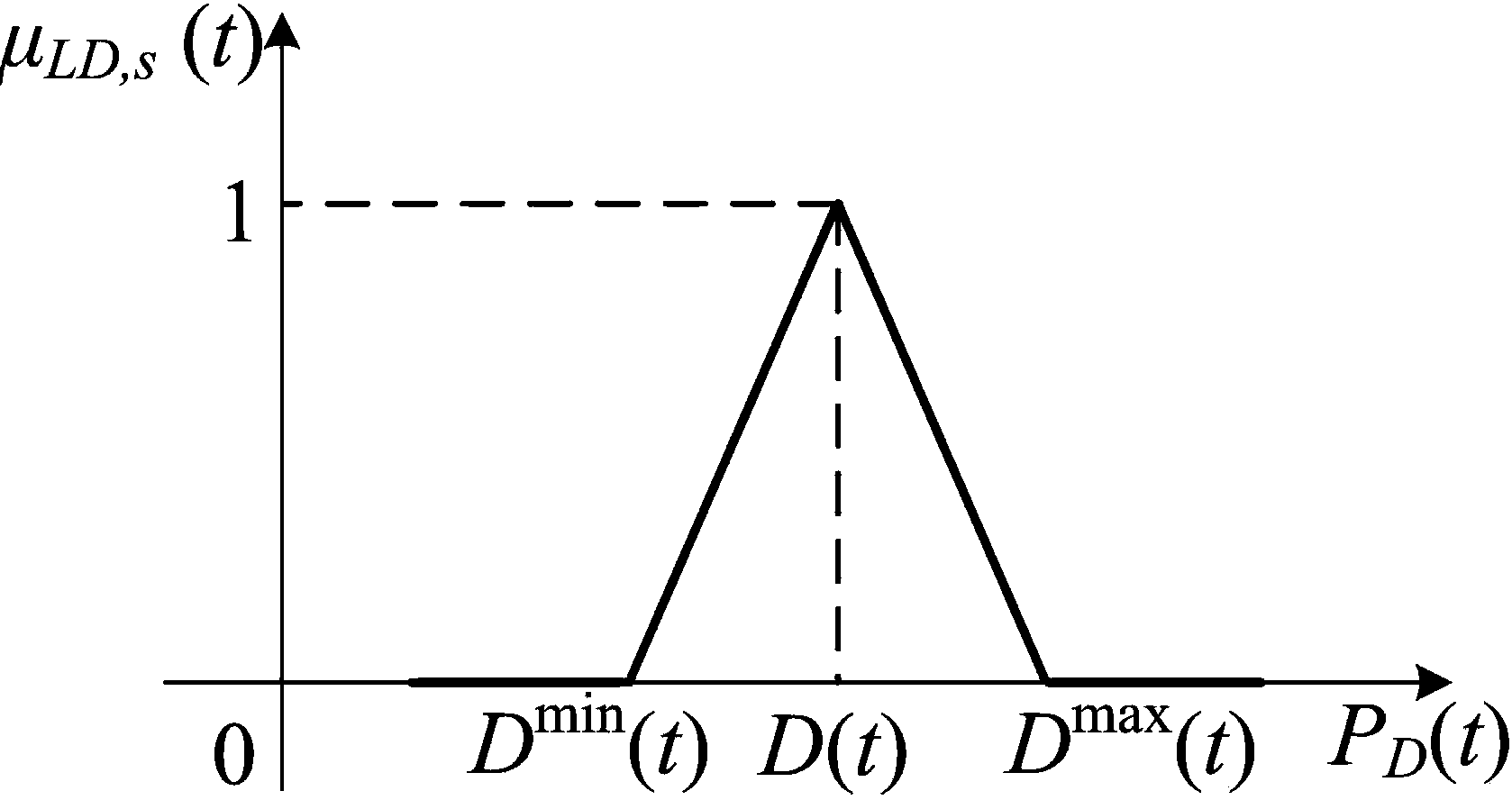Patents
Literature
147results about How to "Balance security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
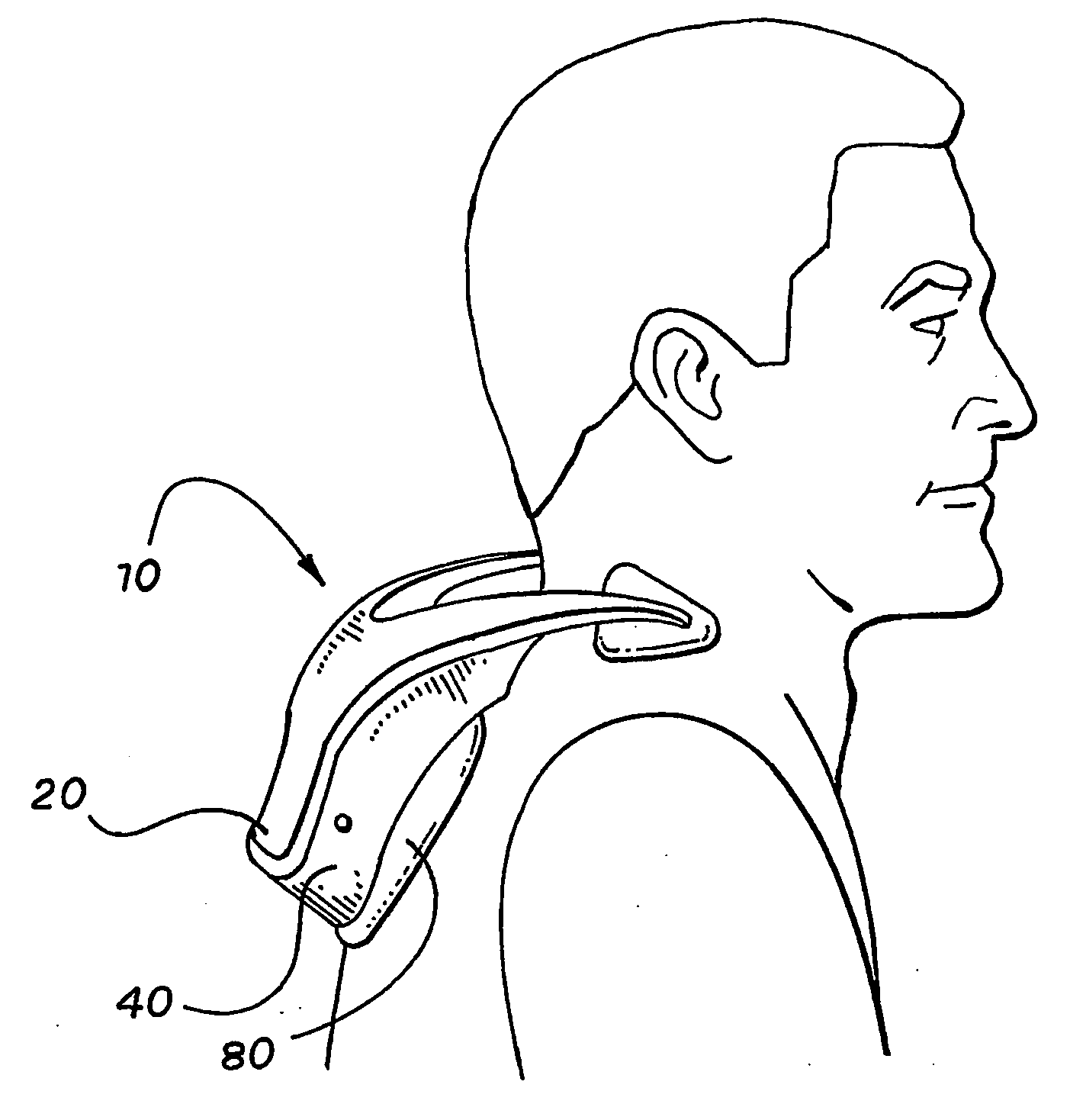
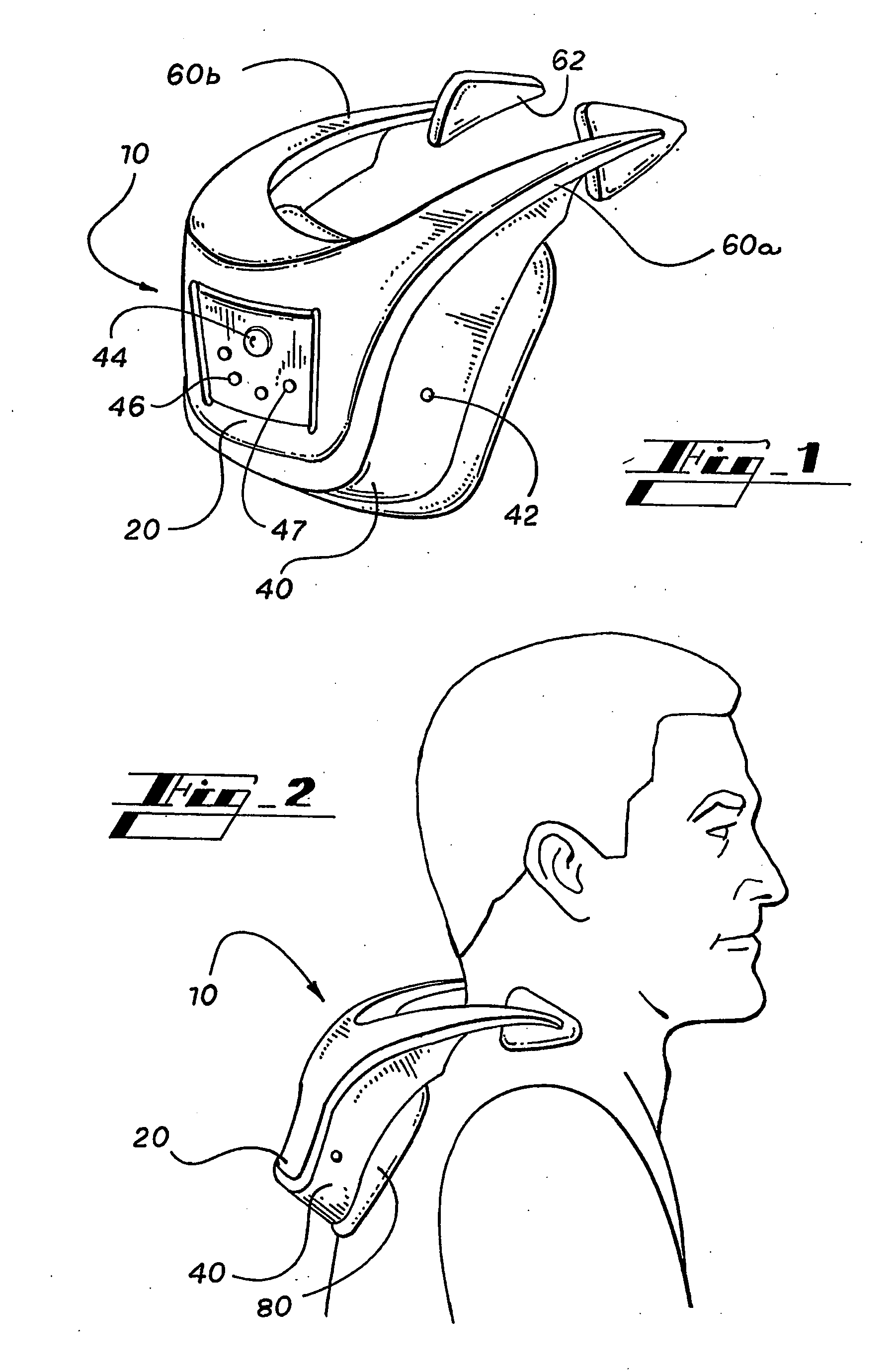
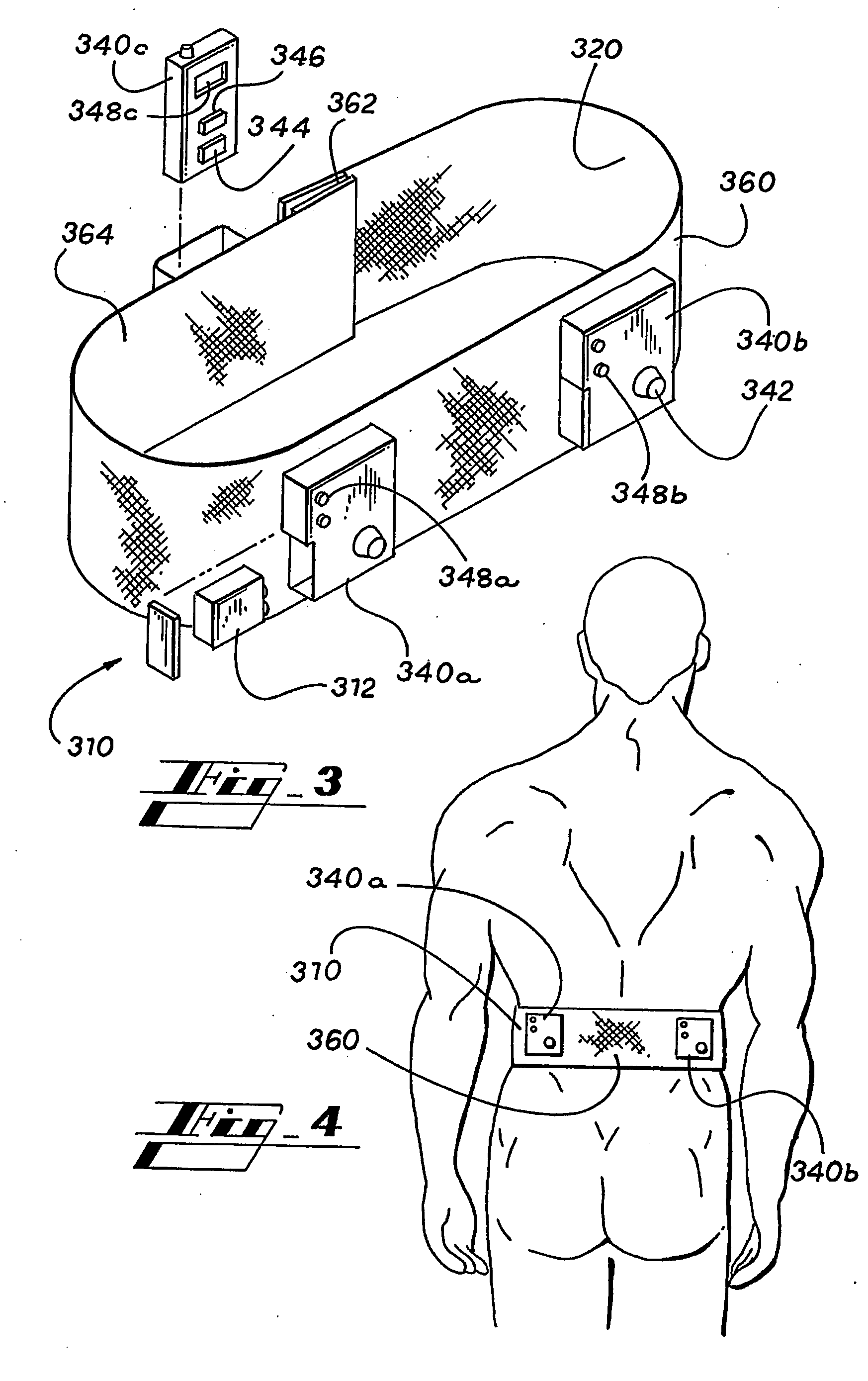
Frequency Stimulation Trainer
InactiveUS20090076421A1Relief the painRelieve painMassage combsMassage beltsRe educationPerformance enhancement
A preferably non-electrical nerve communication enhancement tool that sends specific, pre-timed, controlled vibrational and / or acoustical stimulation frequencies to the body to enhance nerve communication for the purpose of assisting in proper function of skeletal muscle, smooth muscle, sympathetic and parasympathetic nervous systems, and facilitating rapid and improved cerebellar timing circuit and related cerebellar learning mechanism pathways such as the inferior olivary-Purkinje-Thalamus cell system and other similar neuronal pools, to improve muscle memory, coordinated functional neuron-musculo-skeletal performance improvement, enhance blood flow, increased range of motion, flexibility, strength and dexterity, neuromuscular re-education, muscle tone recovery, pain modulation, improved eye-hand coordination, gait improvement, balance and stability gains, kinetic chain integration, neurological performance enhancement, sensory dysfunction reduction, and improvement in mental and cognitive function.
Owner:STIMTRAINER
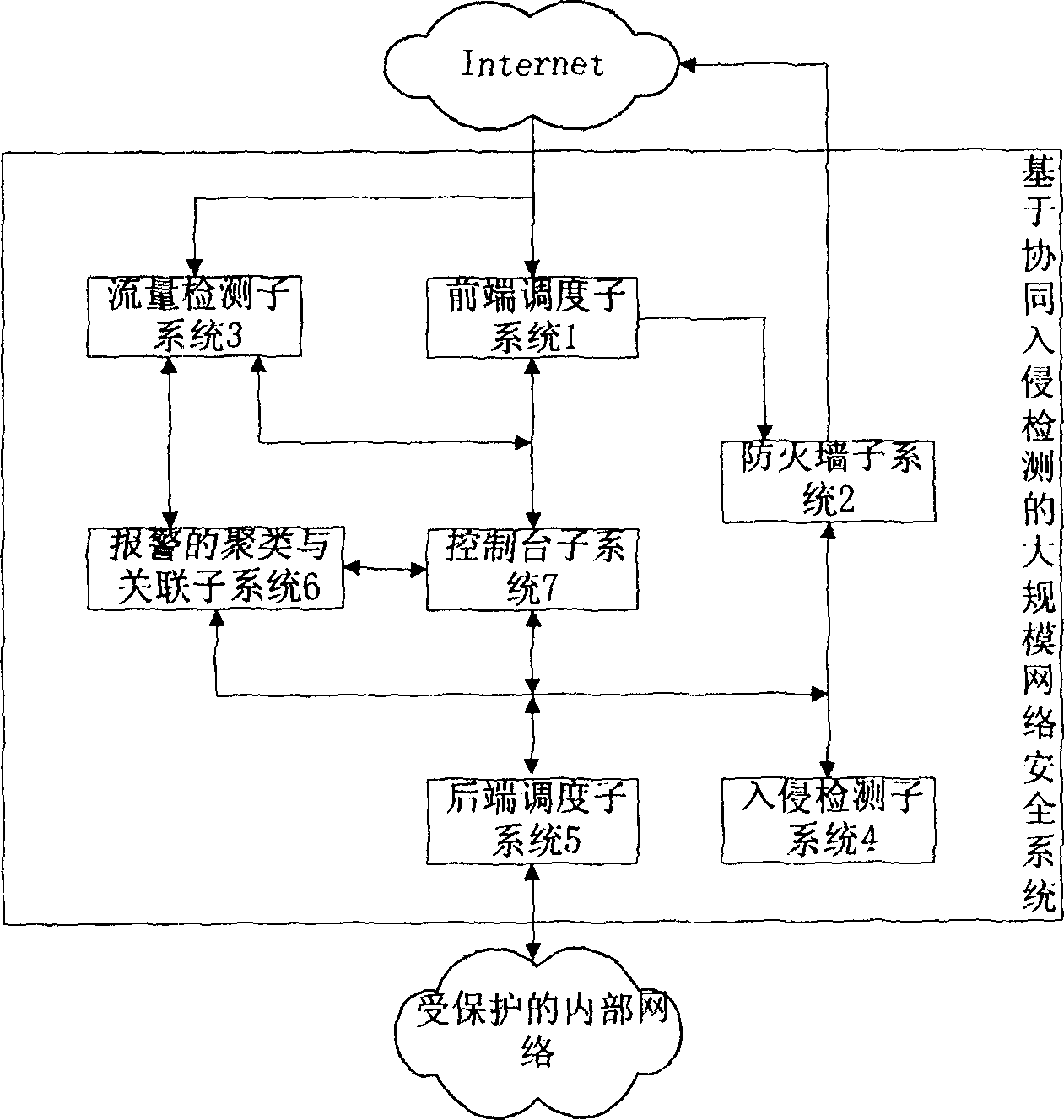
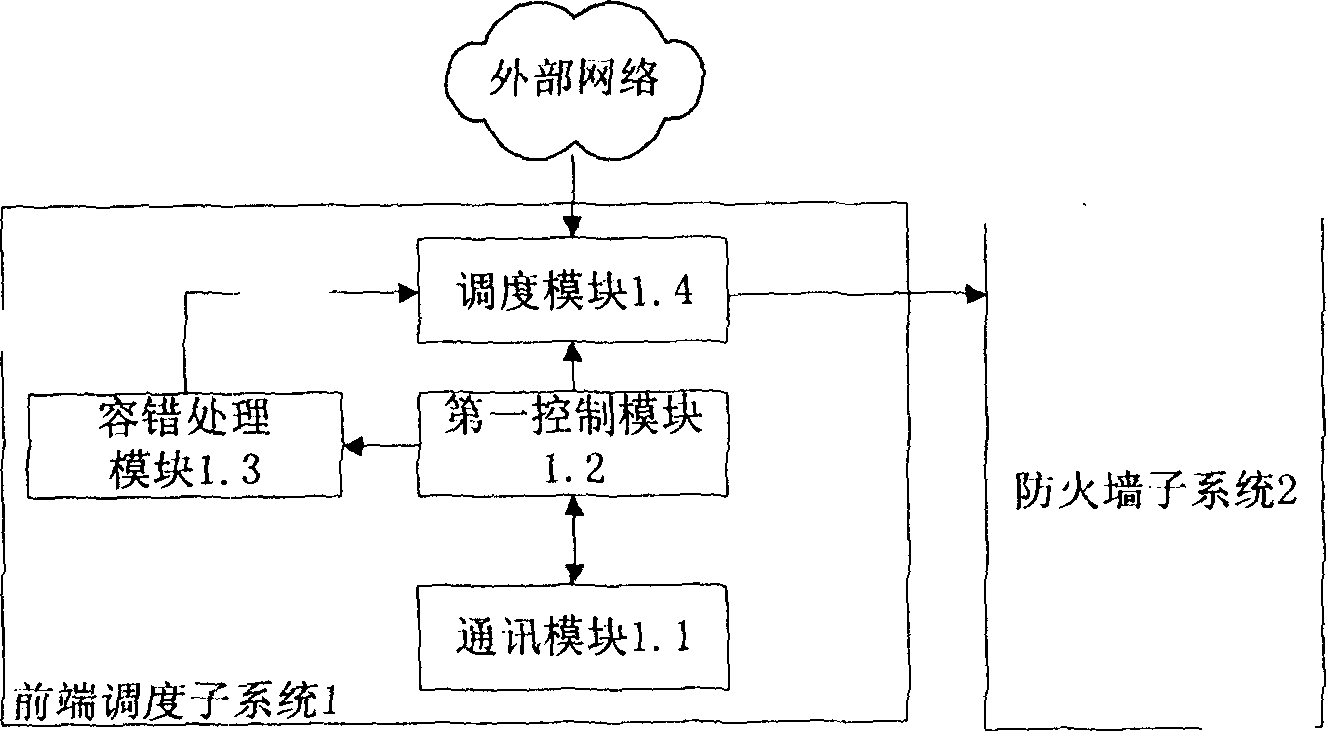
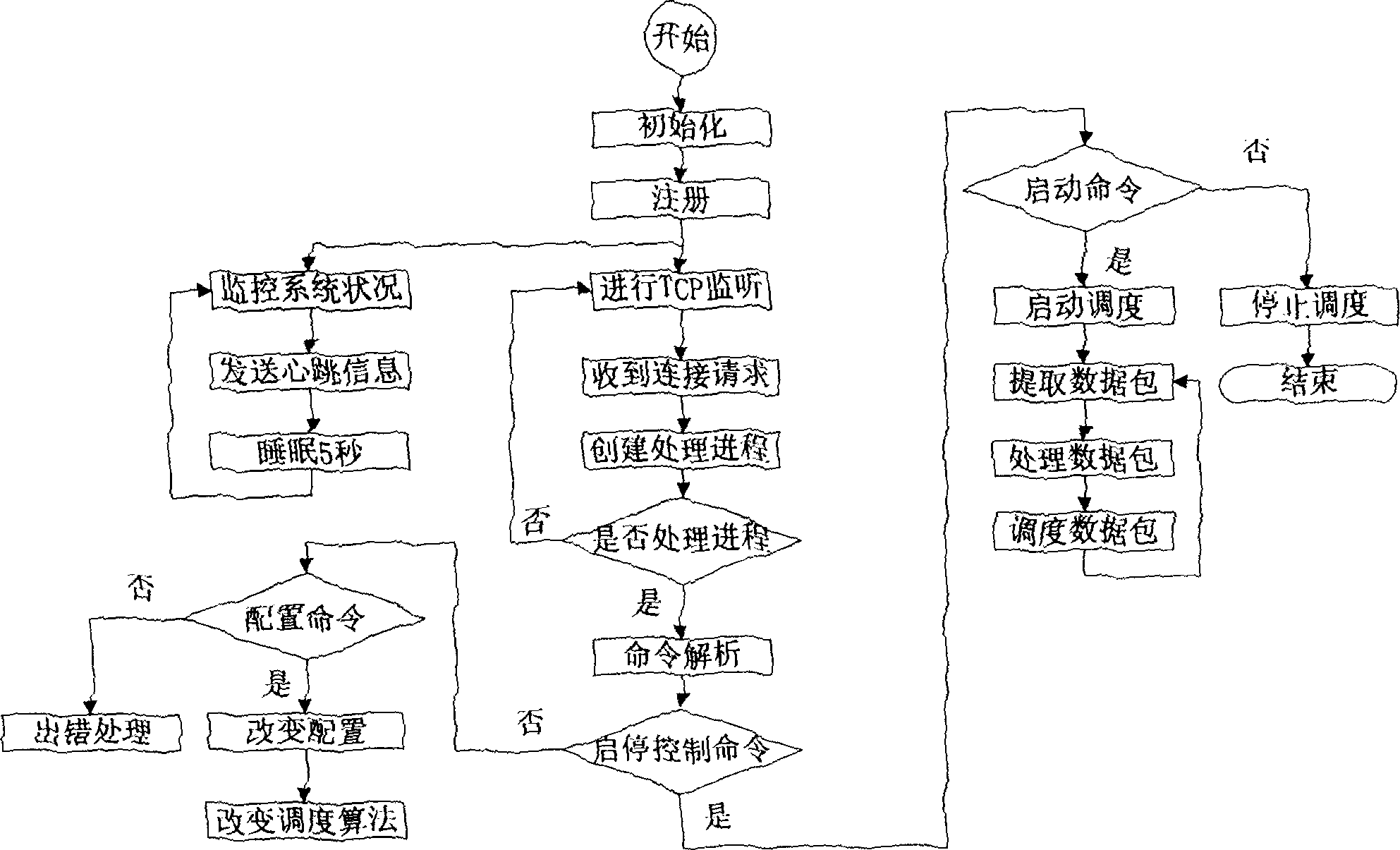
Cooperative intrusion detection based large-scale network security defense system
InactiveCN1668015ACoordinated Intrusion PreventionPrevent intrusionData switching networksTraffic volumeNerve network
This invention discloses a large scale network safety protection system based on cooperative intrusion detection, in which, a parallel fire wall system is formed by applying an advanced parallel technology and a model based on trust to protect against DDOS attack effectively, the parallel IDS sub-system applies a technology combing parallel technology and the state detection technology. The flow detection subsystem has high identifying ability to un-rule data based on the artificial nerve network model to detect the known attack and discover new attack behavior. The subsystems of the parallel fire wall, IDS, flow detection and co-related analysis and alarm are independent and complete to each other in function to exchange detection information and transfer detection and protection rules by an information driven system. The control station manages the subsystems.
Owner:HUAZHONG UNIV OF SCI & TECH
Quantitative risk and income self-adaptive dynamic multiple-factor authentication method
ActiveCN102510337AQuick responseBalance securityUser identity/authority verificationSystem safetySelf adaptive
The invention belongs to the technical fields of system safety and access control, and particularly relates to a quantitative risk and income self-adaptive dynamic multiple-factor authentication method. Through the method provided by the invention, an information system dynamically binds multiple authentication factors in different access scenes, thereby carrying out safety identification on a user logging in the system. Through the assessment of quantitative risk and income generated by access and the implementation of multiple-factor binding strategies, the information system determines the combination of authentication factors aiming at the corresponding access implementation so as to realize user identity authentication. The information system updates the assessed source historical data, thereby dynamically updating the assessment result of the quantitative risk and income so as to realize the self-adaptive characteristic of dynamic binding. By applying the method, the requirements for safety and usability of the information system can be balanced, and the response speed of the information system to an abnormal event can be improved.
