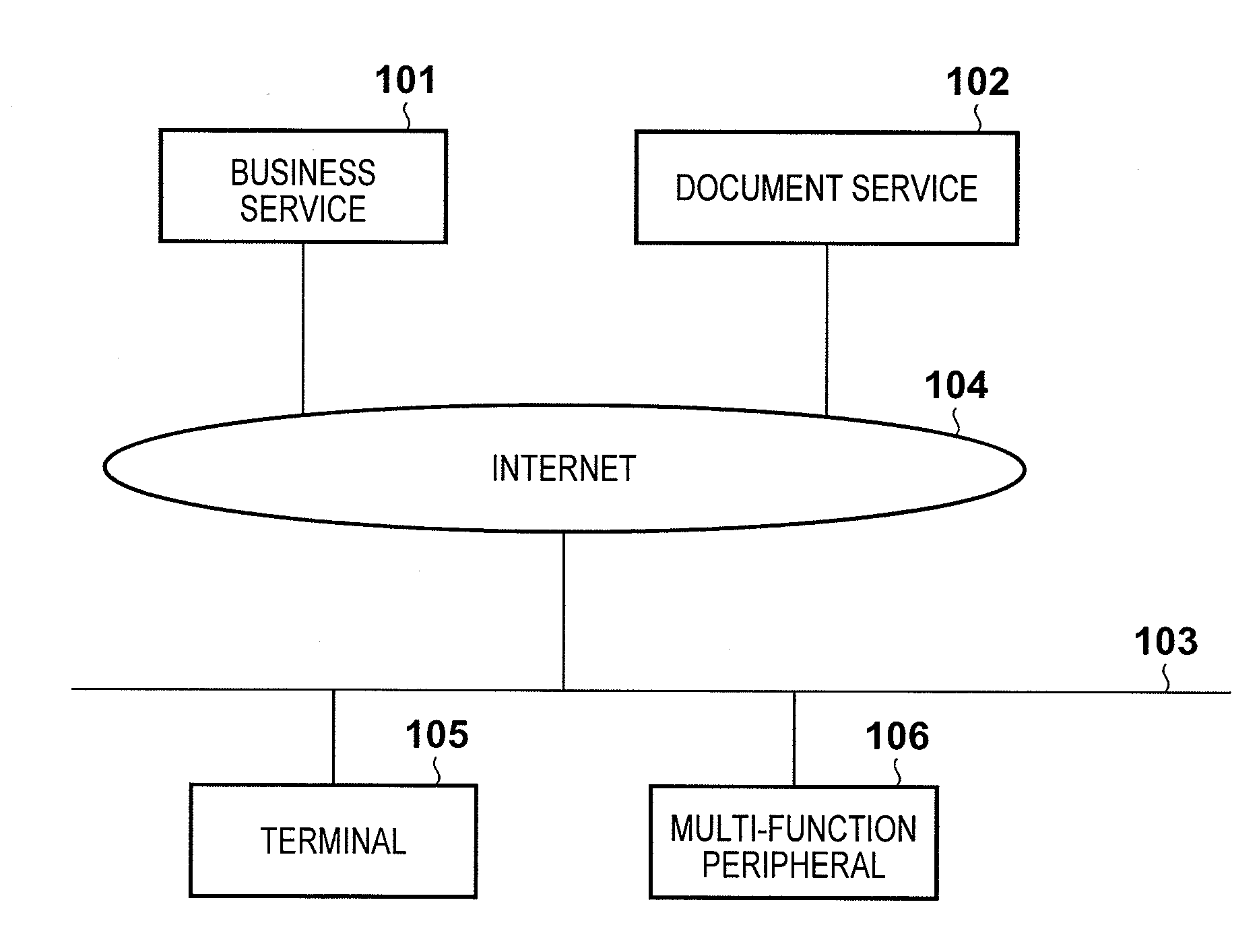
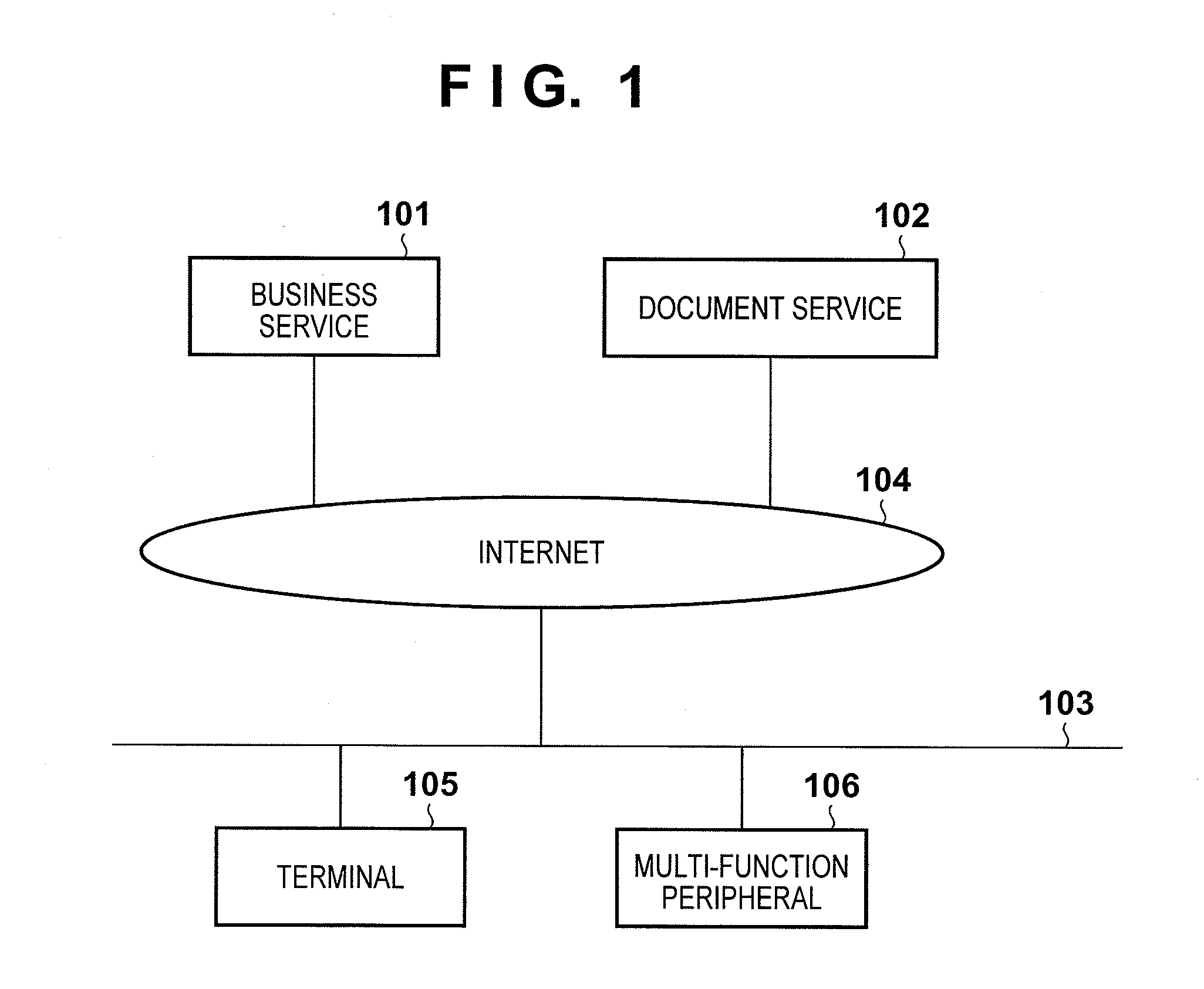
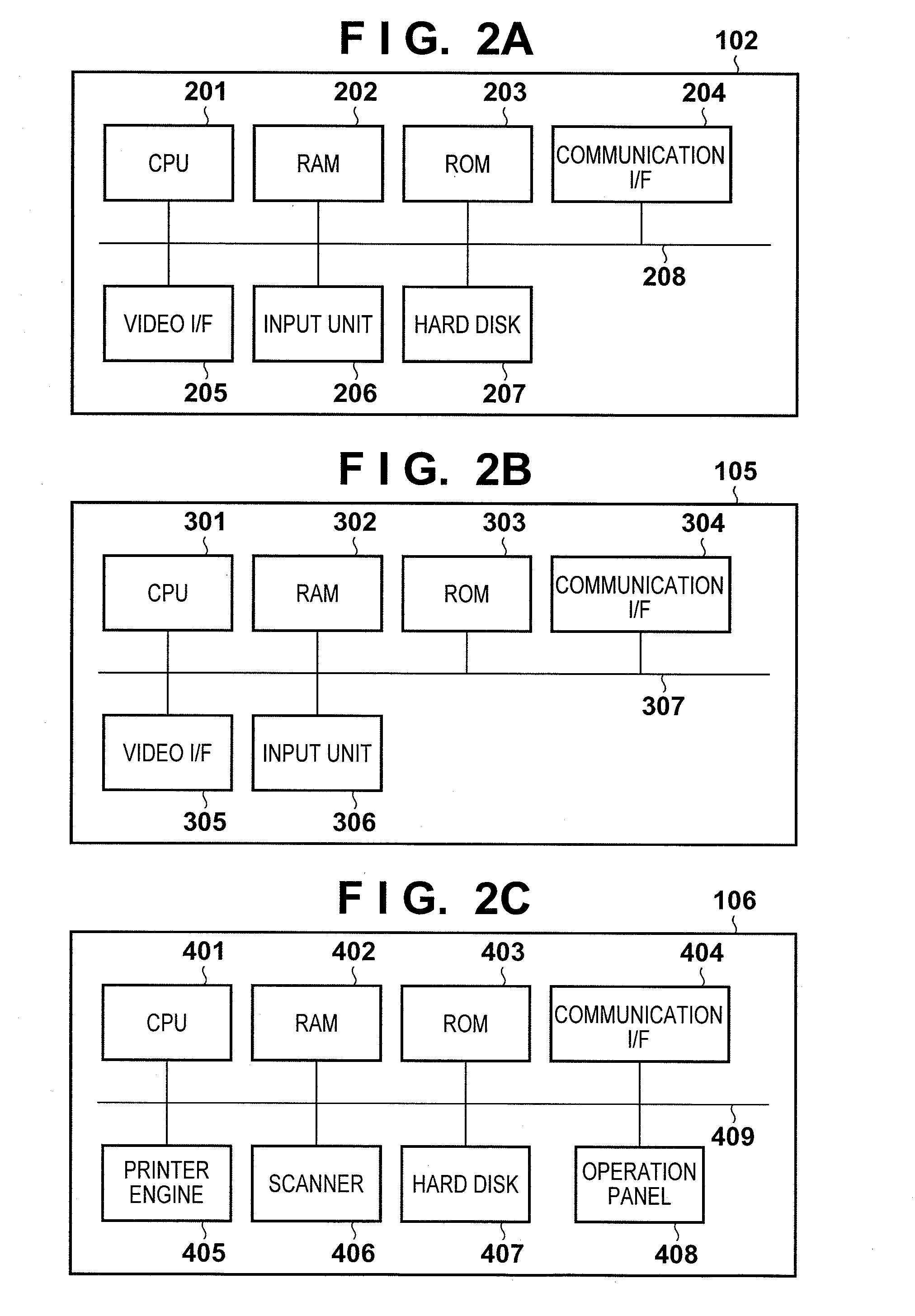
Scanning system, printing system, service providing system, and control method
InactiveUS20120182575A1Improve securityEasy to displayDigital computer detailsPictoral communicationService provisionProcessing element
A scanning system comprises a server, scanner, and terminal, the server including: a reception unit configured to receive a scan setting and a start instruction from one of the scanner and the terminal; a storage unit configured to store the scan setting and to issue the identification information; a determination unit configured to determine which of the scanner and the terminal has transferred the scan setting and the start instruction; and a processing unit configured, when the determination unit determines that the scanner has transferred the scan setting and the start instruction, to transfer the scan setting and the start instruction to the scanner, and when the determination unit determines that the terminal has transferred the scan setting and the start instruction, to cause the storage unit to store the scan setting and to transfer, to the scanner, identification information indicating the stored scan setting.
