Method for establishing trusted path in secure operating system
A secure operating system and trusted path technology, applied in the field of secure operating system design, can solve security problems and other issues, and achieve the effect of protecting system security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
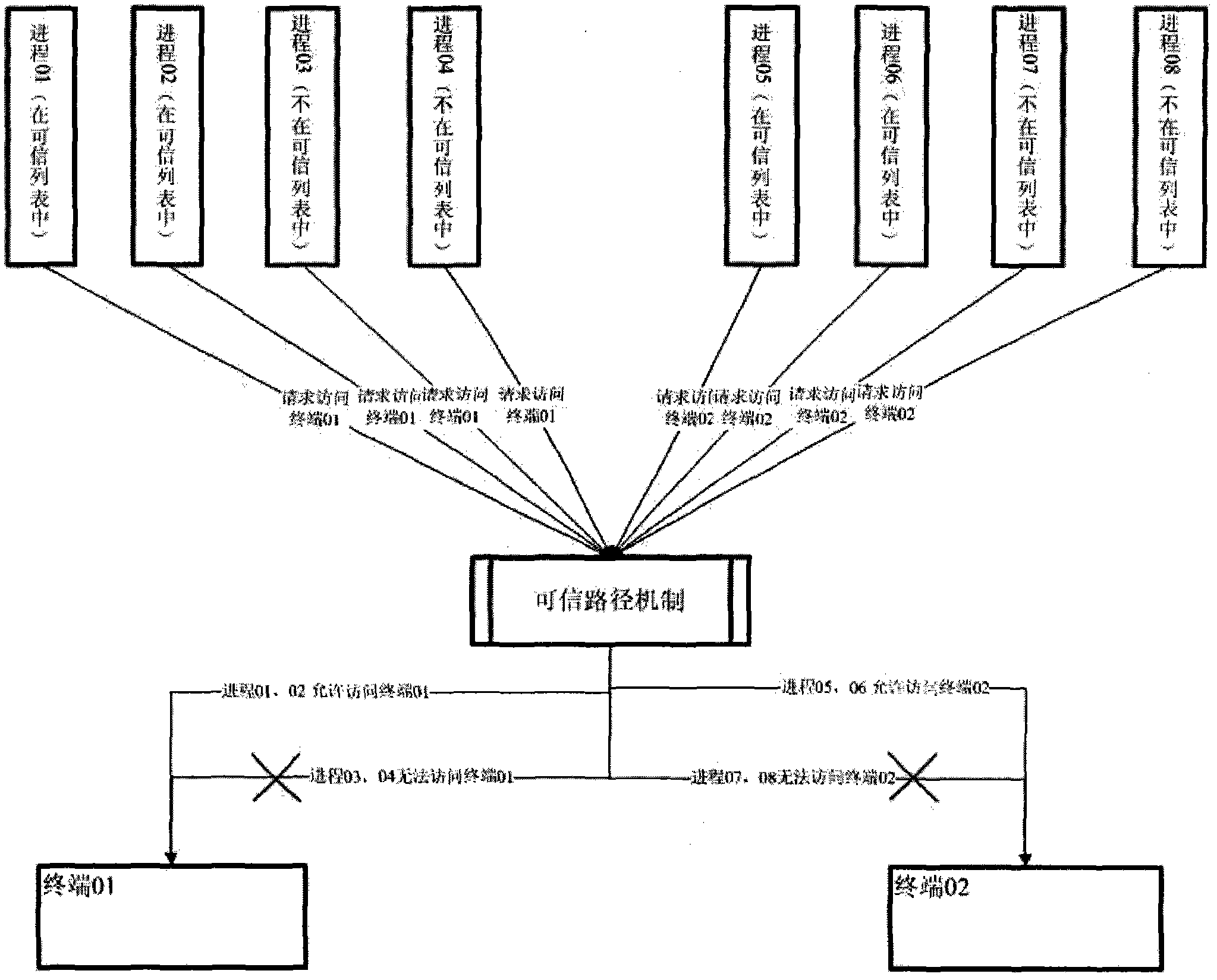
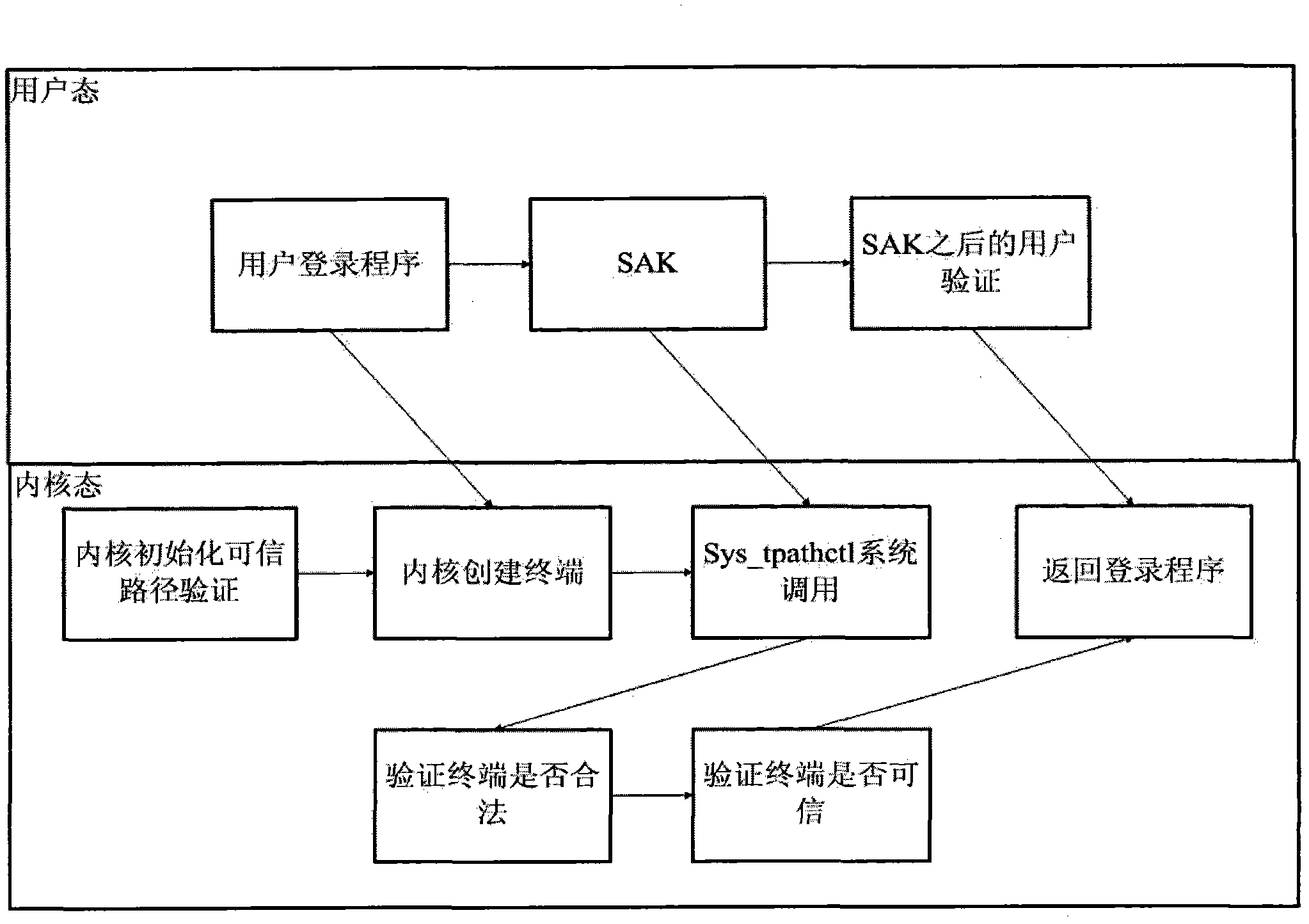
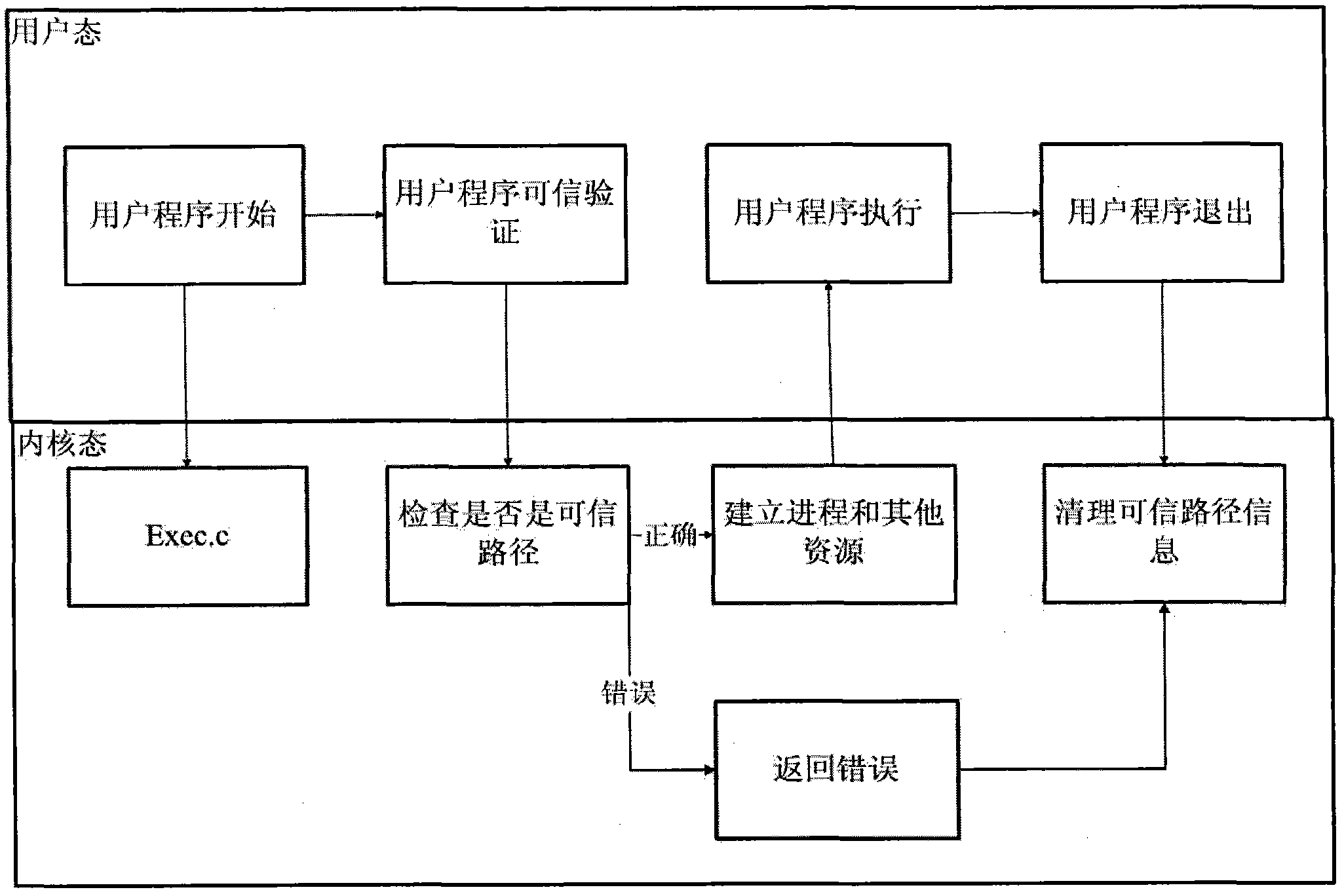
[0020] The trusted path mechanism refers to a mechanism that enables end users to communicate directly with the Trusted Computing Base (TCB) of computer information systems. Trusted Computing Base (TCB) is "the totality of protection devices in a computer system, including hardware, firmware, software, and a combination responsible for implementing security policies. It establishes a basic protection environment and provides a trusted computing system. additional user services". The trusted computing base generally referred to is the combination of all security protection devices (commonly referred to as security subsystems) that constitute a secure computer information system to prevent interference and tampering by untrusted subjects. Trusted computing base is a concept in the field of computer security information protection, which does not depend on a specific operating system. According to the requirements of the standard (GB / T20272 / 20271-2006) on the trusted path of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com