Attack detection rule opening method, and equipment
A technology of attack detection and rules, which is applied in the field of communication, can solve the problems of affecting security, missing attacks, reducing the utilization rate of attack detection rules, etc., and achieve the effect of balancing cost and security and increasing the number
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
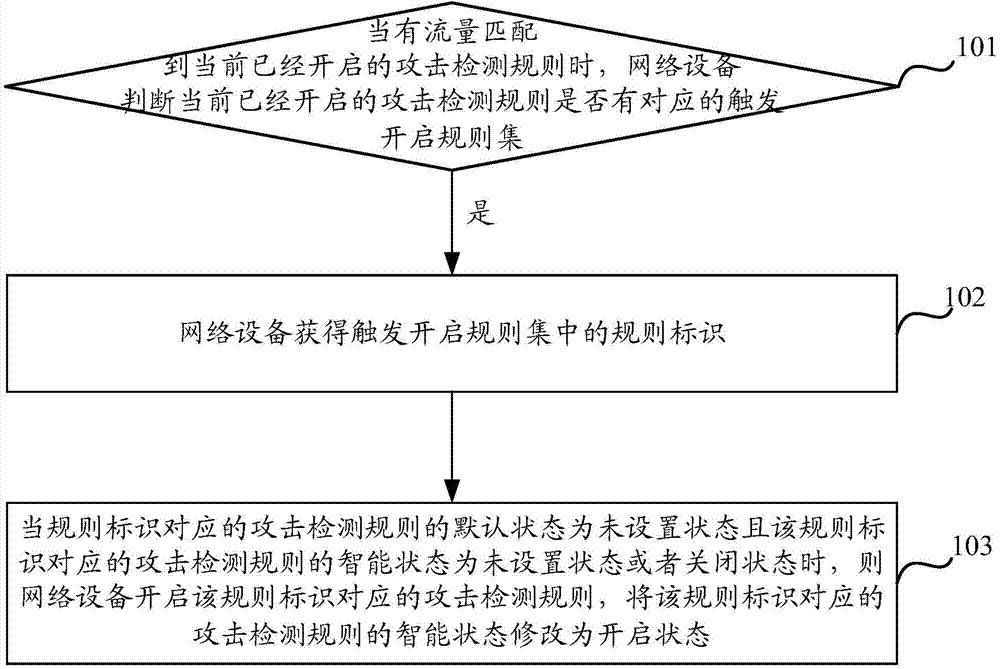
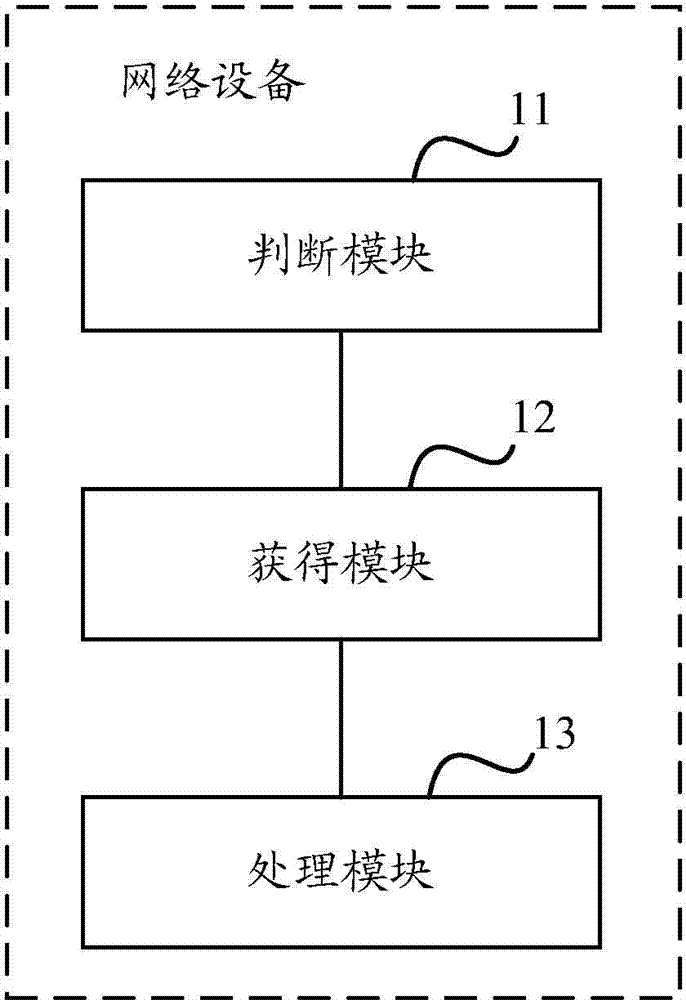
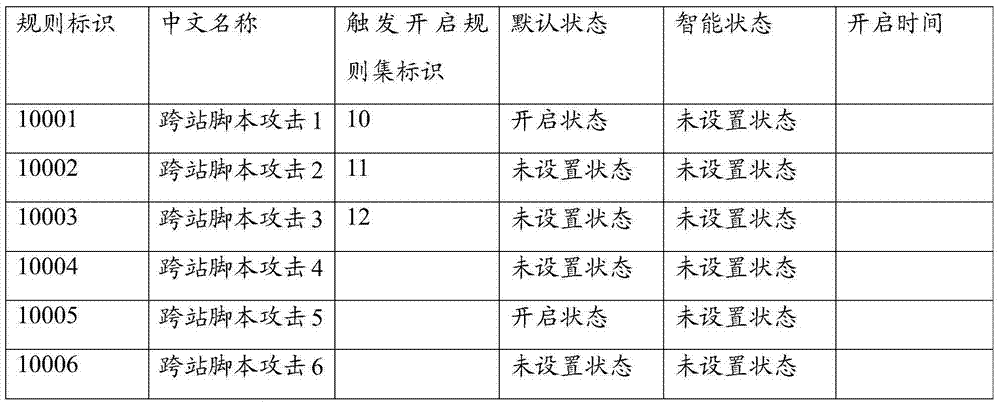
[0023] Aiming at the problems existing in the prior art, the embodiment of the present invention provides a method for enabling attack detection rules, which intelligently adjusts the number of enabled attack detection rules in real time, and reduces the number of enabled attack detection rules under the condition of controllable false positives. In the embodiment of the present invention, the attack detection rule table is pre-configured on the network device, and the triggering and opening rule set is configured for the attack detection rule. The attack detection rule and the corresponding attack detection rule in the triggering and opening rule set are attacks of the same attack type. A detection rule or an associated attack detection rule is, for example, an attack detection rule for detecting a cross-site scripting attack.
[0024] In the embodiment of the present invention, the attack detection rule table includes information of a plurality of attack detection rules, and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com