Owner:FUDAN UNIV
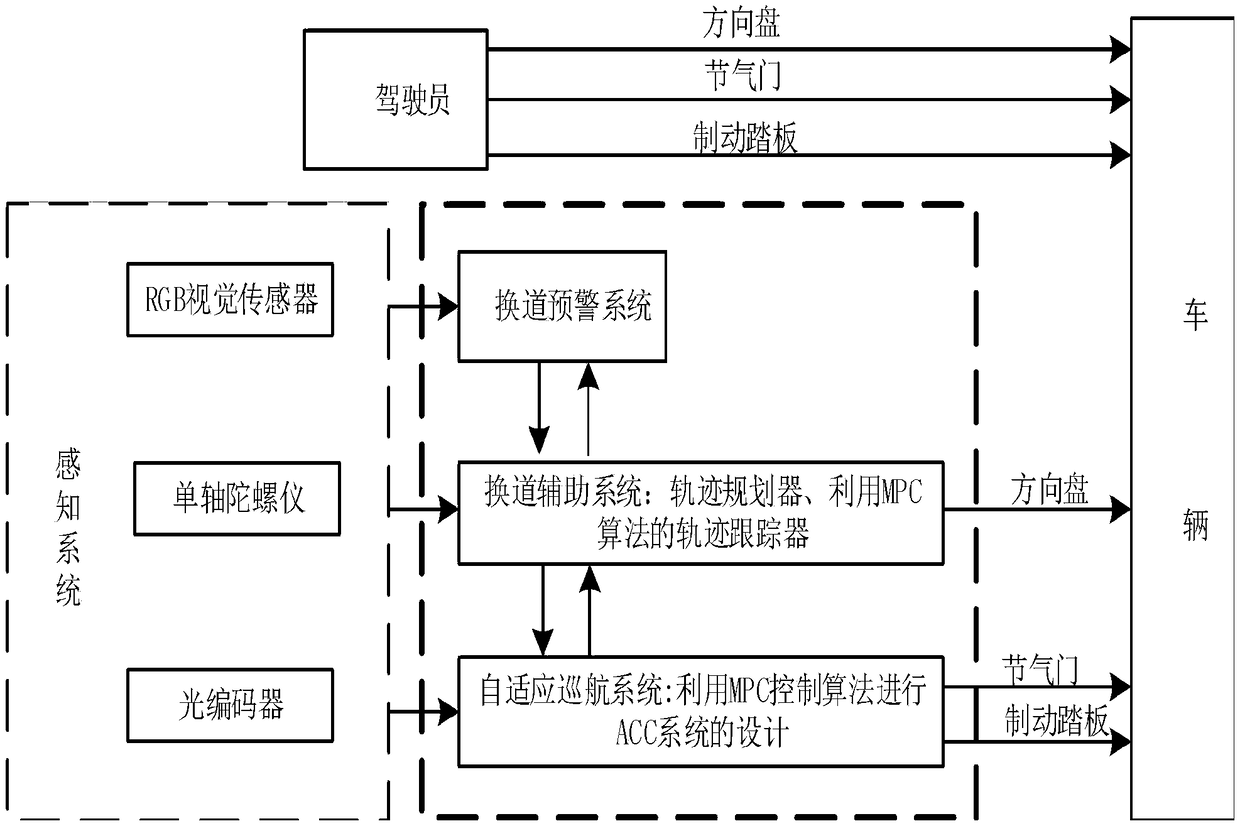
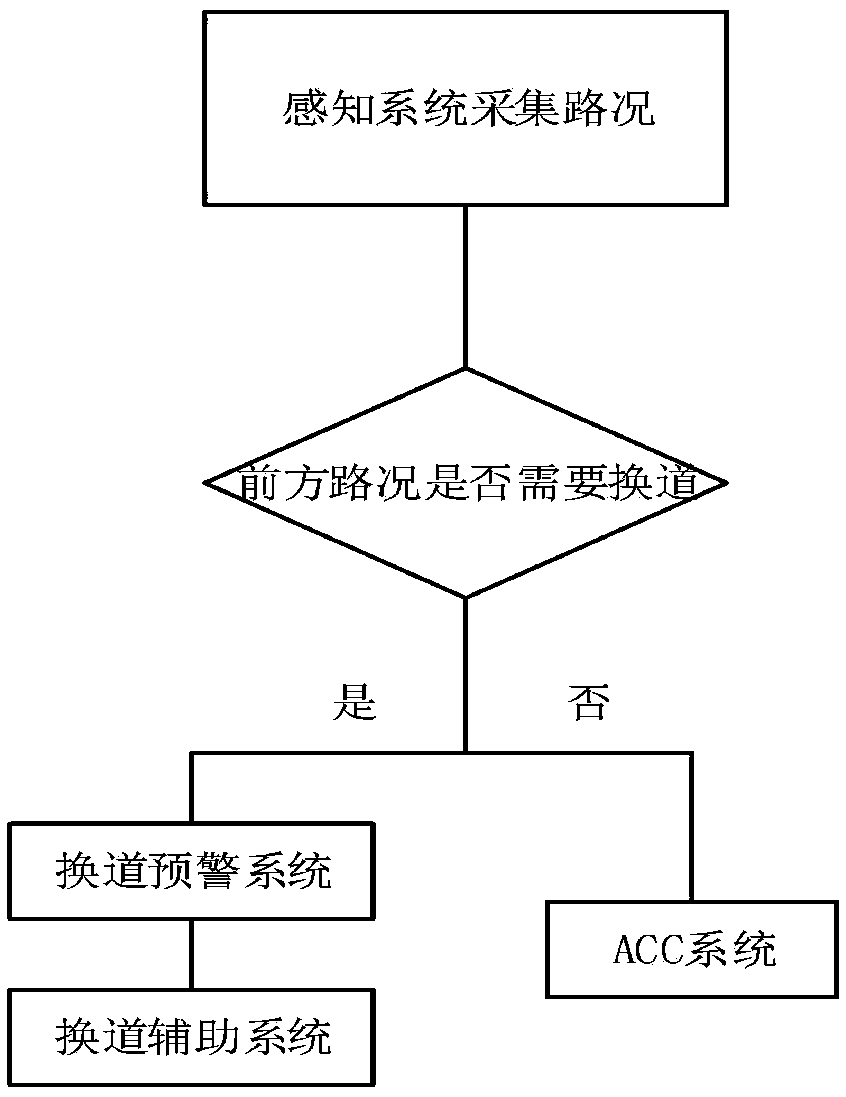
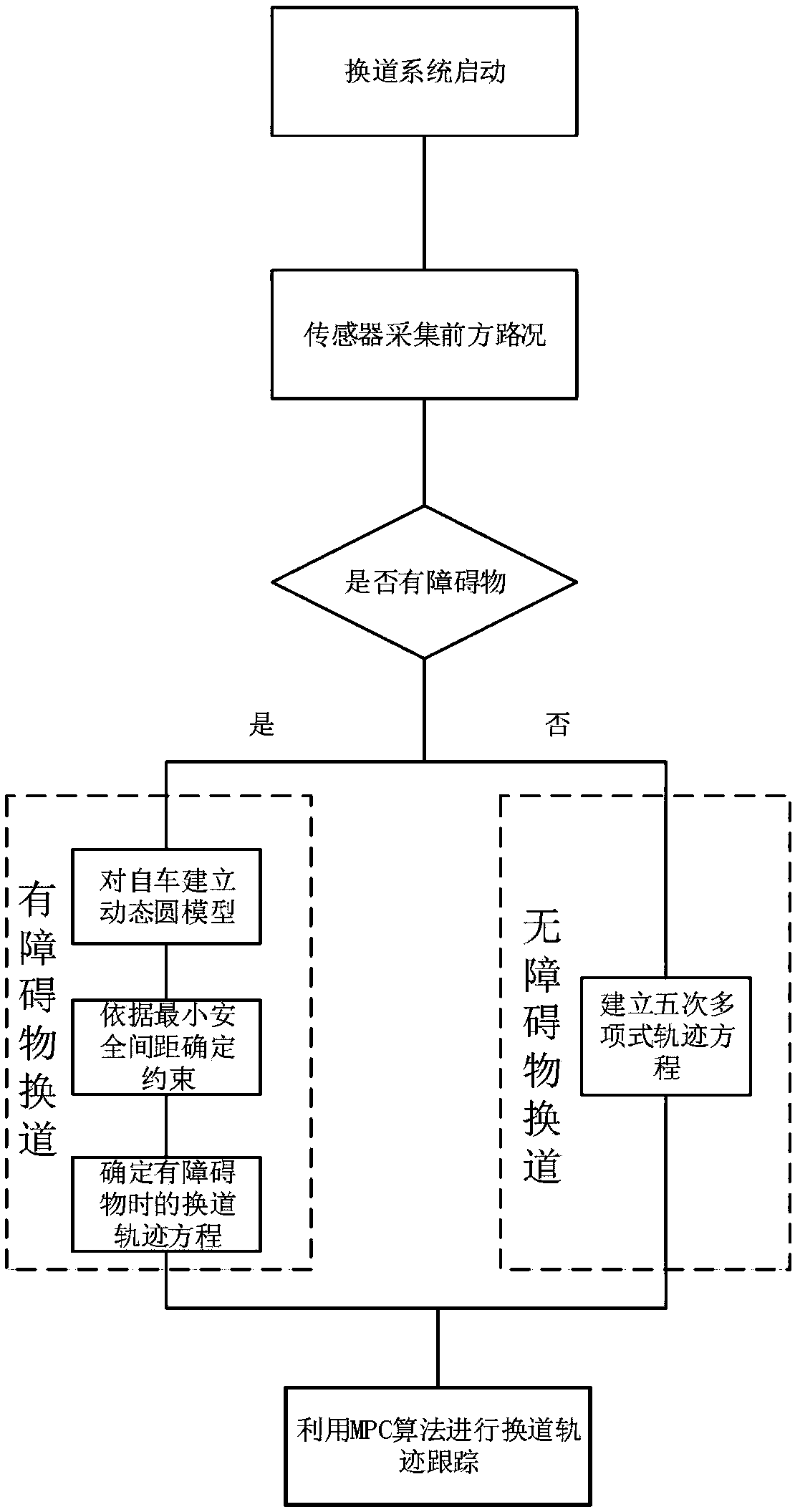
The invention relates to an adaptive cruise controller with lane changing auxiliary function and a working method thereof
The invention discloses an adaptive cruise controller with lane changing auxiliary function and a working method thereof, the controller includes a sensing system, a lane change warning system, a lanechange assistance system and ACC systems, the sensing system is respectively connected with a lane change warning system, a lane change assistant system and an ACC system, the lane change assistant system is respectively bidirectionally connected with the lane change warning system and the ACC system, and the lane change assistant system is respectively connected with a lane change trajectory planning path tracker and an MPC controller. The invention not only has all the functions of the original ACC system, that ios, the rad traffic environment in front of the vehicle can be monitored by sensors such as a vehicle-mounted radar, and the vehicle can be longitudinally controlled so as to keep a safe distance between the vehicle and the front vehicle. It can also change lanes automatically when there is complicated traffic condition in front or the driver has the intention to change lanes to avoid obstacles. And the controller can effectively avoid accidents, but also greatly improve theACC system of driver lane change caused by discomfort.
Owner:DALIAN UNIV OF TECH
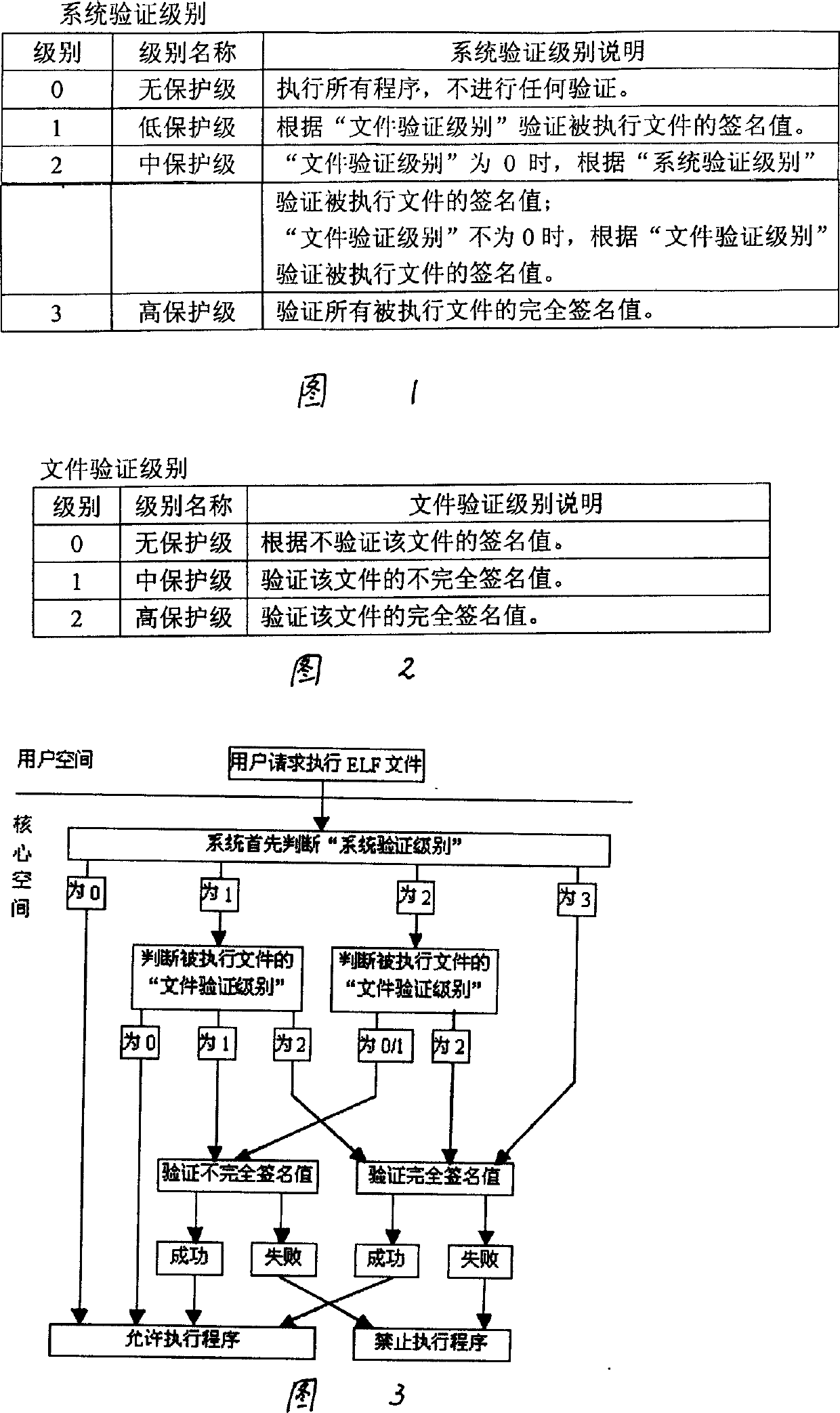
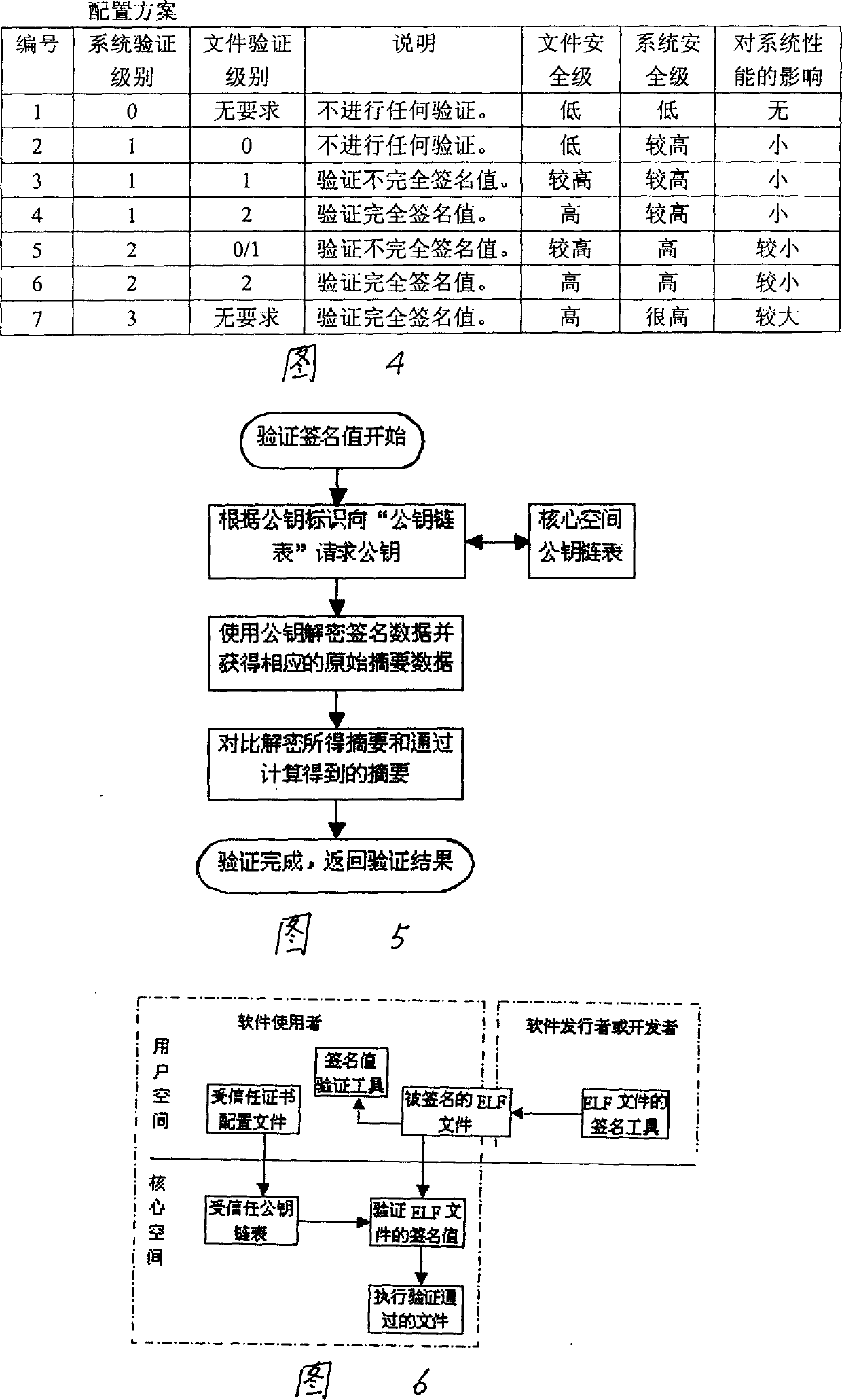
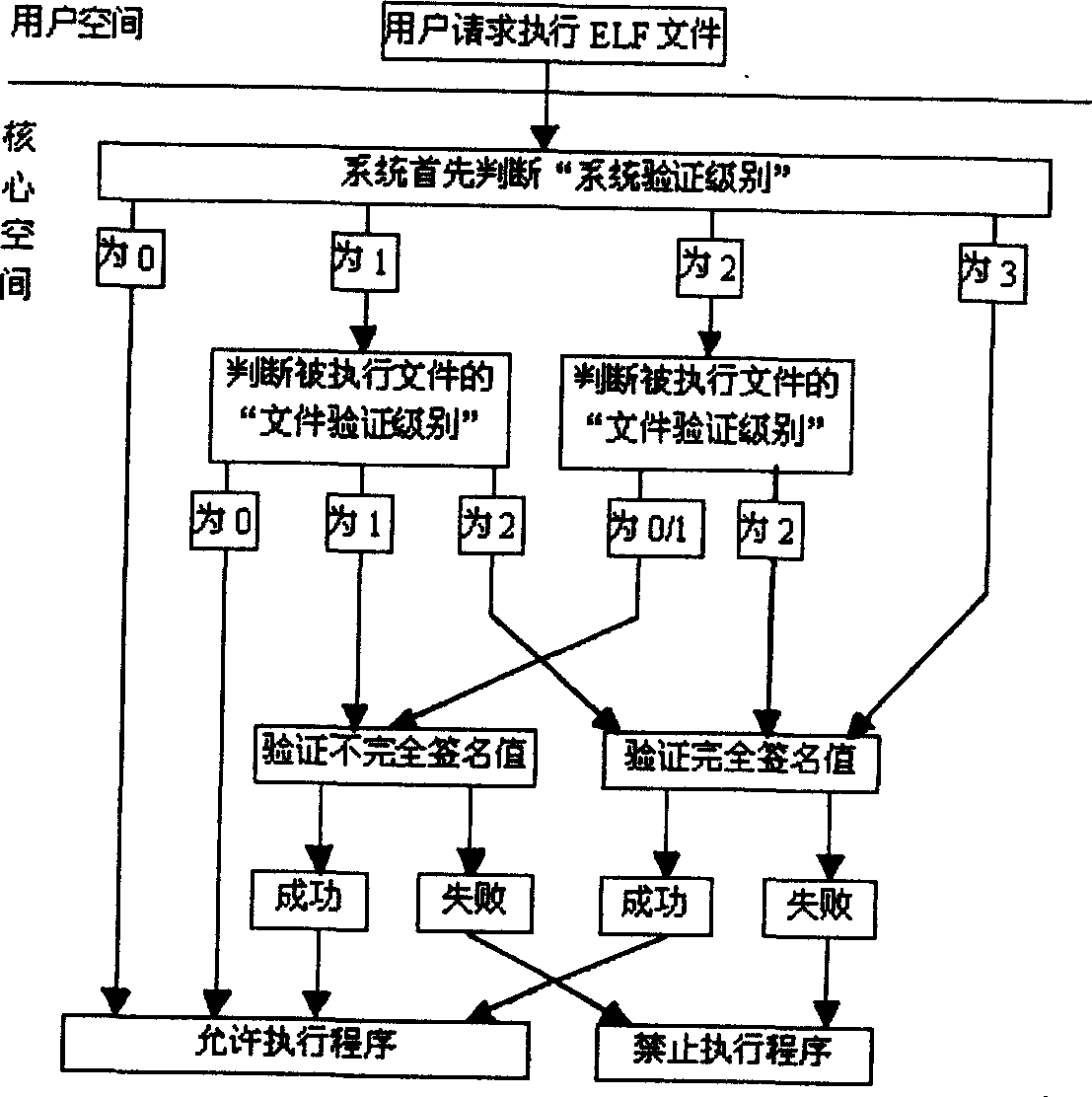
Code signature verifying method of ELF file form
InactiveCN1512355AImprove securityPrevent Malicious Code AttacksMemory loss protectionUnauthorized memory use protectionSystem safetySoftware development
The present invention discloses the verifying method of code signature in ELF file format. After the user requests executing ELF file, the system judges the level of system verification and determines the level of file verification of the executed file. For 0-level system verification, no code signature is not verified. For non-zero level, incomplete or complete signature value of the executed file is verified. During verification, the signer's public key is taken out from the kernel space chain table to decipher signature data and primary abstract data while available file is used to calculate the corresponding abstract data. The two pieces of abstract data are compared, and when they are the same, the verification is successful, or else failed. The present invention has the advantages of raised system safety resisting virus attack, optimal balance between safety and efficiency of the operation system and effective protection of software resource.
Owner:成都三零盛安信息系统有限公司
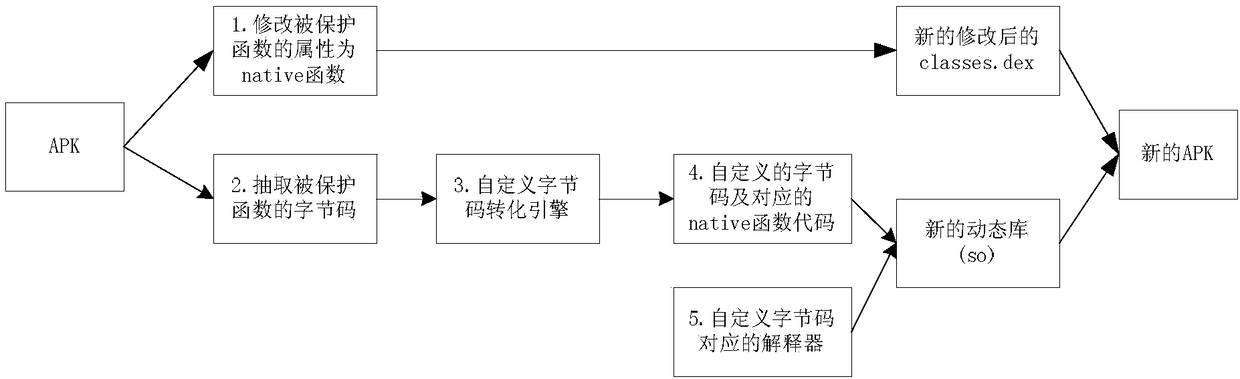
Protection method of executable program on Android platform
ActiveCN108733988AImprove securityIncrease flexibilityProgram/content distribution protectionSpecific program execution arrangementsReverse analysisSoftware engineering
The application provides a protection method of an executable program on an Android platform. The protection method comprises the following steps: determining a function needing to be protected in a classes.dex file in an APK file package, and forming new classes.dex file after the modification; compiling the C / C+ language realization of the function; and compiling the C / C++ language realization of the function as a dynamic library; replacing the original classes.dex file by using the new classes.dex file in the APK file package, and adding the dynamic library in the APK file package. Throughthe protection method provided by the application, the reverse analysis difficulty is increased, and the difficulty of reducing the code is greatly increased.
Owner:BEIJING BANGCLE TECH CO LTD
Block chain-based multi-granularity data processing method, system and device, and storage medium
InactiveCN108345685AAchieve securityAchieve performanceDatabase distribution/replicationDigital data protectionGranularityUnstructured data
The invention provides a block chain-based multi-granularity data processing method, system and device, and a storage medium. The method comprises the following steps of receiving stored business databy a block chain node, and determining a data attribute of the business data; if the data attribute of the business data is a rich text type, storing the data in the block chain node; if the data attribute of the business data is a picture type, storing the data in a private storage cloud, and creating second navigation information of a storage path of the business data of the picture type in theprivate storage cloud by the block chain node; and if the data attribute of the business data is a video type, storing the data in a public storage cloud, and creating third navigation information ofa storage path of the business data of the video type in the public storage cloud by the block chain node. A multi-granularity non-structured data trusted storage scheme is introduced for data processing granularity through automatic judgment of the data type, thereby achieving balance between security and performance or expense.
