A system for detecting security performance of security chip under induced error attack
A security chip and error attack technology, applied in the direction of platform integrity maintenance, internal/peripheral computer component protection, etc., can solve problems such as limited effectiveness of security measures, leakage of confidential data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
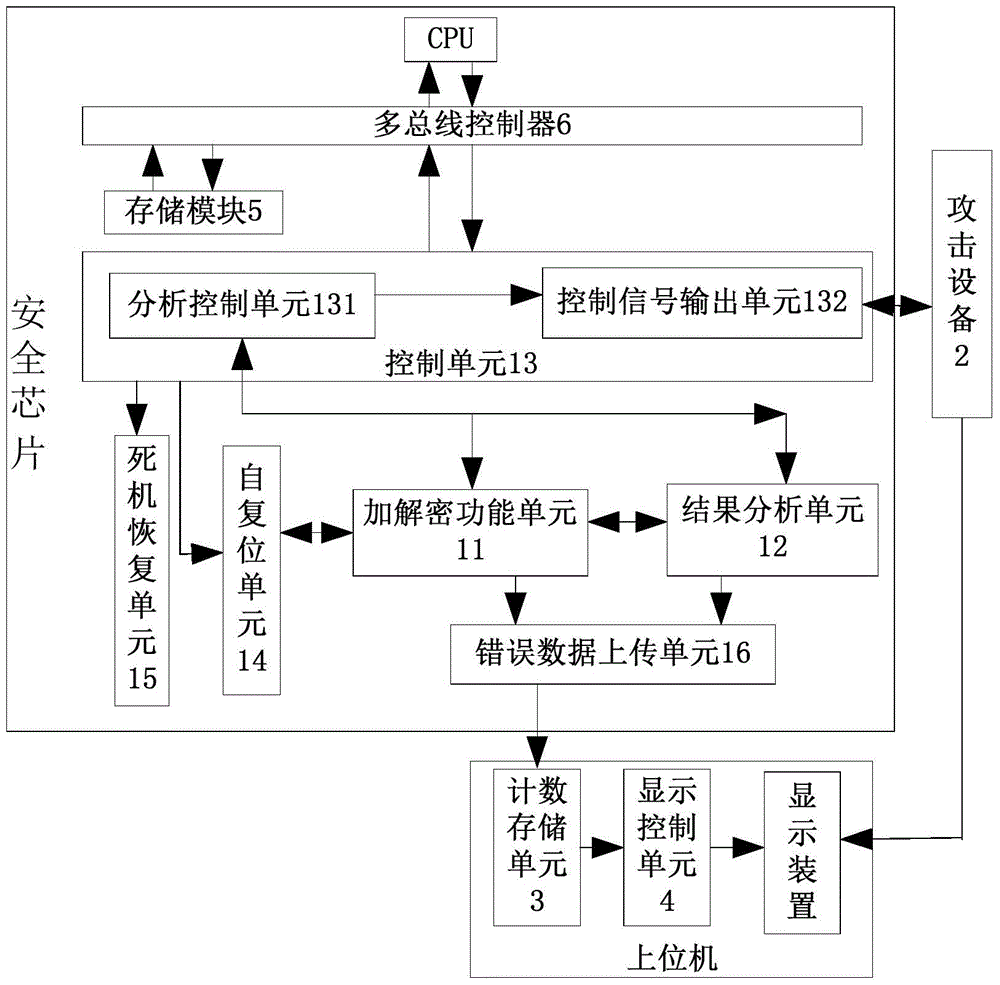
[0052] This embodiment provides a system for detecting the security performance of security chips under induced error attacks, such as figure 1 shown, including:
[0053] The control unit 13 controls the encryption and decryption functional unit 11 in the security chip to perform a decryption operation under an error-induced attack.
[0054] The result analysis unit 12 reads the operation result of the encryption and decryption functional unit 11 and compares it with the built-in reference result, and outputs the analysis result.
[0055] The control unit 13 and the result analysis unit 12 in this embodiment can be arranged inside the security chip or outside the security chip. Regardless of whether it is arranged inside or outside the security chip, as long as there is signal transmission with the encryption and decryption functional unit 11 in the security chip, the corresponding functions can be realized.
