Patents
Literature
33results about How to "Protect reputation" patented technology
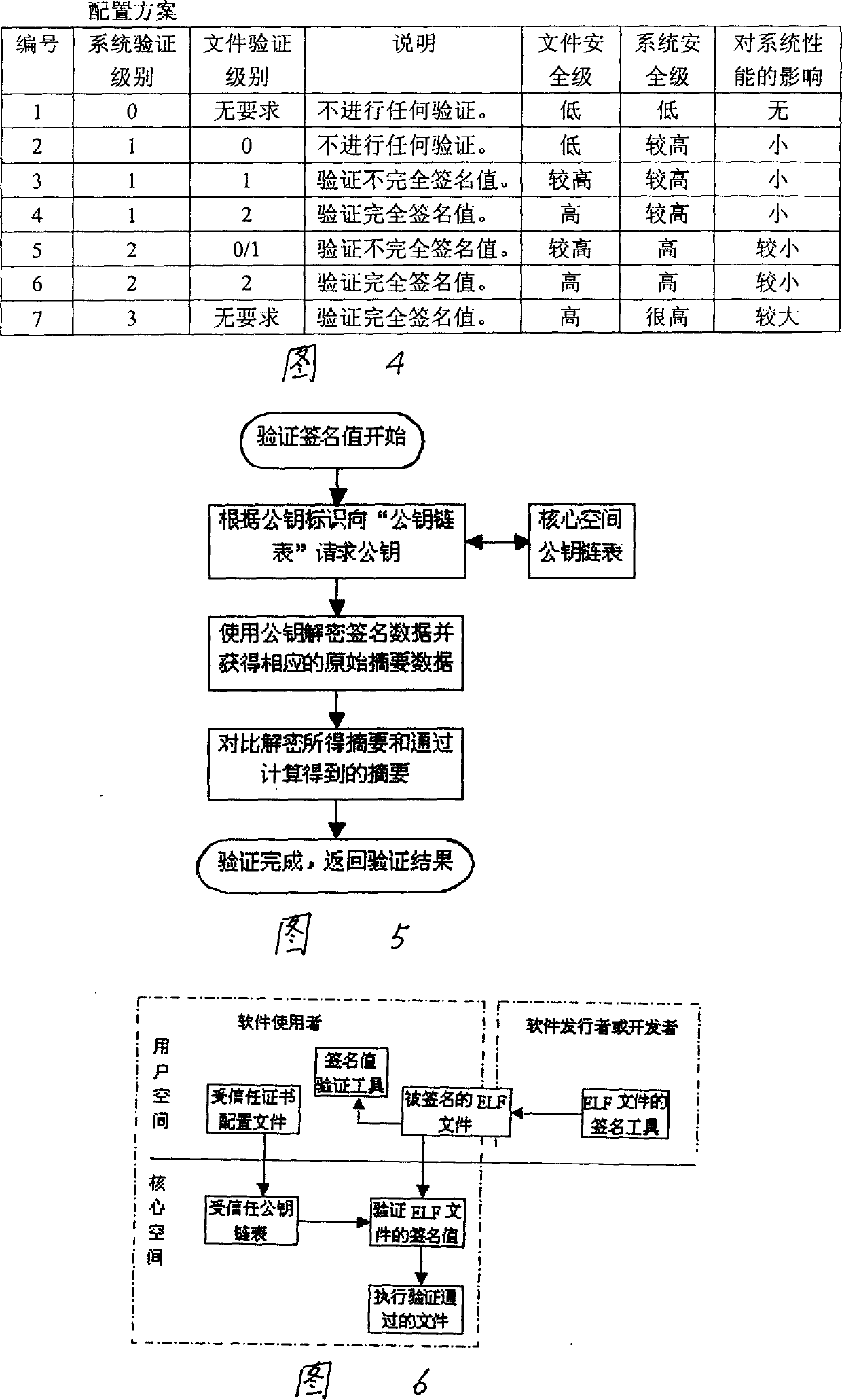
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
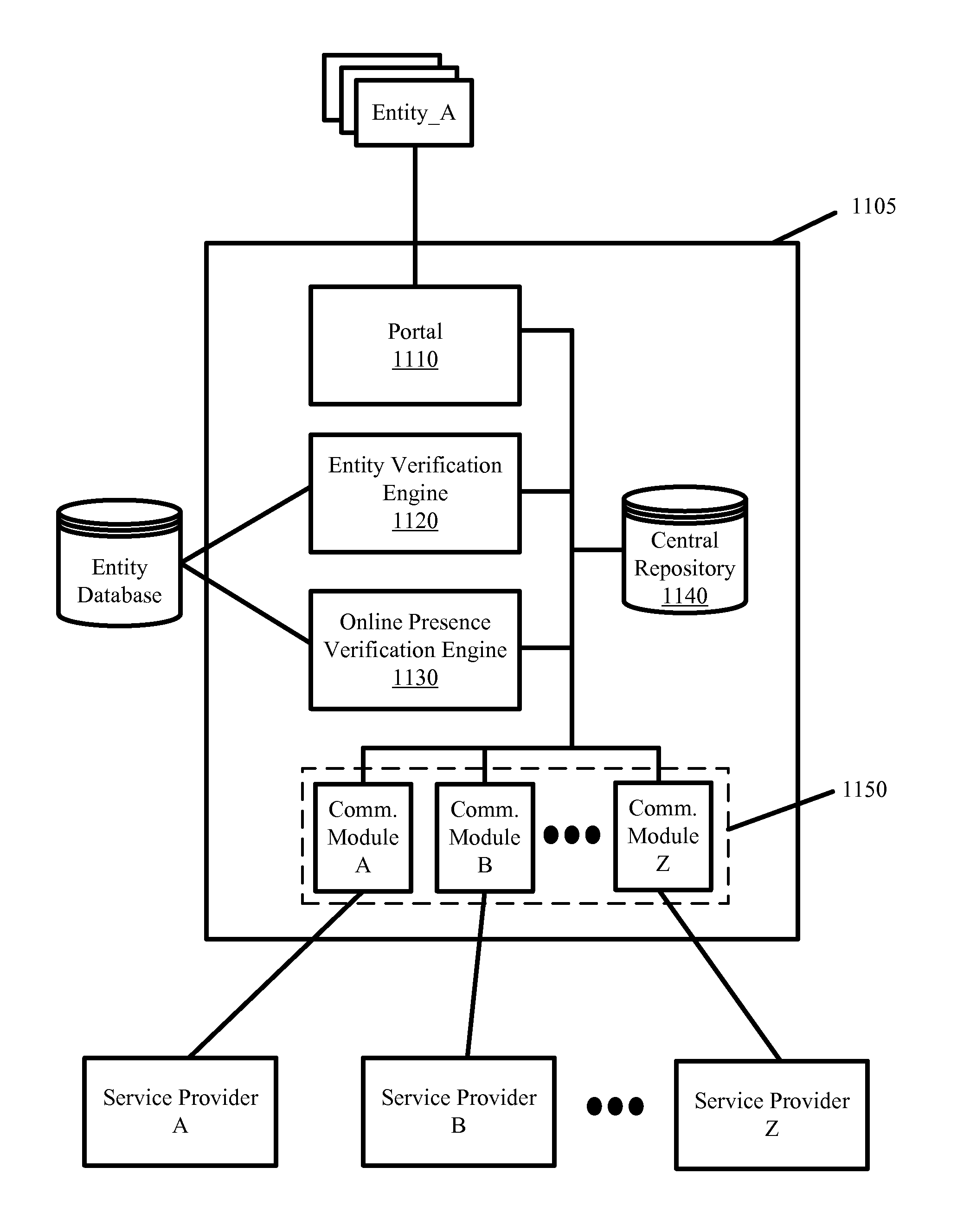
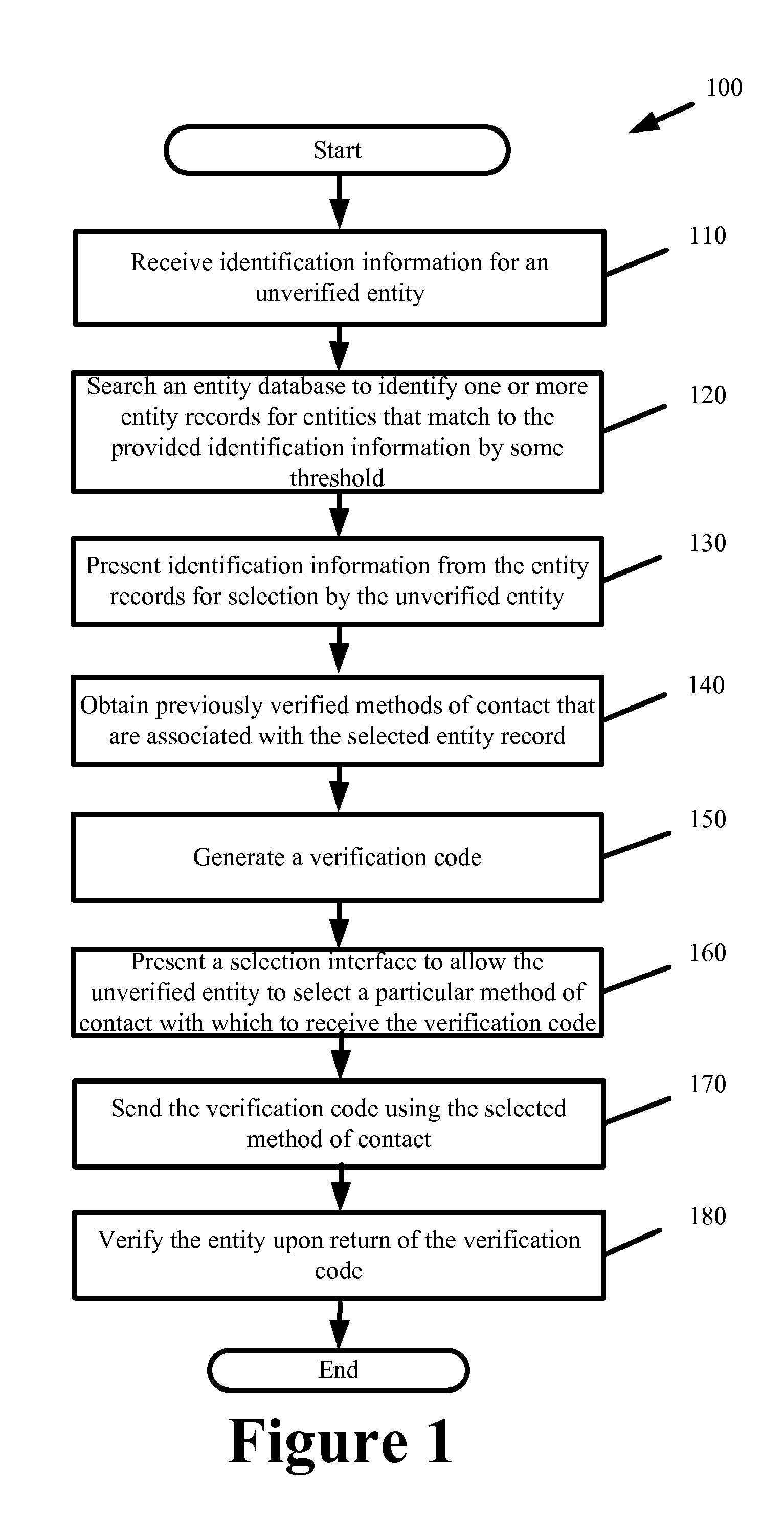
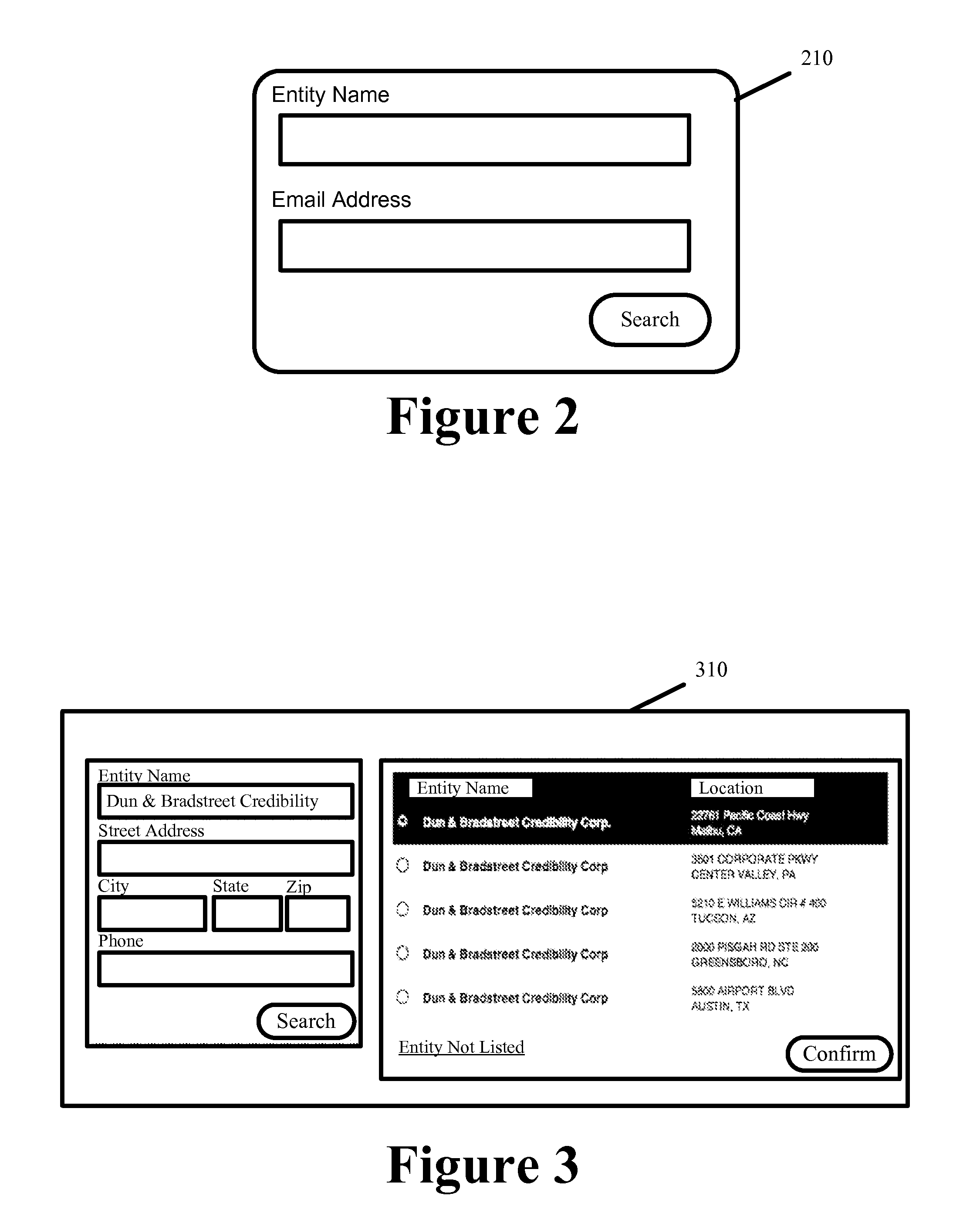
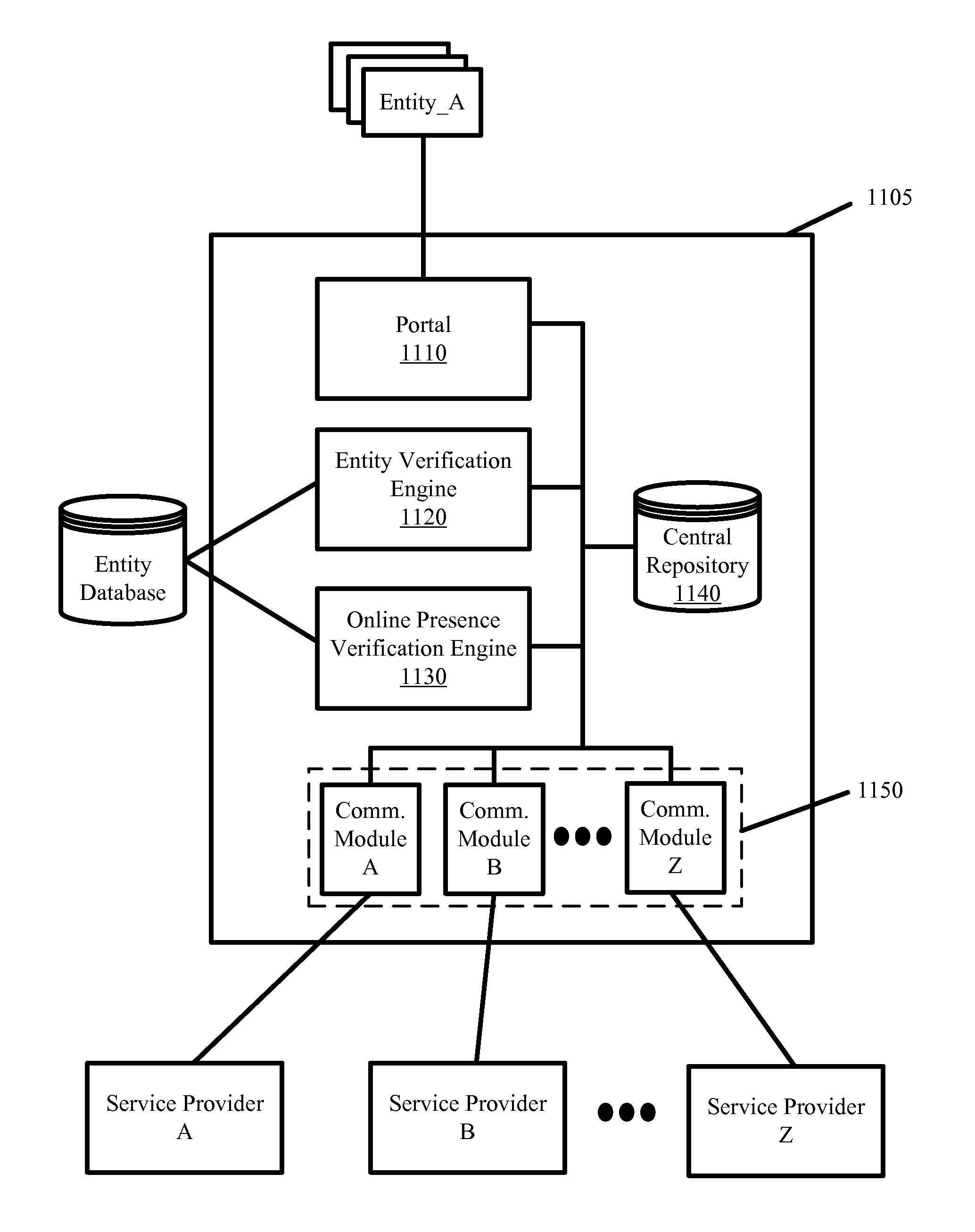
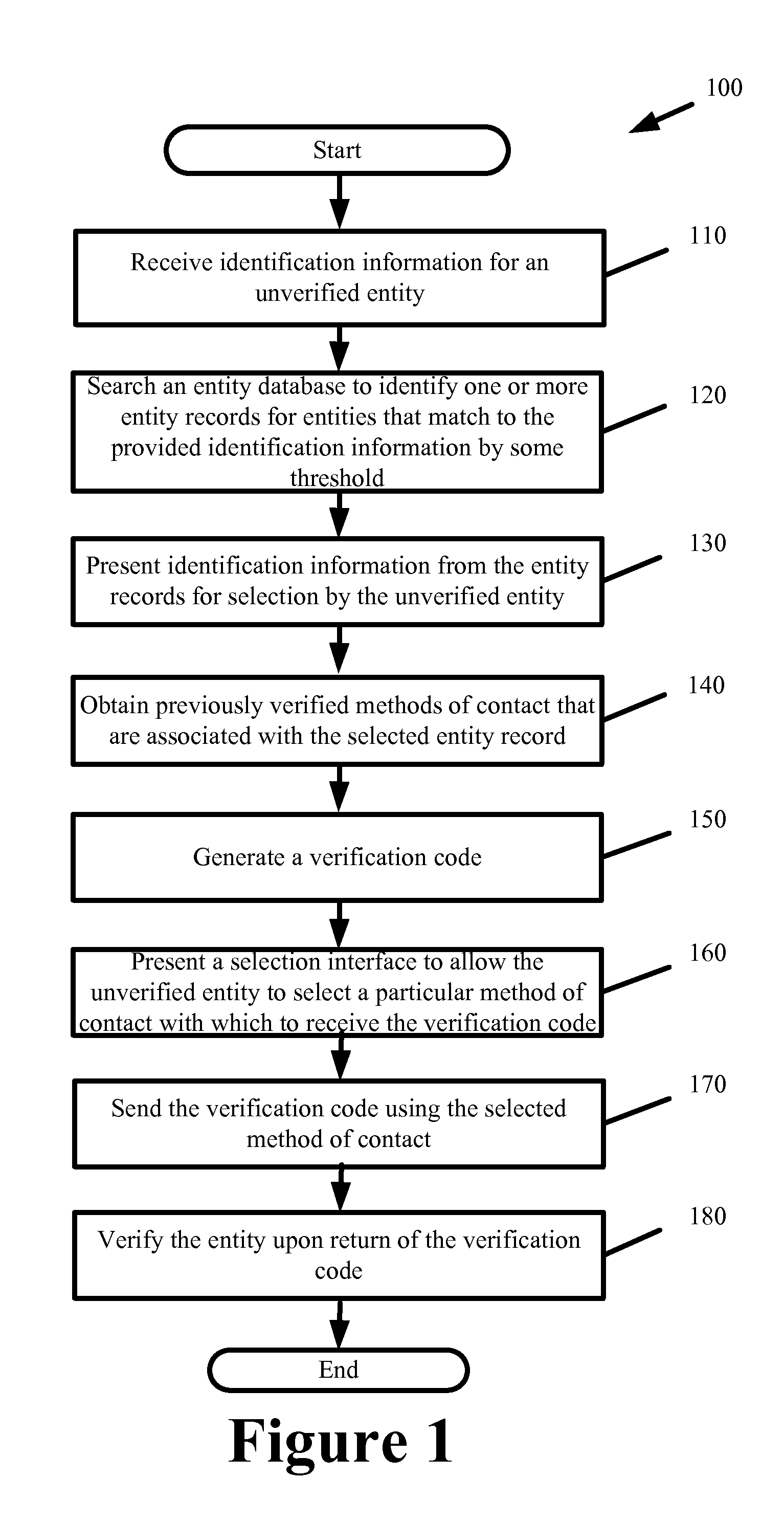
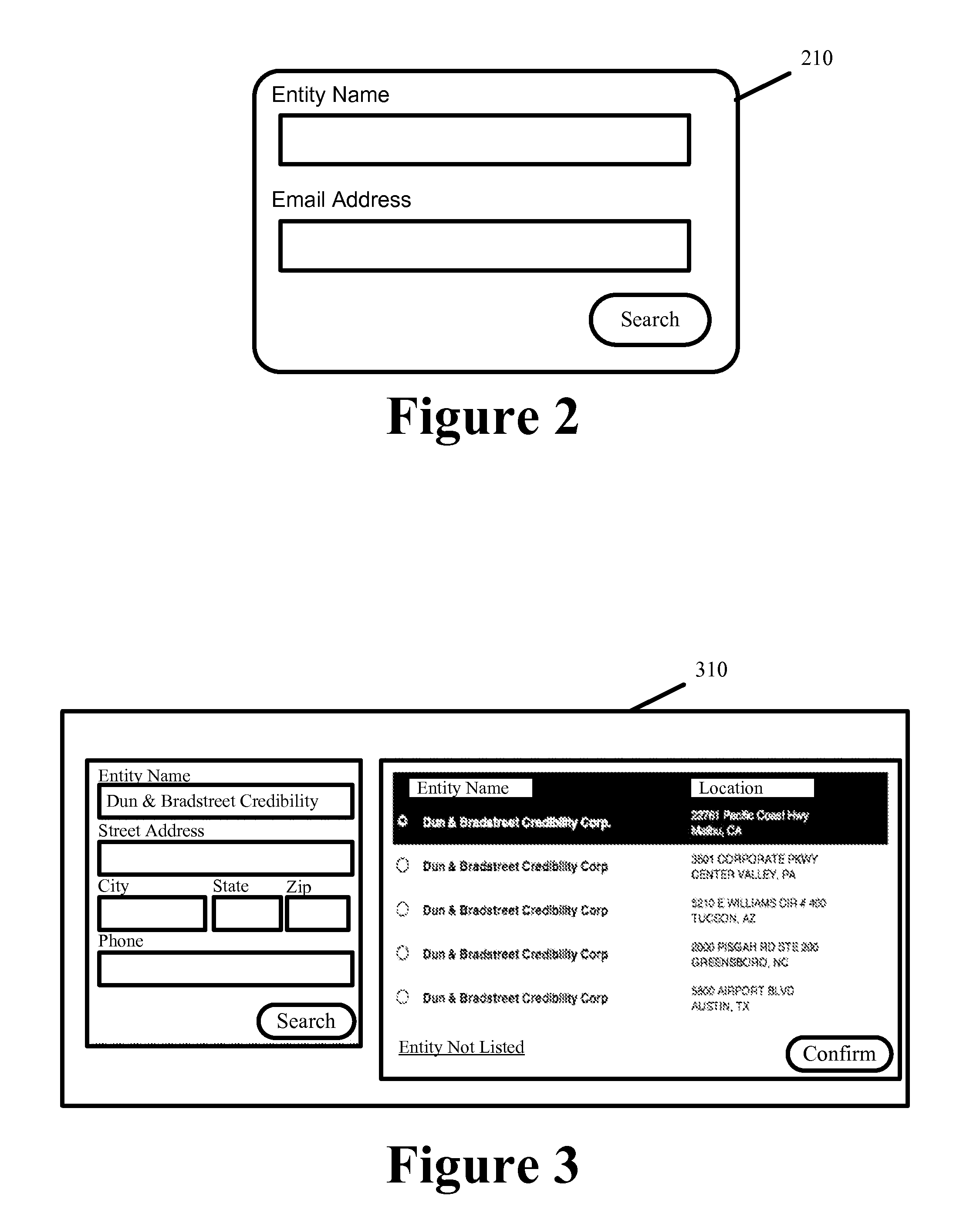
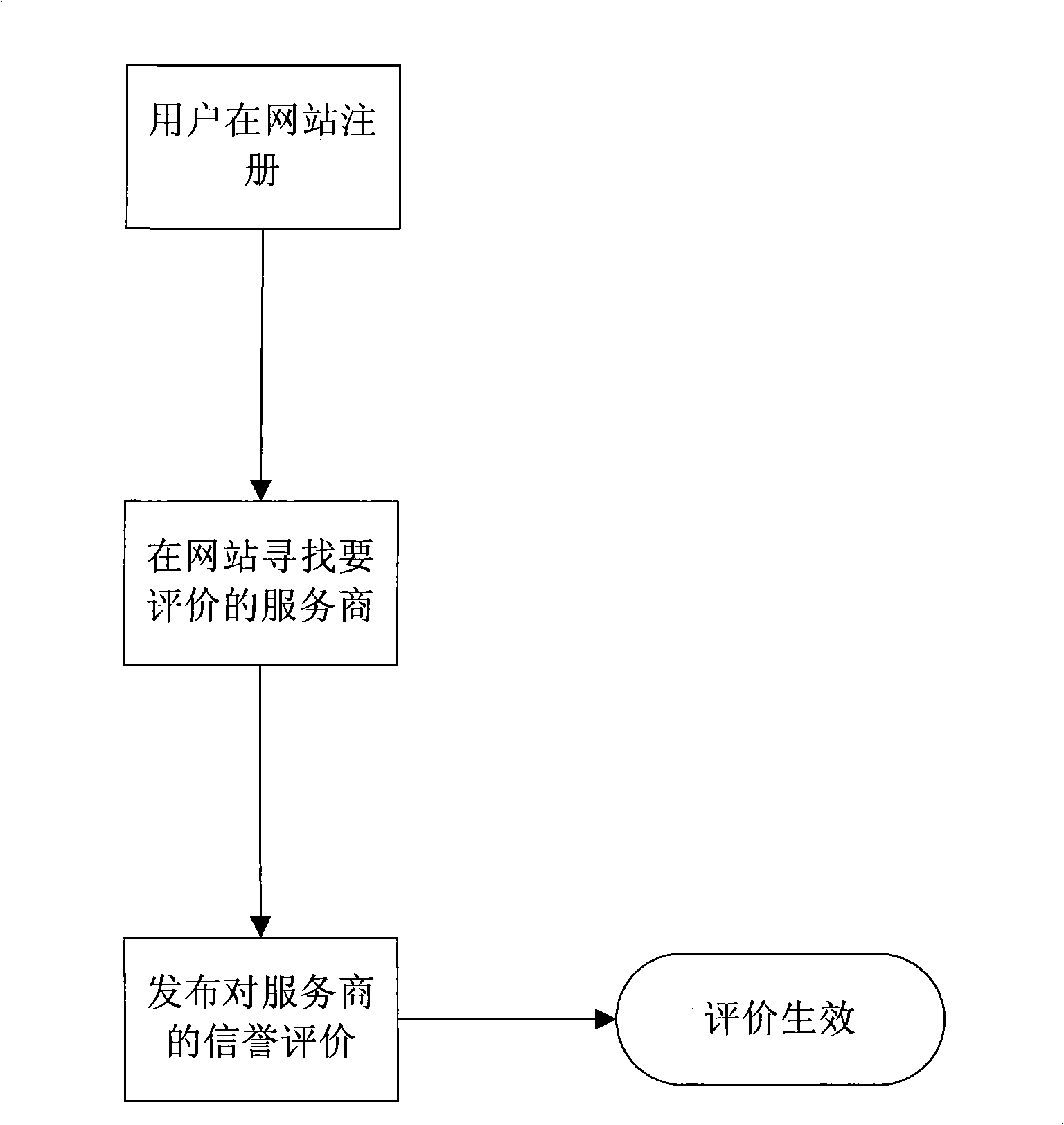
Advocate for facilitating verification for the online presence of an entity
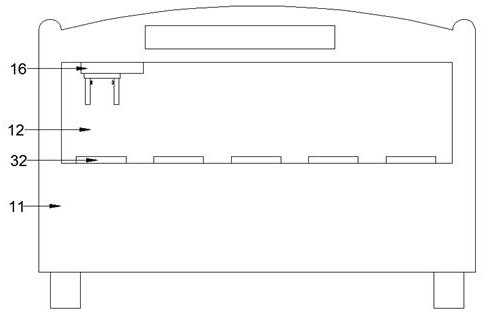
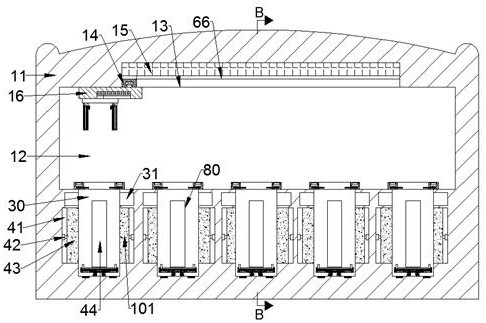
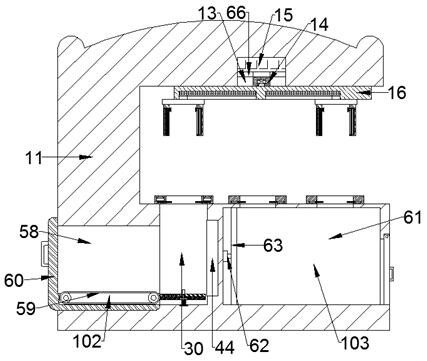
ActiveUS8544091B2Facilitate automated online presence verificationConvenient verificationMemory loss protectionDigital data processing detailsIdentity theftComputer science
Owner:DUN & BRADSTREET EMERGING BUSINESSES
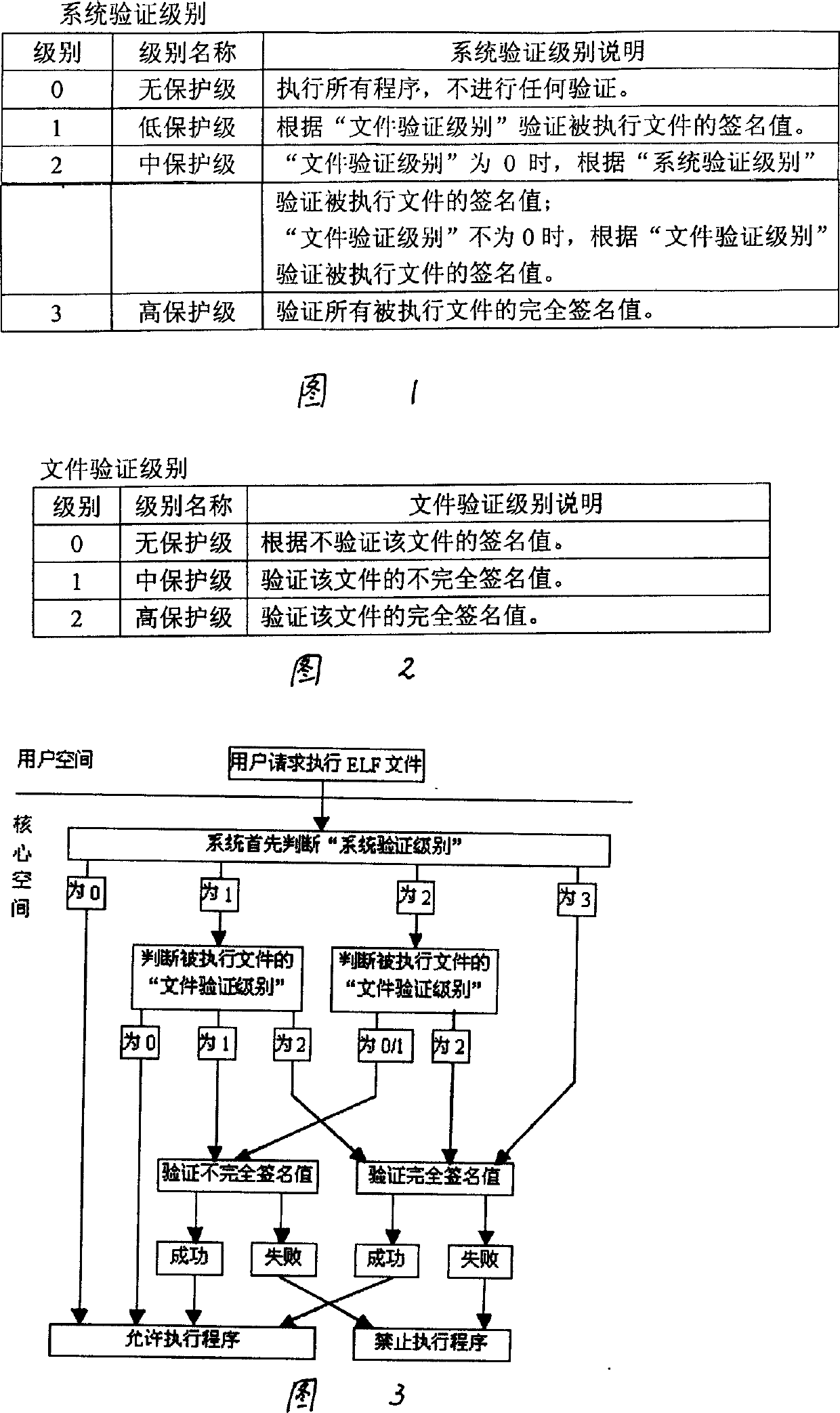
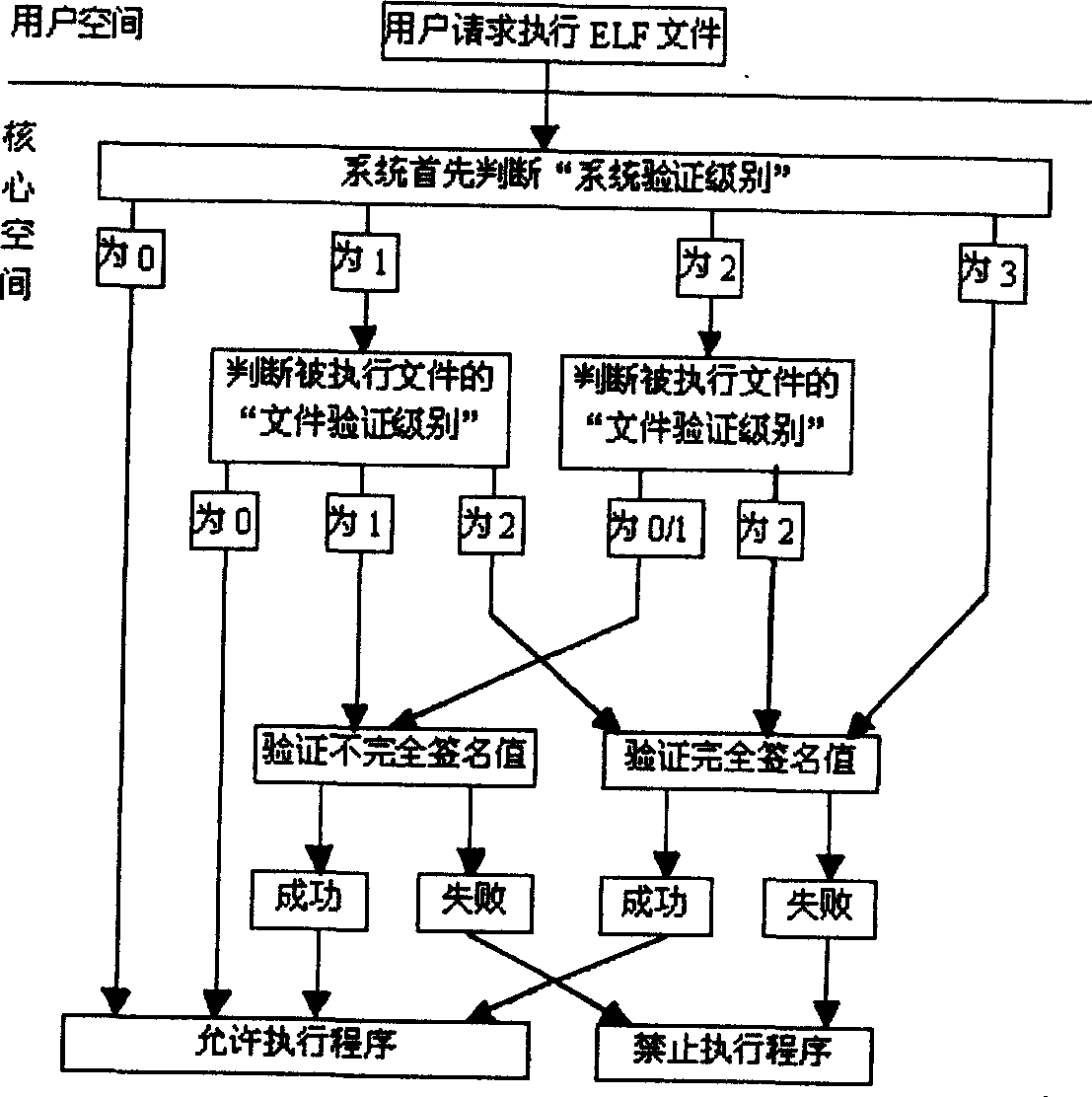
Code signature verifying method of ELF file form
InactiveCN1512355AImprove securityPrevent Malicious Code AttacksMemory loss protectionUnauthorized memory use protectionSystem safetySoftware development
The present invention discloses the verifying method of code signature in ELF file format. After the user requests executing ELF file, the system judges the level of system verification and determines the level of file verification of the executed file. For 0-level system verification, no code signature is not verified. For non-zero level, incomplete or complete signature value of the executed file is verified. During verification, the signer's public key is taken out from the kernel space chain table to decipher signature data and primary abstract data while available file is used to calculate the corresponding abstract data. The two pieces of abstract data are compared, and when they are the same, the verification is successful, or else failed. The present invention has the advantages of raised system safety resisting virus attack, optimal balance between safety and efficiency of the operation system and effective protection of software resource.