Owner:物数(上海)信息科技有限公司
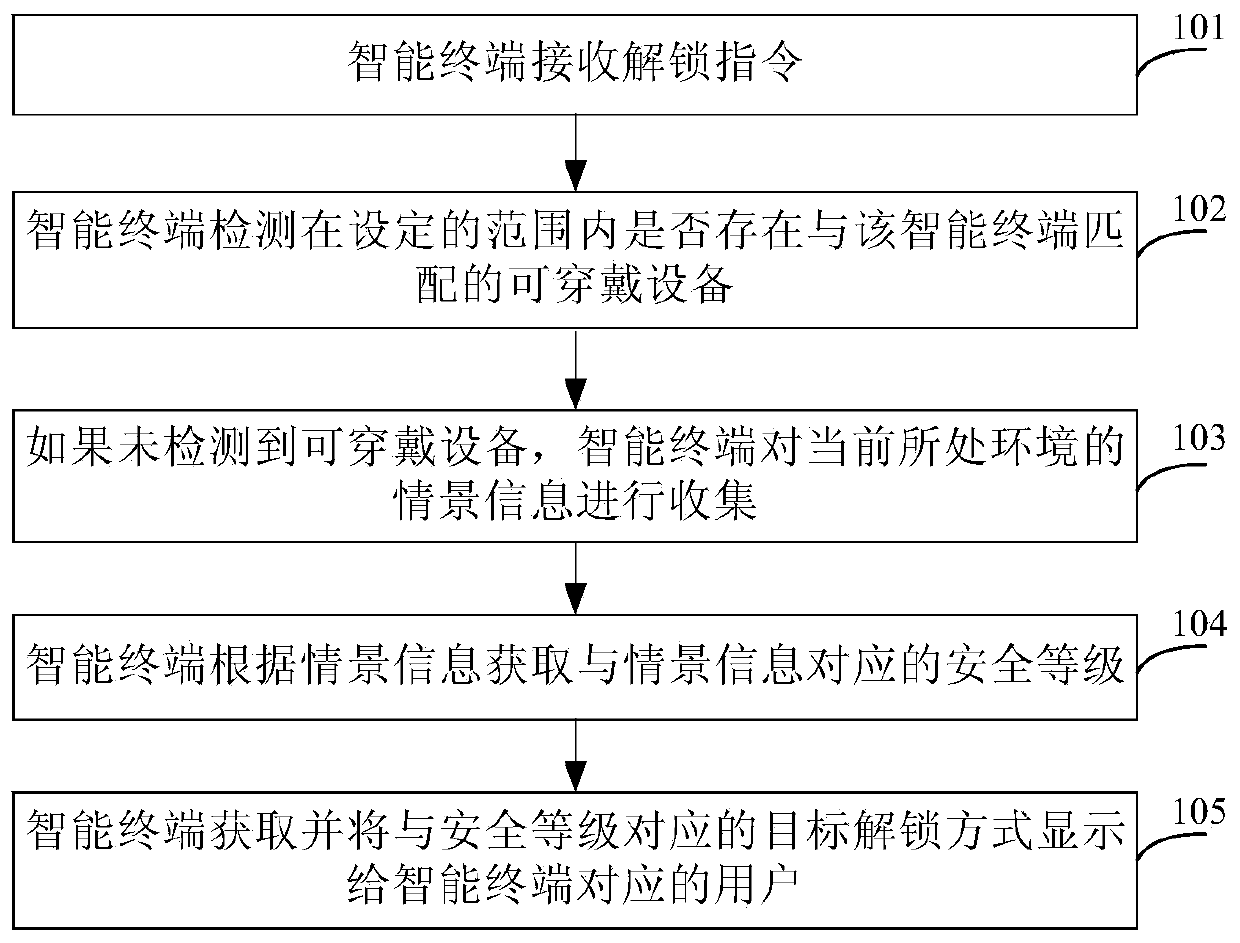
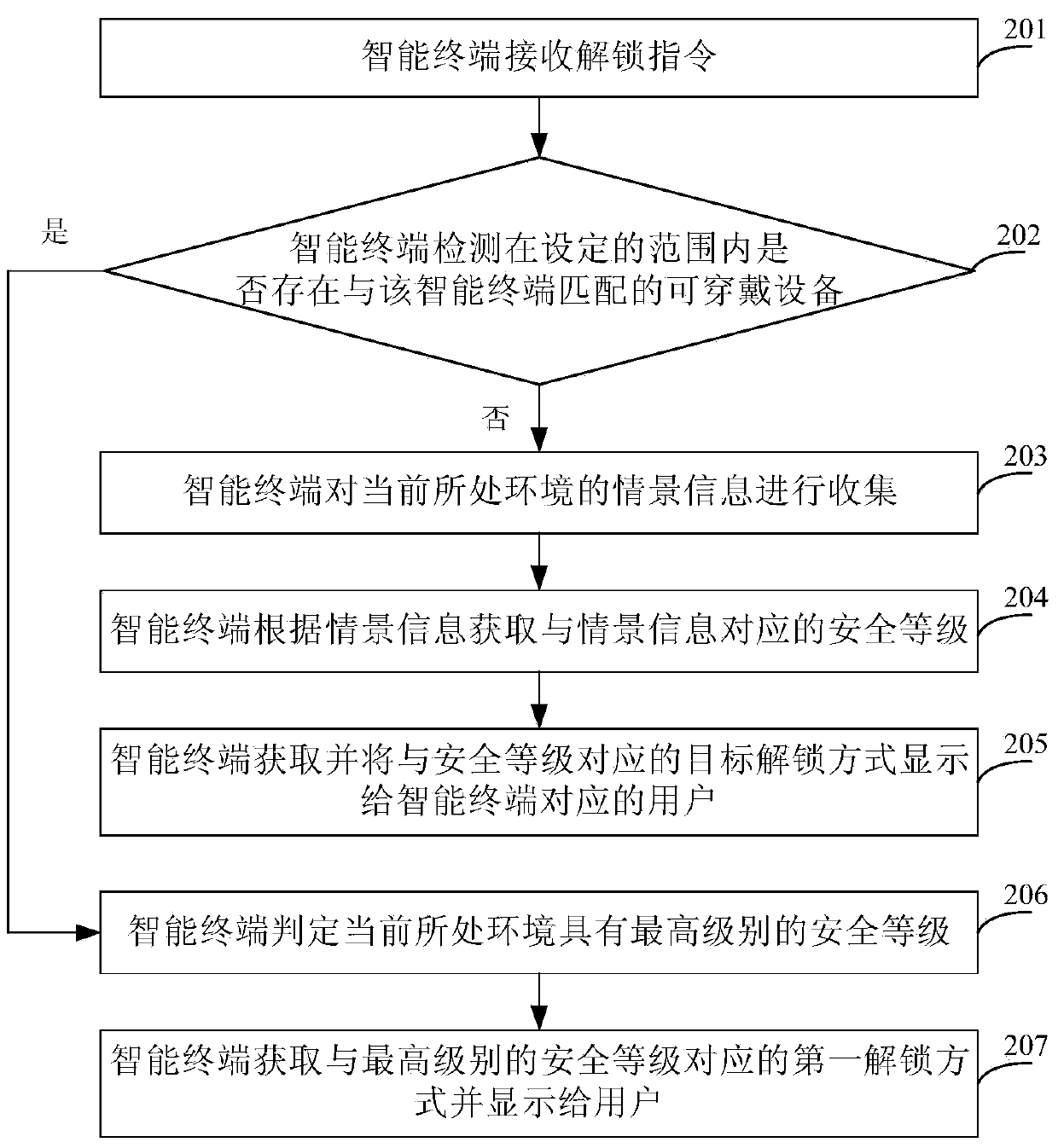
Method for switching unlocking modes of intelligent terminal and intelligent terminal
ActiveCN104217147ABalance securityBalance between ease of useDigital data authenticationComputer hardwareUsability
The invention provides a method for switching unlocking modes of an intelligent terminal and the intelligent terminal. After receiving an unlocking instruction, the intelligent terminal detects whether wearable equipment matched with the intelligent terminal exists in a set range; if the wearable equipment does not exist, the intelligent terminal collects the scene information of a current environment, acquires a safety level corresponding to the scene information according to the scene information, and acquires and displays a target unlocking mode corresponding to the safety level to a user corresponding to the intelligent terminal. The corresponding unlocking mode can be selected for the intelligent terminal according to the safety of the current environment, so that the safety and the usability of the intelligent terminal can be balanced.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Intelligent equipment unlocking method based on human eye motion feature
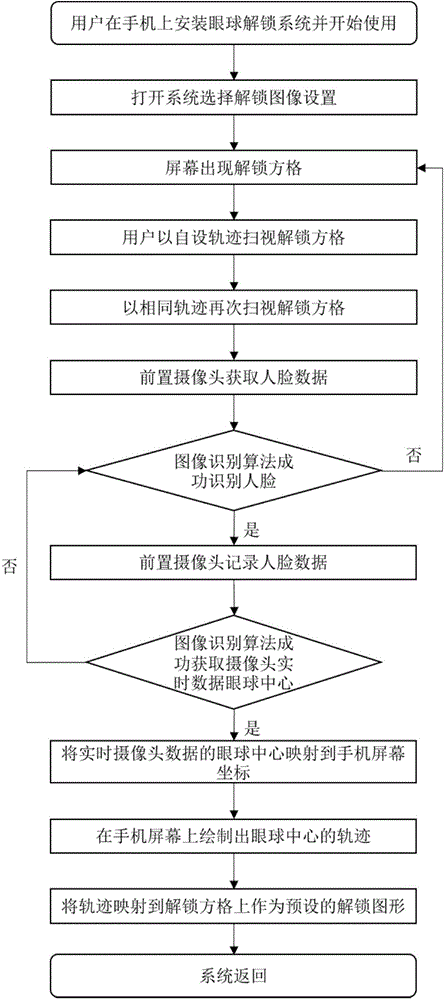
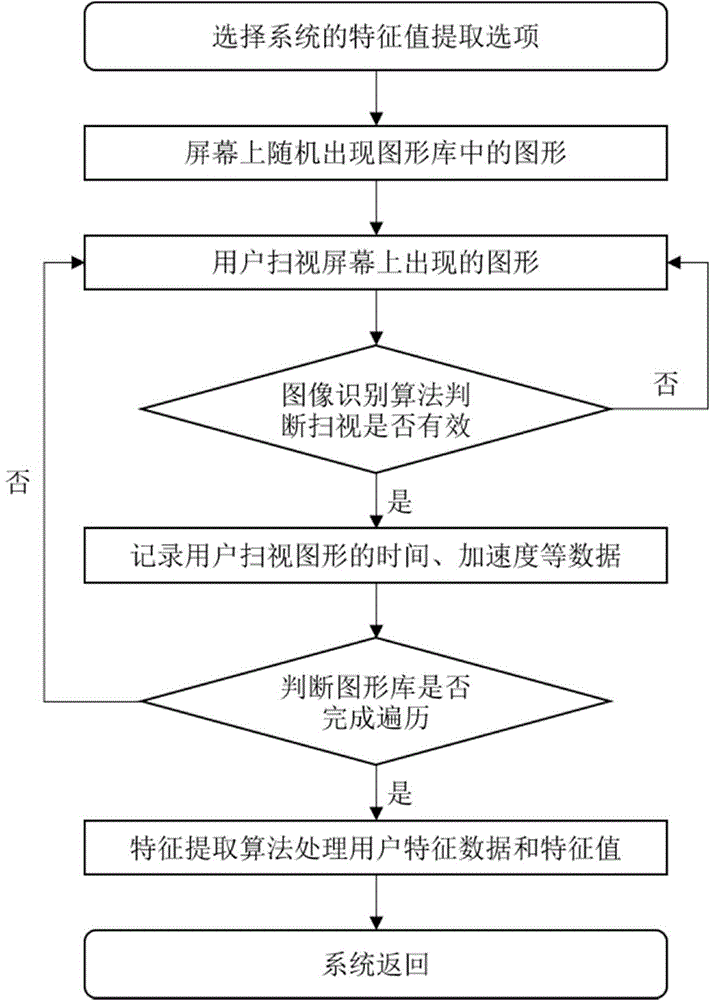
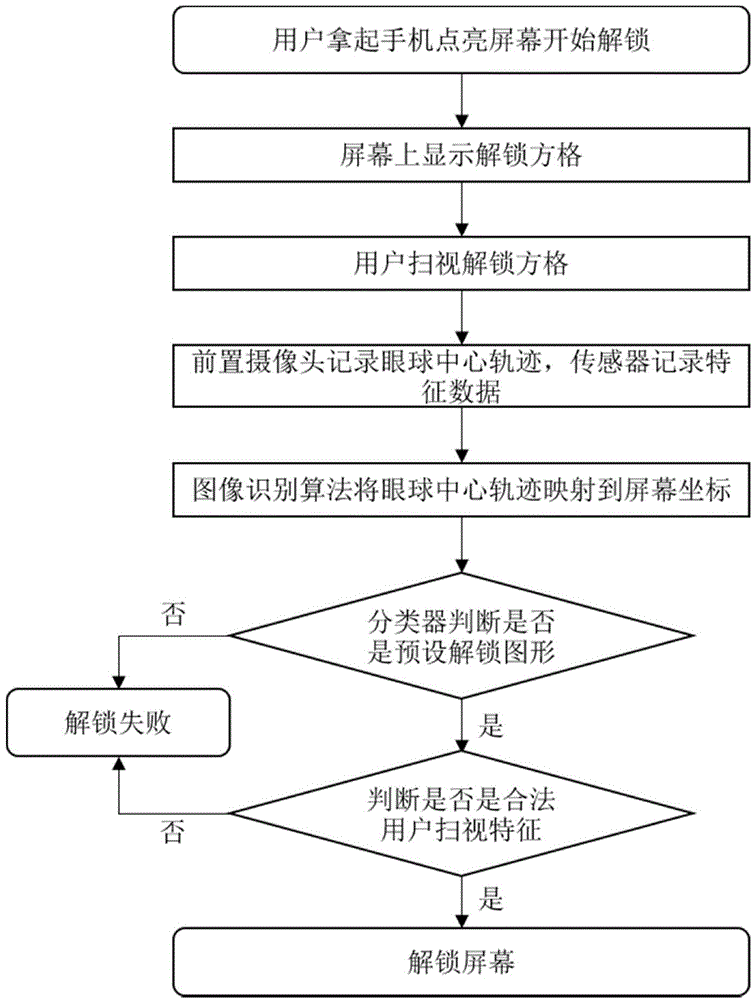
ActiveCN104158980ABalance securityEasy to unlockCharacter and pattern recognitionSubstation equipmentHand shakesShoulder surfing attack
The invention relates to an intelligent equipment unlocking method based on a human eye motion feature. The method comprises the following steps: acquiring a human face identification parameter, a user eye motion feature parameter as well as hand shake, movement and acceleration parameters during glancing of a user; extracting a user feature value and storing the user feature value; during unlocking, acquiring the human face identification parameter, the user eye motion feature parameter as well as the hand shake, movement and acceleration parameters during glancing of the user; extracting the user feature value; and comparing the user feature value of an unlocking person with the stored feature value, and outputting a signal indicating whether to unlock or not. A mobile phone can be unlocked conveniently and rapidly in an eyeball glancing way. On the other hand, 'shoulder surfing attack' can be prevented by adopting a mechanism of feature parameters, and an illegal user cannot unlock the mobile phone even if an unlocking pattern is obtained, so that the safety is improved. By adopting the unlocking way, the problem of user experience and safety is balanced. The intelligent equipment unlocking method has wide development and popularization prospects.
Owner:徐州泰丰泵业有限公司
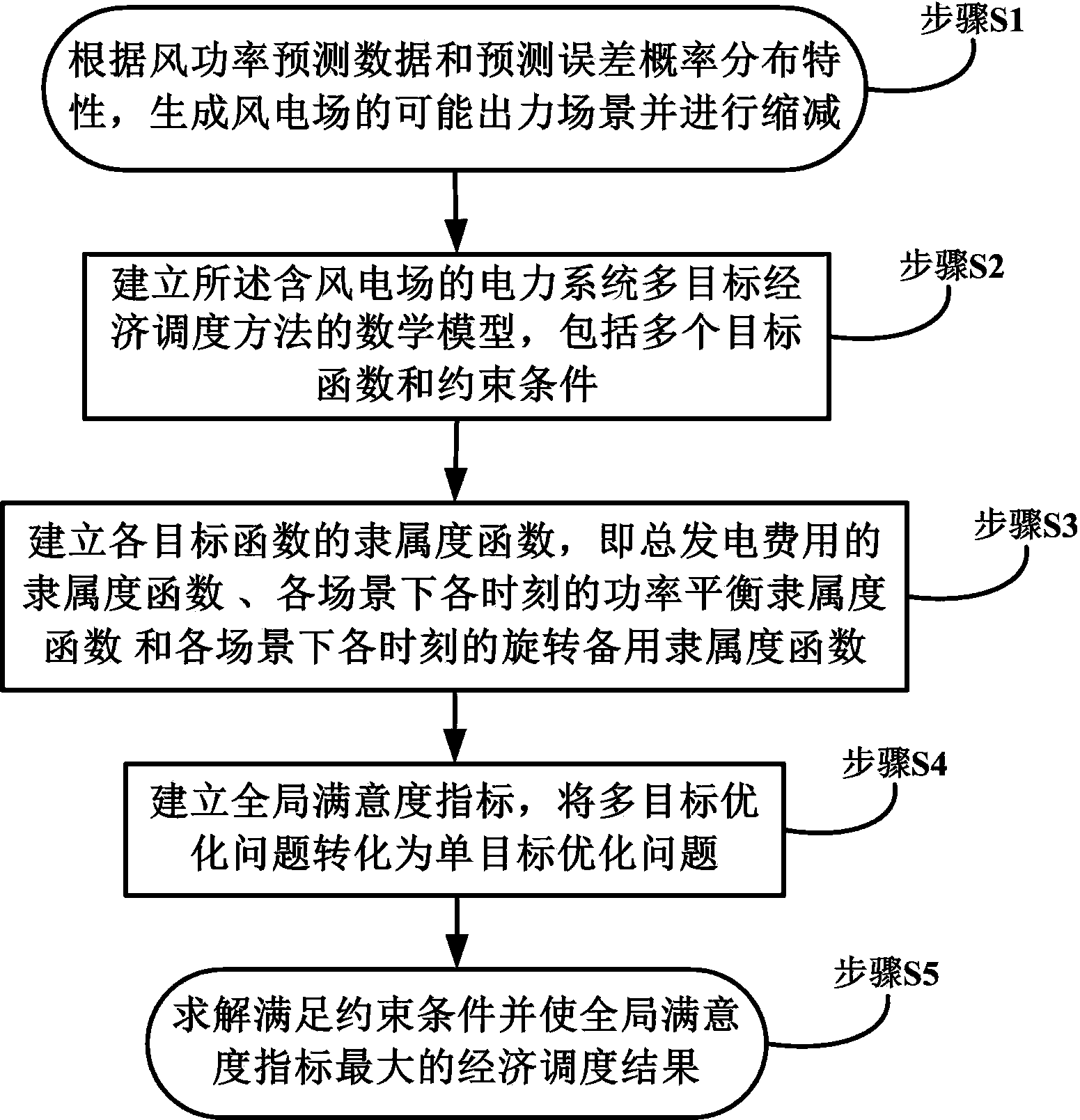
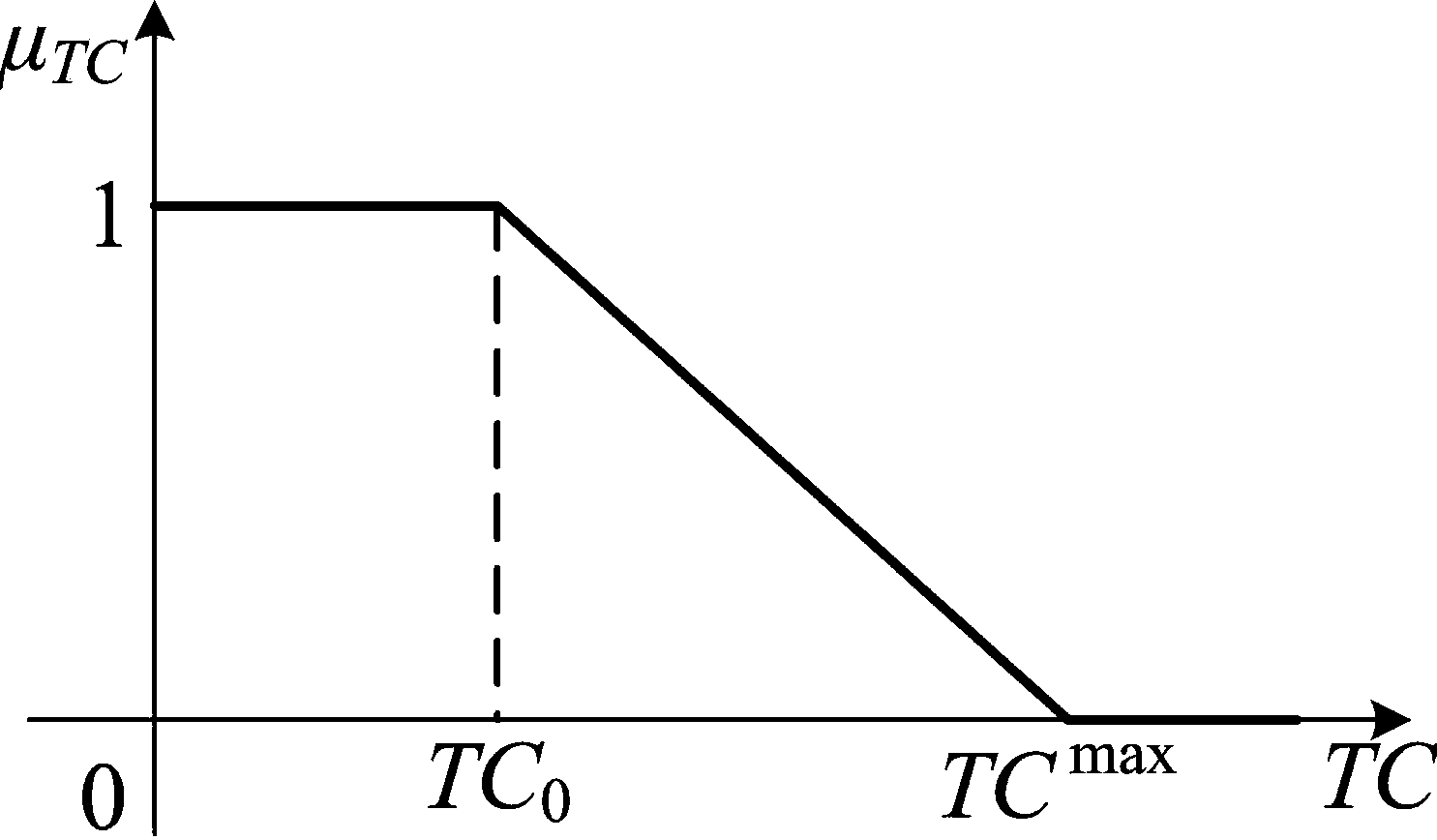
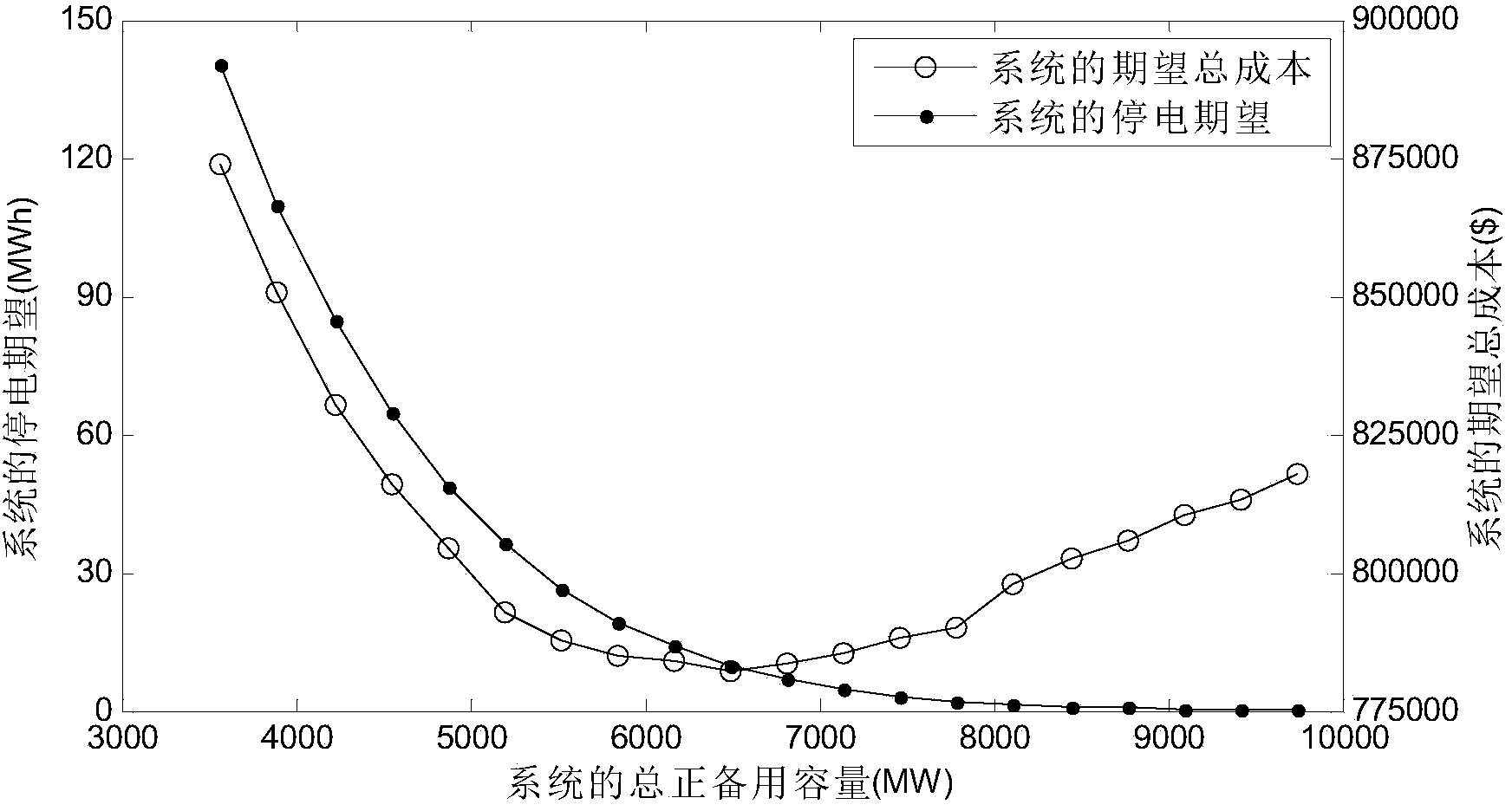
Multi-target economic dispatch method for power system with wind farm
InactiveCN104239967ABalance securityGuaranteed adaptabilityForecastingResourcesLower limitElectricity
The invention provides a multi-target economic dispatch method for a power system with a wind farm. The method comprises the steps that first, possible wind power output scenes in a dispatch cycle are generated, and the number of the scenes is reduced to S; second, a mathematical model of the method is built, target functions include total electricity generation cost, power balance levels of all the moments of all the scenes and spinning reserve levels of all the moments of all the scenes, and constraint conditions include output upper limit and output lower limit constraints of thermal power units, climbing rate constraints and the minimum start and shut down time constraints; third, fuzzification processing is carried out by building membership functions of all the target functions; fourth, the minimum values of all the membership functions are obtained to serve as global satisfaction degree indexes; fifth, an economic dispatch result meeting the constraint conditions in the second step and enabling the global satisfaction degree indexes in the fourth step to be maximum is solved. The economic dispatch method is suitable for solving the problems about economic dispatch of the power system with the wind farm and the thermal power units, and a plurality of optimization targets are balanced in a dispatch result.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Preparation method of anti-bacteria non-woven fabric and antibacterial agent
The invention discloses a preparation method of an anti-bacteria non-woven fabric and an antibacterial agent. The anti-bacteria non-woven fabric is prepared by comprising the steps of: dissolving chitosan by using lactic acid to prepare the chitosan solution; dissolving zinc lactate in deionized water to prepare the zinc lactate solution; mixing the chitosan solution with the zinc lactate solution to prepare the antibacterial agent; and modifying a non-woven fabric in an antibacterial way: adding the antibacterial agent on the non-woven fabric, drying to prepare the anti-bacteria non-woven fabric. According to the second part of antibacterial performance of fabrics in GB / T20944.2-2007, the anti-bacteria non-woven fabric prepared by the invention has bacterial inhibiting ratio more than 99 percent through absorptive method detection, is qualified through skin irritation and vagina mucosa irritation and skin allergic reaction irritation tests, and meets sanitation requirements on sanitation standard GB15980-1995 of disposable medical supplies and sanitation standard GB15979-2002 of disposable hygienic products.
