Analysis method, analysis device, and analysis program
An analysis method and process technology, applied in the field of analysis, analysis device and analysis program, can solve the problems of increased web application attacks, service provider damage, content tampering, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
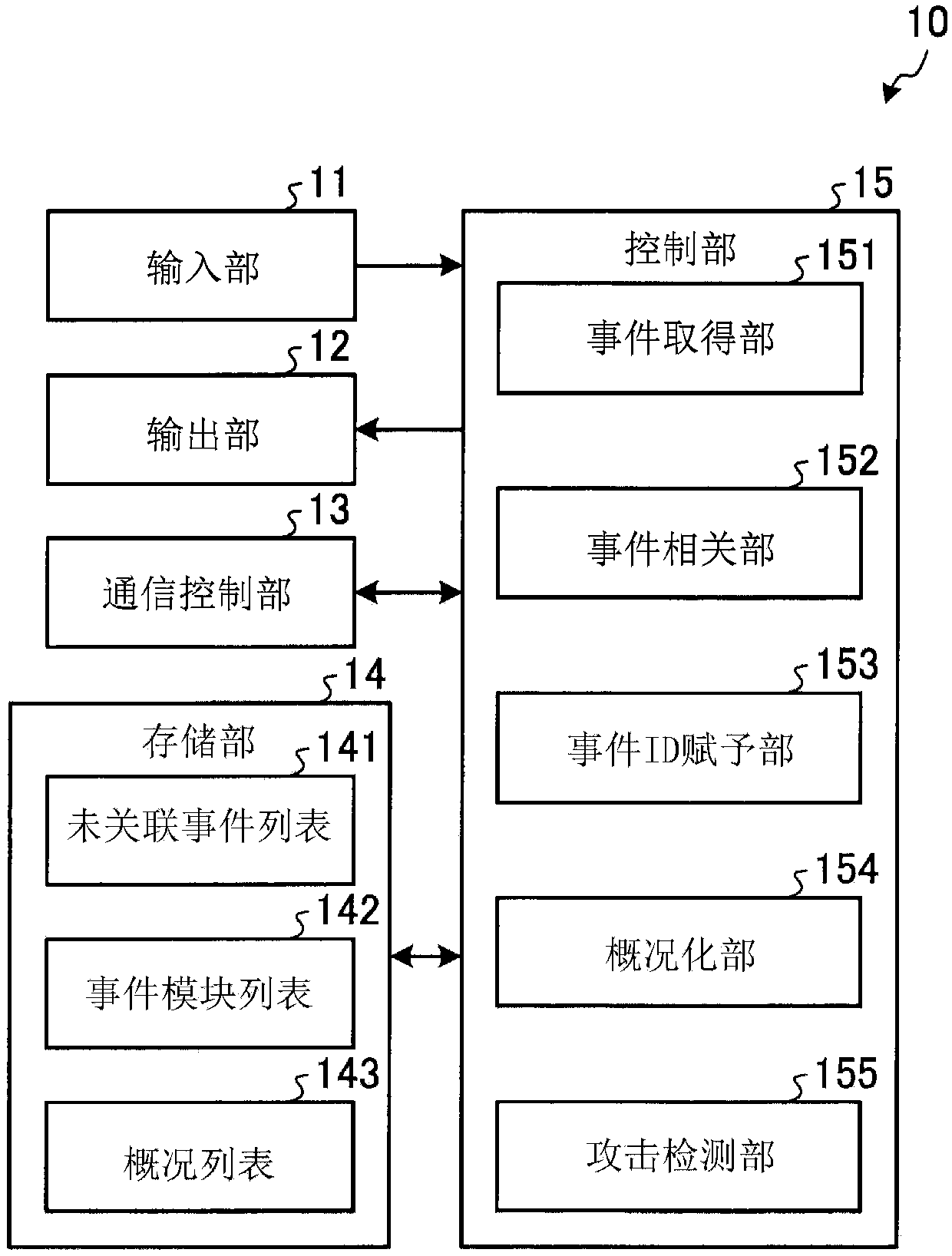
[0028] Hereinafter, one embodiment of the present invention will be described in detail with reference to the drawings. In addition, this invention is not limited to this embodiment. In addition, in the description of the drawings, the same reference numerals are assigned to the same parts.
