PKI certificate cross-domain authentication method based on blockchain
An authentication method and block chain technology, applied in the field of block chain-based PKI certificate cross-domain authentication, can solve problems such as difficult effective management, difficulty for third parties to obtain recognition from all institutions, and low risk, so as to improve real-time performance and security performance, good scalability, and improved update efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
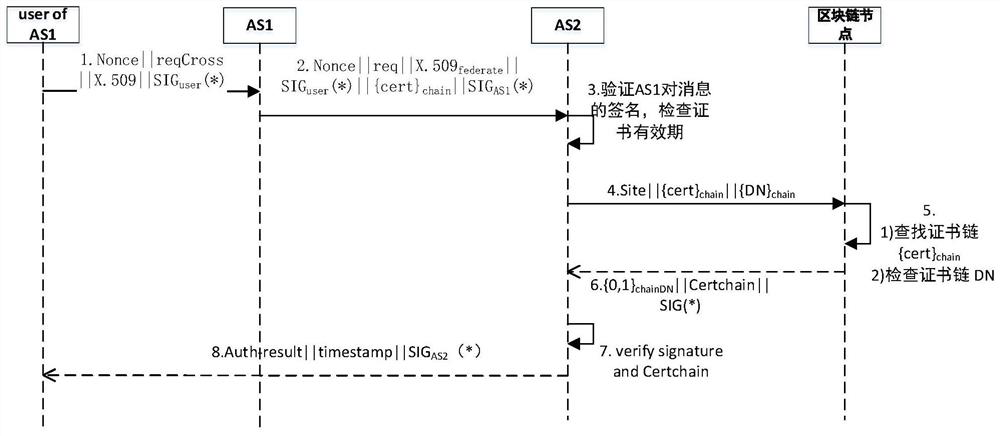
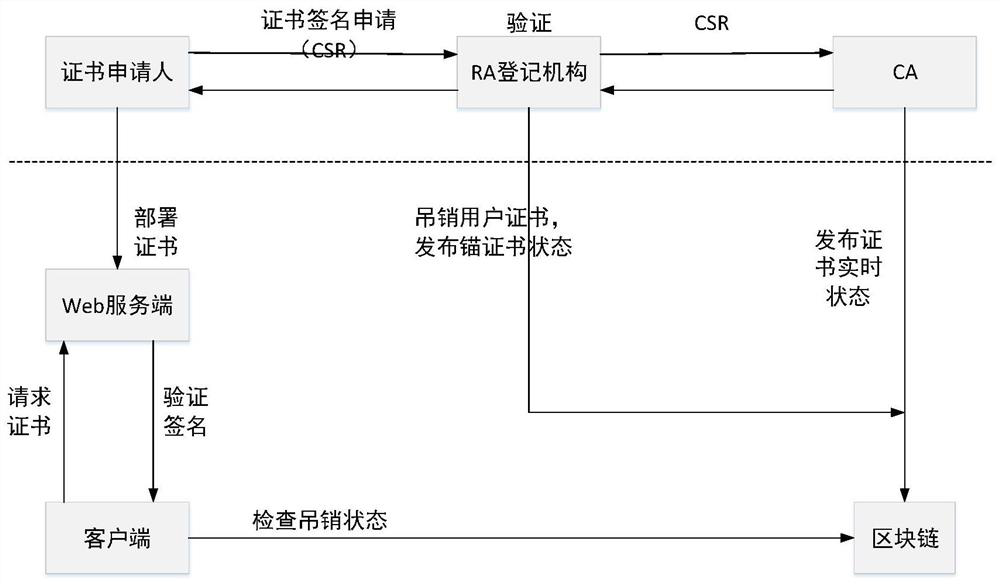
[0023] refer to figure 1 As shown, the present invention discloses a blockchain-based PKI certificate cross-domain authentication method. figure 2 It shows the whole lifecycle management of certificates based on blockchain. The whole life cycle of a certificate mainly includes: certificate application, verification and issuance, status update, revocation, etc. This embodiment uses the commonly used X.509 certificate as an example to illustrate, and the main items of the X.509 certificate are shown in Attached Table 1.
[0024] Attached Table 1 Main Contents of X.509 Certificate
[0025]
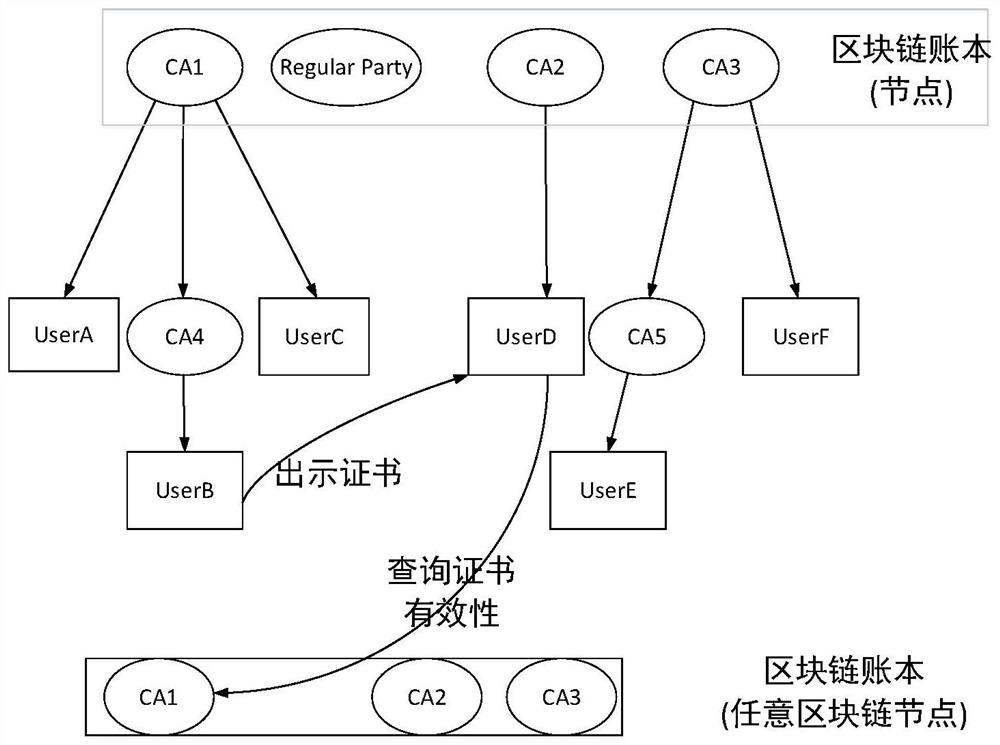
[0026] The method of the present invention transfers the cross-domain trust transfer part in the traditional PKI to the block chain, and provides the upper-level CA certificate chain download and user certificate revocation number information through the block chain, abandons the problem of too large CRL list, and improves the real-time performance of certificate update. With the help o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com