Method capable of updating chameleon hash function
A hash function and chameleon technology, applied in digital transmission system and key distribution, to achieve the effect of anti-key leakage, satisfying key leakage and using requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
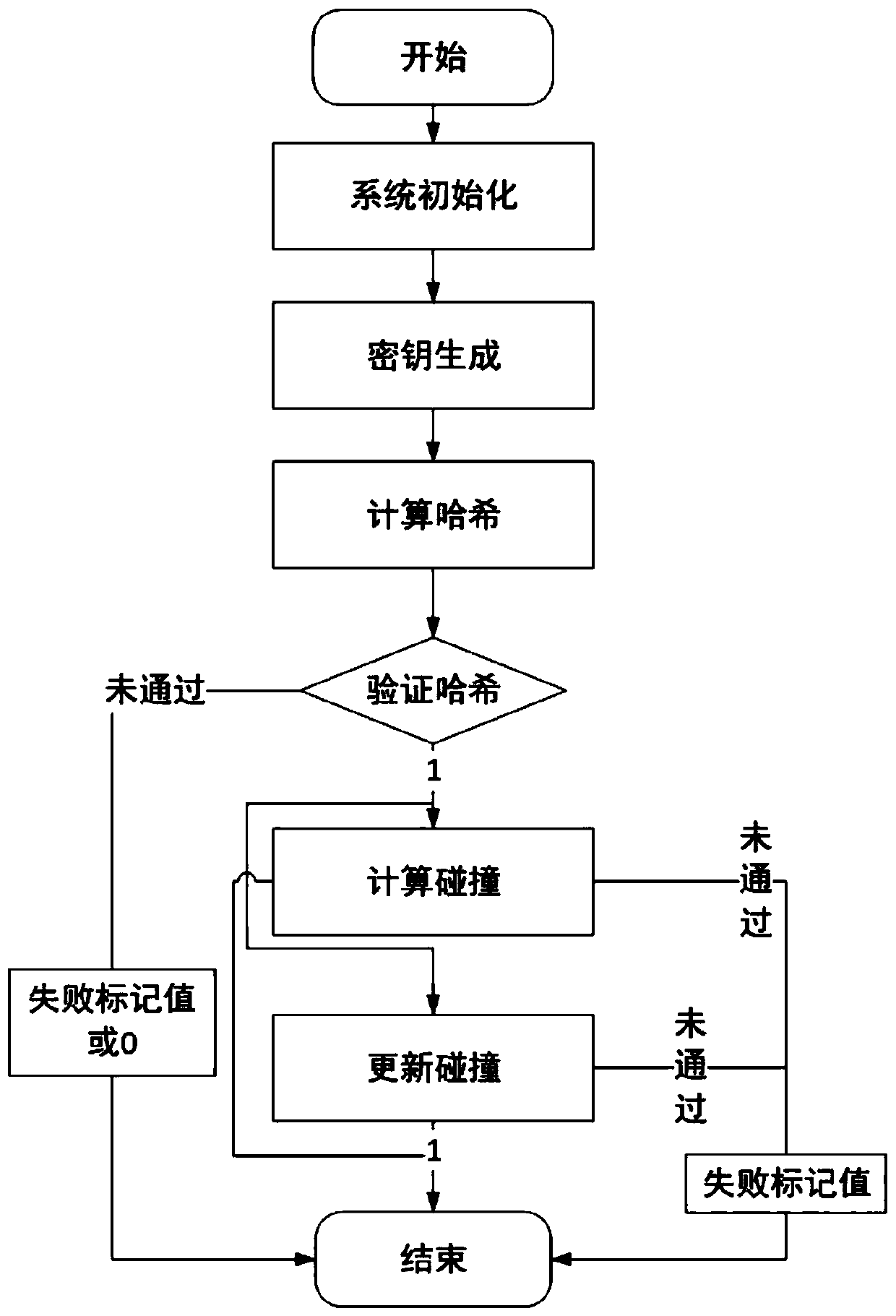
[0050] The invention includes: system initialization, key generation, hash calculation, verification of chameleon hash value, calculation of collision, update of collision, periodic update of chameleon random numbers satisfying collision according to trapdoor key, and correct update The following Chameleon random number can pass the authentication at the current time point, otherwise, it cannot pass the authentication. The present invention is suitable for safe and efficient calculation of chameleon hash values, and can resist key leakage, and can periodically update chameleon random numbers that satisfy collisions, prevent collision values from being abused, and improve the freshness of chameleon hash values at the same time . details as follows:
[0051] A method for updating a chameleon hash function, comprising the following steps:
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com