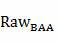Quantitative risk and income self-adaptive dynamic multiple-factor authentication method
An authentication method and risk-based technology, applied in the field of dynamic multi-factor authentication, can solve problems such as being unable to adapt to highly changing network environments, changing authentication methods, and improving security levels
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0089] by figure 2 For example, the access process in an online bank is as follows:
[0090] (1) The online banking system administrator determines that the security level is normal according to the current system situation, and sets it accordingly series variable. The authentication strength of access requests and the corresponding authentication methods are divided into four groups:
[0091] Certification Strength and Scope Transfer / Payment Authentication Method very safe, < 0.1
Password + picture verification code Safe, 0.1 – 0.3 Password + one-time password token + picture verification code Normal, 0.3 – 0.5 Password + SMS token + one-time password token suspicious, 0.5 – 0.7 Password+SMS token+USB token Hazardous, 0.7 – 0.8 Password + SMS token + one-time password token + USB token High risk, >= 0.8 reject
[0092] (2) The user purchases goods on a third-party shopping website.
[0093] (3) The user selects ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com