Code signature verifying method of ELF file form
A signature verification and file format technology, applied in the direction of preventing unauthorized use of memory, protecting stored content from loss, etc., can solve problems such as the imbalance between security and efficiency, and achieve the effect of improving security and preventing malicious code attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] An implementation example based on the Linux operating system is given below.
[0019] 1. Functional module design
[0020] This example mainly includes the following six functional modules:
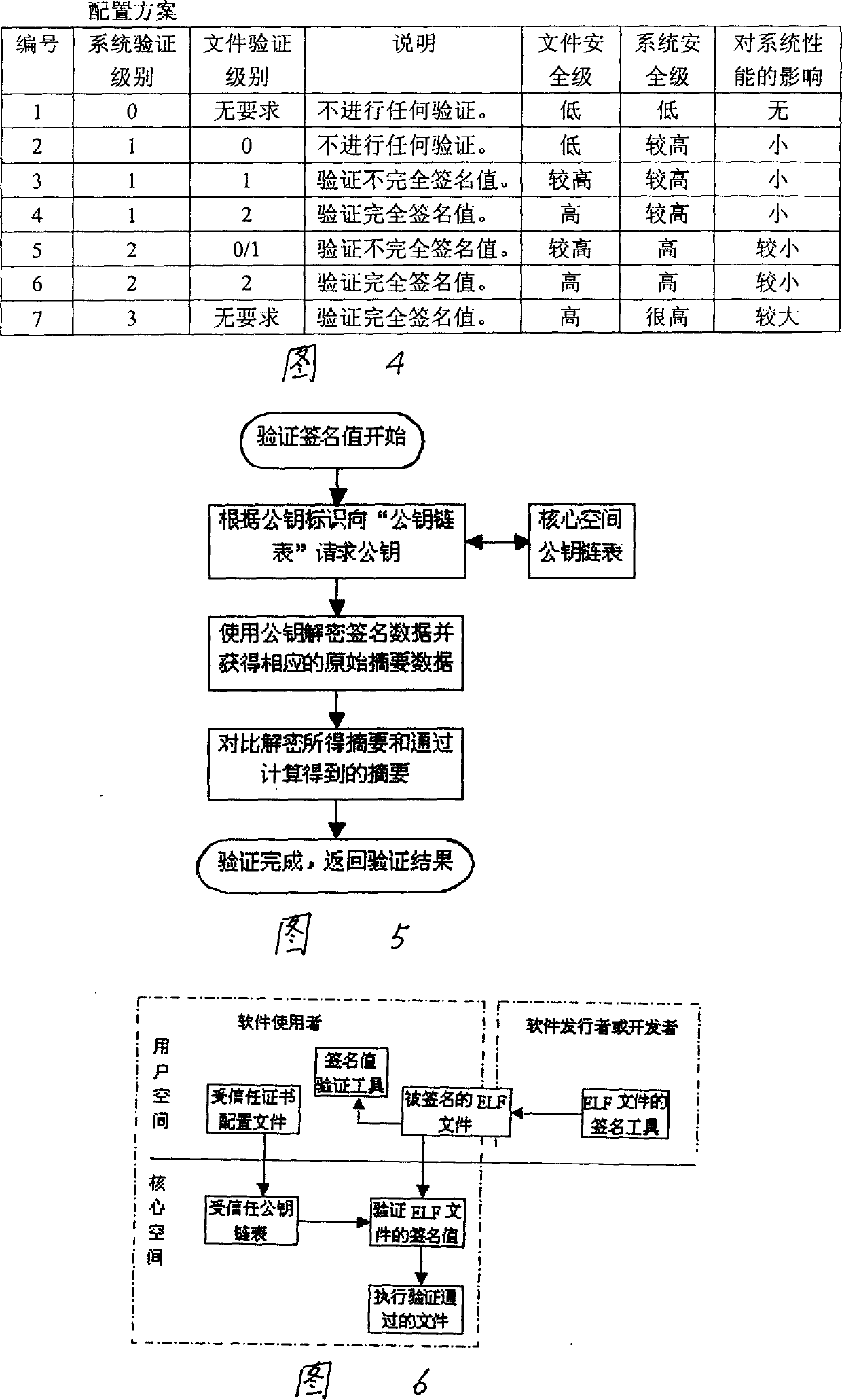
[0021] 1. Signature module
[0022] 2. Core layer verification module
[0023] 3. Application layer verification module
[0024] 4. Public key management module
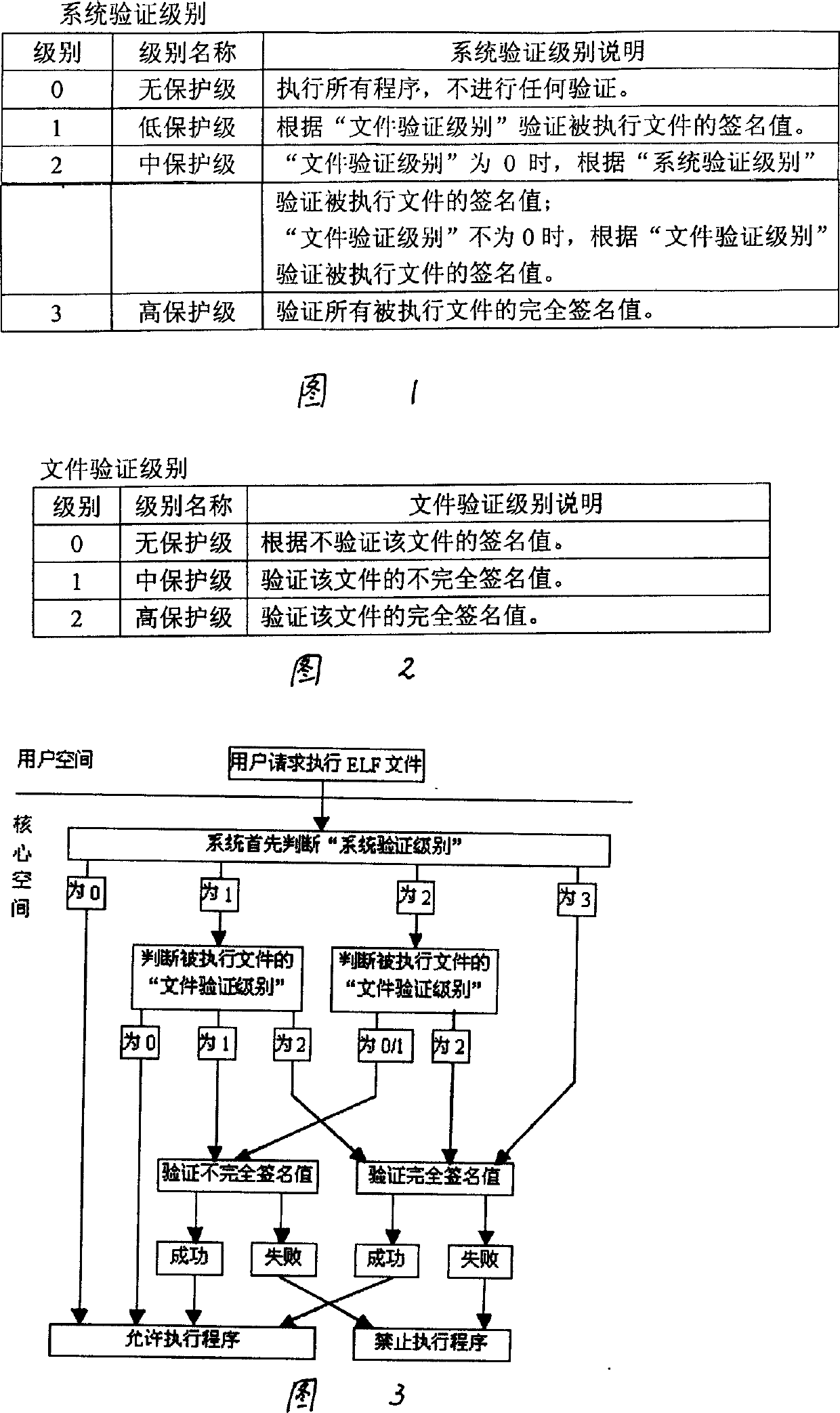
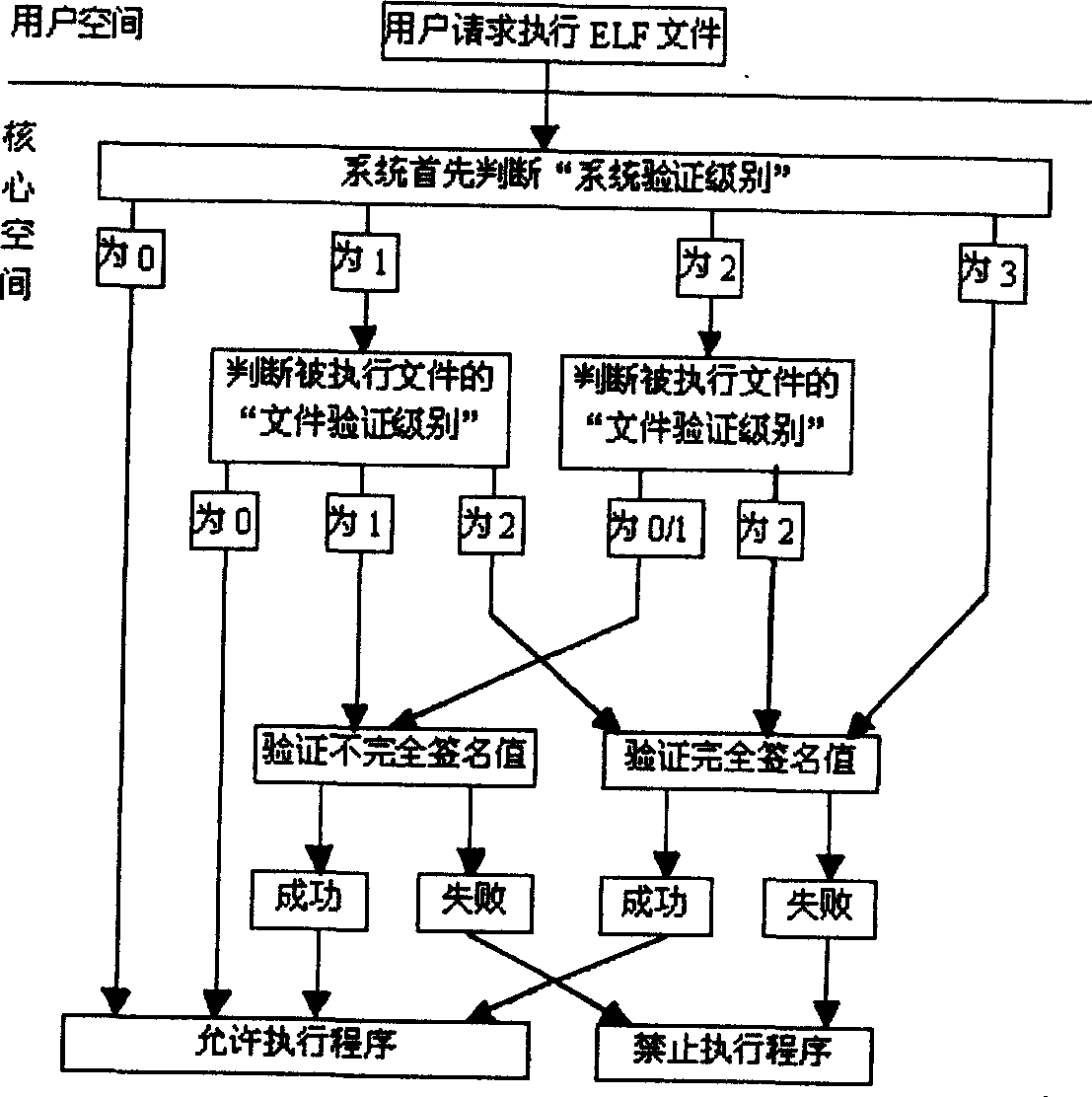
[0025] 5. System verification level management module
[0026] 6. File verification level management module
[0027] 2. Functional modules
[0028] 1. Signature module
[0029] The signature module is a relatively independent module, which is provided to software publishers and is mainly used to sign ELF files.
[0030] The main functions of this module are: sign the specified ELF file, sign all ELF files in the specified directory, and generate a signature report. At the same time, this module also has basic exception handling functions, such as: can identify whether the signed file is an ELF file, can identify...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com