A detection method for rop attack
A detection method and dynamic link library technology, applied in the field of detection against ROP attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
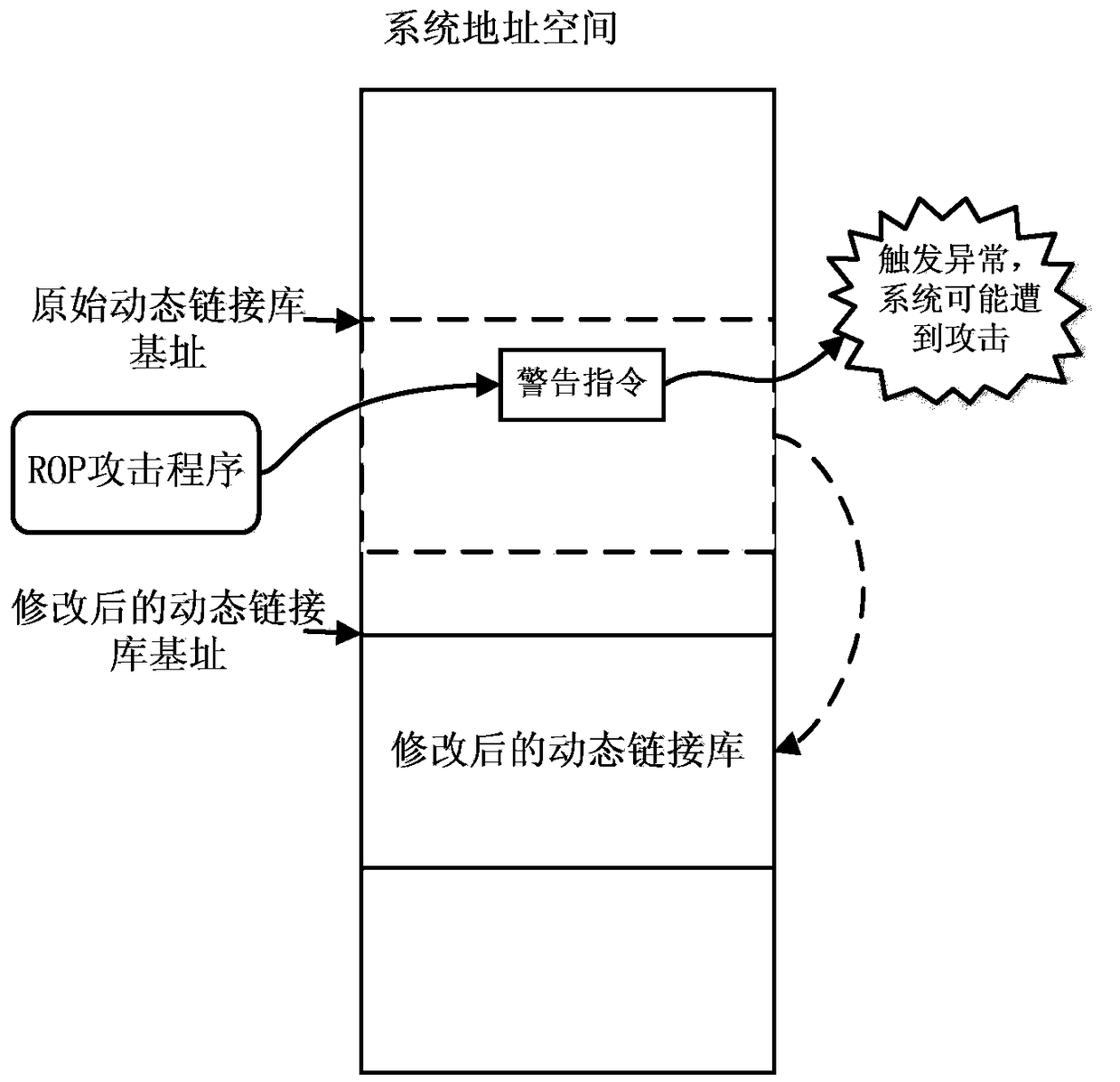
[0038] PE files refer to program files of the Microsoft Windows operating system, and dynamic link libraries are typical PE files. At present, the modification technology of PE files is very mature, but there is no mature technology to detect ROP attacks only by modifying the dynamic link library. Using this idea to detect ROP attacks does not need to modify the kernel program of the system, and it is compatible with all Windows systems.