Owner:成都三零盛安信息系统有限公司
Anti-counterfeiting apparatus capable of remote identifying
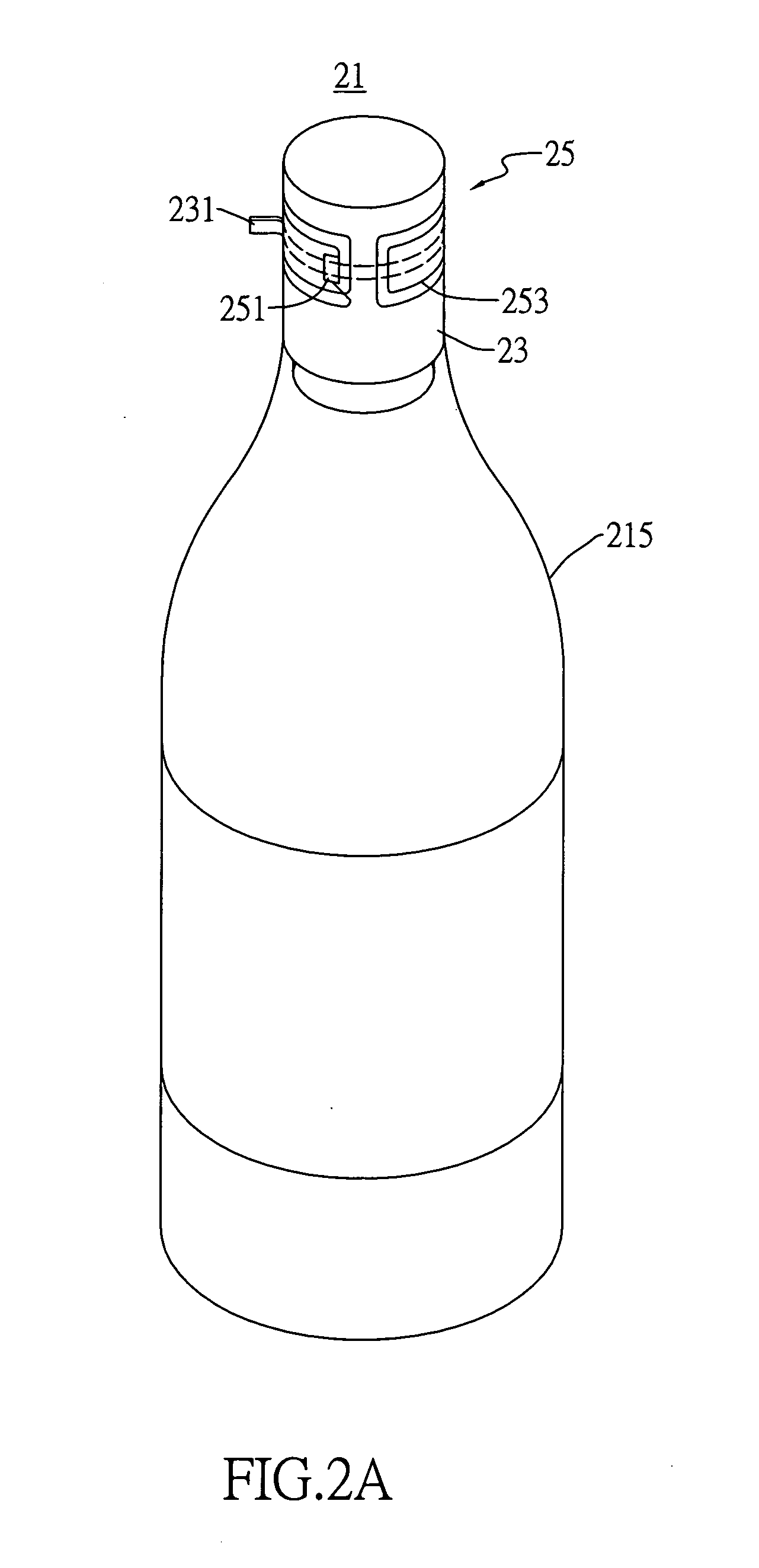
InactiveUS20060139173A1Easy to manageProtect reputationStampsRecord carriers used with machinesMembrane configurationOverwrap
An anti-counterfeiting apparatus capable of remote identifying is provided. It mainly sets a membrane on an outer package of a product, and an identifying module capable of remote identifying is set on the membrane such that in a process of transmitting, transporting, and managing the product, an outer apparatus is used to read stored product data by the identifying module thereby easier controlling the product. Further, when using and sealing off the product, the identifying module can be destructed or removed at the same time to remove its identifying ability. Although the outer package of the product is refilled fake or counterfeited product to be sold, since the membrane or the identifying cannot be read again, normal product transaction cannot be done thereby easily distinguishing real or counterfeited products.
Owner:FANG CHIEN HSING +1
Anti-foreign object structure for a liquid container pump
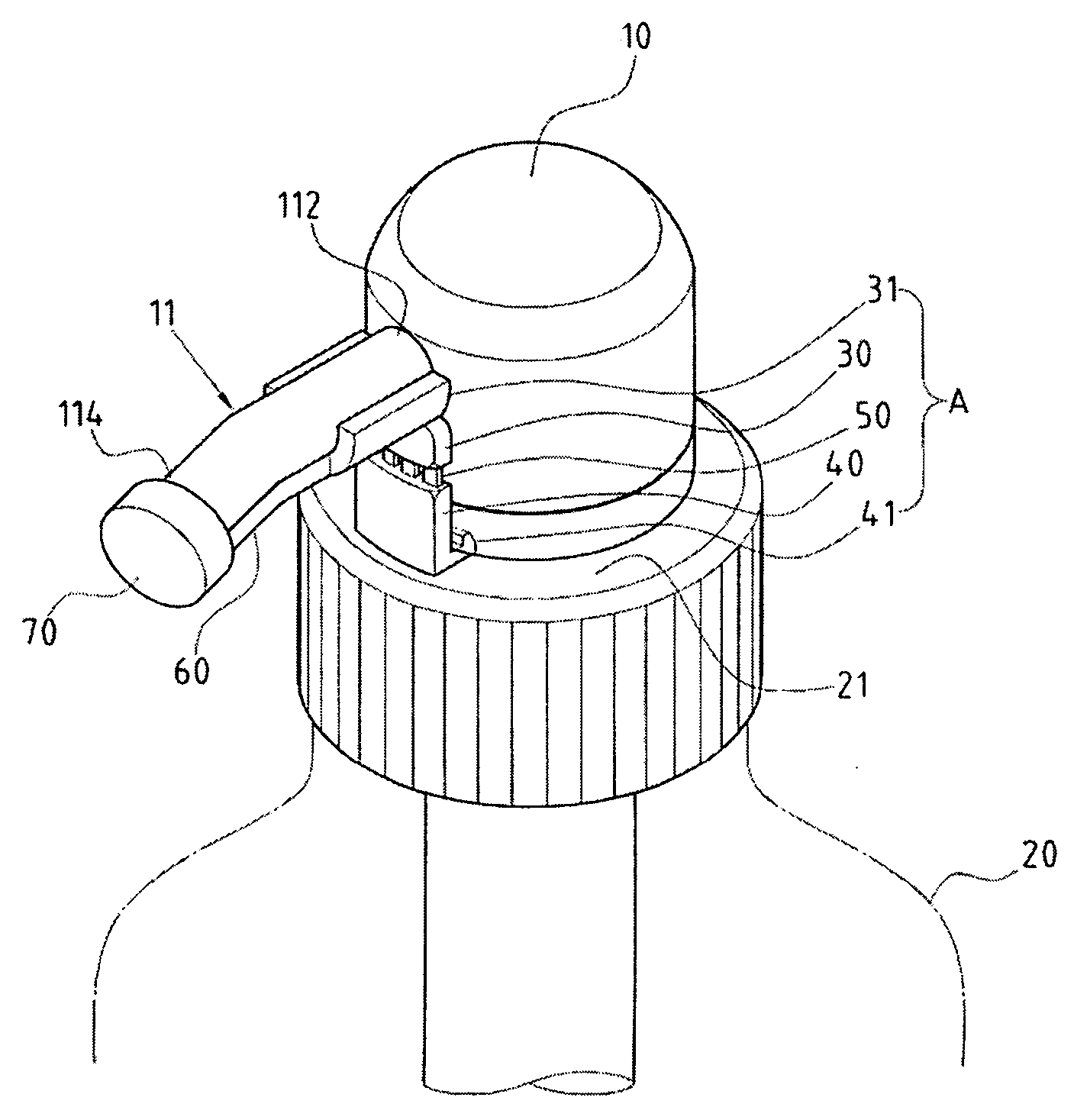
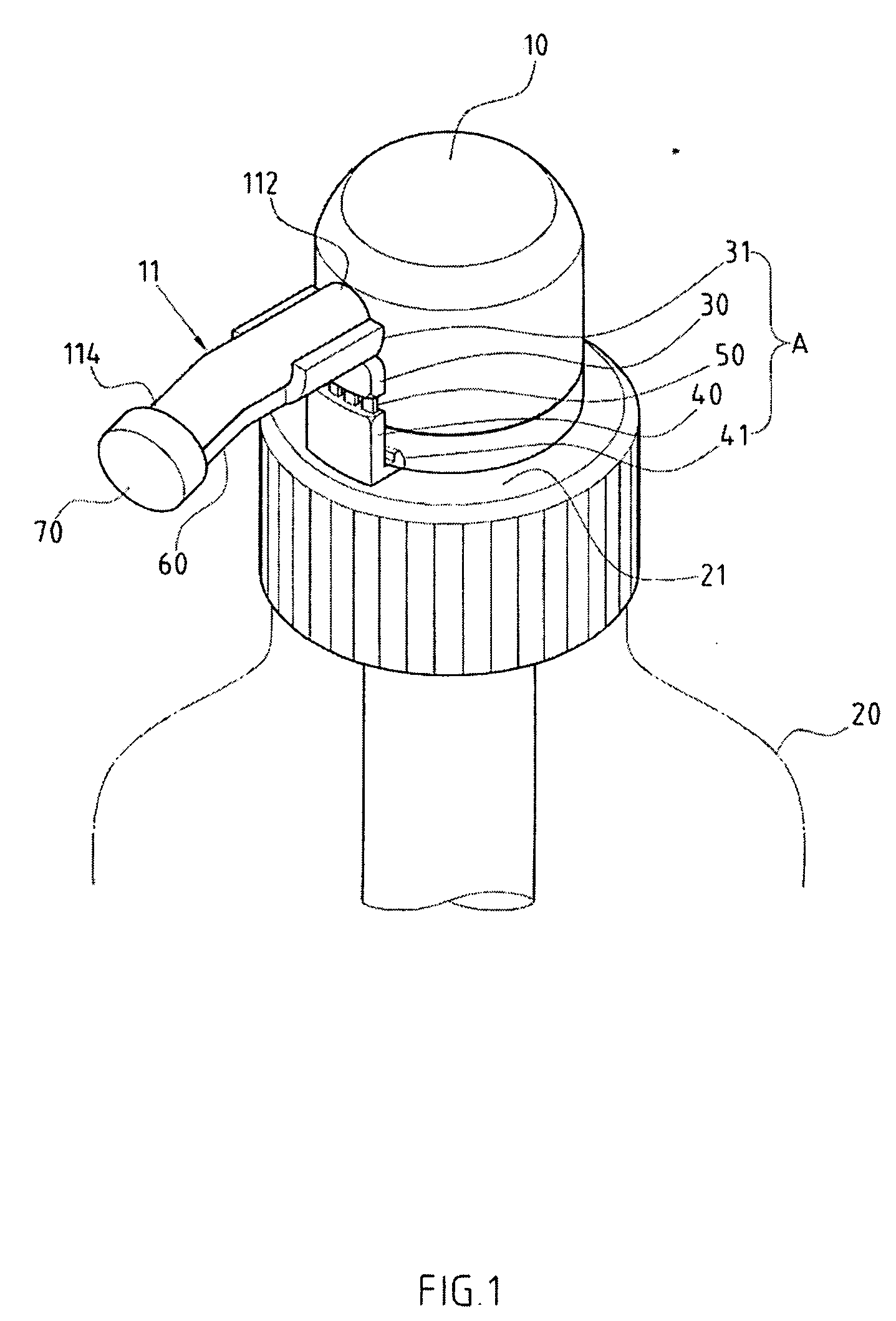
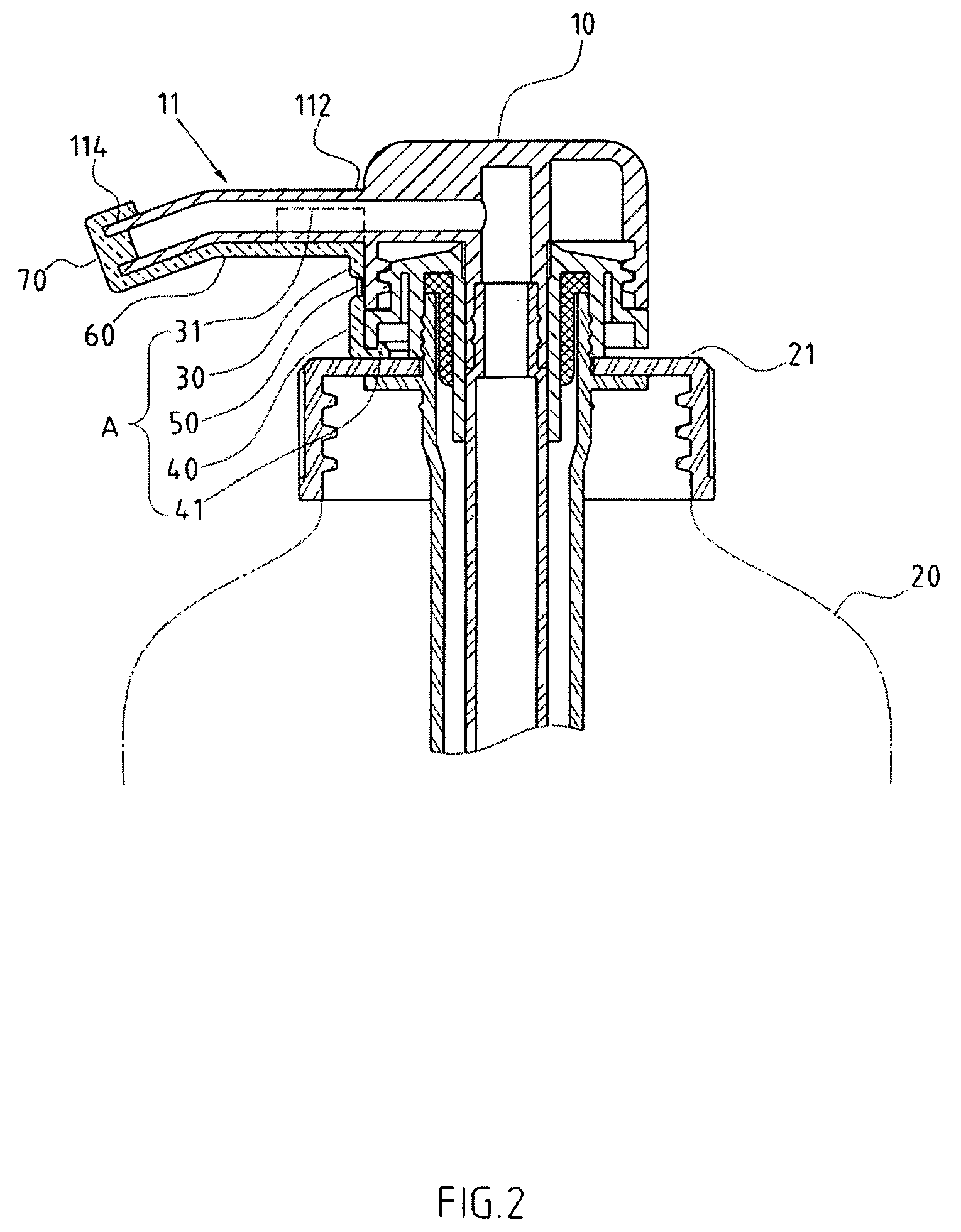
InactiveUS20070102449A1Improve liquid qualityProtect reputationDecorative coversClosure decorative/protective coversForeign matterEngineering
The structure that can keep a foreign object from coming into the container for the pump of the liquid container is focused on solving the dust accumulated inside the container before being sold. An anti-lock device is placed between the pump and the tip of the bottle, which includes an upper stopper, lower stopper, and a pre-snap rib. The upper stopper has a limit stopper that is placed at the end of the outlet tube of the pump, and the lower stopper is placed on the opening of the bottle. The pre-snap rib is placed between the upper and lower stopper. An extension part is placed on the upper stopper that extends to the outlet of the outlet tube, and a sealable lid is placed at the end of the extension part that can seal the outlet of the outlet tube.
Owner:LIVING FOUNTAIN PLASTIC IND CO LTD
Advocate for Facilitating Verification for the Online Presence of an Entity
ActiveUS20130160089A1Facilitate online verificationConvenient verificationMemory loss protectionError detection/correctionIdentity theftComputer science
Some embodiments provide an advocate system to facilitate automated online presence verification for different entities on behalf of the entities. The advocate system places service providers on notice that profiles and information hosted by them and that form the online presence for a particular entity should first be verified with that particular entity. The advocate system further facilitates online presence verification by 1) directly or indirectly connecting the service providers that are placed on notice with the appropriate authoritative entities to facilitate the verification of the profiles and information, 2) selectively targeting service providers hosting profiles and information that are unverified, 3) automatedly verifying hosted profiles and information based on a verified profile lists and verified information that authoritative entities provide to a central repository. In so doing, the advocate system prevents potential damage to the authoritative entity's credibility while also mitigating potential for fraud, identity theft, etc.