Owner:俊富非织造材料(肇庆)有限公司
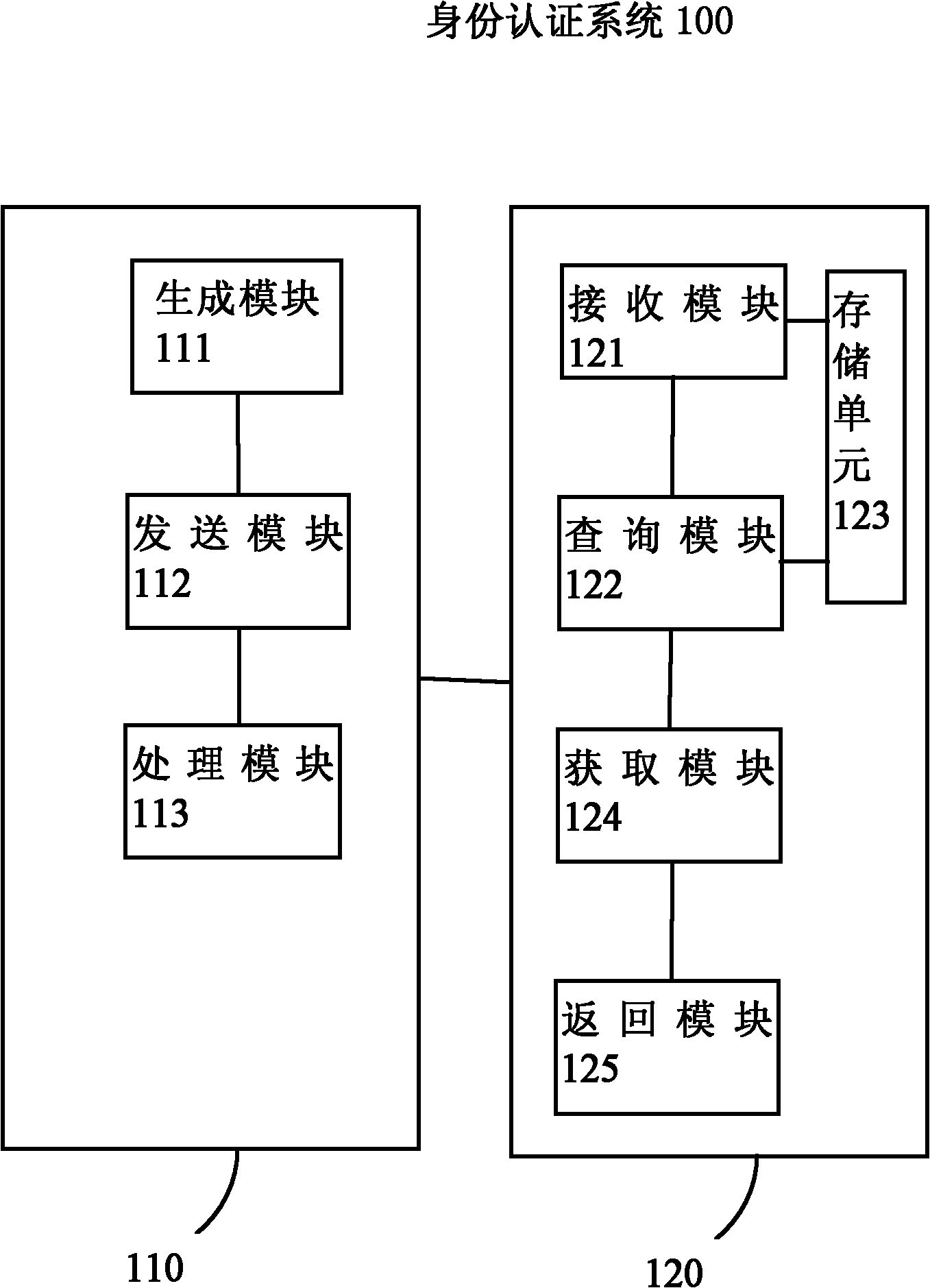
Identity authentication method and system
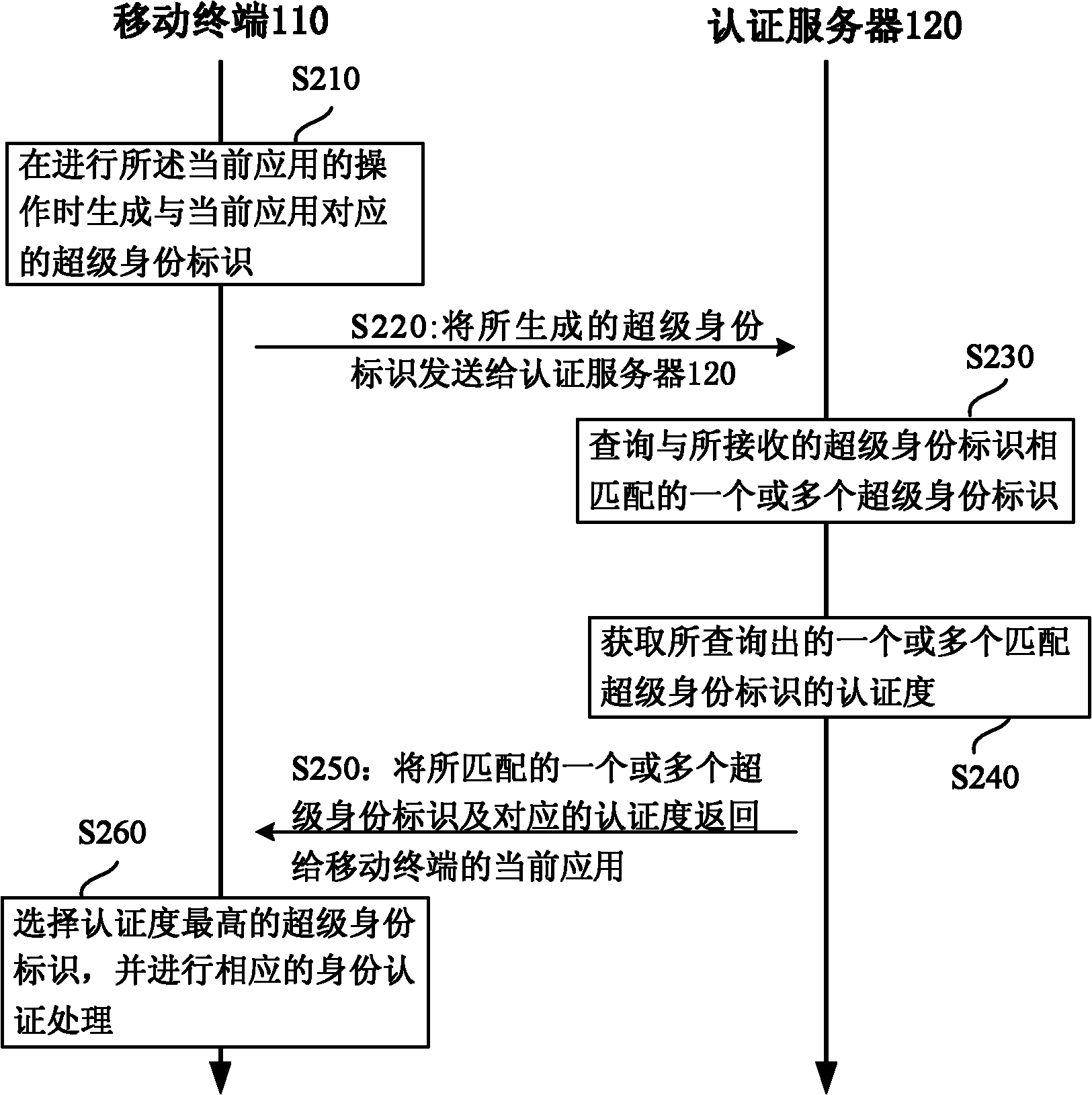
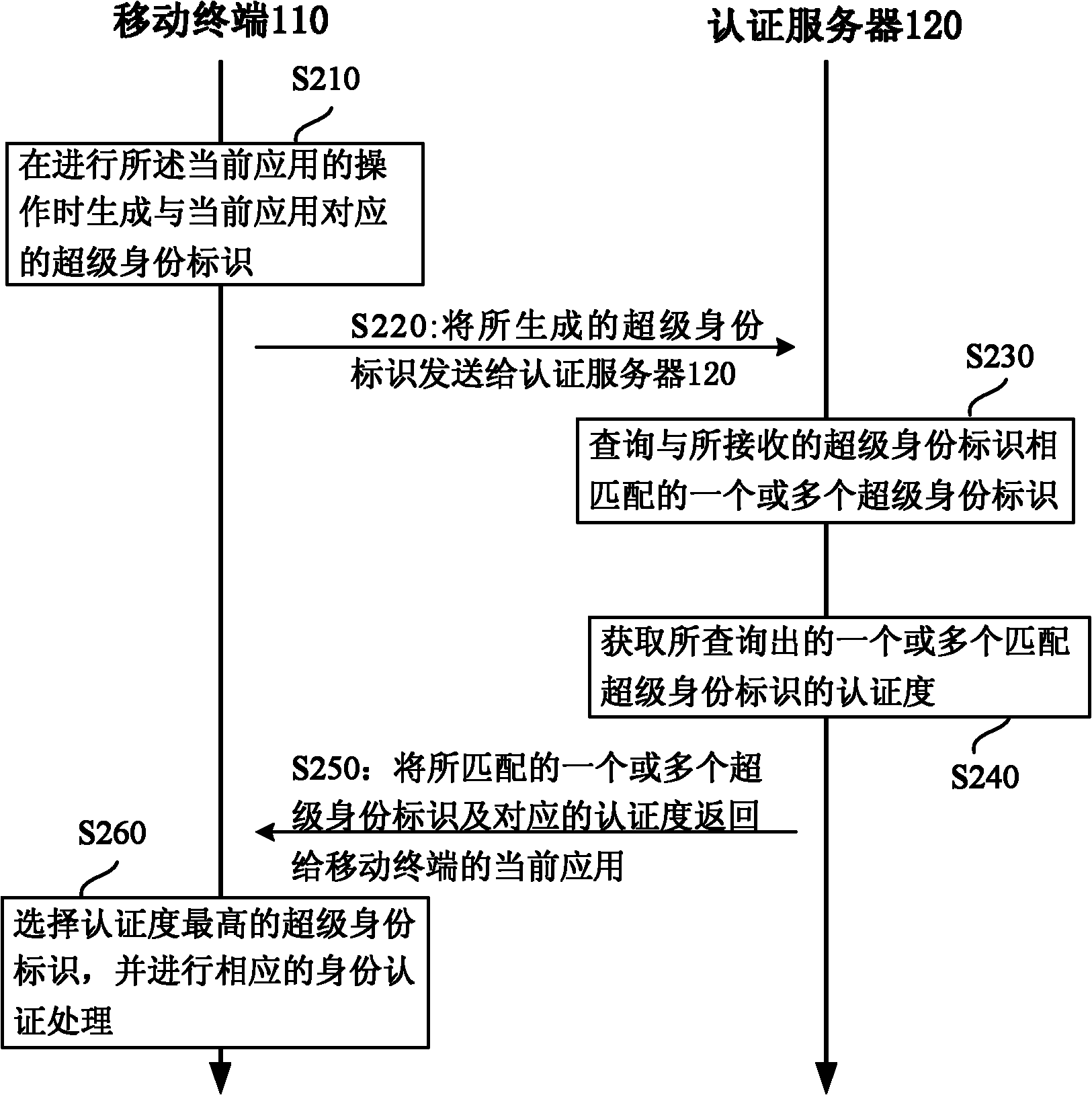
ActiveCN102186173AEnsure consistencyBalance security and convenienceTransmissionSecurity arrangementData libraryAuthentication server
The invention provides an identity authentication method carried out by an authentication server. The method comprises the following steps of: receiving a super identity identifier corresponding to the current application of a mobile terminal from the mobile terminal; inquiring one or more super identity identifiers matched with the received super identity identifier in a super identity identifier database of the authentication server, wherein the super identity identifier(s) corresponding to one or more applications and combinations of the super identity identifiers as well as authenticationdegrees corresponding to respective component elements in a generated super identity identifier are stored in the super identity identifier database; acquiring one or more inquired authentication degrees matched with the super identity identifiers; and returning the one or more matched super identity identifiers and corresponding authentication degrees to the current application of the mobile terminal for identity authentication processing. When the method is used, the identities of users can be found as much as possible when the users use the mobile terminal; thus, repeated register can be reduced, and the consistency of user accounts can be ensured.
Owner:ALIBABA (CHINA) CO LTD
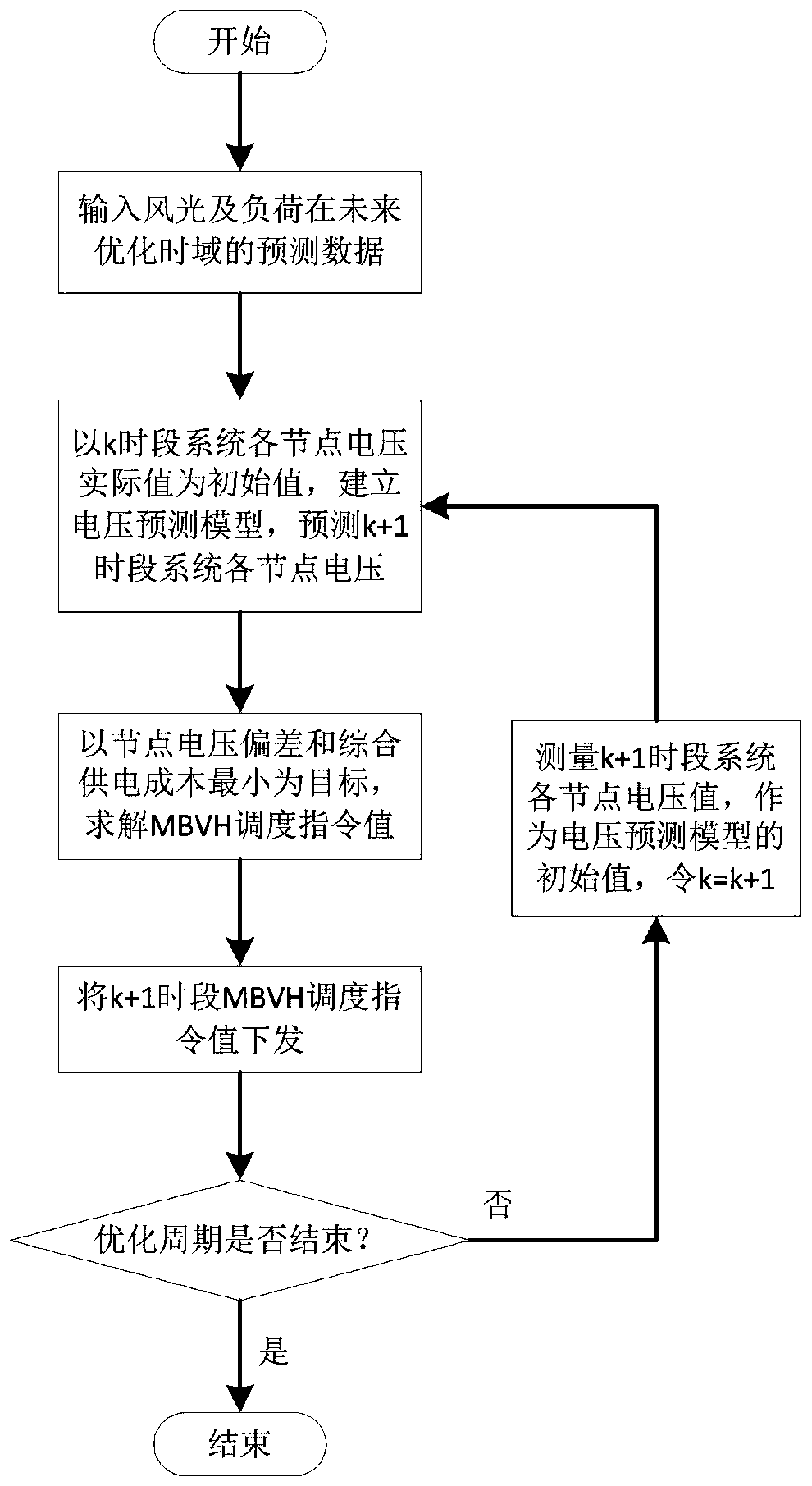
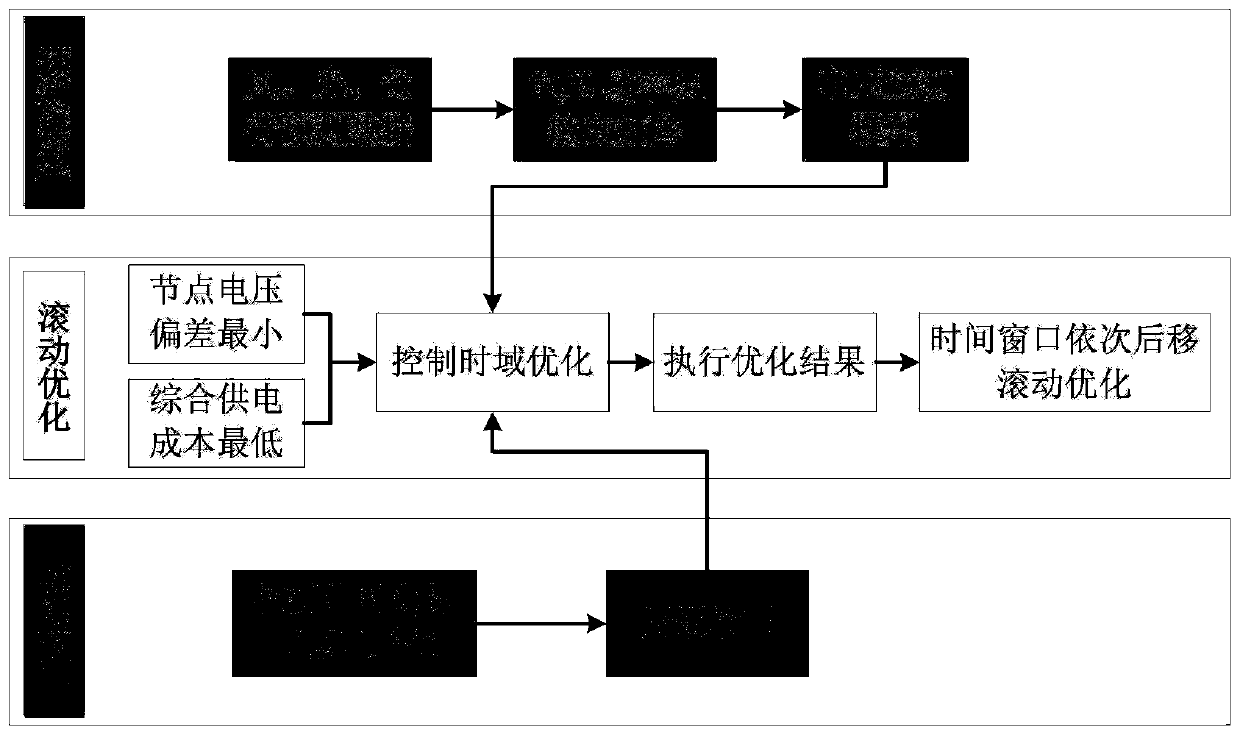
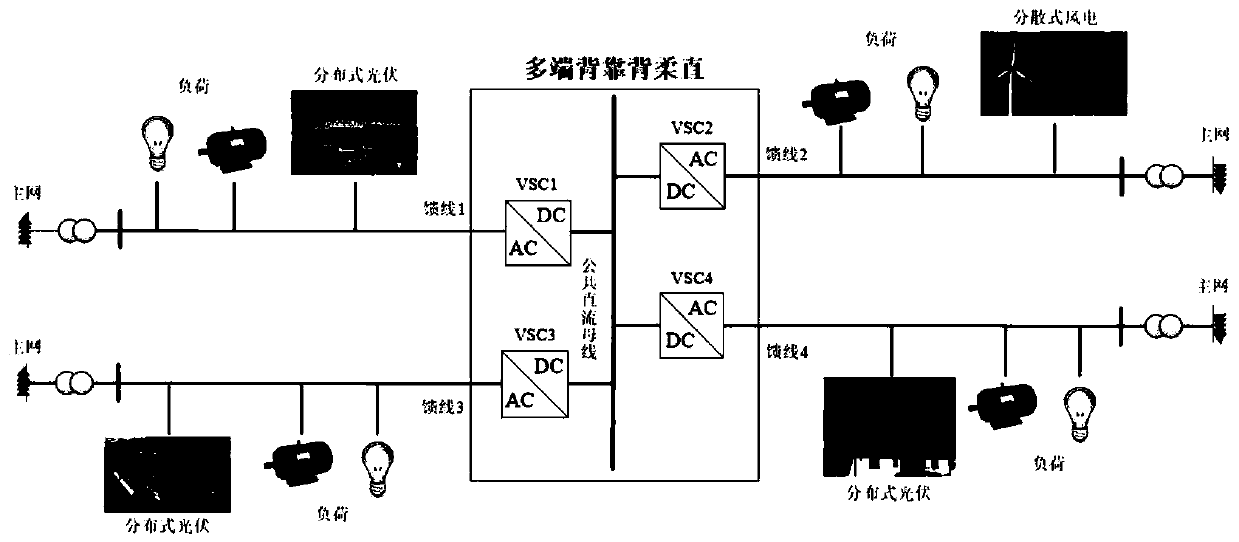
Dynamic optimization scheduling method and system for flexible interconnected distribution network
The invention discloses a dynamic optimization scheduling method and system for a flexible interconnected distribution network. A dynamic optimization scheduling method of a flexible interconnected distribution network based on model prediction control is provided for the uncertainty of renewable energy output and load demands by taking a flexible interconnected distribution network connected witheach feeder through a multi-terminal back-to-back VSC-HVDC. The method comprises the steps of: based on the renewable energy and load ultra-short term power prediction information, establishing a voltage prediction model through calculation of voltage sensitivity of each node, establishing a flexible distribution network optimization operation model to take the minimum of the deviation of a predicted voltage and a rated voltage and the integrated power supply cost by a target, and combining a method of adaptive dynamic weight and feedback correction to optimize and obtain a dispatching instruction value and perform issuing. The method can effectively solve the problem of voltage out-of-limit generated by random fluctuation of the distributed power supply output and load demands and effectively balances the economical efficiency and the safety of the operation of the flexible interconnected distribution network.
Owner:STATE GRID JIANGSU ELECTRIC POWER CO ELECTRIC POWER RES INST +4
Aggregation method and system supporting fault tolerance and resisting differential attacks in smart power grid
ActiveCN104580061ABalance securityDistribute computing loadCryptographic attack countermeasuresFault toleranceCiphertext
The invention discloses an aggregation method and system supporting fault tolerance and resisting differential attacks in a smart power grid. According to the method, a smart electric meter is used for recording and reporting the power consumption of users in real time; a control center is responsible for collecting, processing and analyzing real-time power consumption data of the users; a gateway is responsible for data aggregation; a trusted center is responsible for the whole system. Main modules include a system initialization module, a data aggregation request module, a data aggregation request relay module, a user data reporting module, a security data aggregation module and an aggregated data recovery module. A security data aggregation system is realized and is used for protecting power consumption privacy of the users, preventing a vicious external attacker and an electric energy control center from abusing authority and effectively resisting malicious software instrumentation and attacks; since an auxiliary ciphertext is introduced, physical and communication fault tolerance is achieved, and it is guaranteed that the power consumption data of the users can still automatically aggregate and be reported successfully on the condition that a part of the power consumption data fails to be reported.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
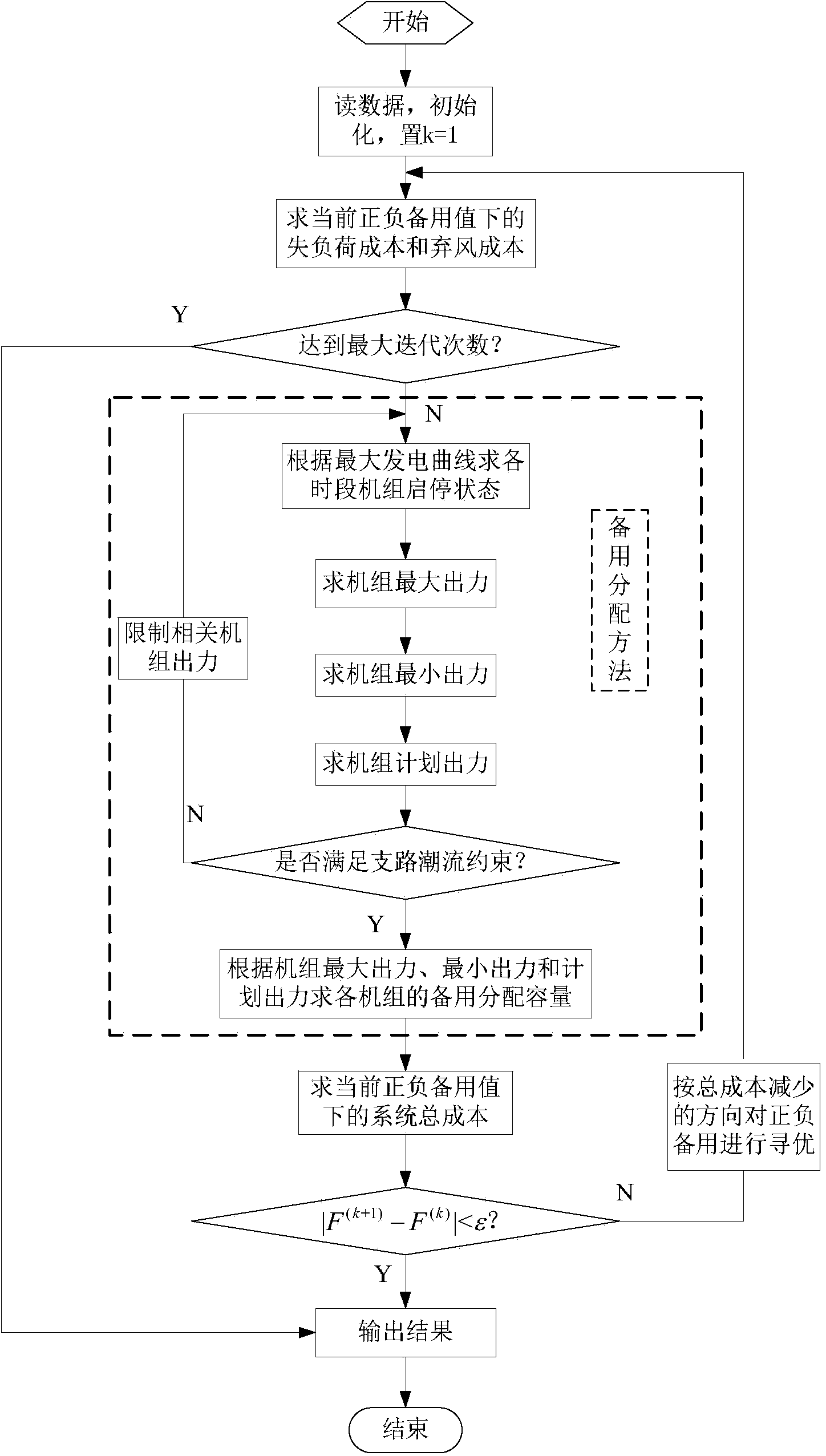
Standby configuration optimization method adopting wind power system unit
InactiveCN103956773AGood plus and minus spin spareBalance securitySingle network parallel feeding arrangementsWind energy generationConfiguration optimizationElectric power system
The invention provides a standby configuration optimization method adopting a wind power system unit. The standby configuration optimization method provides a method for computing two risk costs including outage cost and wind curtailment cost under certain forward-reverse rotation spare capacity by utilizing an integral of a wind power and load joint probability density function, an optimum allocation method for allocating the total system forward-reverse rotation spare capacity to different coal consumption units, and a decision-making method comprehensively considering the risk costs and power generating cost, the total system forward-reverse rotation spare capacity when the power system performs most economical operation and power generating plans and spare allocation capacities of the units. The standby configuration optimization method is suitable for the power system accessed to a wind power plant, can make a decision on the total system forward-reverse rotation spare capacity giving consideration to the economical efficiency and safety and contribution plans and optimum forward-reverse rotation spare capacities of the units, meanwhile unit climbing constraint and network security constraint are considered for spare capacity allocation of the units, and completely available standby application provided by the units is ensured.
