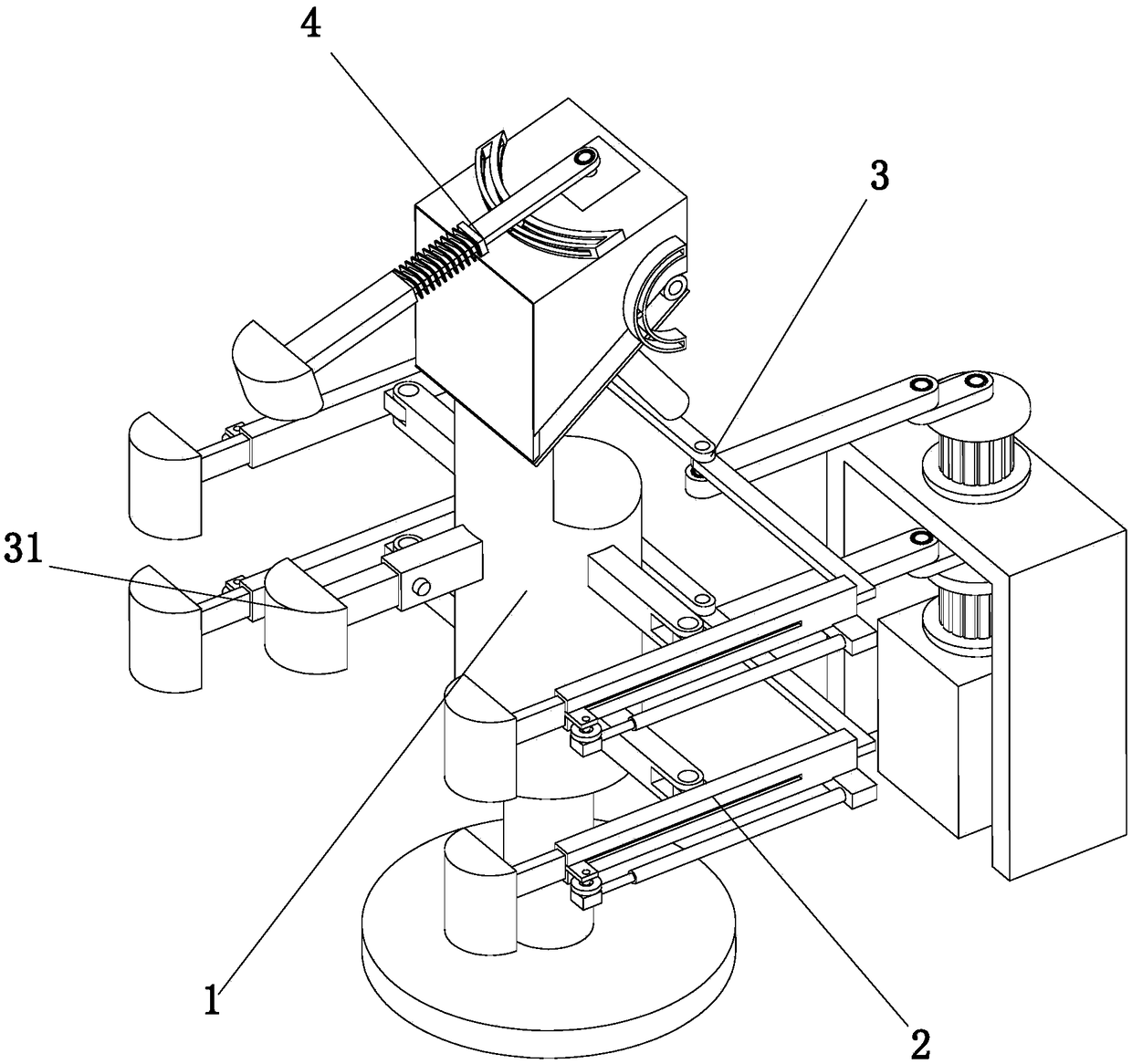
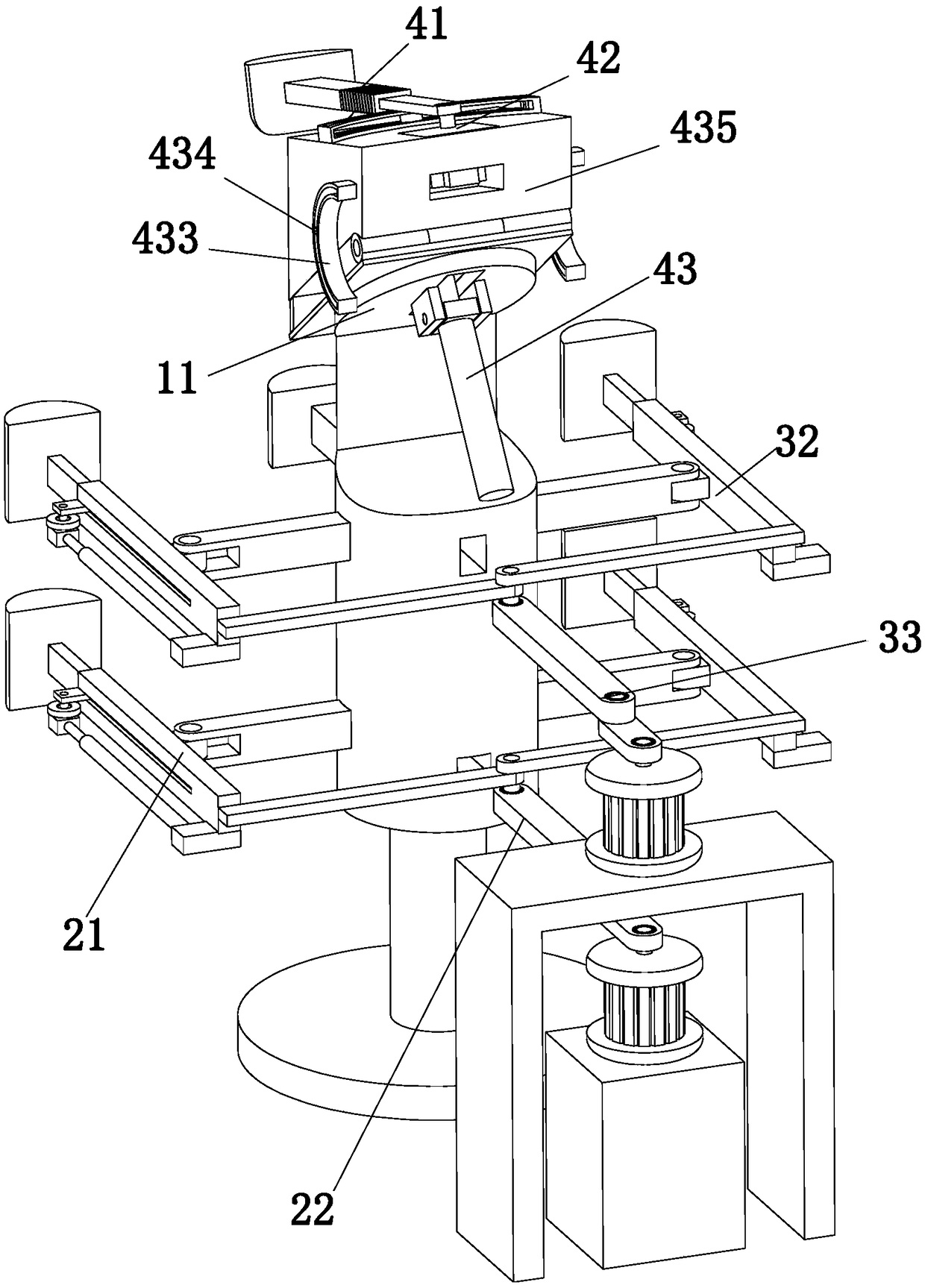
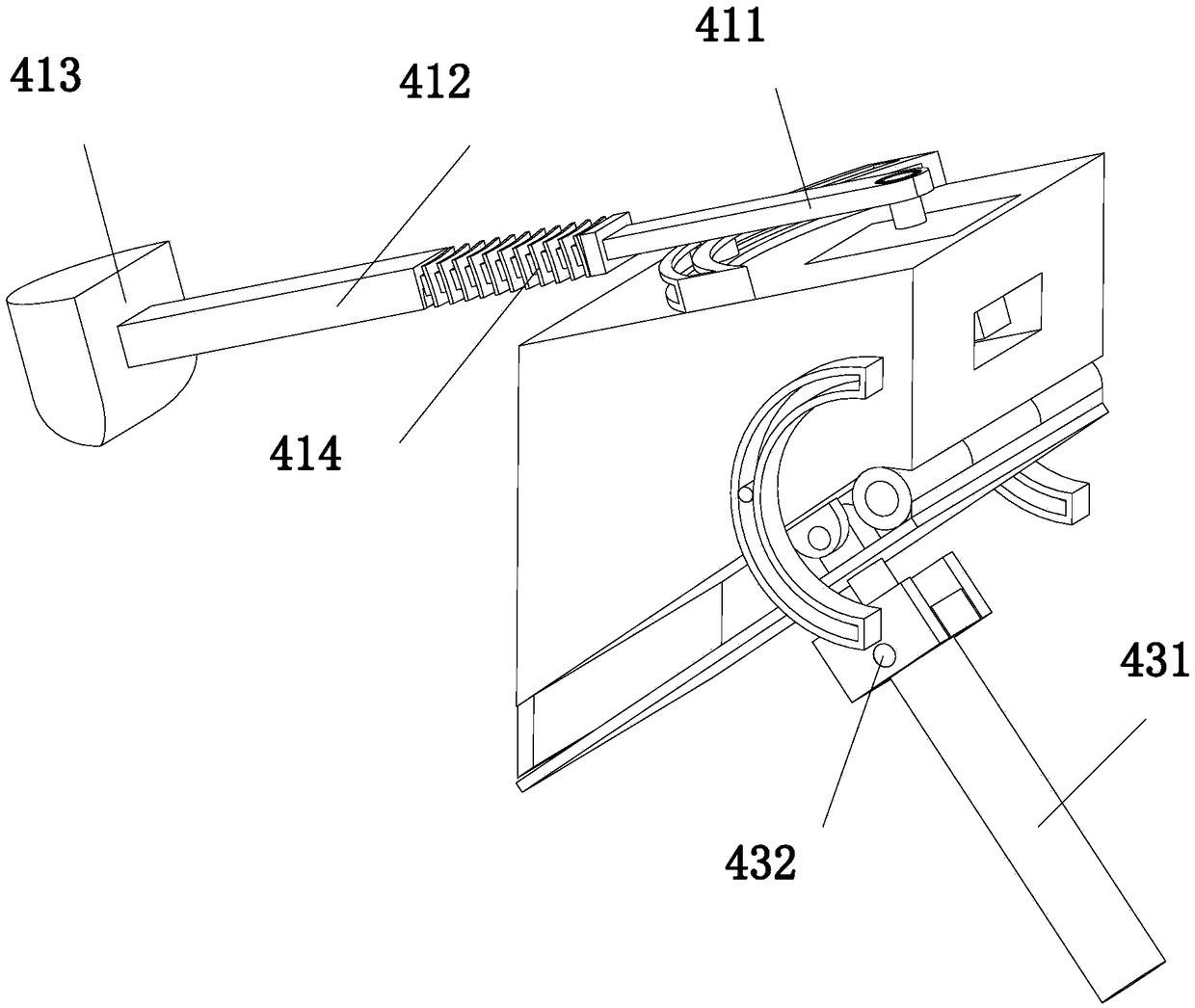
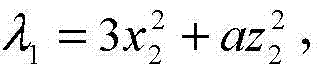Patents
Literature
115 results about "Attack device" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
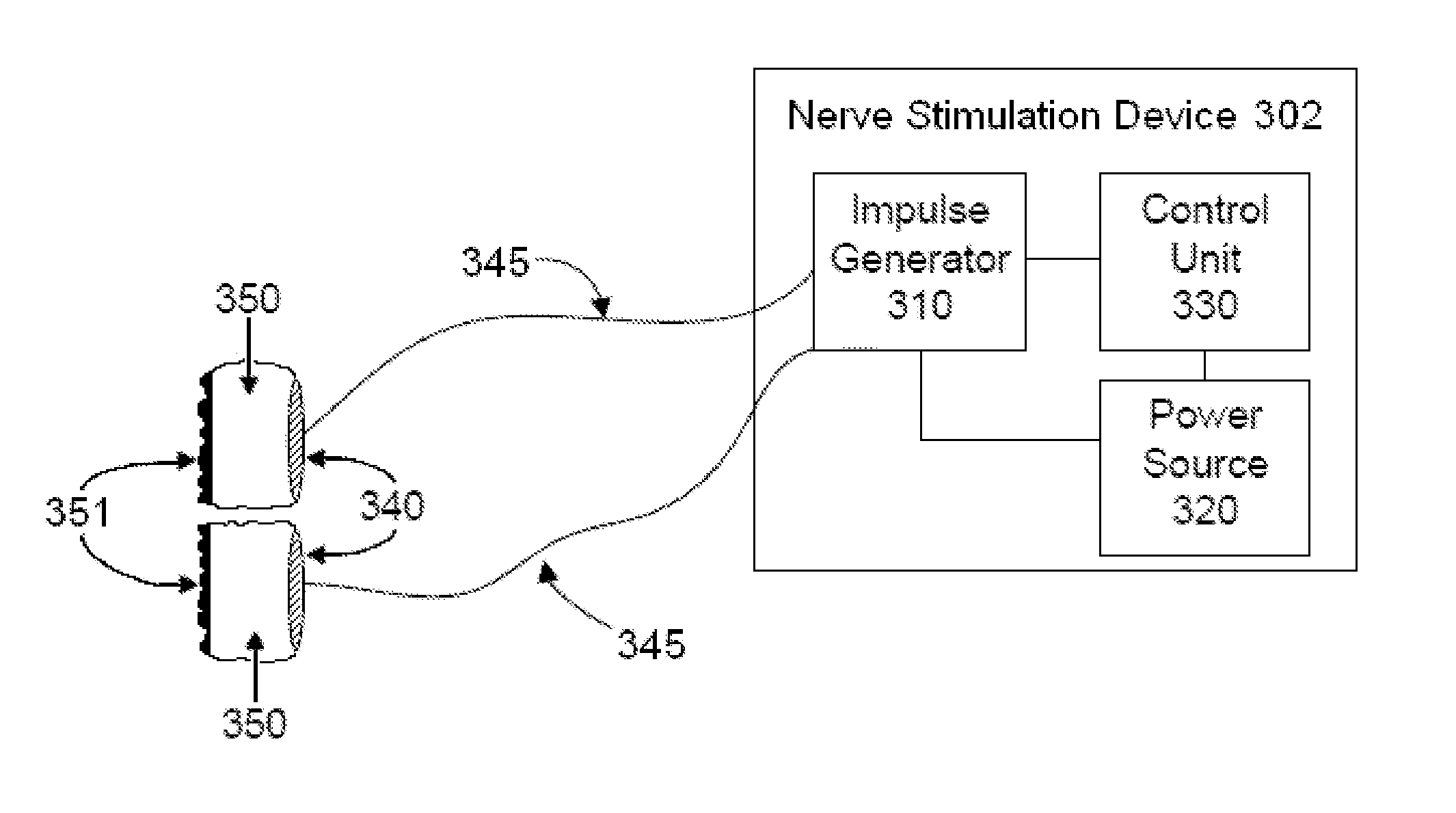
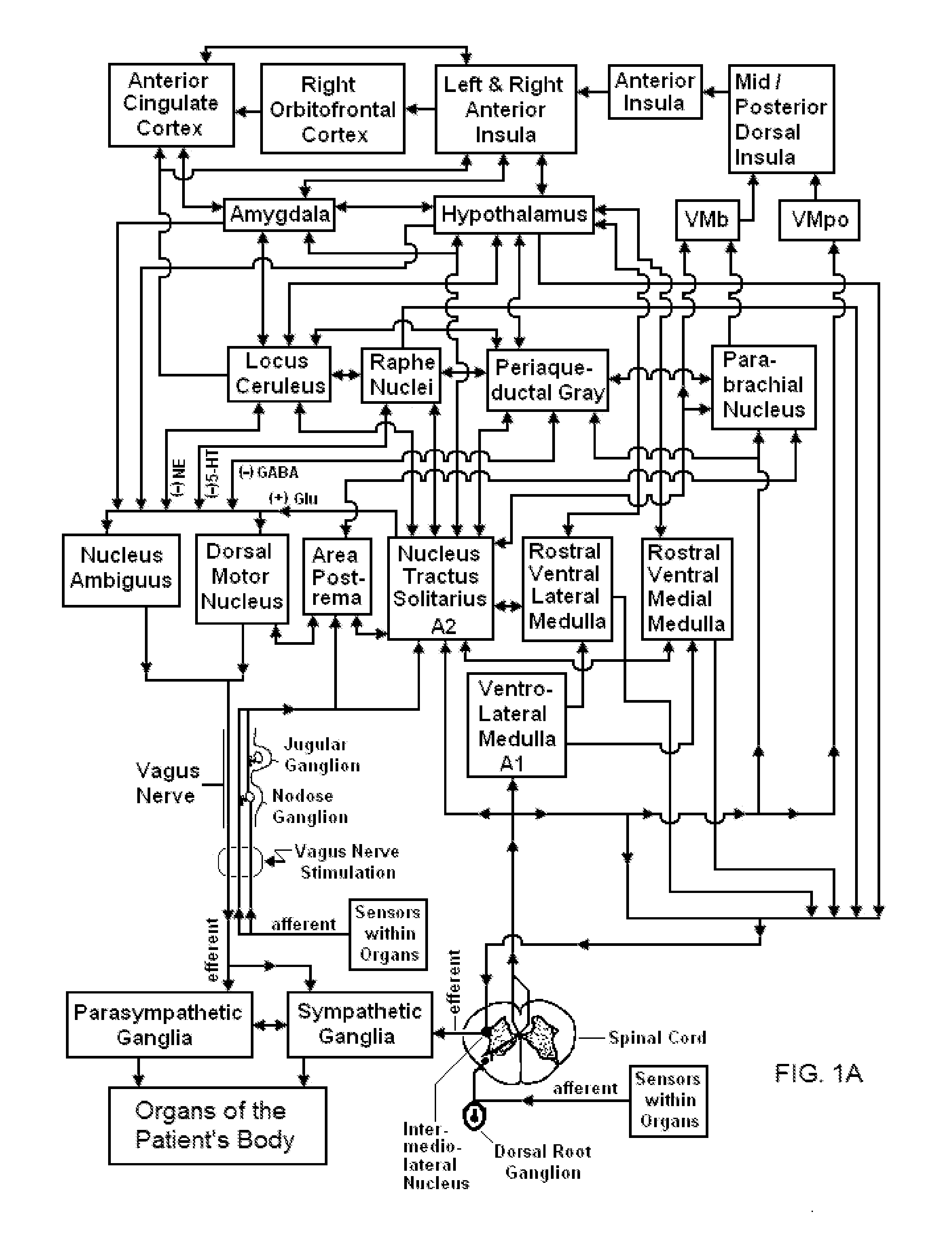
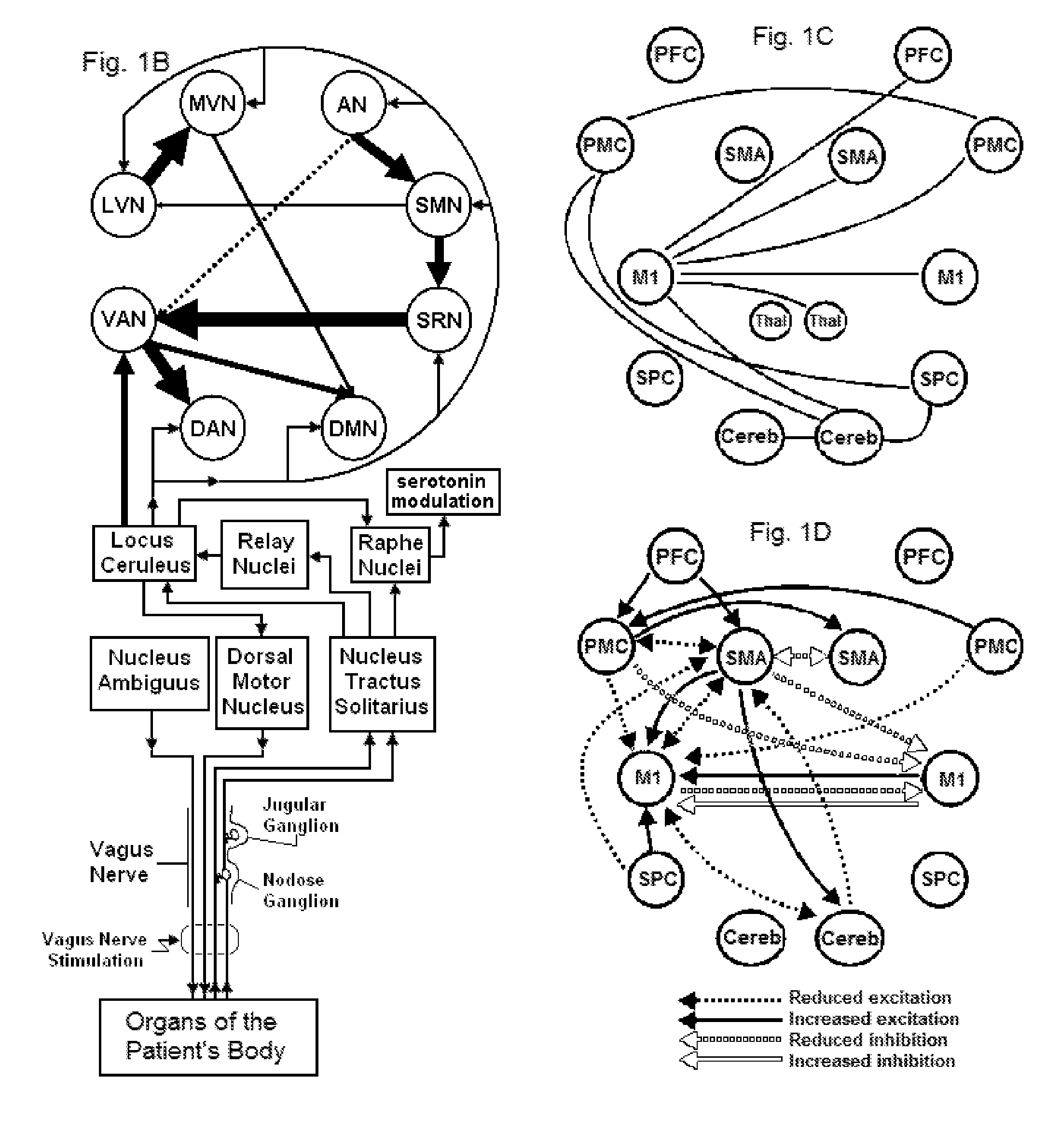
Vagal nerve stimulation to avert or treat stroke or transient ischemic attack
ActiveUS20130317580A1Improve the level ofInhibition of excitementSpinal electrodesMagnetotherapy using coils/electromagnetsSerotoninRisk stroke
Devices, systems and methods are disclosed for treating or preventing a stroke and / or a transient ischemic attack in a patient. The methods comprise transmitting impulses of energy non-invasively to selected nerve fibers, particularly those in a vagus nerve. Vagus nerve stimulation is used to modulate the release of GABA, norepinephrine, and / or serotonin, thereby providing neuroprotection to the patient; to modulate the activity of resting state neuronal networks, particularly the sensory-motor network or resting state networks containing the insula; and to avert a stroke or transient ischemic attack that has been forecasted.
