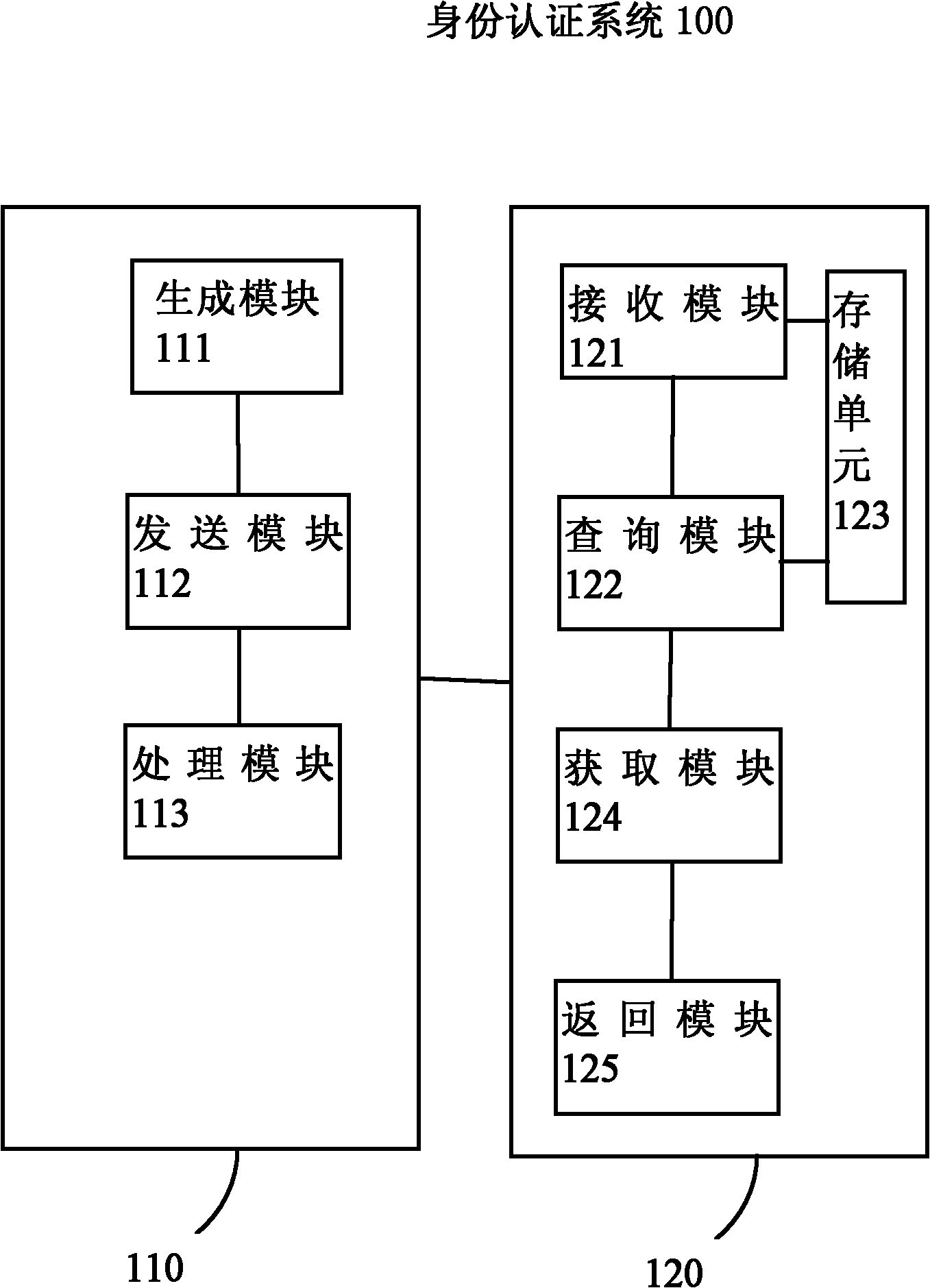
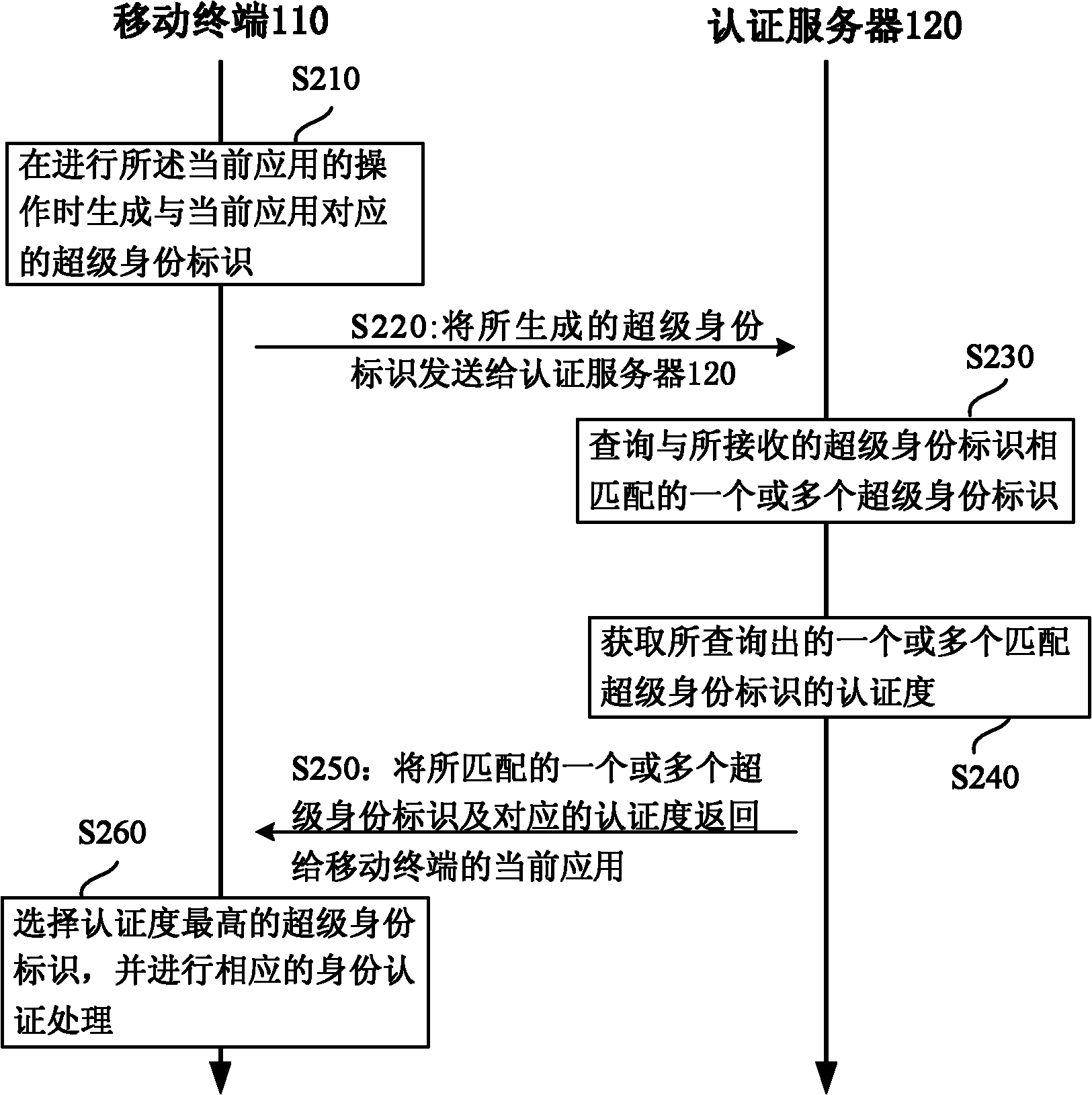
Identity authentication method and system
An identity authentication and identification technology, applied in the field of mobile Internet, can solve the problems of loss of account information and historical behavior, inability to obtain records, poor application experience, etc., and achieve the effect of ensuring consistency, balancing security and convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0053] In this embodiment, it is assumed that there are three application scenarios: application 1, application 2, and application 3. In the application 1 scenario, user A accesses the UC website by using the UC browser of the mobile phone. In the application 2 scenario, user A sends a text message by using the UC desktop application. In the scenario of application 3, user A queries the experience value of the UC website by sending a text message. Wherein, application 3 is an application currently activated on the mobile terminal, and application 1 and application 2 are applications previously activated on the mobile terminal.
[0054] In application 1, when user A accesses the UC website using the UC browser of the mobile phone, the UC browser obtains user A's identification data. Here, the identification data may be software parameters, hardware parameters and / or user data related to applications of the mobile terminal. For example, UC browser obtains identification data,...
no. 2 example
[0070] In this embodiment, it is assumed that the application scenarios are still the three application scenarios described in the first embodiment: application 1, application 2, and application 3. Wherein, application 3 is an application currently activated on the mobile terminal, and application 1 and application 2 are applications previously activated on the mobile terminal. But the difference is that user A changed a new mobile phone number, such as 13987654321, after performing the operations of application 1 and application 2 as described in the first embodiment, but still used the original mobile phone. That is to say, the hardware of user A's mobile phone has not changed, but the mobile phone number has changed.
[0071] In this case, if user A uses a new mobile phone number to send a text message in App 3 to query the experience value of the UC website, since the new mobile phone number is not in the super identity database, no matching SUID can be found. However, as...
no. 3 example
[0082] In this embodiment, it is assumed that the application scenarios are the application scenarios described in the first embodiment: application 1 and application 2. Wherein, application 1 and application 2 are previously activated applications on the mobile terminal. However, user A, after performing the operations of application 1 and application 2 as described in the first embodiment, changed a new mobile phone due to the loss of the mobile phone, but retrieved the original mobile phone number through the operator. That is to say, user A's mobile phone hardware has changed, but the mobile phone number has not changed. At this time, user A needs to obtain the login information of using the UC browser to access the UC website in application 1, so as to restart application 1.
[0083] As described in the first embodiment, before user A loses his mobile phone, SUID-1 and SUID-2 are generated and saved in the super identity database in application 1 and application 2 respec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com