Owner:CANON KK
Distributed automatic application operation abnormity detecting method and system
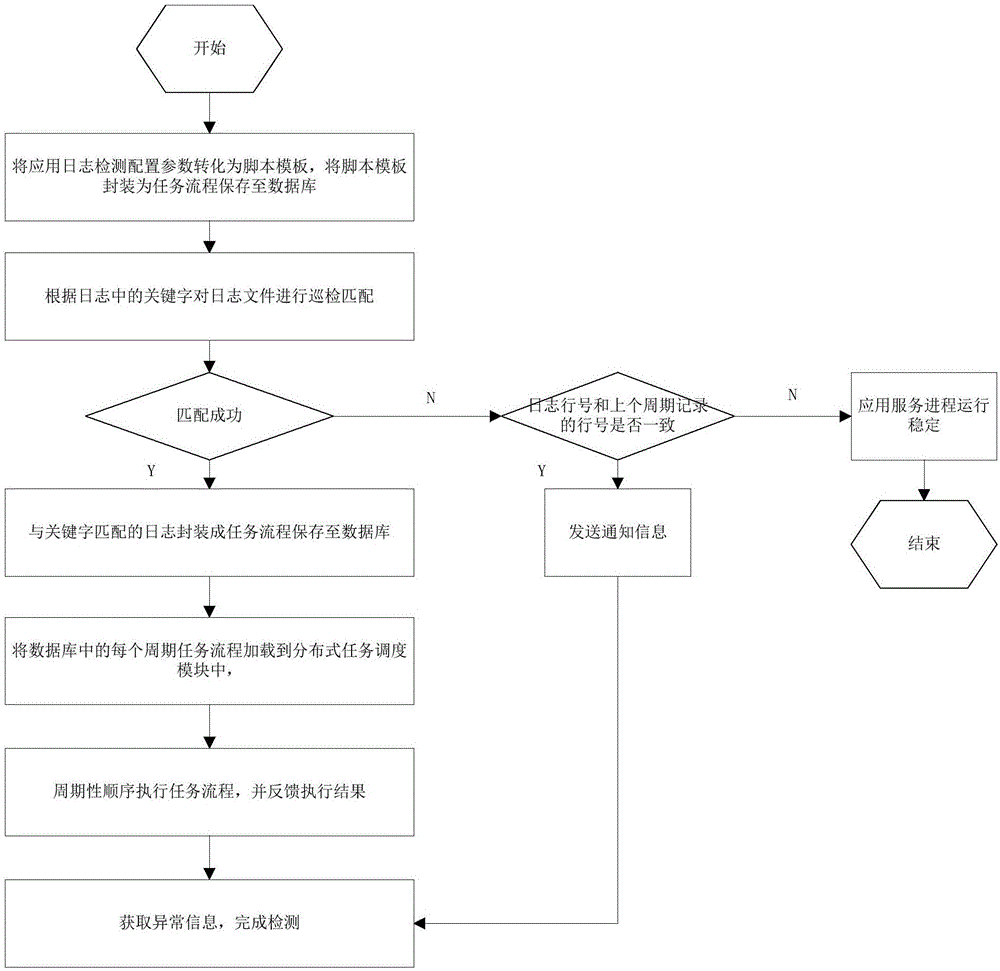
ActiveCN106681930AAvoiding Duplicate Logging IssuesEasy to detectSoftware testing/debuggingRepeatabilitySafe operation
The invention relates to a distributed automatic application operation abnormity detecting method and system. The distributed automatic application operation abnormity detecting method comprises the steps that routing inspection and matching are conducted on log files according to keywords in logs, the logs matched with the keywords are packaged into task processes to be saved in a database, each periodic task process in the database is loaded to distributed task scheduling modules, the task processes are periodically executed, execution results are red back, abnormity information is obtained according to the fed-back execution results, and detection is completed. The distributed automatic application operation abnormity detecting method can automatically detect whether application service operation is abnormal or not, the problem that full-amount log scanning is required during each time of detection and accordingly a large number of repeated logs is produced is avoided, detecting results are accurate while the detection process can be simplified through increment scanning and matching of application logs during each time of detection. In addition, load is balanced through the multiple distributed task scheduling modules, the disaster tolerant capability of the system is greatly improved, and safe operation of the system is ensured.
Owner:北京思特奇信息技术股份有限公司
Mobile device starting method and device
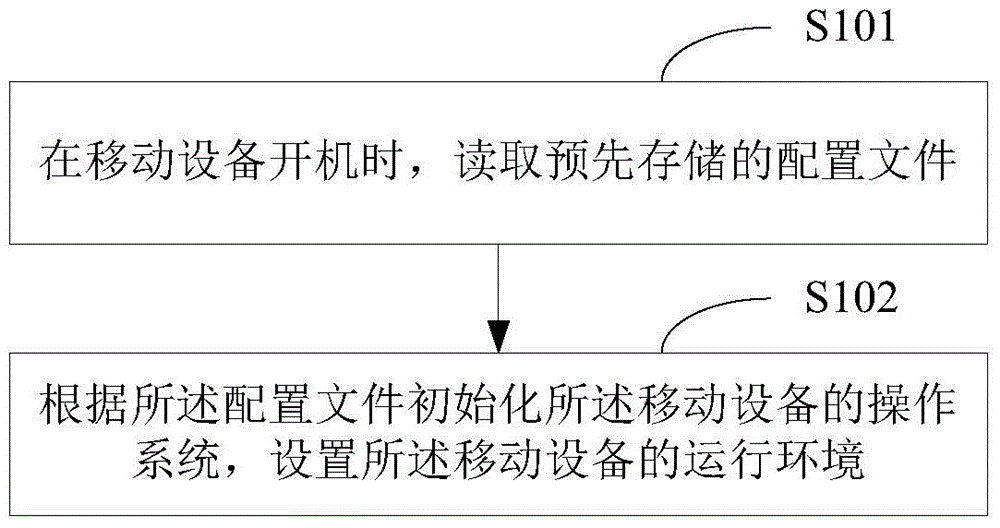
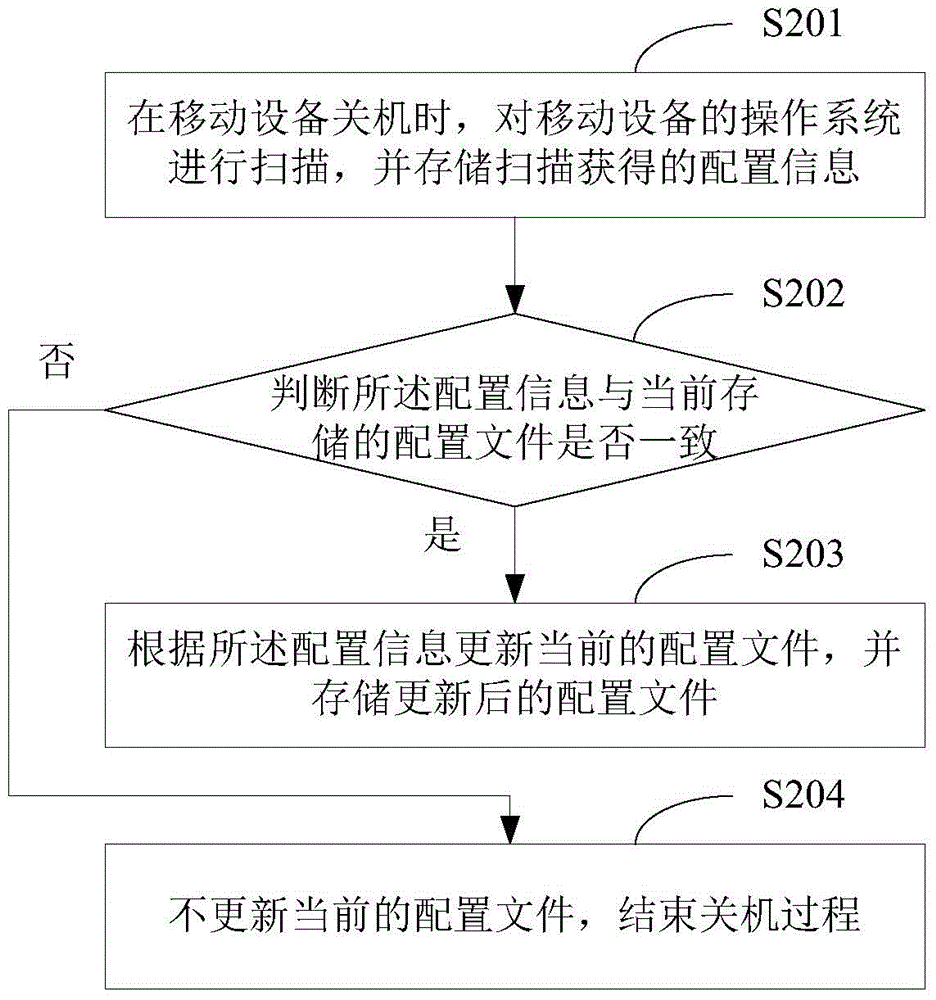
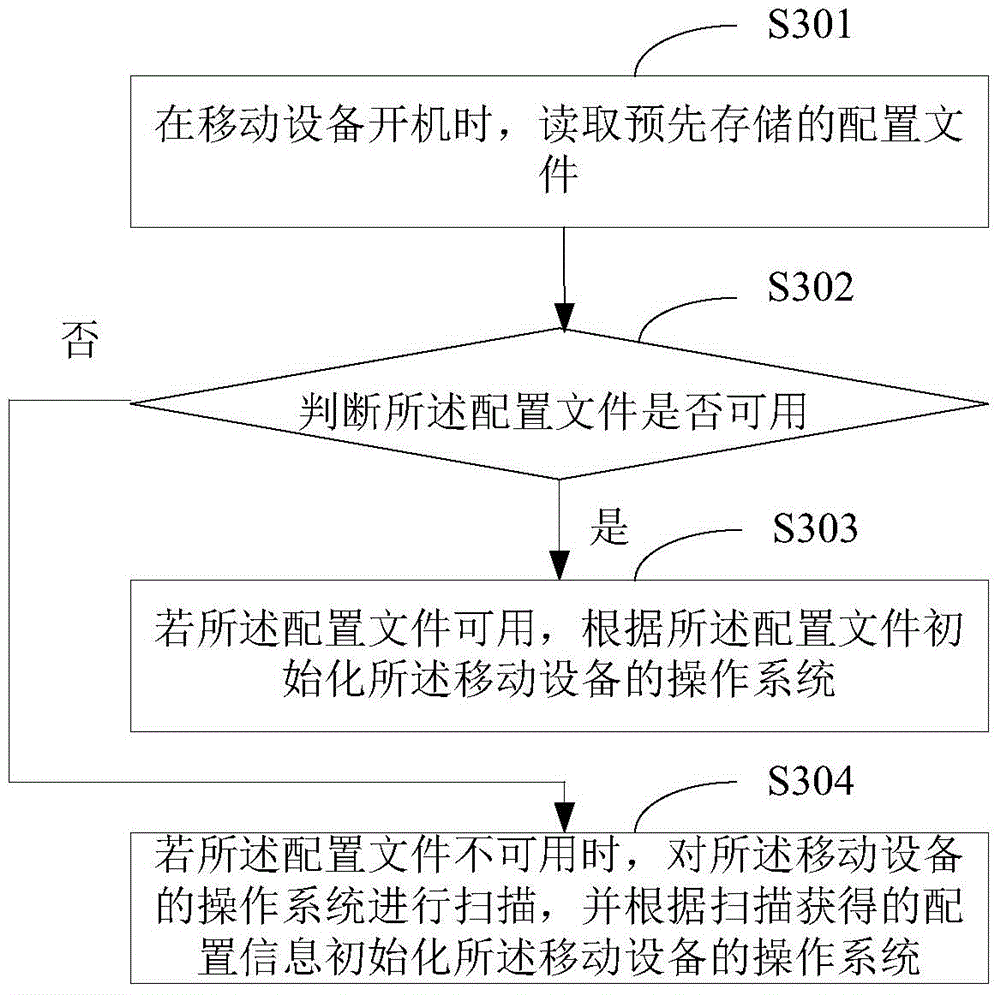
InactiveCN104636165AEasy to bootShorten the timeProgram loading/initiatingOperational systemApplication software