Owner:ELECTROCORE
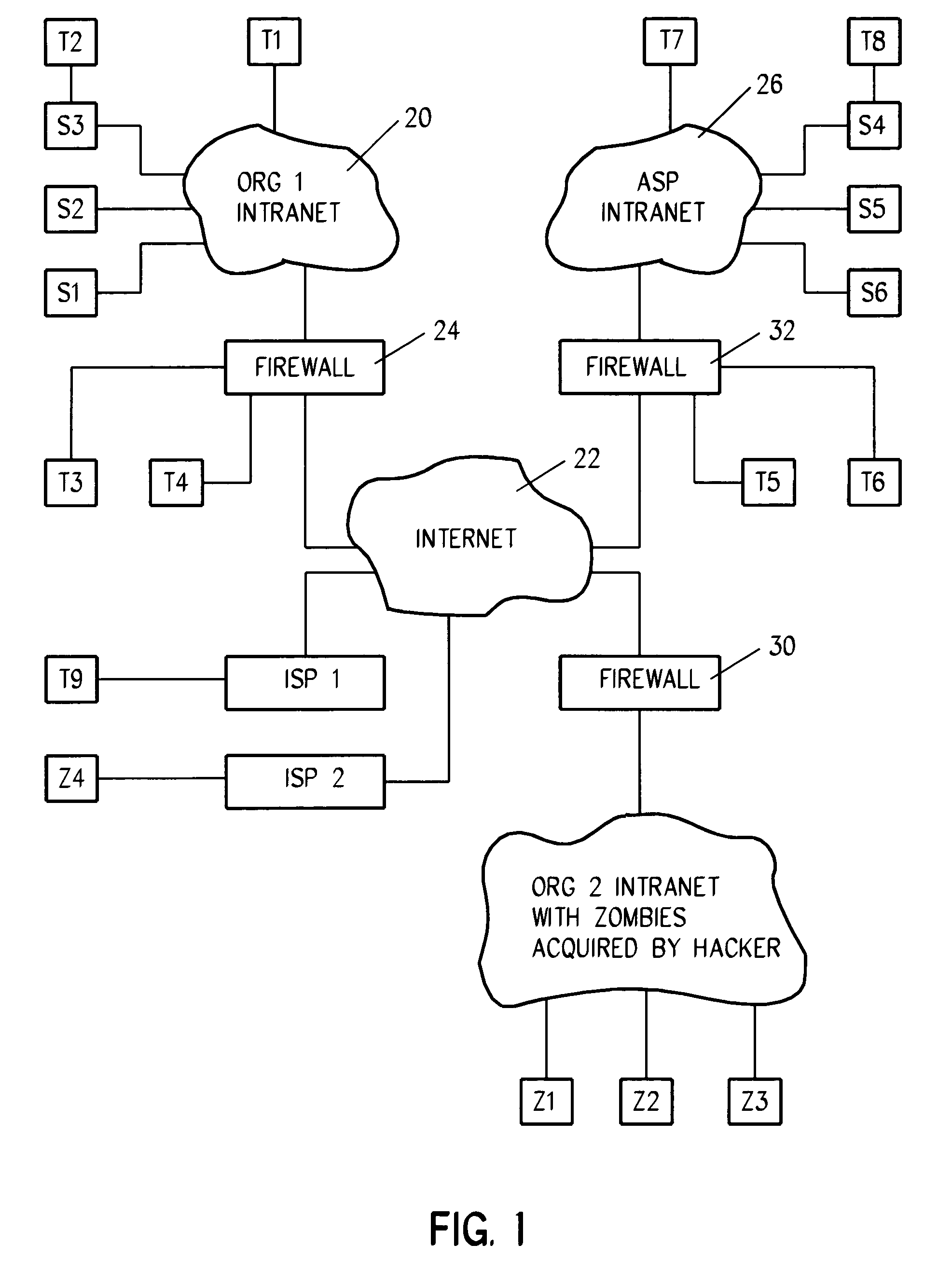
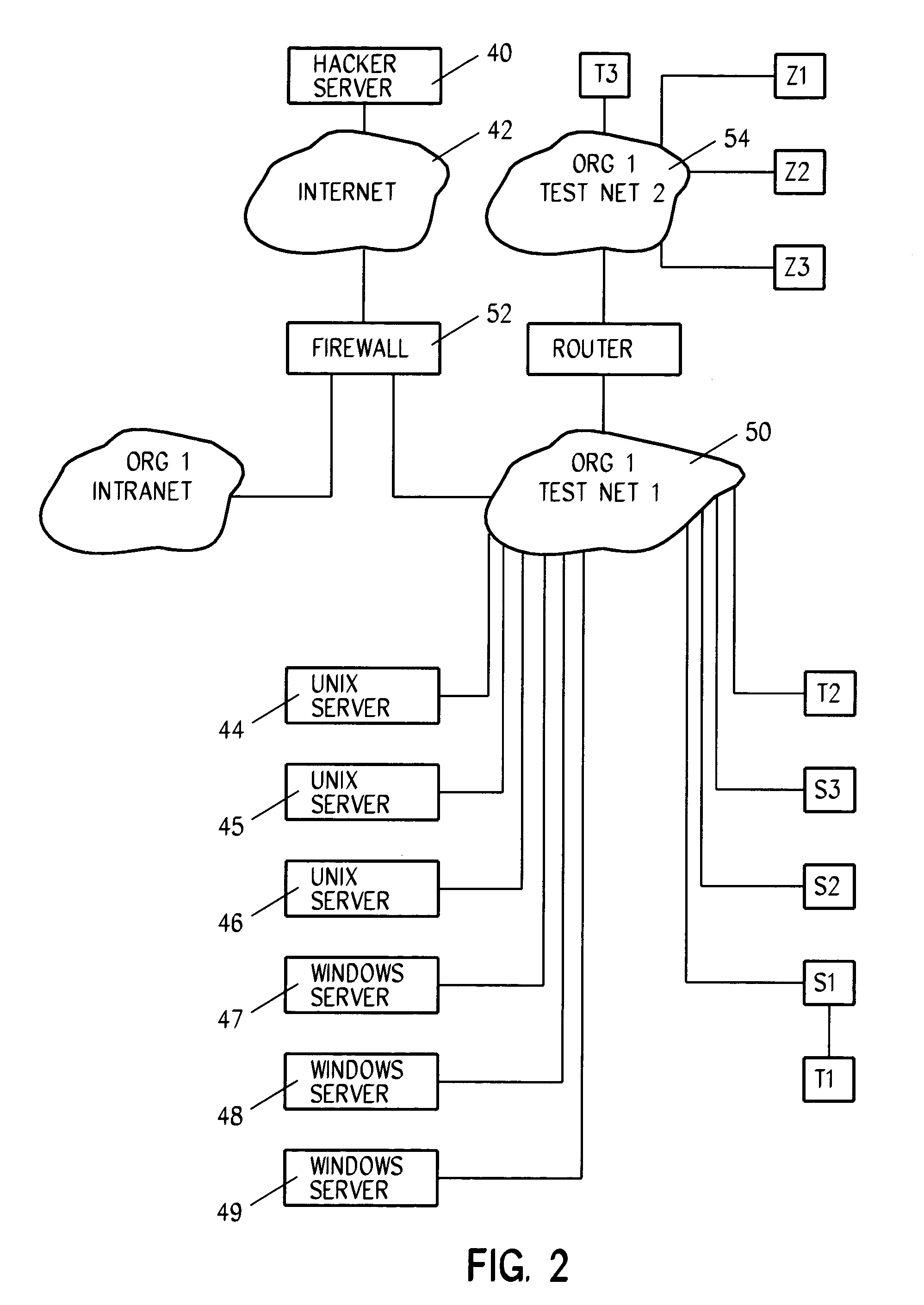
System and method for the detection of and reaction to denial of service attacks
Challenge-response and probative methods together or independent of each other enable detection of devices participating in denial of service (DOS) and distributed DOS (DDOS) attacks upon a network resource, and upon identification of devices participating in attacks, minimize the effect of the attack and / or minimize the ability of the device to continue its attack by placing the attacking devices in a state of reduced or denied service.
Owner:TREND MICRO INC
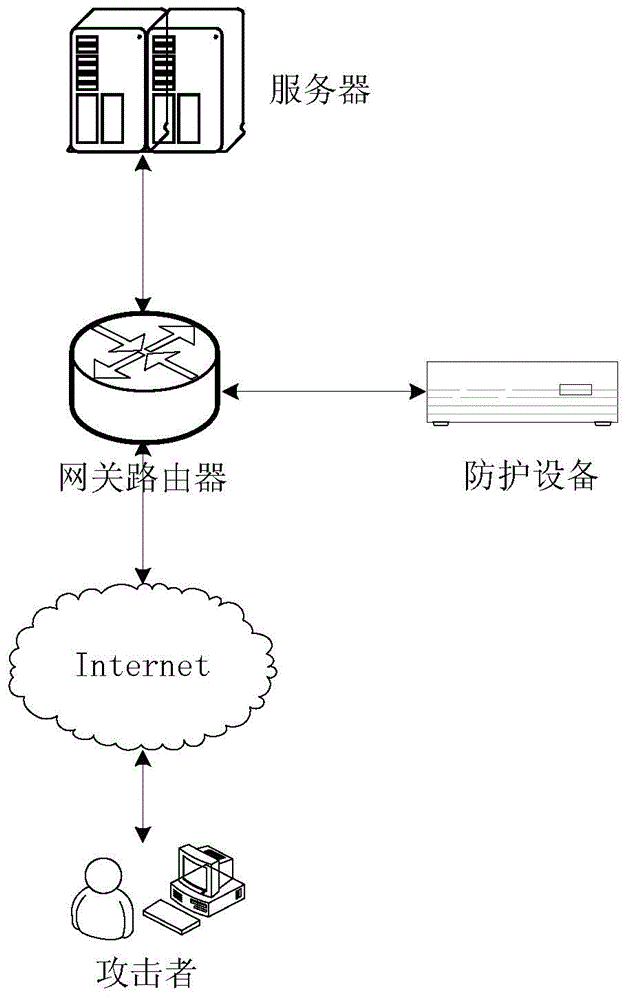
Method, device and system of protection of hostile attacks
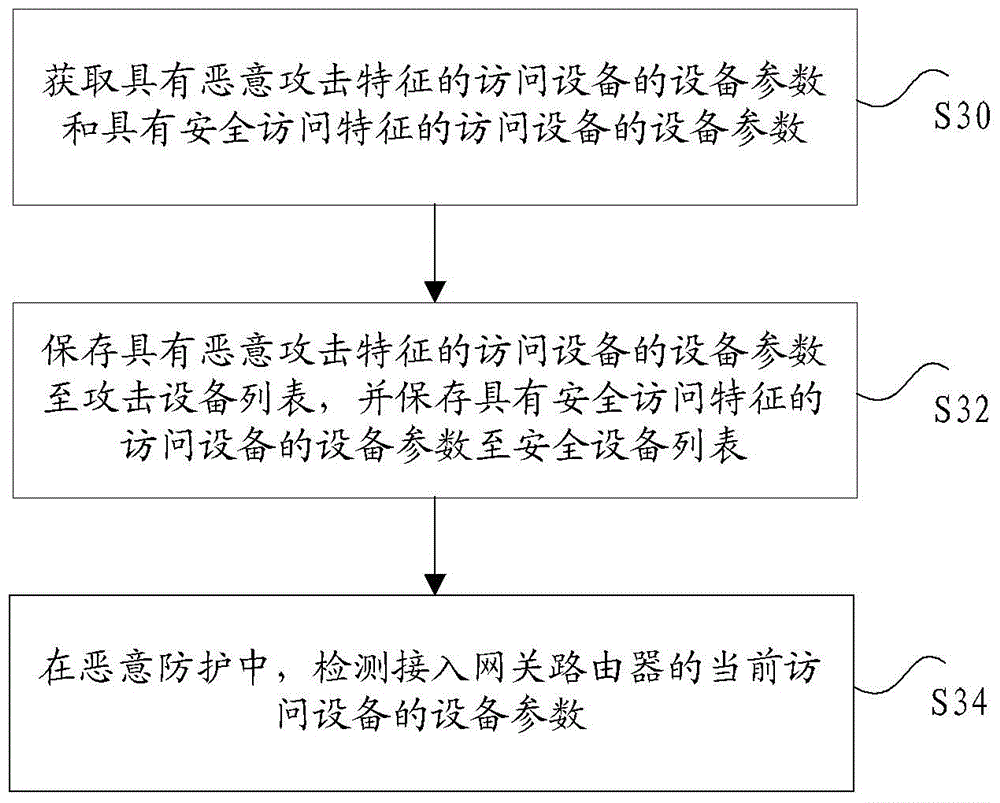
The present invention discloses a method, device and system of protection of hostile attacks. The method of protection of hostile attacks comprises: obtaining device parameters of an access device with hostile attack features and device parameters of an access device with safe access features; storing the device parameters of the access device with hostile attack features to an attack device list, and storing the device parameters of the access device with safe access features to a safety device list; detecting the device parameters of the current access device which accesses a gateway router in the protection of hostile attacks, wherein if the matching degree of the device parameters of the current access device which accesses the gateway router and one or more than one device parameters in the attack device list is not less than a first threshold value, the current access device is determined to be an attack device. The technical problems of the existence of protection vulnerability in the protection scheme aiming at hostile attacks and the lack of the universality are solved in the prior art.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Seismic defense system
A set of seismic detectors is distributed throughout a defense zone in communication with a set of attack or other controllable devices. A seismic signal source controlled by a zone defense coordinator communicates at scheduled times to the seismic detectors and through them to the associated devices to convey mission critical information. The seismic detectors and the attack devices are controlled singularly and / or collectively by self-contained processors. The seismic source may be at a fixed site and is substantially repeatable as well as controllable. The system may be specially adapted to a wide range of terrains including land and water; and from very shallow to very deep water. Targets may be characterized in terms of their typical seismic signatures and the same hardware system used for seismic communication may be also programmed for target detection and device activation.
Owner:HARMON JERALD L +1
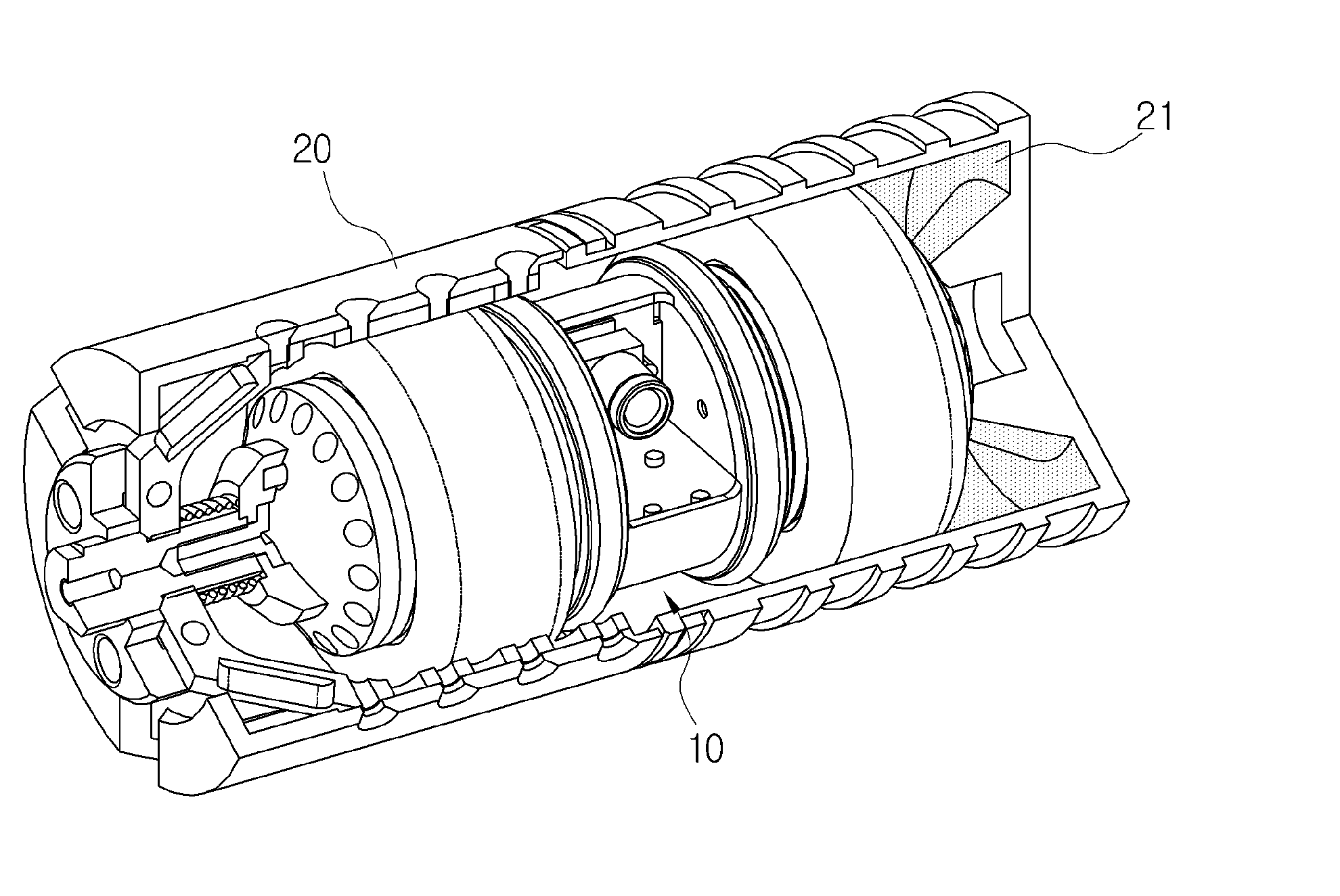
Launchable remote-control attack device
ActiveUS20120043149A1Penetrate fastIncrease lethalityAmmunition projectilesDirection controllersWireless controlRemote control
Provided is a launchable remote-control attack device that enables an operator to remotely grasp the status of a target place and to remotely control weapons it has been equipped with to perform an attack using explosives or gas when necessary. The remote-control attack device includes a cylindrical body with a camera, drivers which are made up of two tires that are disposed on opposite sides of the body and can be driven individually, and battery units for supplying power and which are disposed in central openings of the tires of the drivers. The attack device further includes a plurality of storage units and a wireless control unit.
Owner:KOREA ADVANCED INST OF SCI & TECH +1
Malware Detection for SMS/MMS Based Attacks
Devices, systems, and methods are disclosed which utilize lightweight agents on a mobile device to detect message-based attacks. In exemplary configurations, the lightweight agents are included as contacts on the mobile device addressed to an agent server on a network. A malware onboard the mobile device, intending to propagate, unknowingly addresses the lightweight agents, sending messages to the agent server. The agent server analyzes the messages received from the mobile device of the deployed lightweight agents. The agent server then generates attack signatures for the malware. Using malware propagation models, the system estimates how many active mobile devices are infected as well as the total number of infected mobile devices in the network. By understanding the malware propagation, the service provider can decide how to deploy a mitigation plan on crucial locations. In further configurations, the mechanism may be used to detect message and email attacks on other devices.
Owner:AT&T INTPROP I L P
Seismic defense system
A set of seismic detectors is distributed throughout a defense zone in communication with a set of attack or other controllable devices. A seismic signal source controlled by a zone defense coordinator communicates at scheduled times to the seismic detectors and through them to the associated devices to convey mission critical information. The seismic detectors and the attack devices are controlled singularly and / or collectively by self-contained processors. The seismic source may be at a fixed site and is substantially repeatable as well as controllable. The system may be specially adapted to a wide range of terrains including land and water; and from very shallow to very deep water. Targets may be characterized in terms of their typical seismic signatures and the same hardware system used for seismic communication may be also programmed for target detection and device activation.