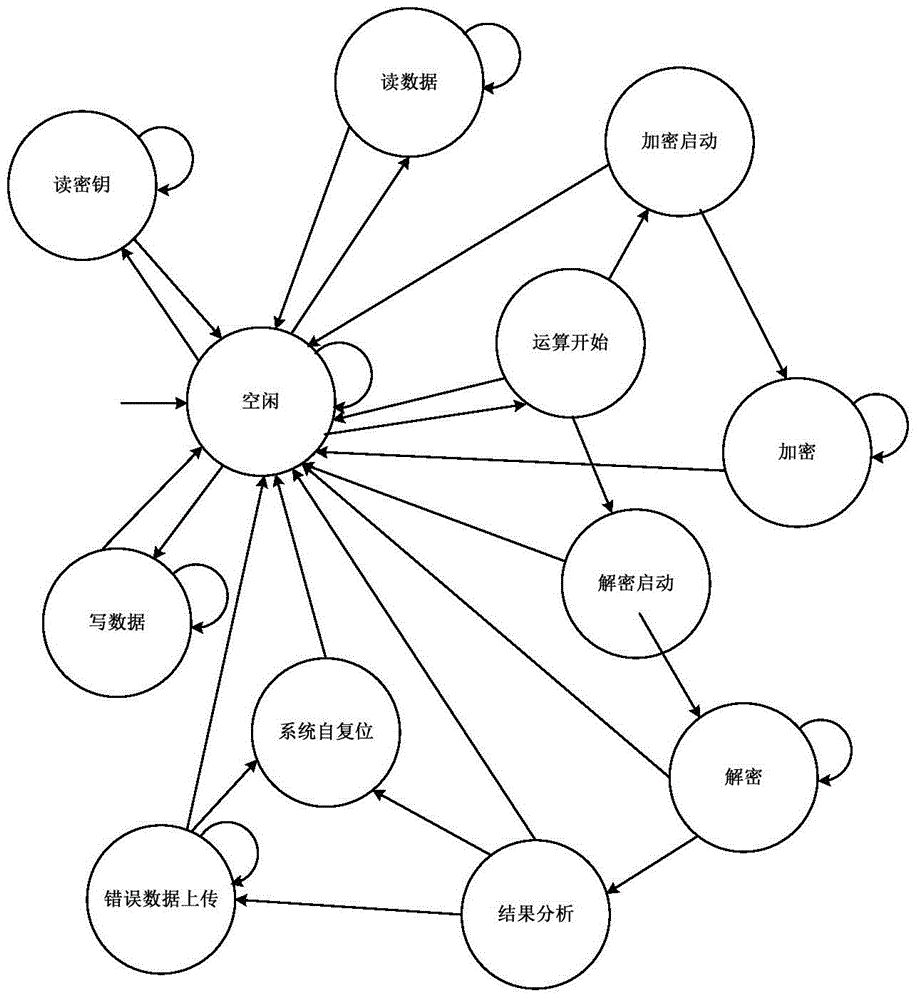
[0056] The system for detecting the safety performance of the sec...
Embodiment 2
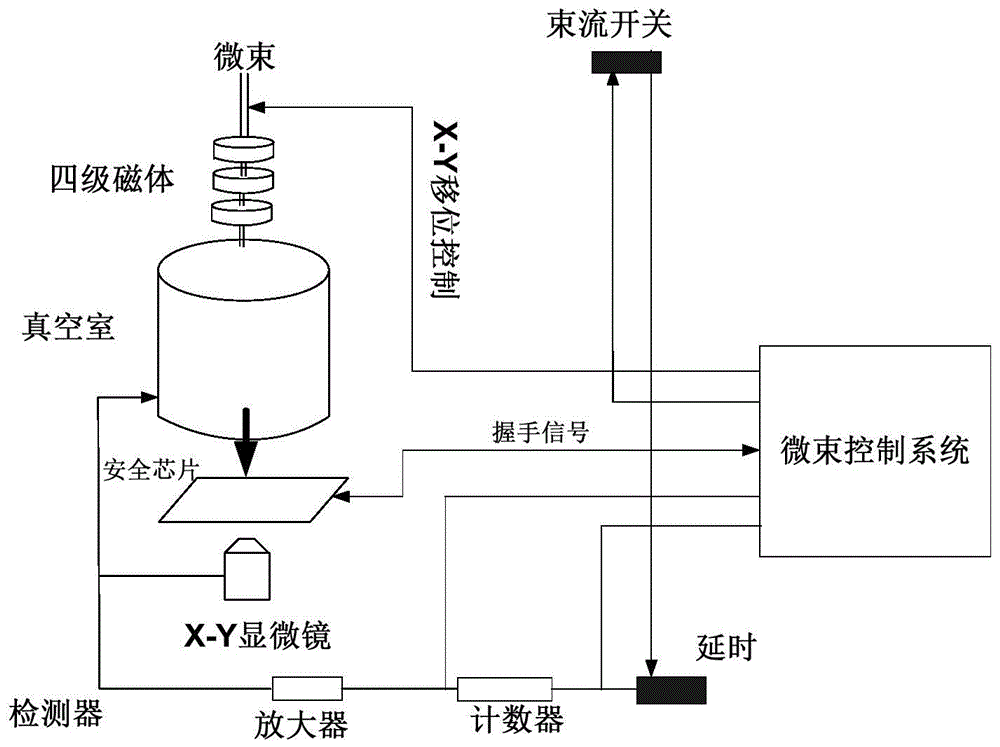
[0068] On the basis of Embodiment 1, the system for detecting the security performance of the security chip under the detection-induced error attack described in this embodiment, such as figure 1 As shown, the control unit 13 is further configured to control the attack device 2 to stop the round of induced error attack after the encryption and decryption functional unit 11 completes the decryption operation; and trigger the attack device 2 to detect the analysis result , if the analysis result is an error identification, the coordinates of the attacking device 2 locating the location of this round of induced error attack on the security chip are the fault point coordinates.
[0069] The display control unit 4 is also used to control the display device to display the fault point coordinates.
[0070] Therefore, this embodiment provides a system that can effectively detect the security performance of the security chip, and can locate and evaluate the weaknesses of the security c...
Embodiment 3
[0072] On the basis of embodiment 1 or embodiment 2, the system described in this embodiment detects the safety performance of security chips under induced error attacks, such as figure 1 and Figure 4 shown, also includes:
[0073] The self-resetting unit 14 is configured to reset the encryption and decryption functional unit 11 , the result analysis unit 12 and the control unit 13 .
[0074] The control unit 13 is also used to control the encryption and decryption functional unit 11 to start a decryption operation after the encryption and decryption functional unit 11 is reset, and at the same time control the shift of the attack device 2 to the next attack point. Conduct a new round of induced error attacks.
[0075]Therefore, the system for detecting the security performance of the security chip under the induced error attack described in this embodiment can remove the soft error generated by the previous induced error attack through the self-resetting unit 14, so that i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com