The invention belongs to the technical field of mobile devices, and provides a mobile device starting method and device. The method comprises the steps of reading a prestored configuration file when a mobile device is started; initializing an operating system of the mobile device according to the configuration file, and setting the running environment of the mobile device, wherein the configuration file comprises configuration information of each application program in the operating system. According to the starting method, the phenomenon that the operating system is scanned when the mobile device is started is avoided, the time spent in the scanning process when the mobile device is started is shortened, and then the starting speed of the mobile device is increased.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
Connected domain extraction method and device
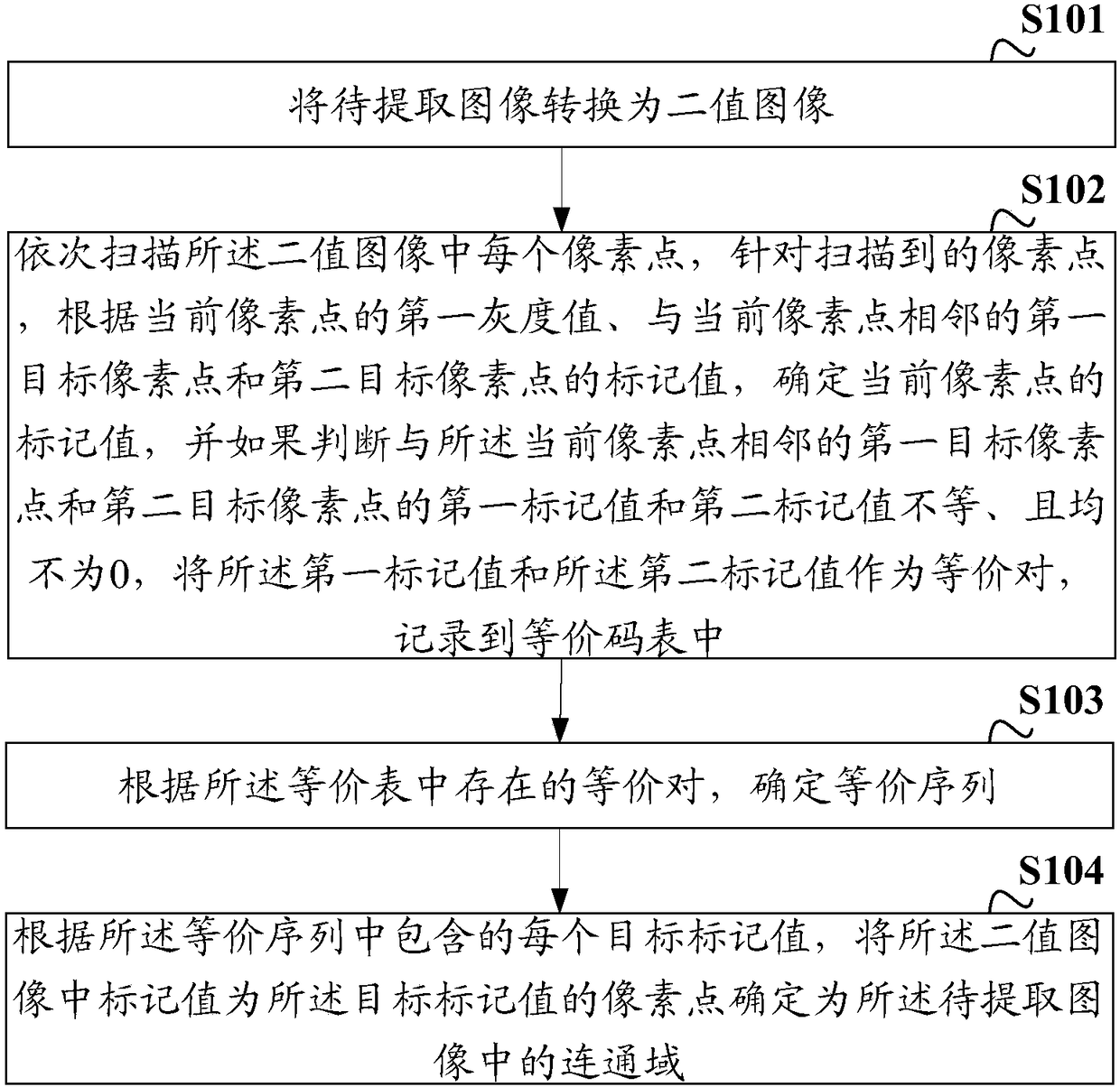
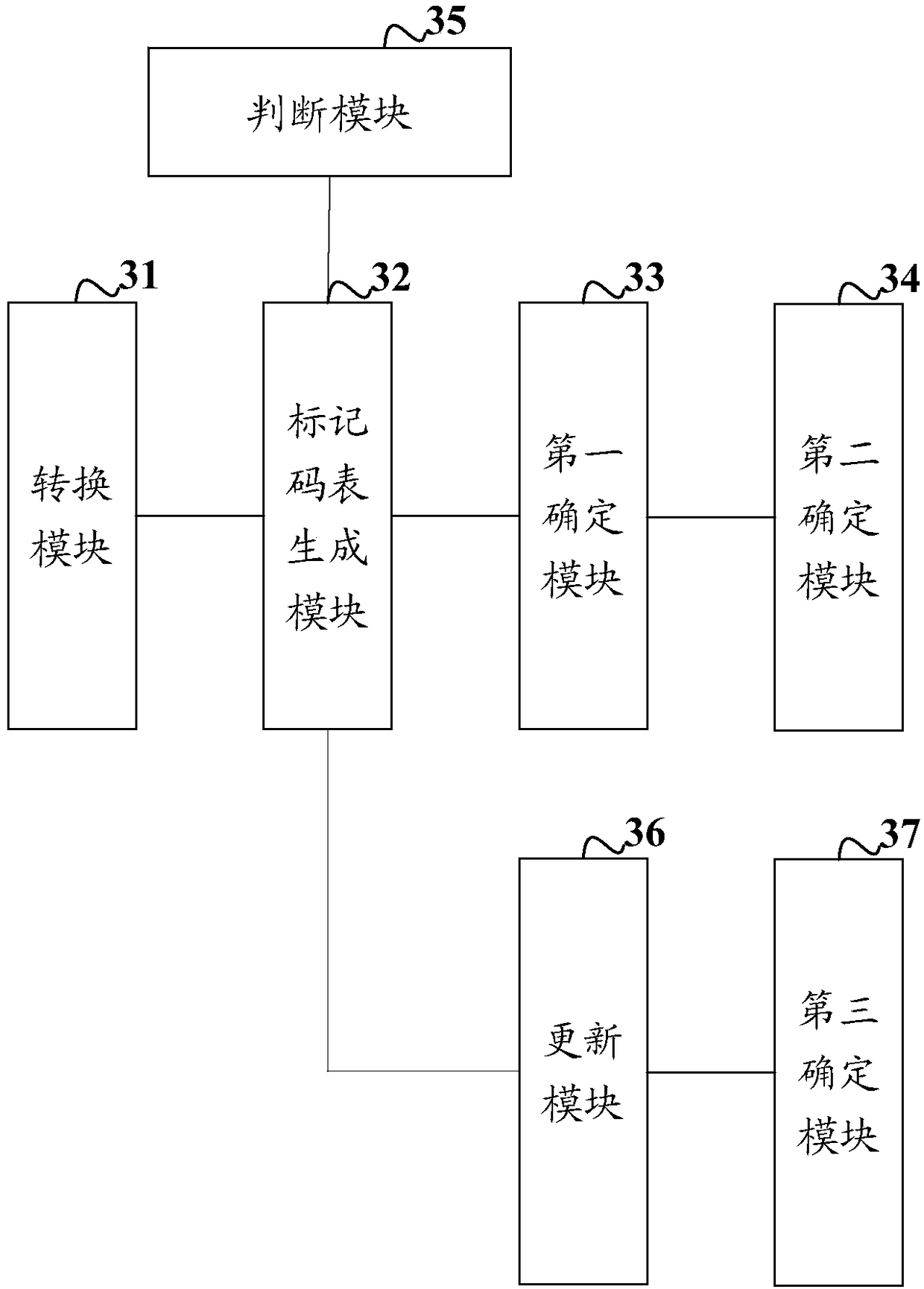
InactiveCN108345888AEasy extractionImprove extraction efficiencyCharacter and pattern recognitionPattern recognitionImage conversion
The invention discloses a connected domain extraction method and device, and the method comprises the steps: converting a to-be-extracted image into a binary image; sequentially scanning all pixels inthe binary image, determining a mark value of the current pixel of the scanned pixels according to a first gray scale value of the current pixel, a mark value of a first target pixel adjacent to thecurrent pixel and a mark value of a second target pixel; taking the first mark value and the second mark value as an equivalent pair if the first and second mark values of the first target pixel, adjacent to the current pixel, and the second target pixel are not equal and are not equal to zero, and recording the mark values into an equivalent code table; determining an equivalent sequence according to the equivalent pairs in the equivalent table; and determining the pixels with the mark values being target mark values in the binary image as a connected domain of a to-be-extracted image according to each target mark value in the equivalent sequence. The invention provides a simple and efficient connected domain extraction scheme.