Owner:DUN & BRADSTREET EMERGING BUSINESSES
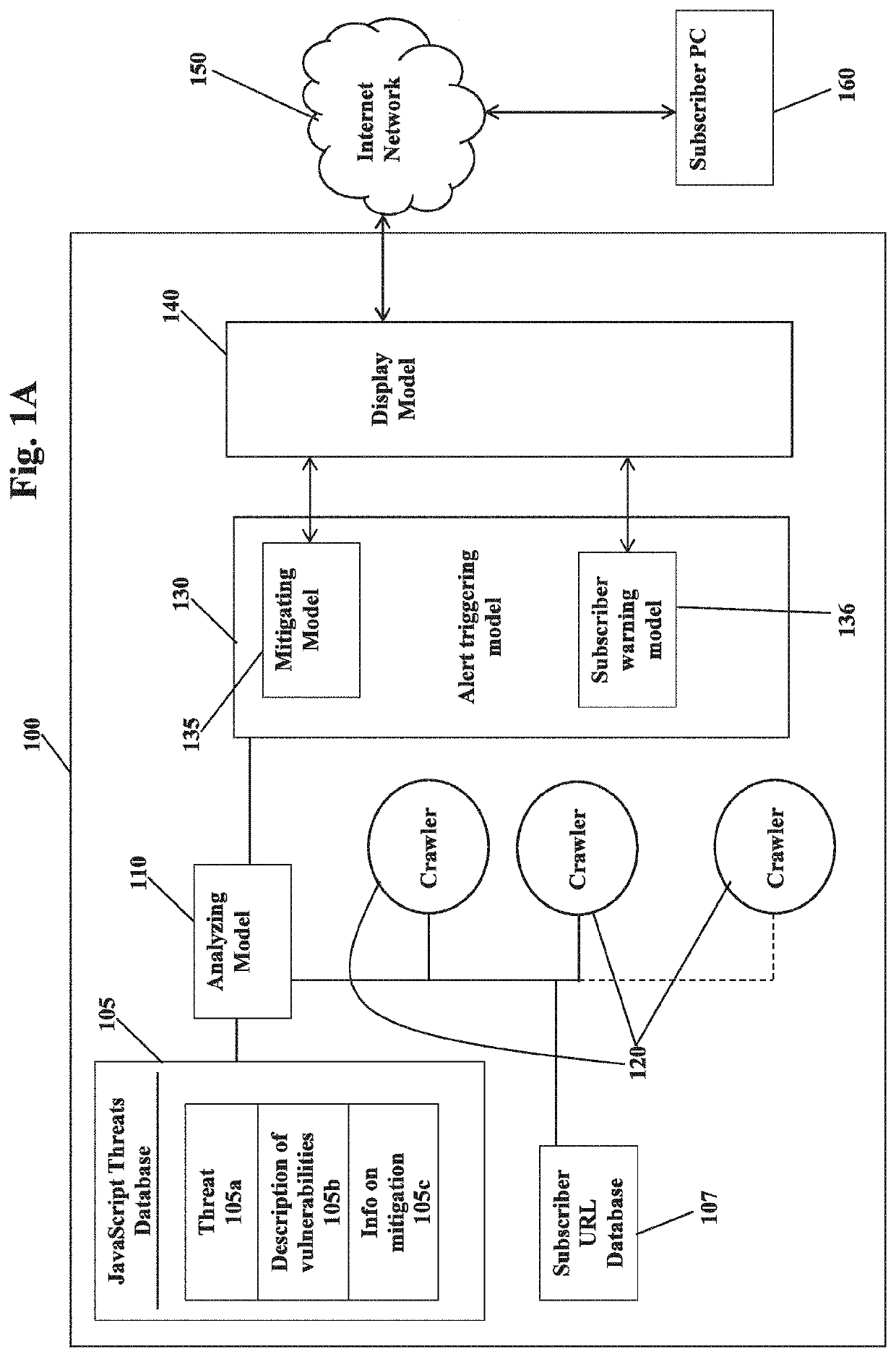
Online assets continuous monitoring and protection
PendingUS20200125729A1Protect the brandProtect reputationWeb data indexingError detection/correctionInternet privacyEngineering
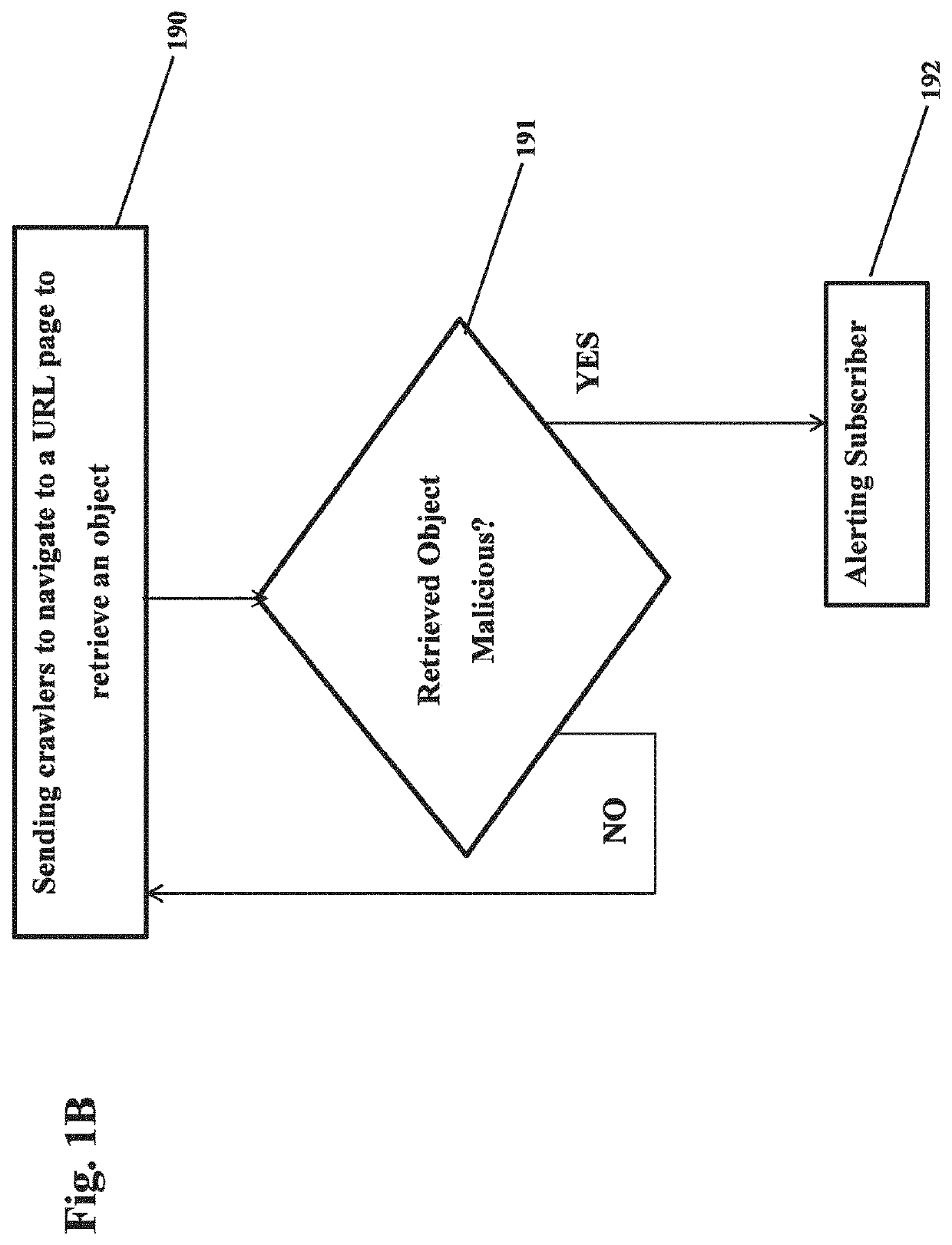
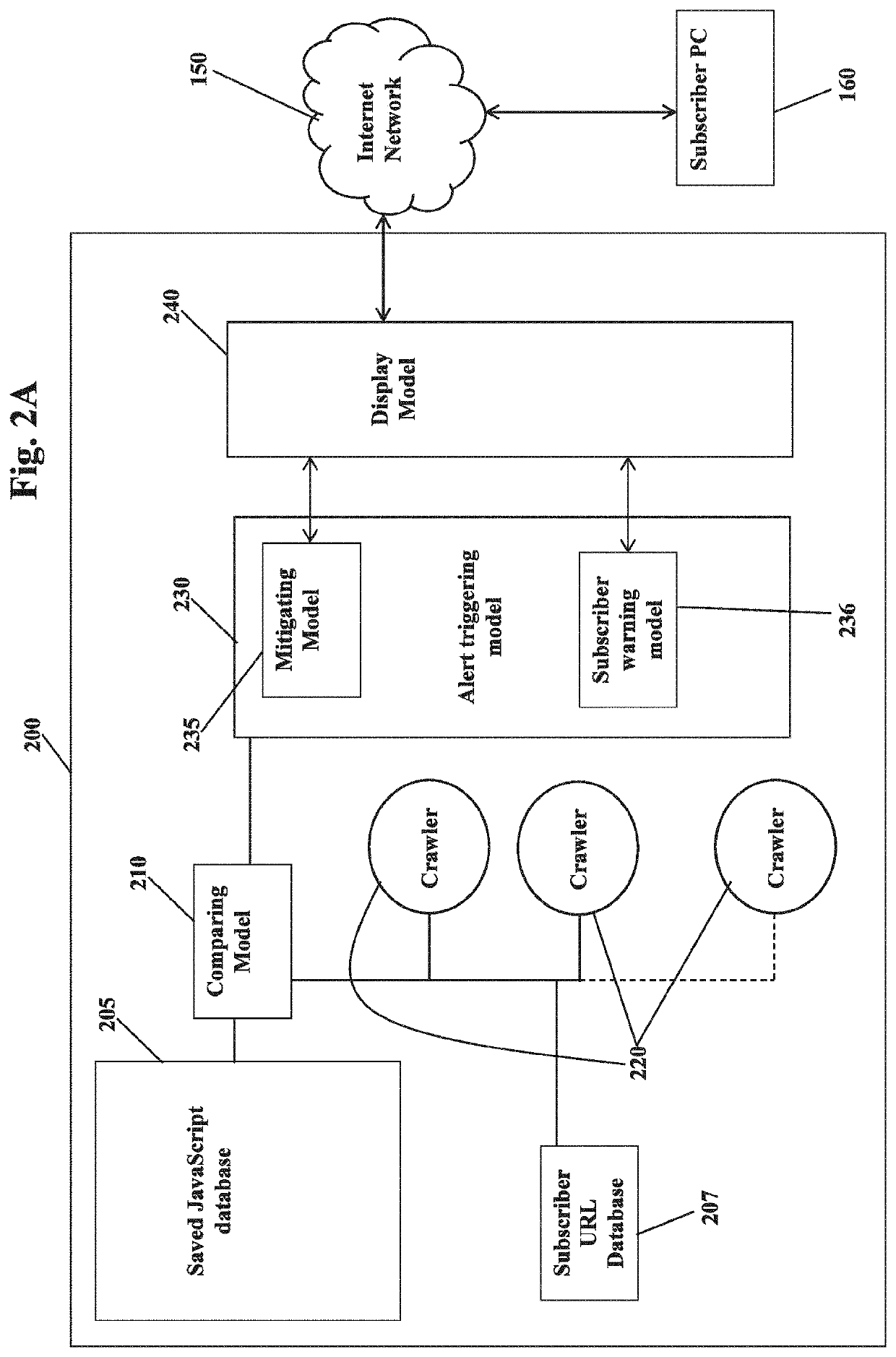
The present invention relates to a method and system for monitoring webpages for detecting malicious contents. According to a preferred embodiment the method comprises A) providing a plurality of URLs provided by a subscriber, employing a crawler to visit a URL webpage of said plurality of URLs; B) retrieving an object from said URL webpage by said crawler; C) analyzing said object retrieved by said crawler from said URL webpage, and determining whether said object retrieved is malicious or not; and D) alerting the subscriber, when said retrieved object is deemed malicious. According to one embodiment, the method further comprises E) employing a crawler to visit a URL webpage of a following URL of the plurality of URLs, when the determination of step C) is deemed not malicious; and F) returning to step B).
Owner:CYBERINT TECH LTD
Jade nondestructive detection sample model and manufacturing method thereof
ActiveCN103983492AMeet teaching needsMeeting Research NeedsPreparing sample for investigationRaman scatteringCarbon filmLight dispersion
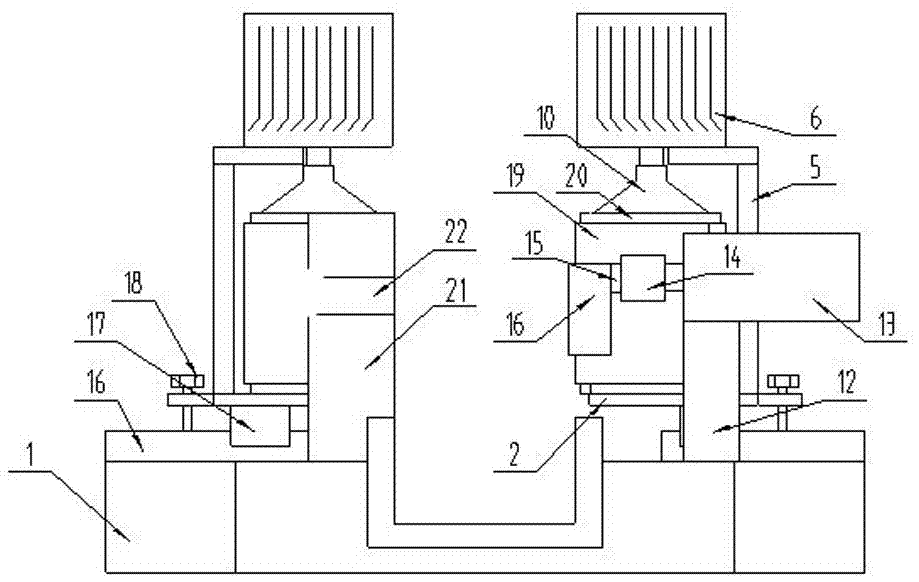
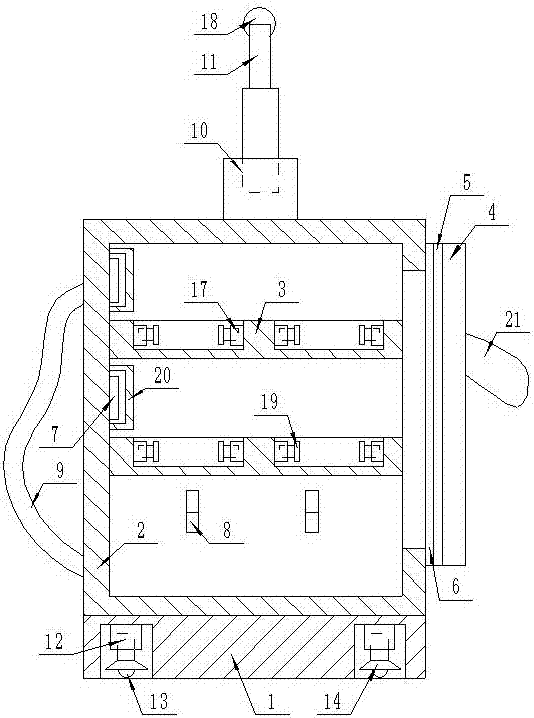
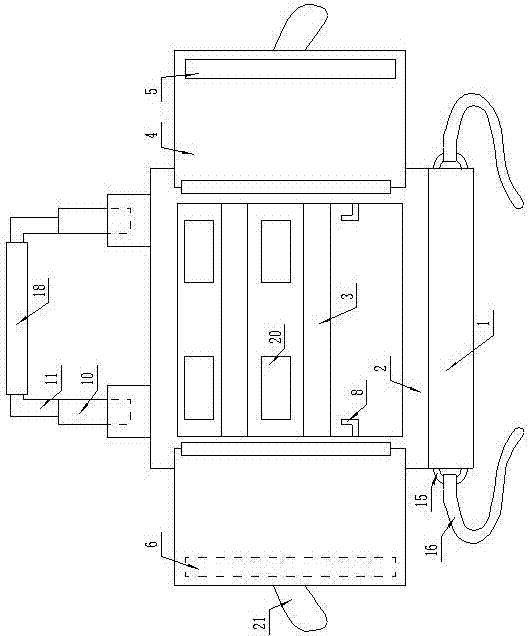
The invention discloses a jade nondestructive detection sample model and a manufacturing method thereof. The sample model comprises a jade model plate, wherein a smooth planar area, a bucket-shaped thinned area, a concave thinned area, a concave gold film area, a concave carbon film area, a cylindrical thinned area, a penetrability varying area, a light dispersion prism area, a raw material remain area, a cutting remain area, a color vector area, a special lighting area and a marking area are arranged on the jade model plate. The manufacturing method of the sample model comprises the following steps: A. selecting materials; B. cutting; C. polishing; D. carving; E. polishing; F. labeling an ingredient labeling area, a name labeling area, a lattice labeling area and a color vector area depending on a detection result; G. finishing manufacturing of the sample model, and packaging. The sample model disclosed by the invention fills the blank that the fields of domestic and international jade detection and identification teaching and research fail to acquire 15 specified national standard data and conclusions rapidly on the premises of not dividing a sample and not changing state of the sample detected.
Owner:温新续
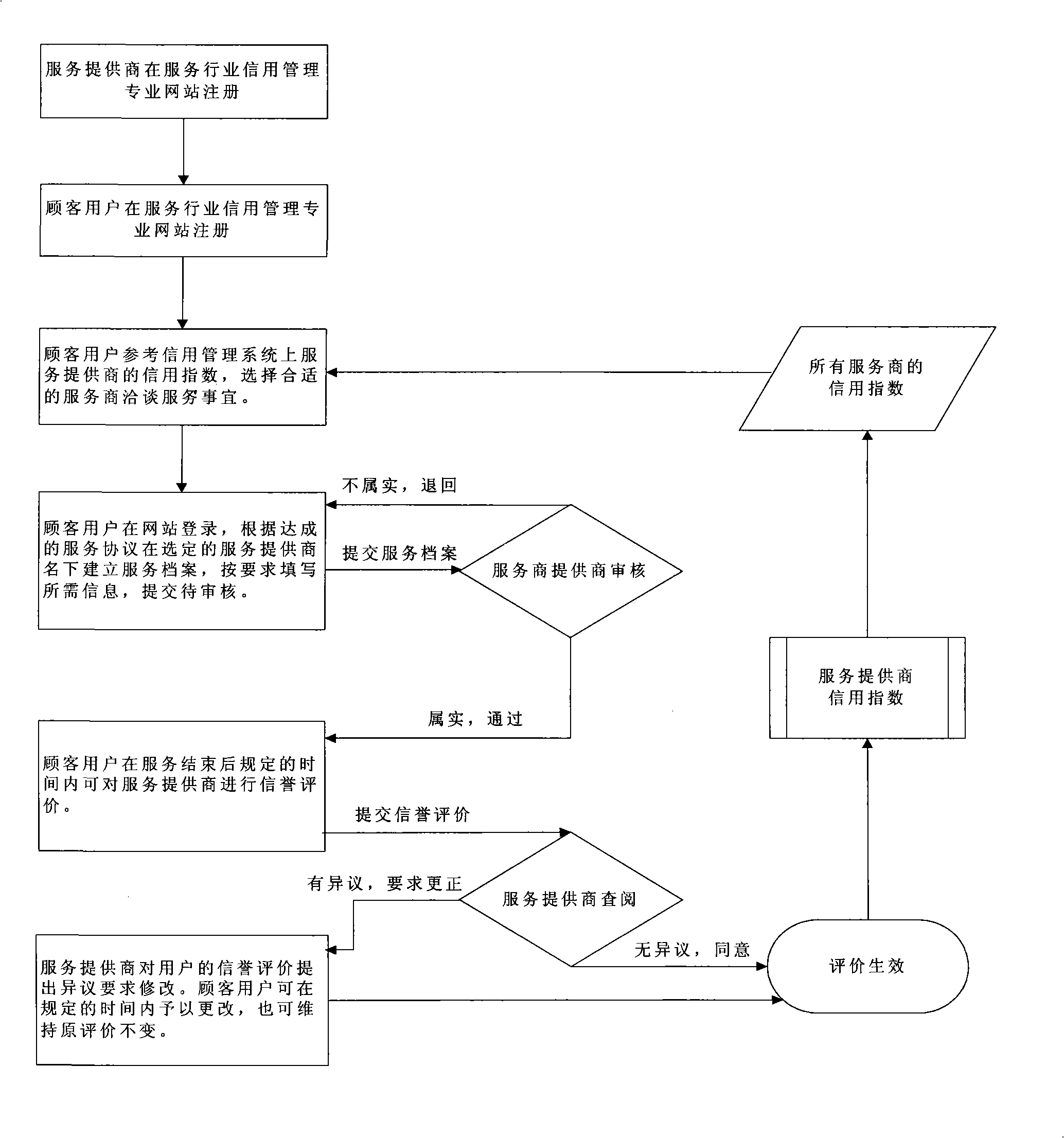
Method for reflecting ISP internet credit rating using internet
InactiveCN101281638AProtect reputationRestricted behaviorMarketingProtocol for Web Description ResourcesService provider
The invention discloses a method for reflecting the creditability of the service provider by the Internet, wherein the service provider registers to build a commercial account in the web, while the customer registers to build a personal account in the web and builds the service file according to the service protocol signed with the service provider; the service provider checks the service file, only the real customer passing through the approval of the service provider can perform the credit rating to the service provider in the scheduled time after completing the service. If the service provider has different opinions on the credit rating by the customers, the service provider can give clear indication of the reason to ask the customers to correct, and the customer determines whether to correct in the scheduled time. The credit managing system converts the credit rating of the customer to the credit index of the service provider according to the rules. The invention ensures the reality of the customers, solves the problems of the network false rating through the service provider to check the service file filled by the customer according to the service protocol.
Owner:太族网络科技(上海)有限公司 +1
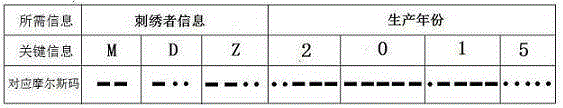
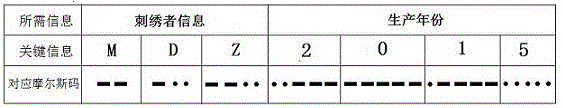
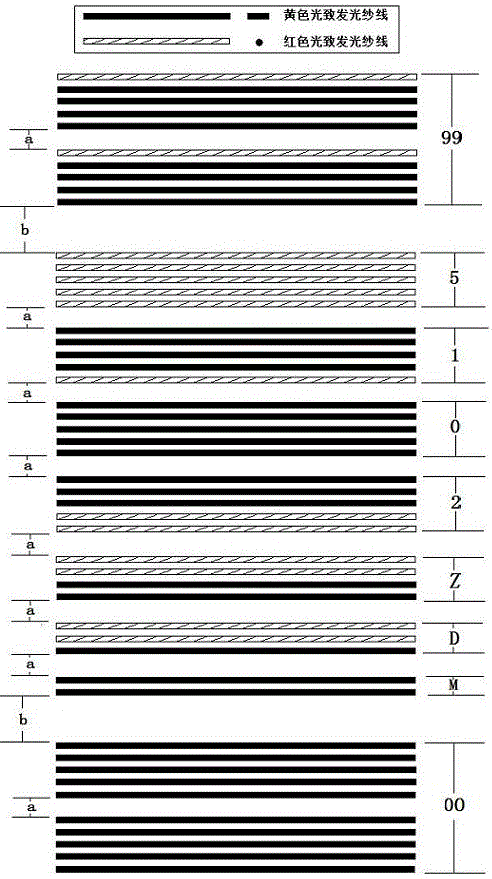
Anti-fake Sichuan embroidery cloth based on photoluminescence yarn and Morse code and manufacturing method thereof
InactiveCN105177815AQuality improvementProtection of rights and interestsWoven fabricsEmbroidering machines apparatusTime informationPhotoluminescence
The invention discloses anti-fake Sichuan embroidery cloth based on photoluminescence yarn and a Morse code and a manufacturing method thereof. Satin weave, twill weave and plain weave are adopted, the photoluminescence yarn serves as characteristic yarn capable of being inspected and identified, ordinary yarn serves as main yarn of the embroidery cloth, the identity information of an embroiderer and embroidery time information which are represented by the Morse code are shown through the arrangement of the characteristic yarn and the main yarn so as to be internalized into fabric, the embroidery cloth is tested for identification through a corresponding detection instrument, and then Sichuan embroidery fake resisting and quality tracking purposes are realized. According to the anti-fake Sichuan embroidery cloth, the photoluminescence yarn which is invisible under daily illumination and displays color only under the irradiation of a specific light source is adopted, the overall attractiveness of Sichuan embroidery products is not affected, invisible fake resistance is achieved, and the aesthetics completeness of Sichuan embroidery products is guaranteed.
