A method and system for mining cross-site scripting vulnerabilities in a cloud computing environment
A cross-site scripting vulnerability, cloud computing environment technology, applied in transmission systems, software deployment, electrical components, etc., can solve non-persistent XSS attacks, browser and application source code solutions are not feasible, browsers do not meet user requirements Self-interest and other issues, to achieve the effect of low false negative rate and false positive rate, easy deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] In order to facilitate those of ordinary skill in the art to understand and implement the present invention, the present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the implementation examples described here are only for illustration and explanation of the present invention, and are not intended to limit this invention.
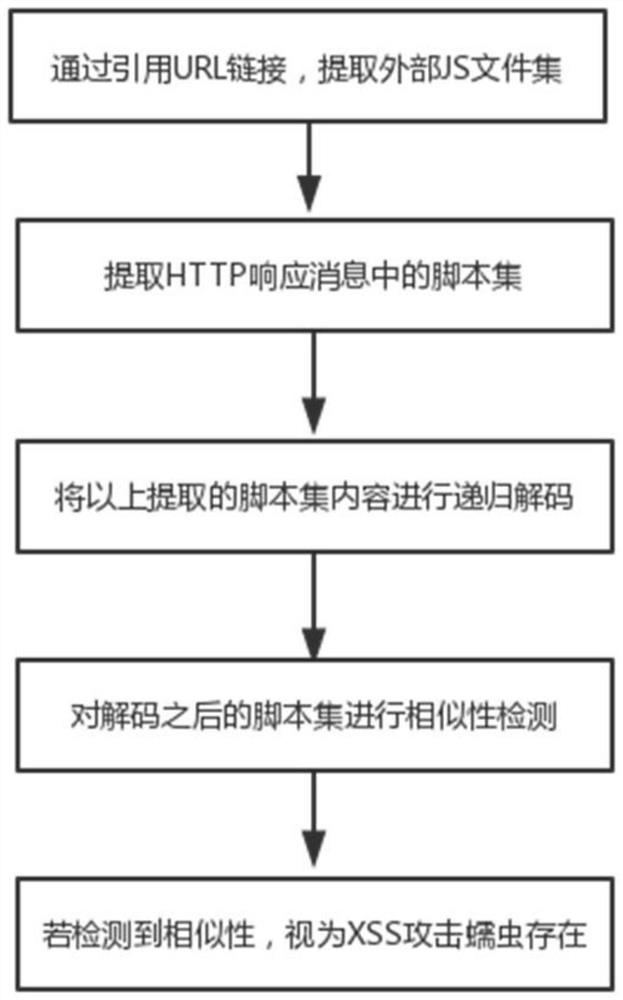
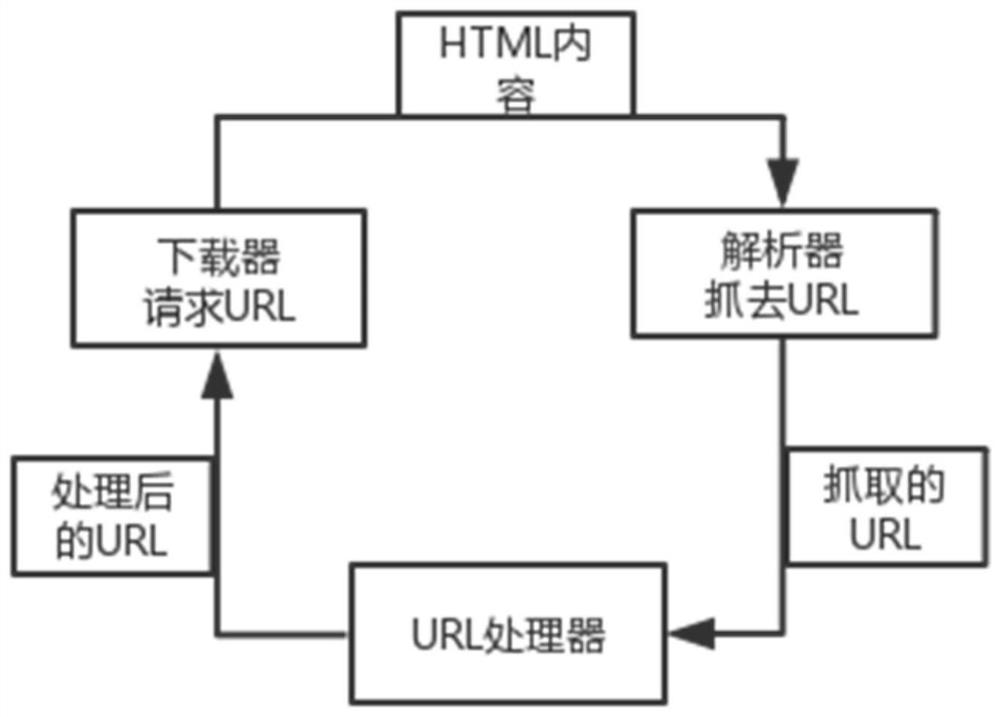
[0031] please see figure 1 A method for mining cross-site scripting vulnerabilities provided by the present invention for a cloud computing environment comprises the following steps:
[0032] Step 1: Grab the Web page of the HTTP protocol;
[0033] In this embodiment, by traversing the Web sites in the URL links, and these Web sites support and follow the HTTP protocol, the Web site hierarchy is automatically extracted, and the URL links are added to the Web hierarchy to find the Web pages containing parameters .
[0034] Step 2: Parse the web page to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com