Owner:ゼジャンハーレイテクノロジーカンパニーリミテッド
Statistical statement generating method of vehicle monitoring system
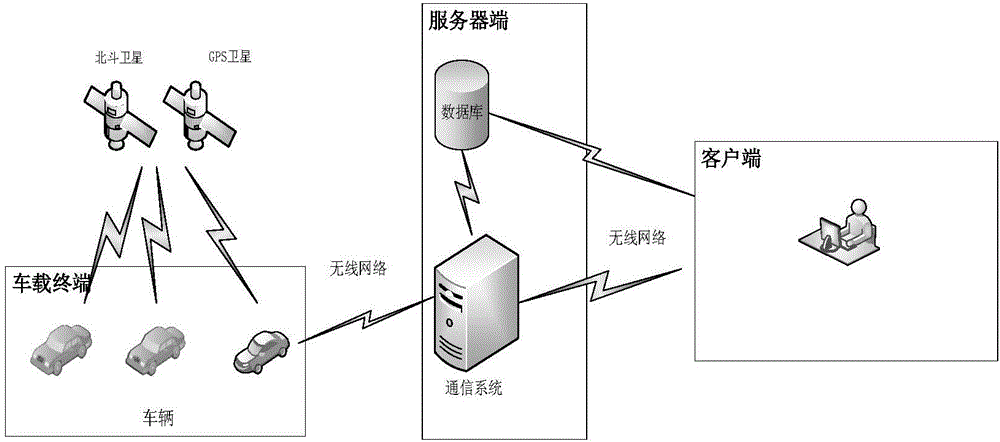
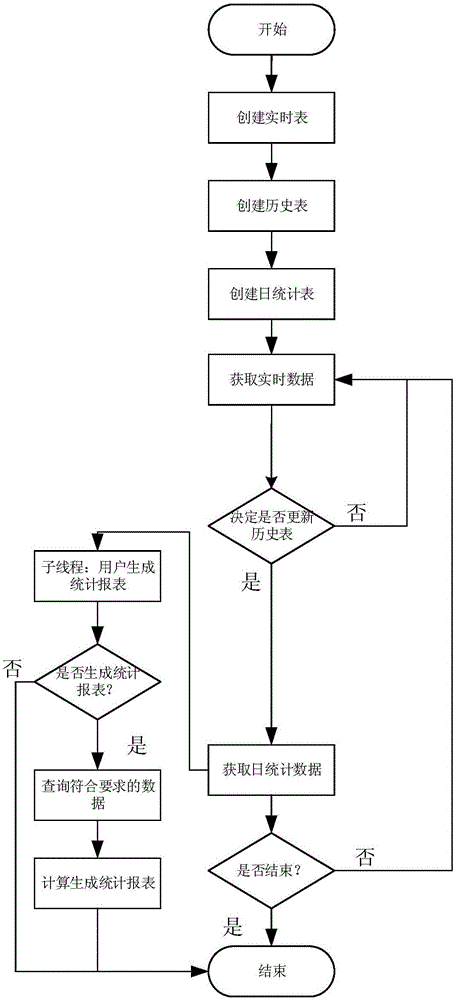
InactiveCN106682232AImprove query efficiencyImprove reusabilitySpecial data processing applicationsCurrent meterReal-time data
The invention discloses a statistical statement generating method of a vehicle monitoring system. The problem that overlong consumed time is caused by the low querying efficiency and the low data reusability when an existing statistical statement is generated is mainly solved. The statistical statement generating method in the technical scheme includes the steps that 1) a real-time table is established; 2) a history list is established; 3) a daily statistical table is established; 4) real-time data is obtained and stored in the real-time table; 5) when current time is zero o'clock in the morning, the history list is updated, and when current time is non-zero o'clock in the morning, the method returns to the step 4); 6) the real-time data is calculated, daily statistical data is obtained and stored in the daily statistical table, the real-time table is emptied, and the method returns to the step 4); 7) the daily statistical data meeting the requirements is screened to generate the statistical statement. According to the statistical statement generating method, the real-time data and history data are partitioned, the daily statistical data with the day as the particle size is stored in a database, it is avoided that a large amount of history data is scanned, the querying efficiency is improved, the data reusability is improved, the generating time of the statistical statement is shortened, and the statistical statement generating method can be used for real-time statistics of travelling chartered vehicles, third-grade-or-above route passenger vehicles and dangerous chemical vehicles.
Owner:XIDIAN UNIV
Processing method and device of quick response codes, video playing apparatus
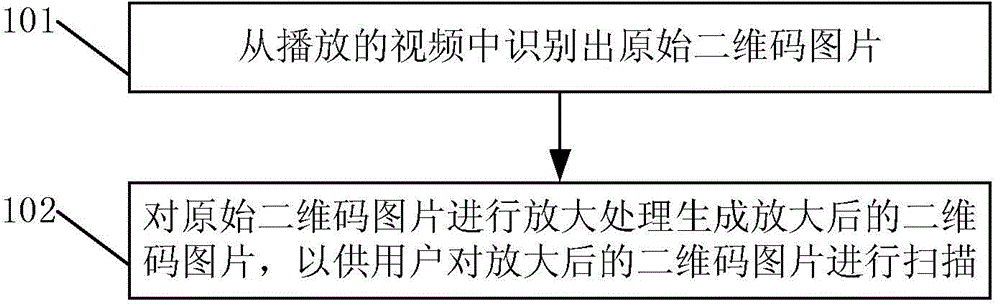
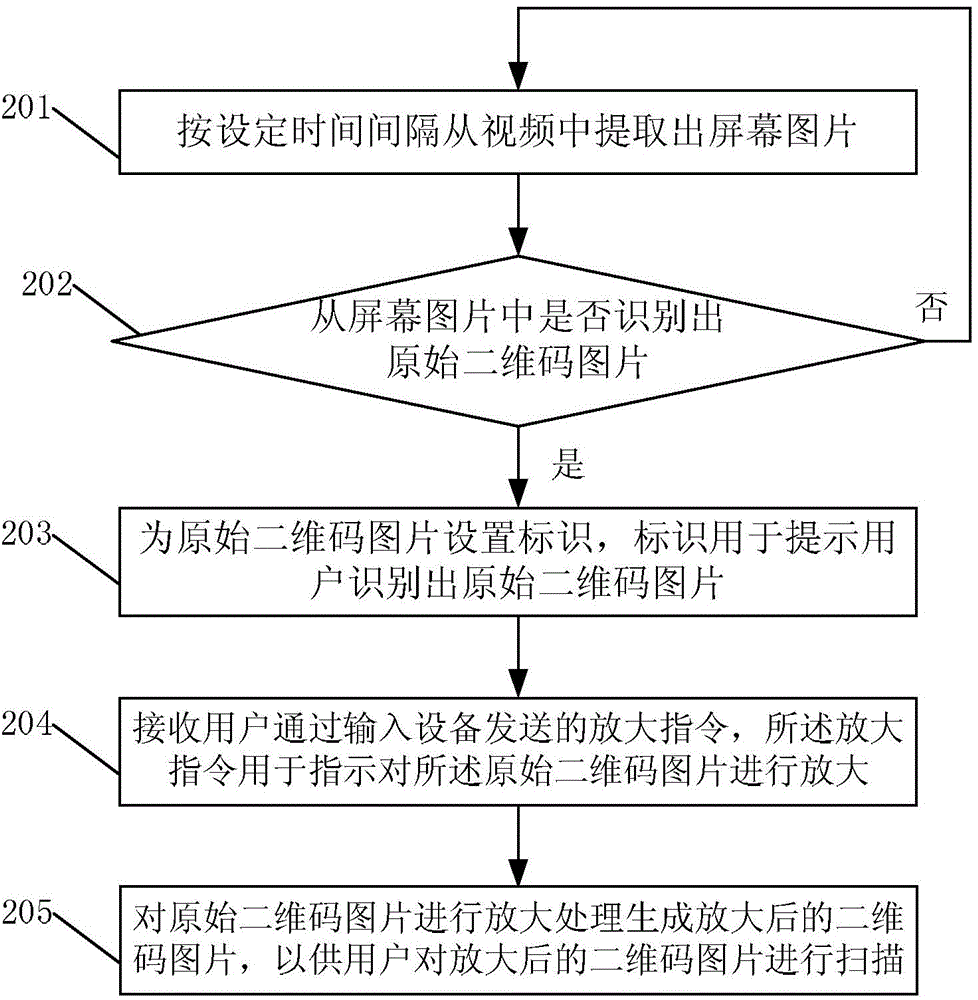
ActiveCN104703020AAvoid scanningImprove experienceSelective content distributionComputer scienceCable television
The invention discloses a processing method and a processing device of quick response codes, as well as a video playing apparatus. The processing method of the quick response codes comprises the following steps: recognizing an original quick response code image from a playing video; zooming in on the original quick response code image to generate a zoom-in quick response code image; accordingly, a user can scan the zoom-in quick response code image. In the technical scheme of the provided processing method of the quick response codes, the original quick response code image is recognized from the playing video; the zoom-in quick response code image is generated by zooming in on the original quick response code image; accordingly, the user can scan the zoom-in quick response code image; therefore, the situation of scanning the quick response code image only by walking beside the television is avoided, thereby increasing the user experience.