Owner:HOHAI UNIV
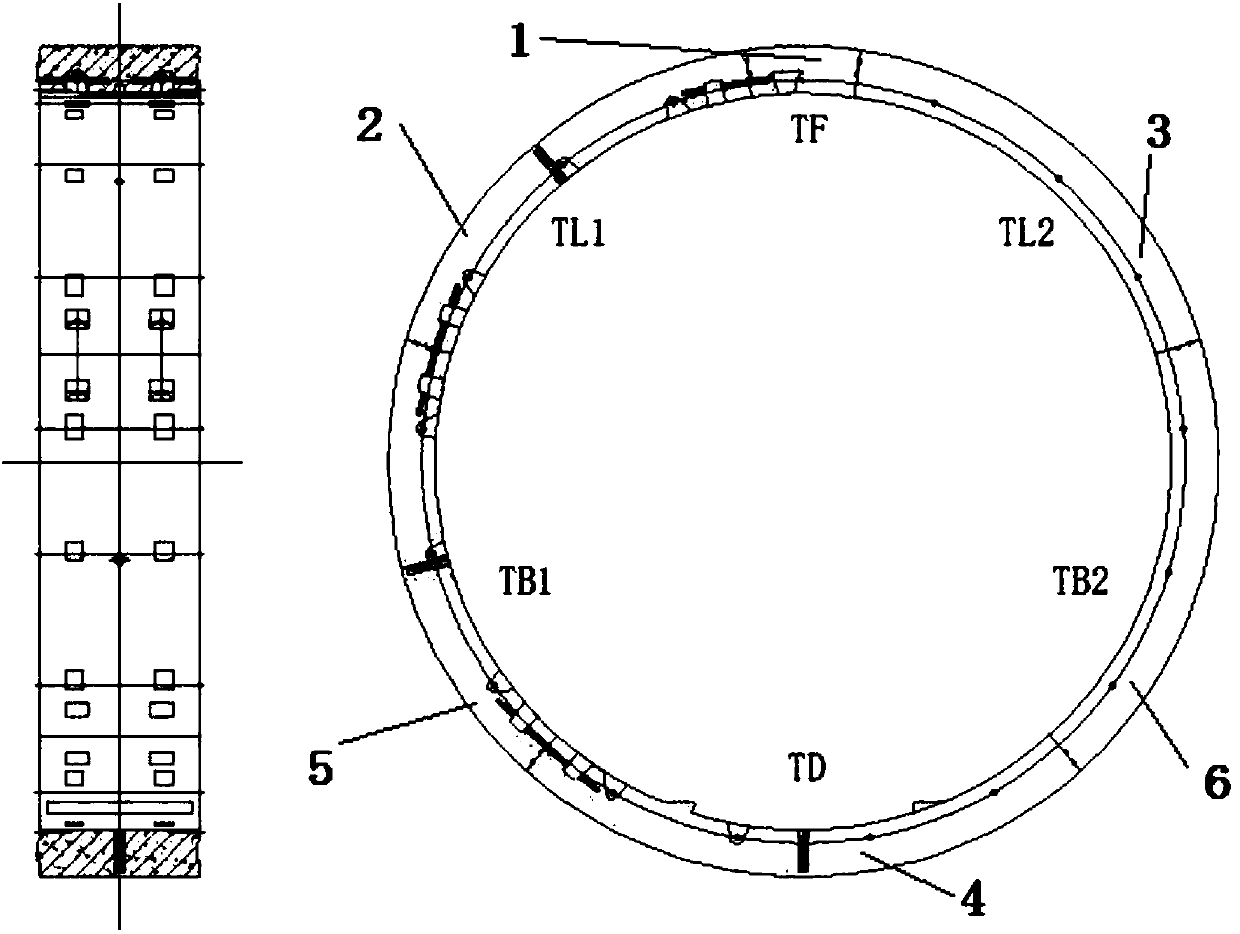
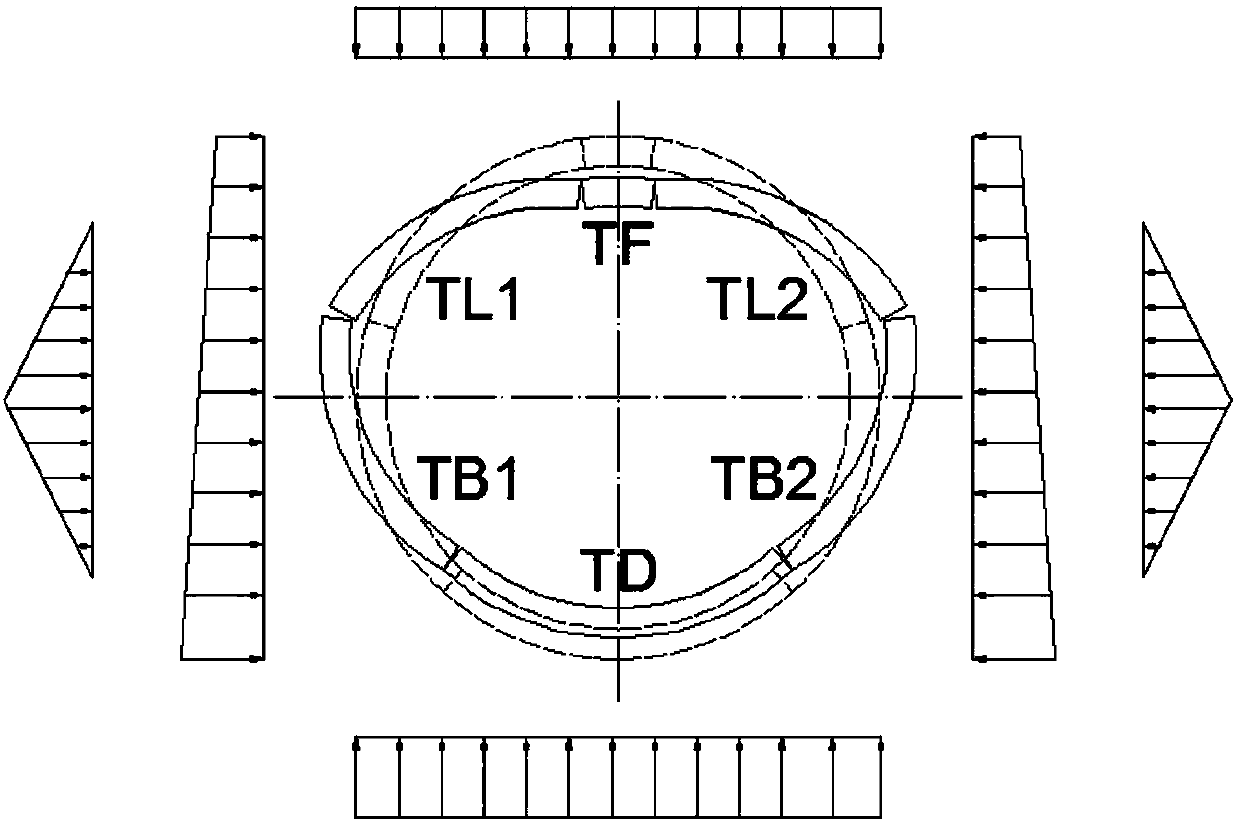
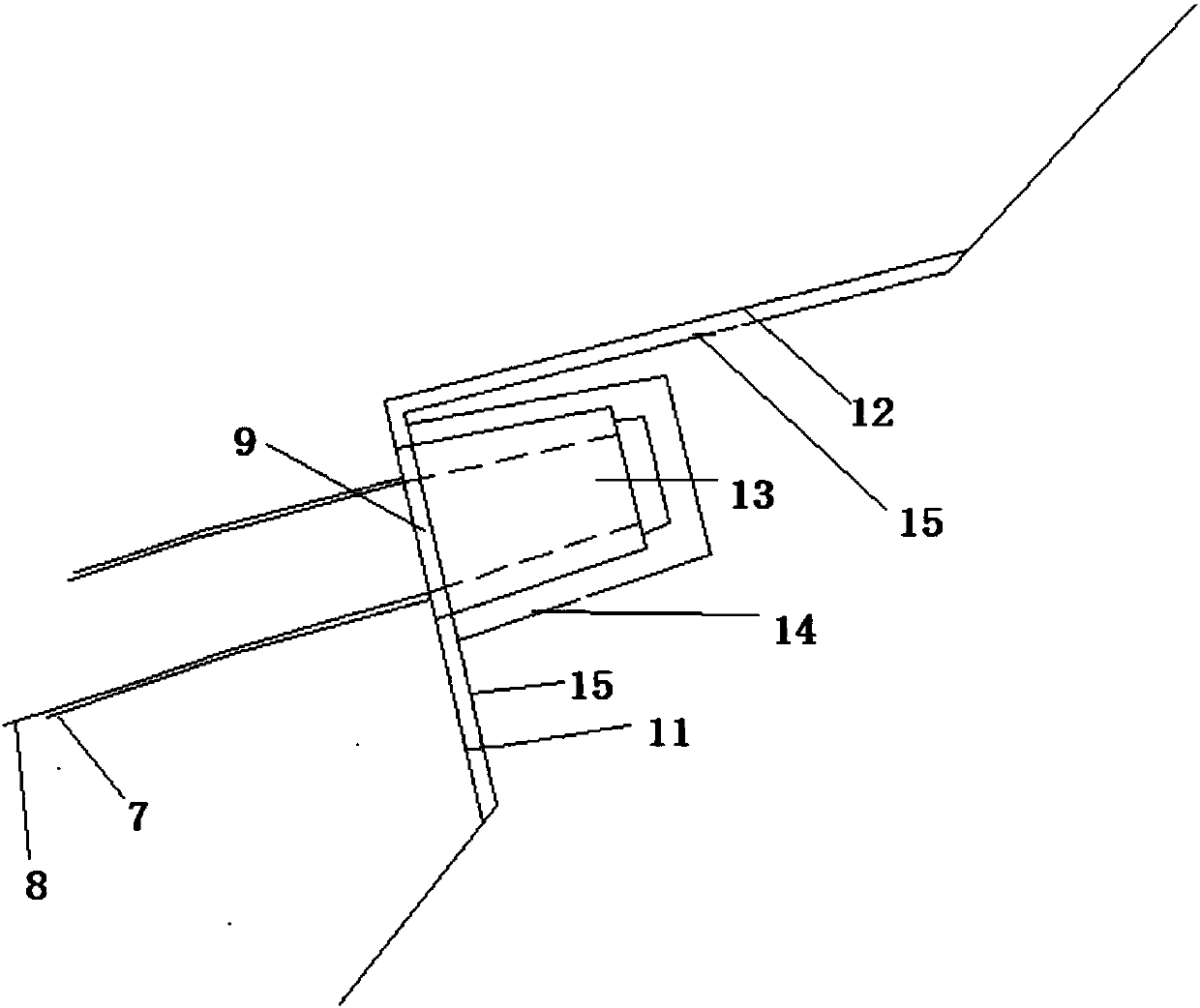
Shield tunnel lining segment and reinforcing method thereof
ActiveCN107620598AImprove integrityIncrease stiffnessUnderground chambersTunnel liningStress conditionsEngineering
The invention discloses a shield tunnel lining segment and further discloses a reinforcing method of the shield tunnel lining segment. An existing structure comprises a top-sealing block, a first adjoining block, a second adjoining block, a bottom-sealing block, a first standard block and a second standard block, wherein the first adjoining block and the second adjoining block are located at the two ends of the top-sealing block, and the first standard block and the second standard block are located at the two ends of the bottom-sealing block. The first adjoining block is connected with the first standard block, and the second adjoining block is connected with the second standard block. Steel strand hole passages are formed in the existing first adjoining block and first standard block, steel strands are arranged in the steel strand hole passages, and steel strand outlets are formed in the inner sides of the first adjoining block and the first standard block. The second adjoining blockand the second standard block are also treated in the same way. The reinforcing method comprises the steps that (1) the lining segment is prefabricated according to the borne load of a tunnel structure; (2) the stress condition of the lining segment is judged, and the reinforcing method of the lining segment is determined; and (3) the lining segment is reinforced. According to the shield tunnel lining segment and the reinforcing method, the overall rigidity and the deformation harmony of the tunnel structure are improved, and tunnel operation safety can be ensured.
Owner:TONGJI UNIV
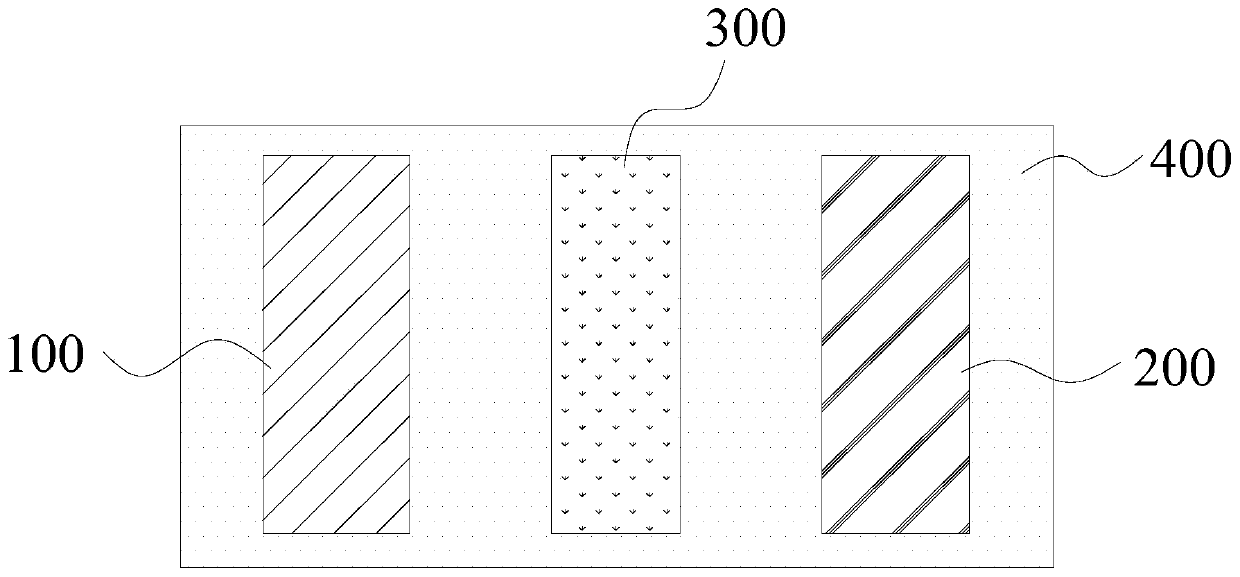
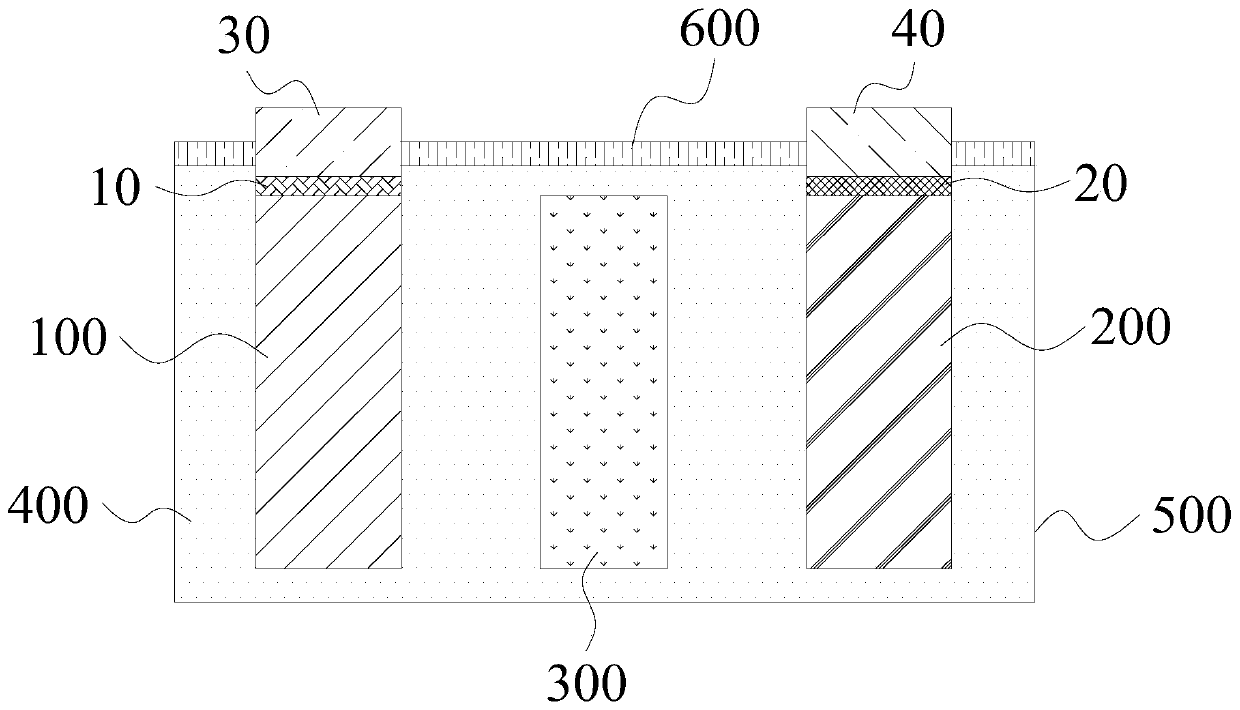
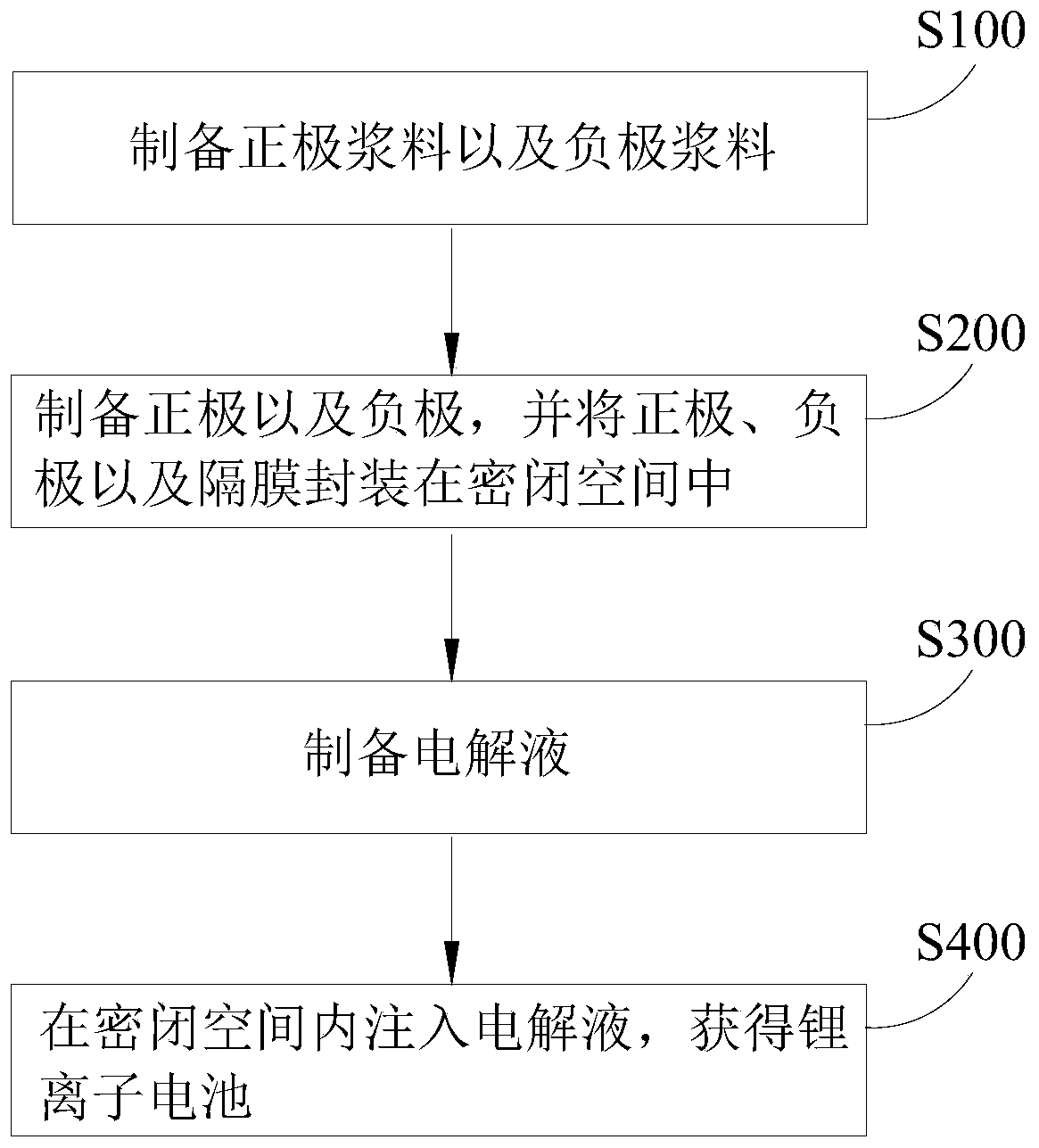
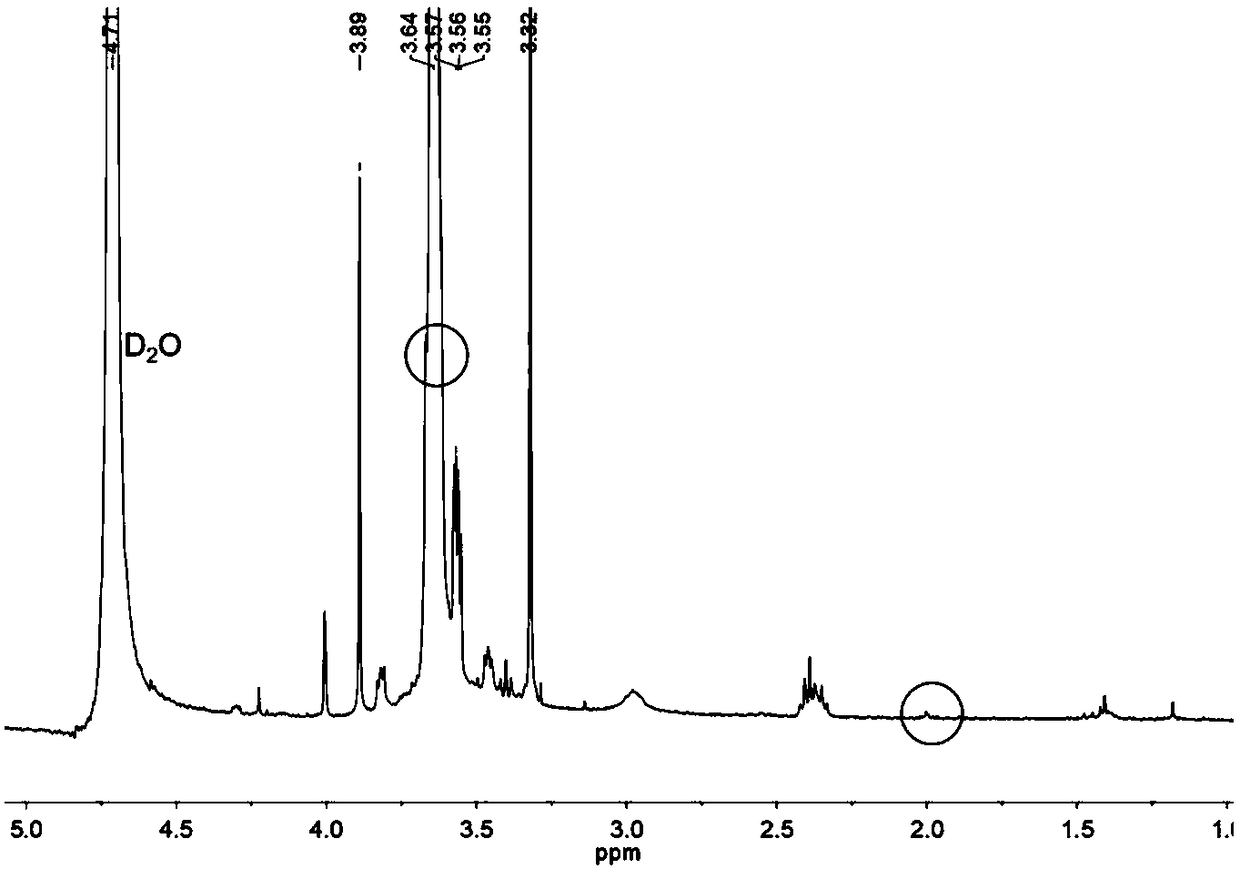
Lithium ion battery and preparation method
ActiveCN109713298ALow costExtended service lifeCell electrodesFinal product manufactureDifluorophosphateAluminium-ion battery
The invention provides a lithium ion battery and a preparation method. The lithium ion battery includes a positive electrode, a negative electrode, a diaphragm, and an electrolyte. The positive electrode and the negative electrode are separated by the diaphragm; the positive electrode, the negative electrode and the diaphragm are encapsulated in an enclosed space; the electrolyte is filled in theenclosed space; the positive electrode includes a positive active material, the positive active material includes a nickel-cobalt-manganese ternary material, and the percentage of the amount of a substance of nickel in the nickel-cobalt-manganese ternary material is 50-60%; the negative electrode includes a negative active material, the negative active material includes graphite, and the degree ofgraphitization of the graphite is 91-94%, and an OI value is 6-7; and the electrolyte includes a lithium salt, a solvent and an additive, wherein the lithium salt includes lithium hexafluorophosphateand lithium bis(fluorosulfonyl)imide, the solvent includes ethylene carbonate, ethyl methyl carbonate, dimethyl carbonate and propyl propionate, and the additive includes lithium difluorophosphate, lithium bis(oxalate)borate, tris(trimethylsiloxy)boron, vinylene carbonate, and succinonitrile. The lithium ion battery has the characteristics of high safety, low cost, long service life and excellentusage performance.
Owner:SVOLT ENERGY TECHNOLOGY CO LTD
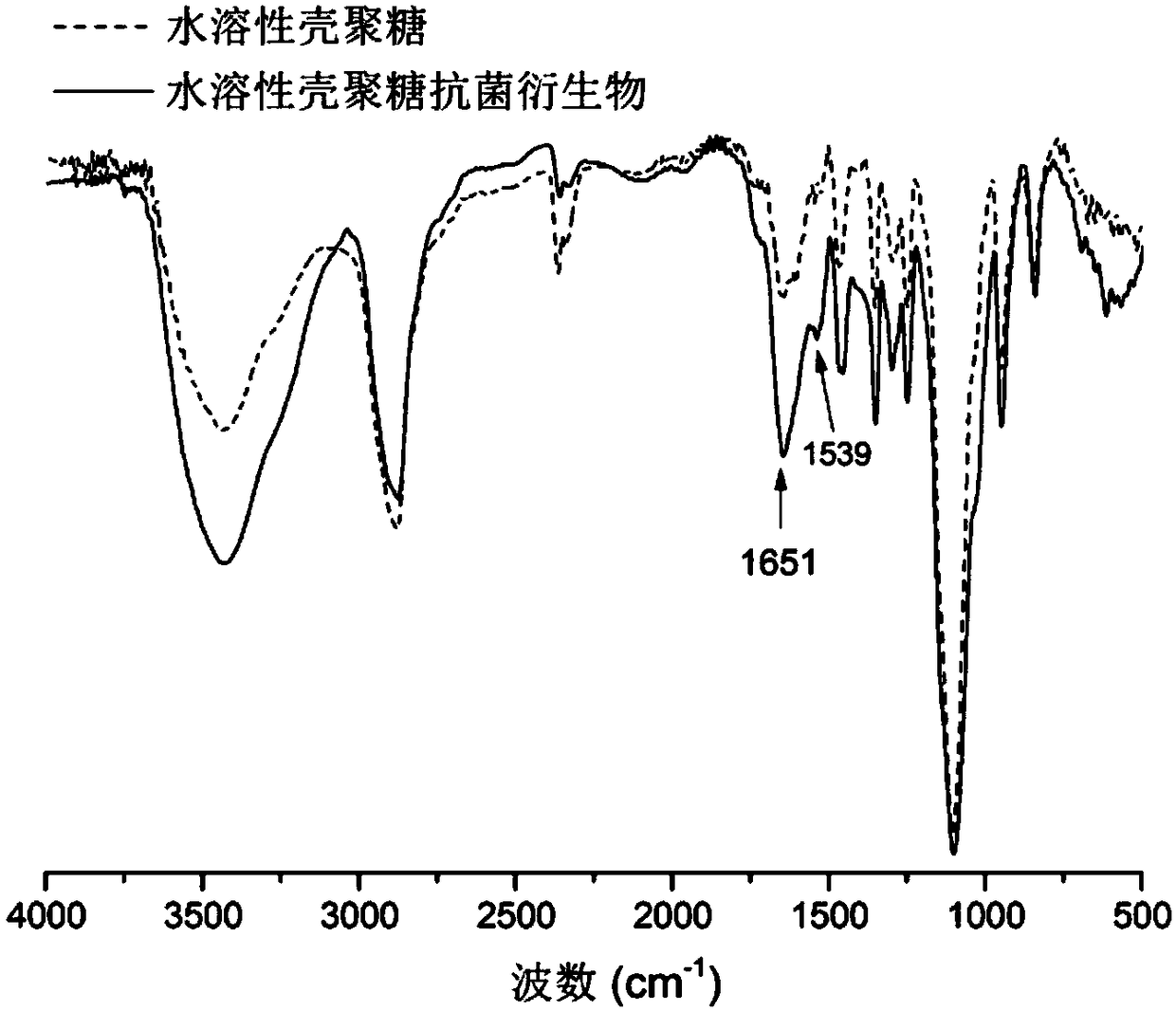
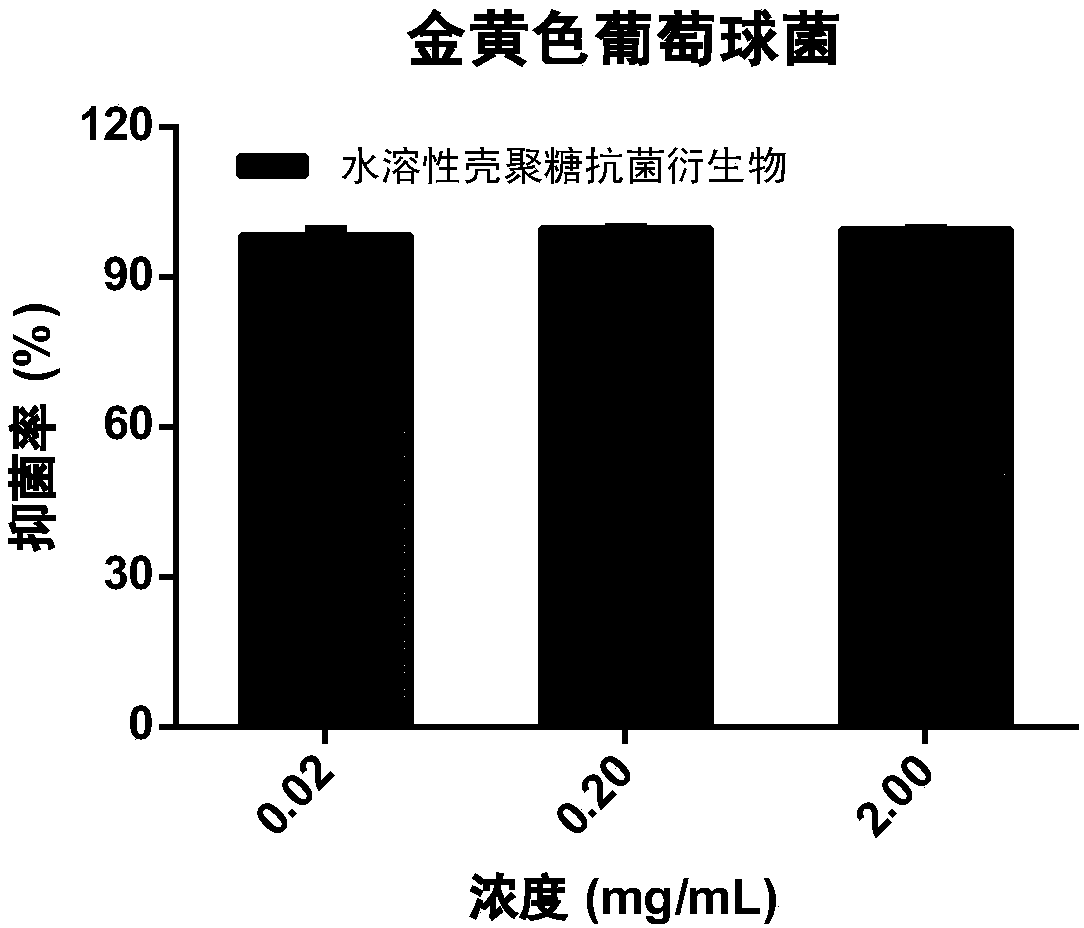
Water-soluble chitosan antibacterial derivative and preparation method thereof
ActiveCN109485747ABalanced antimicrobial propertiesBalance securityBiocideFungicidesSolubilityThiourea
The invention discloses a water-soluble chitosan antibacterial derivative and a preparation method thereof. The water-soluble chitosan antibacterial derivative comprises a chitosan framework and a bifunctional group for modifying amino on the chitosan framework, wherein the bifunctional group comprises guanidino and carbonyl methoxy polyethylene glycol. The side chain of chitosan is modified withguanidino and short-chain polyethylene glycol, and the chitosan achieves good antibacterial property and higher biological safety. According to the preparation method, firstly, the chitosan reacts with the carbonyl methoxy polyethylene glycol, water solubility of the chitosan is sufficiently improved, and biological safety is greatly improved; secondly, the chitosan reacts with thiourea trioxide,participation of the amino in subsequent reaction is effectively avoided if the guanidino is grafted in the first step, rich positive charge of the guanidino is effectively retained, and the positivecharge density of the water-soluble chitosan antibacterial derivative is ensured, so that the antibacterial effect of the water-soluble chitosan antibacterial derivative is better.