[0029] [system structure]
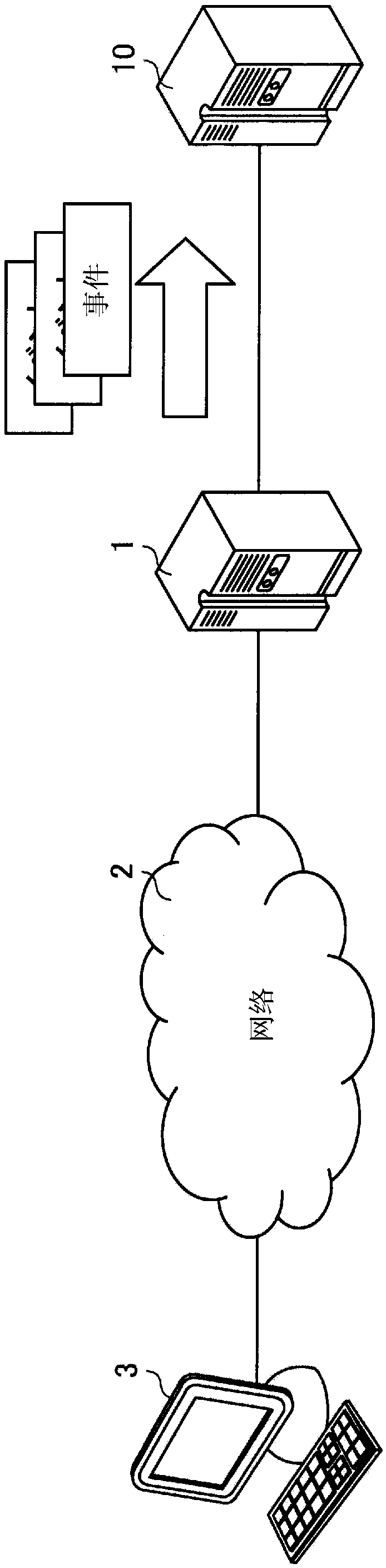
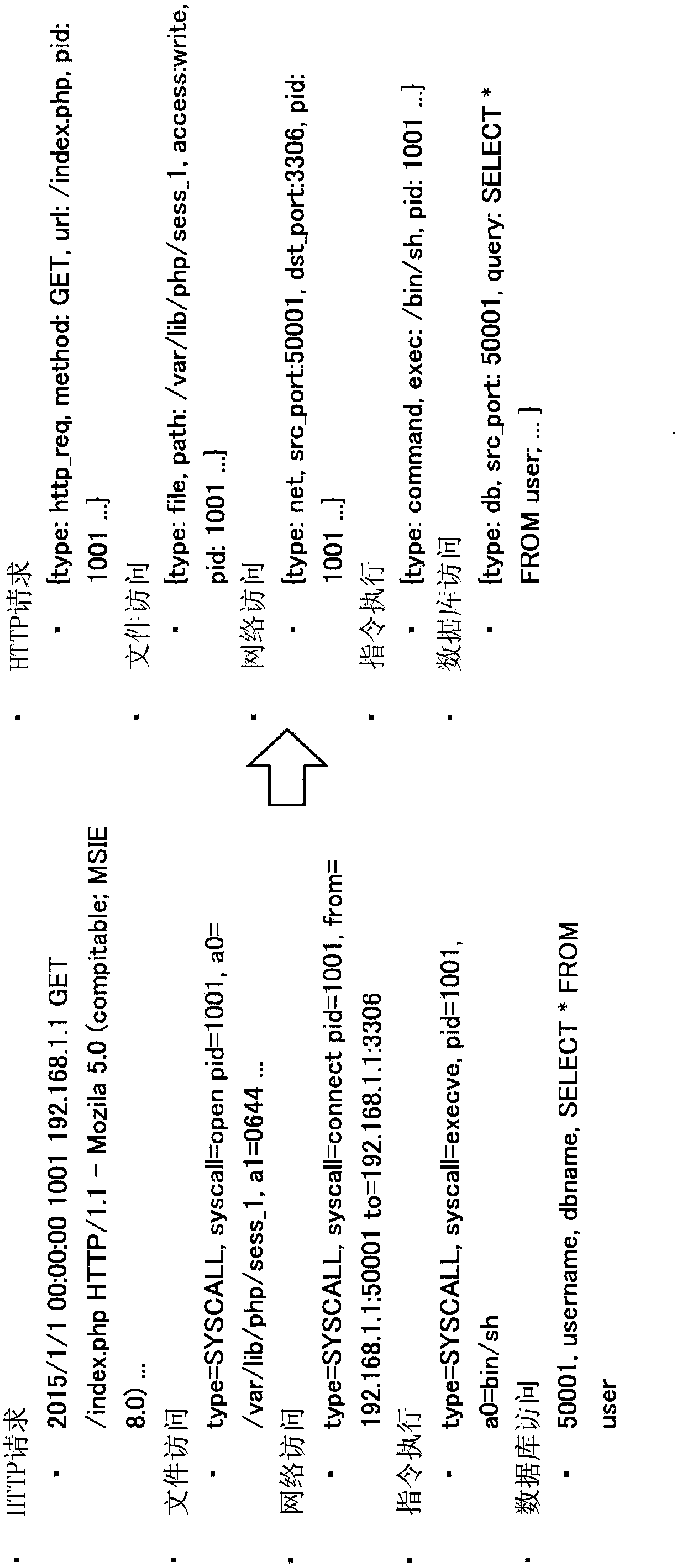
[0030] figure 1 It is a schematic diagram showing an example of a schematic configuration of a system to be analyzed by the analysis device of the present embodiment. Such as figure 1 As shown, the Web server 1 operated by the service provider receives requests to the Web server 1 such as HTTP requests from the client terminal 3 through the network 2, and provides Web application services to users of the client terminal 3. The Web server 1 stores logs of events such as HTTP requests, file access, network access, command execution, and database (DB) access related to the provision of Web application services in an appropriate storage area.
[0031] In such ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com