Owner:KUYUN INTERACTIVE TECH
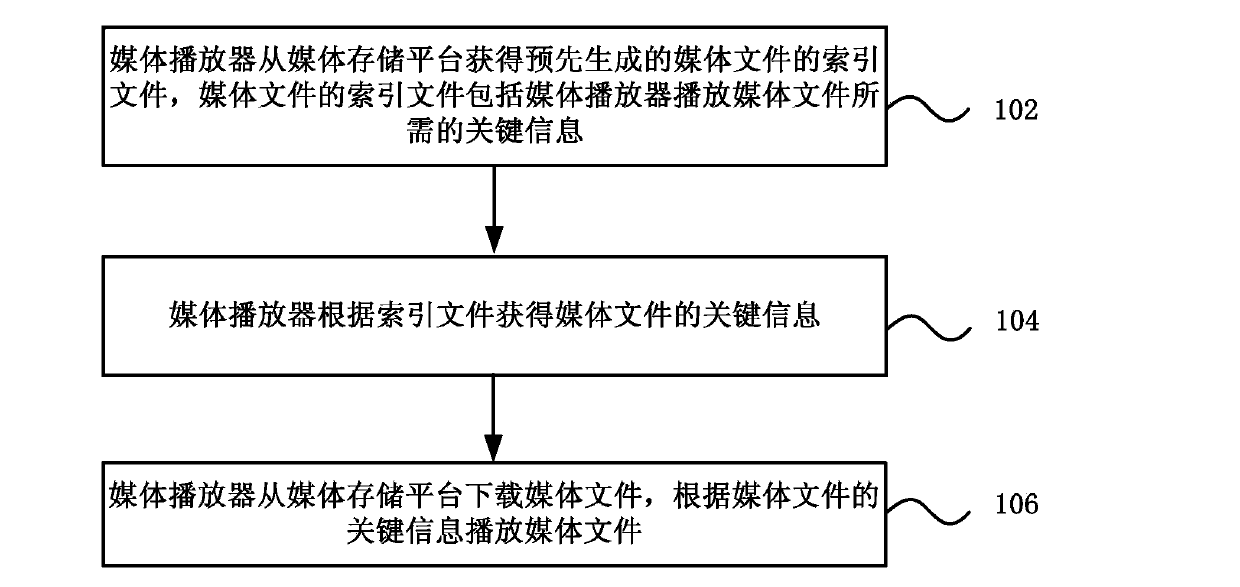
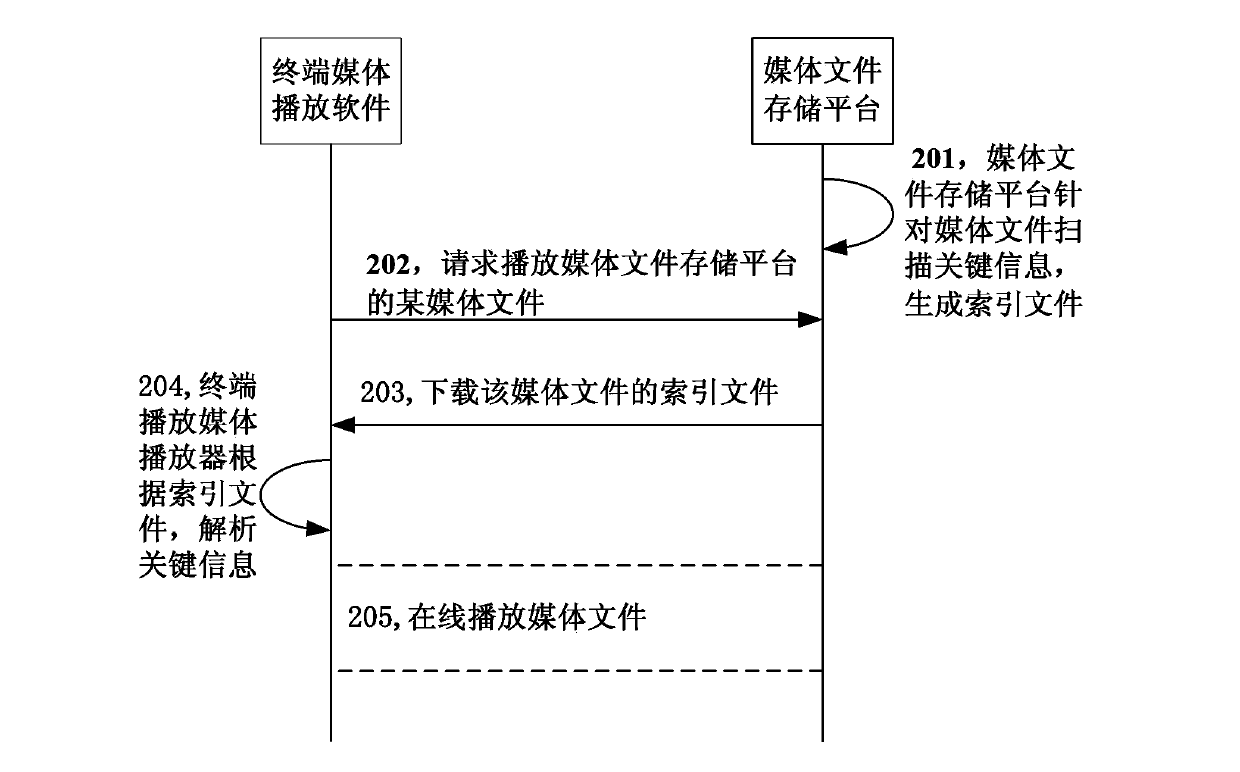
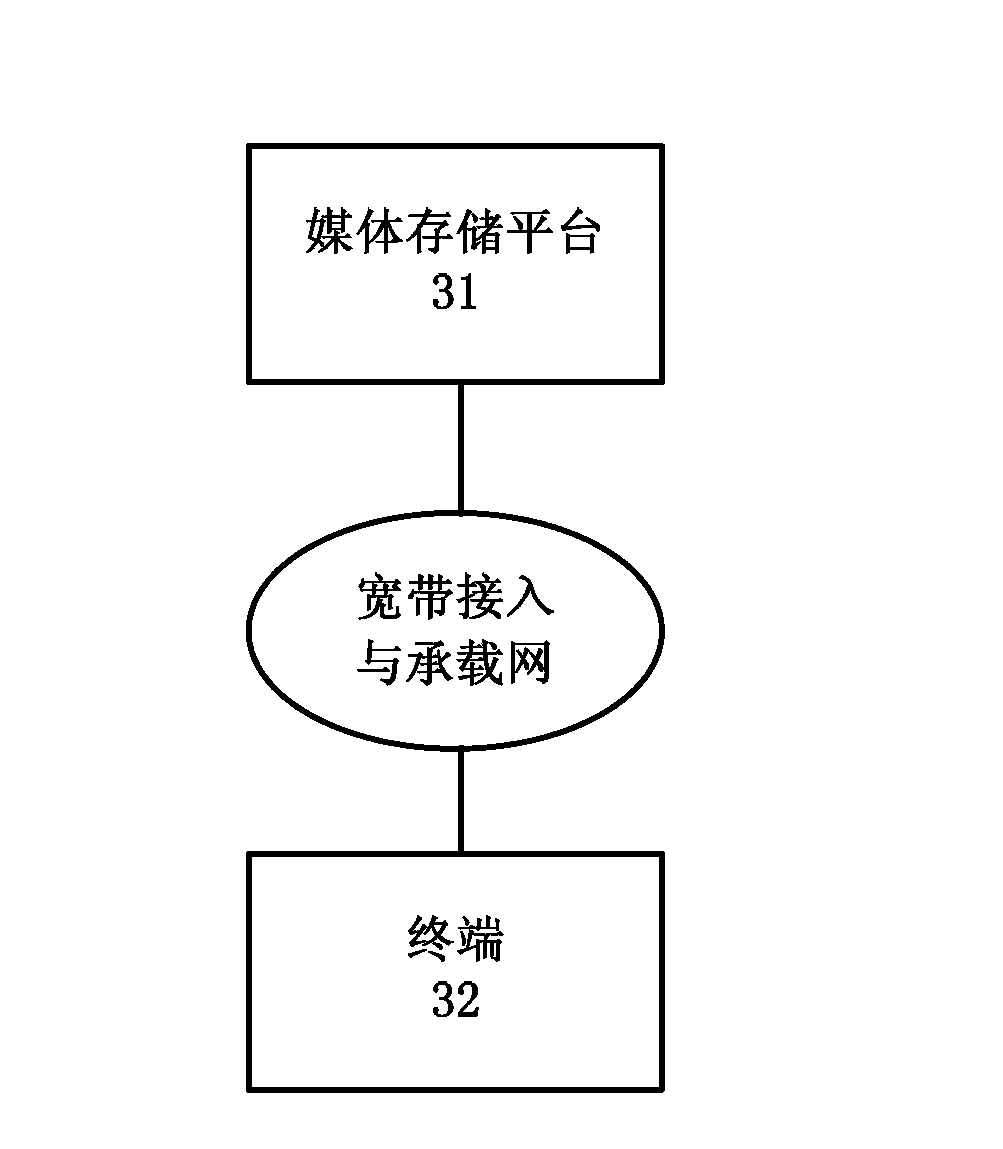
Media file playing method and system, player, terminal and media storage platform
The invention discloses a media filter playing method and system, a player, a terminal and a media storage platform, relating to the media playing technology. The method comprises that the media player obtains an index file of a media file from the media storage platform, and the index file is generated in advance and comprises key information which is required for playing the media file by the media player; the media player obtains the key information of the media file according to the index file; and the media player plays the media file according to the key information of the media file. According to the method, system, terminal and platform, when the media file at a far-end platform side is played at a terminal side, the terminal side scans the media file locally, obtains the key information required by the media player, and generates the index file; when media playing software at the terminal side plays the media file of the platform side, real-time scanning of the platform-side file is avoided, instead, the media file is played by obtaining information from the index file; and thus, playing of the media file can be rapidly started, and the latency is shortened.
Owner:CHINA TELECOM CORP LTD
Offline license anti-counterfeiting method based on reliable digital signature and two-dimensional code
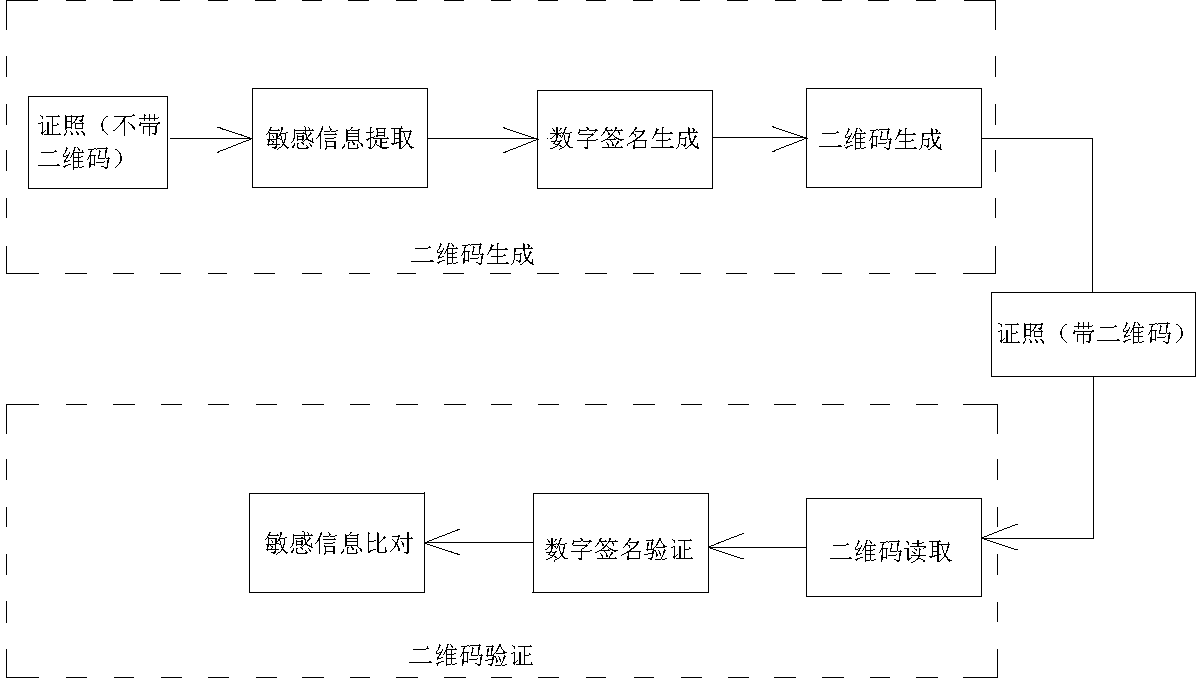
InactiveCN103810457AAvoid scanningPrevent copyingDigital data protectionRecord carriers used with machinesGraphicsDigital signature
The invention relates to an offline license anti-counterfeiting method based on a reliable digital signature and a two-dimensional code, aiming to effectively realize high offline anti-counterfeiting security. The method comprises the following steps: extracting sensitive information in a license, performing digital signature, coding the sensitive information of the license and the digital signature thereof to generate a two-dimensional code, binding the two-dimensional code with an issued license; acquiring the two-dimensional code from the license, extracting the sensitive information and the digital signature, verifying the validity of the signature, and comparing and checking whether the sensitive information in the license is consistent with information correlated with the digital signature or not; generating an anti-counterfeiting two-dimensional code of the license by using a license anti-counterfeiting two-dimensional code generating module; extracting the sensitive information in a license to be issued, and signing the sensitive information by using the private key of a license issuer; coding the sensitive information and the signature to generate a two-dimensional code pattern; printing the two-dimensional code pattern on the license to form an anti-countering two-dimensional code on the license. By adopting the offline license anti-counterfeiting method, the license is effectively prevented from being scanned and duplicated, and the trueness of the license can be verified off line. The method is convenient to use, and high in security.