Owner:HARMON JERALD L +1
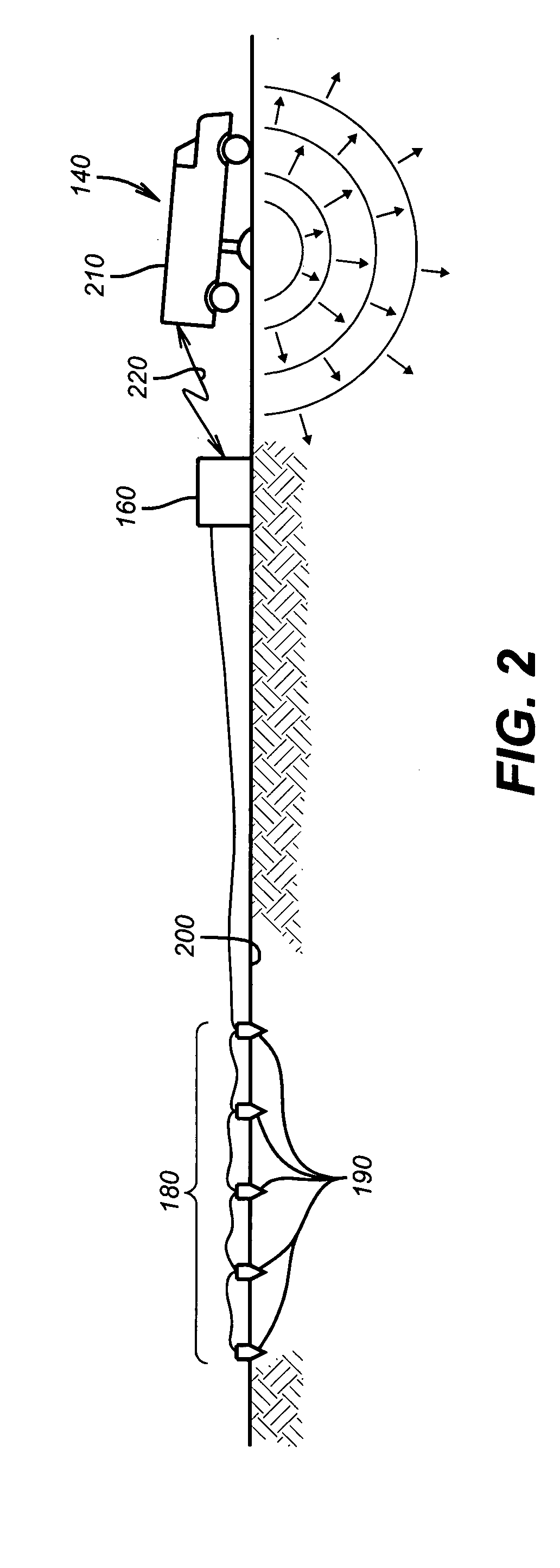
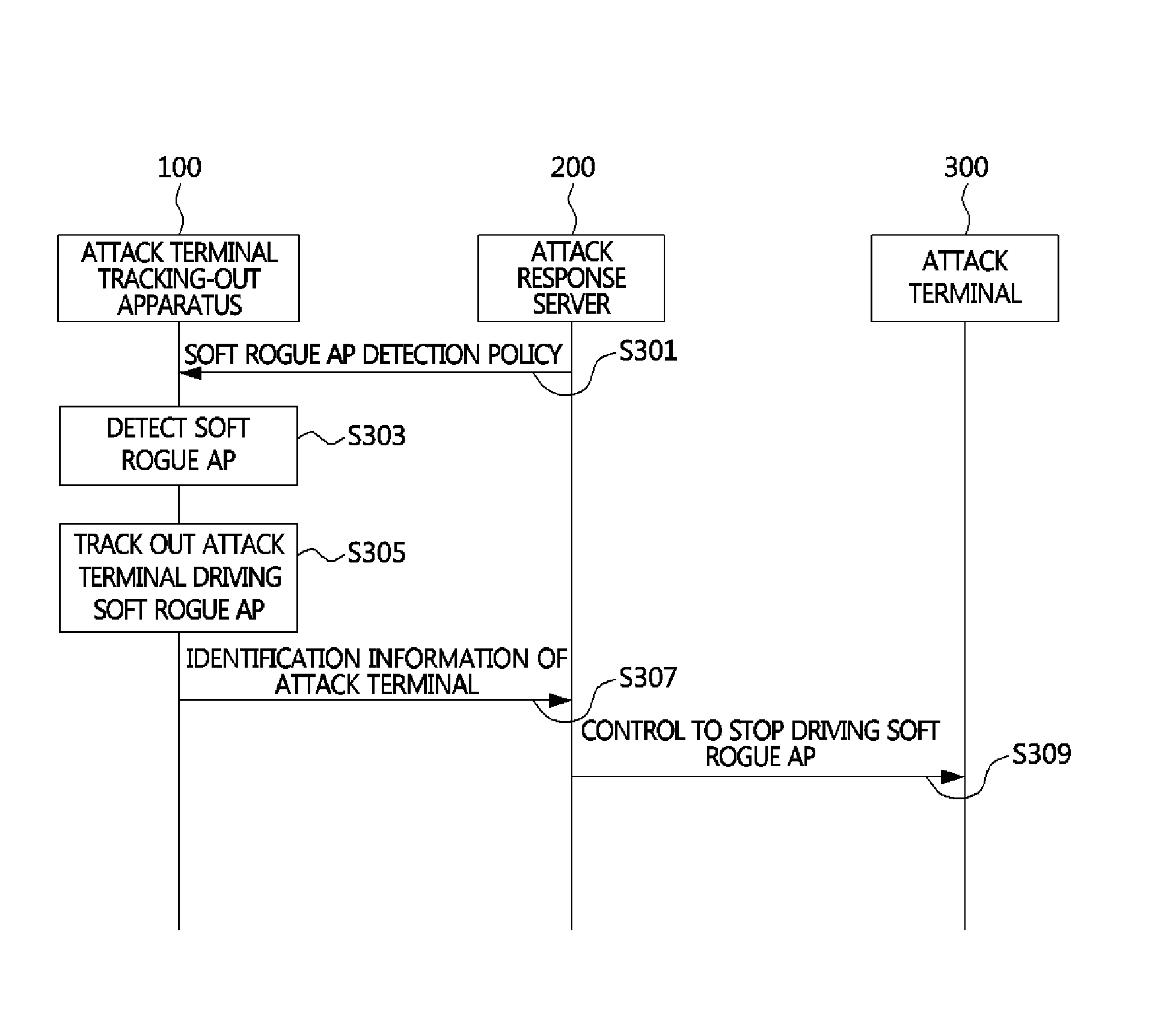
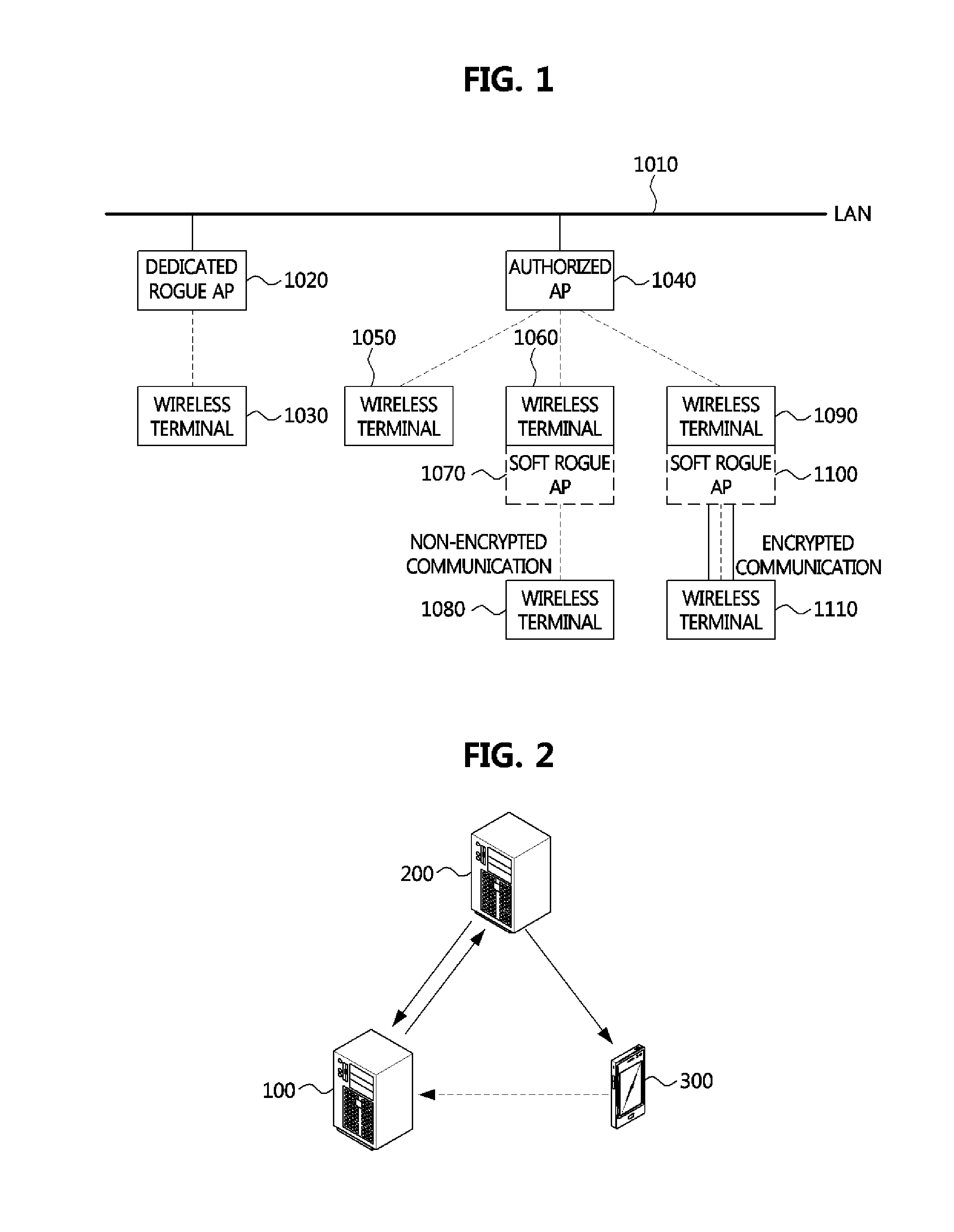
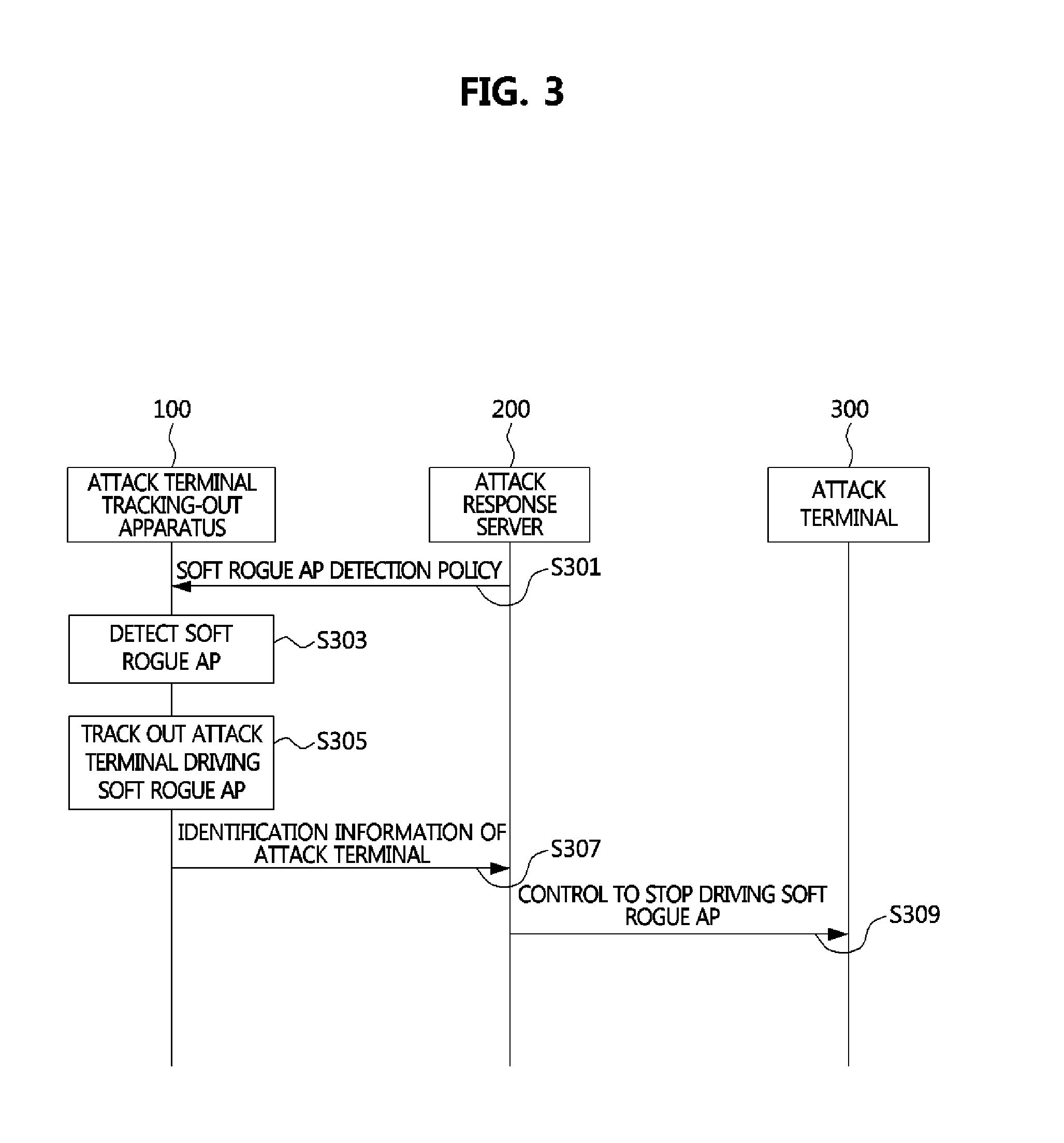
Method for tracking out attack device driving soft rogue access point and apparatus performing the method
InactiveUS20140130155A1Effective blockingEasy to trackMemory loss protectionError detection/correctionComputer networkRogue access point
Owner:ELECTRONICS & TELECOMM RES INST
Nut shell breaking machine
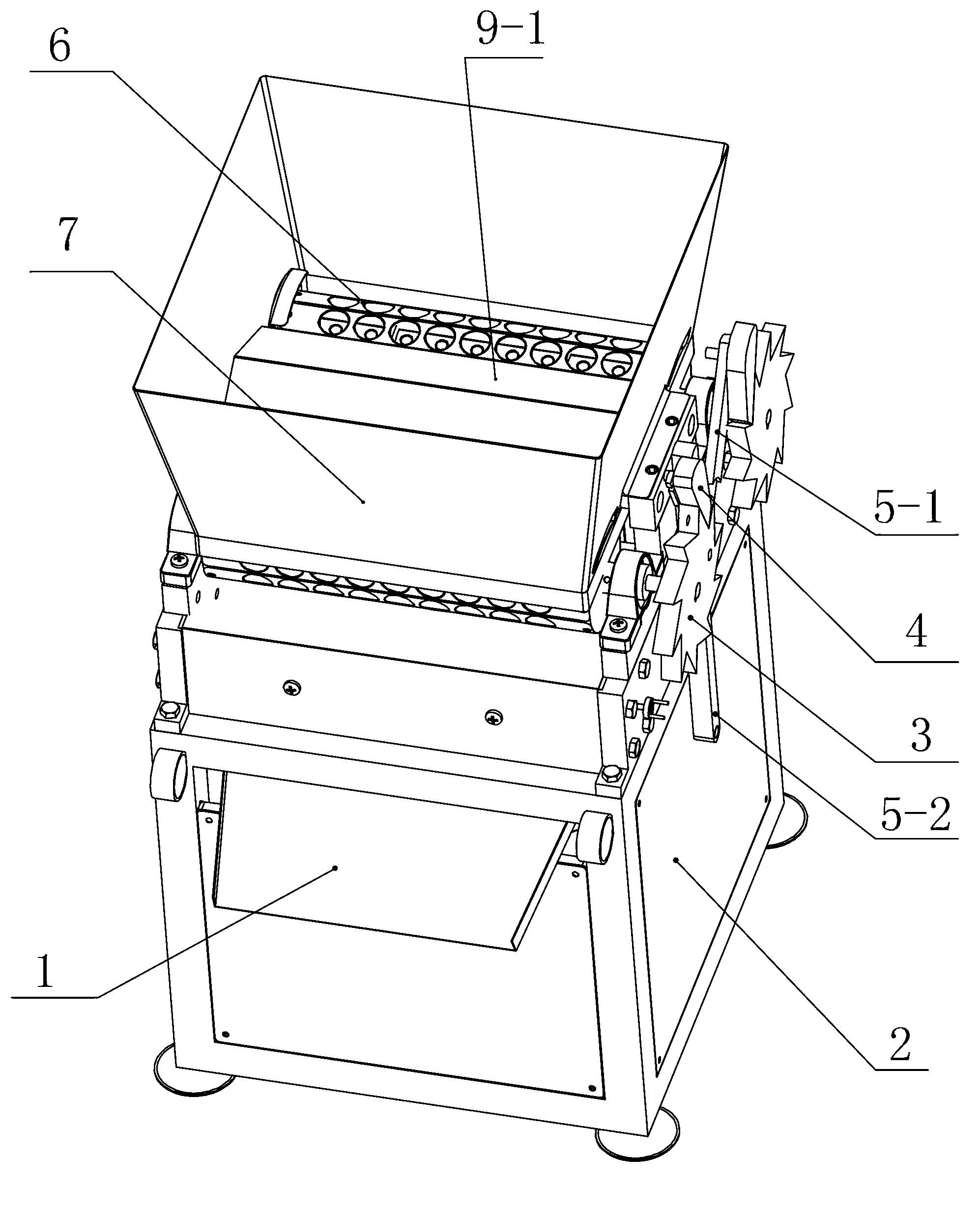
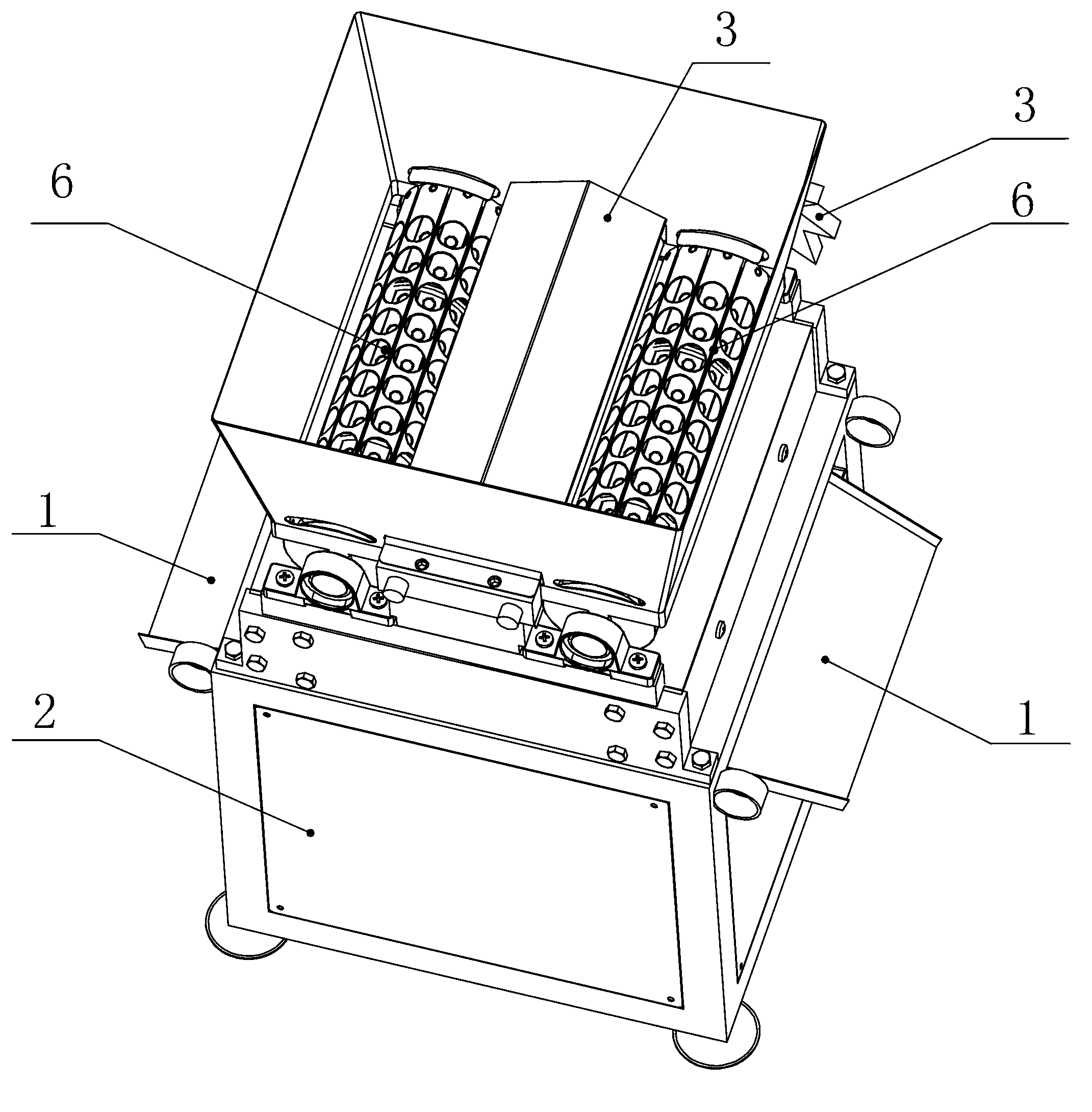
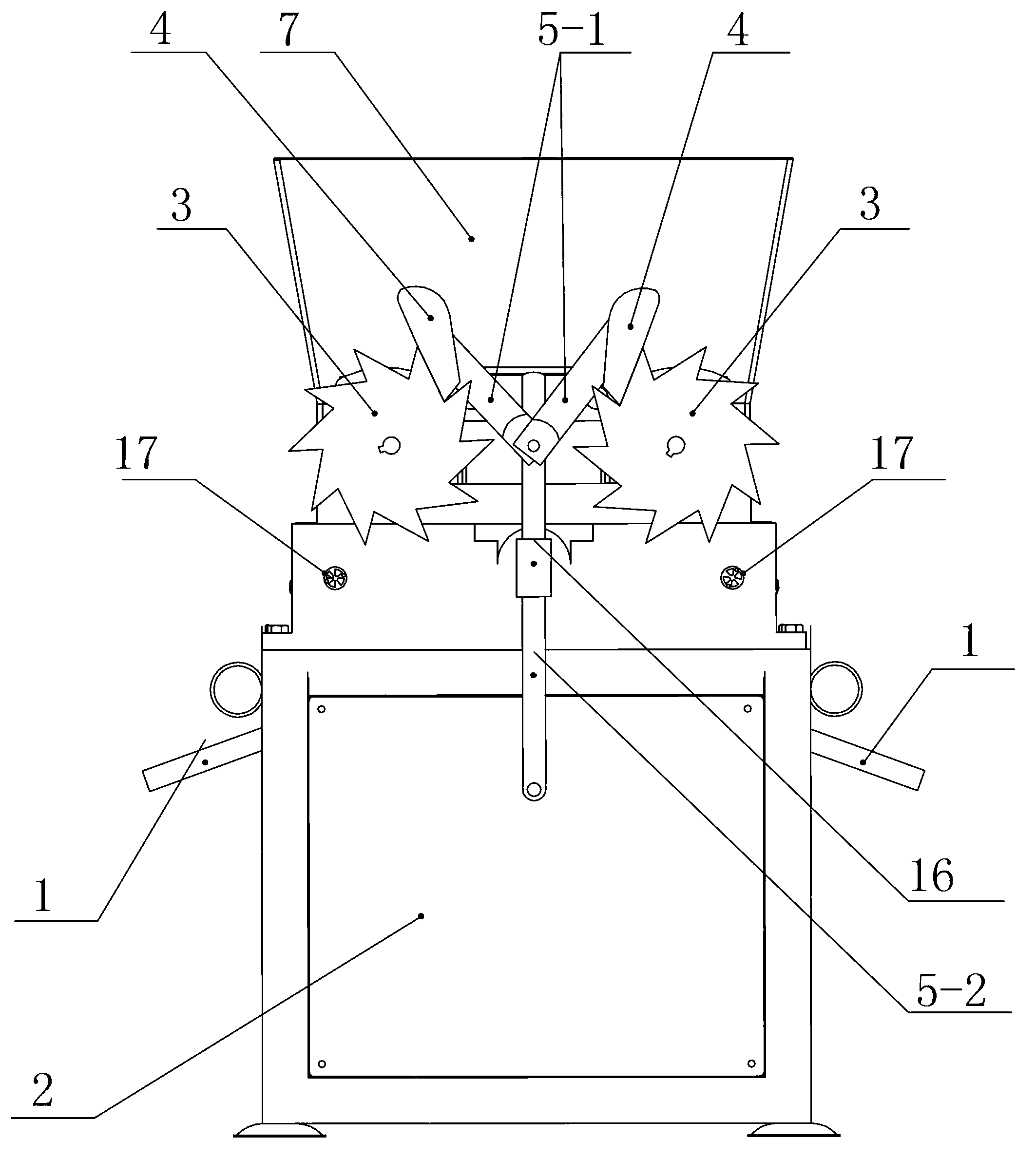
InactiveCN103005621ASmall space volumeIncrease productivityHuskingHullingEngineeringMechanical engineering
The invention relates to a nut shell breaking machine, aiming at providing the shell breaking machine which has the characteristics of simple structure, high production efficiency and convenience in use. The shell breaking machine comprises a rack, a feed hopper and a discharge port, wherein the feed hopper and the discharge port are positioned on the rack. The shell breaking machine is characterized in that a feeding device and an attacking device are also arranged at the shell breaking machine; the feeding device comprises two rotatable feeding rollers, a ratchet-pawl mechanism and a power machine, the two feeding rollers are horizontally and symmetrically arranged at the bottom end of the feed hopper, and the ratchet-pawl mechanism is used for driving the feeding rollers to intermittently rotate; the attacking device comprises fixed attacking plates, movable attacking plates, a transverse push rod and a power machine; the fixed attacking plates are positioned under each feeding roller and are vertically fixed, and the movable attacking plates are arranged correspondingly to the plate faces of the fixed attacking plates and are positioned at the inner side of the rack; the transverse push rod is hinged with the movable attacking plates to drive the movable attacking plates to do a horizontal attacking motion; and the power mechanism is used for driving the transverse push rod.
