Detecting spam email using multiple spam classifiers
a classifier and spam technology, applied in the field of electronic mail or email, can solve the problems of unsolicited e-mail, received hundreds of unsolicited e-mails, and the use of e-mail has not come without its drawbacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
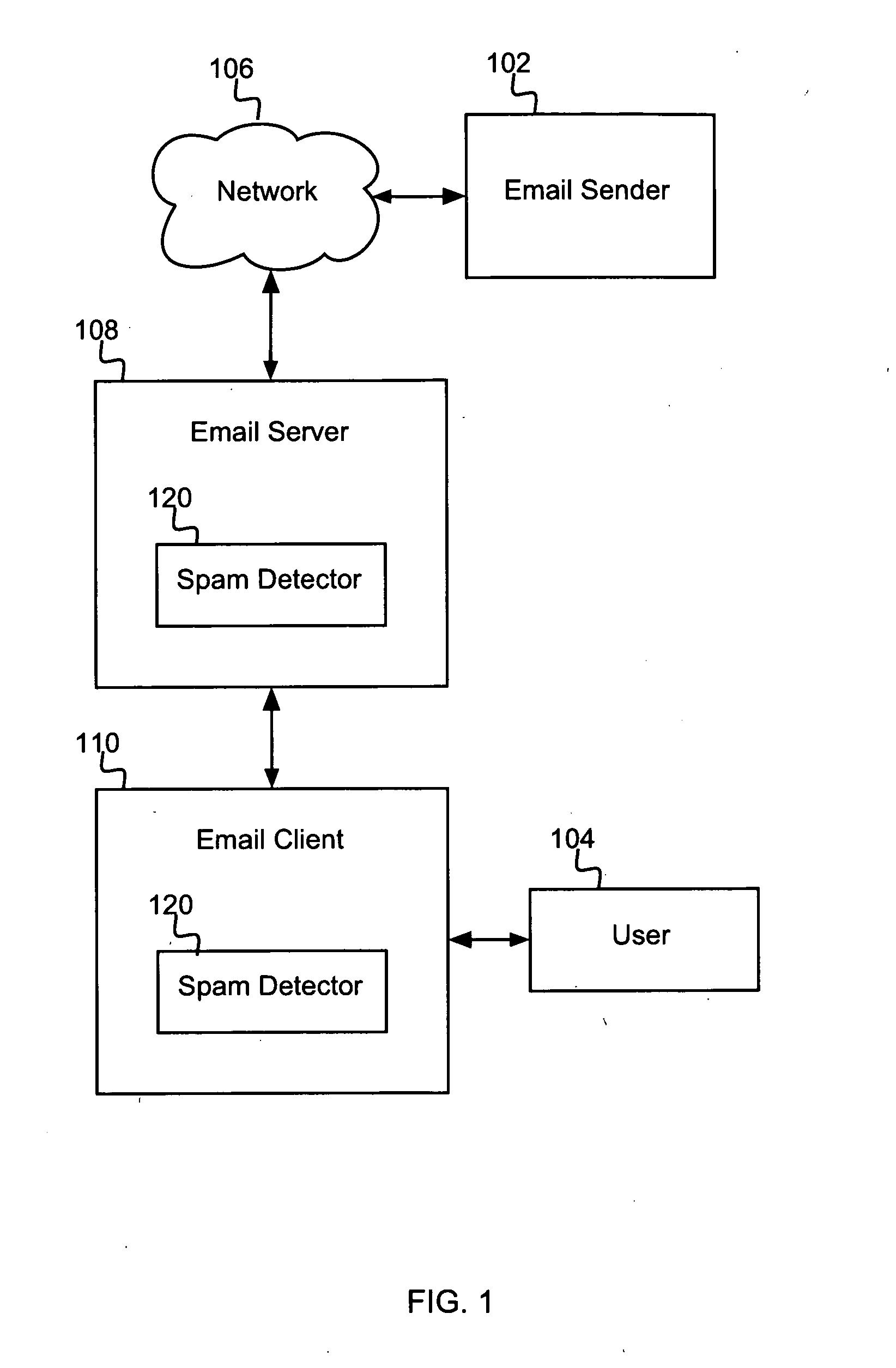
[0030]FIG. 1 is a block diagram showing a high-level network architecture according to an embodiment of the present invention. FIG. 1 shows an e-mail server 108 connected to a network 106. The e-mail server 108 provides e-mail services to a local area network (LAN) and is described in greater detail below. The e-mail server 108 comprises any commercially available e-mail server system that can be programmed to offer the functions of the present invention. FIG. 1 further shows an e-mail client 110, comprising a client application running on a client computer, operated by a user 104. The e-mail client 110 offers an e-mail application to the user 104 for handling and processing e-mail. The user 104 interacts with the e-mail client 110 to read and otherwise manage e-mail functions.
[0031]FIG. 1 further includes a spam detector 120 for processing e-mail messages and detecting unsolicited, or spam, e-mail, in accordance with one embodiment of the present invention. The spam detector 120 c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com