[0039] This embodiment provides a detection method for ROP attacks, including a preprocessing stage and a loading stage:
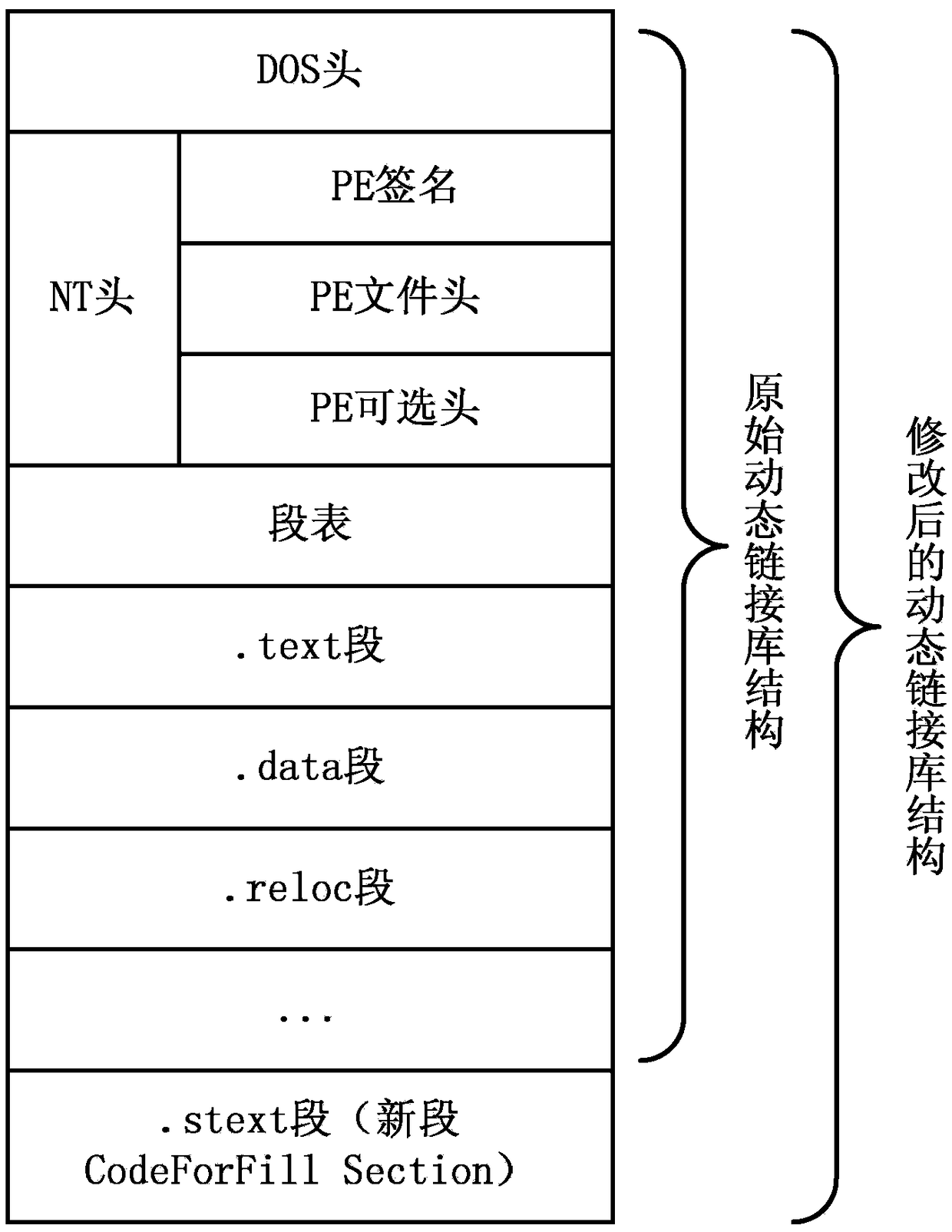
[0040] In the preprocessing stage, the solution we adopt is to add a new code segment in the original dynamic link library as a new segment, and then add code to the new segment to realize the function of filling warning instructions in the loading position of the original dynamic link library.