Owner:杭州虹环电子有限公司
Launchable remote-control attack device
ActiveUS8636096B2Penetrate fastIncrease lethalityAmmunition projectilesProgramme-controlled manipulatorWireless controlRemote control
Provided is a launchable remote-control attack device that enables an operator to remotely grasp the status of a target place and to remotely control weapons it has been equipped with to perform an attack using explosives or gas when necessary. The remote-control attack device includes a cylindrical body with a camera, drivers which are made up of two tires that are disposed on opposite sides of the body and can be driven individually, and battery units for supplying power and which are disposed in central openings of the tires of the drivers. The attack device further includes a plurality of storage units and a wireless control unit.
Owner:KOREA ADVANCED INST OF SCI & TECH +1
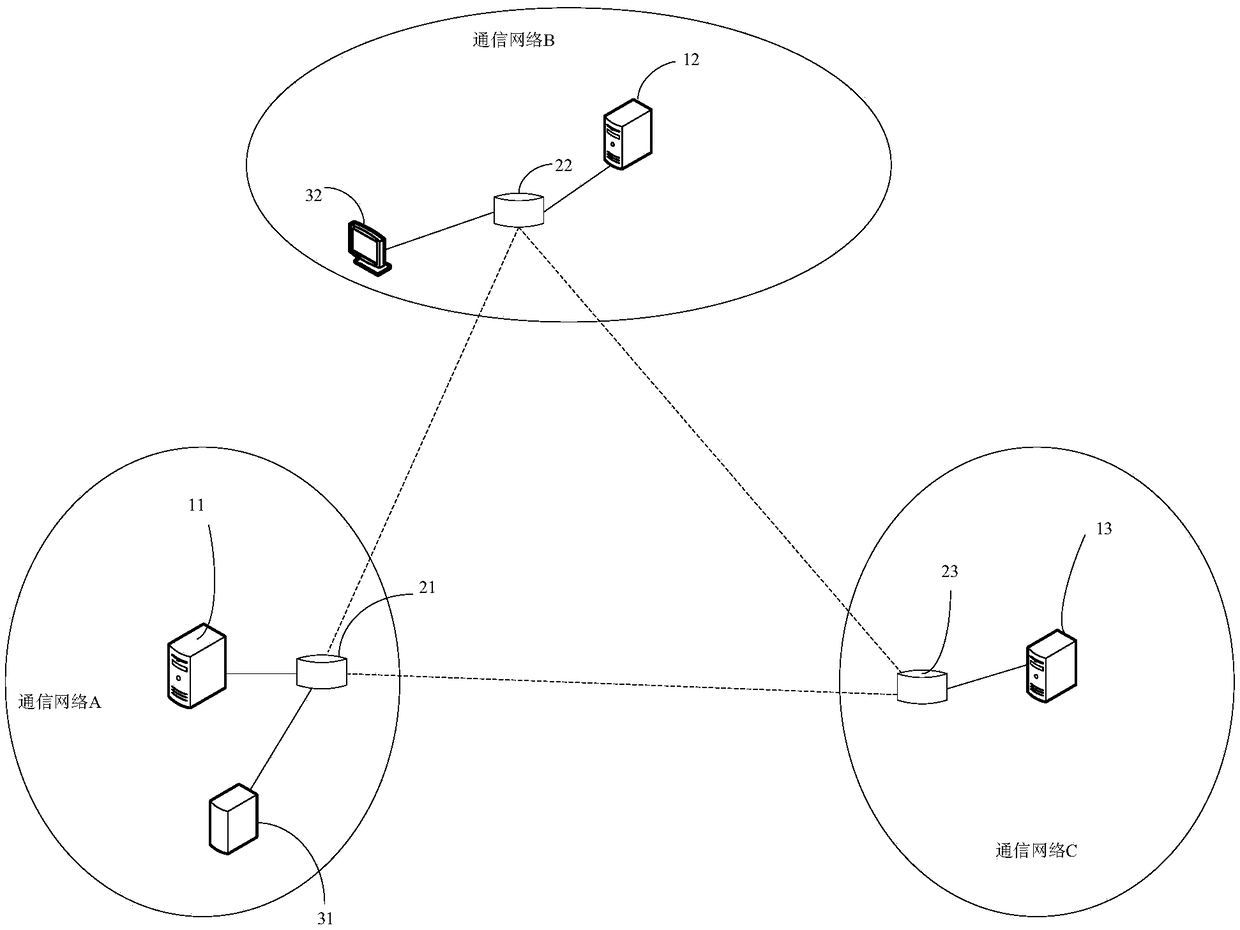
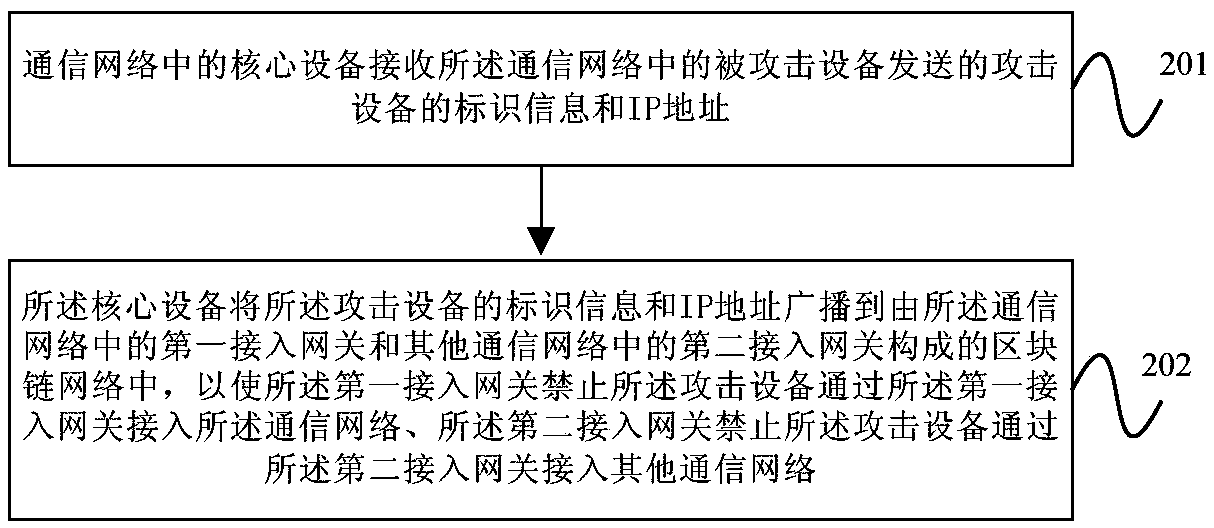
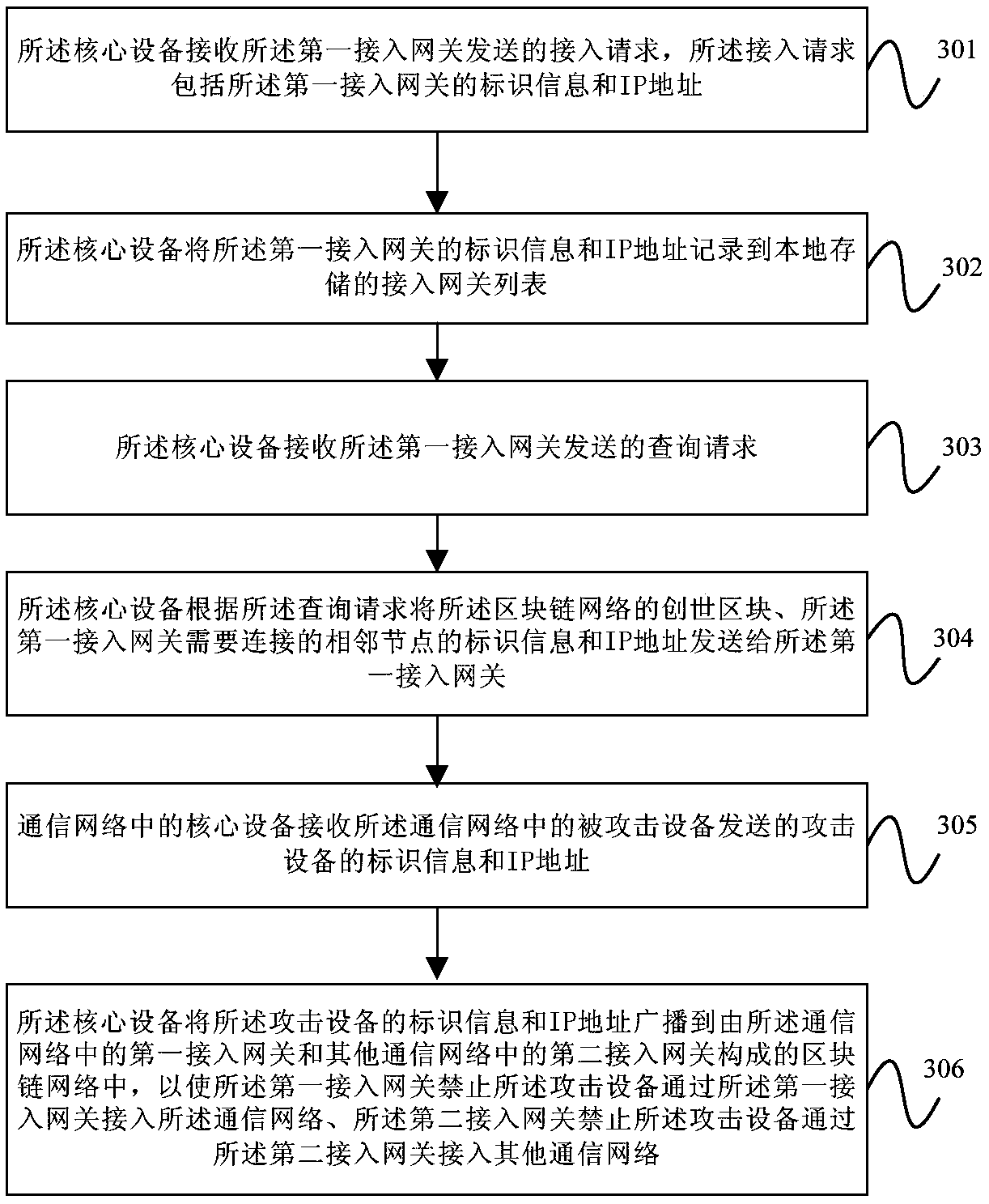
Attack prevention processing method and device, equipment and storage medium
The embodiment of the invention provides an attack prevention processing method and device, equipment and a storage medium. The method comprises the steps that core equipment in a communication network receives identifier information and an IP address, sent by attacked equipment in the communication network, of attacking equipment; and the identifier information and the IP address of the attackingequipment are broadcast to a block chain network formed by a first access gateway in the communication network and second access gateways in other communication networks, therefore, the first accessgateway can forbid the attacking equipment from accessing the communication network through the first access gateway, and the second access gateways can forbid the attacking equipment from accessing the other communication networks through the second access gateways. According to the method, the core equipment broadcasts the identifier information and the IP address of the attacking equipment to the block chain network formed by the access gateways of different communication networks, therefore, the access gateways of all the communication networks can forbid the attacking device from accessing the corresponding communication networks, and then the DDoS attack is effectively prevented.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
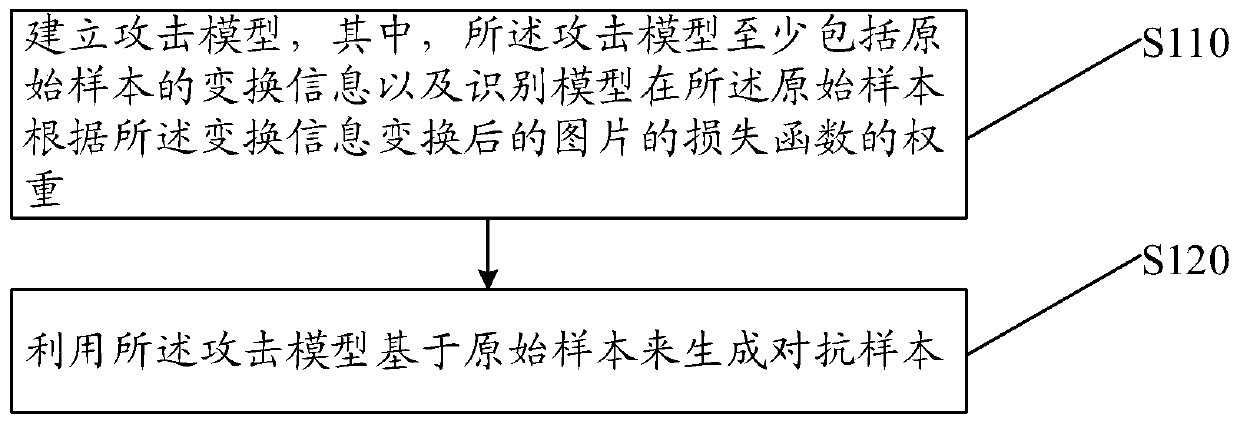
Deep neural network attack method and device, medium and computing equipment
PendingCN110084002AImprove transfer abilityLow costNeural architecturesProgram/content distribution protectionAttack modelAlgorithm
The embodiment of the invention provides a deep neural network attack method. The method comprises the steps that an attack model is established, and the attack model at least comprises transformationinformation of an original sample and the weight of a loss function, transformed by a picture of the original sample according to the transformation information, of an identification model; an adversarial sample is generated based on an original sample using the attack model. According to the method, the confrontation sample is generated for the real picture and the group of pictures after translation, and the transfer performance of the generated confrontation sample is greatly improved, so that the sensitivity of the confrontation sample to the attacked model is remarkably reduced, and thegeneration cost of the confrontation sample is reduced. In addition, the embodiment of the invention provides a deep neural network attack device, a medium and computing equipment.
Owner:TSINGHUA UNIV
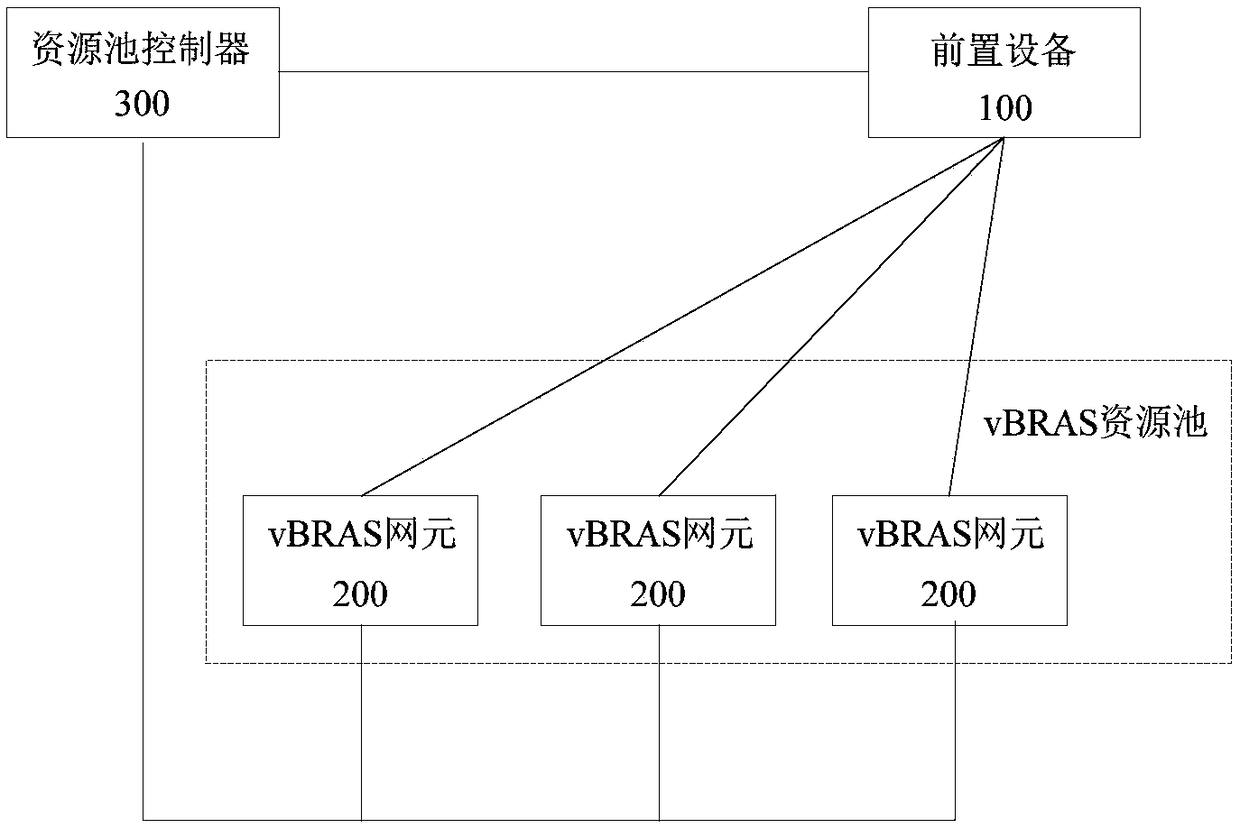
Anti-attack method and device, as well as electronic equipment
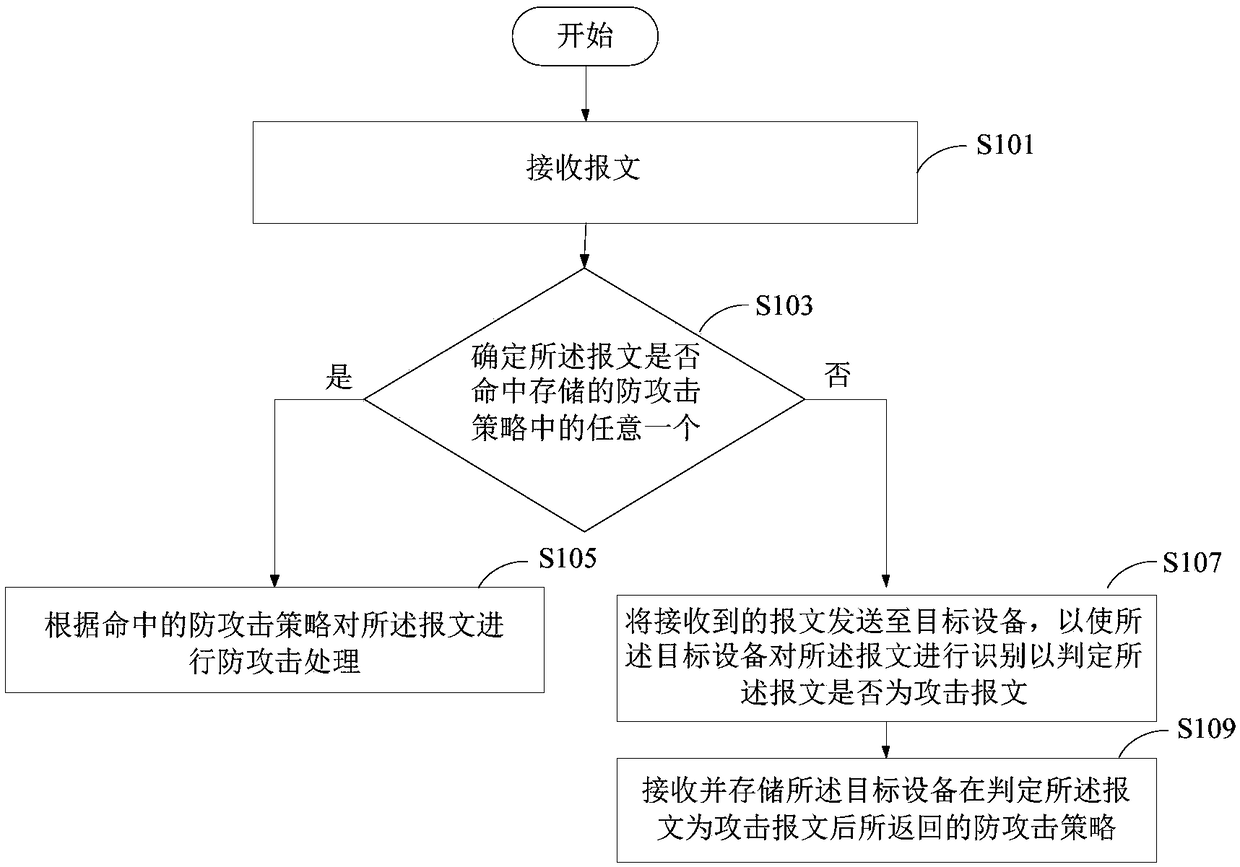
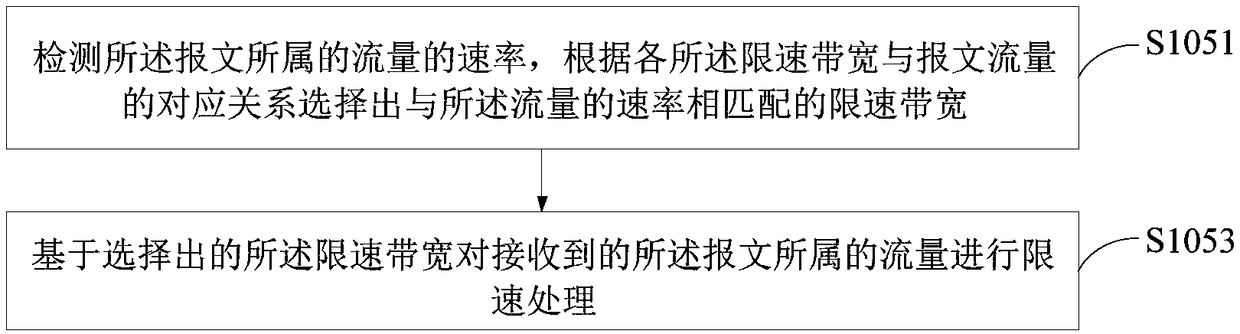
ActiveCN108429731AReduce the risk of being attackedAvoid attackData switching networksAttack deviceElectronic equipment
Embodiments of the invention provide an anti-attack method, an anti-attack device, and a piece of electronic equipment. The method comprises the following steps of: receiving a packet; determining whether the packet hits any one of the stored anti-attack policies; if so, performing an anti-attack process on the packet according to the hit anti-attack policy; otherwise, sending the received packetto the target equipment, so that the target equipment identifies the packet to determine whether the packet is an attack packet; receiving and storing the anti-attack policy returned by the target equipment after determining that the packet is an attack packet. The anti-attack solution provided by the embodiments of the invention performs the anti-attack protection on the vBRAS network element bycombining the pre-equipment, thereby reducing the risk of the vBRAS network element being attacked, and reducing the CPU consumption of the vBRAS network element.
