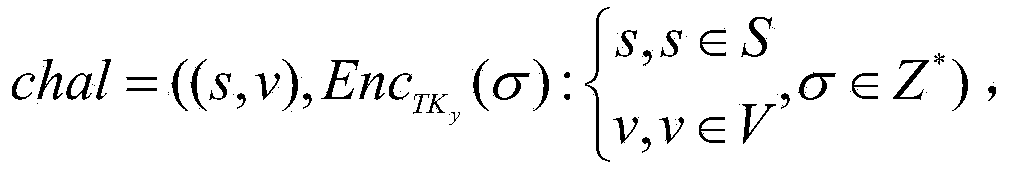Cloud computing data security boundary protection method
A technology of data security and border protection, applied in electrical components, user identity/authority verification, transmission systems, etc., can solve problems such as lack, lack of customization, and easy damage to data integrity, and achieve good universality , Satisfy data confidentiality, improve the effect of invulnerability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be further described in detail in conjunction with the accompanying drawings and specific embodiments.
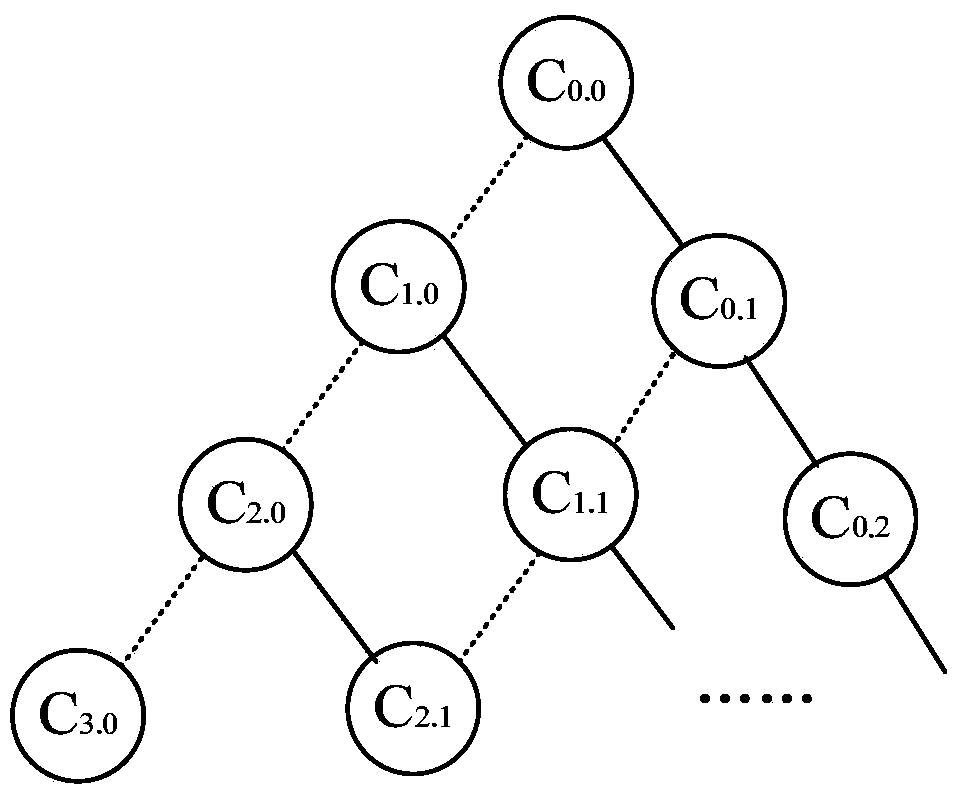
[0045] see figure 1As shown, a cloud computing data security boundary method described in the present invention takes the data interaction between the client computer and the cloud data center as the basic system model, and the client computer converts the data involved in the cloud service into unformatted data blocks The form is entrusted to the cloud data center for storage. By adopting the data block tree organization structure, it is convenient to use the metadata header information to verify the remote data block, which well ensures the security boundary of different data.
[0046] H(·):{0,1} * →{0,1} k Represents a one-way mapping function of any length to k bits in length.
[0047] Specifically include the following steps:
[0048] Step 1: The cloud server accepts the cloud service request instruction sent by the user, initiali...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com