Owner:HENAN RONGXIN DATA
Hydraulic power plant device polling method
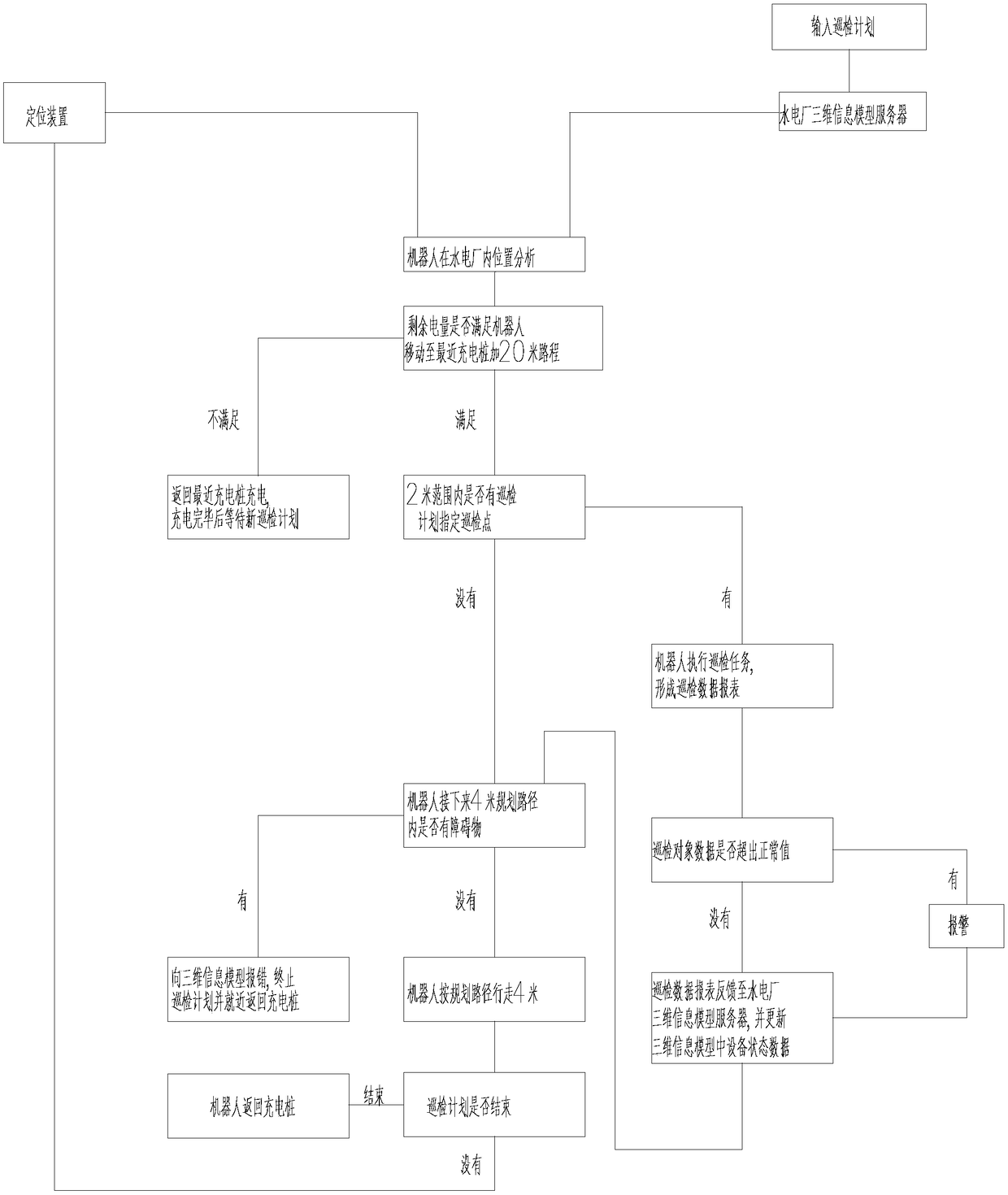
InactiveCN108960442AAvoid scanningAvoid lookingChecking time patrolsData processing applicationsProgram planningEngineering
A hydraulic power plant device polling method comprises the steps of: the step 1, making a polling plan on a three-dimensional information model server, and emitting a command to start a polling robot; the step 2, detecting the position of the polling robot; the step 3, detecting whether the dump energy of the polling robot meets a first condition or not, if no, allowing the polling robot to return a charging pile for charging, and returning to the step 1, and if yes, entering the next step; the step 4, detecting whether the polling robot has polling points or not in a first distance, if yes,executing a polling task, or else, entering the next step; the step 5, determining whether the polling robot has a barrier or not in a second distance, if yes, reporting errors to the three-dimensional information model server, terminating the polling plan and returning the polling robot to the charging pile nearby, or else, allowing the polling robot to travel for the second distance; and the step 6, determining whether the polling plan is finished or not, if yes, returning the polling robot to the charging pile, finishing the polling, or else, returning the step 2.
Owner:POWERCHINA HUADONG ENG COPORATION LTD
Body laser positioning system and method used for computed tomography (CT) system
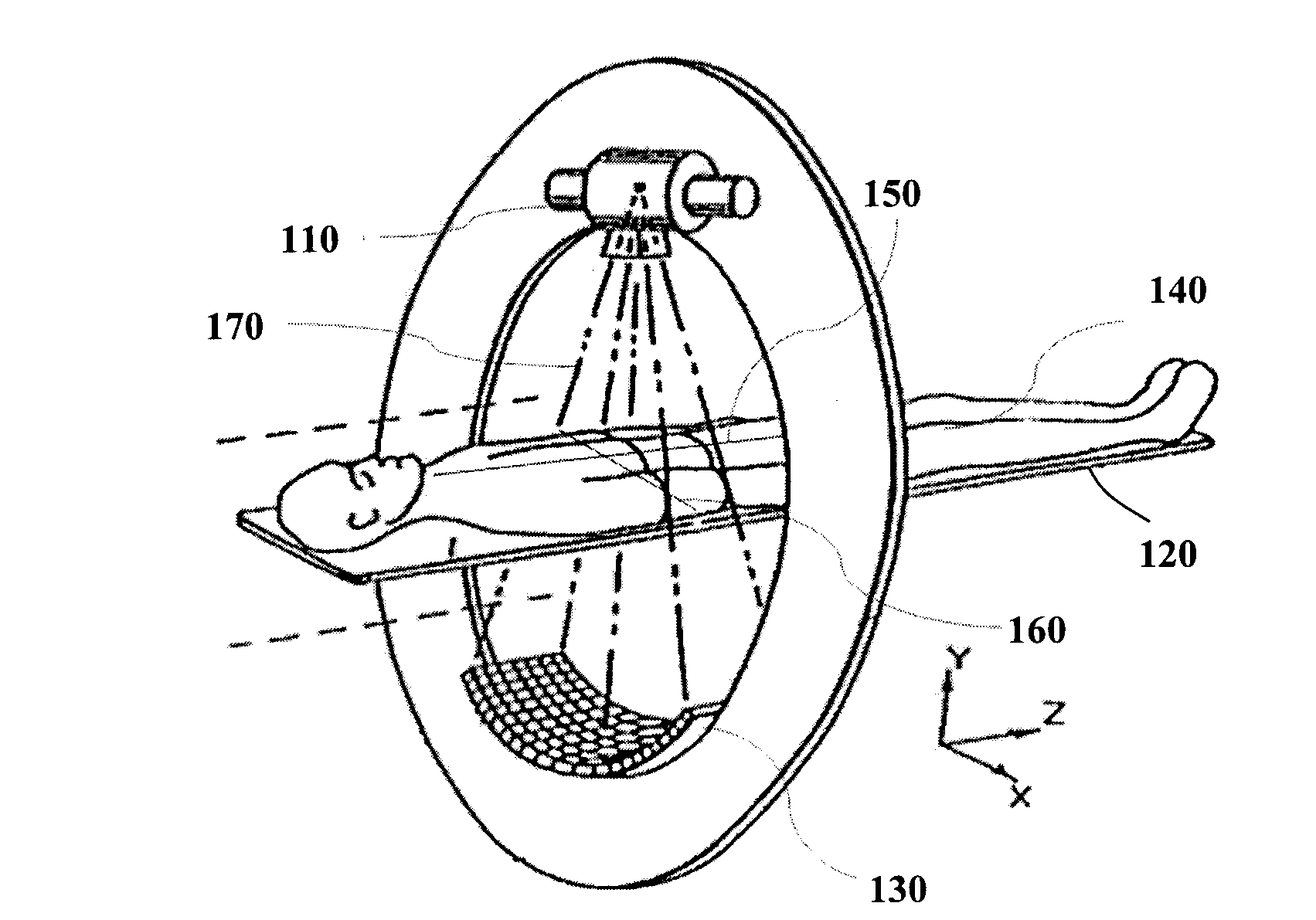
ActiveCN103126703AReduce workloadPrecise positioningPatient positioning for diagnosticsComputerised tomographsComputed tomographyField of view
The invention relates to a body laser positioning system and a method used for a computed tomography (CT) system. The body laser positioning system used for the CT system comprises a laser positioning device and a laser piece generation device, wherein the laser positioning device is used for emitting lasers to an object to be scanned and using the emitted lasers to carry out initialization positioning for CT scanning, the laser piece generation device is used for enabling the emitted lasers to be diffused to laser pieces in a CT scanning plane, and edges of the laser pieces along the direction of propagation are at least tangential to a circumference of scanning field of view (SFOV) of the CT system. The body laser positioning method used for the CT system comprises that the lasers are emitted to the object to be scanned, and the emitted lasers are utilized to carry out the initialization positioning for the CT scanning, the emitted lasers are diffused to the laser pieces in the CT scanning plane, and the edges of the laser pieces along the direction of propagation are at least tangential to the circumference of the SFOV of the CT system.