Owner:SICHUAN UNIV
Service life monitoring device of wear-and-tear component, and intelligent electric appliance
ActiveCN106485304APrevent tamperingProtection of legal rightsCo-operative working arrangementsMicrocontrollerEngineering
The invention discloses a service life monitoring device of a wear-and-tear component. The service life monitoring device comprises a trusted platform module, a separated electronic tag mutually communicated with the wear-and-tear component, a connection bridge and a single chip microcomputer, wherein one end of the connection bridge is in two way communication with the separated electronic tag, and the other end of the connection bridge is in safe communication with the trusted platform module; and the single chip microcomputer controls the trusted platform module. The electric energy acquisition unit of the separated electronic tag utilizes the induction signal of an antenna to obtain electric energy and has a two-stage voltage regulation function. A near-field communication technology is combined with a TPM (Trusted Platform Module) technology to be applied to the intelligent electric appliance, and high-safety protection is realized for the service life and the fake prevention of the wear-and-tear component in the intelligent electric appliance; in addition, the separated electronic tag is of a separated design, so that the electronic tag can be recycled, and energy saving and environment protection are realized; meanwhile, the service life of the wear-and-tear component can be prevented from being tampered to achieve a purpose on protecting the legitimate interest of customers, protecting merchant reputation, protecting social environment and the like; meanwhile, the electric energy acquisition unit of the electronic tag also can automatically optimize and regulate a power supply electric quantity, the electricity supply demands of equipment can be further met, and loss is lowered.
Owner:上海周南科技有限公司
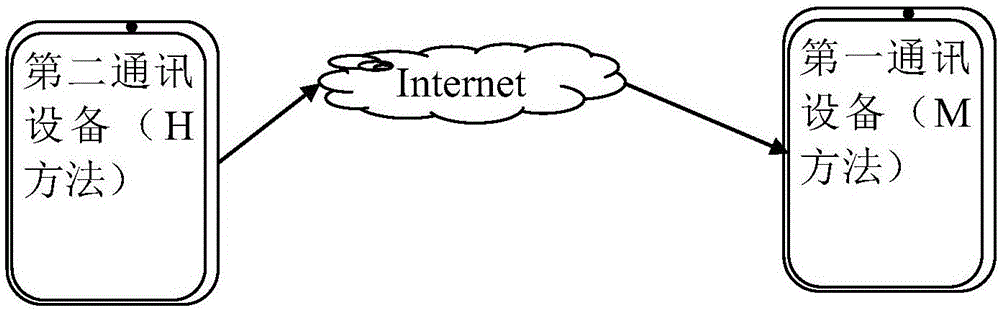
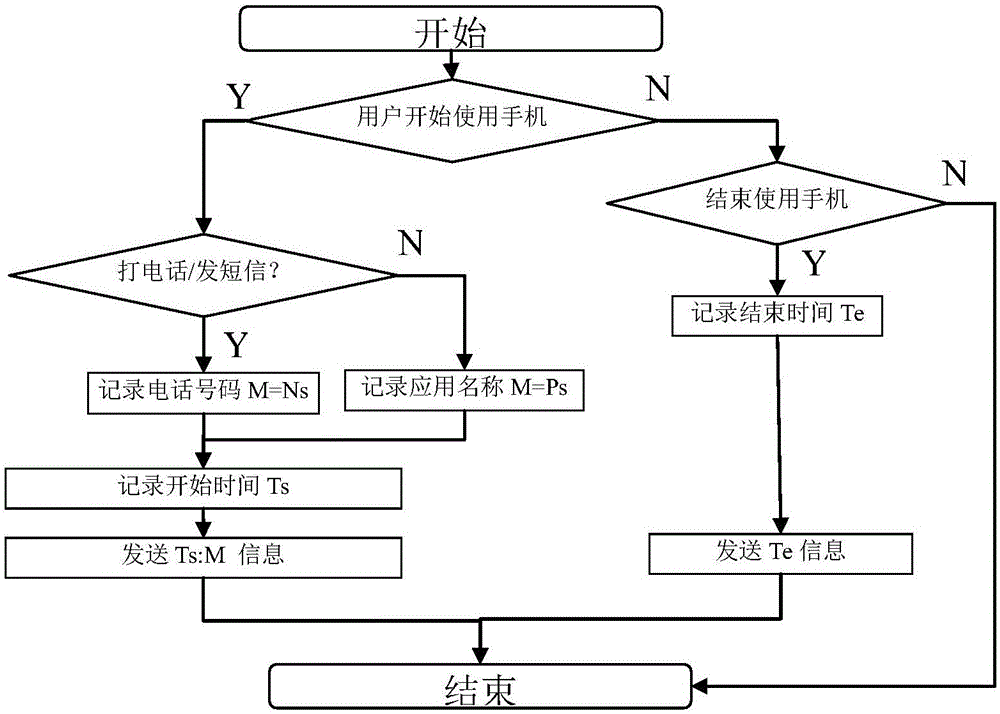
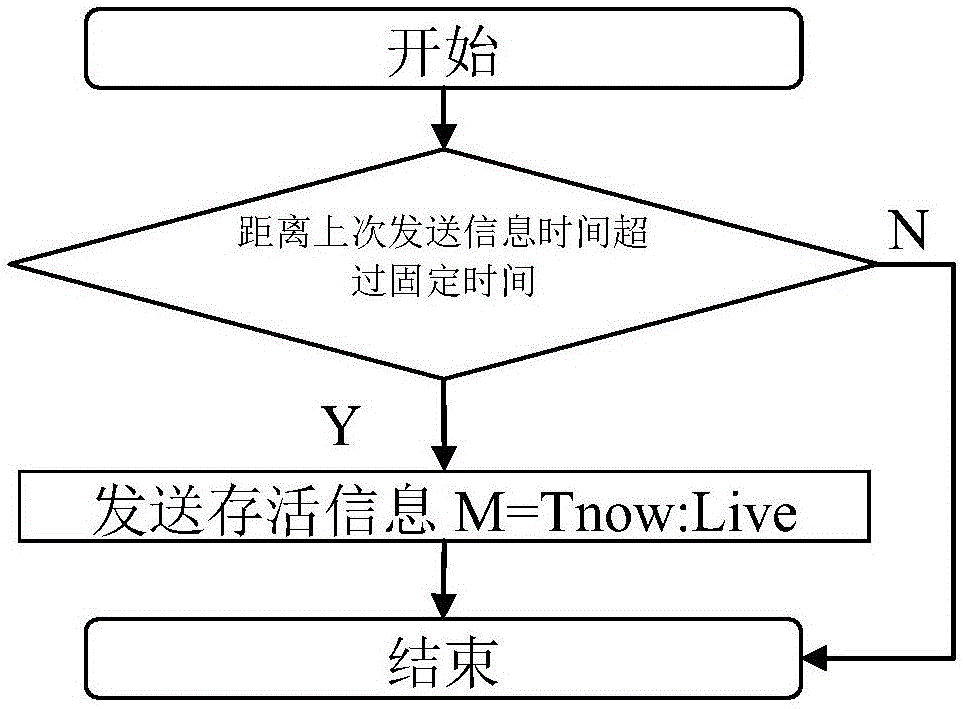
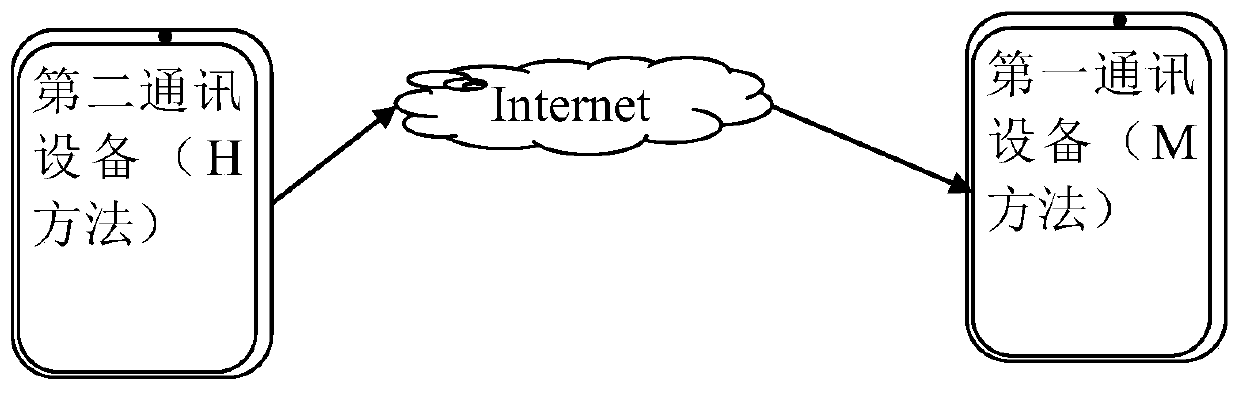
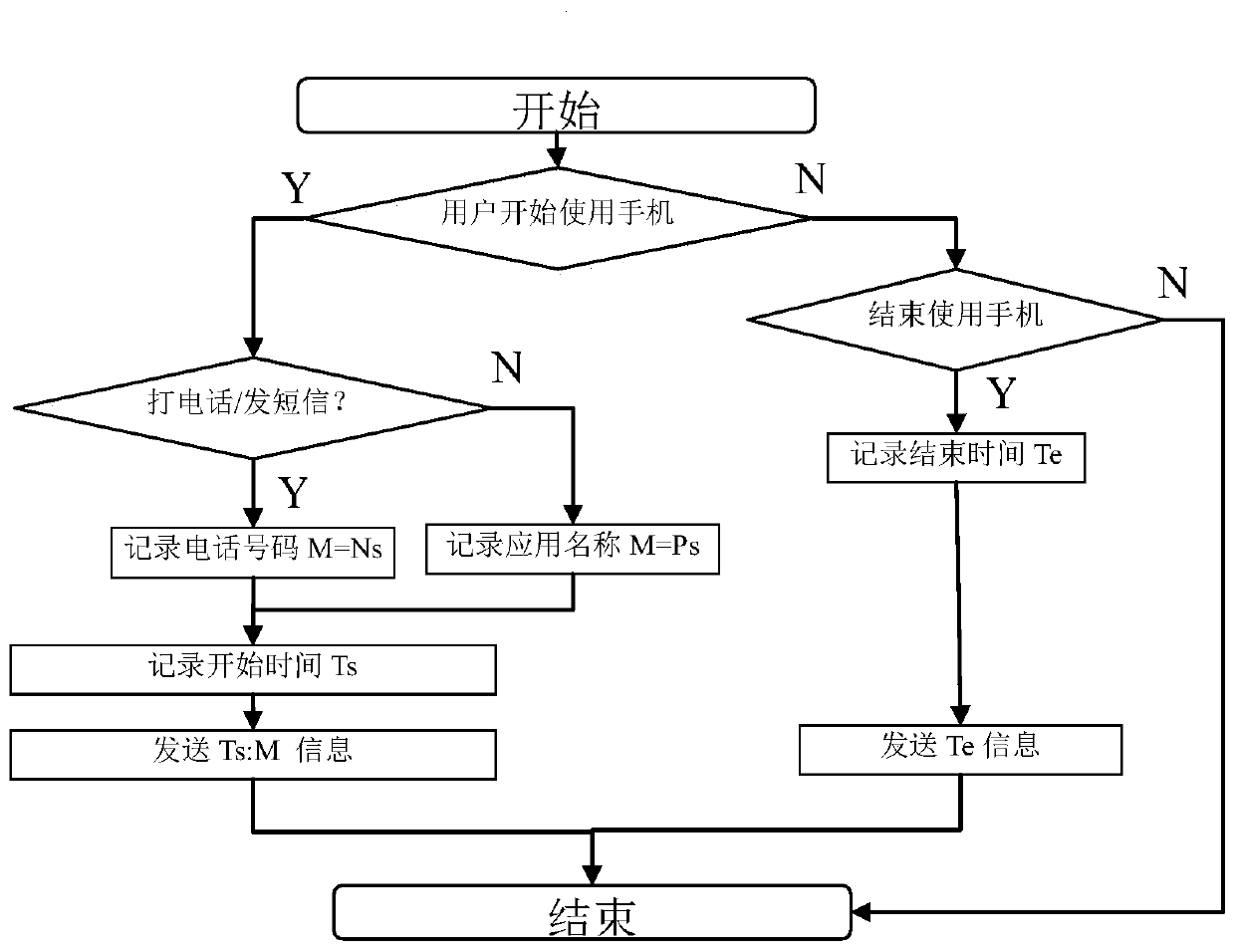
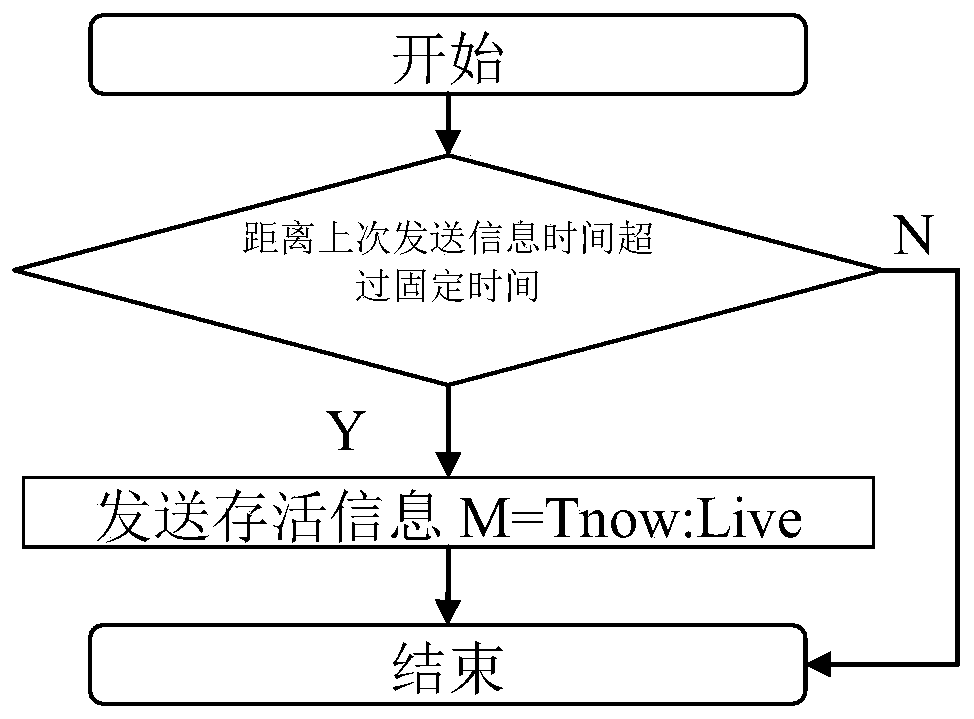
Method for sensing whether communication device is forgotten or not
ActiveCN106453894AProtect reputationLoss of protectionSubstation equipmentCurrent timeReal-time computing
The invention discloses a method for sensing whether a communication device is forgotten or not. The method comprises the steps that a first communication device receives usage data from a user of a second communication device, analyzes the usage data, determines a plurality of continuous usage time periods in which the second communication device is used, and judges whether current time is in certain continuous usage time period of the plurality of continuous usage time periods or not; if the current time is in the certain continuous usage time period and the number of survival information which is received by the first communication device and comes from the second communication device exceeds the preset fixed number, judging that the second communication device is forgotten, and the first communication device initiates a reminding signal; and when the first communication device initiates the reminding signal, the user of the first communication device obtains the second communication device and processes a communication event received by the second communication device. According to the method, the user of the first communication device can sense whether the second communication device is forgotten or not, initiates the reminding signal and can timely help the second communication device to process the communication event.
Owner:重庆蓝岸科技股份有限公司
Woven label for single and double layer clothing
PendingCN107672235AReduce staticProtect reputationStampsLayered productsEngineeringMultiple function
The invention provides a woven label for single and double layer clothing. The woven label comprises a woven label body, a sewing edge and cutting edges; the woven label body comprises a soft layer, abase fabric layer and an antistatic layer; the base fabric layer comprises a surface base fabric and inner base fabric, the surface base fabric is interwoven by face warp and face weft, the inner base fabric is interwoven by inner warp and inner weft, the antistatic layer is interwoven by tying warp and the face weft as well as the face warp respectively, the sewing edge is interwoven by first warp and first weft, the first warp and the first weft are interwoven into twill weave in a one-upward and three-downward manner, the twill weave includes warp interweaving points and weft interweavingpoints, an anti-fake label is arranged on the weft interweaving points, the cutting edges are arranged at two ends of the sewing edge, and a plurality of cutting threads is arranged at one ends of thecutting edges and away from the sewing edge. The woven label has the advantages of multiple functions of anti-fake performance, high-temperature resistance, anti-static electricity and the like, comfort with skin contact is increased, and high practicability is achieved.