Owner:TECHNICAL INST OF PHYSICS & CHEMISTRY - CHINESE ACAD OF SCI +1
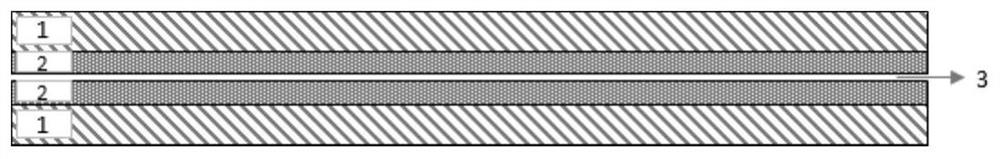
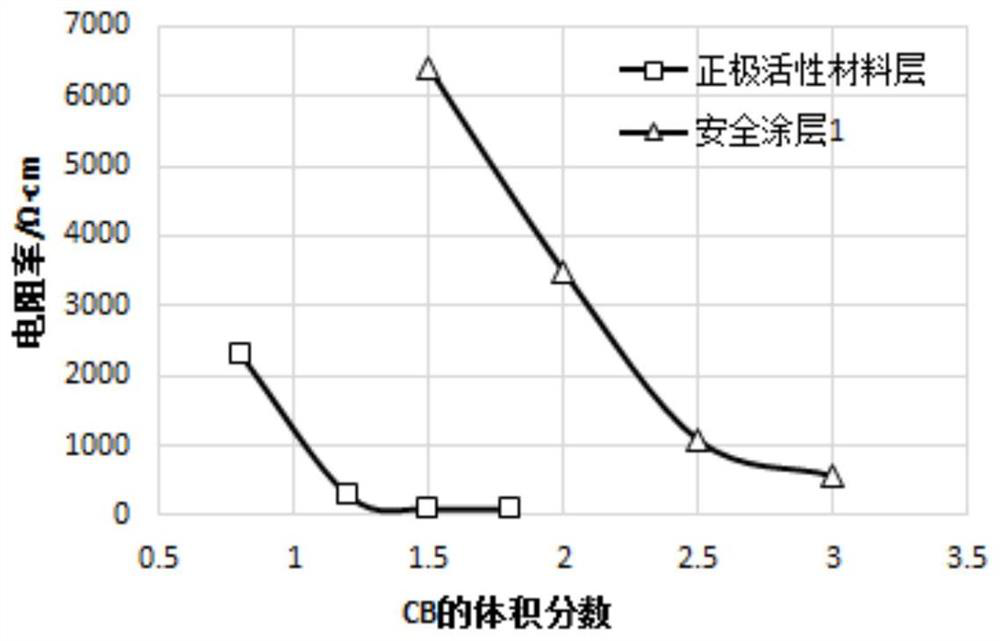
Positive plate and lithium ion battery containing positive plate
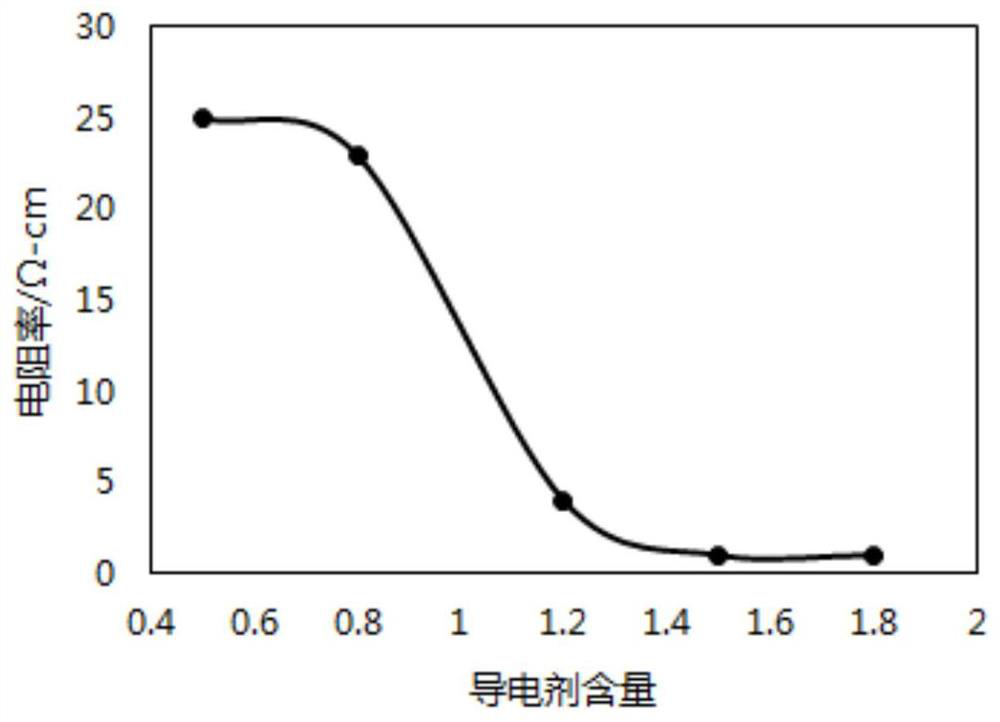
ActiveCN111900392AIncrease energy densityIncreased seepage thresholdPositive electrodesSecondary cells servicing/maintenanceHigh energyPhysical chemistry
The invention provides a positive plate and a lithium ion battery containing the positive plate. The safety of the battery cell is improved by controlling the seepage thresholds of the safety coatingcoating the surface of the positive current collector and the positive active material layer, and meanwhile, relatively high energy density and excellent electrical properties are ensured. Particularly, the seepage threshold value of the positive active material layer is small, and the addition amount of the conductive agent is small, so that a good electron path can be ensured, and the energy density of the positive plate can be increased.
Owner:ZHUHAI COSMX BATTERY CO LTD
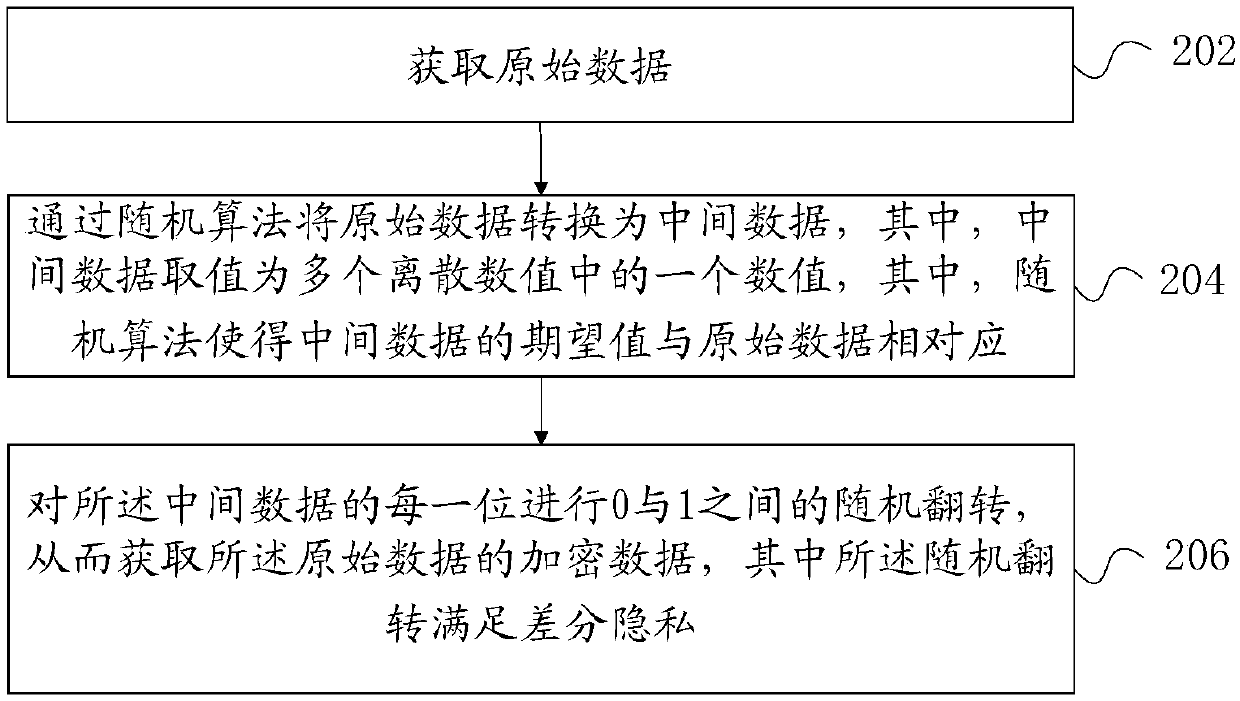
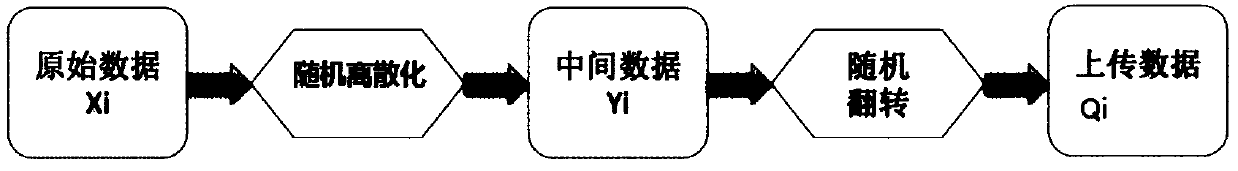
Data encryption, data analysis method and apparatus
ActiveCN109063502ABalancing Accuracy and SecurityBalance securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesNumeric ValueAnalysis method
Embodiments of the present specification provide a data encryption method and apparatus, and a data analysis method and apparatus. Converting the raw data into intermediate data by a stochastic algorithm, wherein the intermediate data takes a value as one of a plurality of discrete values, wherein the stochastic algorithm causes an expected value of the intermediate data to correspond to the raw data, wherein the plurality of discrete values are binary values having the same number of bits; And performing a random flip between 0 and 1 on each bit of the intermediate data to obtain encrypted data of the original data, wherein the random flip satisfies differential privacy.
Owner:ADVANCED NEW TECH CO LTD
Steering assistance device and steering assistance method
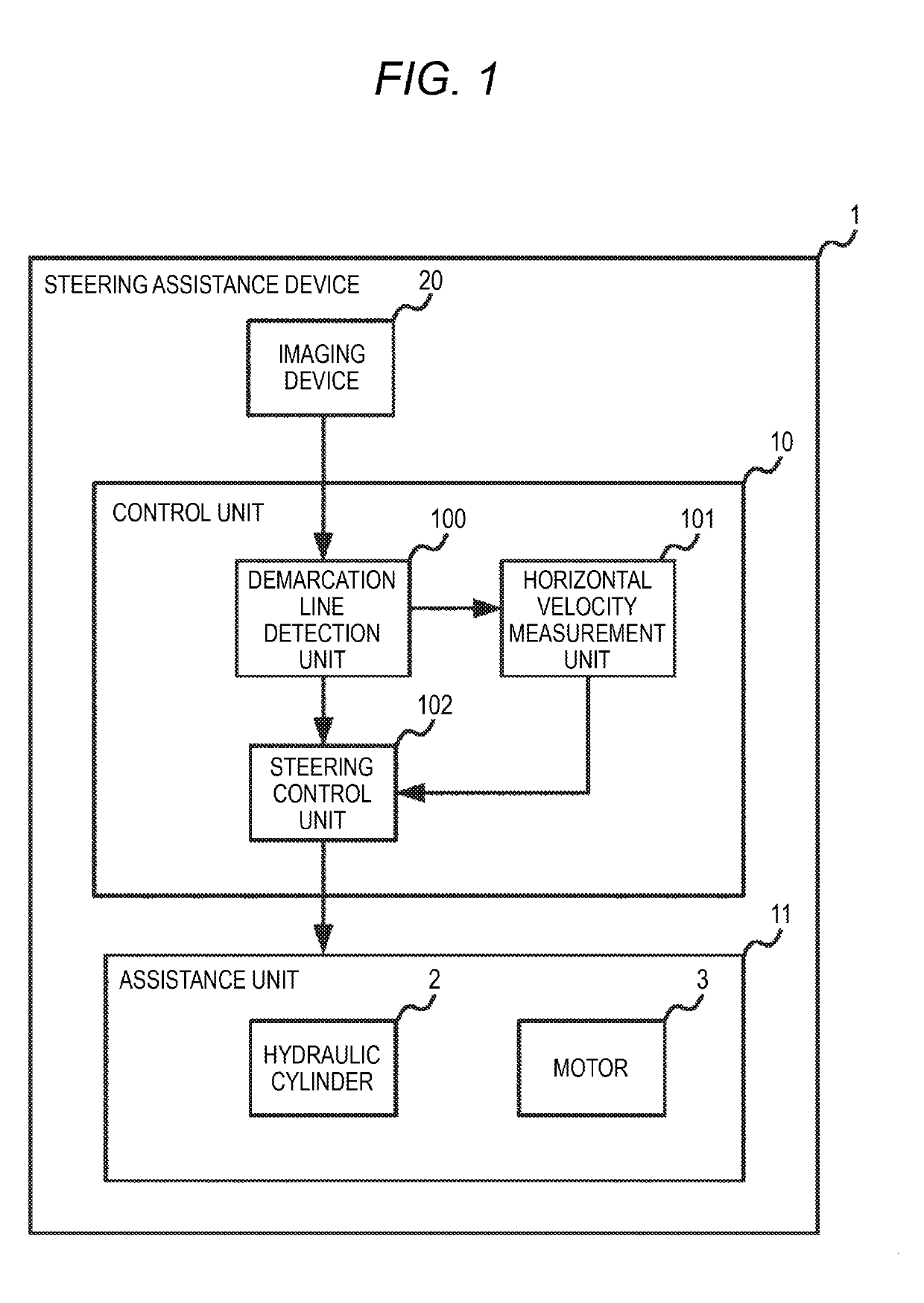
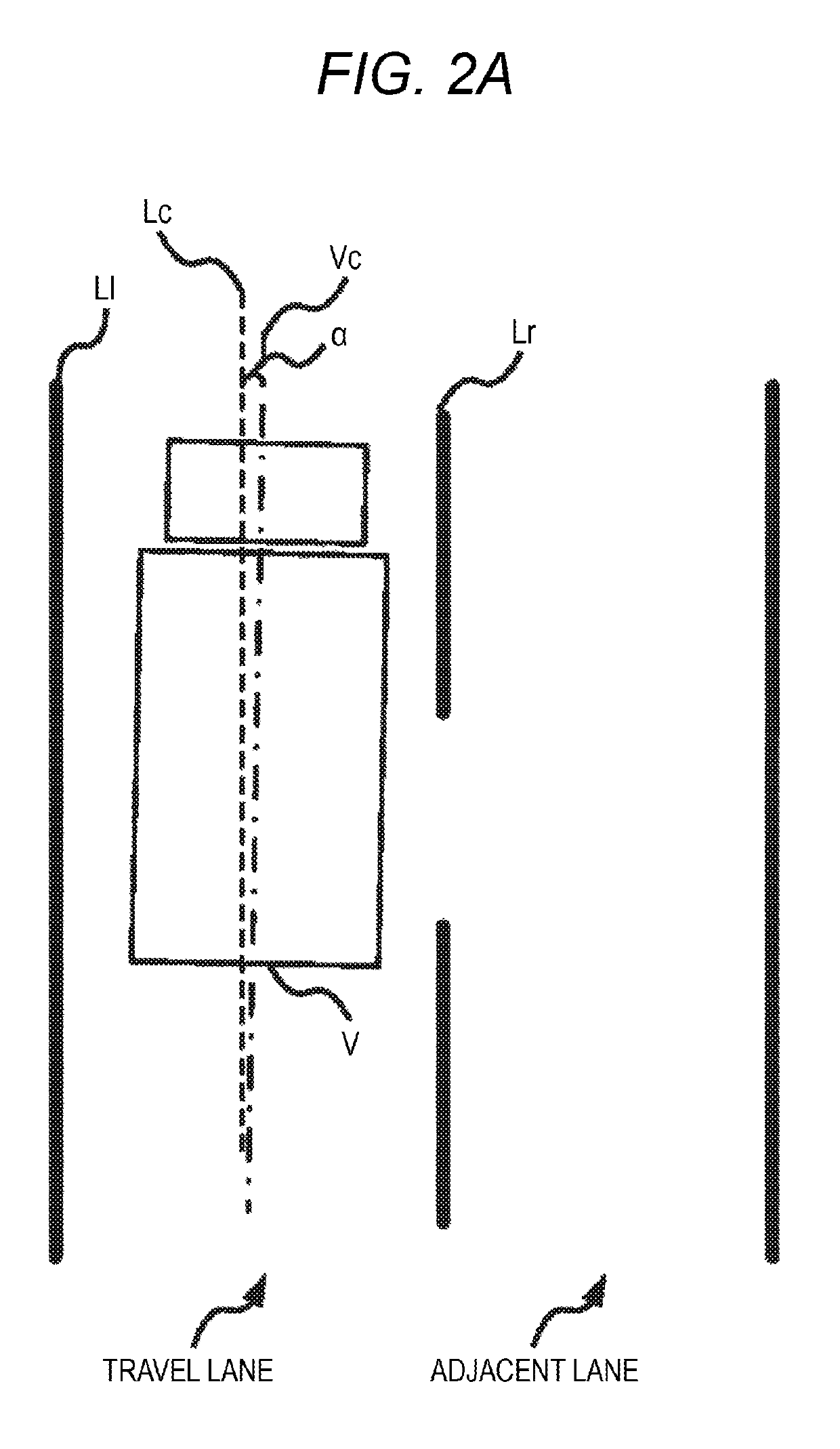
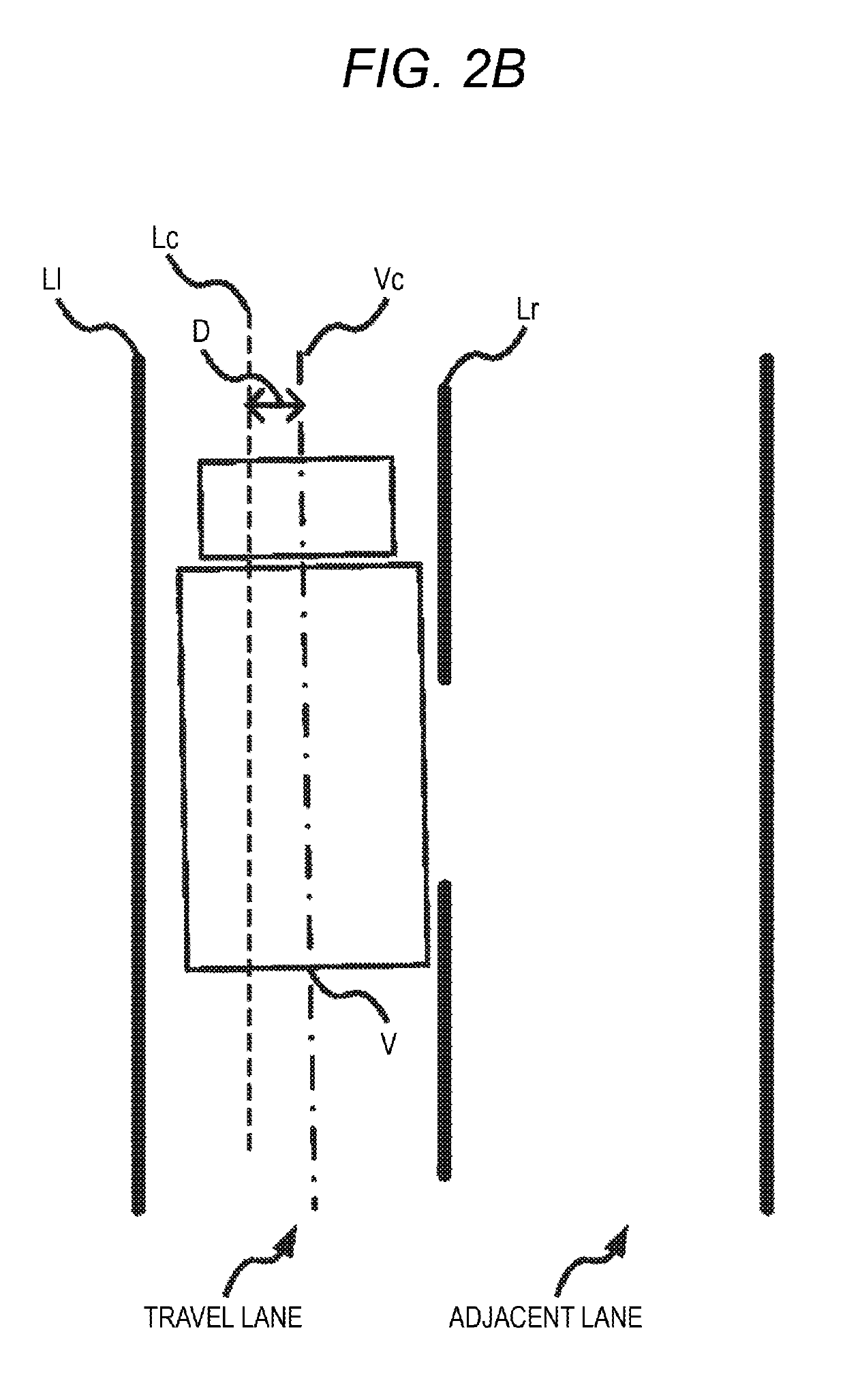
ActiveUS20190168752A1Improve securityInhibit deteriorationSteering linkagesAutomatic steering controlEngineeringVelocity measurement
Provided is a steering assistance device, and a demarcation line detection unit 100 detects left and right lane demarcation lines for a lane in which a vehicle is travels. A horizontal velocity measurement unit 101 calculates the horizontal velocity, which is a velocity component of the vehicle in a direction perpendicular to the lane. An assistance unit 11 performs steering assistance for the vehicle so that the vehicle travels parallel to the left and right lane demarcation lines. In a case where the horizontal velocity equal to or greater than a prescribed velocity and the center of the vehicle is separated from the center between the left and right lane demarcation lines by equal to or greater than a prescribed distance, a steering control unit 102 starts the steering assistance of the vehicle by the assistance unit 11.
Owner:ISUZU MOTORS LTD
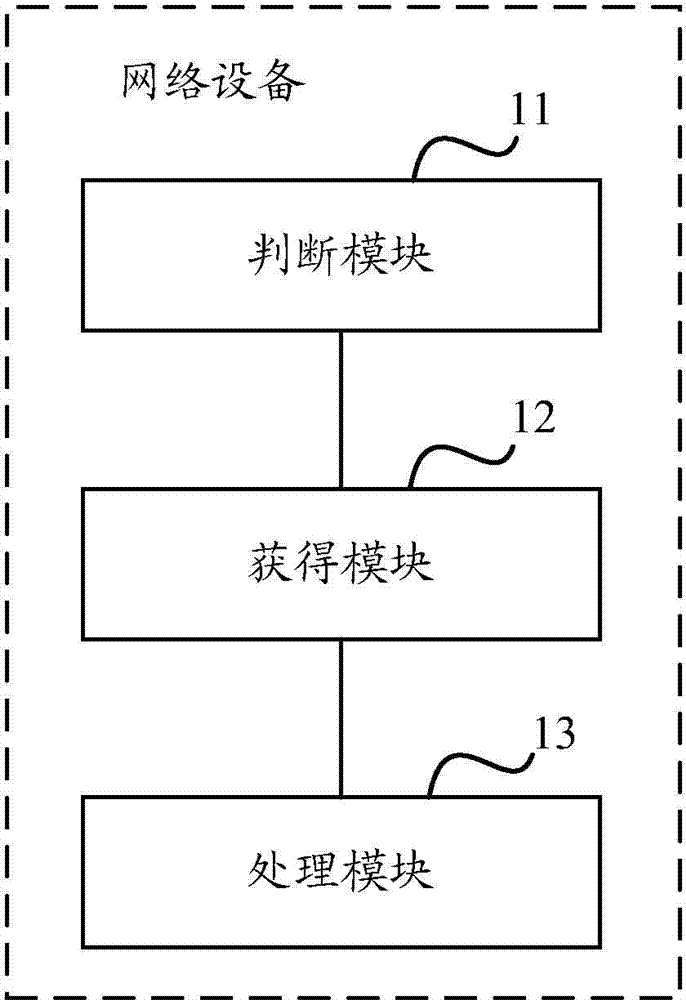
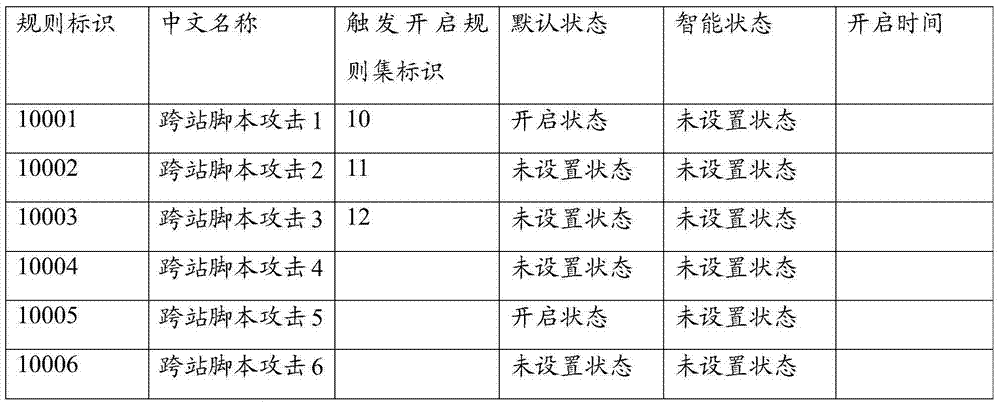
Attack detection rule opening method, and equipment
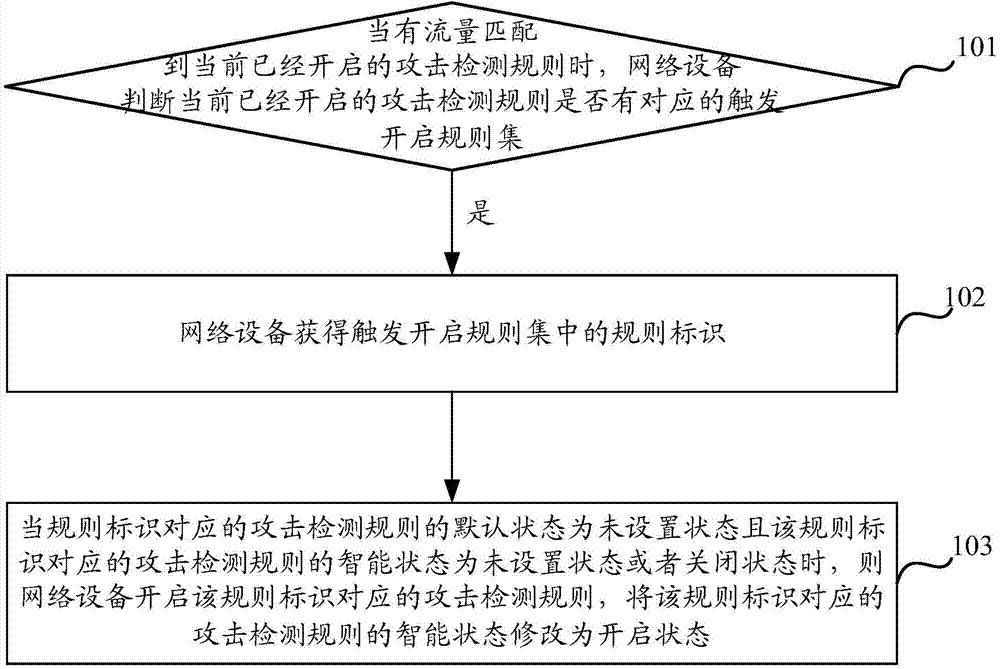
ActiveCN104852909AReal-time intelligent adjustment to open the numberIntelligent adjustment to open the numberTransmissionAlgorithmComputer science
The invention discloses an attack detection rule opening method, and equipment. The method includes the steps that network equipment determines whether a current opened attack detection rule has a corresponding trigger opening rule set when flows are made to match the current opened attack detection rule; the network equipment obtains a rule identification in the trigger opening rule set if the current opened attack detection rule has a corresponding trigger opening rule set; and when the default state of the attack detection rule corresponding to the rule identification is a non-set state and the intelligent state of the attack detection rule corresponding to the rule identification is a non-set state or a closed state, the network equipment starts the attack detection rule corresponding to the rule identification, and modifies the intelligent state of the attack detection rule corresponding to the rule identification to be an opening state. According to the embodiment of the invention, the cost and the security of the network equipment can be as balanced as possible.