Owner:NEW H3C TECH CO LTD
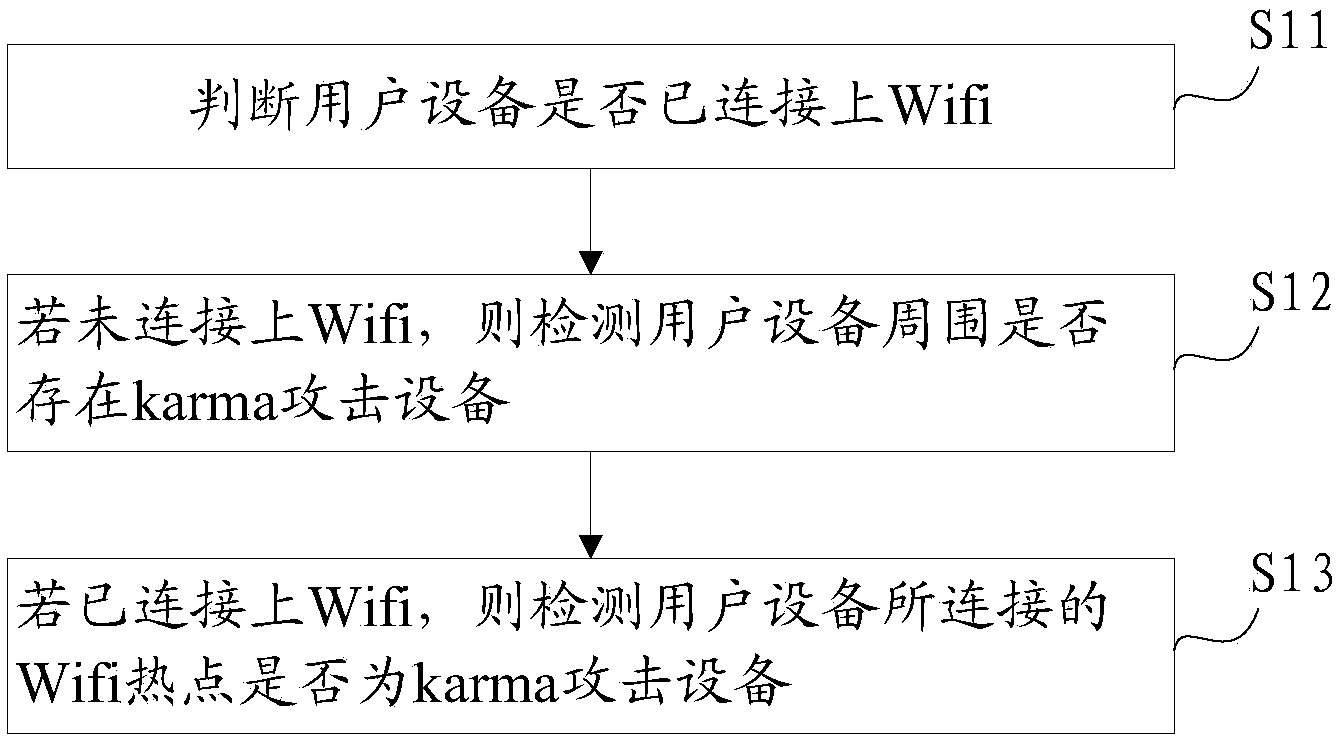
Method and device for detecting karma attack
The embodiment of the invention discloses a method and device for detecting the karma attack, and relates to the technical field of wireless networks. The method and the device solve the problem that in the prior art, the karma attack on a user device may happen when the user device has access to the WIFI. The method for detecting the karma attack includes the steps of judging whether the user device has had access to the Wifi or not, detecting whether a karma attack device exists around the user device or not if the user device has not had access to the Wifi, and detecting whether the Wifi hotspot which the user device has access to is the karma attack device or not if the user device has had access to the Wifi. The method and the device are mainly used for detecting whether the karma attack happens to the user device when the user device has access to the Wifi.
Owner:KINGSOFT
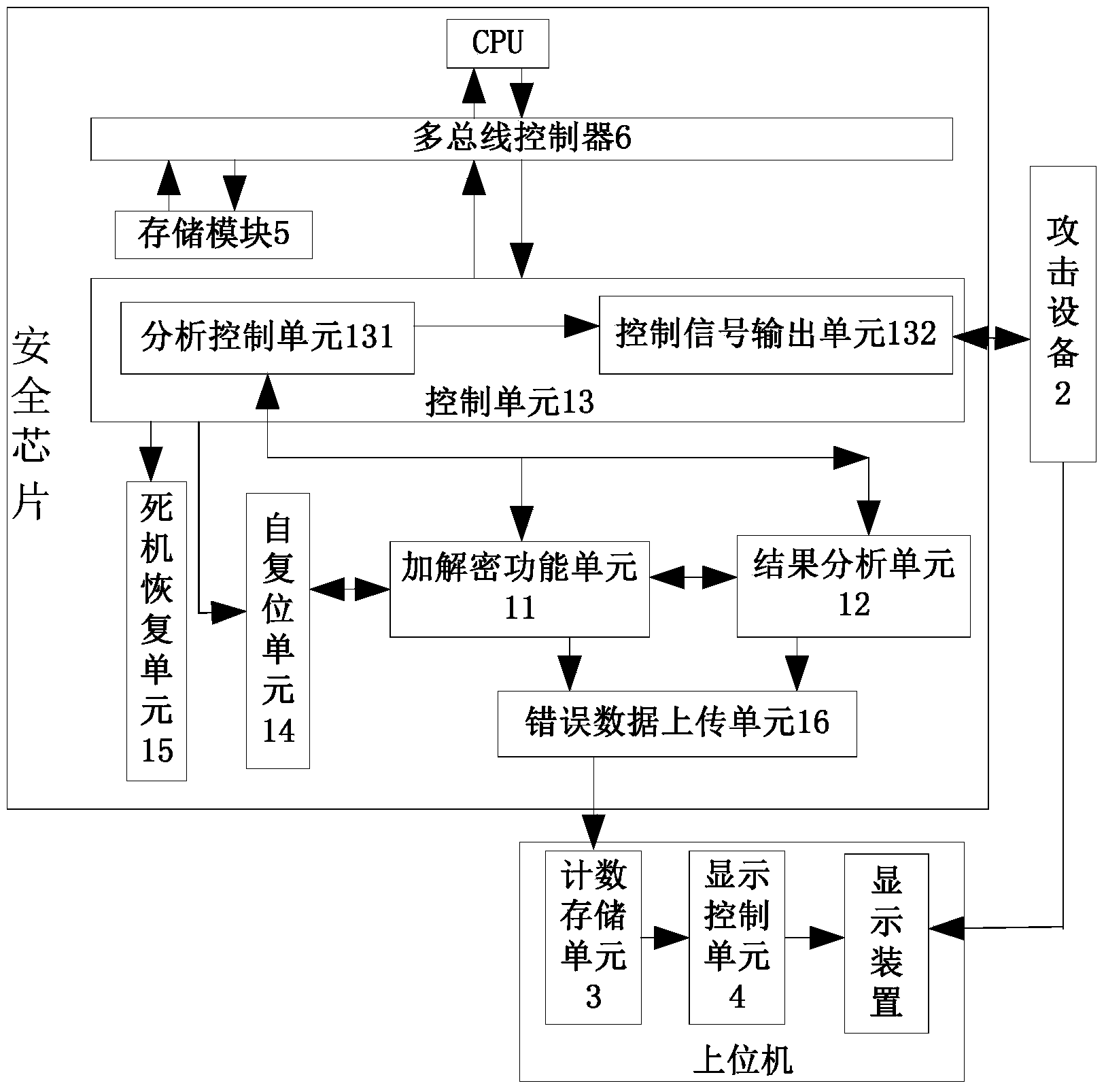
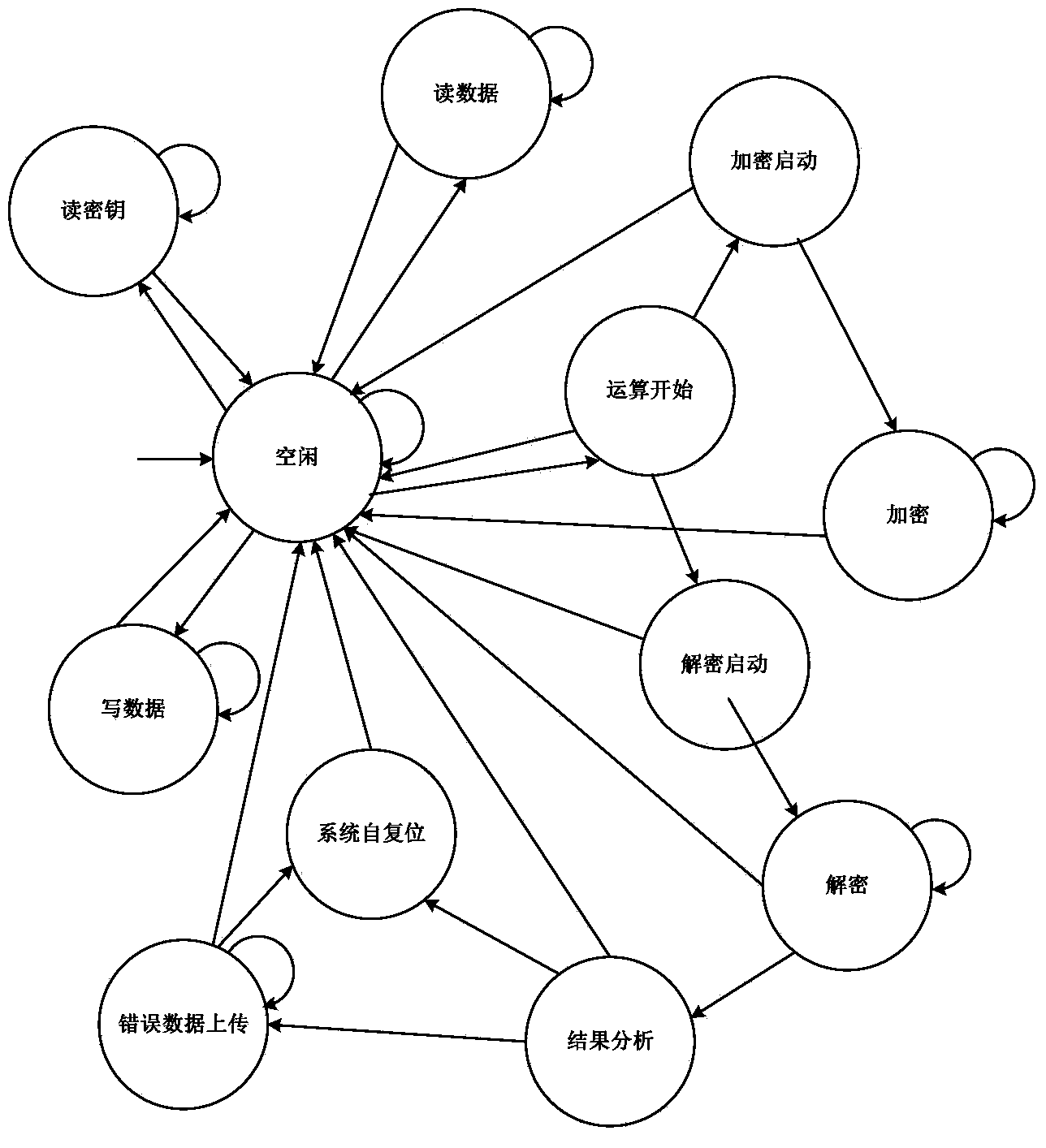
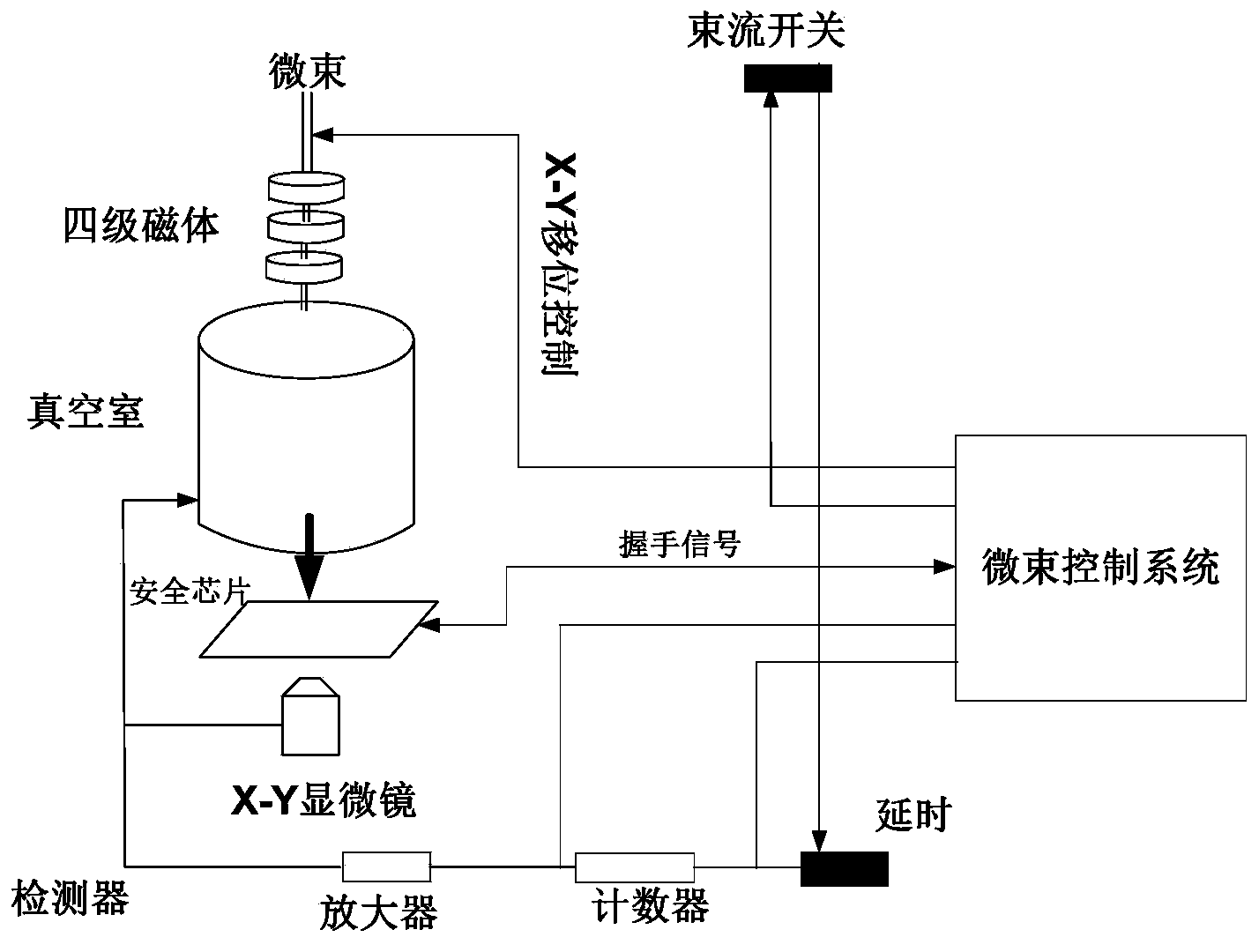
System for detecting safety performance of safety chip under induced error attacks
ActiveCN103530566ADetect securityThe detection environment is stableInternal/peripheral component protectionPlatform integrity maintainanceEmbedded systemEncryption
The invention relates to a system for detecting the safety performance of a safety chip under induced error attacks. The system comprises a control unit, a result analysis unit and an attack device, wherein the control unit controls a safety chip encryption and decryption functional unit to carry out encryption and decryption calculation under the induced error attacks; the result analysis unit reads a encryption and decryption calculation result and compares the result with a built-in reference result; the attack device performs the induced error attacks on the safety chip under the control of the control unit. Therefore, the safety chip and the attack device are combined together through the control unit, the calculation result, under the induced error attacks, of the encryption and decryption functional unit is analyzed through the result analysis unit, and after an error is caused on the encryption and decryption calculation result, the attack device is controlled by the control unit to position coordinates of the positions, on the safety chip, of the induced error attacks as fault point coordinates, so that the system effectively detects the safety performance of the safety chip and positions the fault points.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
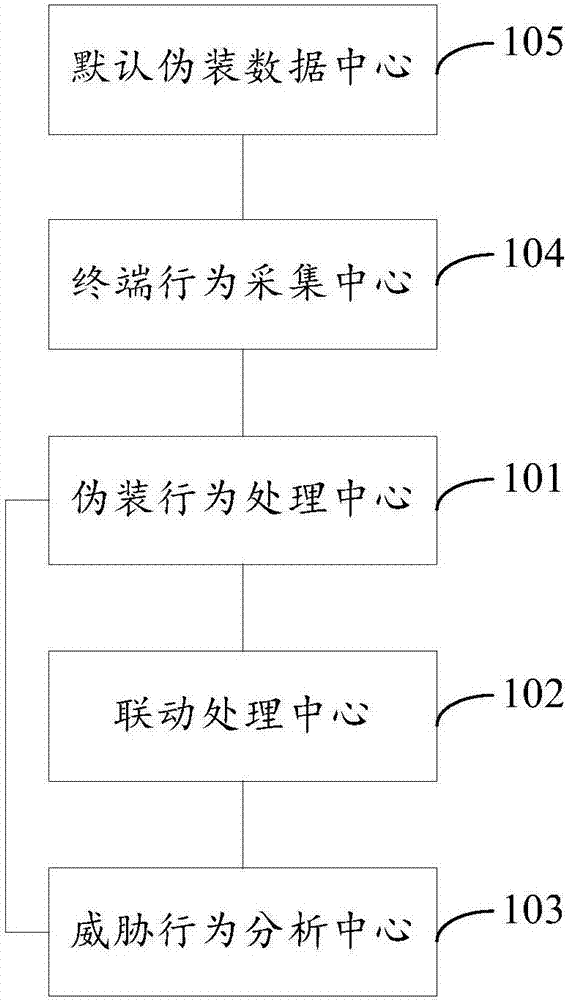
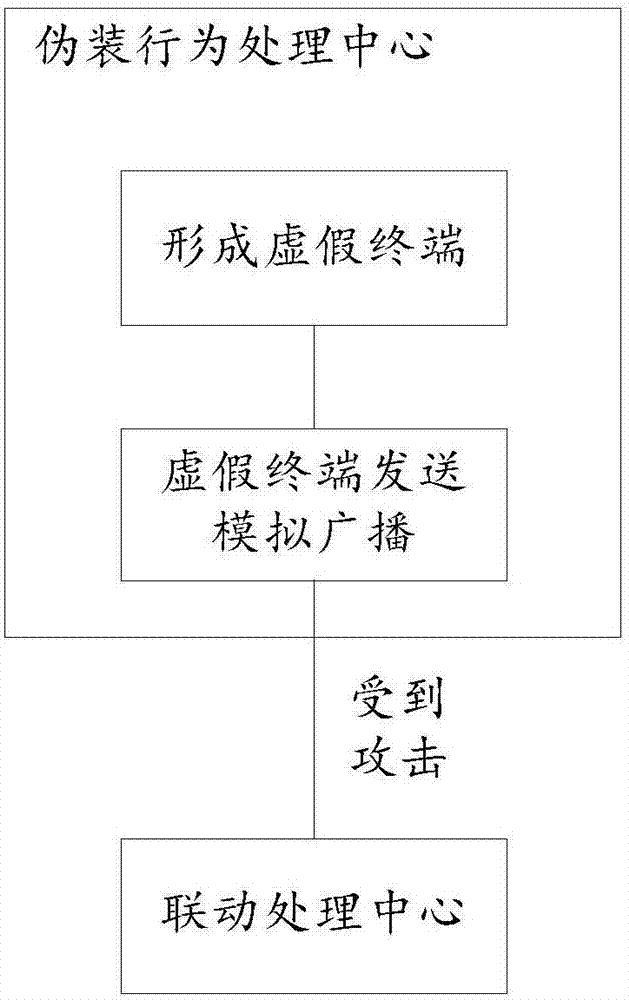
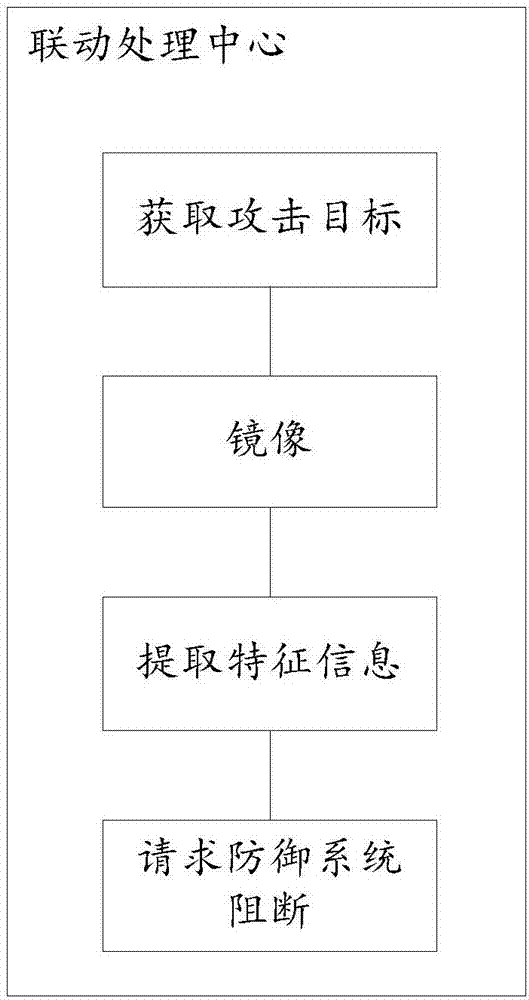
Network anti-attack device, system and method, readable medium and storage controller
The invention discloses a network anti-attack device, system and method, a readable medium and a storage controller. The network anti-attack device comprises a camouflage behavior processing center, a linkage processing center and a threatening behavior analysis center, wherein the camouflage behavior processing center is used for camouflaging a preset number of false terminals and making the false terminals to transmit analog broadcasts to a network; the linkage processing center is used for intercepting the attack and extracting attack behavior characteristics of the attack when the analog broadcasts are attacked and transmitting the attack behavior characteristics to a defensive system in the network to interrupt the attack through the defensive system; and the threatening behavior analysis center is used for receiving interrupt information transmitted by the defensive system after successfully interrupting the attack, extracting interrupt information characteristics of the interrupt information, packaging the attack behavior characteristics and the interrupt information characteristics to form a characteristic group and transmitting the characteristic group to a database to form a characteristic library. The problem that a passive defense mode falls behind virus transmission is effectively solved, an overall network defense linkage system is formed, and the security of a real terminal is improved.