Owner:GE MEDICAL SYST GLOBAL TECH CO LLC
Device and method for deblocking optical workpieces, in particular spectacle lenses
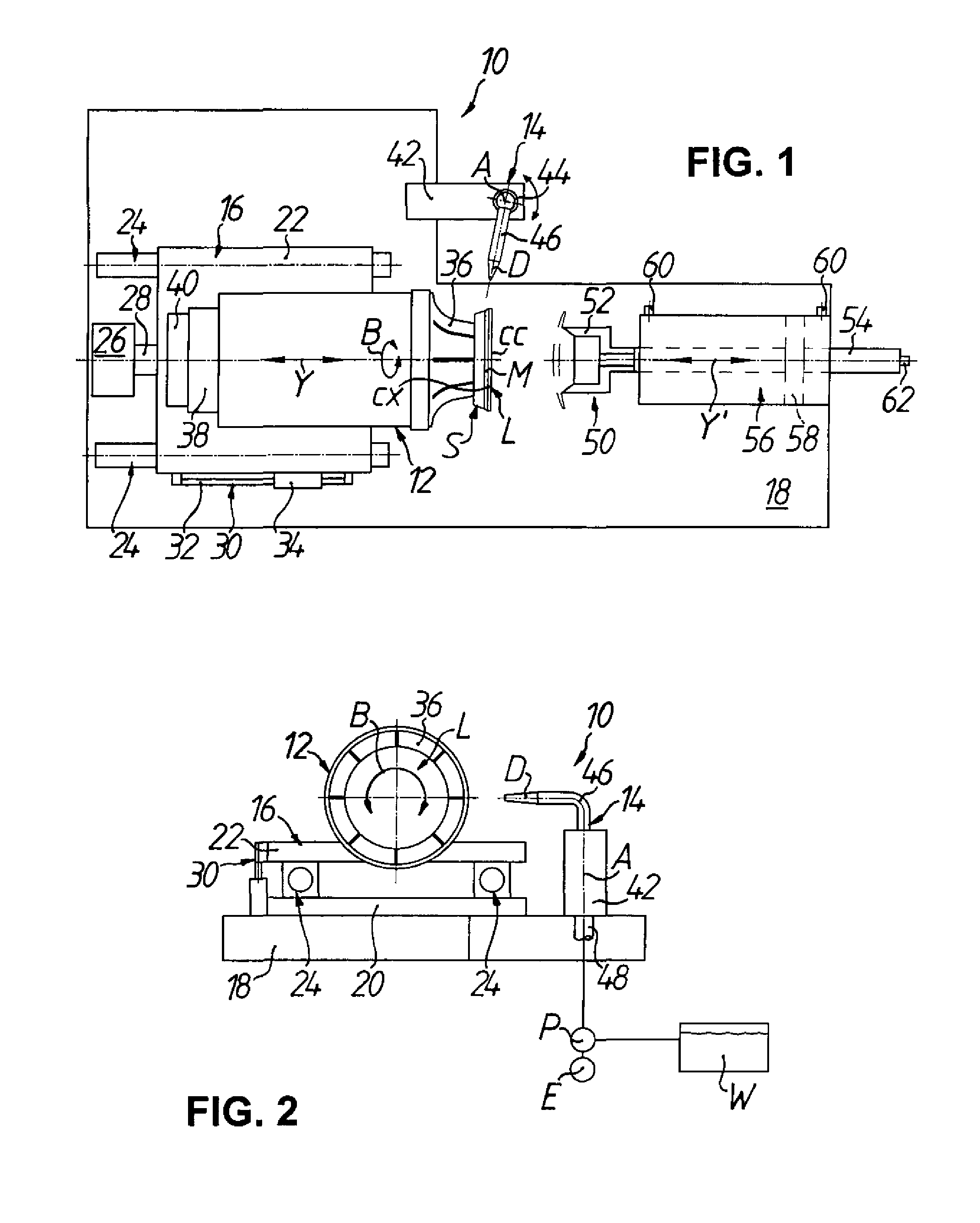
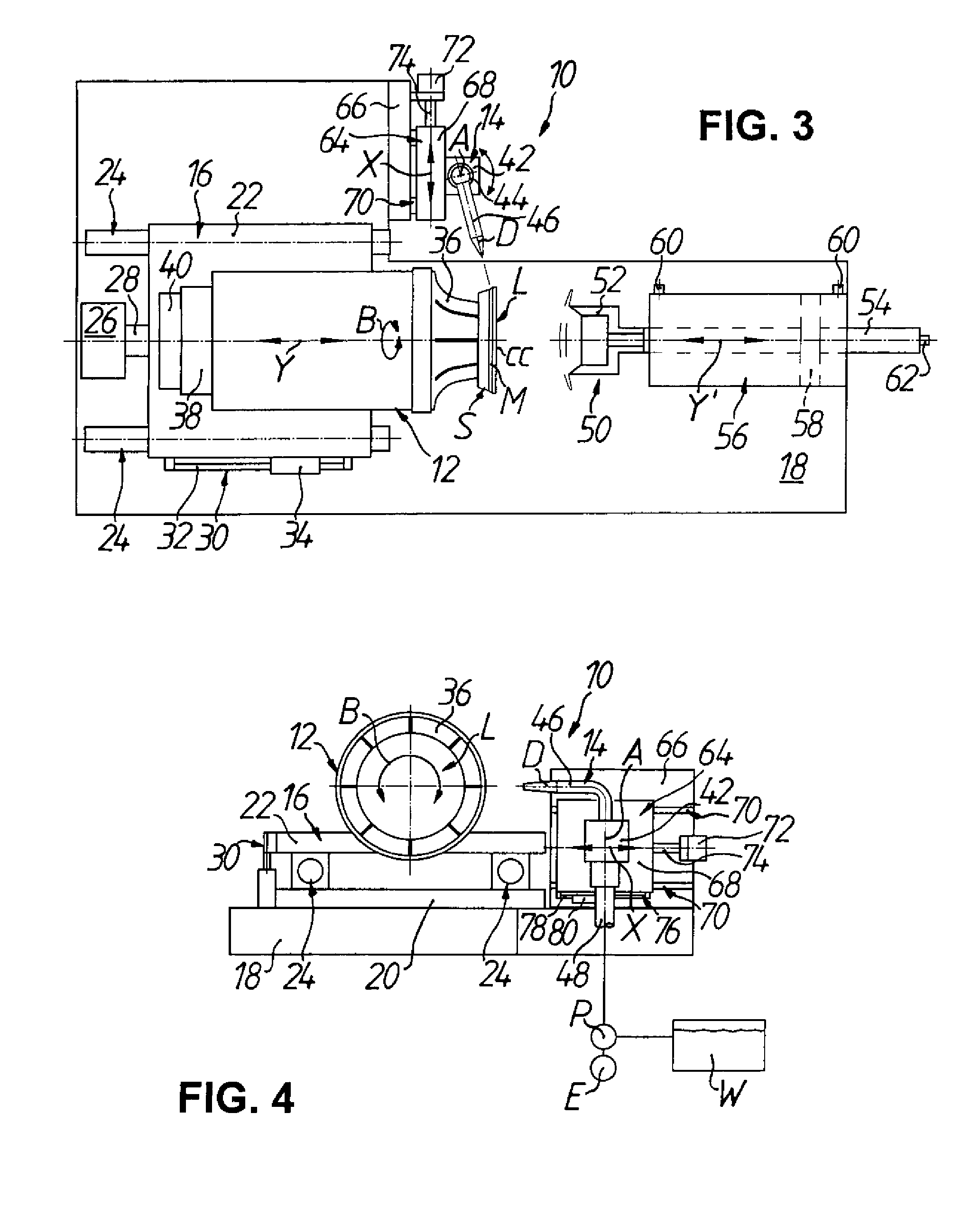
ActiveUS8931769B2Quickly deblockAvoid scanningOptical surface grinding machinesOptical articlesRotational axisEyeglass lenses
The invention relates to a deblocking device and an associated method for deblocking optical workpieces, for example, eyeglass lenses. The deblocking device has a first moving apparatus for rotating a workpiece blocked on a block piece about a workpiece rotational axis, a nozzle assembly having a nozzle for discharging a high-pressure pressure medium jet in a direction substantially perpendicular to the workpiece rotational axis onto an edge area between the workpiece and block piece, and a second moving apparatus for generating a relative motion between the workpiece and the nozzle along the workpiece rotational axis.
Owner:SATISLOH AG
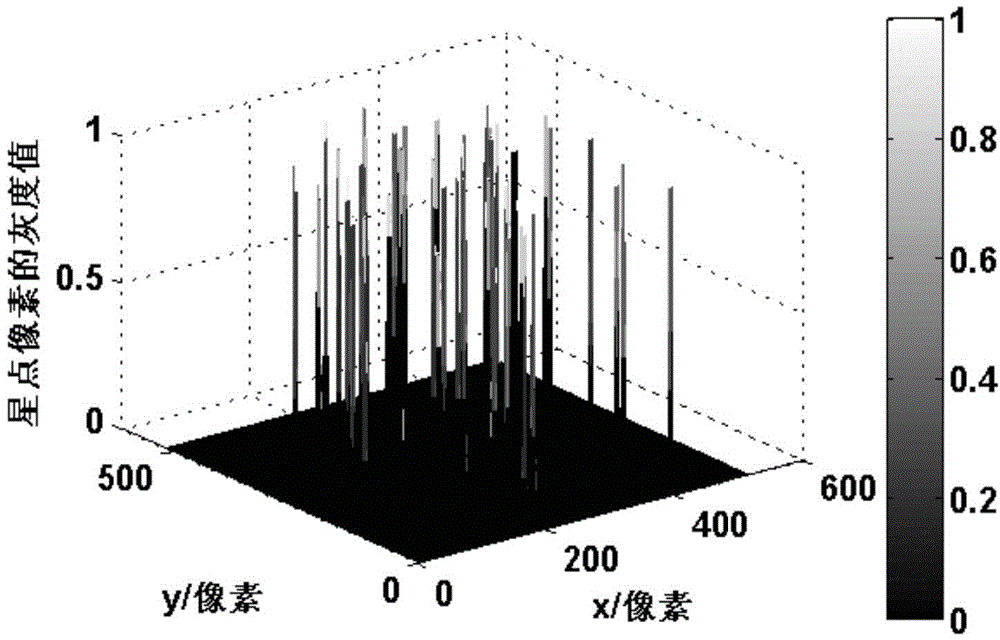
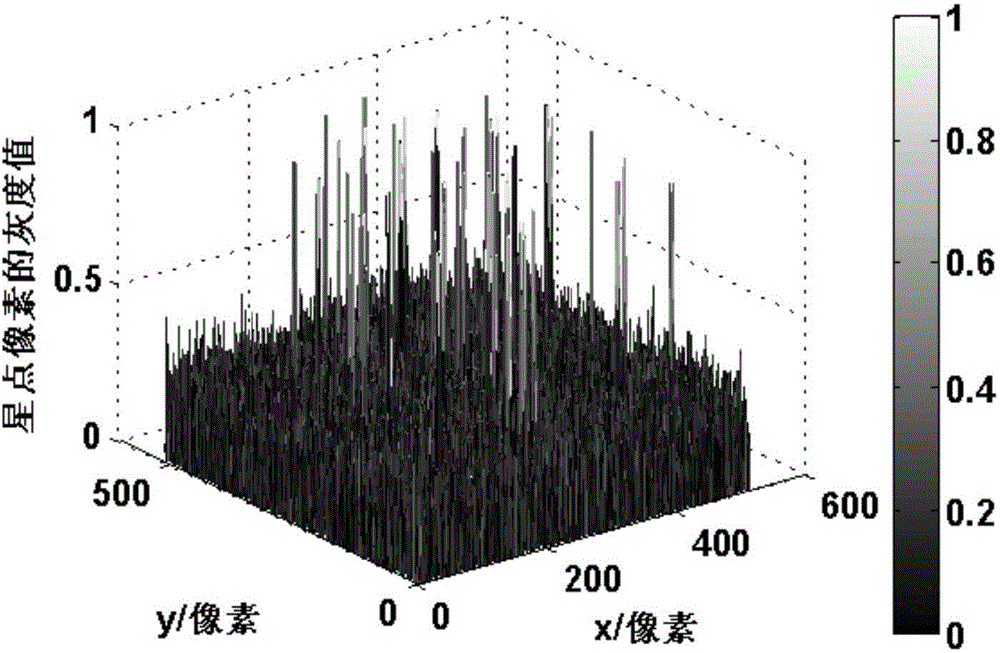
Method for quickly extracting star points from star images
The invention discloses a method for quickly extracting star points from star images. The method includes: according to a clustering concept, adopting part of star point pixels for coarse positioning of star points so as to realize rough estimation on center coordinates of star point dispersion regions; taking the center coordinates of the star point dispersion regions as seed points to automatically screen star point pixels according to a seed point area region growing method; according to characteristics of star point energy distribution, correcting gray values of the star point pixels; adopting a centroid calculation formula for precision positioning of the star points. Since star point extraction operations are centered in local ranges of the star point dispersion regions by means of coarse positioning of the star points, start point extraction speed can be increased; correction of the gray values of the start point pixels is simple and feasible, and image filtering effects can be achieved while more algorithm time and cost are saved as compared with those of image filtering.