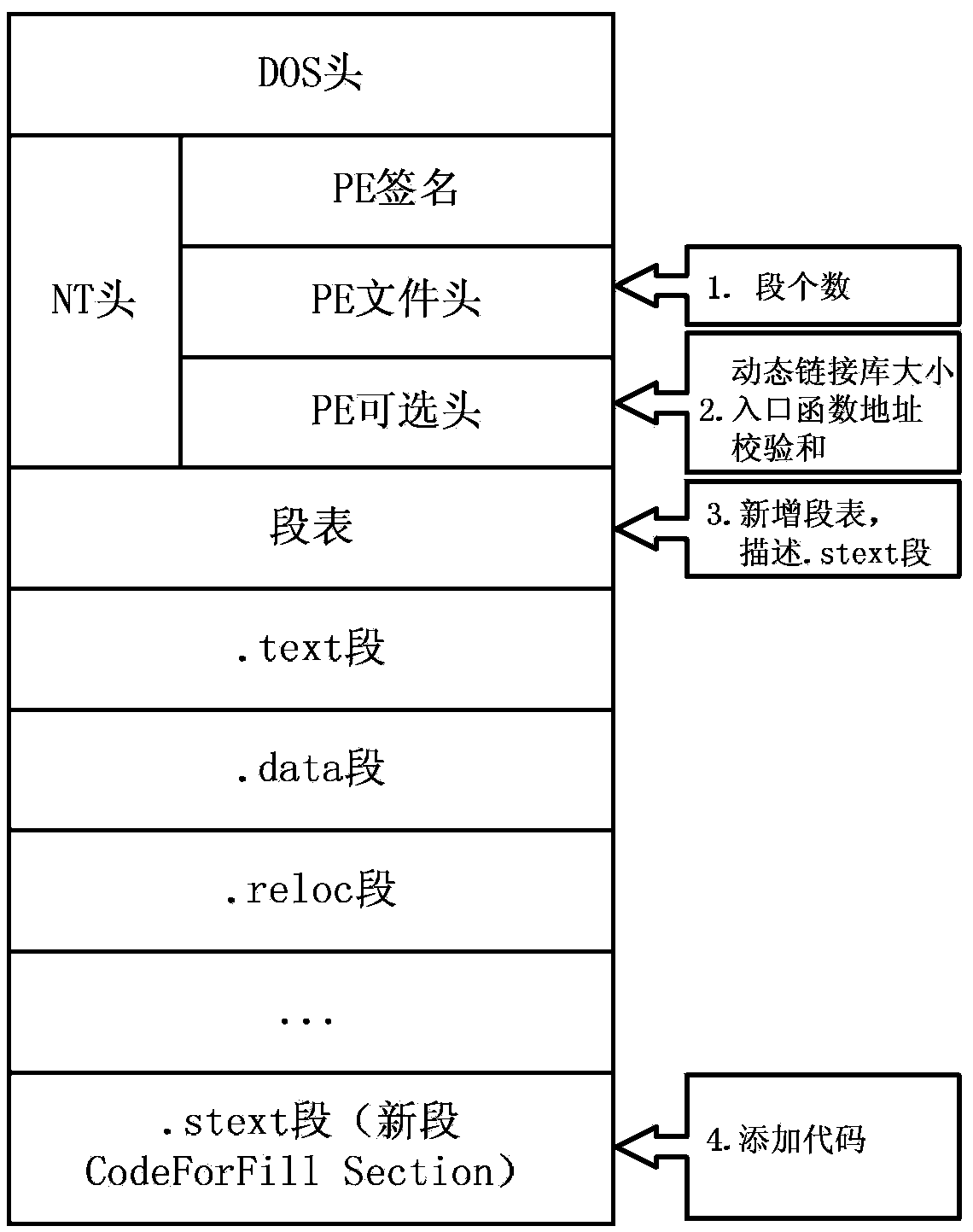
[0041] image 3 is in figure 2 The part to be modified is marked in detail on the basis of the above. In the NT header, fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com