Owner:BEIJING VRV SOFTWARE CO LTD
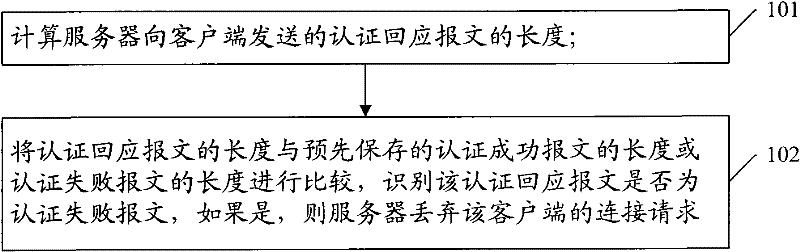
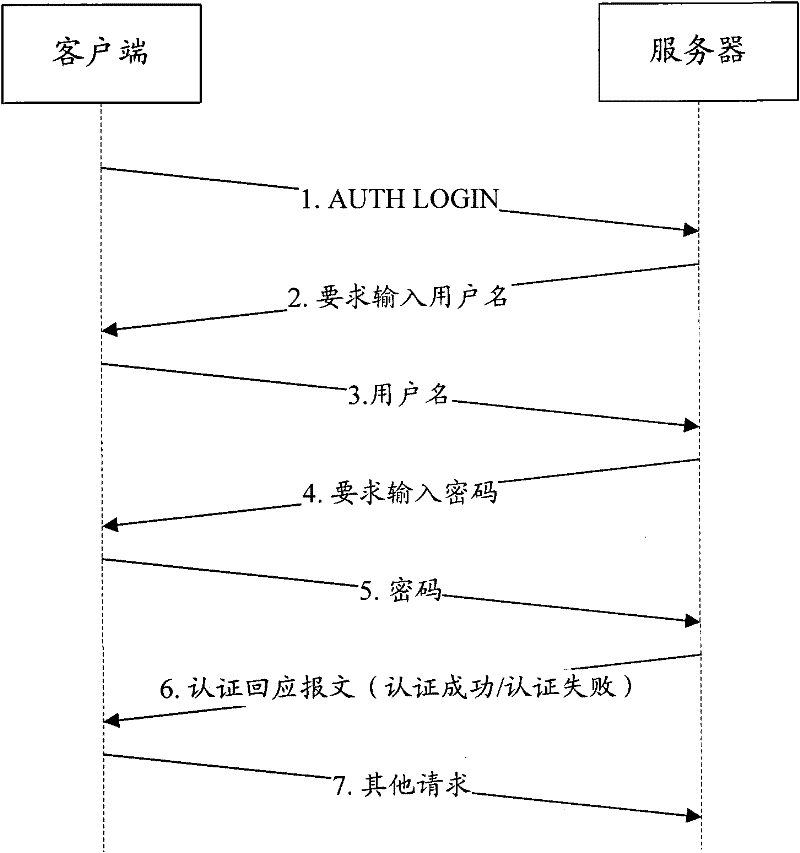
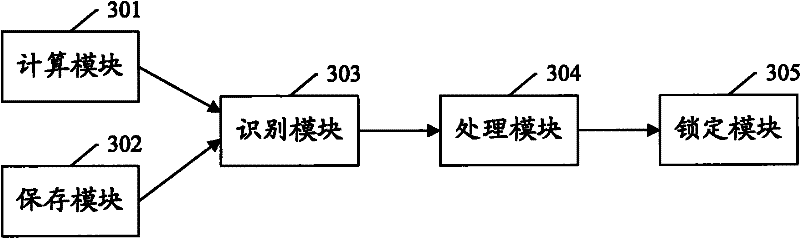
A method and device for defending against ddos attacks
The invention provides a distributed deny of service (DDoS) attack defense method and a device, wherein the method comprises the following step of computing the length of an authentication response message which is sent to a client side through a server. The computation pattern comprises the following steps of: respectively obtaining the values of transmission control protocol (TCP) acknowledgement numbers acknowledgement (ACK) in the last message and the next message of the authentication response message, computing the difference of the TCP ACK value in the next message and the TCP ACK value in the last message, wherein the difference is the length of the authentication response message; and comparing the length of the authentication response message with the length of a successfully authenticated message or an unsuccessfully authenticated message which is stored in advance, identifying whether the authentication response message is the unsuccessfully authenticated message, and if the answer is yes, the server dropping a connection request of the client side. Through the DDoS attack defense method and the device, an attacked device and a normal device can be distinguished, and consequently the DDoS attack on an E-mail server can be defended.
Owner:NEW H3C TECH CO LTD
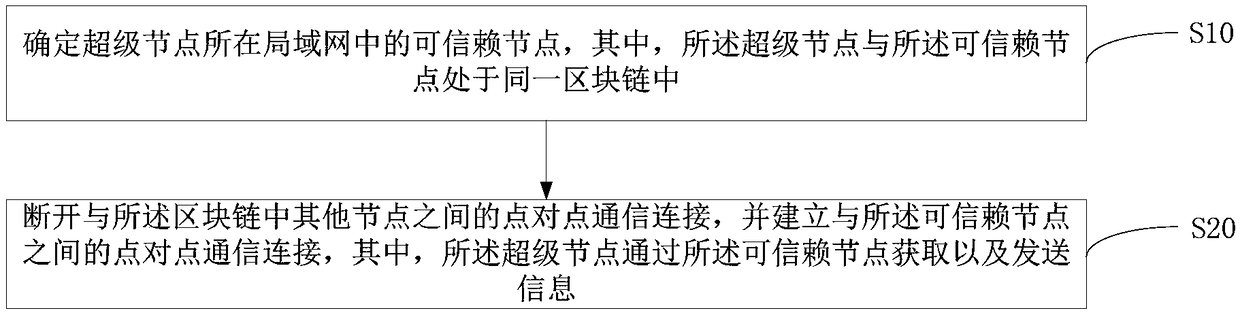
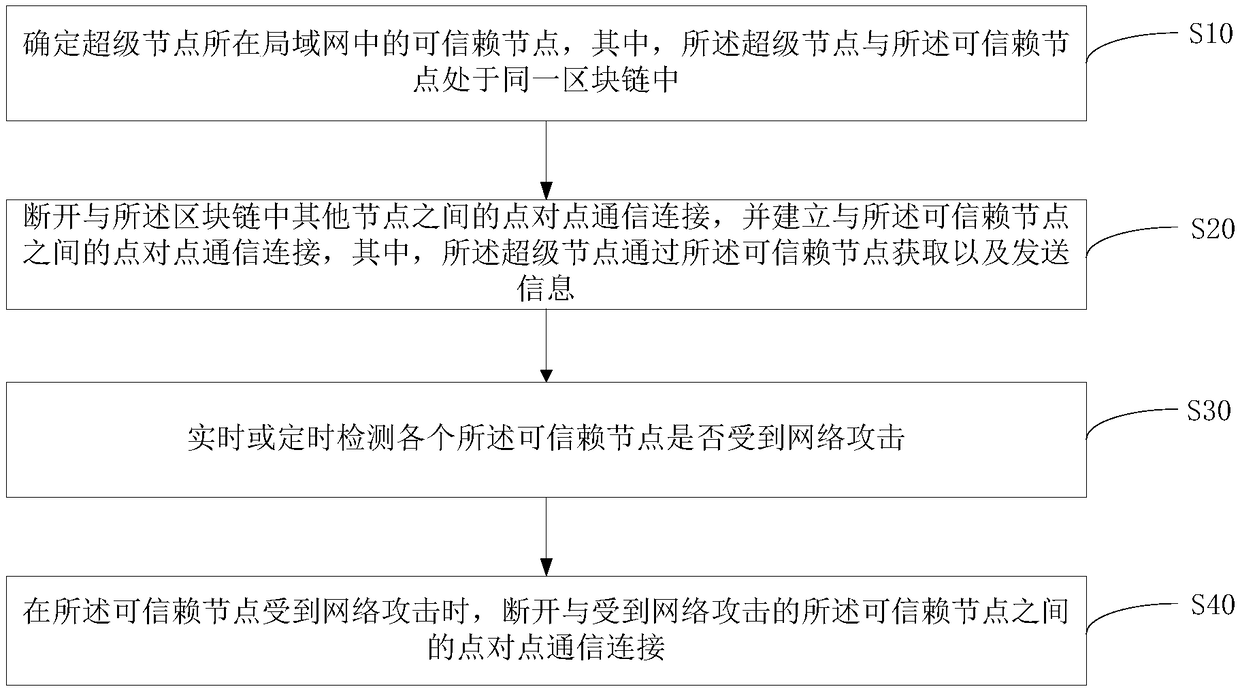
Blockchain system and anti-attack method and device of blockchain super node
The present invention discloses an anti-attack method of a blockchain super node. The method comprises the following steps of: determining trusted nodes in a local area network where a super node is located, wherein the super node and the trusted node are located in the same blockchain; and disconnecting the point-to-point communication connection between the other nodes in the blockchain, and establishing the point-to-point communication connection between the trusted nodes, wherein the super node obtains and sends information through the trusted node. The present invention further disclosesan anti-attack device of a blockchain super node and a blockchain system. The blockchain information safety is high.
Owner:杭州链汇通区块链科技有限公司
Door and window defense system and apparatus composition
InactiveCN101038695AImprove securityStrong repressionAlarms with smoke/gas/colored-powderBurglar alarm short radiation actuationInductorMulti path
The invention is a door and window defense system and a device composing thereof, is a multi-path gradual defense mechanism composed of two infrared inductor, an illumination lamp group, an video capturing device and an attack device, the defense mechanism comprises a first mechanism by which lamplight illumination is started to achieve an elementary caution and stopping effect when a person approachs to the door or window in 1-3 M, a second mechanism by which the video capturing device is started to store video data of the person when the person approachs to the door or window in 60-100 cm, a third mechanism by which the attack device is started to attack the person when the door or window is damaged by the person, thereby achieving a strong stopping and defense effect, with the defense mechanism, the door and window is provided with an initiative defense function to increase safety of home circumstance.
Owner:沈协和
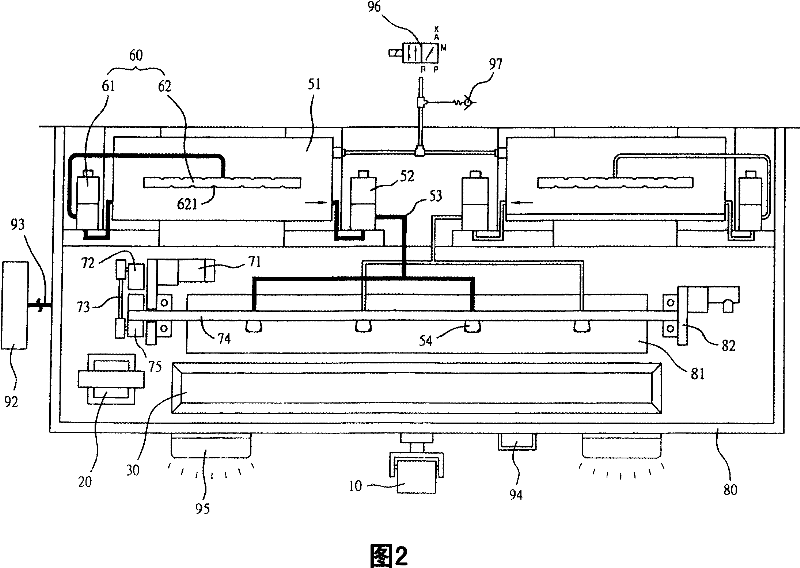
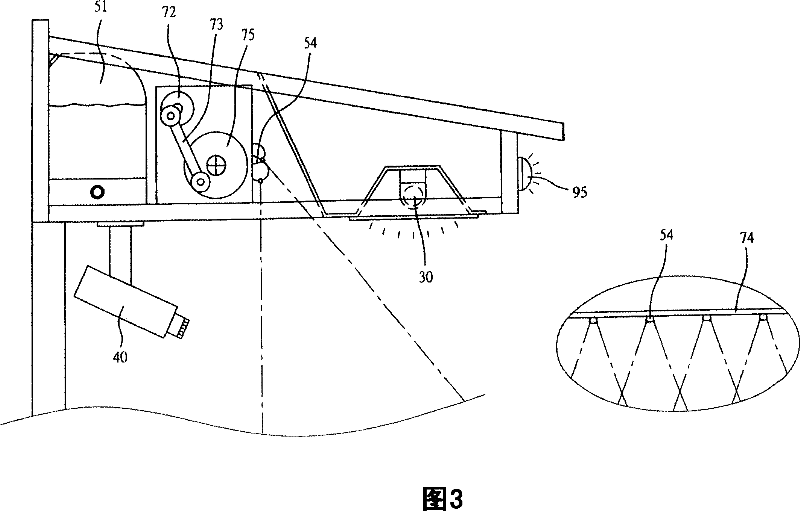
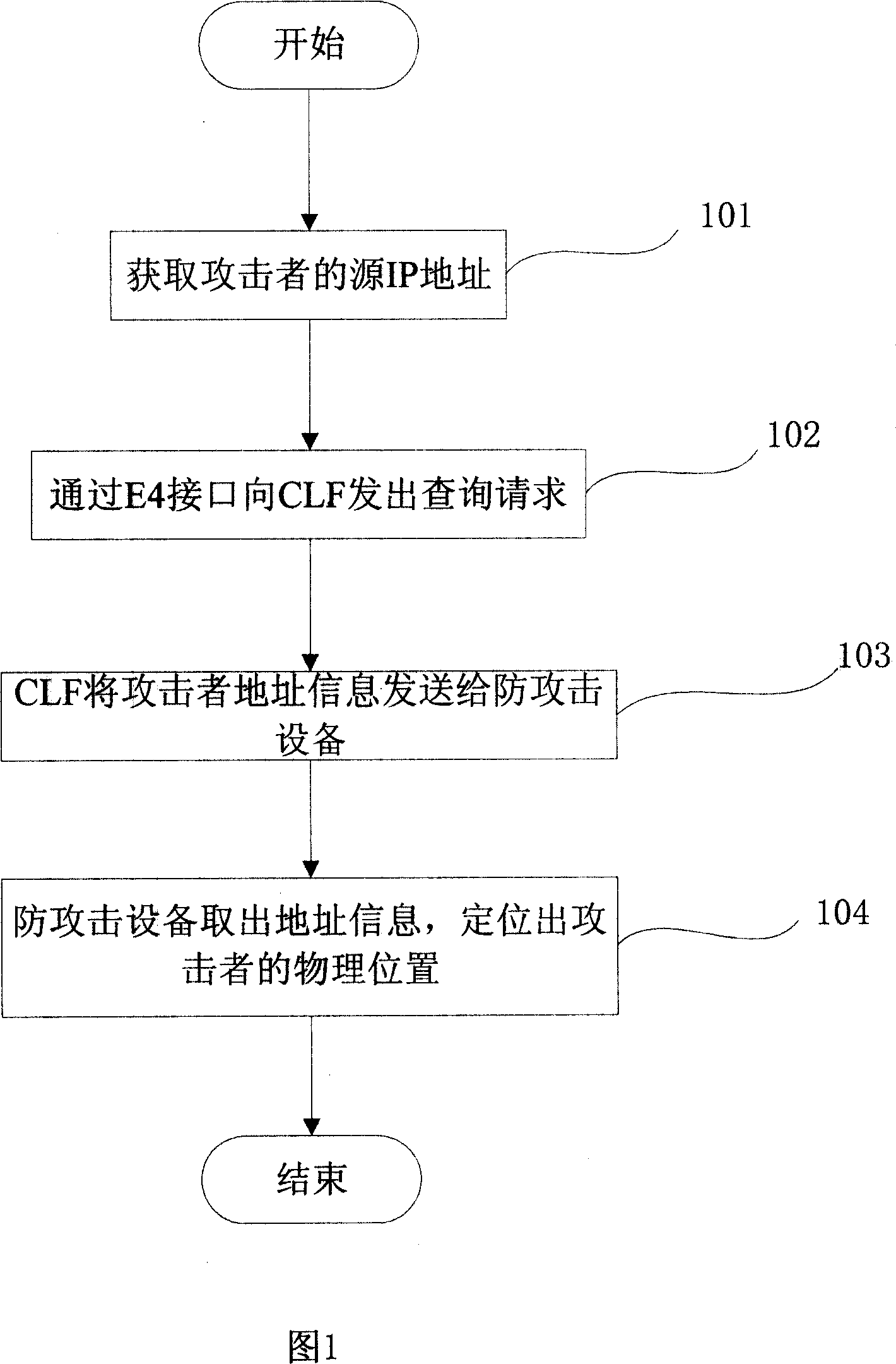
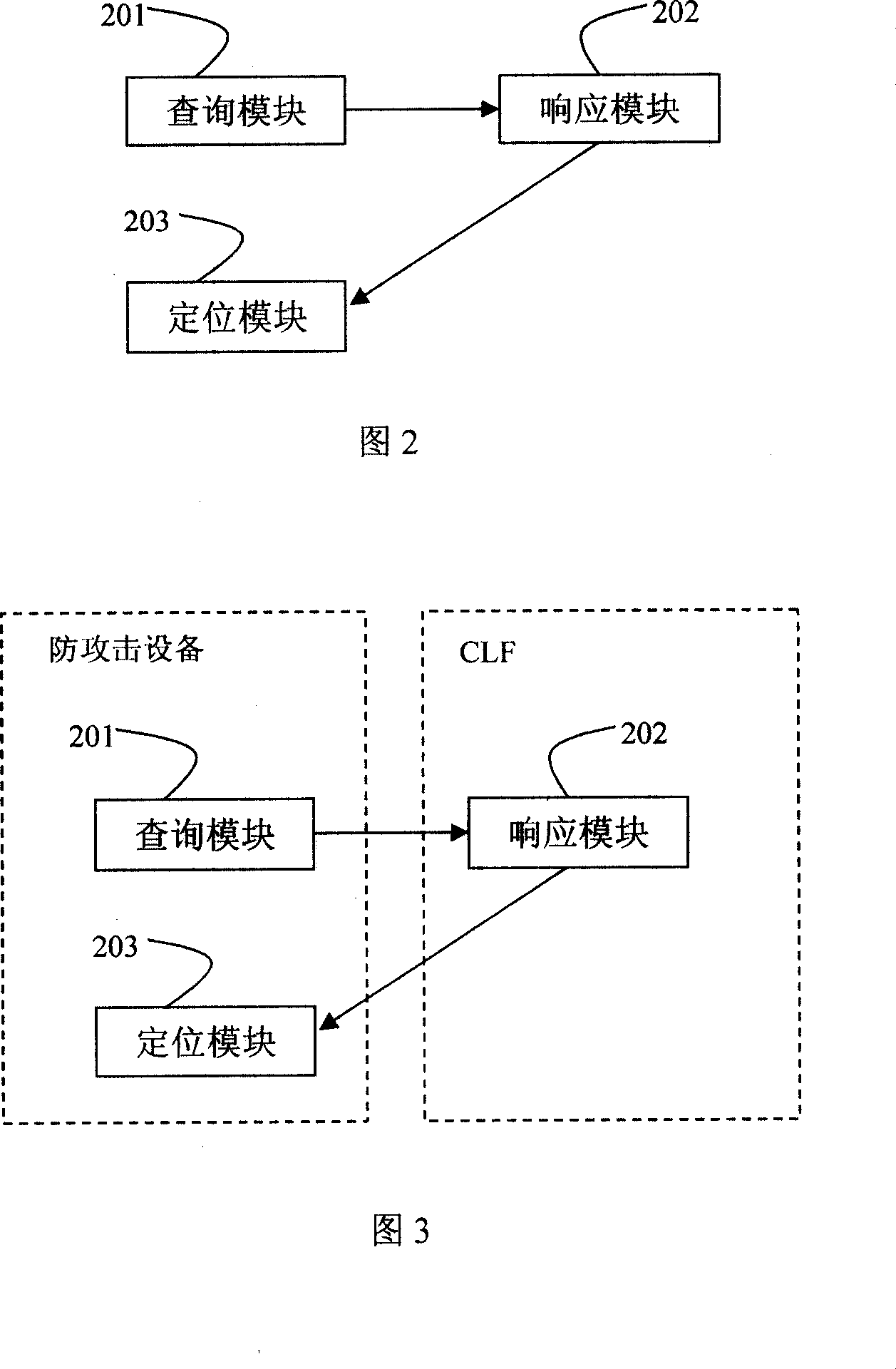
Method for locating the attack source of multimedia subsystem network, system and anti-attack system
InactiveCN101014047ASolve the problem of attackAchieve positioningRadio/inductive link selection arrangementsSecuring communicationIp addressNetwork attack
The invention provides one method, device and anti-attack system of one position IMS network attack source, which comprises the following steps: the anti-attack device tests attacks and sends require to CLF with require content composed of attacker source IP address information, CLF attacker source IP address information and sends the response information to the attack device; anti-attack device gets address information and positions attacker physical position.