Owner:嘉兴市凯欣印刷股份有限公司
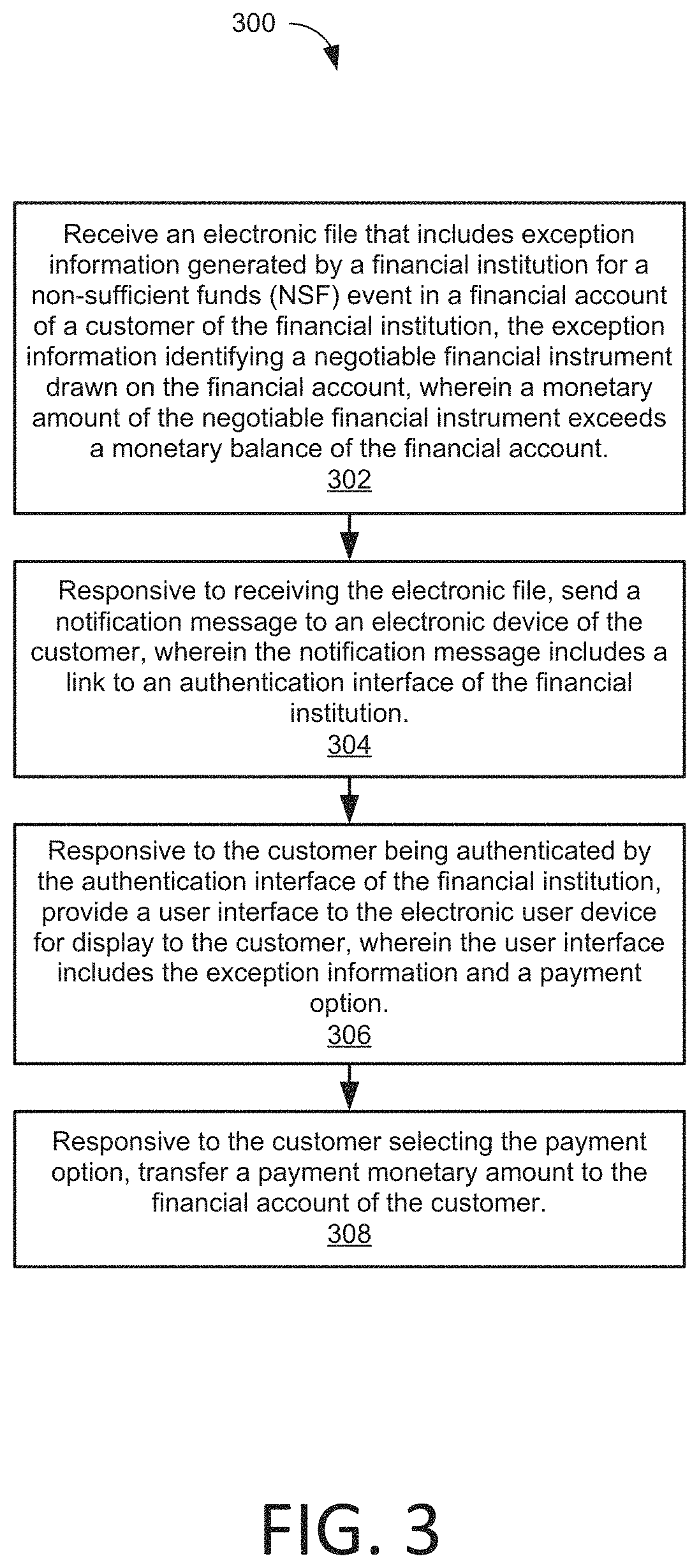
Alert management system with real-time remediation and integration with the exception originating system
ActiveUS11144917B1Minimizing expenseEasy to communicate in real timeTransmissionProtocol authorisationEngineeringManagement system
Owner:DOUBLE CHECK SOLUTIONS
Damping-force adjustable seat damper
PendingCN110145565AOil passage is simpleSimple structureSpringsSprings/dampers functional characteristicsStability of motionRelief valve
The invention discloses a damping-force adjustable seat damper. The damping-force adjustable seat damper comprises an outer cylinder, an inner cylinder, a piston assembly, a hollow piston rod, an adjusting structure, a guide structure and a compression valve, wherein the guide structure comprises a guide base and a guide oil seal, the bottom of the guide base is provided with a non-return sealingfin, and the non-return sealing fin is in interference fit with the hollow piston rod; and the adjusting structure comprises an adjusting rod and an adjusting pushing fork, the surface of the front end of the adjusting rod is provided with a transverse guide groove, one end of the transverse guide groove is provided with a confluence hole, and the hollow piston rod is provided with a guide hole. Asafety relief valve structure is adopted by the compression valve, and the compression valve comprises a valve seat, a valve sleeve, a valve element, a valve clack and a reset spring, wherein the valve clack is provided with a pressure releasing channel, and the valve element is provided with at least one damping valve plate matched with the pressure releasing channel. According to the damping-force adjustable seat damper, up-and-down movement stability of the piston rod can be further guaranteed by means of the guide structure, the making process of the adjusting structure is simple, and theadjusting stability is good; and it can be guaranteed that the damper is stable and reliable to use by means of the compression valve, and the repair rate is decreased.
Owner:杭州金士顿实业有限公司
Quotation sheet processing method and apparatus
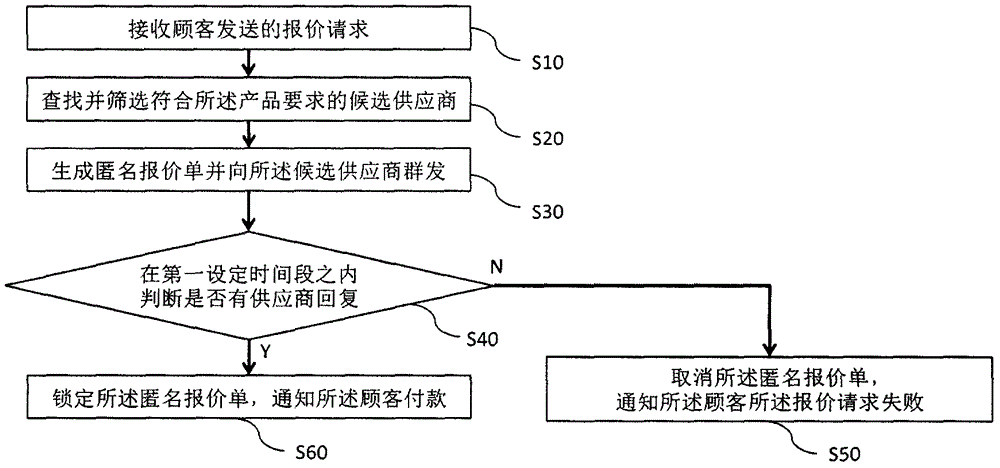
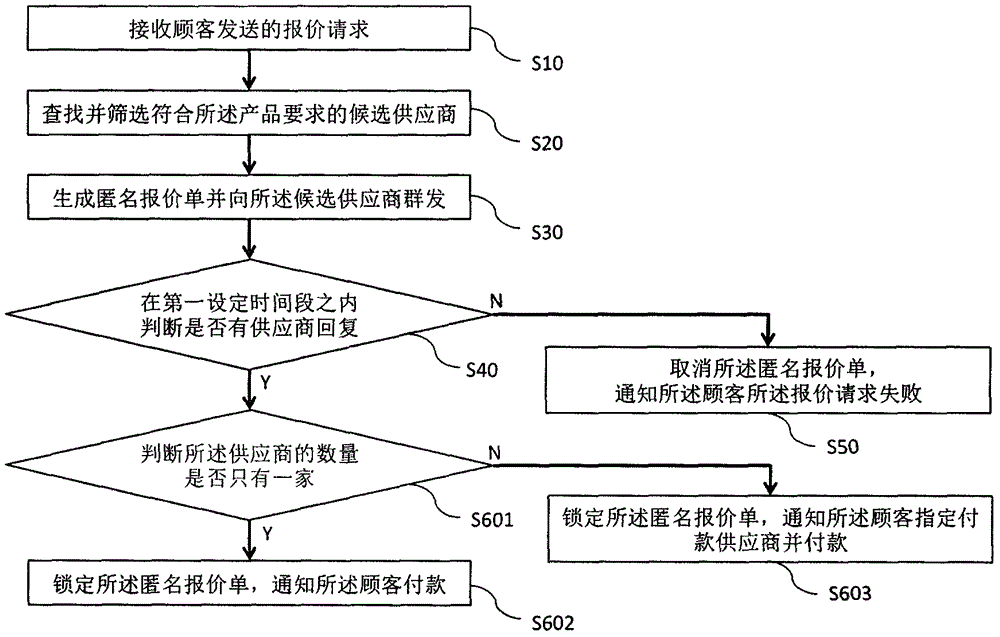
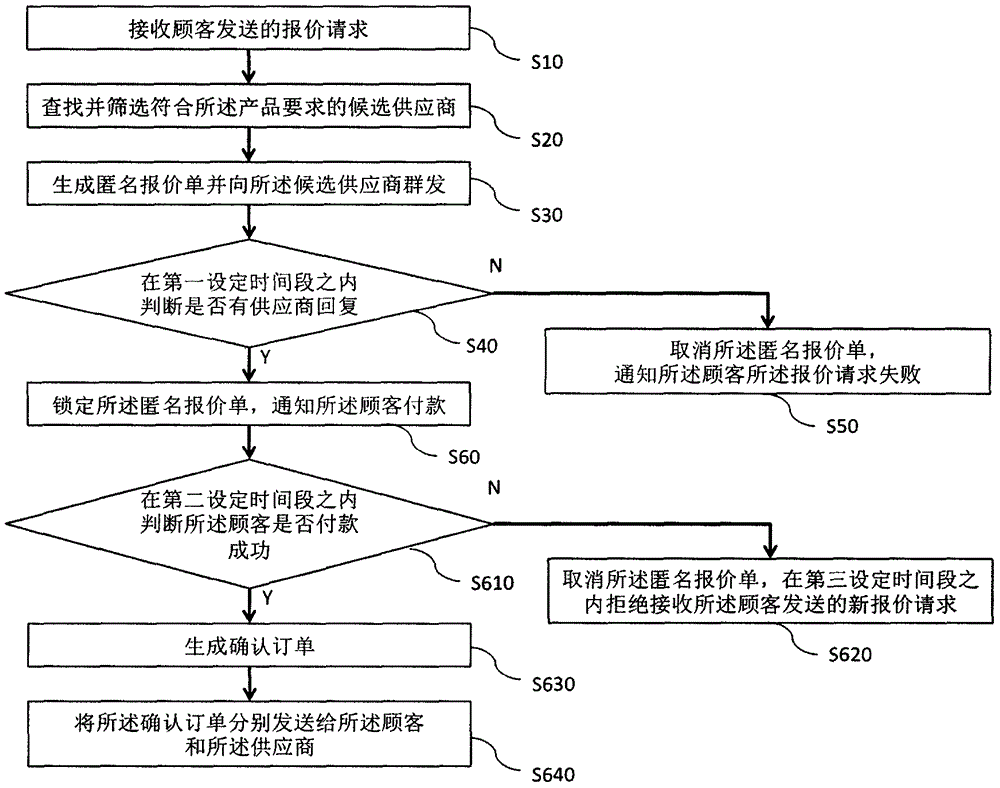
InactiveCN106447423ARaise the possibilityAvoid duplicationBuying/selling/leasing transactionsPaymentRequest for quotation
The invention discloses a quotation sheet processing method. The method comprises the steps of receiving a quotation request containing a product requirement and a corresponding product quotation and sent by a customer; searching for and screening candidate suppliers, wherein the product quotation is in a quotation interval of the candidate suppliers; generating an anonymous quotation sheet, and performing group sending of the anonymous quotation sheet to the candidate suppliers; in a first set time segment, judging whether a supplier makes a reply or not; if no supplier makes the reply, cancelling the anonymous quotation sheet, and notifying the customer that the quotation request fails; and if the supplier makes the reply, locking the anonymous quotation sheet, and notifying the customer to perform payment. The possibility of obtaining a really desired product by the customer is greatly increased, the repeated operation of resetting the quotation by the customer is avoided, the experience effect is improved, the loss of potential customers is avoided for the suppliers, and the reputation of the suppliers and the market balance are effectively protected.
Owner:白宇
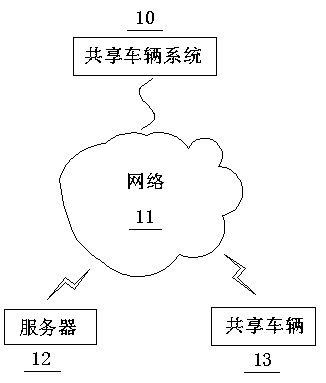
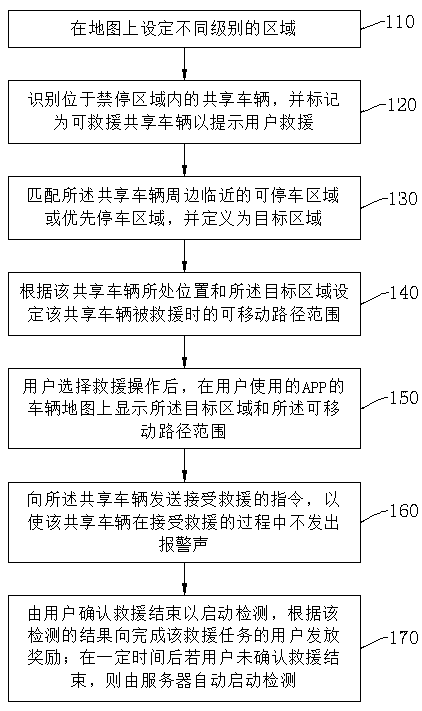
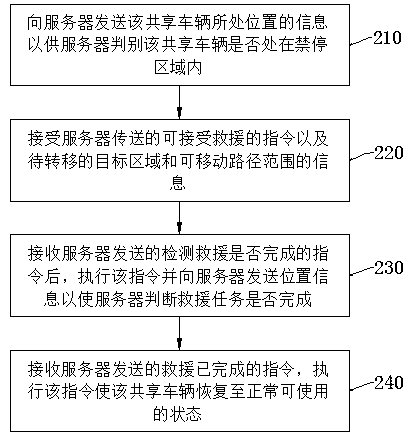
Shared vehicle, and improvement in antitheft system and method thereof
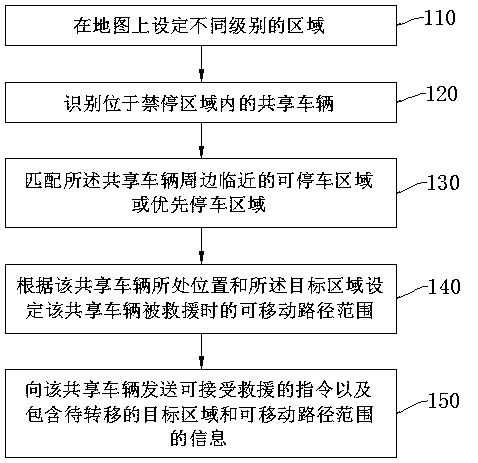
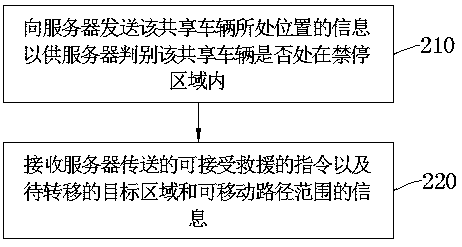
ActiveCN109410642AProtect reputationAvoid unwillingness to do goodParticular environment based servicesIndication of parksing free spacesParking areaReal-time computing
The invention discloses a method for improving a shared vehicle antitheft system. The method comprises: setting different levels of areas, including a parking forbidden area, on a vehicle map; identifying a shared vehicle located in the parking forbidden area, matching a parking area or a priority parking area in the vicinity of the shared vehicle, and defining the area as a to-be-located target area of the shared vehicle; setting a movable path range when the shared vehicle is rescued; transmitting an instruction of accepting the rescue to the shared vehicle and information including the to-be-located target area and the movable path range such that the shared vehicle is transferred to the target area through the movable path range and no alarm sound is emitted in the process. The methodavoids a phenomenon that the alarm sound of a rescue behavior causes the abnormal views of onlookers and thus causes good-hearted people or volunteers to be unwilling to provide help, thereby protecting the reputation of the good-hearted people. A corresponding system, a server, a vehicle and a device are also provided.
Owner:杭州智马科技有限公司
Milk tea bottle strength detection device
InactiveCN107402159APrevent flowProtect reputationMaterial strength using tensile/compressive forcesElectric machineryEngineering
The invention discloses a milk tea bottle strength detection device which comprises a mounting plate, wherein a pair of first brackets are mounted on the mounting plate; first vertical columns are mounted on the first brackets; first bearings are mounted on the first vertical columns; motor racks are mounted on the first brackets; rotating motors are mounted inside the motor racks; second vertical columns are mounted on the first brackets; second bearings are mounted on the second vertical columns; sleeves are mounted outside the second bearings; transmission tubes are fixed on the sleeves; and the transmission tubes are connected with driving ends of the rotating motors. By adopting the milk tea bottle strength detection device, a finished product bottle can be detected, the situation that damaged finished products caused by other problems are delivered to the market is avoided, and thus the reputation of a product can be protected.
