Wireless attack detection and defense device and method thereof
An attack detection, wireless technology, applied in wireless communication, security devices, electrical components, etc., can solve the problem of inability to distinguish whether it is a counterfeiter, legitimate client accidental injury, providing information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
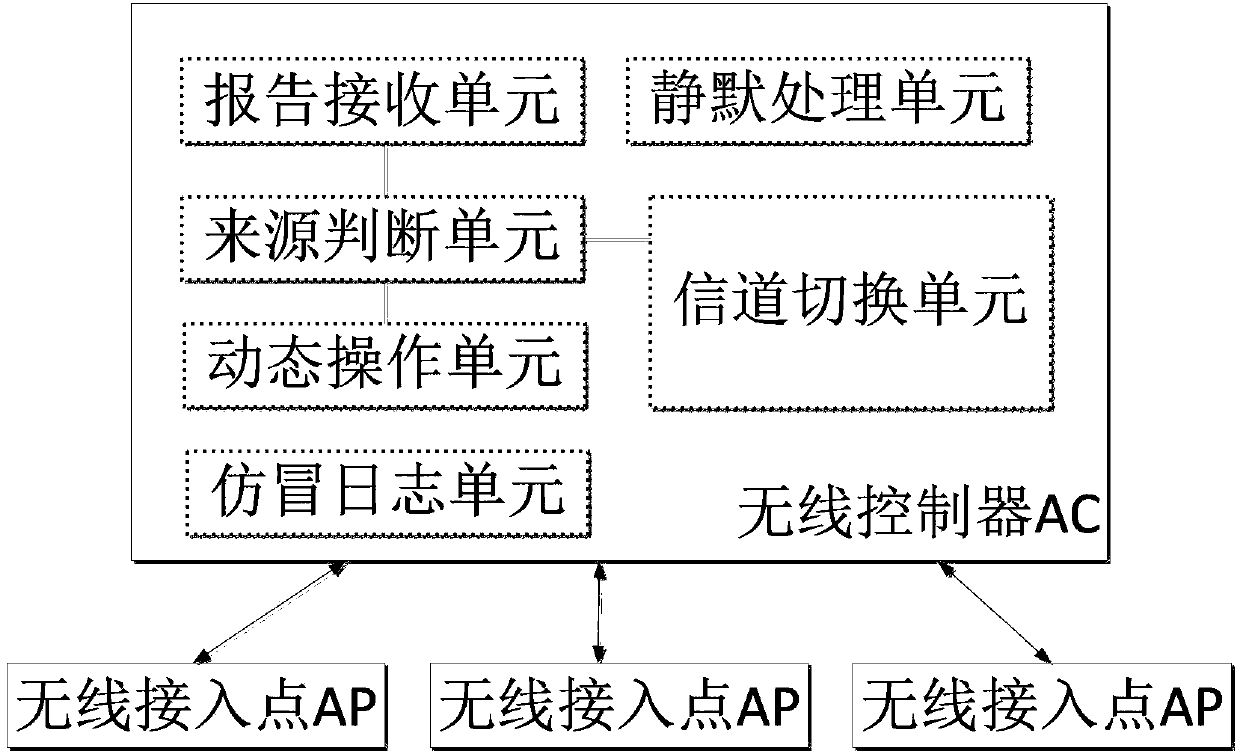
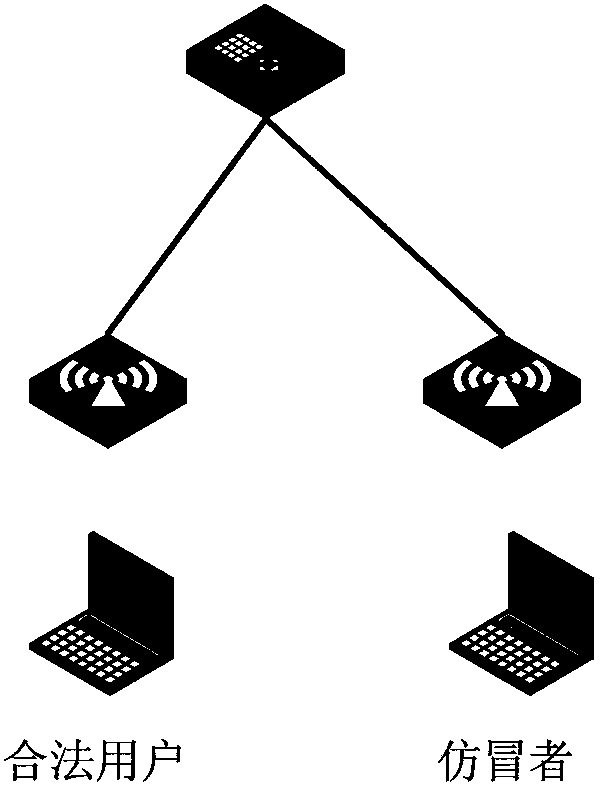
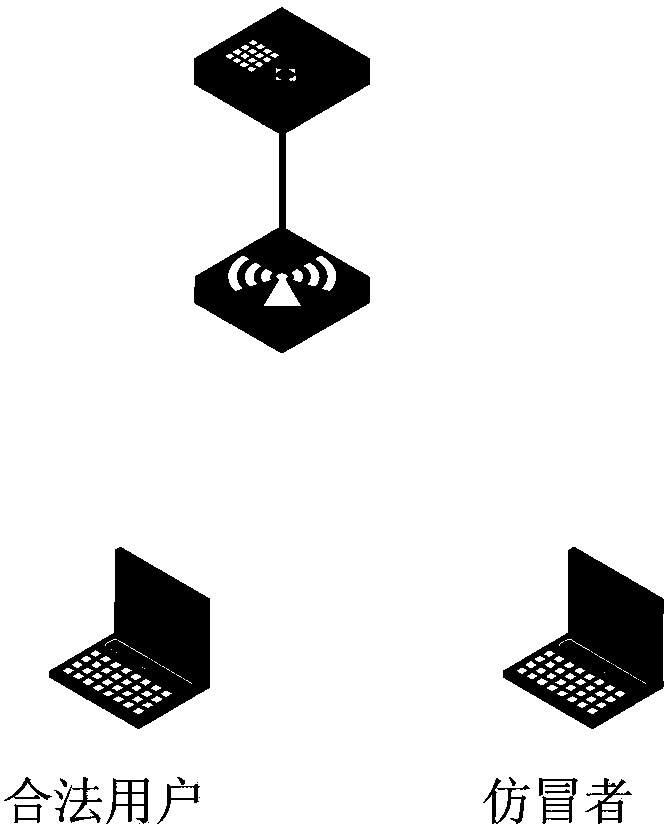
[0044] In order to realize the object of the present invention, the present invention judges whether the attacker is a legitimate client or a counterfeiter according to attack reports sent by different wireless access points AP, and takes corresponding defense measures. Specifically, the present invention is based on whether the wireless access point AP corresponding to the attacker's source MAC address is the wireless access point AP associated with the legal client, that is to say, whether the wireless access point AP that sends the attack report is the source of the attacker The wireless access point AP corresponding to the MAC address. Then determine whether the source MAC address used by the assailant is sent to the dynamic blacklist, and determine whether the assailant Counterfeiters. Therefore, the present invention prevents the legal client from being accidentally injured.
[0045] Specifically, see figure 1, the wireless attack detection and defense device of the p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com