Owner:HUAWEI TECH CO LTD
Safe trapping method and device and computer equipment
ActiveCN114584359AImplement deploymentSave resourcesSecuring communicationHigh level techniquesData packThe Internet
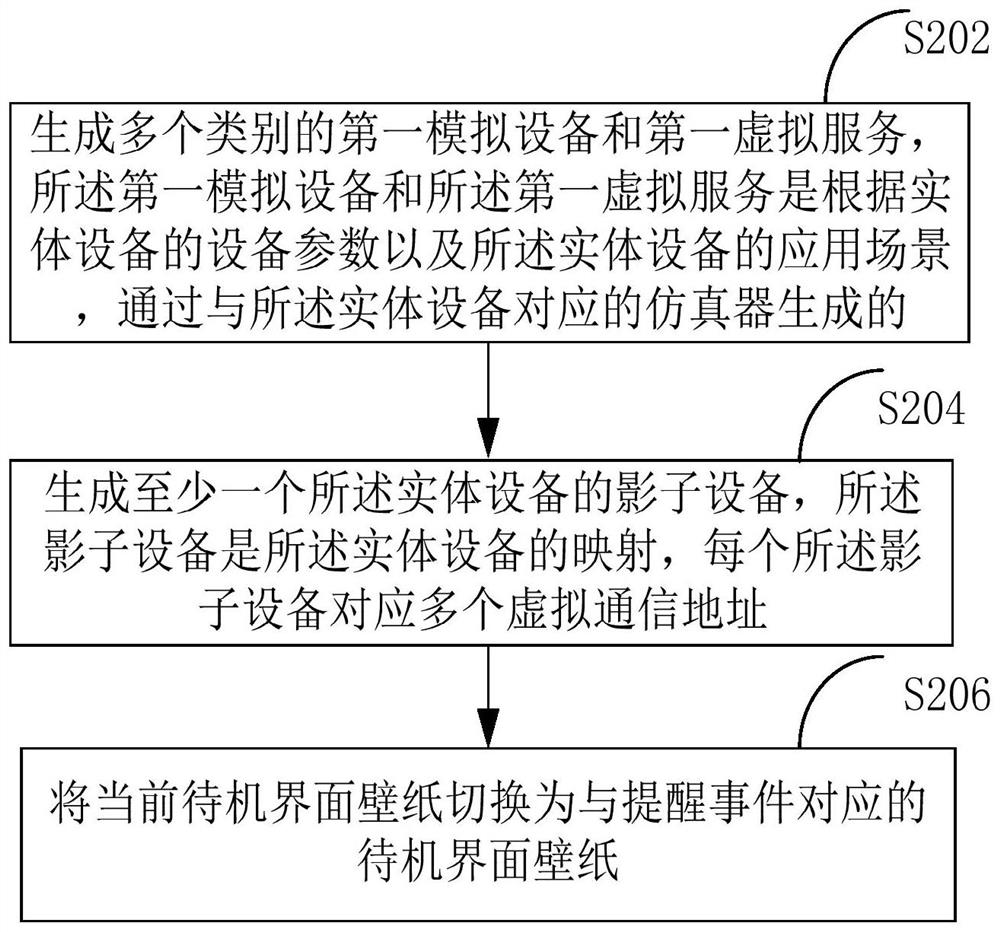
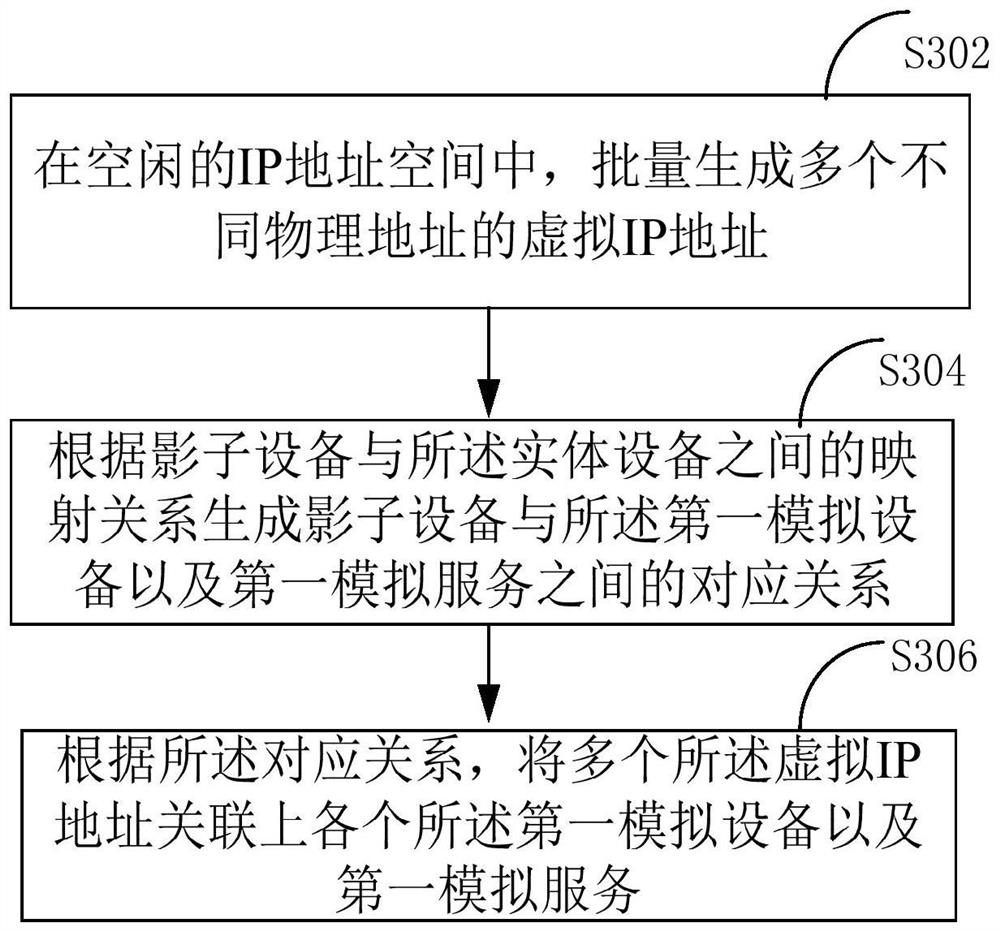
The present application is applicable to the technical field of network security, and provides a secure trapping method, comprising: generating a plurality of categories of first simulation devices and first virtual services, the first simulation devices and the first virtual services being generated through a simulator according to device parameters of physical devices and application scenarios of the physical devices; generating shadow equipment of the entity equipment, wherein each shadow equipment corresponds to a plurality of virtual communication addresses; and when the virtual communication address receives a traffic data packet from the attack device, if the shadow device corresponding to the virtual communication address is high interaction, forwarding the traffic data packet to the corresponding first simulation device and / or the first virtual service through the shadow device. According to the method, the simulation device is generated through the simulator corresponding to the entity device, and then deployment of the industrial internet deception trapping system is achieved. And a plurality of containers do not need to be generated, so that a large amount of server resources can be saved, and the cost of deploying the industrial internet deception trapping system is reduced.
Owner:烽台科技(北京)有限公司
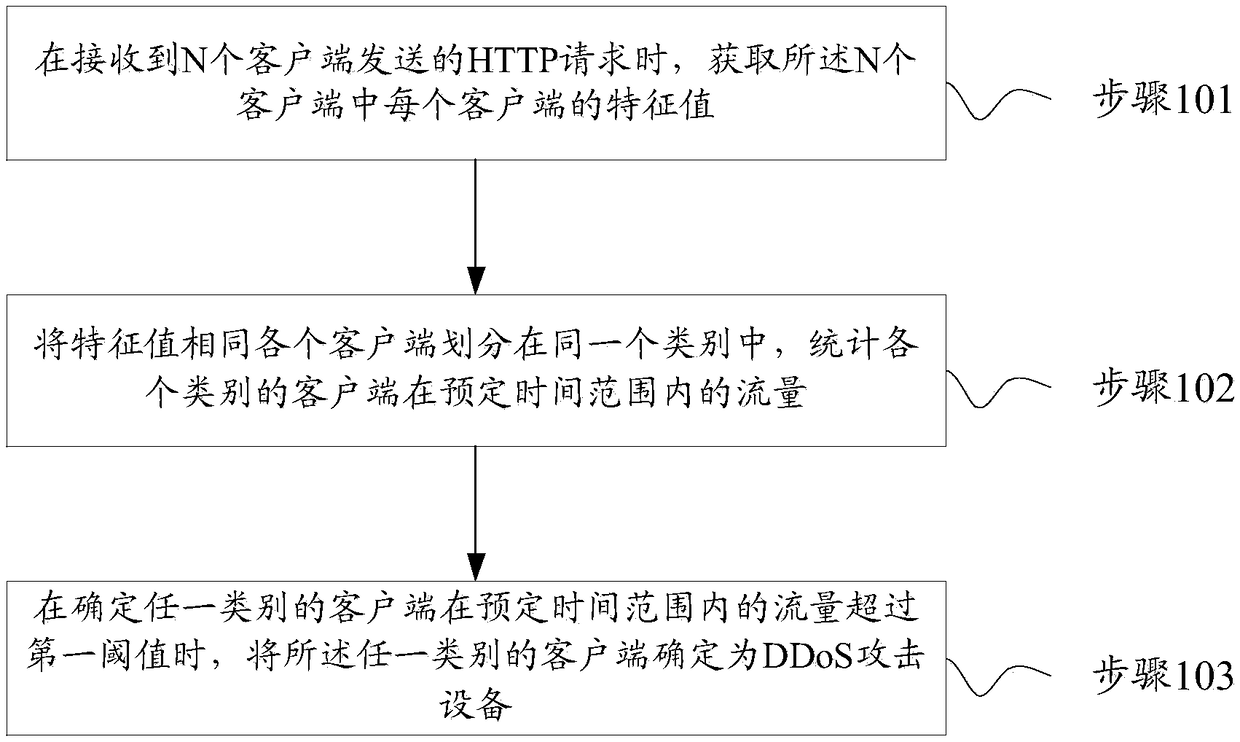
Method and device for determining DDoS attack devices
ActiveCN108600145ASolve the technical problem of not being able to identify DDoS attack devices with complete protocol stack behaviorNo interruption to browsing experiencePlatform integrity maintainanceTransmissionTime rangeProtocol stack
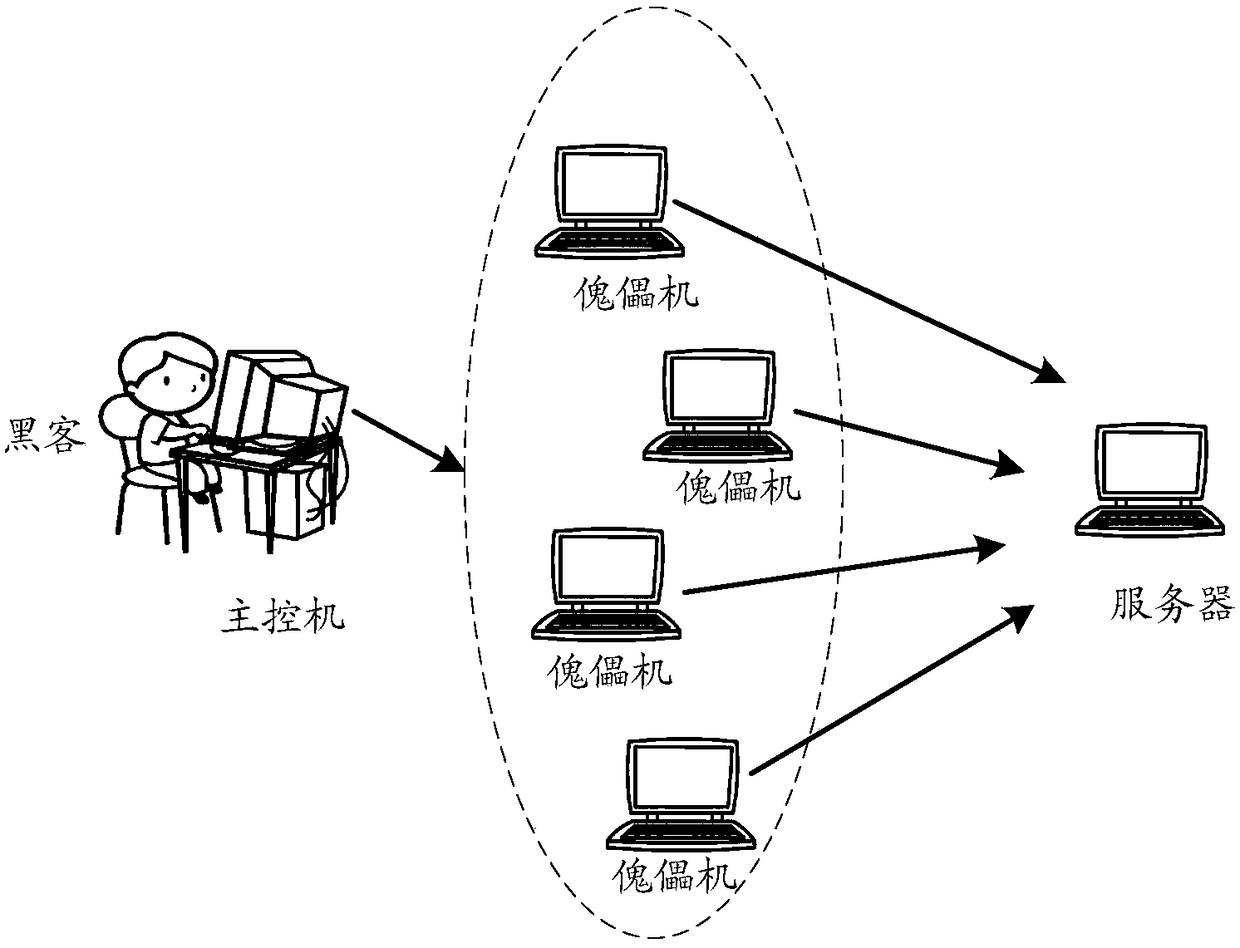
The embodiments of the present invention provide a method and device for determining DDoS attack devices. The invention aims to solve the technical problem of the failure of a method for determining DDoS attack devices in the prior art to identify a DDoS attack device having a complete protocol stack behavior and the technical problem of poor user experience. The method of the prevent invention includes the following steps that: when HTTP requests sent by N clients are received, the feature values of each of the N clients are obtained, wherein the feature values characterize applications requested by the HTTP requests initiated by the clients and / or the operating environments of the applications and / or the features of the hardware of the clients; clients with the same feature values are grouped into the same category, and the traffic of each category of clients within a predetermined time range is put into statistics; and when it is determined that the traffic of any one category of clients within the predetermined time range exceeds a first threshold, the clients of the corresponding category are determined as DDoS attack devices.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
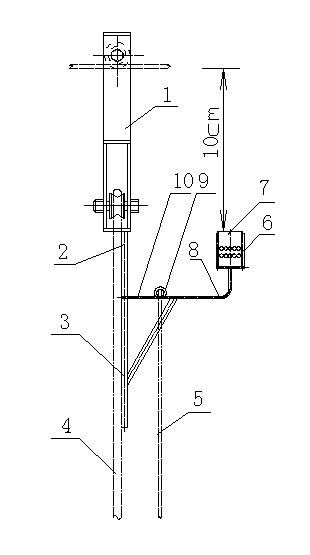
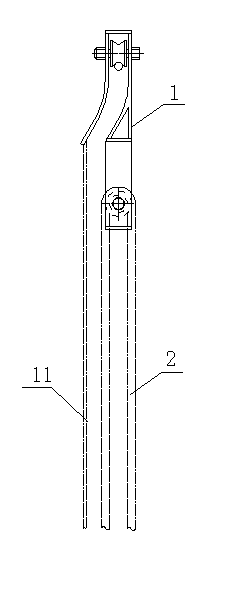
Self-turning type wire walking foreign body clearing fire attacking deviceand using method thereof
ActiveCN102842864AEasy to removeClear utilityApparatus for overhead lines/cablesAlcoholVertical edge
The invention discloses a self-turning type wire walking foreign body clearing fire attacking device which comprises a self-turning type falling pulley, a major rope, a minor rope, and a shot line. The self-turning type wire walking foreign body clearing fire attacking device further comprises a right-angle triangular support. The vertical edge of the right-angle triangular support is fixed on the major rope, and the vertical edge of the right-angle triangular support is provided with an upward extending section. When the self-turning type wire walking foreign body clearing fire attacking device is used, the upper section of the extending section exactly abuts against the lower end face of the self-turning type falling pulley. The upper right-angle edge of the right-angle triangular support is provided with another extending section extending towards the direction of the bevel edge of the right-angle triangular support, an end portion of the another extending section is provided with an L-shaped bend, and the upper end portion of the bend is provided with a U-shaped fence tank. A U-shaped alcohol lamp is arranged in the U-shaped fence tank, and the distance between the upper end of the alcohol lamp and a wire is 10 centimeters. The distance between the alcohol lamp and the major rope is 40 centimeters. A rope ring is arranged on the upper right-angle edge of the right-angle triangular support, and the minor rope is tied to the rope ring. The alcohol lamp is a jar-shaped alcohol lamp. The diameter and the height of an alcohol jar are both 8 centimeters. The height of flame formed when alcohol burns is 4 centimeters. The whole foreign body clearing link needs to be accomplished only by two persons, so that the self-turning wire walking foreign body clearing fire attacking device and the using method of the self-turning wire walking foreign body clearing fire attacking device are simple, rapid and practical.
Owner:STATE GRID CORP OF CHINA +1
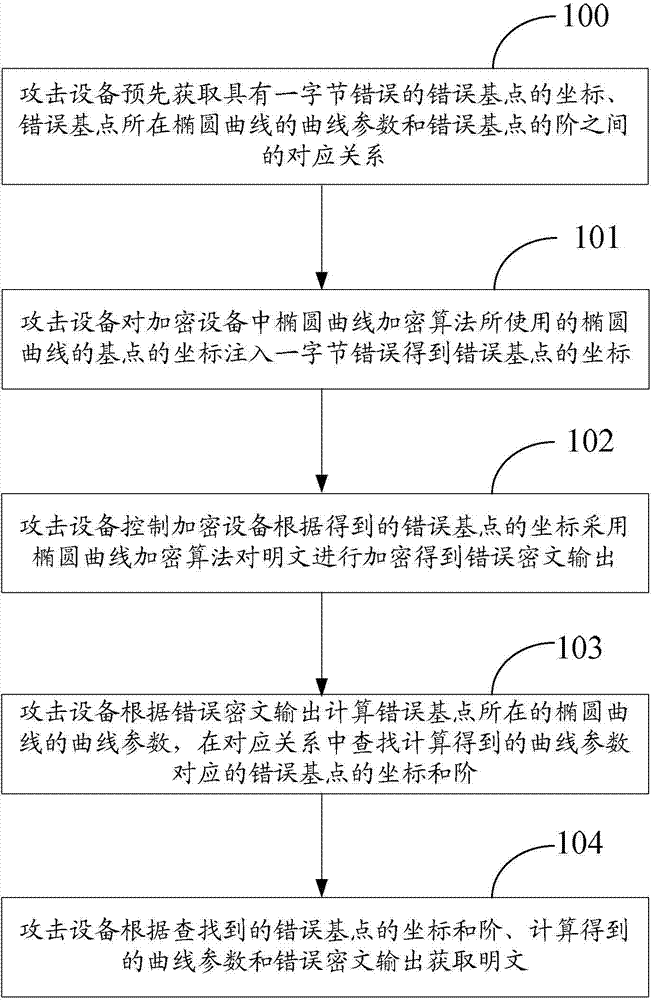
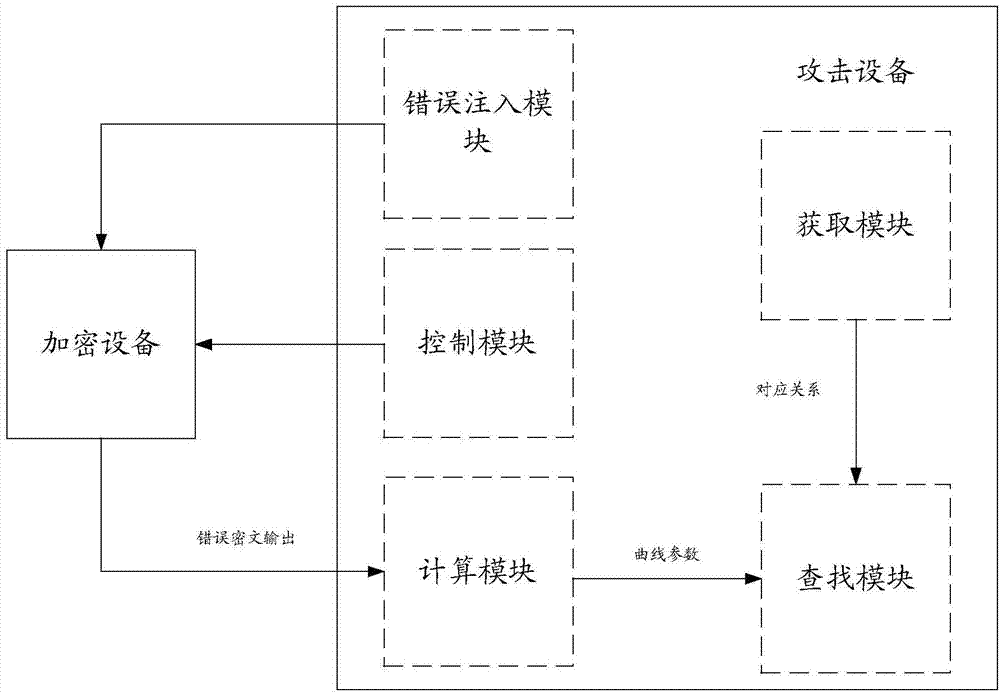
Method for attacking elliptical curve encryption algorithm and attacking device
ActiveCN104717060AThe timing of error injection is easy to controlImprove attack efficiencyPublic key for secure communicationPlaintextCiphertext
The invention discloses a method for attacking the elliptical curve encryption algorithm and an attacking device. The method comprises the steps that the attacking device acquires the corresponding relation between the coordinates of an error base point with one byte error, parameters of an elliptical curve where the error base point is located and order in advance, wherein the order meets the condition that the length of a maximum prime factor is smaller than or equal to a preset threshold value; the attacking device injects one byte error into the coordinates of a base point of an elliptical curve used by the elliptical curve encryption algorithm in an encryption unit to obtain the coordinates of the error base point; the attacking device controls the encryption unit to encrypt a plaintext by means of the elliptical curve encryption algorithm according to the coordinates of the error base point so that error ciphertext output can be obtained; the attacking device calculates the parameters of the elliptical curve where the error base point is located according to the error ciphertext output and finds the coordinates and order of the error base point corresponding to the curve parameters in the corresponding relation; the attacking device acquires the plaintext according to the coordinates and order of the error base point, the curve parameters obtained through calculation, and error ciphertext output. By the adoption of the method for attacking the elliptical curve encryption algorithm and the attacking device, attacking efficiency is improved.