Owner:XIDIAN UNIV
Method for determining an arrangement of measurement points on an anatomical structure
InactiveUS20100198564A1Shorten the timeExpenditure of timeMedical simulationImage enhancementAnatomical structuresMeasurement point
Owner:BRAINLAB
Automatic bias voltage control system and method for double-parallel Mach-Zehnder modulator
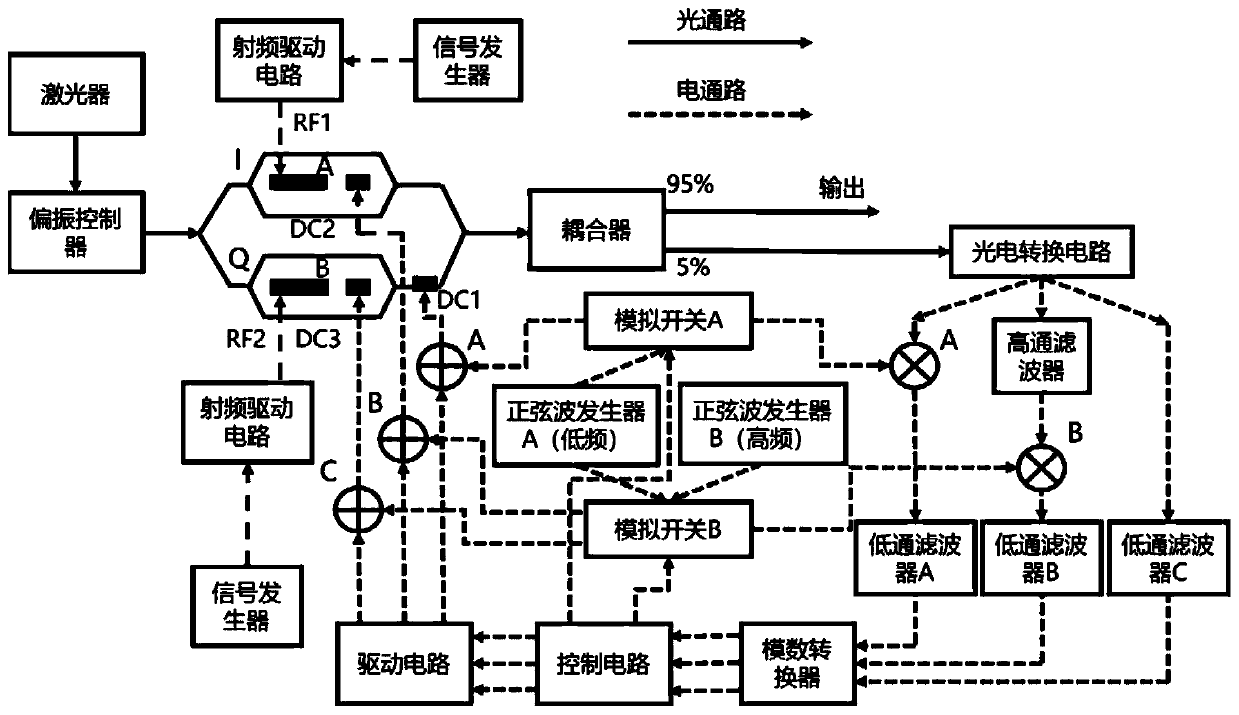
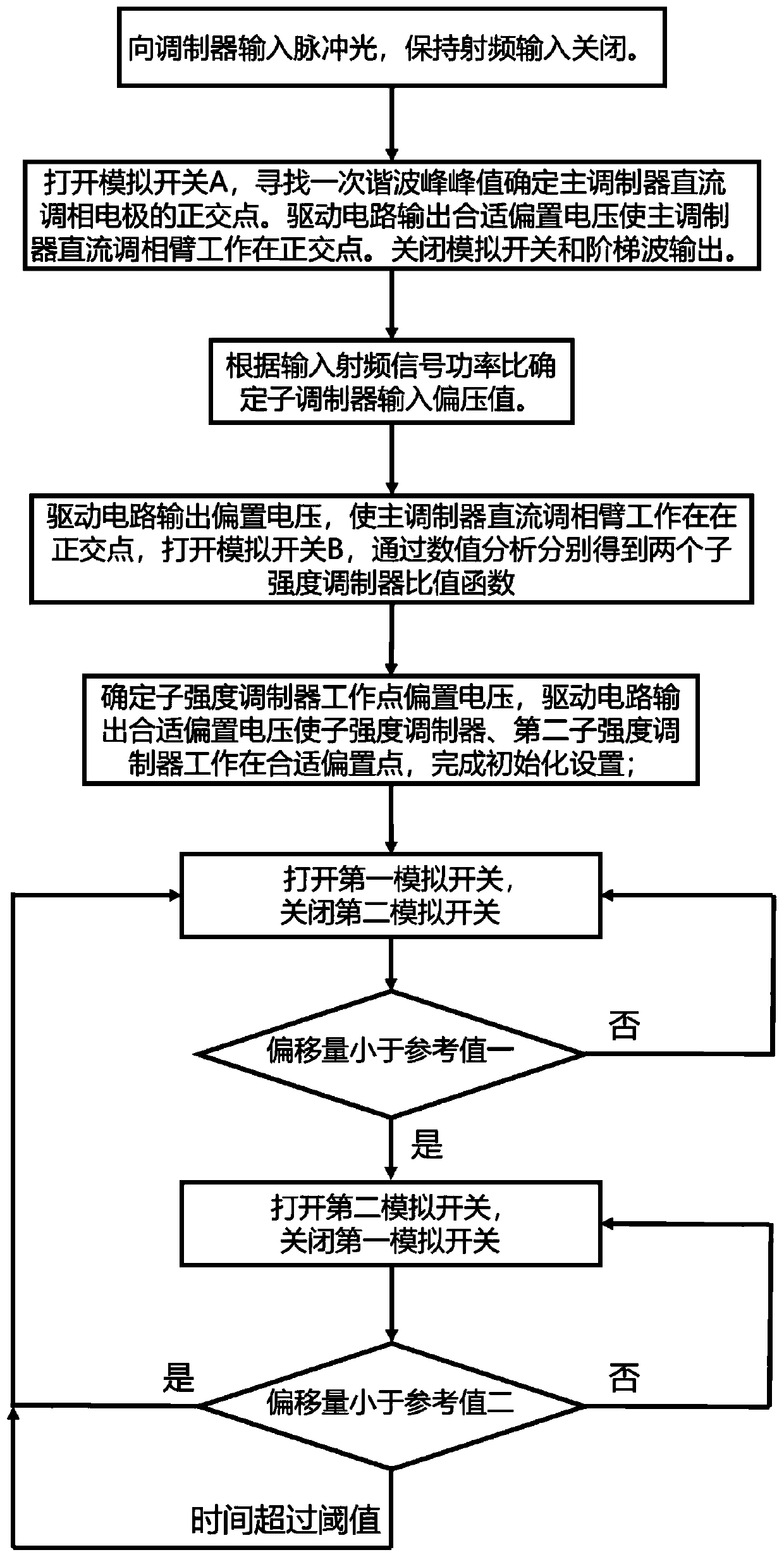
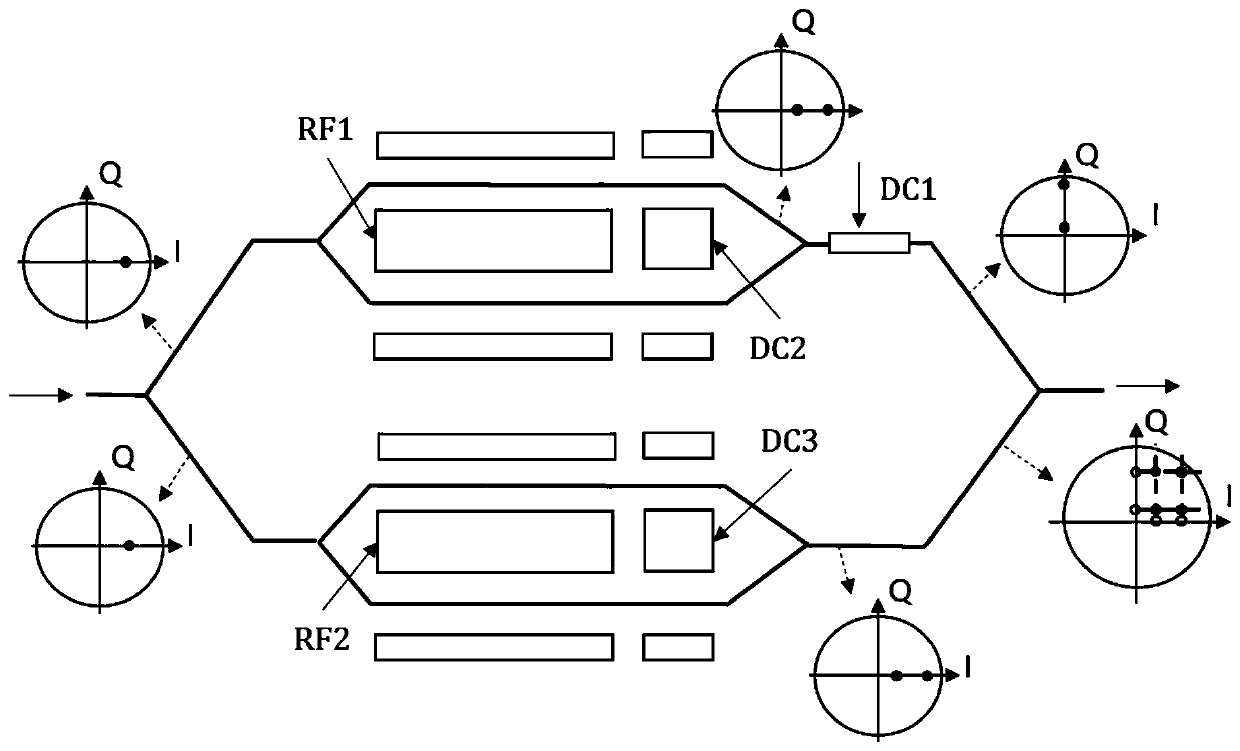
ActiveCN111130645AAvoid scanningSimplify complexityElectromagnetic transmittersAutomatic controlLoop control
The invention discloses an automatic bias voltage control system and method for a double-parallel Mach-Zehnder modulator. The system comprises a light emitting module, a radio frequency driving module, the double-parallel Mach-Zehnder modulator and an automatic bias voltage control device; the double-parallel Mach-Zehnder modulator is used for receiving an optical signal and an radio frequency signal with polarization, and a outputting a bias voltage control signal by the bias voltage automatic control device and modulating the same; the bias voltage automatic control device is used for receiving a modulated optical signal. In the system, perturbation of sine waves of different frequencies is utilized; simultaneous regulation, control and locking of the two paths of sub-intensity modulators are achieved. A main modulator direct current phase modulation electrode bias point is locked at an orthogonal point by searching a perturbation first harmonic extreme point, and a sub-intensity modulator bias point is locked at any bias point by analyzing a perturbation first harmonic and average optical power ratio function. And a preset bias point is quickly locked through numerical calculation of the bias voltage correction value, a specific signal value is extracted after locking and compared with a reference value, and the locking effect is verified. Automatic real-time closed-loop control of bias voltage is realized by switching bias voltage control of different direct-current phase modulation electrodes.
Owner:ZHEJIANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com