Data encryption, data analysis method and apparatus
A technology of data encryption and data analysis, applied in the Internet field, to achieve the effect of balancing security and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] Embodiments of this specification will be described below with reference to the accompanying drawings.
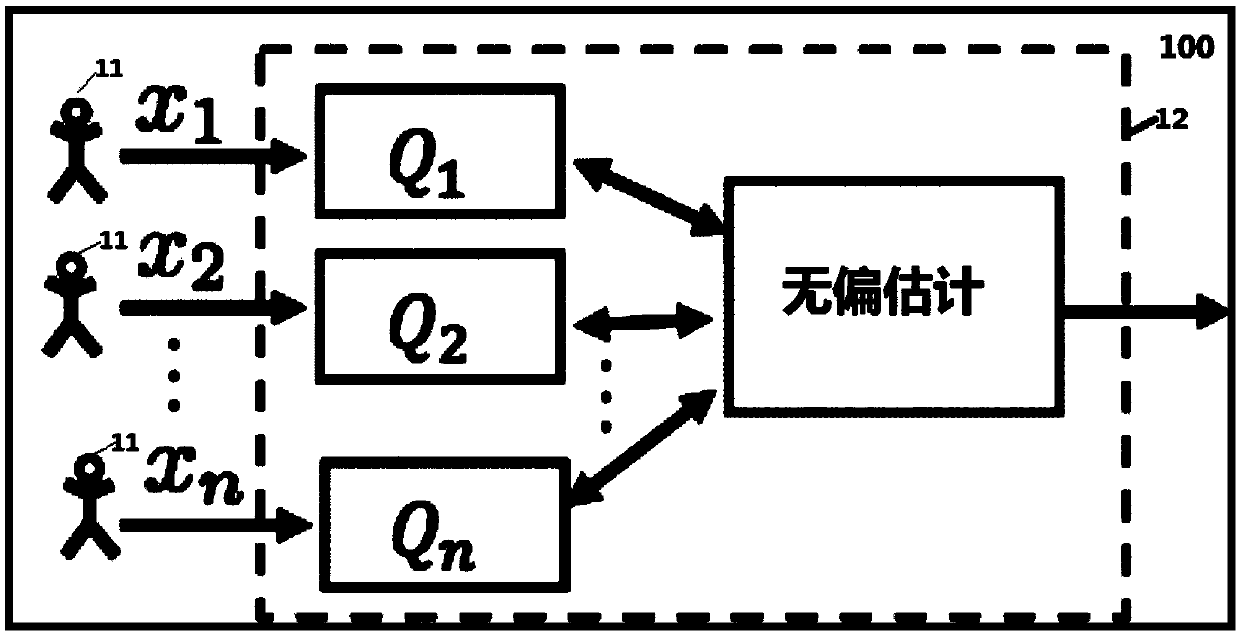
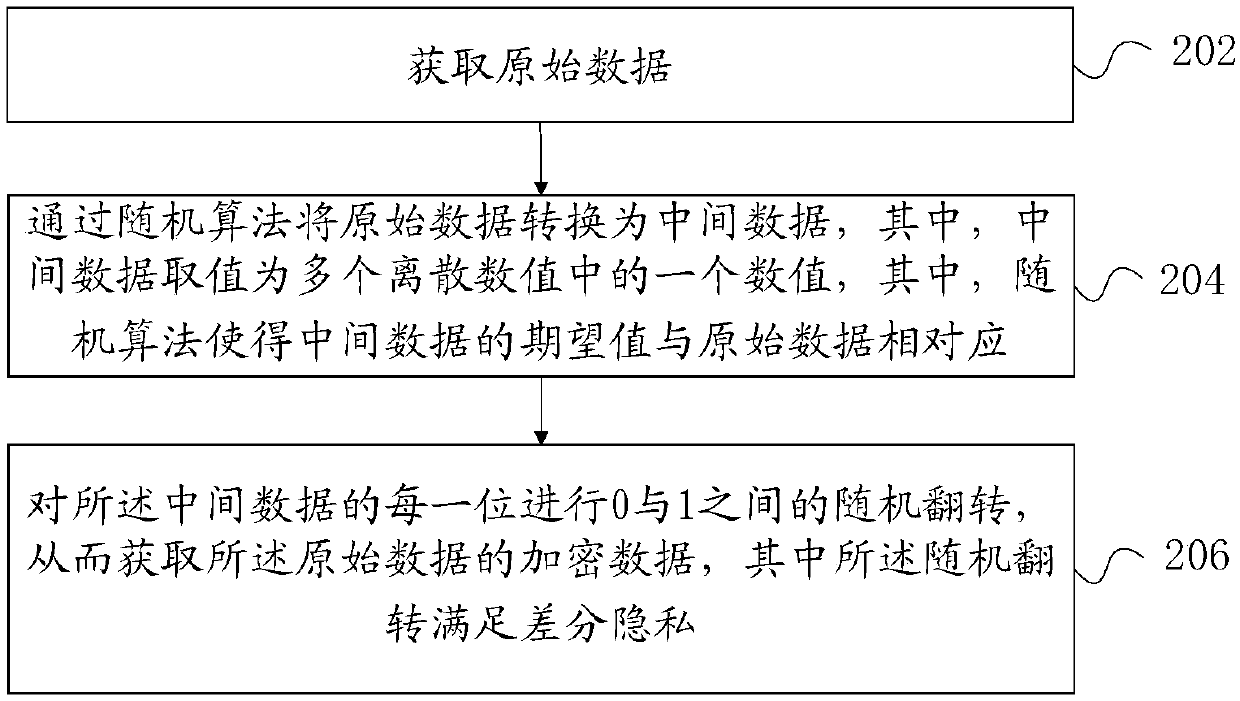
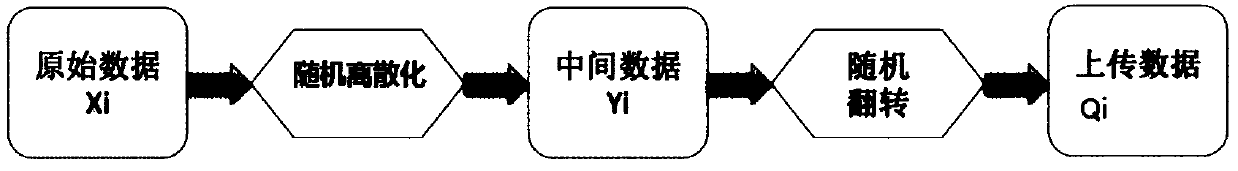
[0046] figure 1 A schematic diagram of a data processing system 100 according to an embodiment of the present specification is shown. Such as figure 1 As shown, the system 100 includes a plurality of user devices 11 and a server 12 . A plurality of user equipments 11 are respectively data providers, which include respective raw data corresponding to the first variable (that is, the value of the first variable) x 1 ,x 2,...,x n . Data providers expect raw data to be protected. The server 12 is the data demander, who wishes to analyze and integrate the relevant information (macro index) of the above-mentioned first variable based on the original data. In the data processing process according to the embodiment of this specification, at the end of the user equipment 11, the original data x 1 ,x 2 ,...,x n Convert to upload data Q 1 ,Q 2 ,...,Q n , and upload...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com