Owner:DATANG MICROELECTRONICS TECH CO LTD +1
Free sparring training aid with agility improving function
InactiveCN109248427AGuaranteed stabilityWill not shiftSport apparatusSports equipmentElectric machinery
The invention relates to the technical field of sports equipment, in particular to a free sparring training aid with an agility improving function. The free sparring training aid comprises a supporting column vertically arranged, a leg main attack device, a front main attack device, a head main attach device and a control device. The head main attack device comprises a head attacking mechanism anda head driving mechanism used for driving the head attacking mechanism to rotate. The front main attack device comprises a front attacking mechanism and a first swinging assembly used for driving thefront attacking mechanism to swing. The leg main attack device comprises a leg attack mechanism and a second swinging assembly driving the leg attacking mechanism to swing. The control device comprises a controller and a sensor assembly electrically connected with the controller. Training stability of an athlete is guaranteed. Output shafts of a rotating motor and a driving motor are prevented from offset. The training effect of the athlete can be improved.
Owner:高婷婷
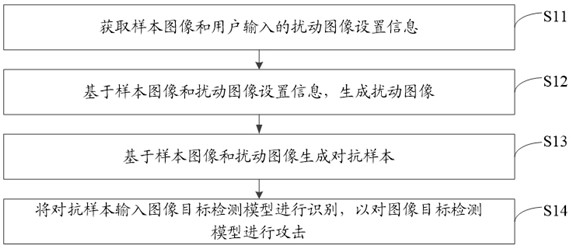
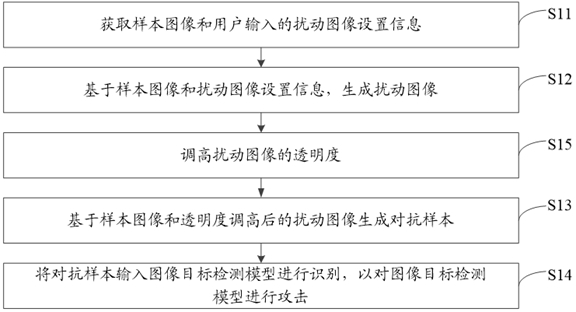
Image target detection model attack method and device, terminal equipment and storage medium
ActiveCN112215227AStrong attackImperceptibleCharacter and pattern recognitionMachine learningRadiologyTerminal equipment
The invention discloses an image target detection model attack method, and the method comprises the following steps: obtaining a sample image and disturbance image setting information inputted by a user, wherein the disturbance image setting information comprises the size and shape of an image; generating a disturbance image based on the sample image and the disturbance image setting information;generating an adversarial sample based on the sample image and the disturbance image; and inputting the confrontation sample into the image target detection model to be recognized so as to attack theimage target detection model. Since the size and the shape of the disturbance image are set by a user and the user setting has randomness and uncertainty, the difference between the confrontation sample and the sample image is not easy to perceive by naked eyes, the disturbance concealment is high, and the attack intensity is large. The invention further discloses an image target detection model attack device, terminal equipment and a storage medium, the concealment of disturbance is improved, and therefore the attack strength on the image target detection model is improved.
Owner:PENG CHENG LAB
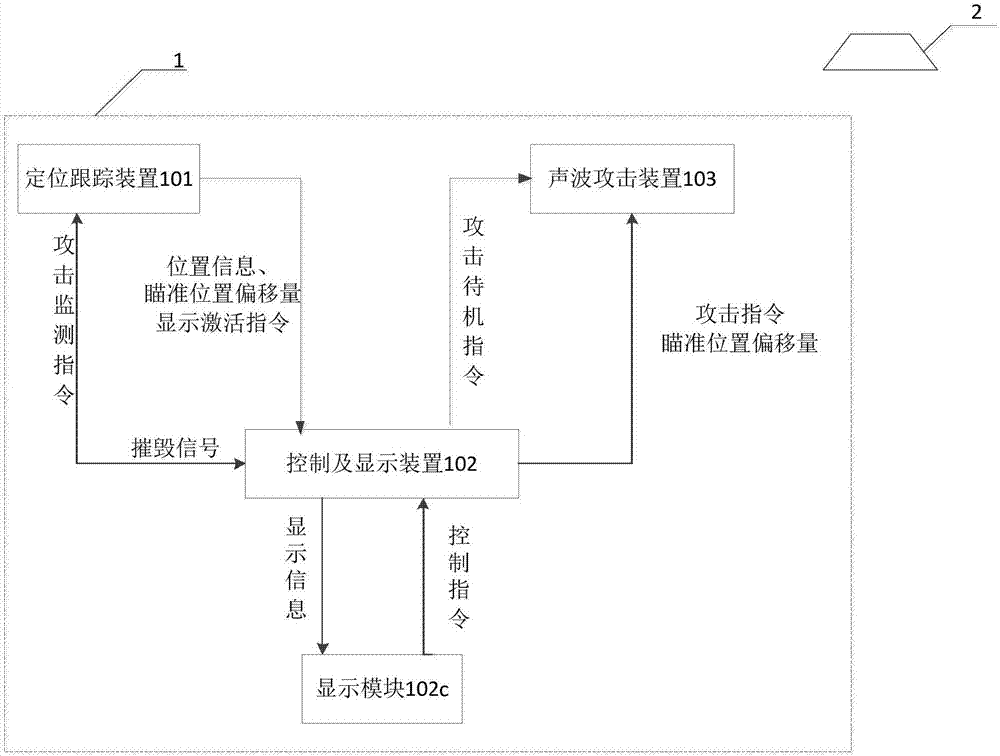
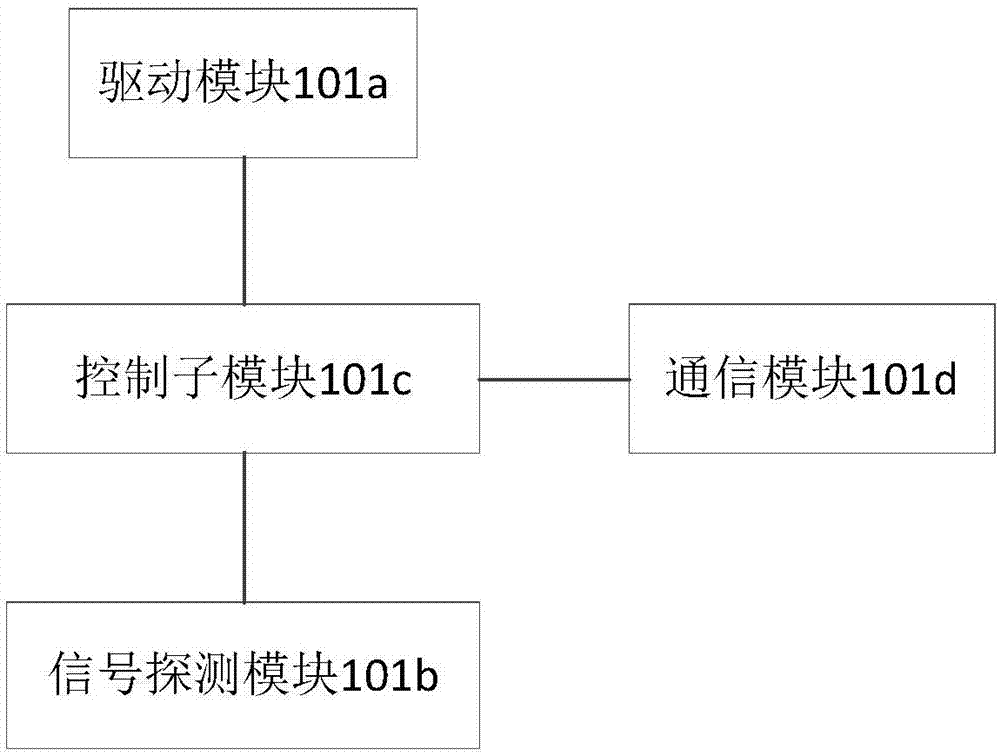
Sound wave based anti-UAV system
The invention discloses a sound wave based anti-UAV (unmanned aerial vehicle) system which is characterized in that position information of an attack UAV is found and collimation position deviation is calculated in real time through a positioning tracking device, and the position information and the collimation position deviation are transmitted to a control and display device in real time; the control and display device transmits the collimation position deviation to a servo module of a sound wave attack device in real time so as to drive the sound wave attack device to aim at the target UAV dynamically in real time; when the target UAV enters an early warning range, the control and display device displays a motion trail of the target UAV in real time; and when the target UAV enters an attack range, the control and display device sends an attack instruction to the sound wave attack device, the sound wave attack device then transmits a sound wave attack signal to the target UAV, and the UAV generates resonance and thus falls down. Through a method of toughly destroying the UAV on general and special occasions by emitting sound waves capable of resonating with a component of the UAV, the purpose that the UAV can be effectively struck in general cases and can also be struck back in particular cases is achieved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Martial art arena robot going onto stage in tail slope mode
InactiveCN109966754AFlexible movementHigh-precision detectionSelf-moving toy figuresRemote-control toysEngineeringLaser sensor
The invention relates to a martial art arena robot going onto a stage in a tail slope mode. The martial art arena robot comprises a base plate part, a slope stage going part, an upper layer structure,a shovel attacking device, a sensor module layout, a battery part and a control circuit part. The martial art arena robot goes onto an arena with a certain height by using the tail slope; the stage going speed is high; and the success rate is high. A plurality of laser sensors and grayscale sensors are installed, so that the arena robot accurately detects the edge of the arena, fast recognizes anopponent, and sensitively gives a response. In a control aspect, a serial bus connection mode is used. In a structure aspect, the martial art arena robot has the advantages that materials are saved;the processing is easy; the production period is short; and the transformation is easy, and the like.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Polarizer attaching device
InactiveCN109143630ASolve the problem of cutting accuracyReduce rework rateNon-linear opticsEngineeringPolarizer
The invention provides a polarizer attaching device. The polarizer attacking device comprises a device platform, an image sensor component and an aligning mechanism, wherein the image sensor componentcomprises a first sensor and a second sensor located at a transverse side of the first sensor, and the first sensor and the second sensor are located on the same straight line; the aligning mechanismcomprises a first aligning component located at a longitudinal side of the first sensor and a second aligning component located at the longitudinal side of the second sensor; the image sensor component further comprise a third sensor located at the longitudinal side of the first sensor. The polarizer attaching device has the beneficial effects of converting a small oblique angle into linear gap,thereby recognizing the small oblique angle by the image sensors, solving a problem that attaching accuracy is influenced by cutting accuracy of the polarizer, reducing factors influencing the attaching accuracy, enabling the attaching accuracy to be more steady, making attaching more accurate, meanwhile, also being capable of performing early warning if cutting of the polarizer exceeds made specifications, and reducing a rate of reworking.
Owner:SHENZHEN CHINA STAR OPTOELECTRONICS SEMICON DISPLAY TECH CO LTD
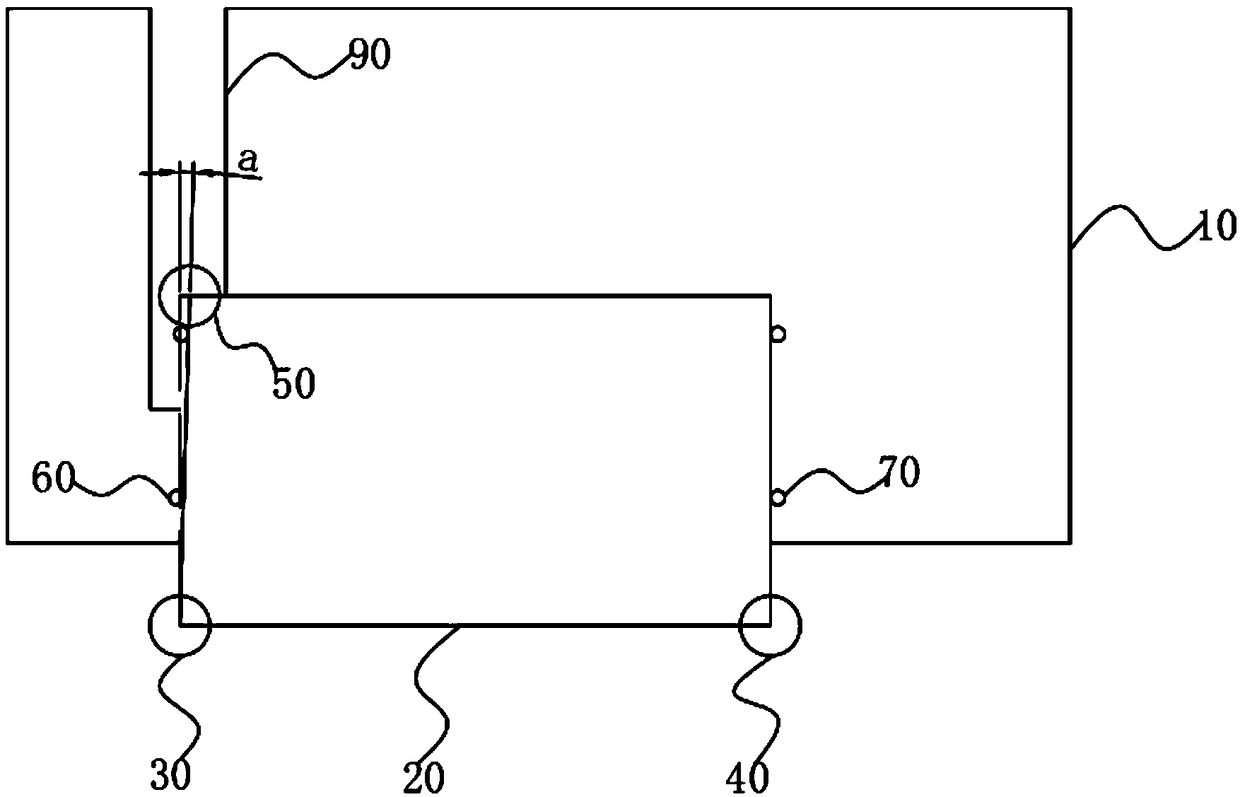
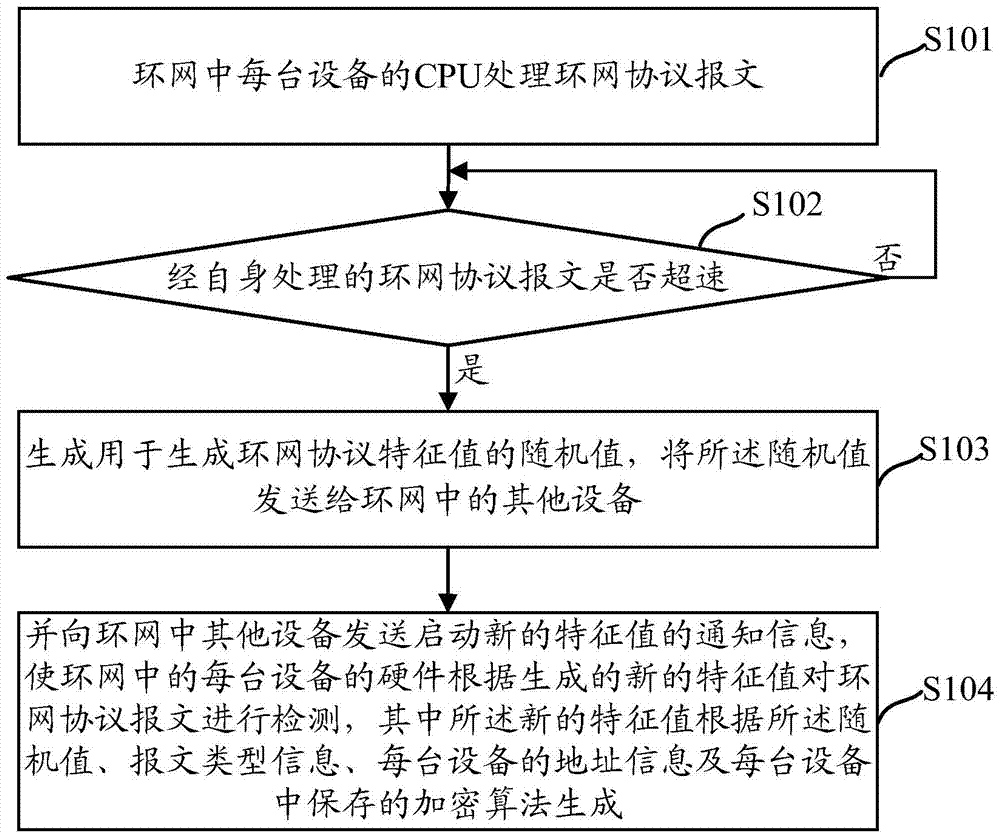
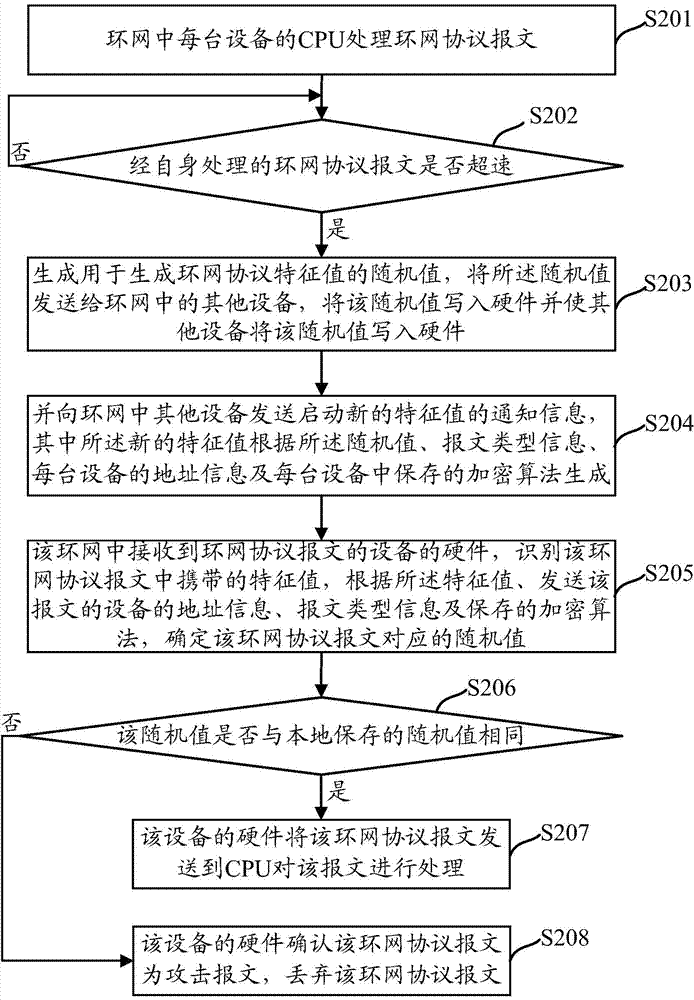
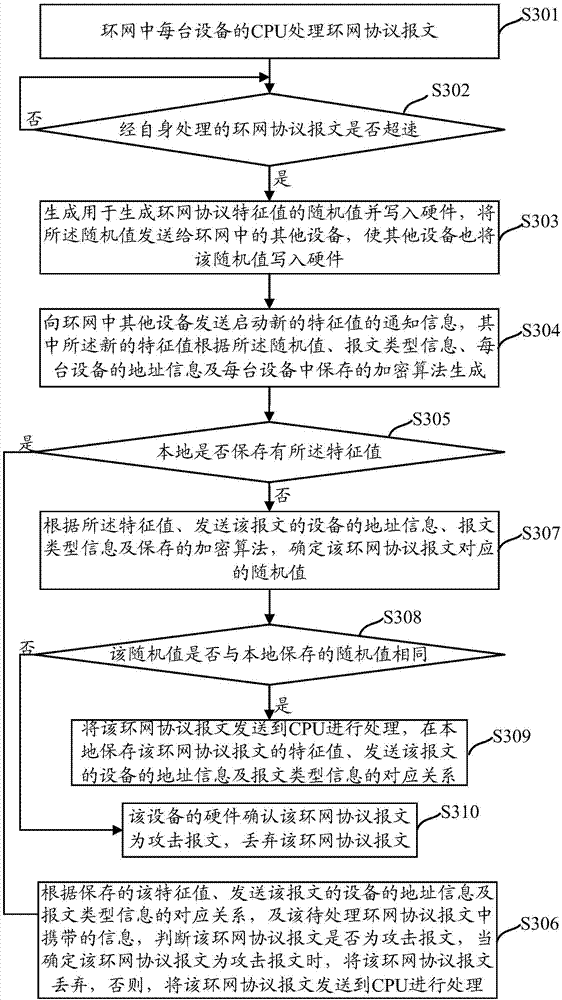
Method and device for preventing looped network protocol message from attacking device CPU
Owner:KYLAND TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com