Embedded variable-granularity control flow verification method and system based on probability prediction
A probabilistic prediction and granularity control technology, applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve problems such as low operating cost, large cost, and insufficient security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
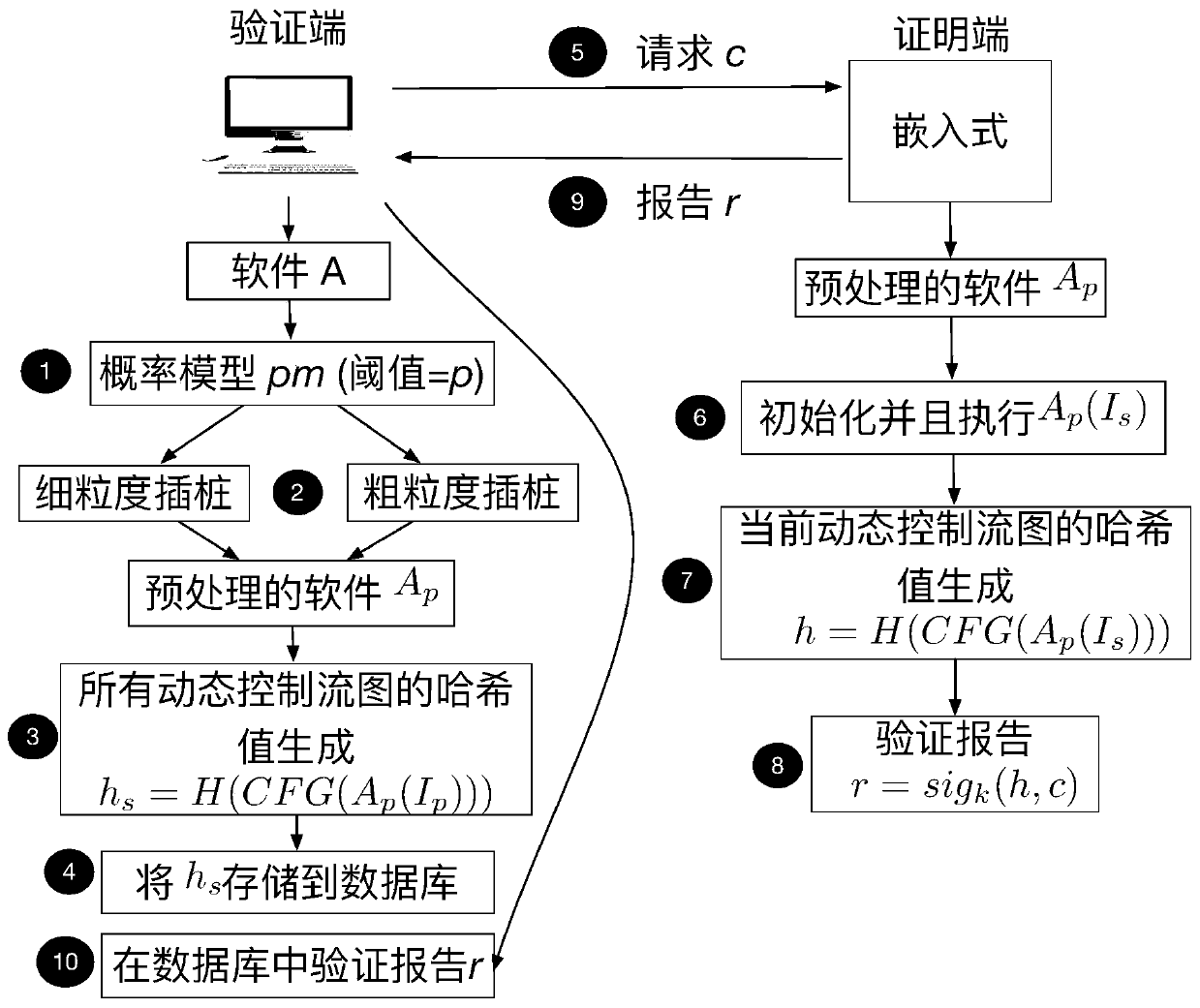
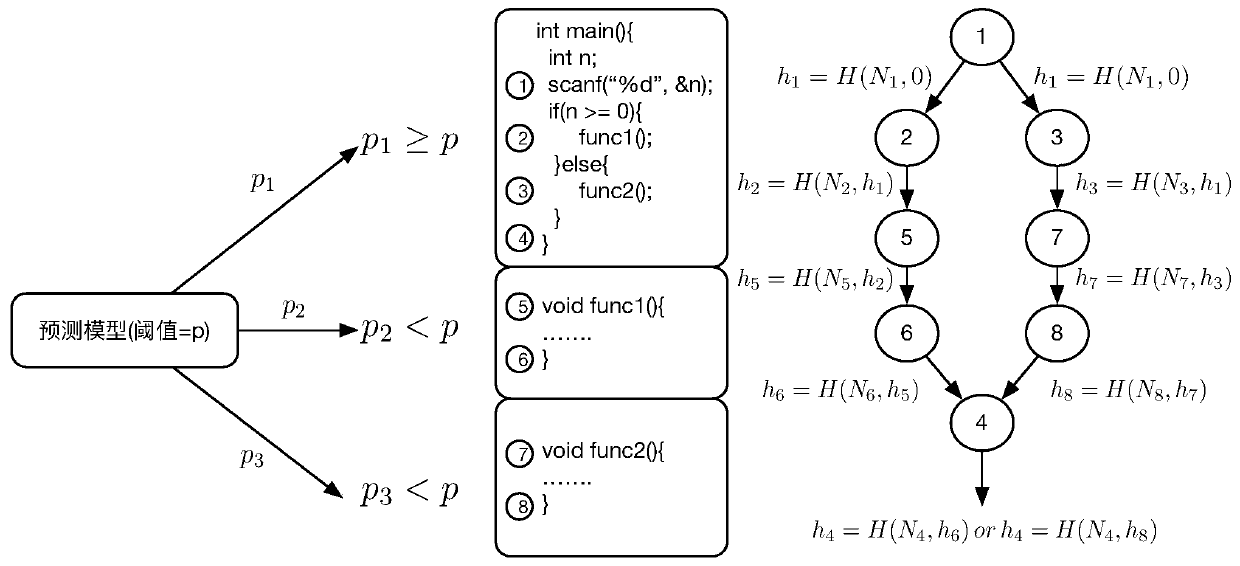
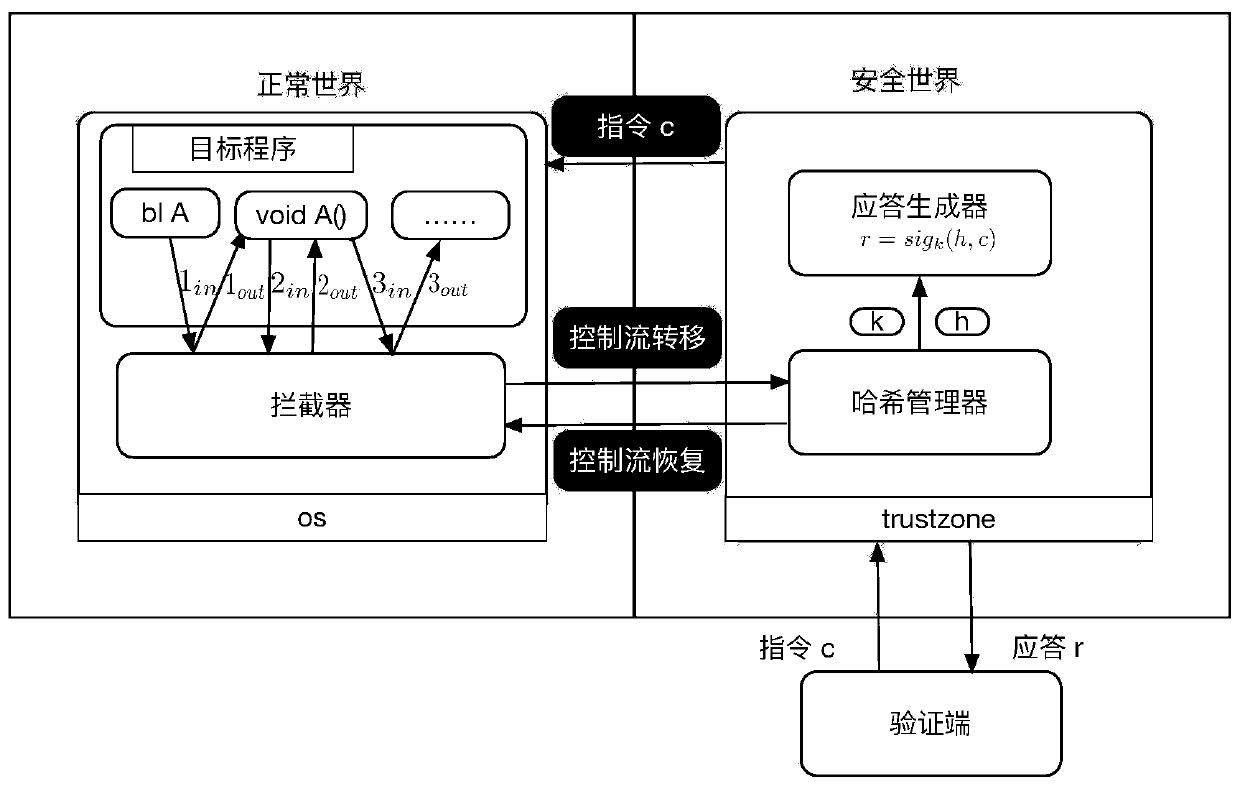
[0036] The present invention is an embedded variable granularity control flow verification scheme based on probabilistic prediction. The scheme verifies the integrity of software on an embedded platform by combining two verification schemes of coarse and fine granularity. There is a relative balance between safeguards. The invention utilizes the remote attestation framework to effectively prove the integrity of the embedded device, and credibly calculates the hash value of the control flow graph based on the TrustZone hardware isolation technology. The invention has the characteristics of high security, low running overhead, variable granularity of control flow and the like.
[0037] In order to make the purpose, advantages and technical solutions of the present invention clearer, the present invention will be further described in detail below through specific implementation and in conjunction with the accompanying drawings.
[0038] figure 1 Describes the overall architectu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com