Owner:安徽优乐亿乳业有限公司
Multifunctional take-out transport box
InactiveCN107323848AGuarantee the quality of transportationProtect reputationSealingShock-sensitive articlesMatched pairComputer engineering
Owner:钱红双
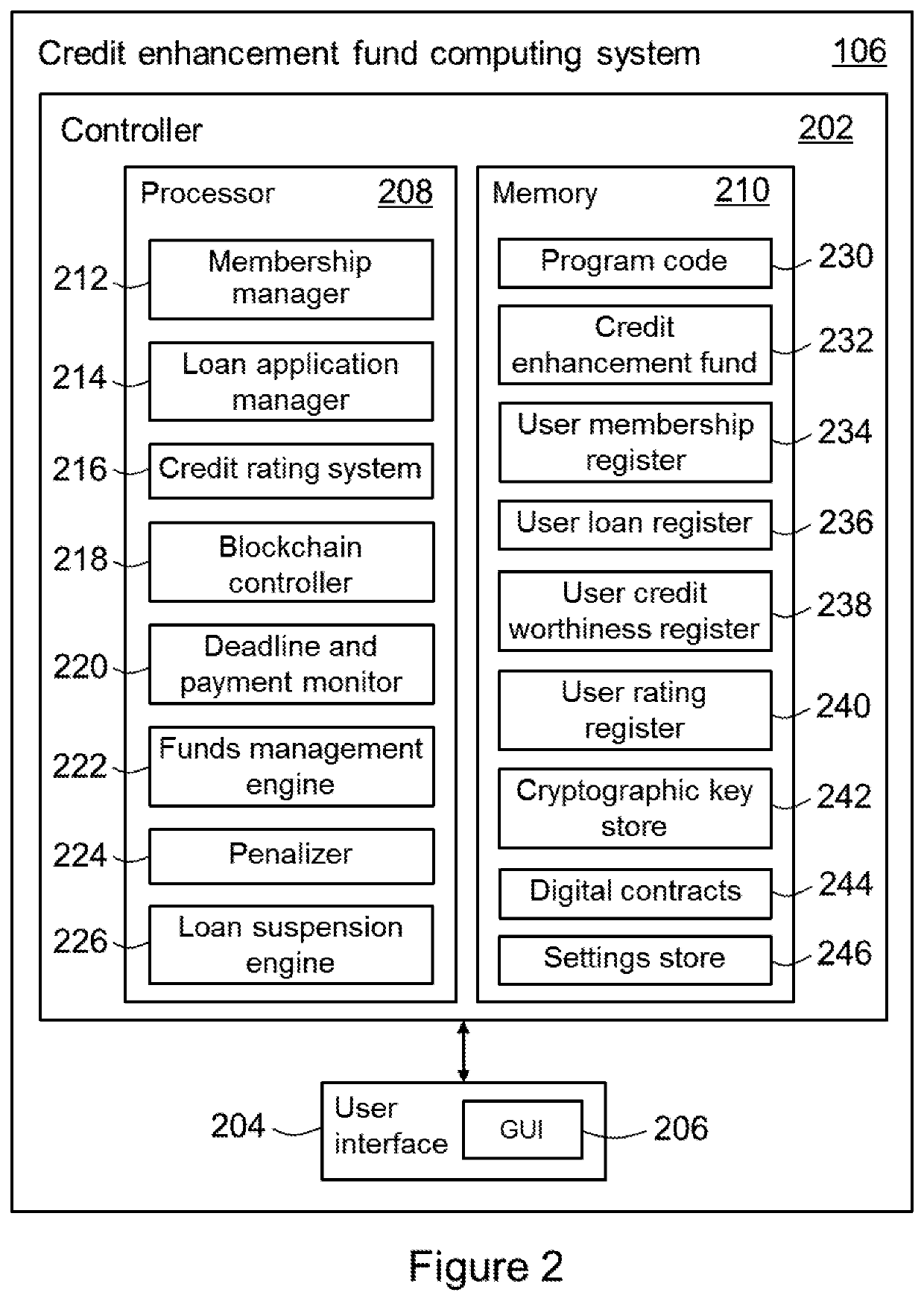
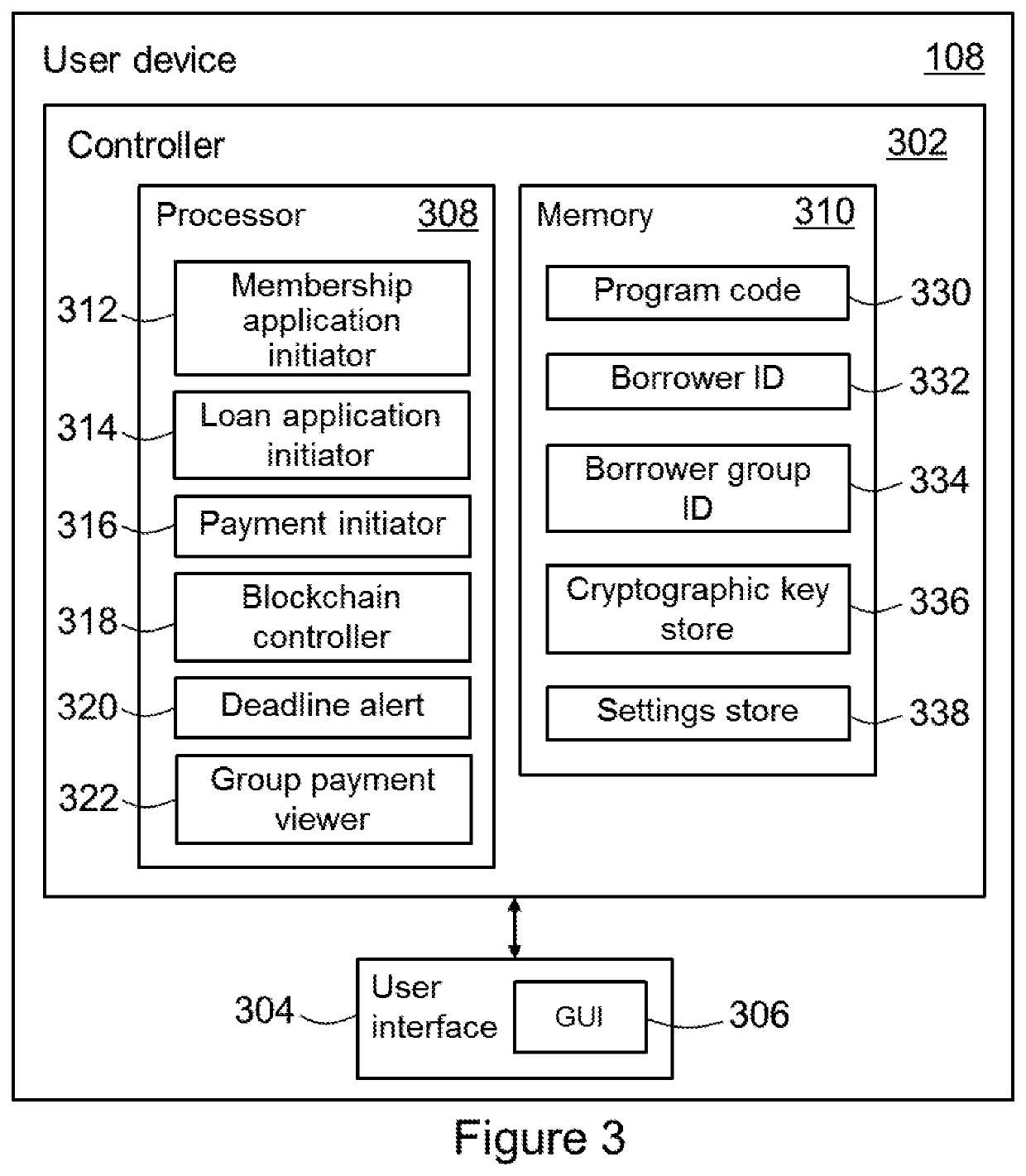
A blockchain-based credit management system
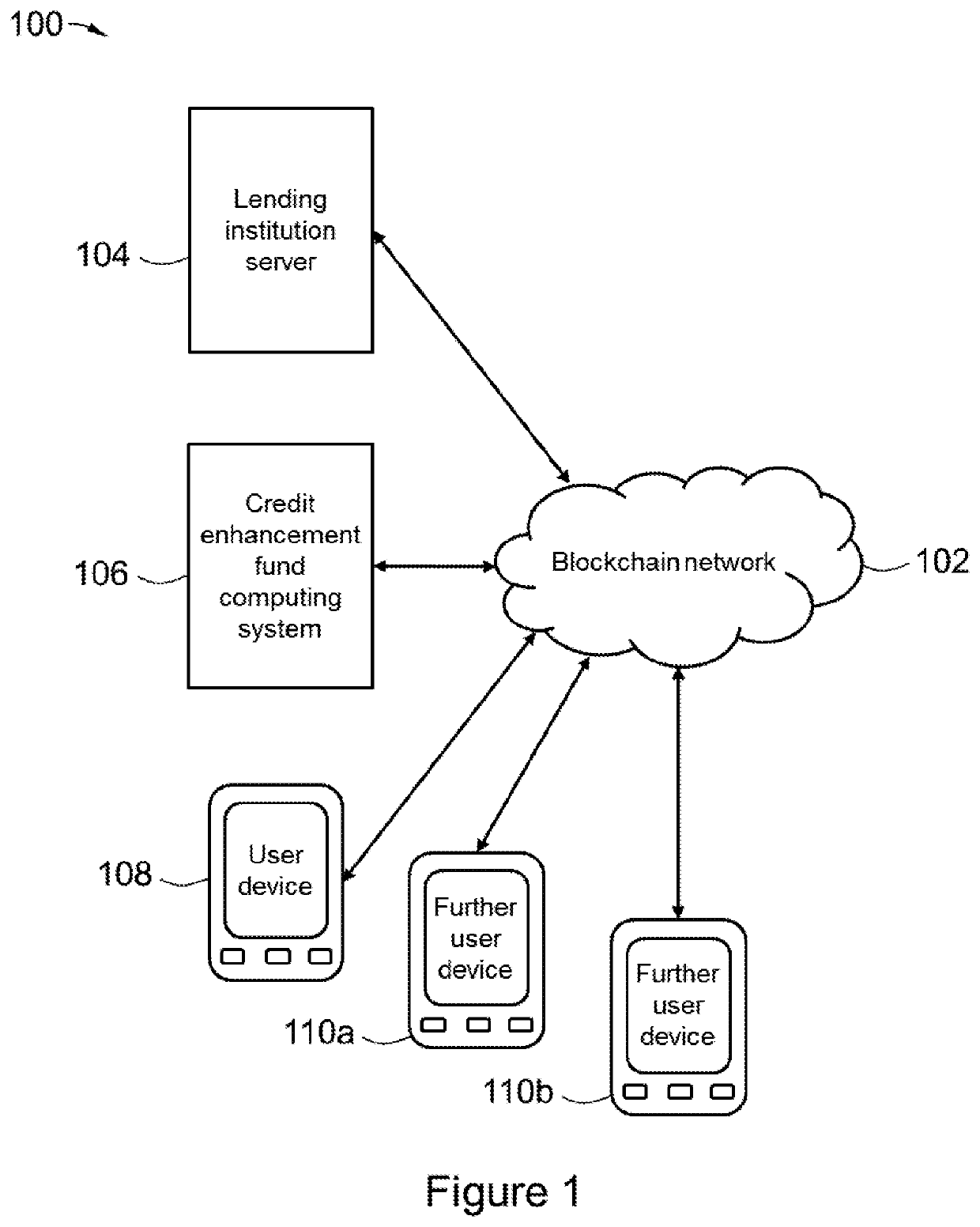
PendingUS20220180431A1Simple wayIncrease ratingsFinanceCryptography processingFinancial transactionData mining
A computer-implemented blockchain-based credit management method and system, the method includes: receiving one or more loan repayments from a user in a first transaction, the loan repayments being in respect of a first loan issued by a lender; receiving a fee from the user in a second transaction associated with the first transaction; transferring the loan repayments to the lender; transferring the fee to a loan insurance fund; registering at least the first transaction in a first blockchain of a blockchain network; determining a number of credit worthiness points based on at least timeliness of the first transaction relative to a first loan repayment schedule; and associating the number of credit worthiness points with the user in a third transaction and registering the third transaction in a second blockchain of the blockchain network.
Owner:ISLAMIC DEV BANK INST
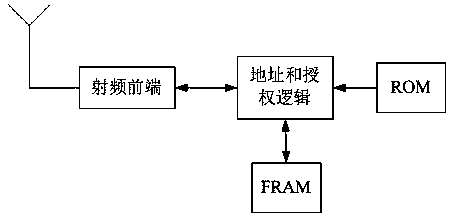
Method and product for discriminating seed authenticity by means of highly imitated seed with embedded electronic label
PendingCN107633281AReduce volumeReduce gravityCo-operative working arrangementsCommerceRadio frequencyAuthorization
The invention provides a method and a product for discriminating seed authenticity by means of a highly imitated seed with an embedded electronic label. The method comprises the steps of embedding theelectronic label into the highly imitated seed for manufacturing a highly imitated electronic seed of which the appearance is same with that of a common seed; placing the highly imitated electronic seed into a seed packaging bag and using the highly imitated electronic seed as an identification label of the seeds in the seed packaging bag; writing seed information by means of a reader; recordingthe ID number of the seed into an F-RAM storage array through controlling and authorization of the electronic label, wherein the ID number is the unique ID number of the seed; in seed authenticity discrimination, reading the seed packaging bag by means of the reader; and identifying the related information of the seed by the reader according to the ID number which is fed back from the highly imitated electronic seed. According to the method and the product, an RF identification non-contact reading characteristic is utilized for realizing terminal authenticity searching and hidden fleeing goodschecking. The method and the product settle the problems of easy forging and easy damage in false-proofing and fleeing goods preventing facilitates in a current seed industry.
Owner:XIJING UNIV
Call tracking using voice quality measurement probe
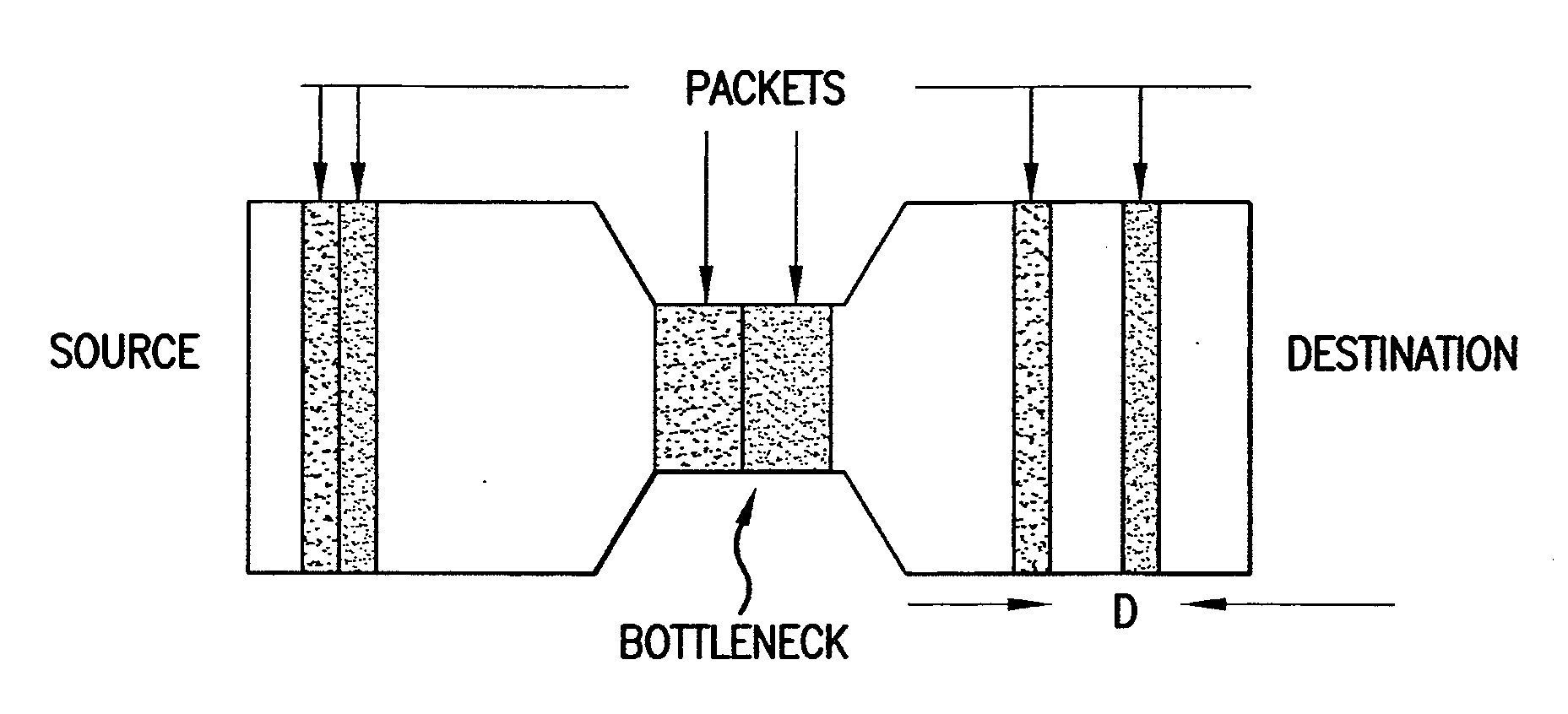
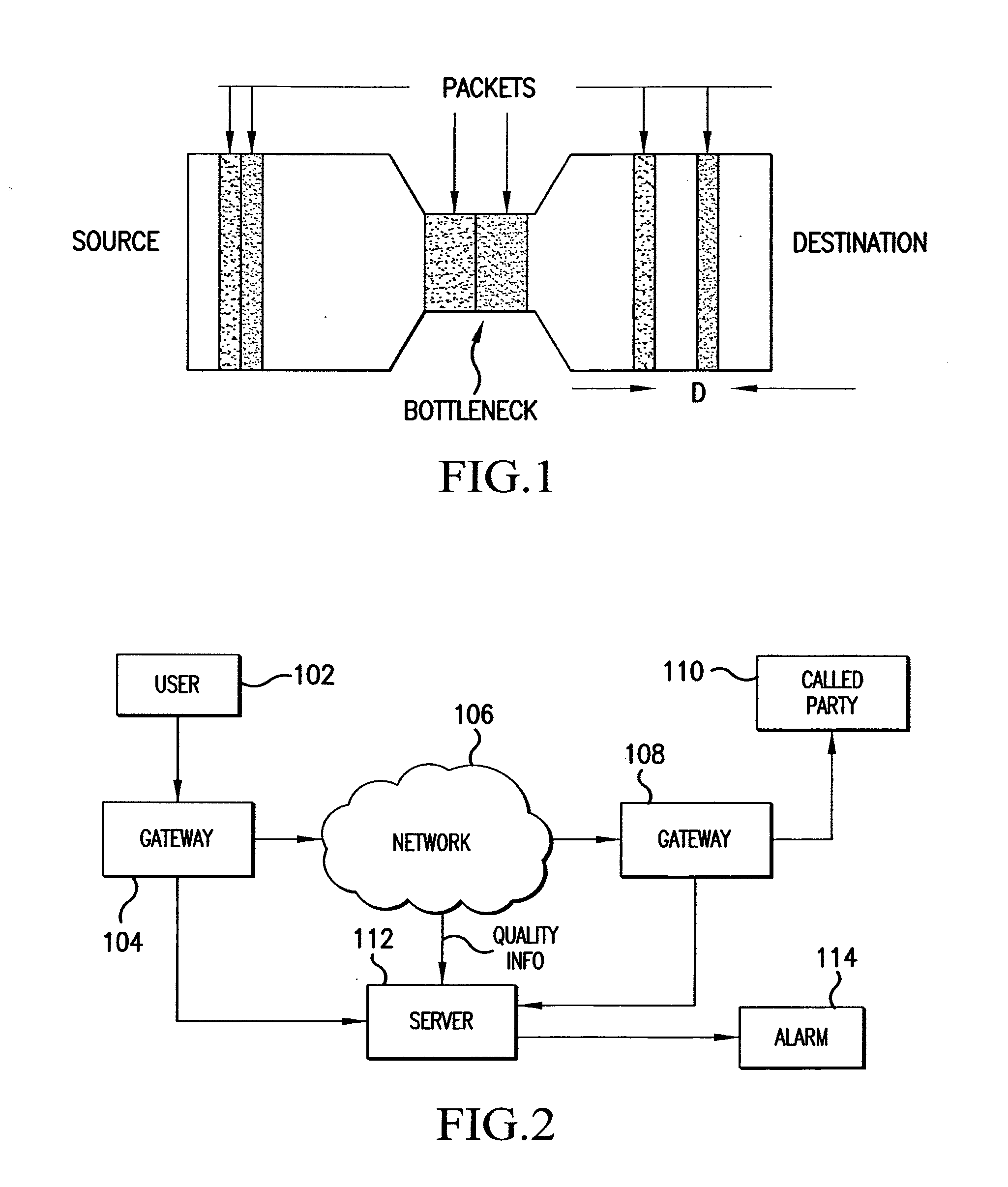
InactiveUS20100098228A1Protect reputationMonitor qualityTelephonic communicationTransmissionQuality of serviceCall tracing
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Methods for facilitating users to participate in rescue shared vehicle, vehicle, system and server
InactiveCN109544961AProtect reputationIncrease motivationDiscounts/incentivesRoad vehicles traffic controlReal-time computingUser participation
The invention discloses a method for facilitating users to participate in a rescue shared vehicle, comprising the following steps: setting different levels of areas including a forbidden area on a vehicle map; identifying a shared vehicle in the forbidden area and marking the same to prompt a user to rescue; matching a to-be-transferred target area of the shared vehicle; setting a movable path range when the shared vehicle is rescued; displaying the target area and the movable path range on the vehicle map after the user selects a rescue operation; sending an instruction to the shared vehicleso that the shared vehicle does not emit an alarm sound during the rescue process; and rewarding the user when the user confirms that the rescue is over, thereby avoiding the misunderstanding caused by a rescue behavior, leading to the unwillingness to do good, and effectively protecting the reputation of those who do good. The situation that the user can complete the rescue operation without theneed of spending too much time to unlock, ride, lock and wait, thereby greatly improving the enthusiasm for participating in the rescue. The invention also provides a corresponding vehicle, server andsystem.
Owner:长沙贤正益祥机械科技有限公司
A candied candy lid that displays the date it was opened
ActiveCN108750357BPrevent mistaken purchaseEasy to checkClosure with auxillary devicesButton batteryEngineering
The invention discloses a candied fruit can cap with opening date displaying. The candied fruit can cap comprises slide-proof groove, a base cap, an alerting lamp hole, an LED alerting lamp, a time display screen, a top cap, a can opening, a threaded ring, a button battery, a display circuit board, a circuit board, a button battery supporting frame, a wire, a first electrode collar, a second electrode collar, an inner pipe, a first electrode sheet, a partition plate, a partition membrane and a second electrode sheet. The alerting lamp hole is formed in the upper surface of the top cap; the alerting lamp hole is internally provided with the LED alerting lamp; the bottom of the LED alerting lamp is fixedly mounted on the upper surface of the partition plate; the partition membrane is arranged at the top of the base cap; the second electrode collar is arranged on the upper surface of the partition membrane; the second electrode sheet is arranged at the center of the upper surface of the partition membrane; a plurality of threads are formed in the inner wall of the base cap; a plurality of slide-proof grooves are formed in the outer side wall of the base cap; the can opening is formedin the top of the can; the threaded ring id arranged on the outer side wall of the can opening; and the can opening and the base cap are matched with each other by the threaded ring and the threads, and are in tight connection.
