Method and system for quickly detecting malicious code
A malicious code and fast technology, applied in the field of malicious code detection, can solve the problems of limited disk IO read speed, long waiting process, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
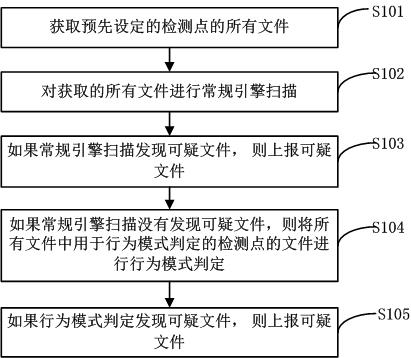
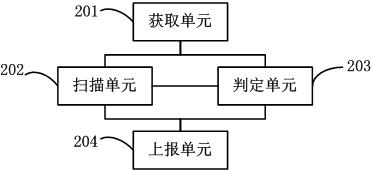
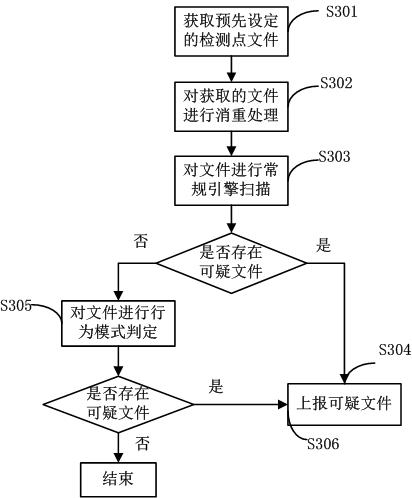
[0081] The present invention provides a method and system for quickly detecting malicious codes, which are mainly aimed at the windows system environment. According to the characteristic that malicious codes will enter the memory after they run, they directly go to the memory to scan all the started processes of the system and the corresponding entity files of the loaded modules. , specific non-PE existence directory, root directory and other sensitive items. Compared with the traditional engine, the invention can avoid scanning other normal files, thereby improving the detection speed. Simultaneously, the present invention judges whether malicious codes are divided into two channels, namely: regular engine scanning through feature code matching, and judgment through behavior patterns. Therefore, even if there is no feature code, the present invention can directly make a judgment on the attribute of the file, realize data acquisition and directional analysis on a special envir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com