Block encryption device, block encryption method, block decryption device and block decryption method considering integrity verification
A block encryption and block technology, applied in encryption devices with shift registers/memory, secure communication devices, computer security devices, etc., to achieve the effect of satisfying confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 10 example
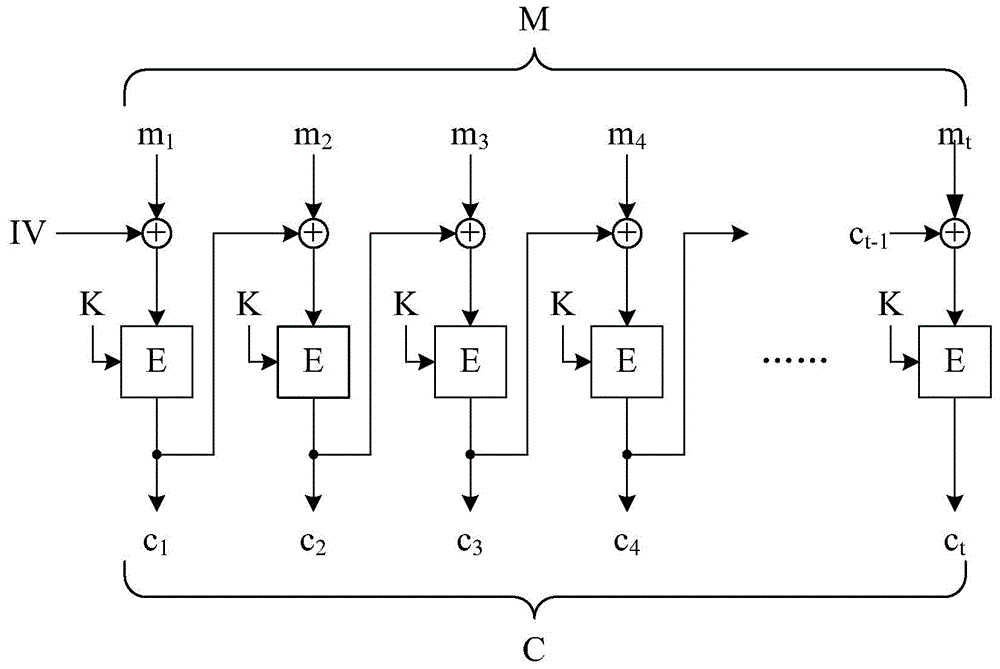
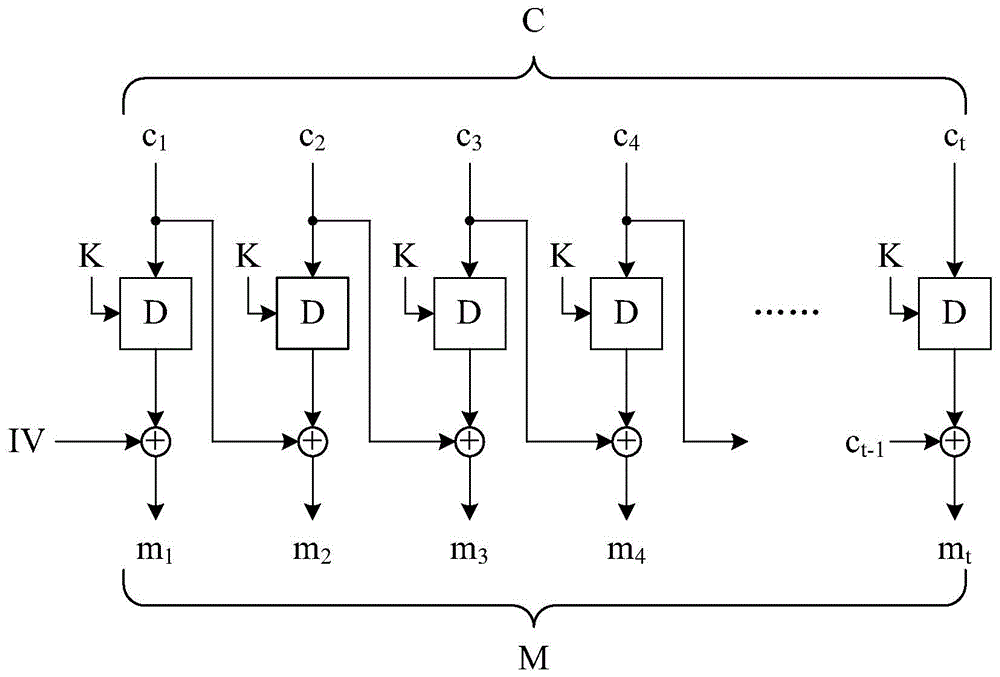
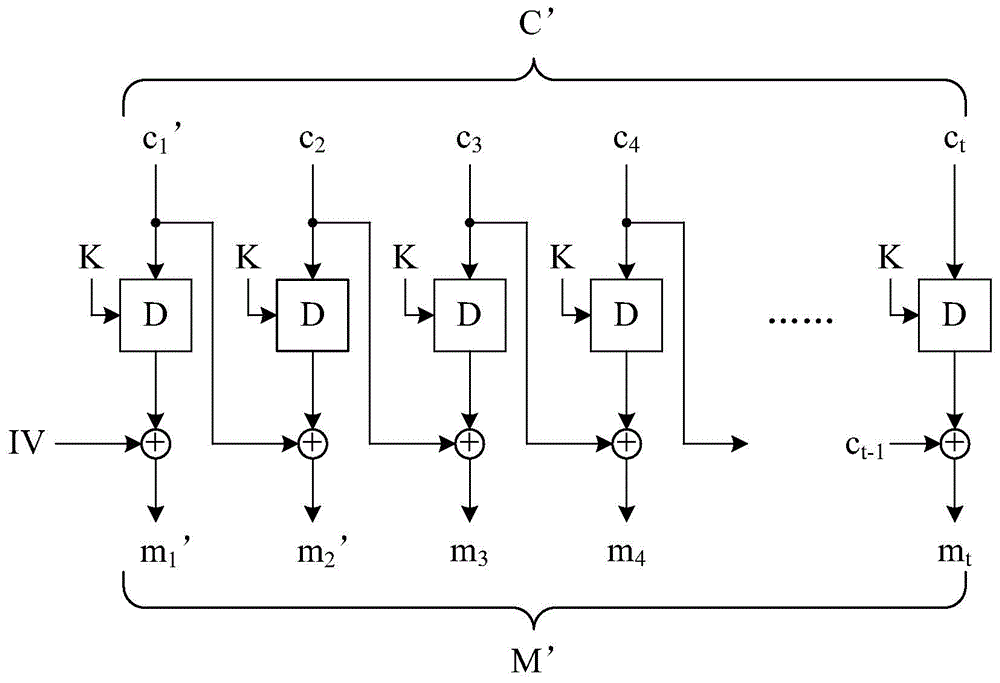
[0181] The tenth embodiment of the present invention is a computer-implemented block encryption method, the flow chart of which is depicted in Figure 8B . The operation principle of the tenth embodiment is the same as that of the ninth embodiment, but this embodiment uses a known encrypted block interlocker to complete certain steps. Only the differences between the tenth embodiment and the ninth embodiment will be described in detail below. For ease of understanding, please refer to Figure 3C .
[0182] Similarly, the block encryption method of this embodiment first executes steps S700, S701 and S703. Next, step S811 is executed to perform an XOR operation on each of the message blocks and the previous message block to obtain several temporary blocks. It should be explained that when the first one of the message blocks is processed in step S811, the preceding message block is an all-zero vector, and when the second one of the message blocks is processed in step S811, T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com