Owner:郎溪品旭科技发展有限公司
A Quality Grading Method of Pinellia Pinelliae Based on Neural Network
ActiveCN110796639BSecurity traceability data trackingImprove bargaining powerImage enhancementImage analysisMachine visionPinellia
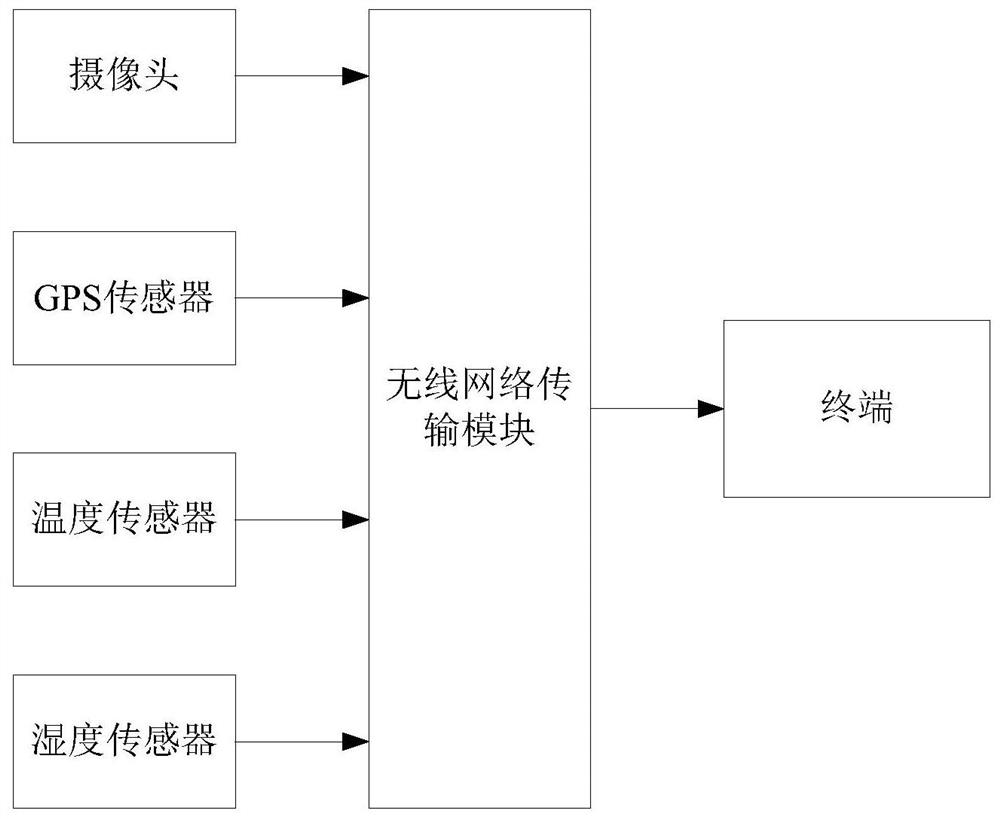
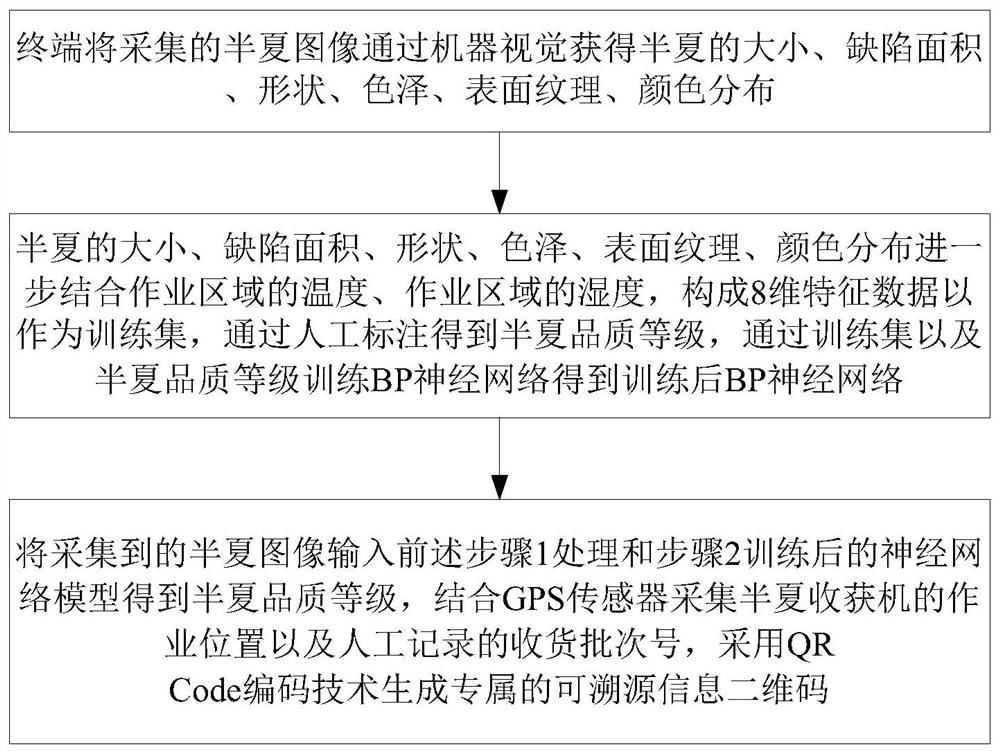
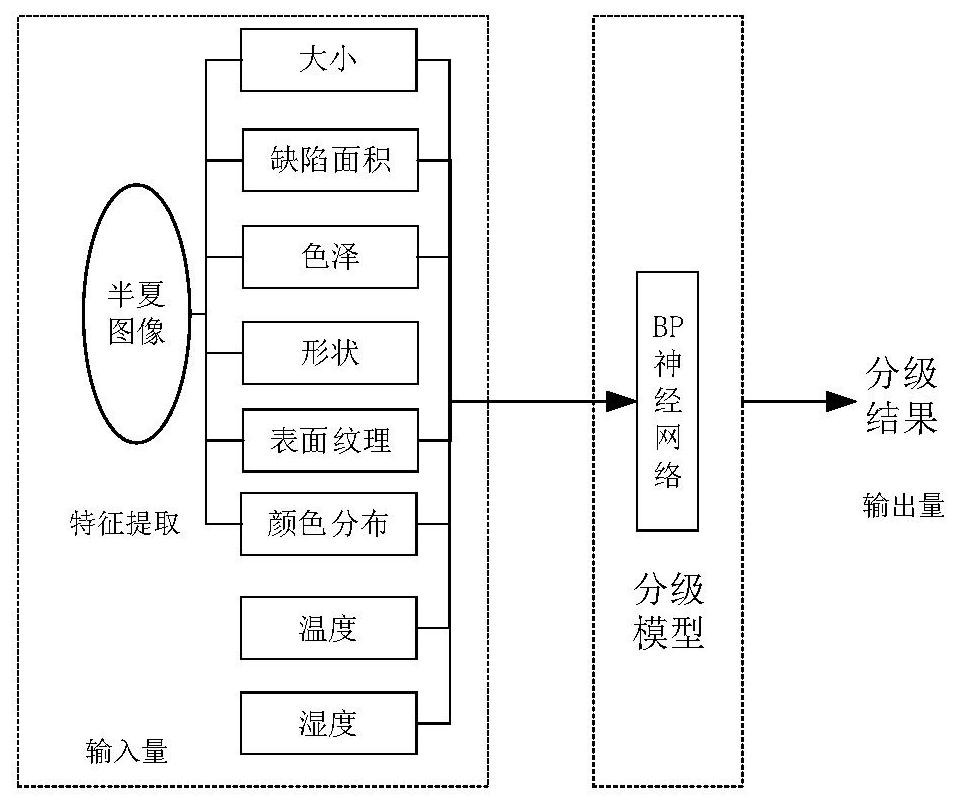
The invention discloses a neural network-based method for grading the quality of pinellia pinellia. The method includes the following steps: the terminal obtains the size, defect area, shape, color, surface texture, and color distribution of Pinellia through machine vision from the collected image of Pinellia; the size, defect area, shape, color, surface texture, The color distribution is further combined with the temperature and humidity of the operating area to form 8-dimensional feature data as the input of the BP neural network, and the manually marked pinellia quality level is used as the output; the BP neural network is trained and tested; the collected pinellia images are Input the neural network model processed in step 1 and trained in step 2 to obtain the quality grade of pinellia, combine the GPS sensor to collect the working position of the pinellia harvester and the batch number of the manual record, and use the QR Code coding technology to generate an exclusive Traceability information QR code. The invention can accurately determine the quality of Pinellia pinelliae, and realize traceability of Pinellia pinellia product information.
Owner:WUHAN UNIV OF SCI & TECH
Humidifier with product information detection function
ActiveCN113028542AExpedite sellingEasy accessMechanical apparatusLighting and heating apparatusDisplay deviceIndustrial engineering
The invention discloses a humidifier with the product information detection function. The humidifier comprises a shell, a display cavity with a forward opening is formed in the front wall of the shell, the bottom wall of the display cavity communicates with multiple sets of display devices arranged left and right, and each display device comprises an in-out groove which communicates with the bottom wall of the display cavity and is arranged front and back. A detection device can wipe the surfaces of the goods and move the goods with the minimum shelf life to the foremost portion at the same time, customers can take the goods conveniently, selling of the goods with the minimum shelf life is accelerated, waste of expired products is reduced, resources are saved, and meanwhile, and the efficiency of mechanical detection and placement is higher than that of manual detection and placement. According to a goods replenishment device, manual replenishment can be replaced by mechanical automatic replenishment, higher efficiency is achieved, the situation that goods are sold out is prevented, the detection device needs to be used once in each goods replenishment, and replenished goods are clean and attractive and are accurately placed according to the shelf life.
Owner:东佳精密光电(南京)有限公司
Method for Detecting Whether a Communication Device Is Forgotten
ActiveCN106453894BProtect reputationLoss of protectionSubstation equipmentCommunication deviceReal-time computing
The invention discloses a method for sensing whether a communication device is forgotten or not. The method comprises the steps that a first communication device receives usage data from a user of a second communication device, analyzes the usage data, determines a plurality of continuous usage time periods in which the second communication device is used, and judges whether current time is in certain continuous usage time period of the plurality of continuous usage time periods or not; if the current time is in the certain continuous usage time period and the number of survival information which is received by the first communication device and comes from the second communication device exceeds the preset fixed number, judging that the second communication device is forgotten, and the first communication device initiates a reminding signal; and when the first communication device initiates the reminding signal, the user of the first communication device obtains the second communication device and processes a communication event received by the second communication device. According to the method, the user of the first communication device can sense whether the second communication device is forgotten or not, initiates the reminding signal and can timely help the second communication device to process the communication event.
Owner:重庆蓝岸科技股份有限公司
A kind of jade non-destructive testing sample model and its manufacturing method
ActiveCN103983492BConvenient researchMeet the needs of high-tech testing instrumentsPreparing sample for investigationRaman scatteringLight dispersionCarbon film
Owner:温新续
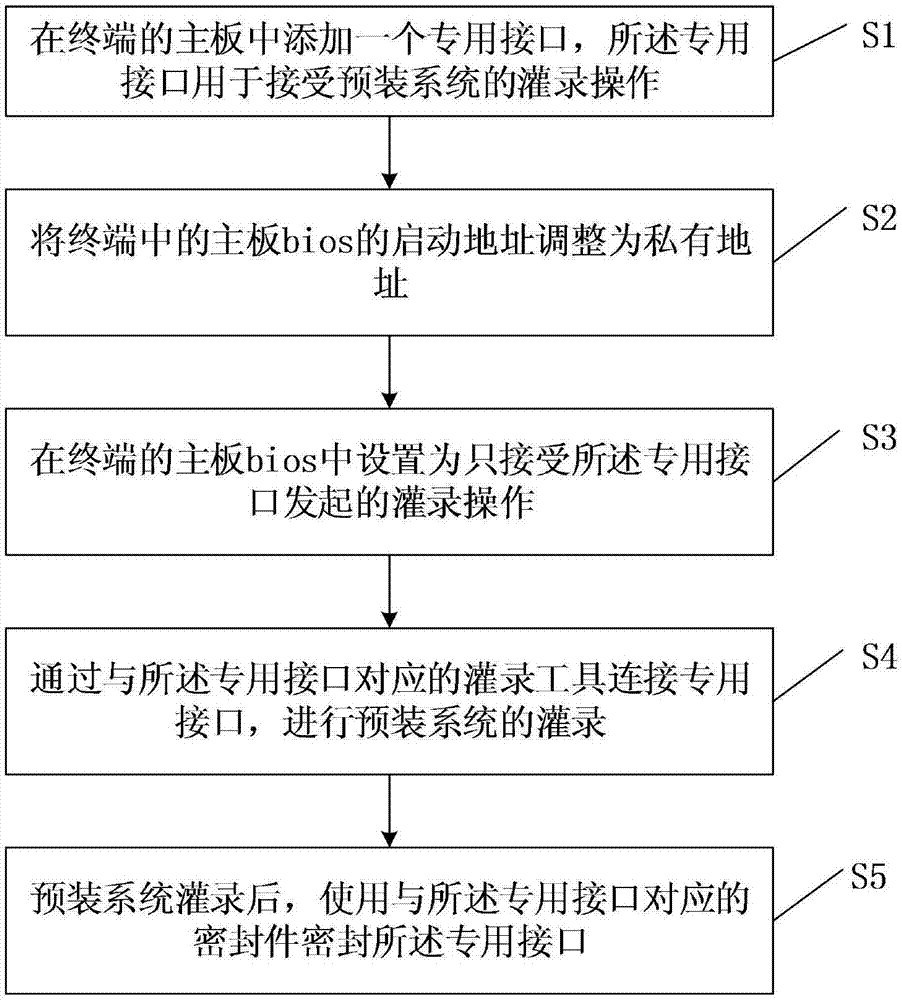
Safety recording method of terminal
InactiveCN107423625AProtect reputationEnsure safetyInternal/peripheral component protectionPlatform integrity maintainancePrivate addressBIOS
The invention discloses a safety recording method of a terminal. The method comprises the following steps: adding a dedicated interface in a main board of a terminal, wherein the dedicated interface is used for accepting a recording operation of a pre-installation system; adjusting a starting address of the main board bios in the terminal as a private address; setting to only accept the recording operation initiated by the dedicated interface in the main board bios of the terminal; recording the pre-installation system through a recording tool connection dedicated interface corresponding to the dedicated interface. By improving the recording way of the existing terminal, an equipment user cannot replace the enterprise pre-installation system, the security of the equipment and the reputation of the enterprise are guaranteed.
Owner:GUANGDONG YOUMAI INFORMATION COMM TECH
A method for making Shu embroidery anti-counterfeit embroidered cloth based on photoluminescent yarn and Morse code
InactiveCN105177815BQuality improvementProtection of rights and interestsWoven fabricsEmbroidering machines apparatusTime informationPhotoluminescence
The invention discloses anti-fake Sichuan embroidery cloth based on photoluminescence yarn and a Morse code and a manufacturing method thereof. Satin weave, twill weave and plain weave are adopted, the photoluminescence yarn serves as characteristic yarn capable of being inspected and identified, ordinary yarn serves as main yarn of the embroidery cloth, the identity information of an embroiderer and embroidery time information which are represented by the Morse code are shown through the arrangement of the characteristic yarn and the main yarn so as to be internalized into fabric, the embroidery cloth is tested for identification through a corresponding detection instrument, and then Sichuan embroidery fake resisting and quality tracking purposes are realized. According to the anti-fake Sichuan embroidery cloth, the photoluminescence yarn which is invisible under daily illumination and displays color only under the irradiation of a specific light source is adopted, the overall attractiveness of Sichuan embroidery products is not affected, invisible fake resistance is achieved, and the aesthetics completeness of Sichuan embroidery products is guaranteed.
Owner:SICHUAN UNIV
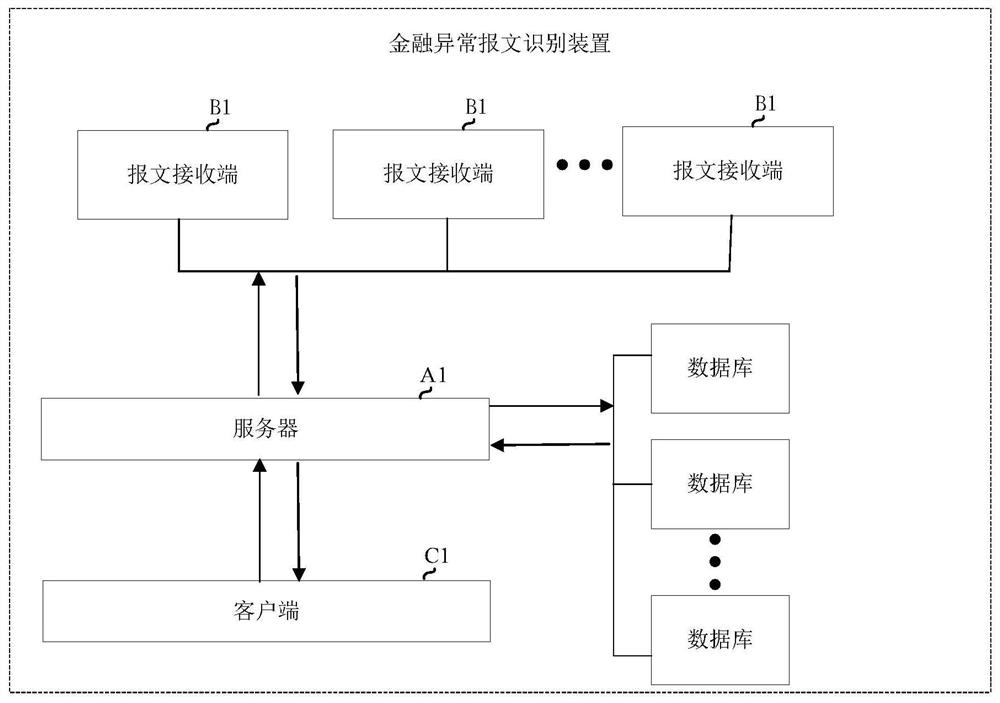
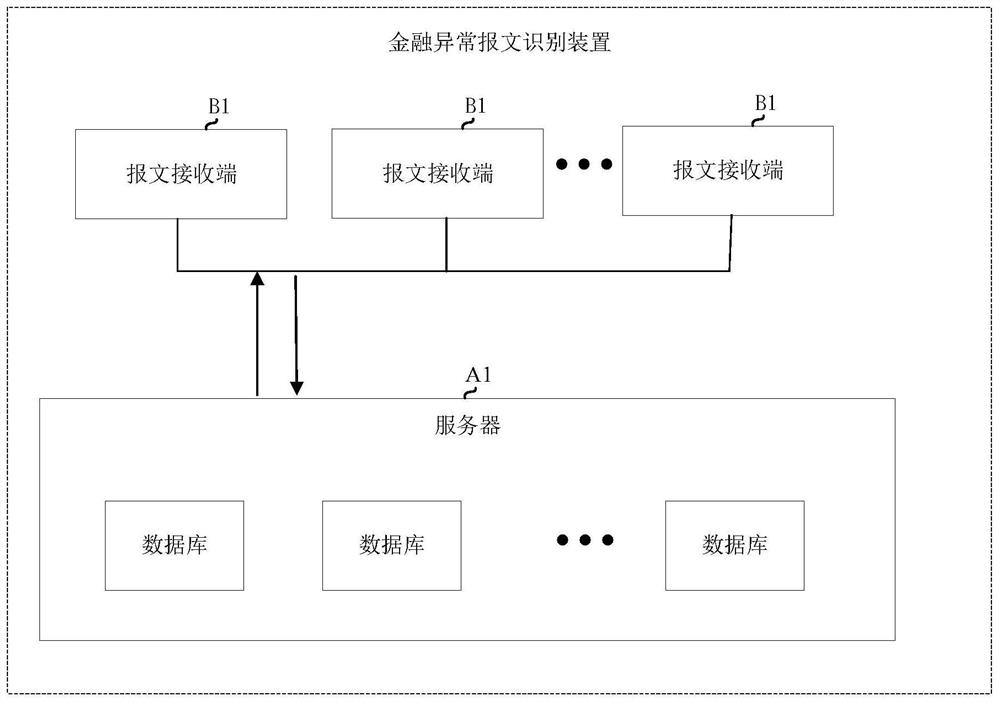
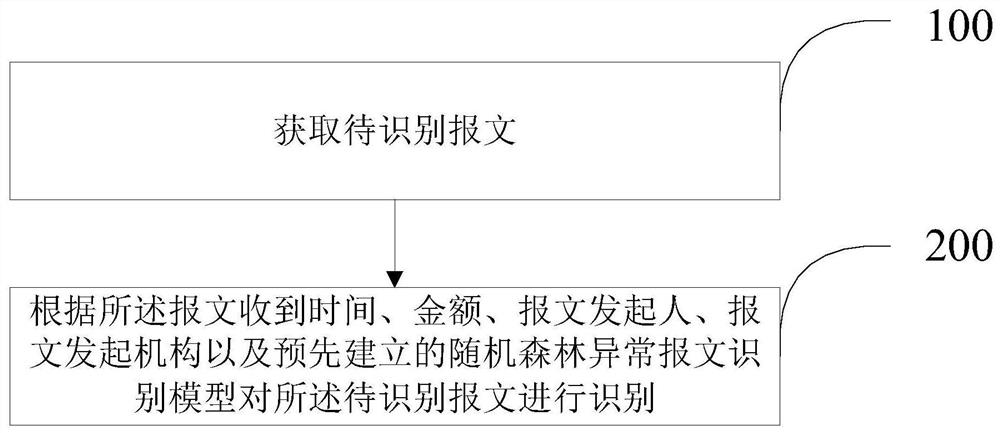
Financial abnormal message identification method and device
ActiveCN112995155AAvoid stress shocksAvoid harassmentFinanceMachine learningComputer networkEngineering
The invention belongs to the technical field of artificial intelligence, and provides a financial abnormal message identification method and device, and the method comprises the steps: obtaining a to-be-identified message which comprises the message receiving time, the amount, a message initiator, a message appendix and a message initiating mechanism; and identifying the to-be-identified message according to the message receiving time, the amount, the message initiator, the message initiating mechanism and a pre-established random forest abnormal message identification model. According to the invention, automatic identification of abnormal messages is realized by adopting automatic acquisition and learning of historical data; a system is prevented from being impacted by the abnormal messages, the workload of tellers for processing the abnormal messages is reduced, clients are prevented from receiving harassment of advertisement pushing, the availability of a financial institution system can be guaranteed, and manpower of workers can be greatly saved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com