Owner:NEW H3C TECH CO LTD
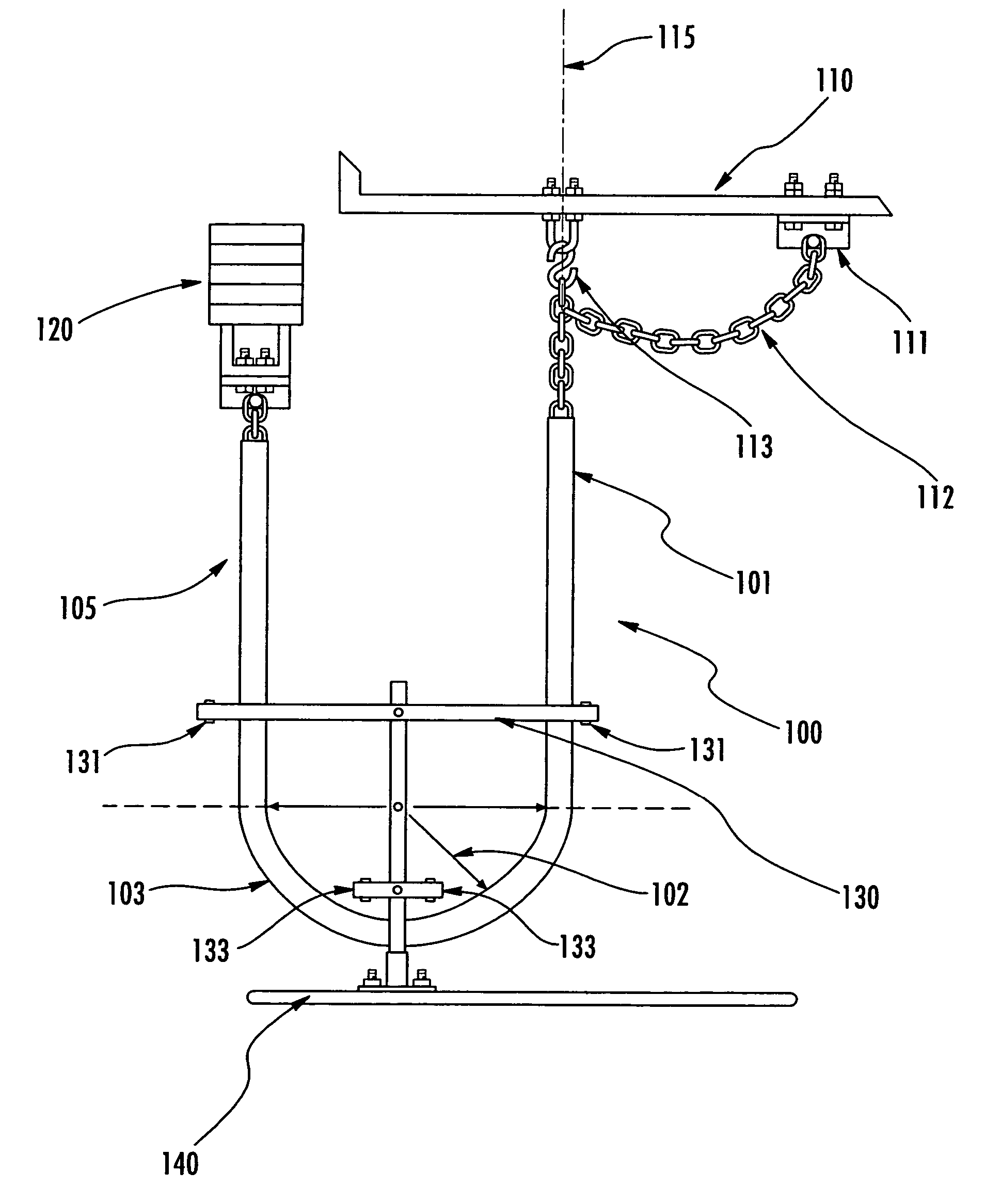
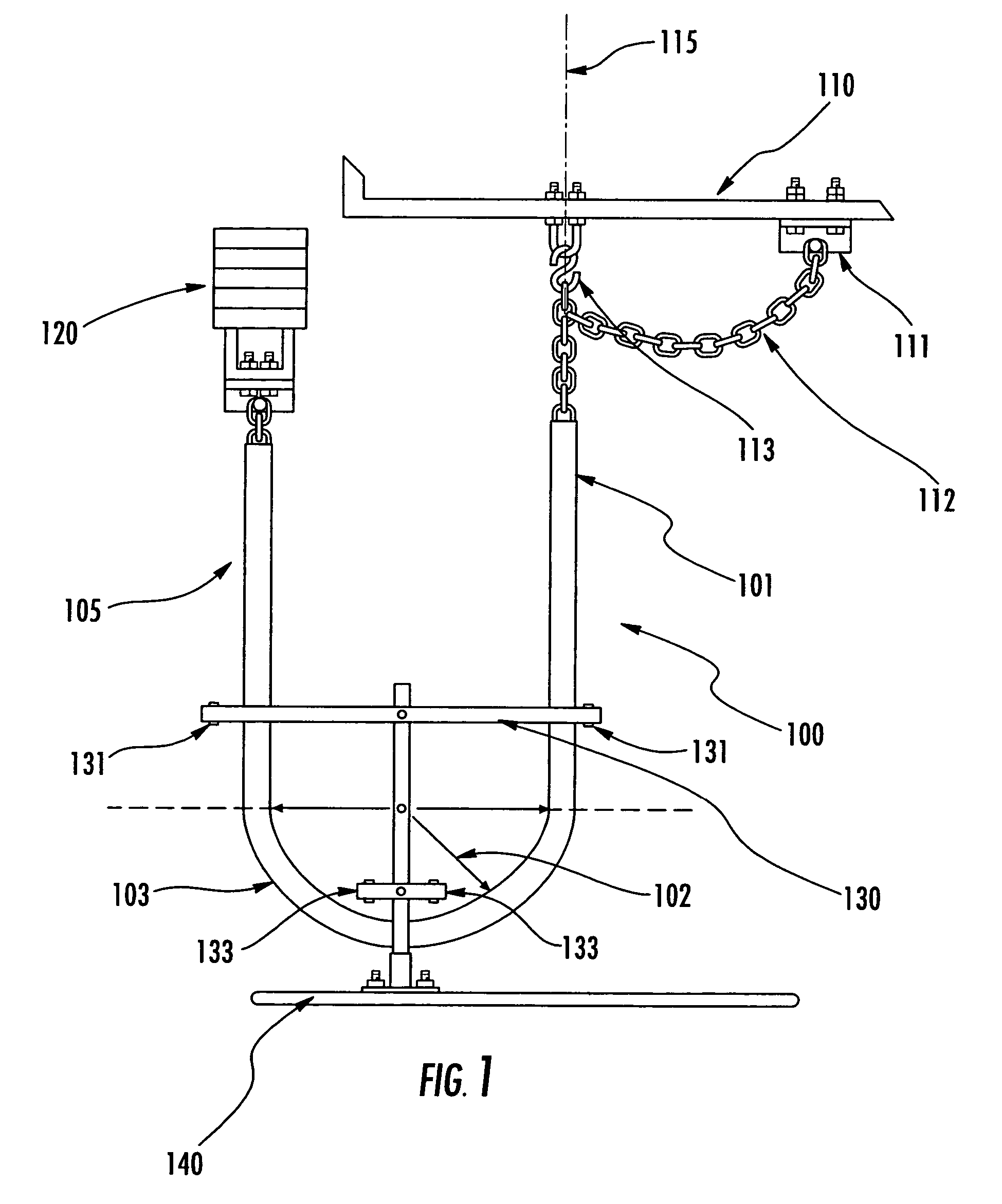
Elevator compensating cable having a selected loop radius and associated system and method
Owner:DRAKA ELEVATOR PRODS
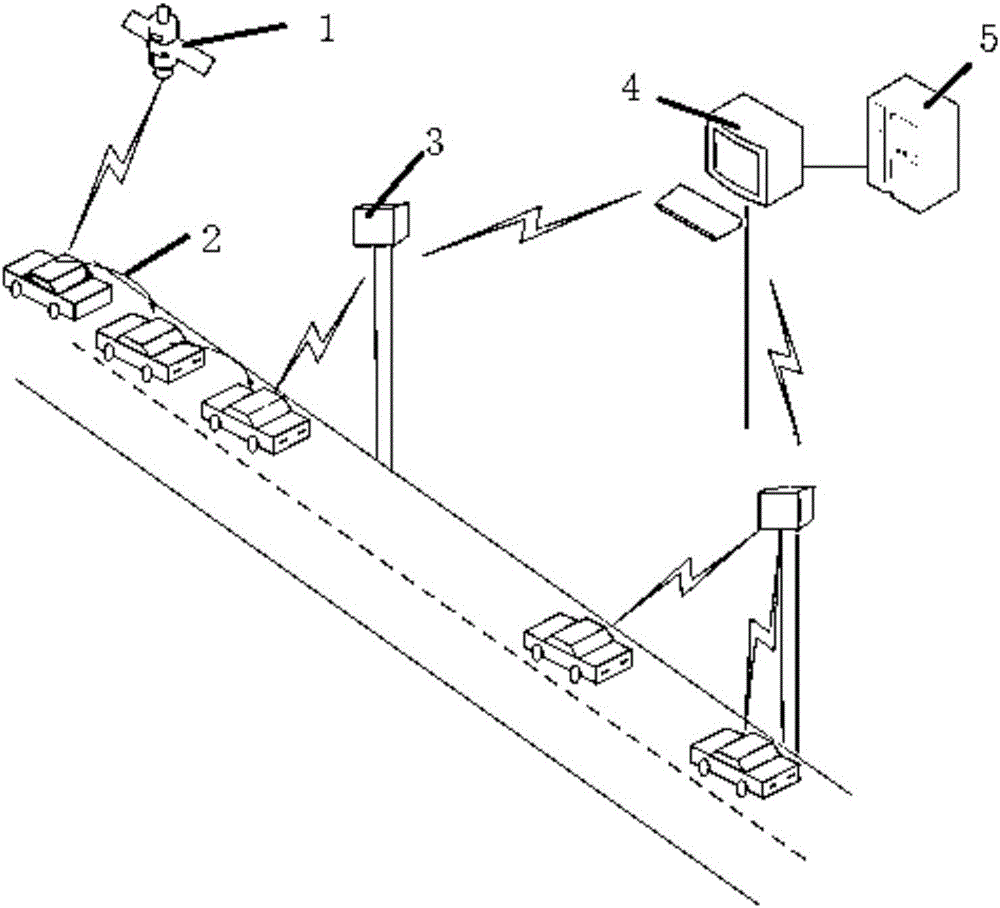
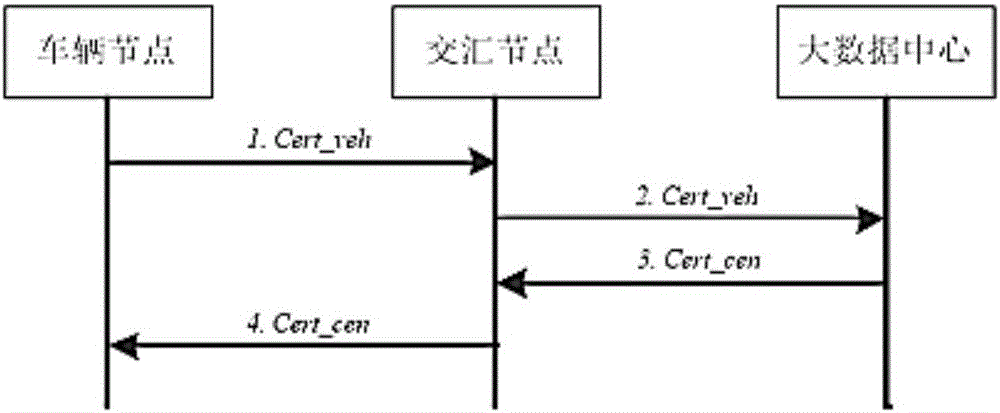
Large-scale IoV security data acquisition method
The invention provides a large-scale IoV security data acquisition method. The method includes an initial step that each vehicle node acquires the legal certificate of an electronic commerce certification and authentication mechanism, all of the vehicle nodes are registered in a big data center, the information exchange between the vehicle nodes and the big data center can be completed by the forwarding of the intersection nodes and the registration of the intersection nodes in the big data center is completed during the forwarding; a primary single sign-on step that the vehicle nodes and the intersection nodes are connected to the big data center according to different protocols; a secondary sign-on step that when the vehicle nodes are far away from the intersection nodes connected in the primary sign-on step, the vehicle nodes establish connection with nearby new intersection nodes; and a safe data acquisition step that the vehicle nodes and the big data center realize the acquisition and the transmission of business data and secret data via the intersection nodes. The safe method adopted in each step is an independent system; and meanwhile, the continuity of the steps is guaranteed, and the security of data acquisition is guaranteed as a whole.
Owner:SHANGHAI JIAO TONG UNIV +2
Anti-lightning evaluation method and device of high-voltage overhead power transmission line
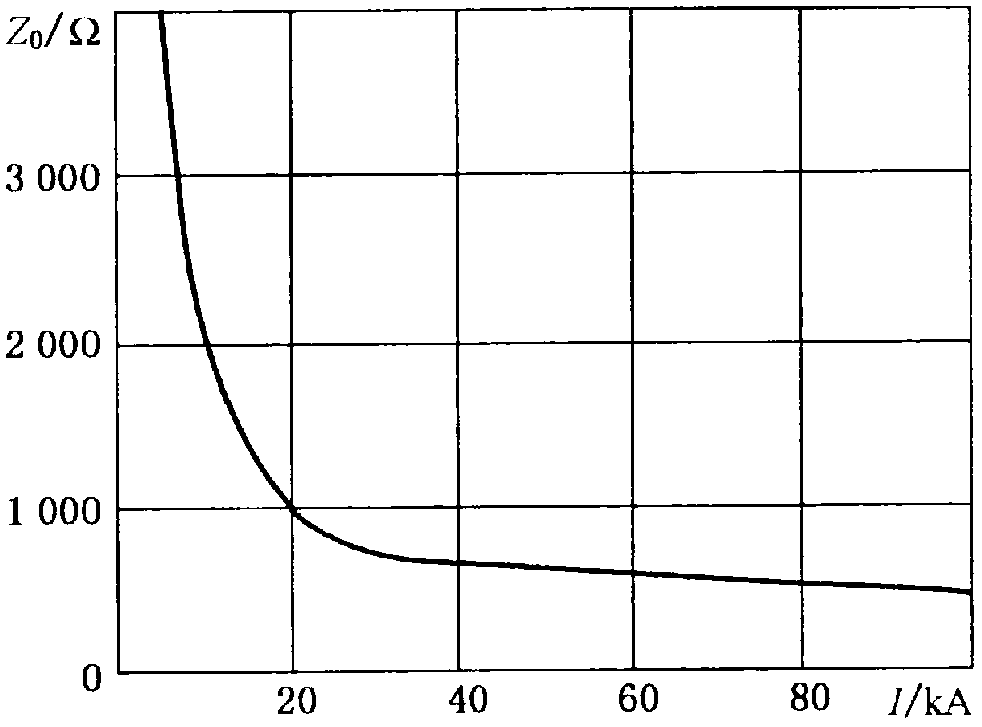
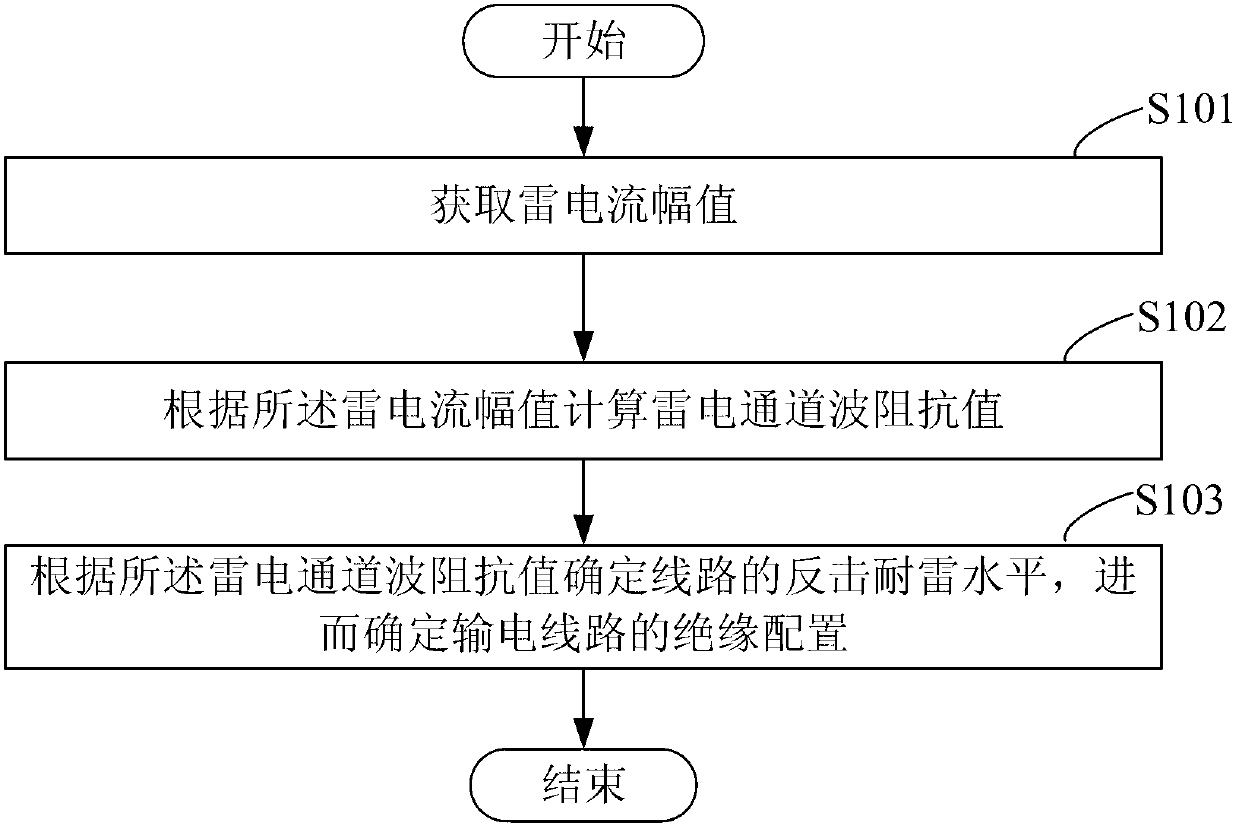
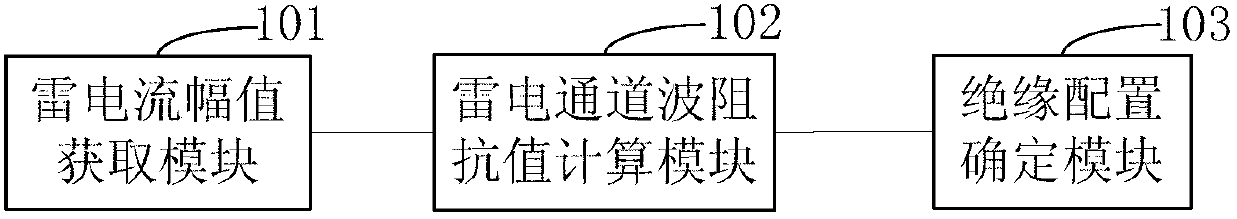
ActiveCN102707210AImprove securityImprove economyTesting dielectric strengthResistance/reactance/impedenceEngineeringHigh pressure
The invention provides an anti-lightning evaluation method and an anti-lightning device of a high-voltage overhead power transmission line. The method comprises the steps of: obtaining a thunder current amplitude, calculating a lightning channel wave impedance value Z by the following formula according to the thunder current amplitude, wherein I is the thunder current amplitude; and determining a counterattack anti-lightning level of the line according to the lightning channel wave impedance value so as to further determine insulation configuration of the power transmission line. The device disclosed by the invention comprises a thunder current amplitude obtaining module, a lightning channel wave impedance value calculating module and an insulation configuration determining module. By the anti-lightning evaluation method and the anti-lightening evaluation device of the high-voltage overhead power transmission line disclosed by the invention, the lightning channel wave impedance value corresponding to any thunder current amplitude can be precisely calculated so as to more accurately evaluate the counterattack anti-lightning level of the high-voltage overhead power transmission line and determine proper insulation configuration, so that the security and the economical efficiency of the power transmission line are better balanced.
Owner:CHINA ENERGY ENG GRP GUANGDONG ELECTRIC POWER DESIGN INST CO LTD +1
Method for configuring secret key of wireless sensor network
InactiveCN102665209AAchieving Energy Spending with Security and ConnectivityBalance costNetwork topologiesSecurity arrangementComputer securityT matrix
The invention relates to a method for configuring a secret key of a wireless sensor network. The method is characterized by comprising the following steps of: step 1, generating a large secret key pool; step 2, generating alpha and beta secret key matrix spaces; step 3, generating a classification secret key matrix space; and step 4, before a network node of a wireless sensor network is firstly configured, randomly selecting t matrix pair elements from primary secret key matrix spaces alpha 1 and beta 1 through a system, and randomly assigning the ith row and ith column of information of each matrix pair element to a node, wherein each node stores t matrixes ID (identity) corresponding to the t matrix pair elements; step 5, randomly throwing the nodes of the step 4 in a configuration area so that the nodes broadcast self stored matrix ID values to surrounding nodes can directly establish right secret keys if finding out that the nodes have the same matrix ID with an opposite node, and each firstly configured nodes cancel row and column information of residual alpha 1; and step 6, sequentially carrying out multiple complementation node configuration from corresponding alpha n and beta n1 according to the step 5, wherein v is larger than and equal to 3, S is larger than and equal to 100 and t is larger than and equal to 60. Compared with the prior art, the invention has the advantages of capability of realizing balance of energy source expense of network nodes with safety and connectivity.
Owner:佛山微创软件科技有限公司
Video and audio credible playing method based on asymmetric encryption
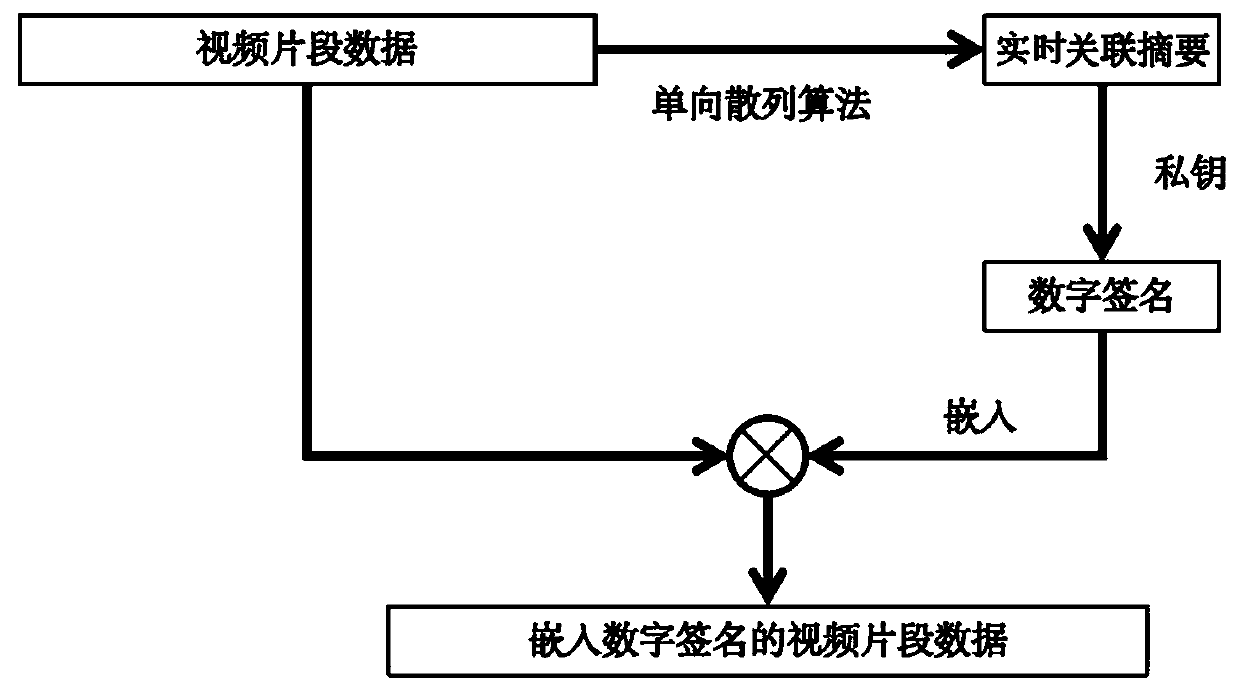
ActiveCN110602570AReduce engineering overheadImprove trustworthinessSelective content distributionDigital signatureThe Internet
The invention discloses a video and audio credible playing method based on asymmetric encryption, and relates to the technical field of digital security, and the method comprises the steps that a publishing end embeds a digital signature encrypted by a private key into a video streaming media in a general transcoding service process of the video streaming media, and pushes the video streaming media embedded with the digital signature to an intermediate network; the client receives the video streaming media through the intermediate network; digital signatures therein is extracted, the digitalsignature is decrypted by using the public key to obtain data for detection; and a detection result is deduced according to the detection data to control the player to play the video streaming media content. According to the invention, the detection process is transferred from the Internet to the transceiving end; by combining the one-way hash algorithm and the asymmetric encryption technology, while it is ensured that the behaviors of tampering and replacing the streaming media in the transmission process can be detected by the user side, the calculation overhead is greatly reduced, the complex asymmetric encryption technology can be applied to video streaming media application, and the basic real-time requirement of the streaming media is met.
