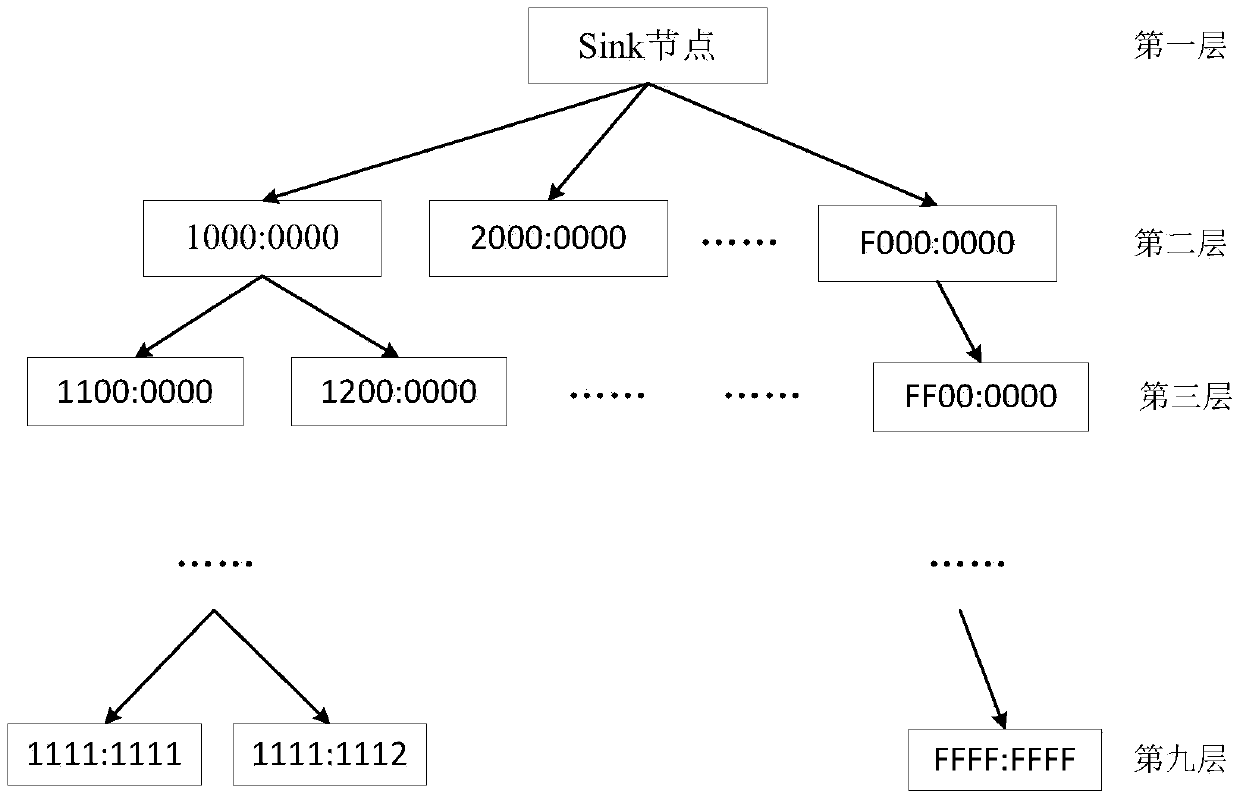
A secure routing method for wireless sensor networks based on IPv6 addressing
A wireless sensor and network security technology, which is applied in the intersection of information security and IPv6 technology, and can solve problems such as node denial of service
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
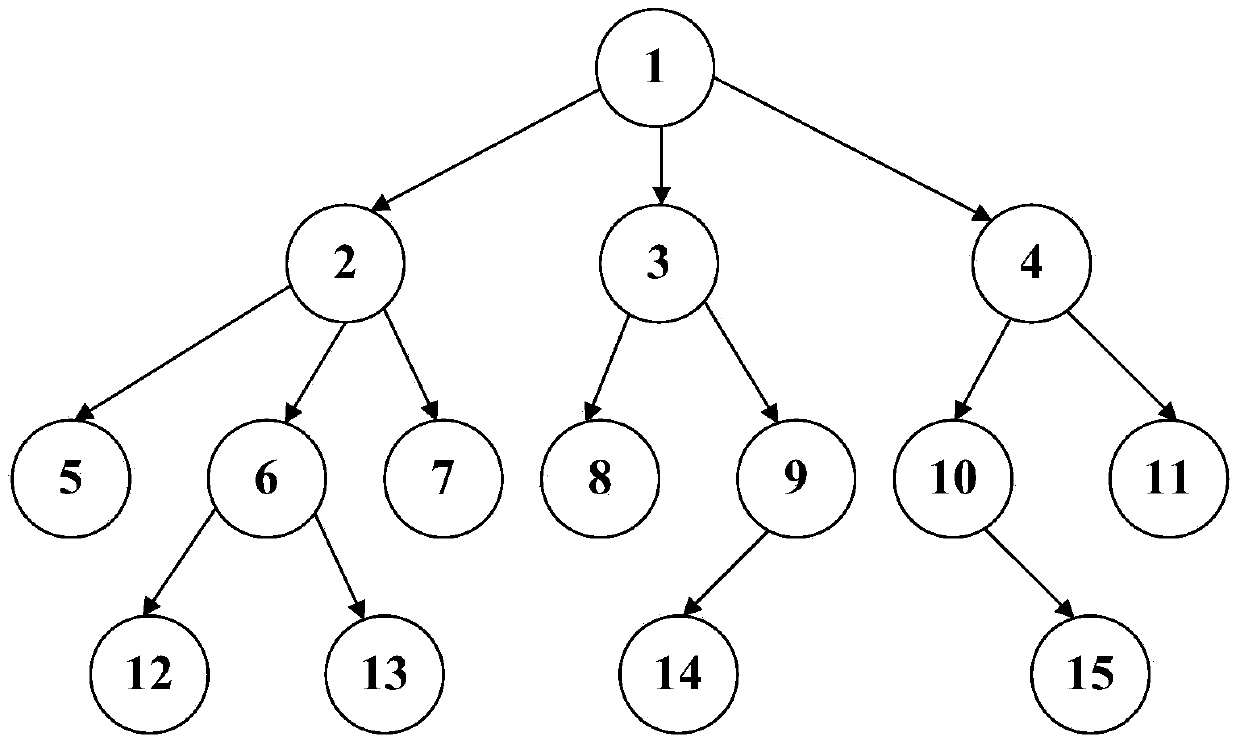
[0106] Assuming that the session is unicast, the topology is as follows figure 2 , node 7 sends a message to node 8, which belongs to the case of S41(4):
[0107] Step 1: First find the lowest ancestor node 1 of nodes 7 and 8, and execute Send(1,3) and Send(3,8), so that node 3 and node 8 are in direct parent-child relationship; then node 1 obviously belongs to FS( 7), according to step S41(3), first execute Send(7,2) and then execute Send(2,1), then 2 and 1 are also parent-child relationships, thereby establishing a route from node 7 to node 8 "7-2 -1-3-8".
