Threat degree ordering method for server attack sources
A sorting method and threat degree technology, applied in the field of information security, can solve the problems of coarse granularity, users' inability to focus, and network administrators' inability to provide decision-making information, and achieve the effect of improving detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
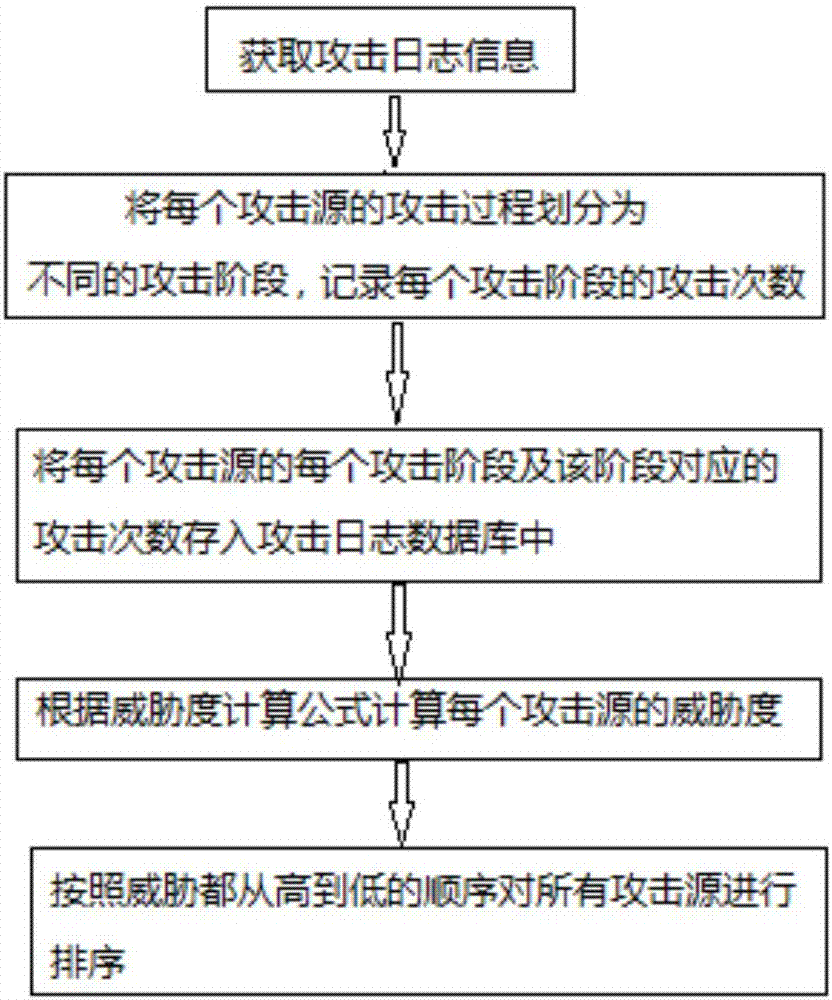
[0033] Step 1. Obtain the log information of the server, which includes the attack records of multiple attack sources on the server. The attack process analysis module classifies the attack process of each attack source on the server by classifying the log information. The classification rules are specifically: :
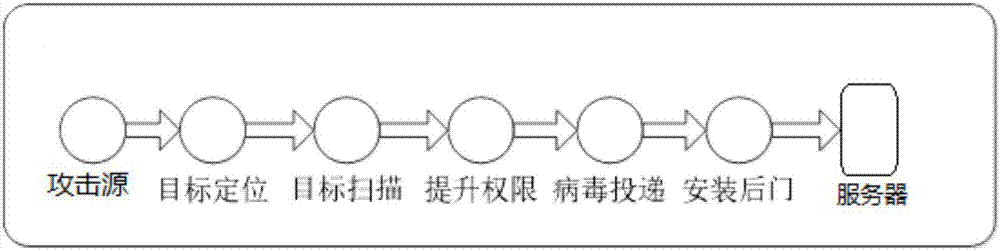
[0034] (1) Divide the log information containing positioning information into the target positioning stage;
[0035] (2) Divide the log information containing port scanning information into the target scanning stage;
[0036] (3) Divide the log information containing vulnerability information into the privilege escalation stage;
[0037] (4) dividing the log information containing virus information into the virus delivery stage;
[0038](5) Divide the log information containing backdoor information into the stage of installing the backdoor;
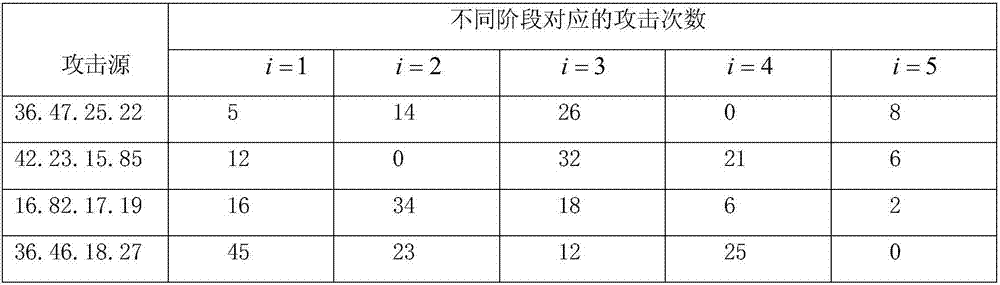
[0039] Simultaneously count the number of attacks of each attack source on each attack stage of the server, and store the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com