Owner:CHENGDU SOBEY DIGITAL TECH CO LTD
Agricultural vehicle balancing system
ActiveUS20100117346A1Reduce the balanceLower center of gravitySoil-working equipmentsVehicle cleaning apparatusGravity centerEngineering
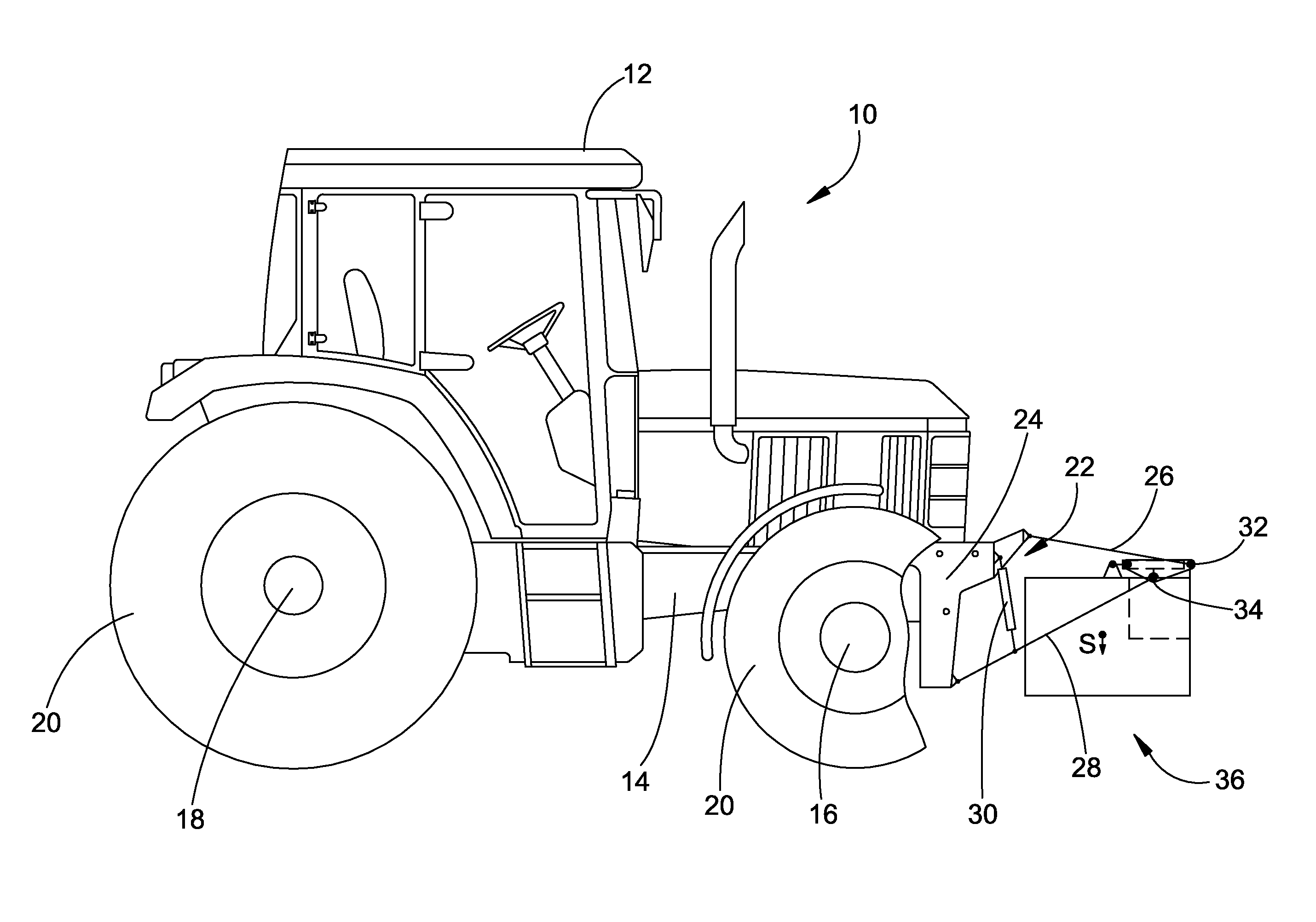
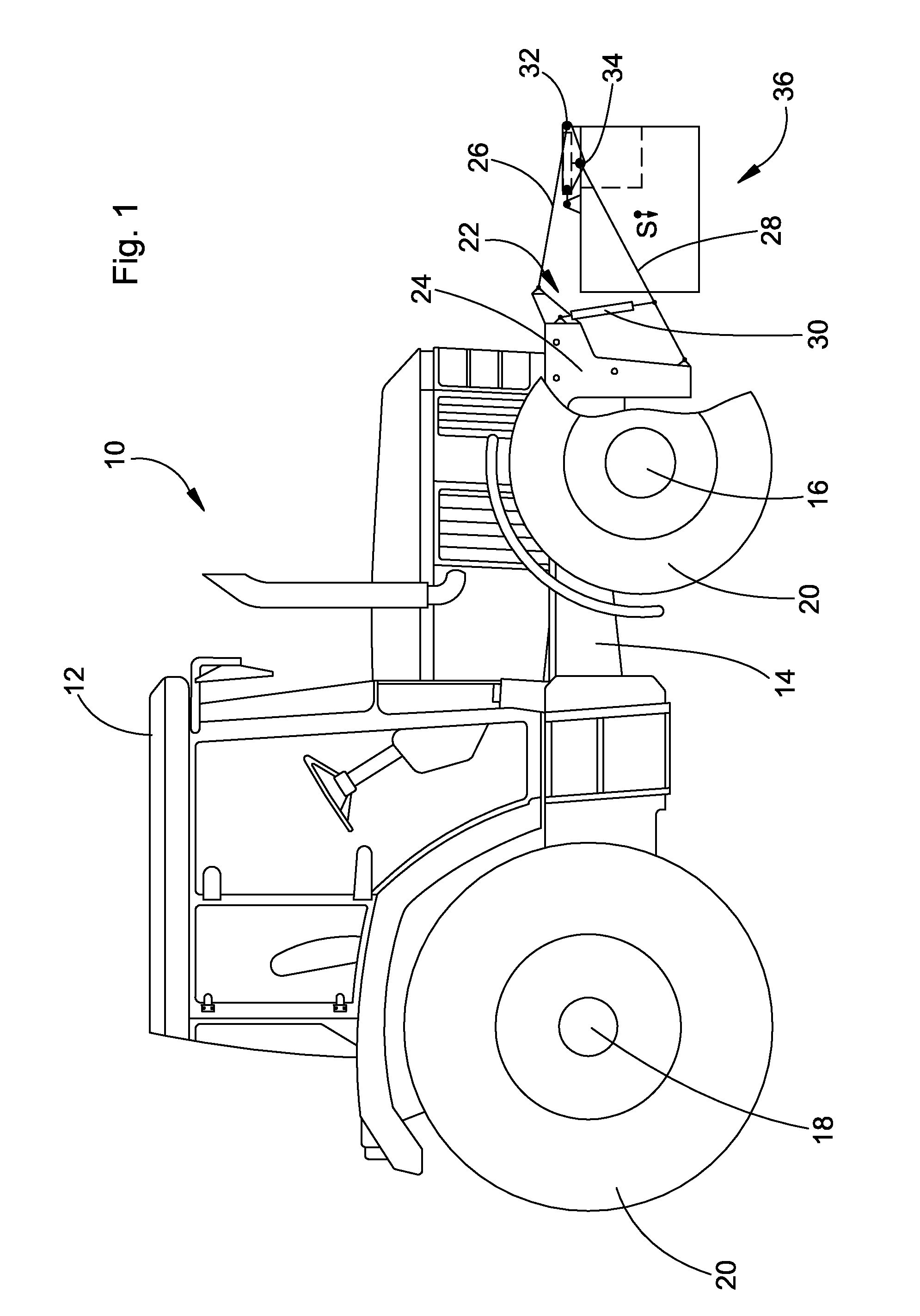
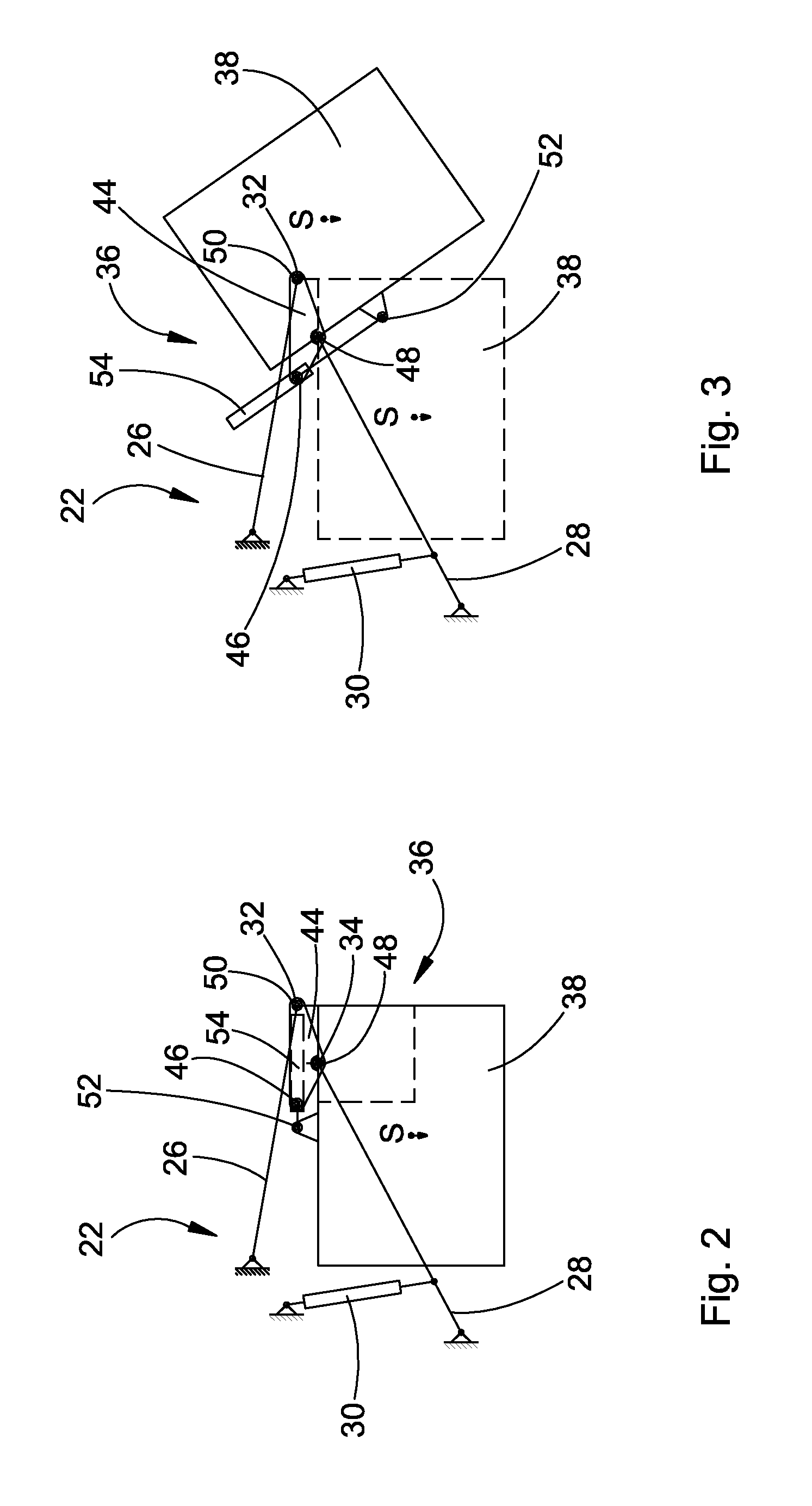
A balancing system for an agricultural vehicle includes a balance weight which has take-up pins at its sides. The pins are oriented coaxially to a common pivot axis so that the balancing weight can be taken up by the lower links of a three point implement hitch. When the balance weight has been taken up, it can be moved from a position of the center of gravity (S) of the balance weight close to the vehicle to a position distant from the vehicle. In order to attain a balance as optimal as possible, the position of the center of gravity of the balance weight in its position close to the vehicle is located below the pivot axis. Pivoting devices are provided so that the balance weight can be pivoted about the pivot axis so that it can also be brought from a position close to the vehicle to a position distant from the vehicle, where the balance weight occupies a lower position of the center of gravity in the position close to the vehicle than in the position distant from the vehicle.
Owner:DEERE & CO
Method capable of updating chameleon hash function
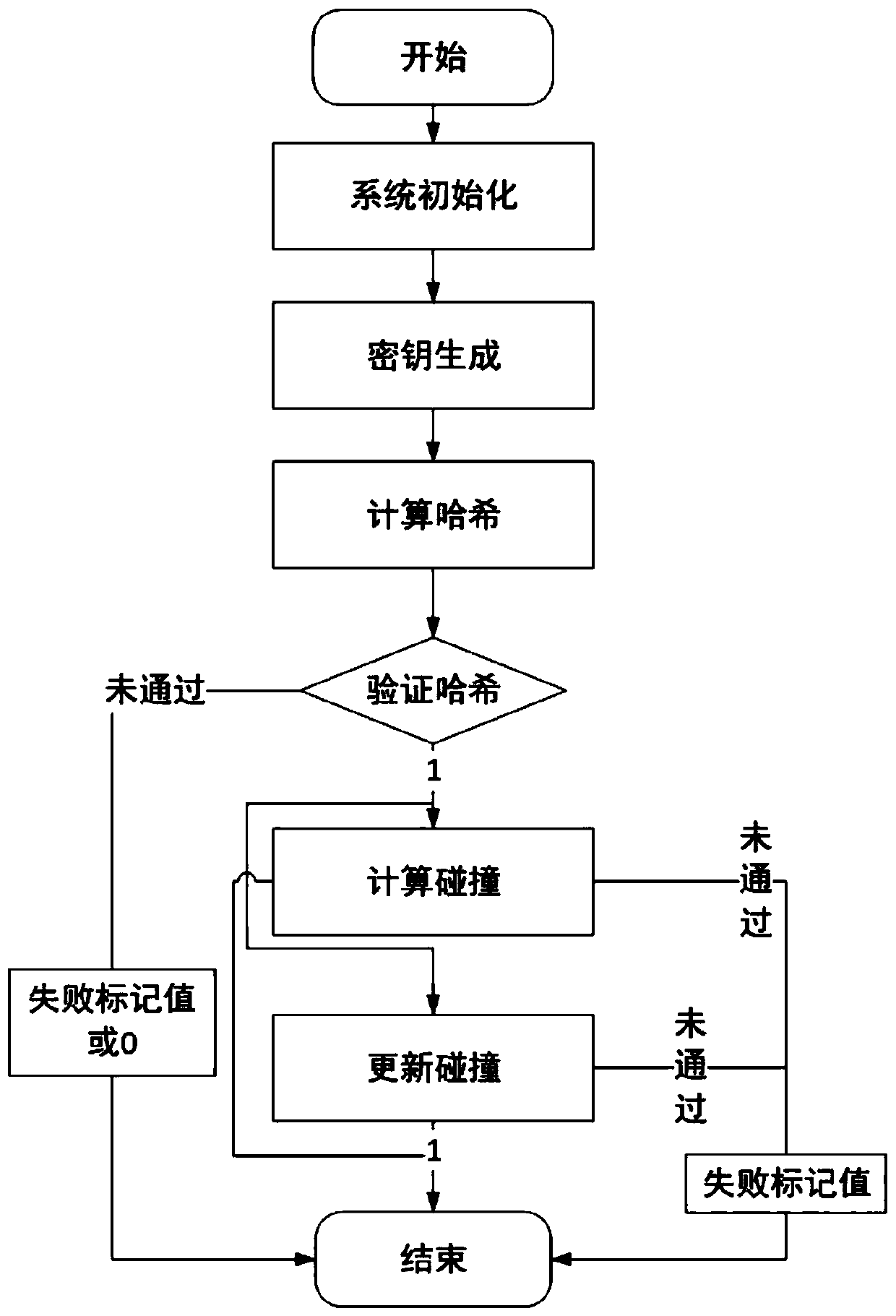
ActiveCN110086631AMeet the needs of useEfficiencyKey distribution for secure communicationUser identity/authority verificationHash functionTrap door
The invention discloses a method capable of updating a chameleon hash function, and belongs to the technical field of network security. The method comprises the steps of initializing a system, generating a secret key, computing hash, verifying hash, computing collision, updating the collision, periodically updating a chameleon random number meeting the collision according to a trap door secret key, enabling the chameleon random number which is correctly updated to pass authentication at the current time point, otherwise, enabling the chameleon random number not to pass authentication, therebysolving the efficiency and safety problems of a chameleon hash value of the chameleon hash function in the prior art. The method is suitable for safely and efficiently calculating the chameleon hash value, can resist the secret key leakage, can periodically update the chameleon random number meeting collision, prevents the collision value from being abused, and improves the freshness of the chameleon hash value at the same time.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Cycling training apparatus with stationary movement
ActiveUS20170246524A1Pleasant feelWell trainingResilient force resistorsCycle standsEngineeringCycling
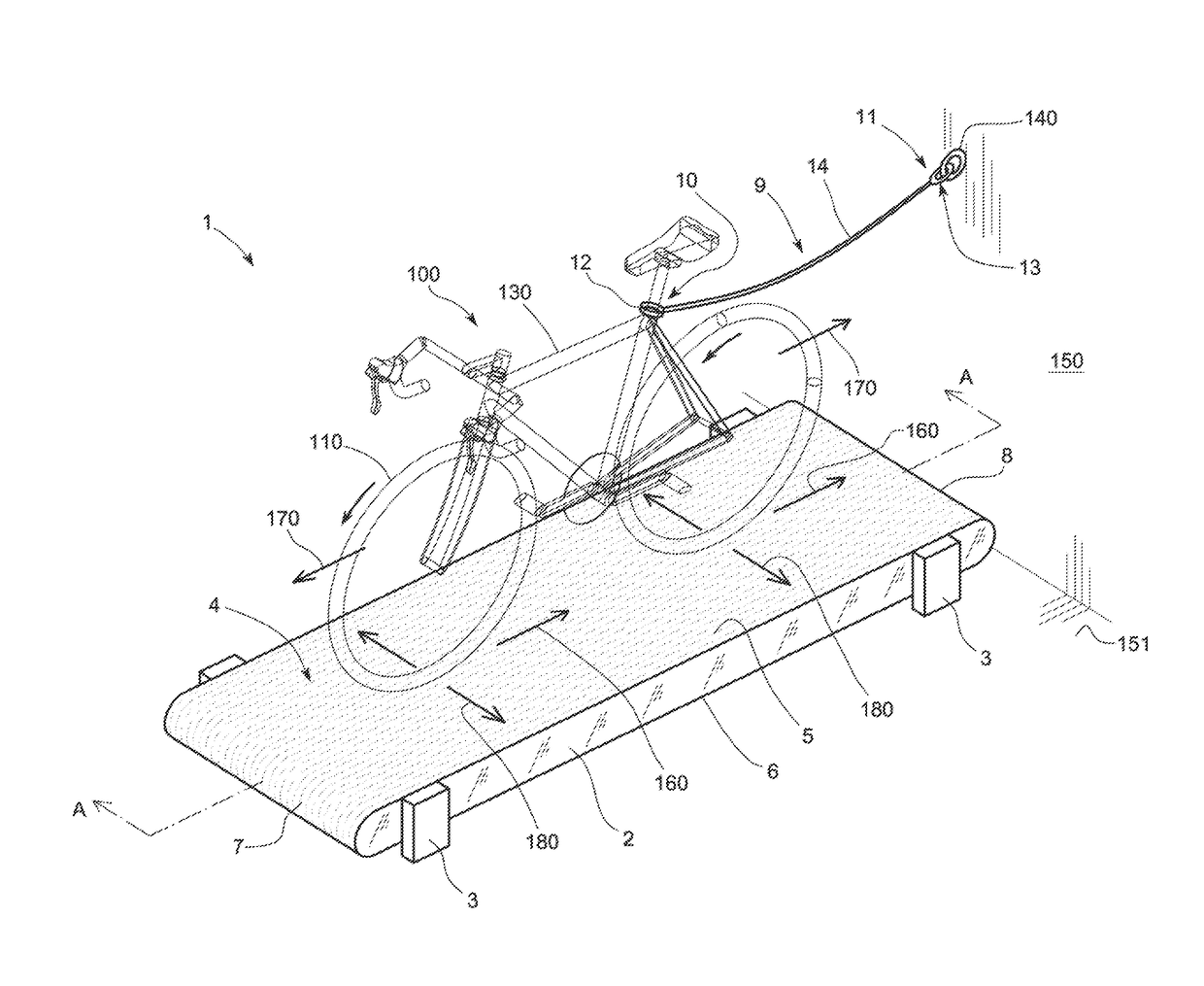
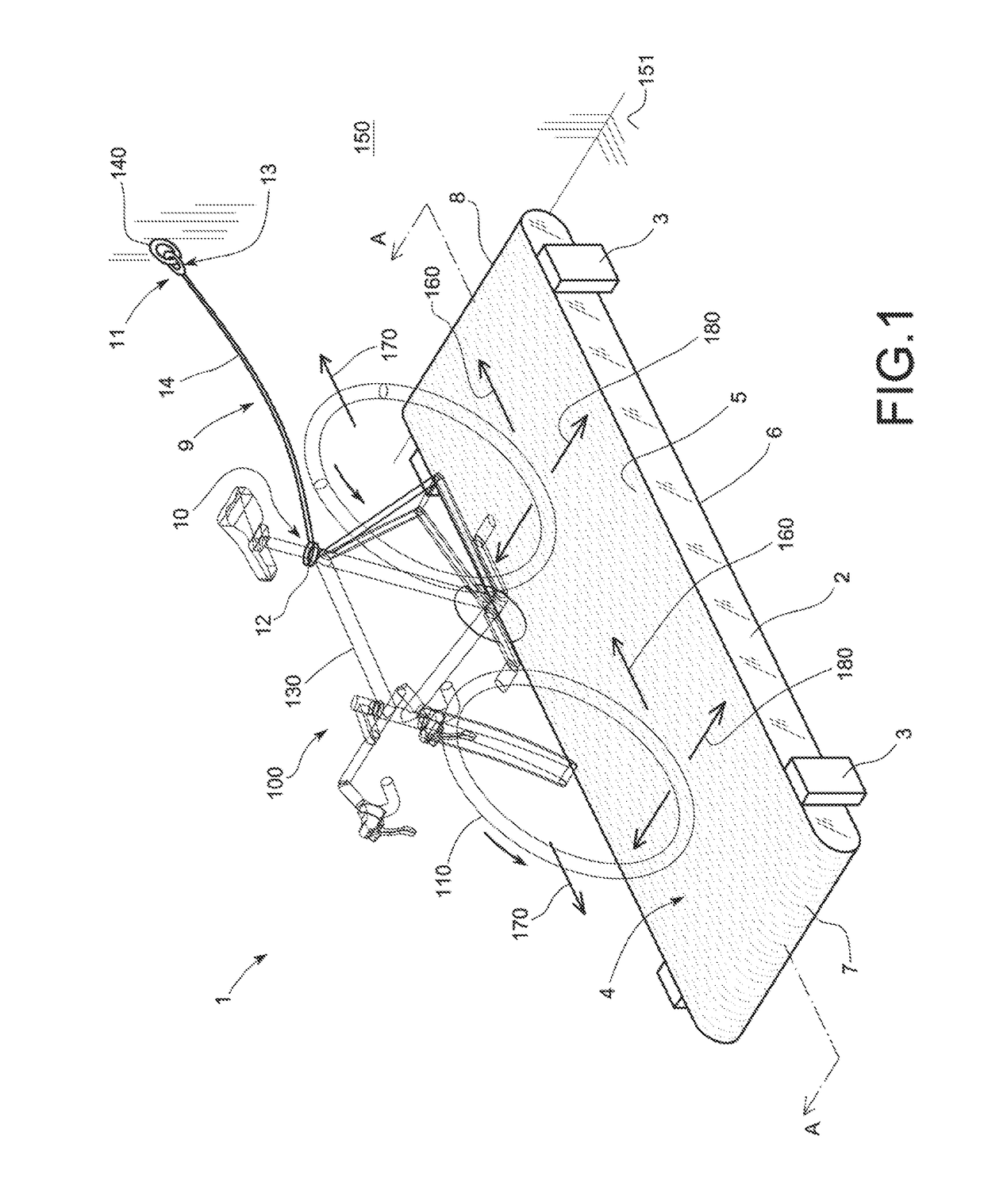
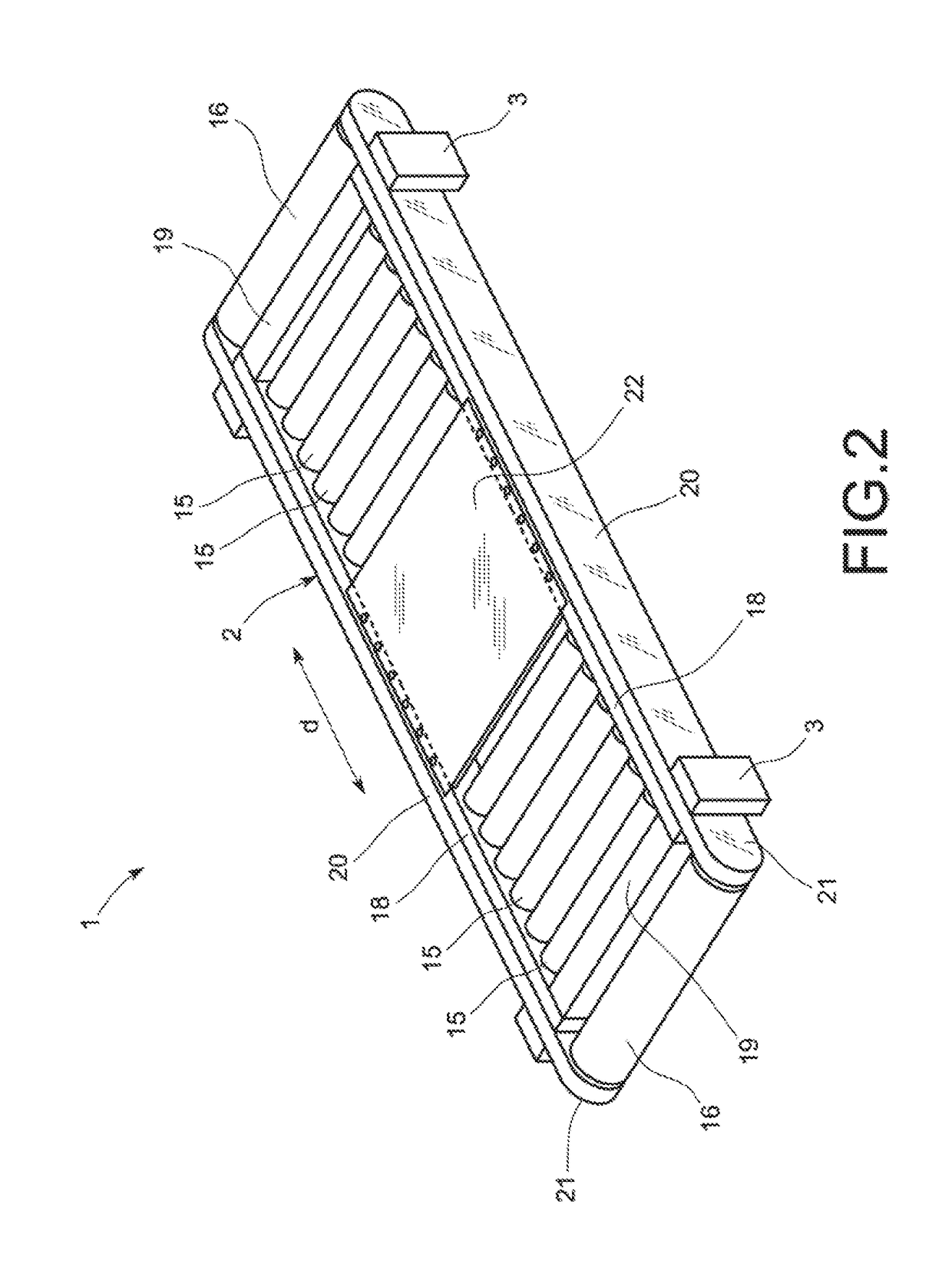
Cycling training apparatus (1), comprising a structure (2) that is supported on the floor (151) and a belt (4) that is movable with respect to the structure (2) and forms a closed longitudinal loop on which a bicycle (100) can be supported and ridden, The apparatus (1) comprises a securing element (9; 29) with two opposite ends (10, 11; 30, 31). One end (10; 30) has a first connector (12; 32) configured to be attached to a bicycle (100). The opposite end (11; 31) includes a second connector (13, 33) configured to be attached to a fixed point, The securing element (9; 29) is flexible so that the straight line distance (D) between these ends (10, 11; 30, 31) is variable, enabling the bicycle (100) to move longitudinally over the belt (4). The connectors also allow for transversal movement and lateral tilting of the bicycle (100).
Owner:OREKA TRAINING SL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com