[0108] Step 2: Execute the key management scheme when establishing a session. Node 7 and node 8 have a pair of session keys Key for secret communication and authentication of both parties' identities.
[0109] Step 3: Node 7 generates a random number r and records the current timestamp T. Node 7 calculates Cipher=E(Message||r,Key) and MAC=hash(Message||r||T).
[0110] Step 4: Node 7 sends Cipher||MAC||T to node 8 th...
Embodiment 2
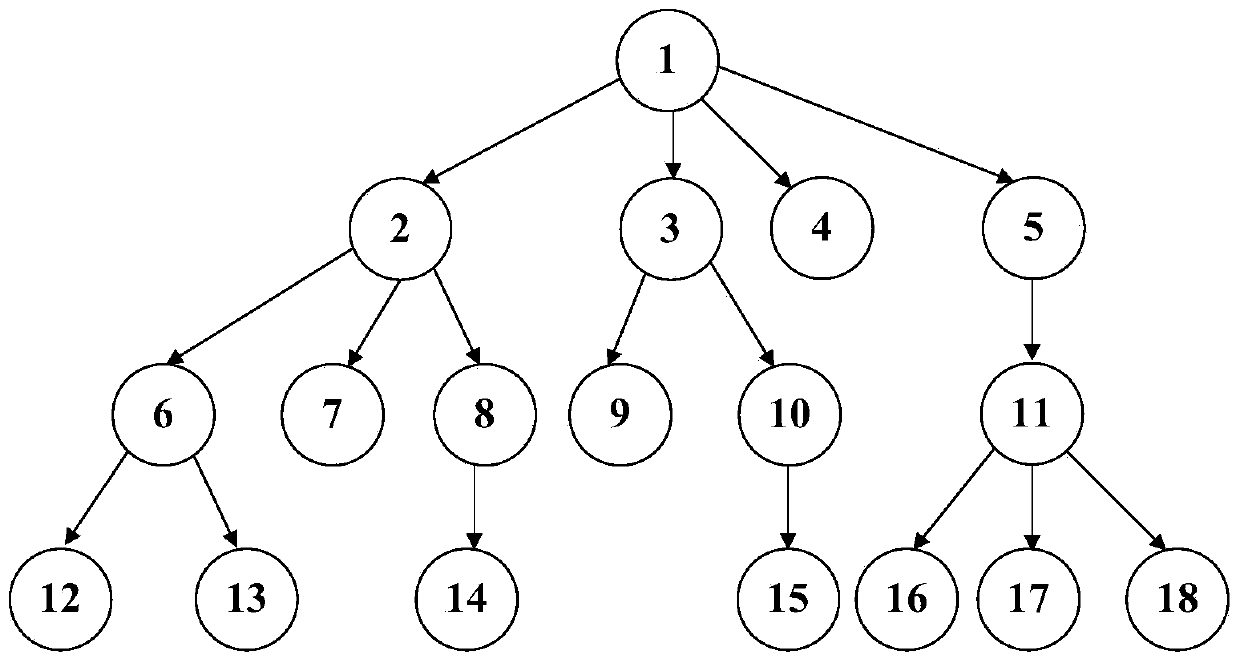
[0113] Assuming that the session is multicast, the topology is as follows image 3 , need to execute Send(2,{1,5,7,9,12,13,16}), the steps are as follows:
[0114] Step 1: Node 2 first establishes a route with the node set {1,5,7,9,12,13,16}.
[0115] Step 2: For the direct child node 7 of node 2, execute Send(2,7), and for the direct parent node 1 of node 2, execute Send(2,1).
[0116] Step 3: For the descendant nodes {12,13} of node 2, execute Send(2,6) node 2 to pass the information to node 6, and execute Send(6,12) and Send(6,13) respectively to find all parents and children Relationships 6 and 12 and 6 and 13, node 6 passes information to node 12, node 1.
[0117] Step 4: For node 5, node 2 has the lowest common ancestor 1, so it is easy to execute until the parent-child relationship of Send(1,5) is established, and obviously the parent-child relationship of Send(2,1) is established, so there is Route "2-1-5"; for node 9, node 2 has the lowest common ancestor 1, so it ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com